RFID lightweight class bidirectional authentication method based on PUF
A two-way authentication, lightweight technology, applied in the field of Internet of Things and information security authentication, can solve the problems of inability to resist counterfeit attacks, insufficient security, incorrect update of readers, etc., to achieve the effect of resisting counterfeit attacks and reducing complexity and cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
[0049] The specific process of a kind of PUF-based RFID lightweight two-way authentication method of the present invention is as follows:
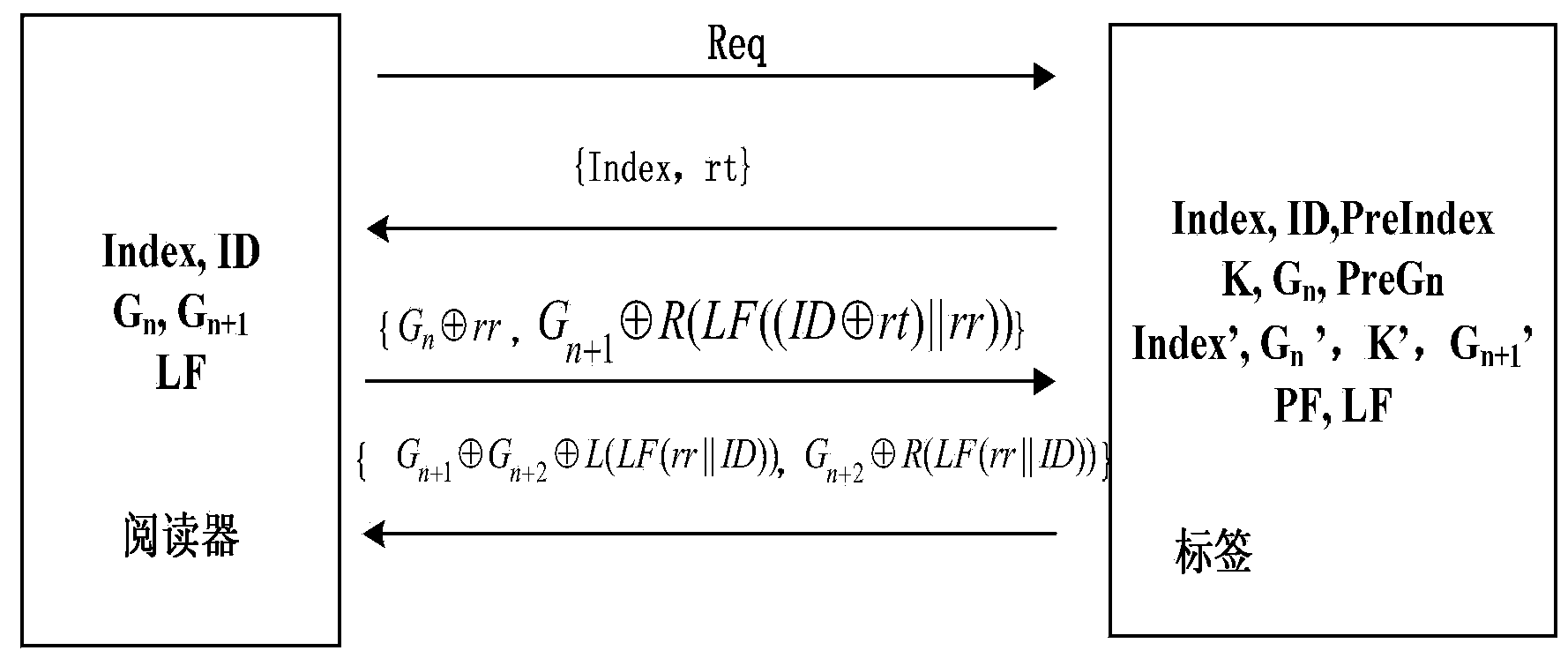
[0050] (1) Initialization
[0051] refer to figure 1 , when the present invention is initialized, there are 2 data structures stored inside each tag, one is {Index, ID, k, Gn}, and the other is the Index and Gn when the last tag passed the reader authentication for synchronization , denoted as {PreIndex, PreGn}, and stores PF, LF and updated values k', Gn' and G n+1 '. And the reader stores a data structure about each tag {Index, ID, Gn, G n+1}, while storing the same LF as the tag, and also integrates a pseudo-random number generator.
[0052] (2) Two-way authentication process
[0053] The RFID two-way authentication process of the present invention is as figure 1 shown. Among them, Req is the authentication request, M1={Index, rt}, M2= { , } , M3={ , }.
[0054] The detailed authentication process of the present inven...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com