Authentication device using true random number generating element or pseudo-random number generating element, authentication apparatus, and authentication method
a technology of true random number generating element and authentication device, applied in the direction of digital transmission, unauthorized memory use protection, instruments, etc., can solve the problems of increasing management cost, and inability to authenticate, so as to achieve the effect of limiting the number of users
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
first embodiment
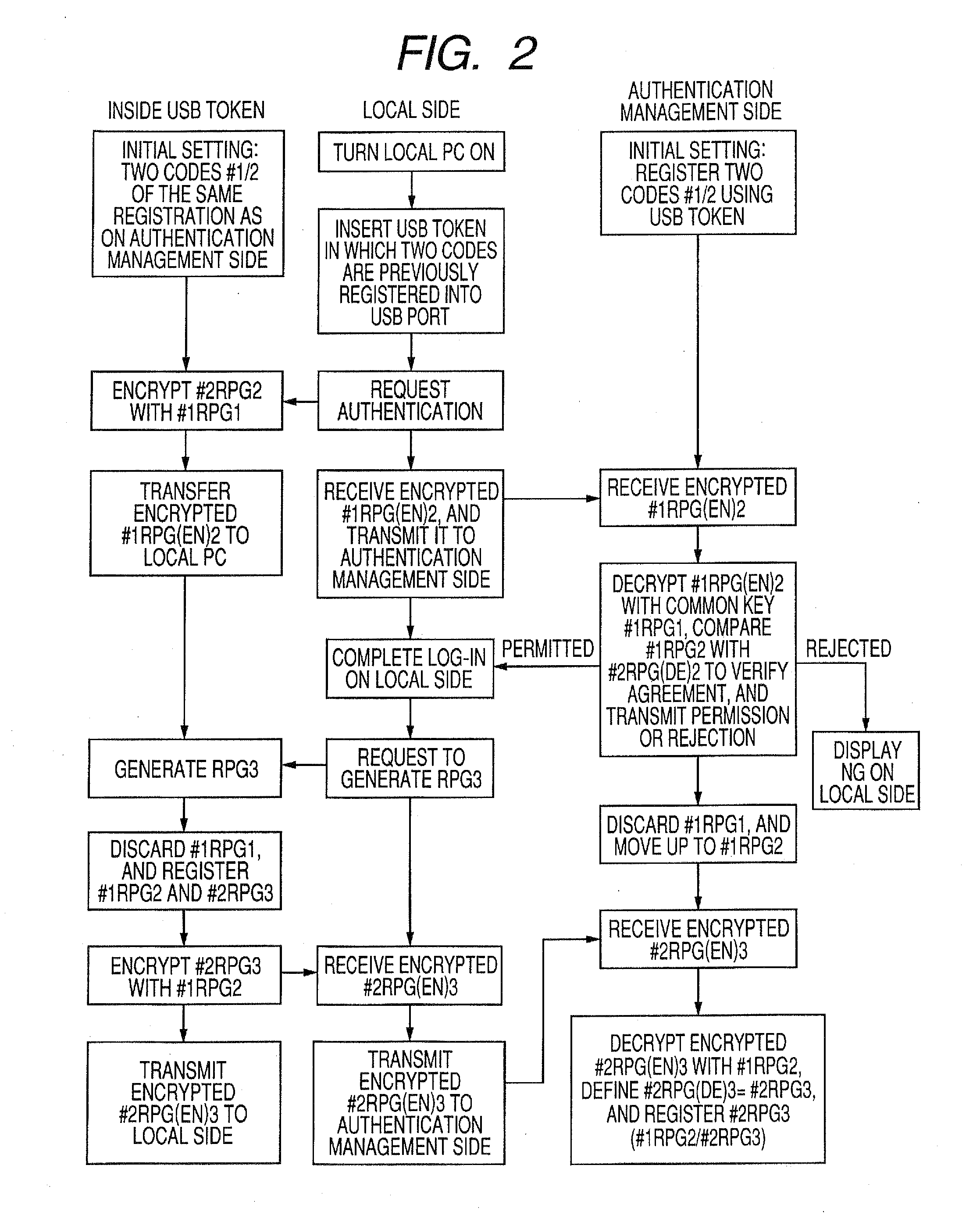
[0030]First, description is made of a system for performing an authentication by using two codes (the number of the used codes is not limited to two) that are generated in a true (or intrinsic) random number generator or a pseudo-random number generator (hereinafter, referred to as “RPG”). The system includes a USB token, a local side (PC), an authentication management side, etc. Herein, the USB token is used as a token (code generating device), and its shape may vary from a card type to a key fob type or the like, but there is no particular limitation on the shape. The same holds true in the other embodiments described later.
