Authentication management method and related equipment
A technology for authentication management and information management, applied in the fields of terminal equipment and authentication management systems, authentication management methods, and empowered servers, it can solve problems such as malicious deductions, evasion of tolls, and irregular key media management, and achieve enhanced Authentication strength, effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
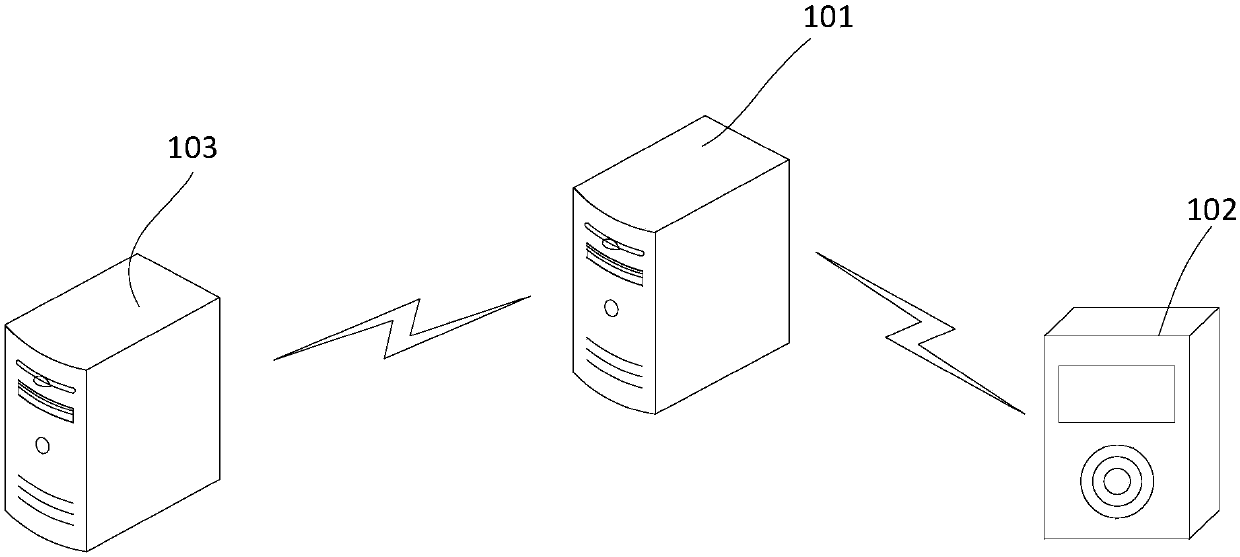
[0059] Such as figure 1 as shown, figure 1 The system architecture diagram involved in the authentication management method provided by the embodiment of the present invention. The system architecture includes an authorization server 101 , a terminal device 102 and a service center system 103 , and the authorization server 101 can communicate with the terminal device 102 and the service center system 103 respectively. In other embodiments, the terminal device 102 can also communicate with the service center system 103 .
[0060] The service center system 103 can be used to authenticate the authorization server, allocate authorization times for the authorization server 101, and identify and manage the authorization server 101 and other equipment.
[0061] The authorization server 101 can be used to authorize and manage the authentication of the terminal device 102 and the authentication module on the terminal device 102, for example, manage the usage times of the authenticati...
