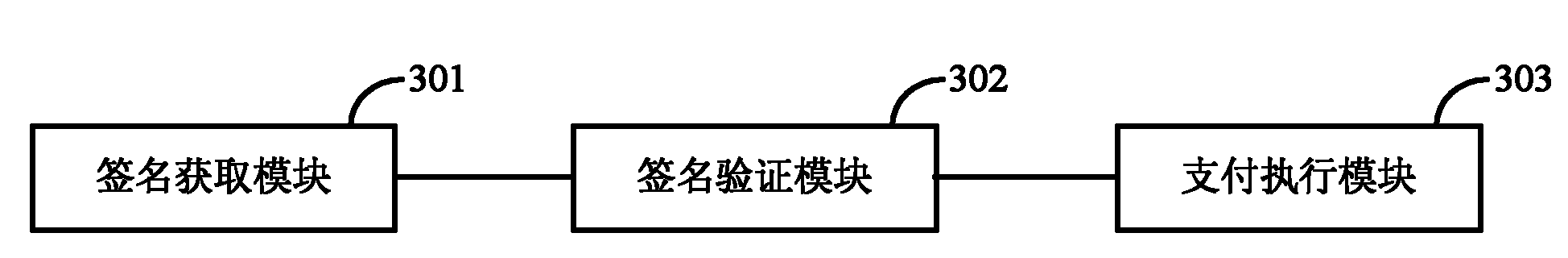
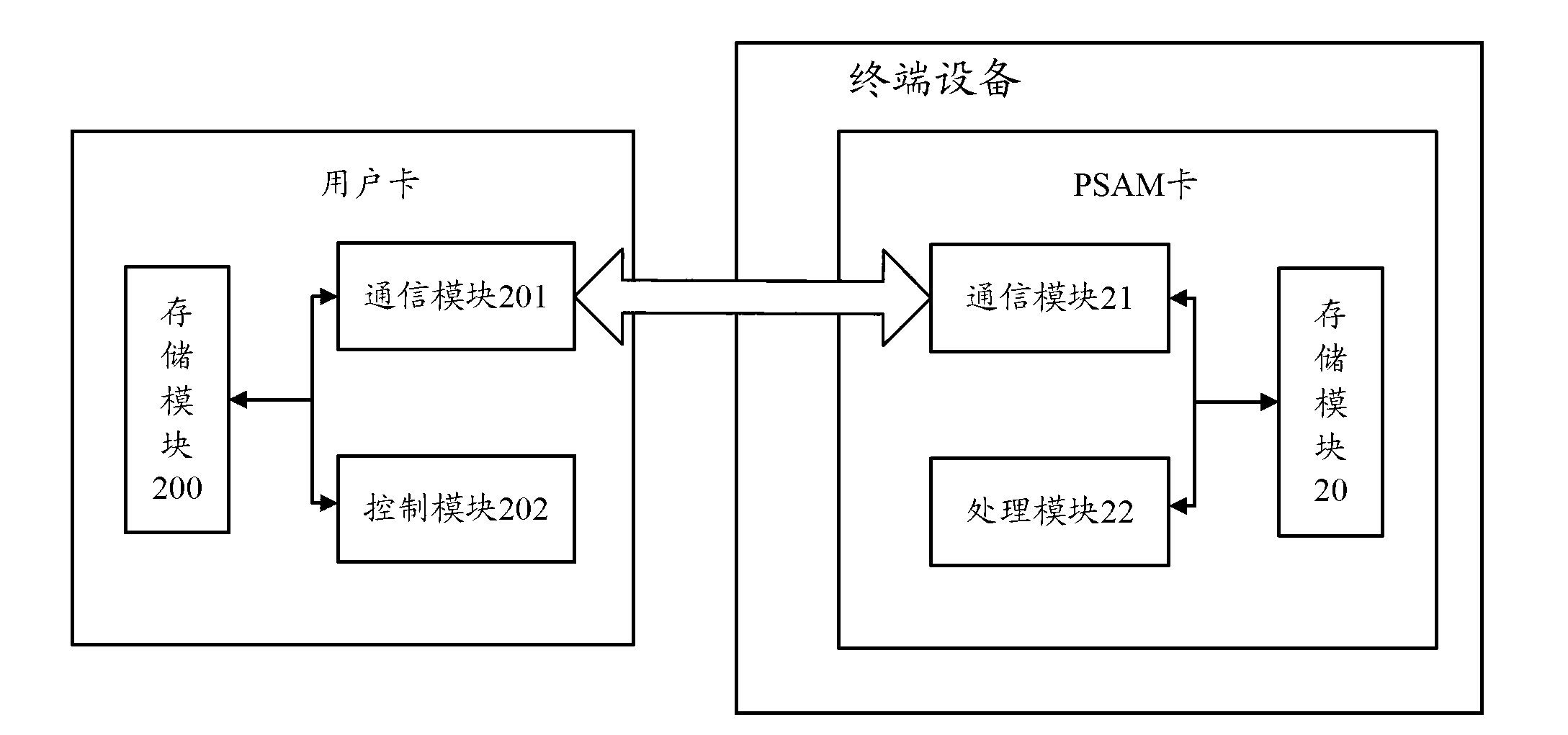
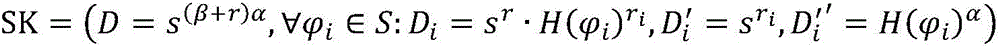Patents