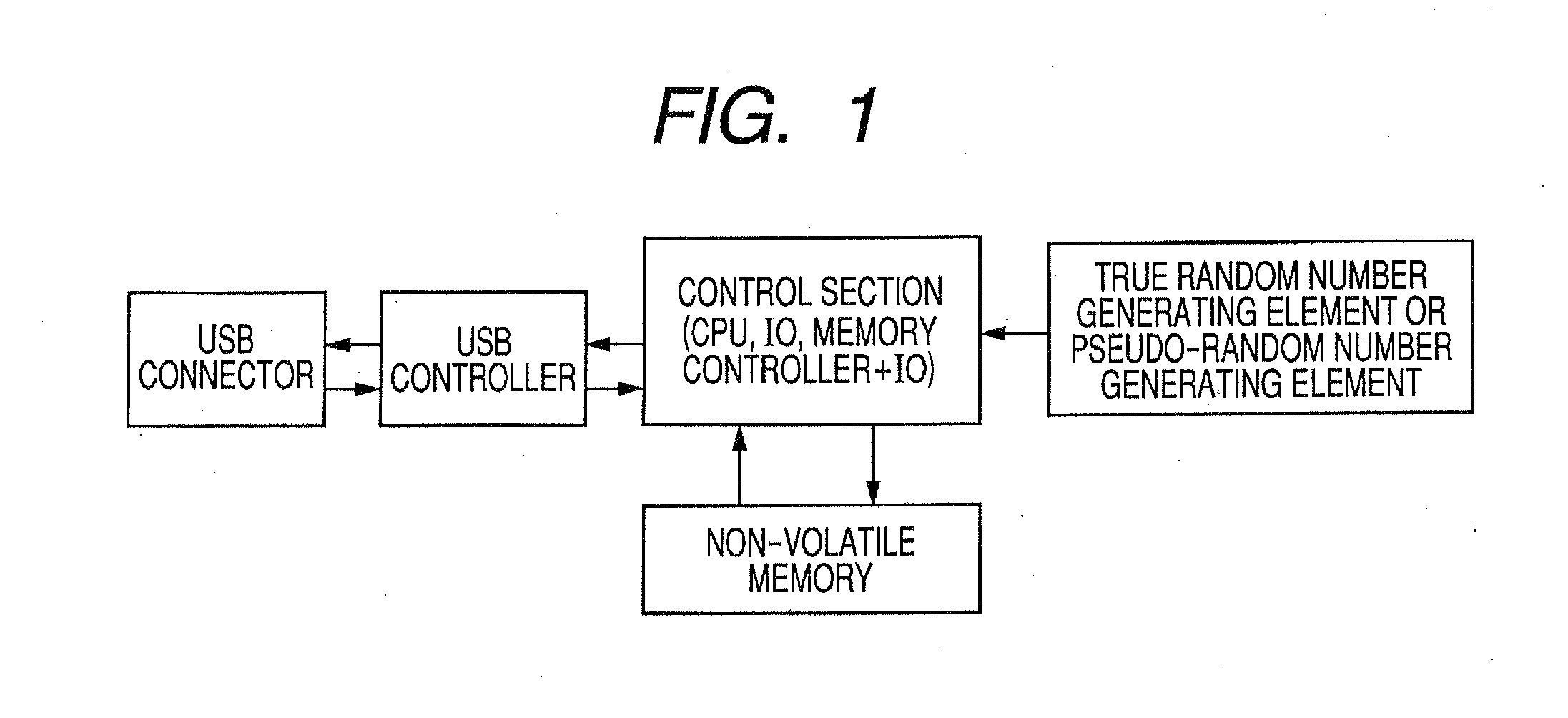
[0031]FIG. 1 is a block diagram of a token used in this embodiment. In this example, USB is used as an interface, but another interface may be used.
[0032]Two codes generated in a true random number generating element or a pseudo-random number generating element are read by a control section, and stored in a non-volatile memory. The control section includes a CP...