Embodiment 2
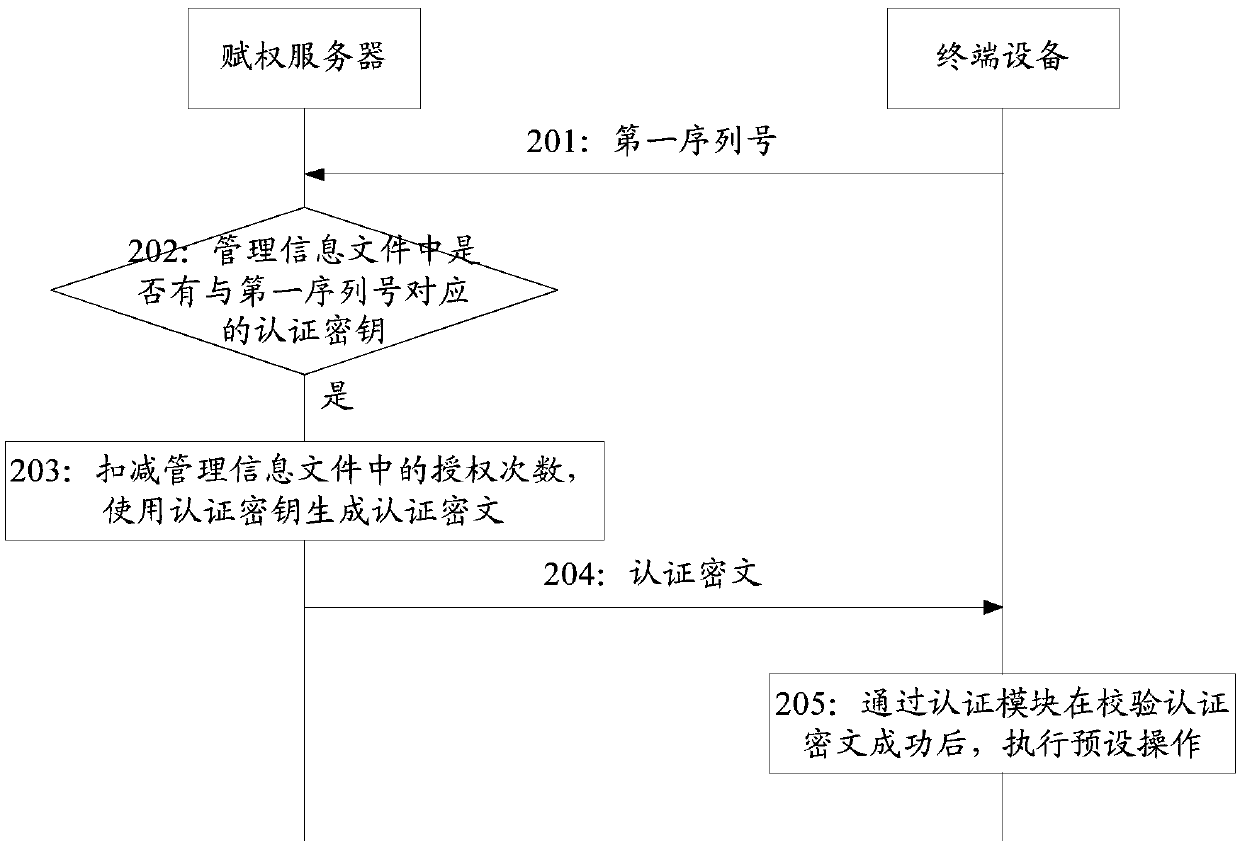
[0071] Such as figure 2 as shown, figure 2 It is a schematic flowchart of an authentication management method provided by an embodiment of the present invention.
[0072] refer to figure 1 Examples shown, and figure 2 , the authentication management method of the embodiment of the present invention, comprises the following steps:
[0073] Step 201: The authorization server acquires the first serial number sent by the terminal device.
[0074] Wherein, the first serial number is identification information of the authentication module on the terminal device. For details about the authorization server, terminal devices and authentication modules, please refer to figure 1 A detailed description of the illustrated embodiment.
[0075] The terminal device sends the first serial number to the authorization server, so that the authorization server can obtain the first serial number.
[0076] For example, after detecting that a certain authentication module is powered off and...