Literature
84 results about "Secure access module" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
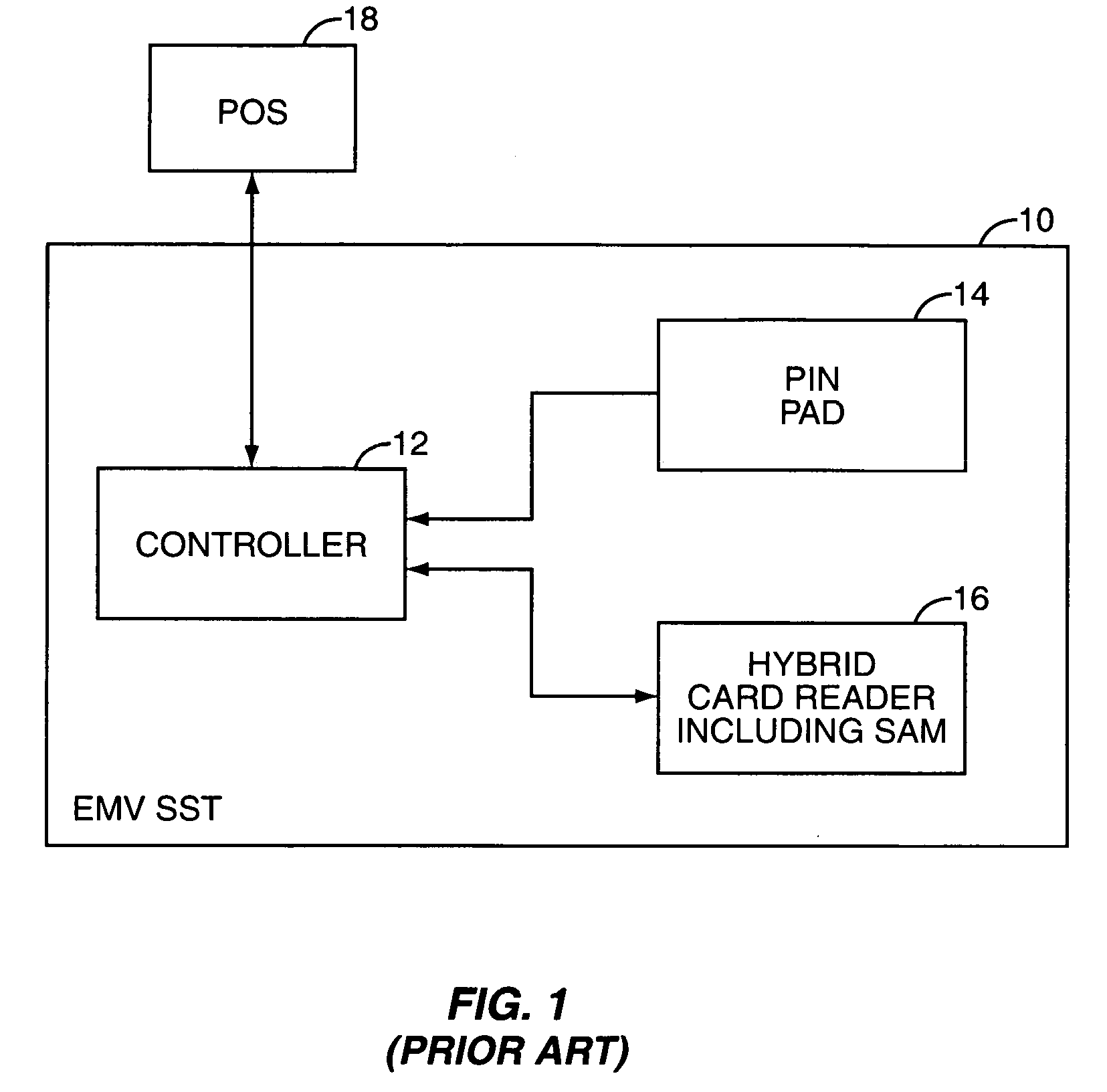
A Secure Access Module (or Secure Application Module) is based on SmartCard Integrated