second embodiment
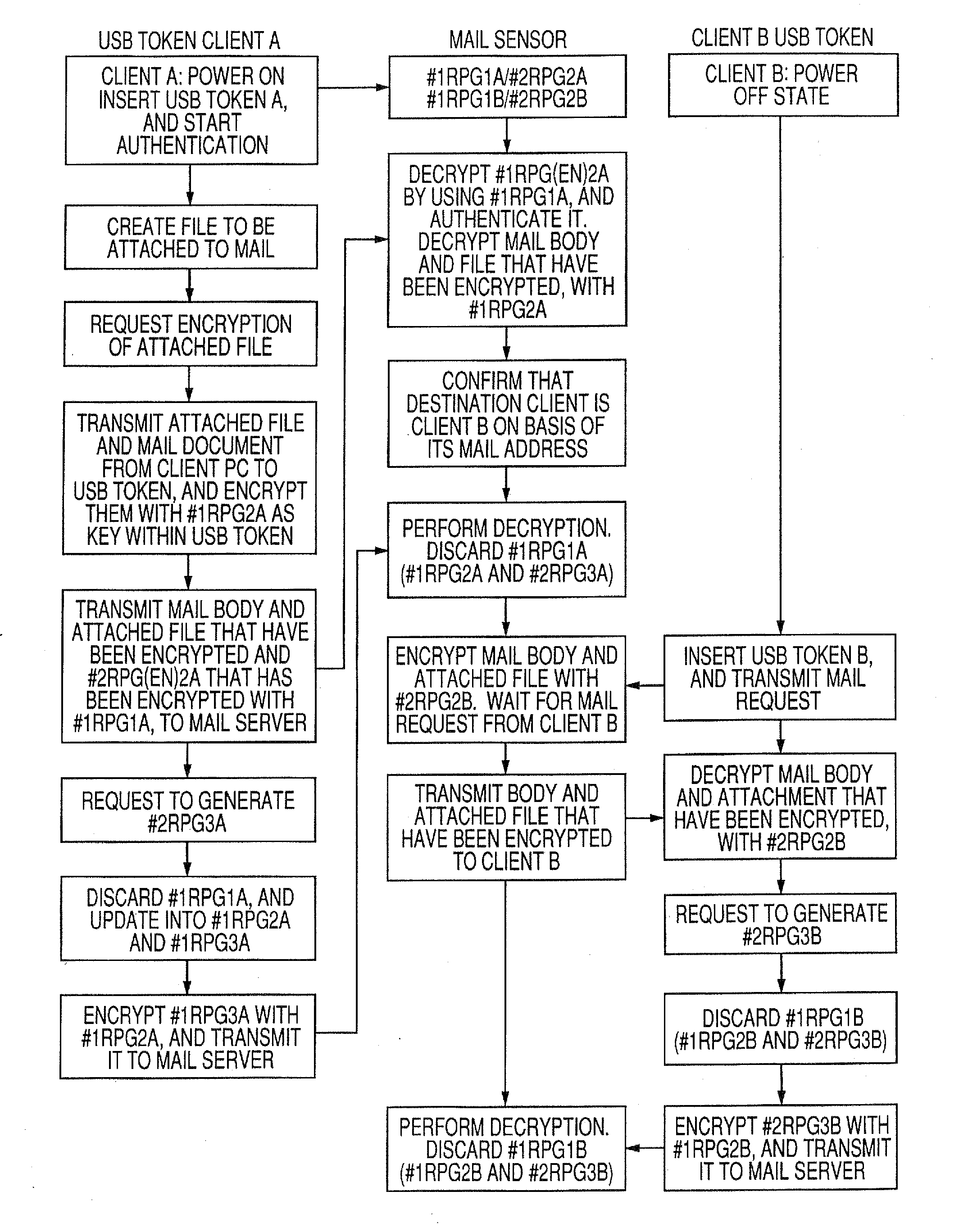
[0062]Next, description is made of a mail server system that can ensure a complete secrecy by using the two codes generated in the true random number generator or the pseudo-random number generator (RPG) to perform an identification authentication and an encryption / decryption of a plain text. The system includes two clients of a sender and a recipient of mail (each owning authentication USB token) and a mail server (SMTP server used for reception and POP server used for transmission).
[0063]First, in order to configure the system, it is assumed that the following preconditions are set.
[0064](1) With regard to (two, herein) the two clients (clients A and B), two codes RPGA1 (initial common key) and RPGA2 (initial ID) and two codes RPGB1 (initial common key) and RPGB2 (initial ID), respectively, are registered on a mail server side in advance. Obviously, mail addresses of the clients A and B are also registered thereon.
[0065](2) Installed on the mail server are a plain text encryption / ...
third embodiment
[0100]Next, description is made of an embodiment of a case of applying the authentication using the two codes generated in the true random number generator or the pseudo-random number generator (RPG) to a system for distributing a streaming video via a network such as a CATV or the Internet.
[0101]FIG. 4 is a block diagram illustrating an outline of a video distribution system to which authentication means according to the embodiment of the present invention is applied. The system shown in FIG. 4 includes a user-side terminal (set-top box of CATV or streaming reception apparatus (PC)), a video streaming server (hereinafter, referred to as “server”), and an authentication manager. An authentication management function of the authentication manager can be installed on the server. In a case of CATV, the server corresponds to a broadcast station of the cable TV.
[0102]An authentication process in the system is as follows.
[0103](1) Logon is made to the server from the user side.
[0104]For e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com