example 1
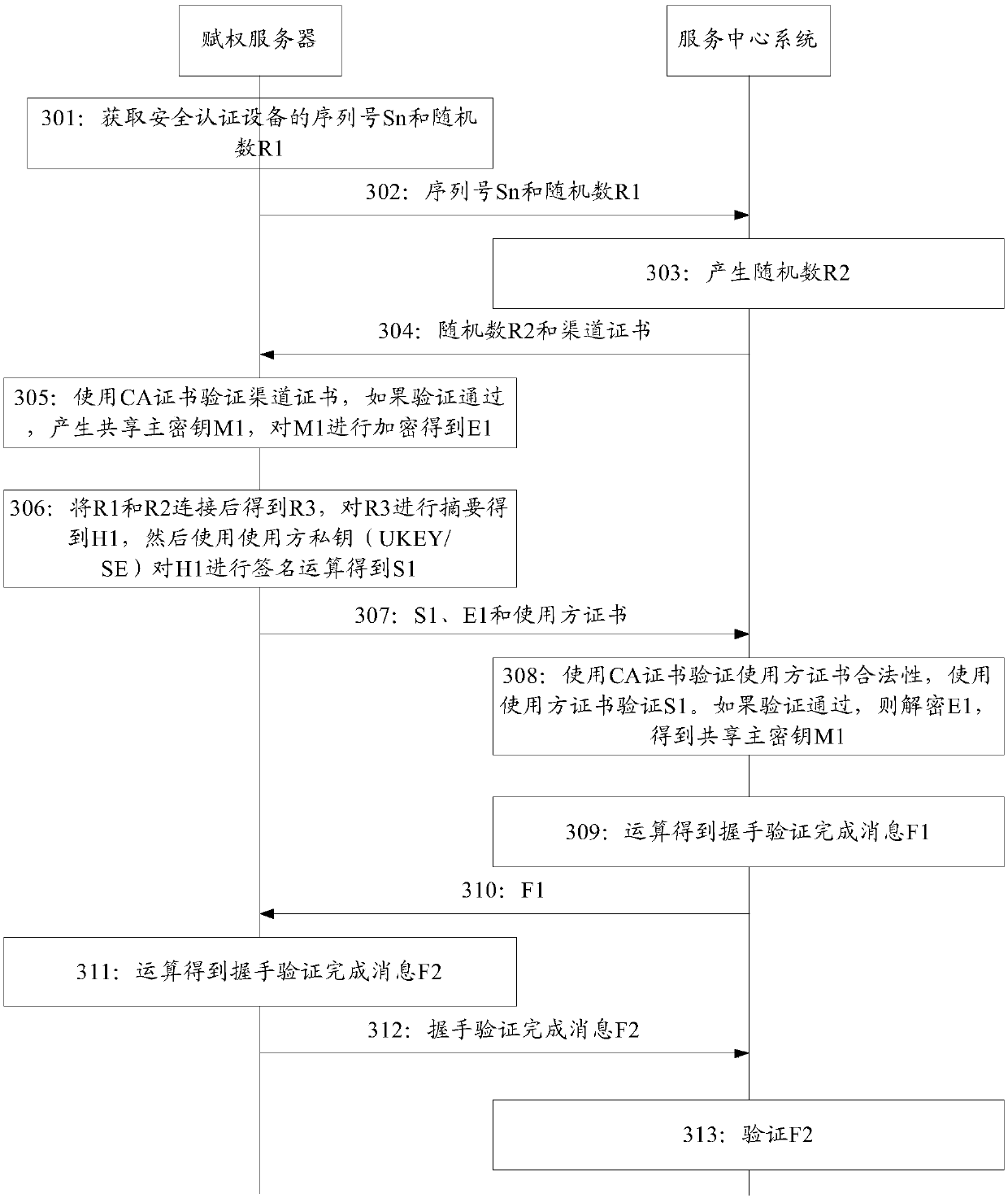
[0130] Such as Figure 4 As shown, in this example, the specific process is as follows:
[0131] Step 401: The authorization server shakes hands with the service center system. For the specific handshake process, please refer to image 3 The specific description of the embodiment of the handshake between the authorization server and the service center system shown. After the handshake is successful, the session key is temporarily stored in the security authentication device, such as the work key and the message authentication code (Message Authentication Code, MAC) key, etc. In the subsequent process, the data transmission between the terminal equipment installed with the authentication module and the center is encrypted and protected by the working key, and the process will not be described in detail.
[0132] Step 402: The authorization server initiates an instruction to acquire a random number of the security authentication device.
[0133] Step 403: The authorization se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com