Identity recognition method based on keystroke characteristics
A technology of identification and keystroke, which is applied in the field of network security identification, can solve the problems of complex operation, low correct identification rate, and high cost, and achieve the effect of convenient data collection and real-time identification and verification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
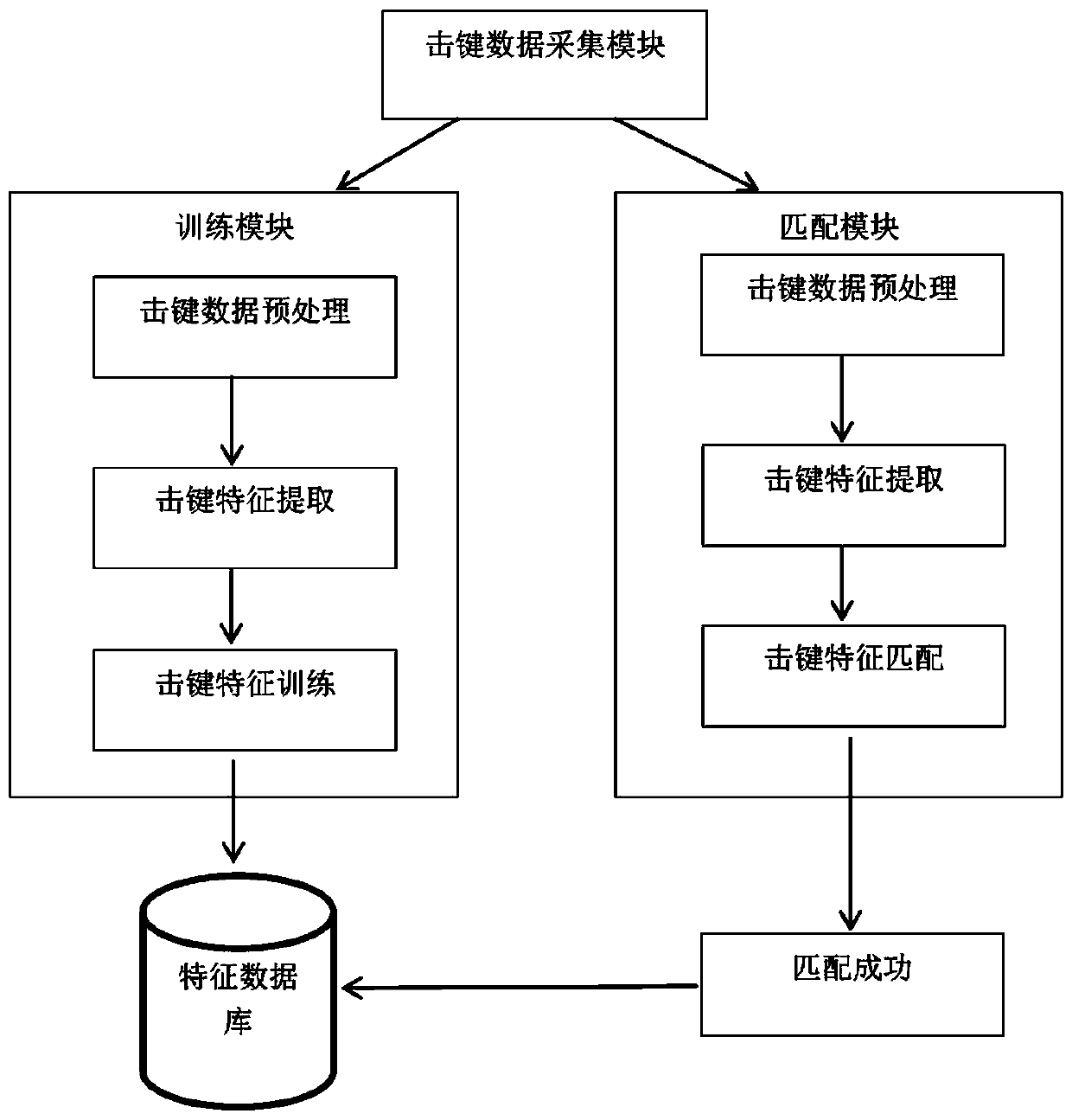
[0032] Such as figure 1 As shown, the identification method based on keystroke features includes a keystroke data acquisition module, a training module and a matching module;
[0033] The keystroke data acquisition module mainly completes the collection of keystroke data generated by the user when the user performs a keystroke behavior, and obtains the original data;