circuits and is used to enhance the security and cryptography performance in devices, commonly in devices needing to perform secure transactions, such as payment terminals. It can be used for cryptographic computation and secure authentication against smart cards or contactless EMV cards.
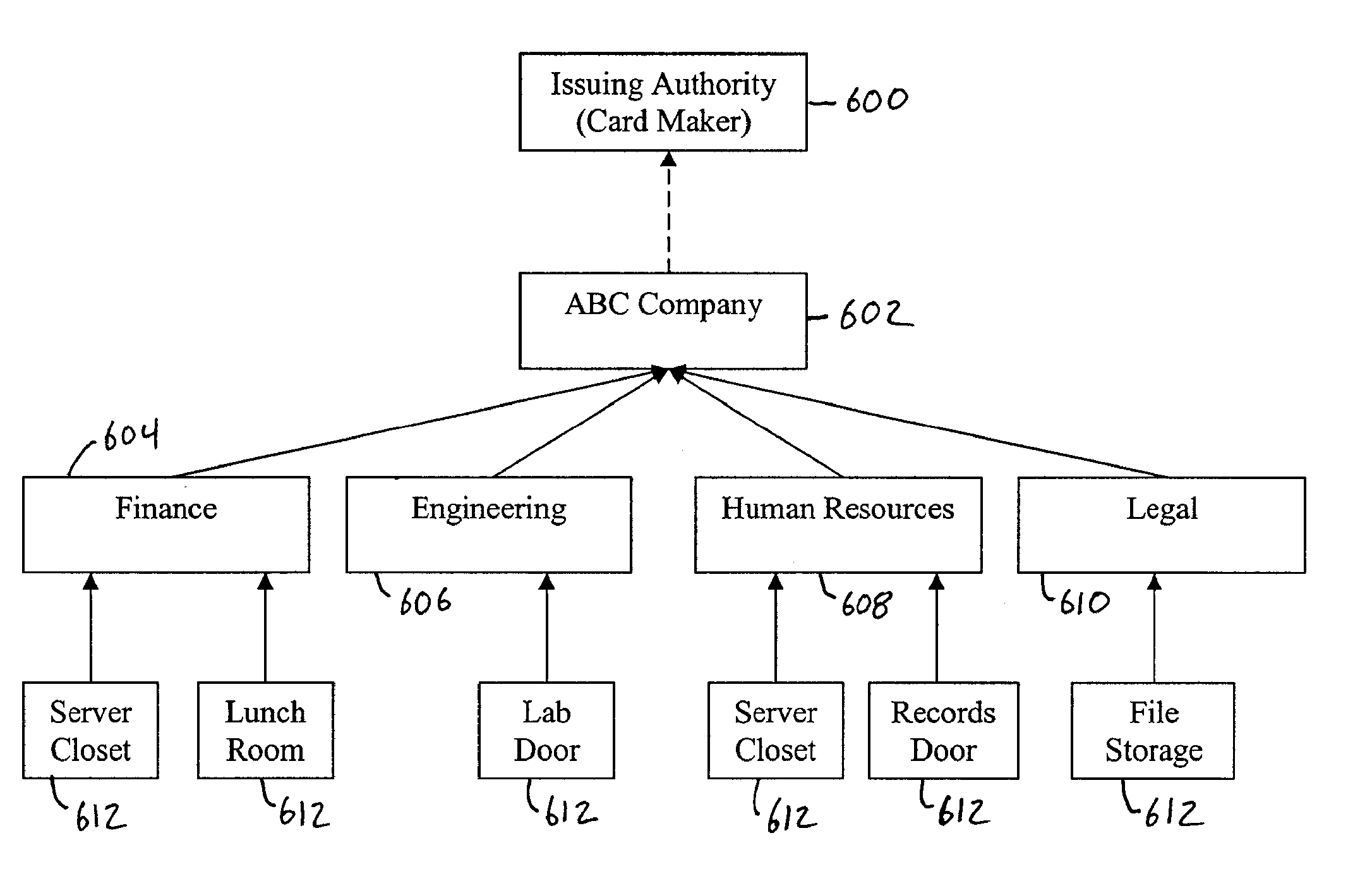
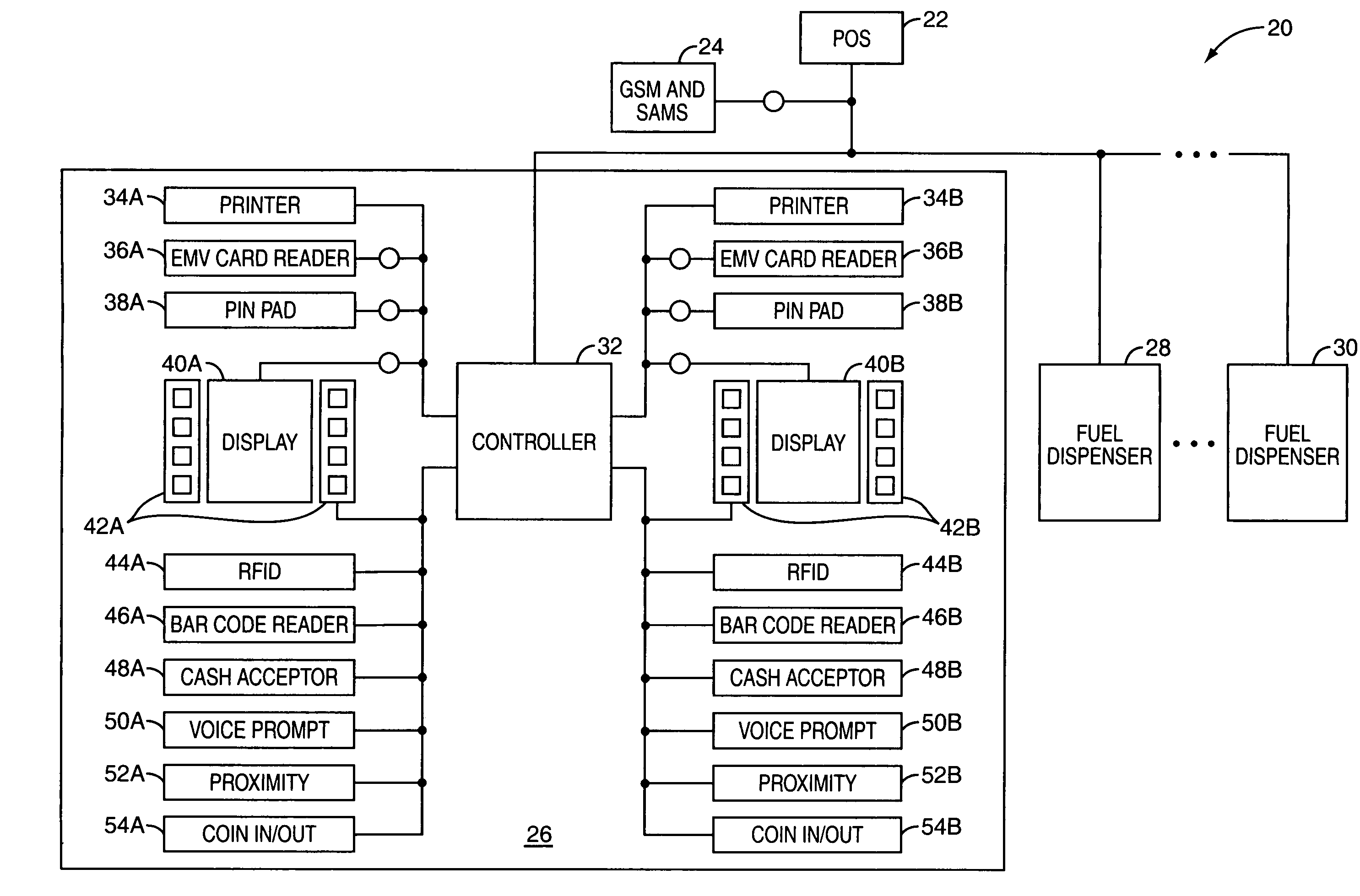