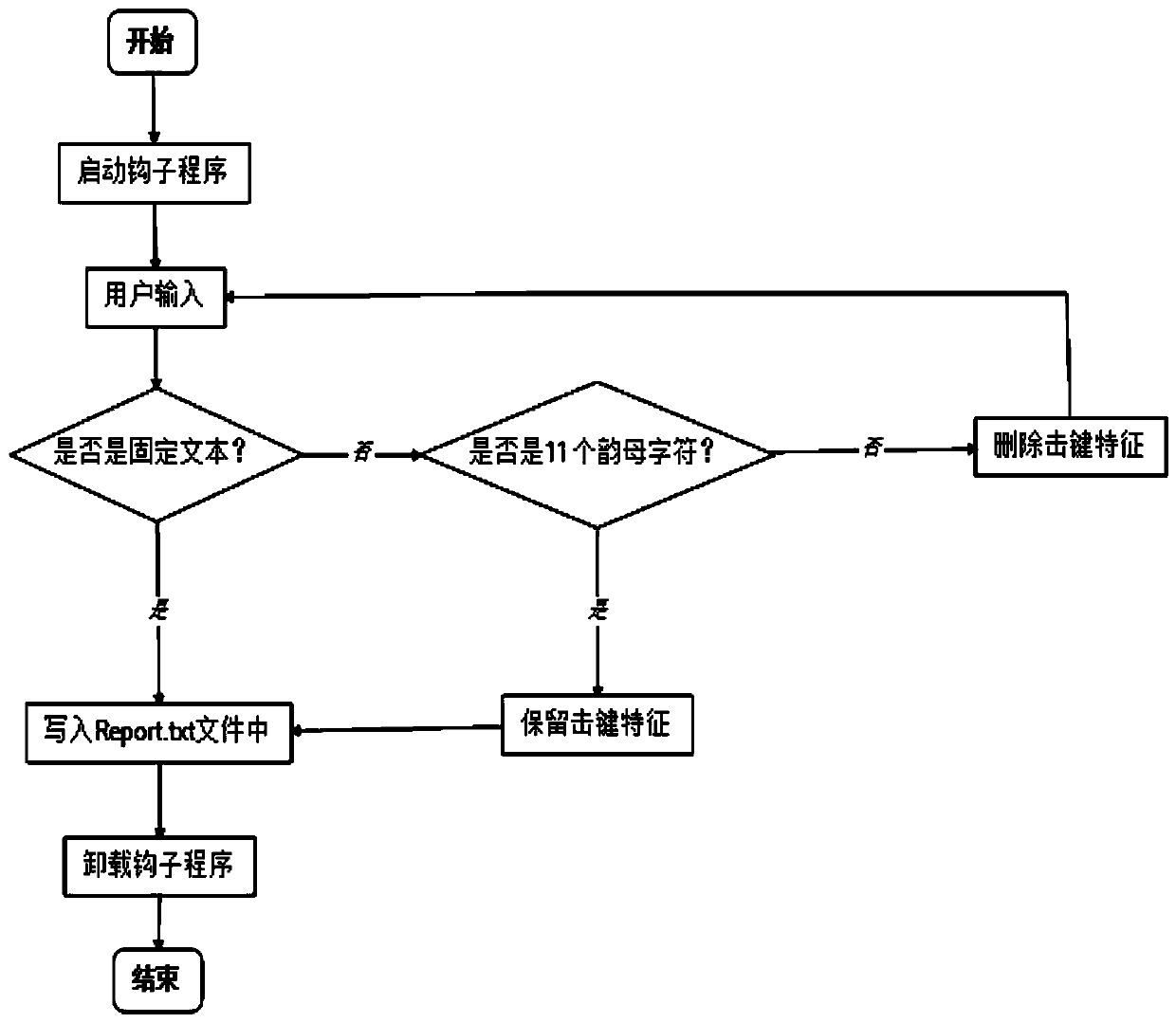
[0034] The training module completes the extraction and separation of keystroke feature data; performs keystroke data preprocessing and keystroke feature extraction on the sample keystroke information input by the user from the keyboard, and completes the training and classification of user sample data to generate a feature database; Data preprocessing mainly cleans the user's keystroke feature data; keystroke feature extraction mainly extracts keystroke feature information, key press time, key release time, key bounce time, and keystroke fingerprint features;
[0035] Described matching module finishes discrim...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com