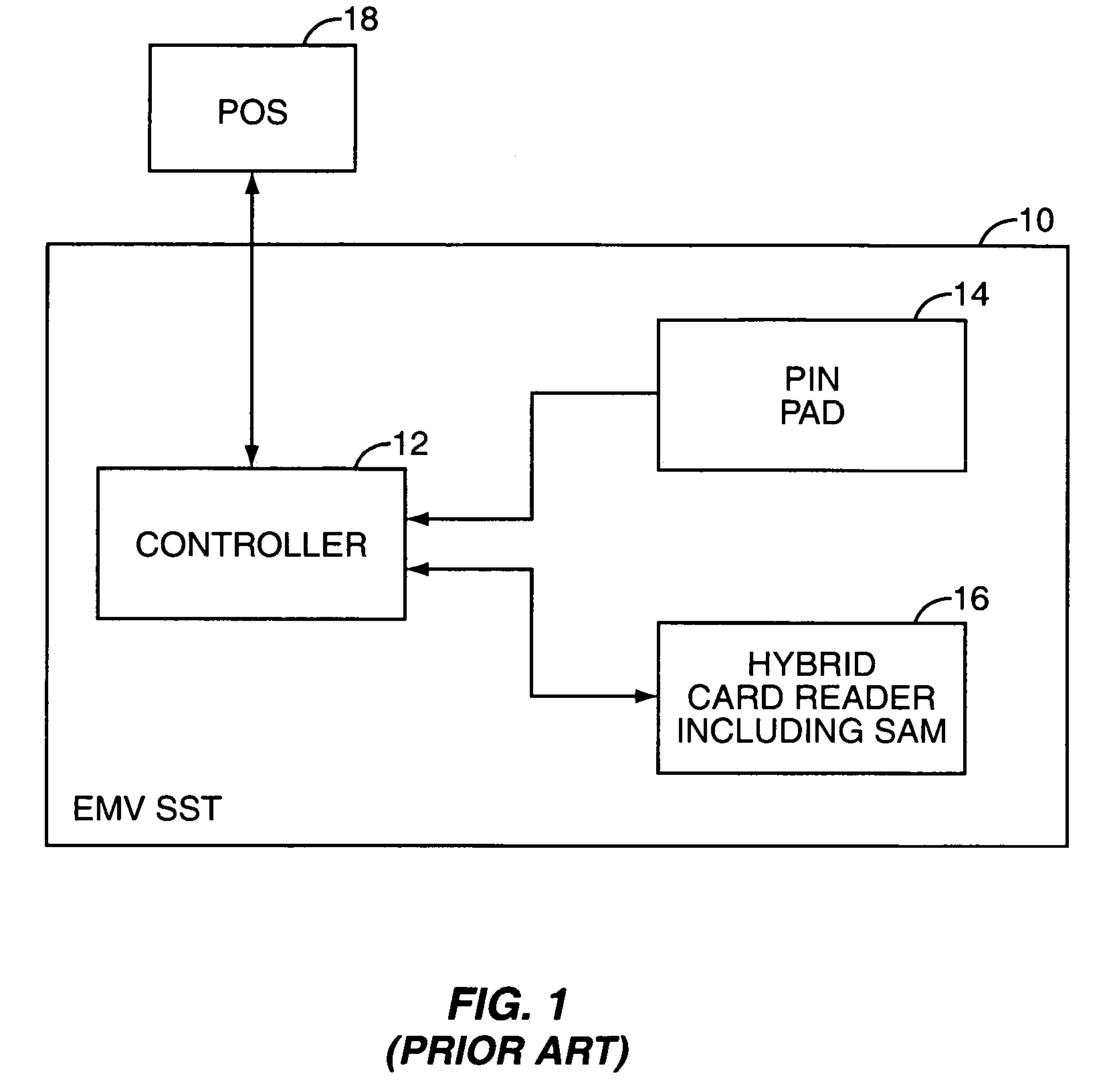
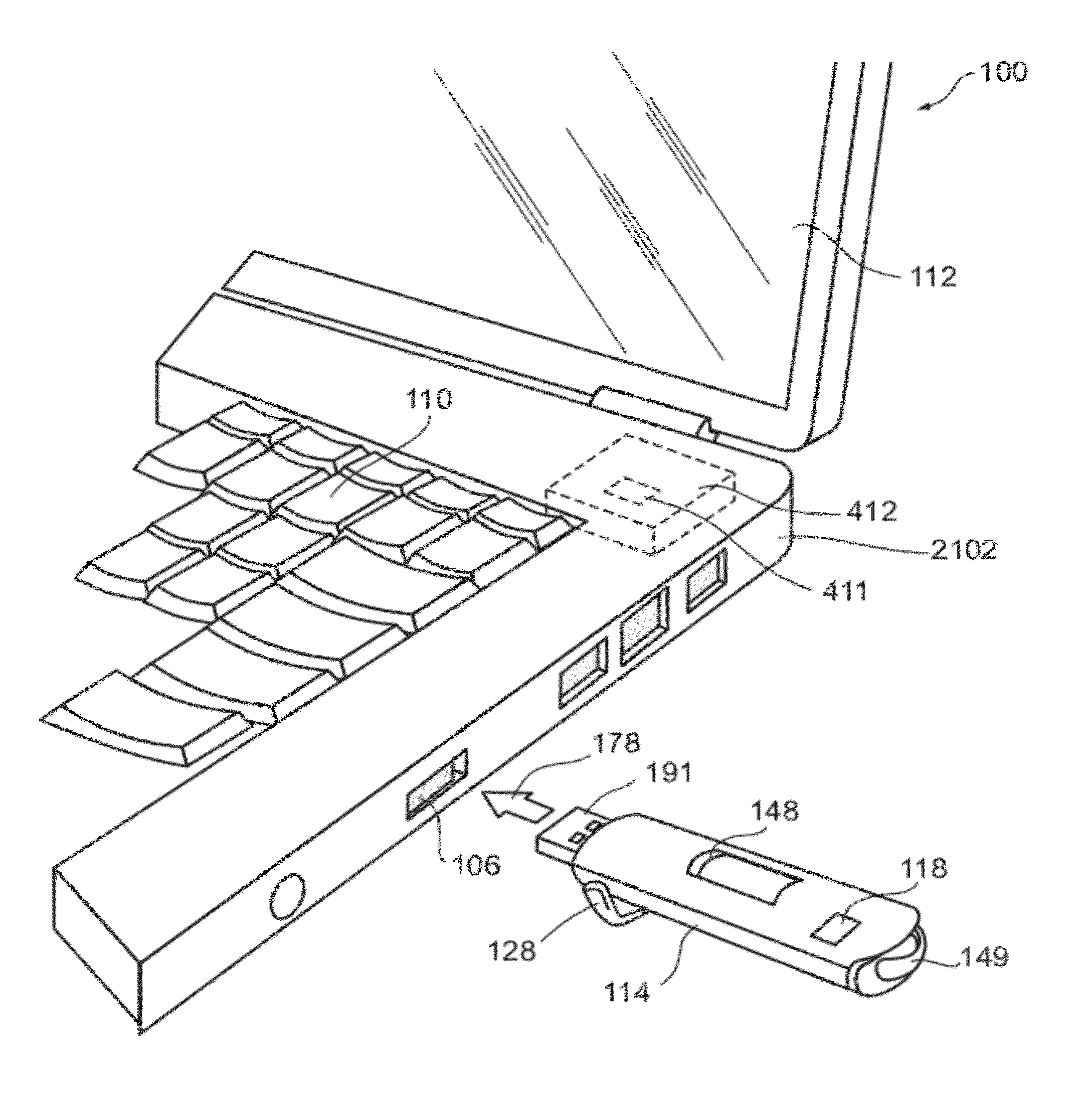
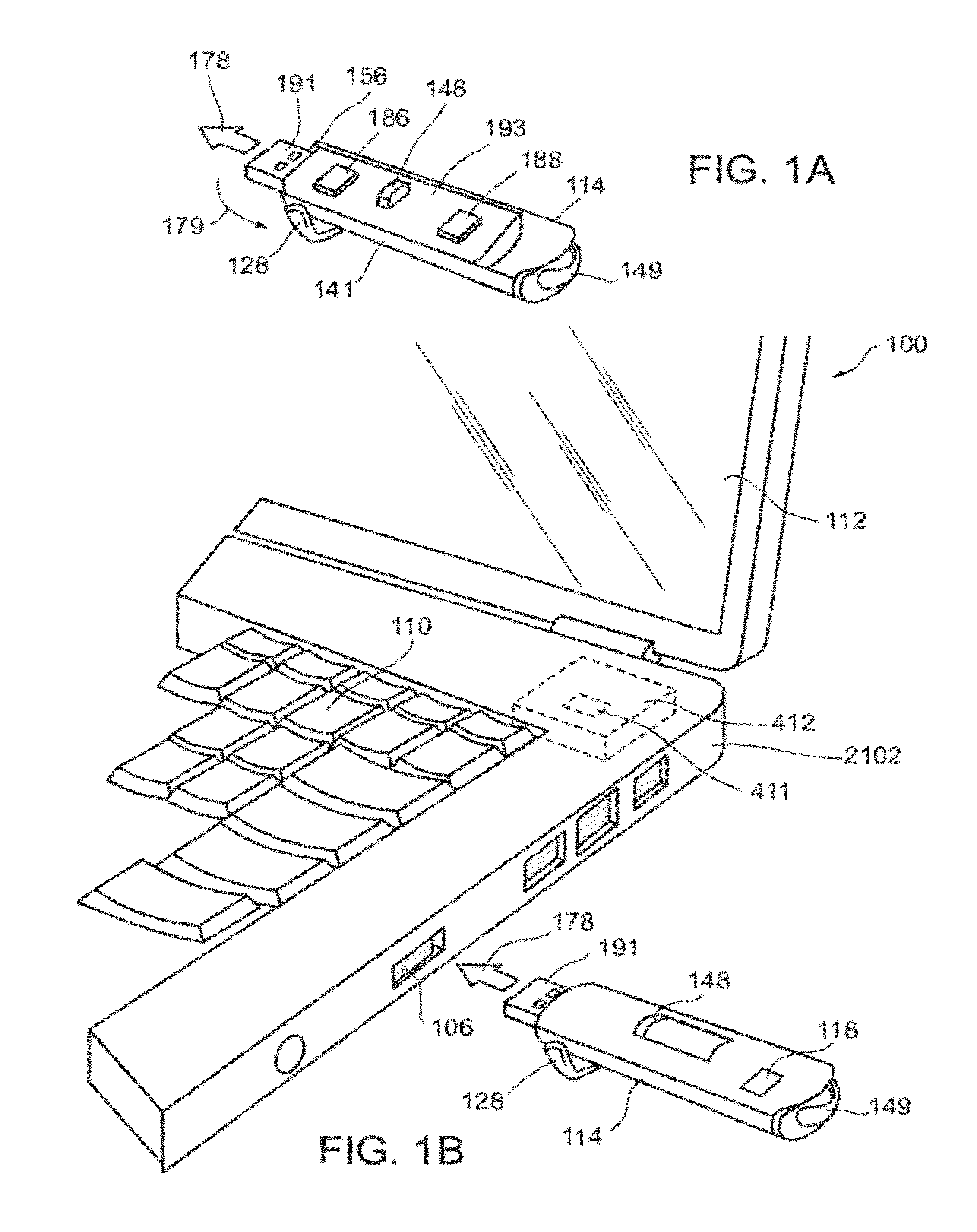
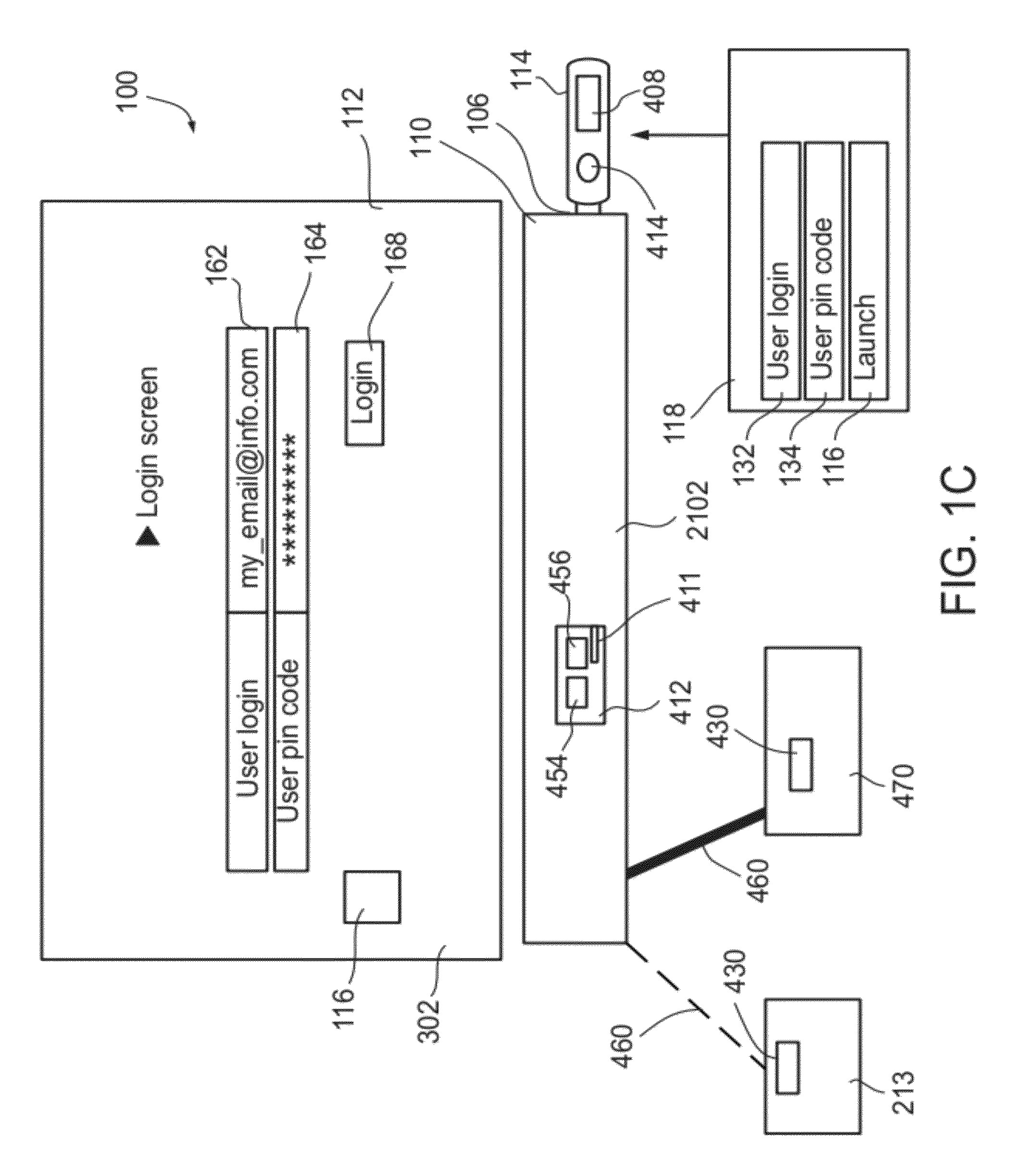
Local zone security architecture for retail environments
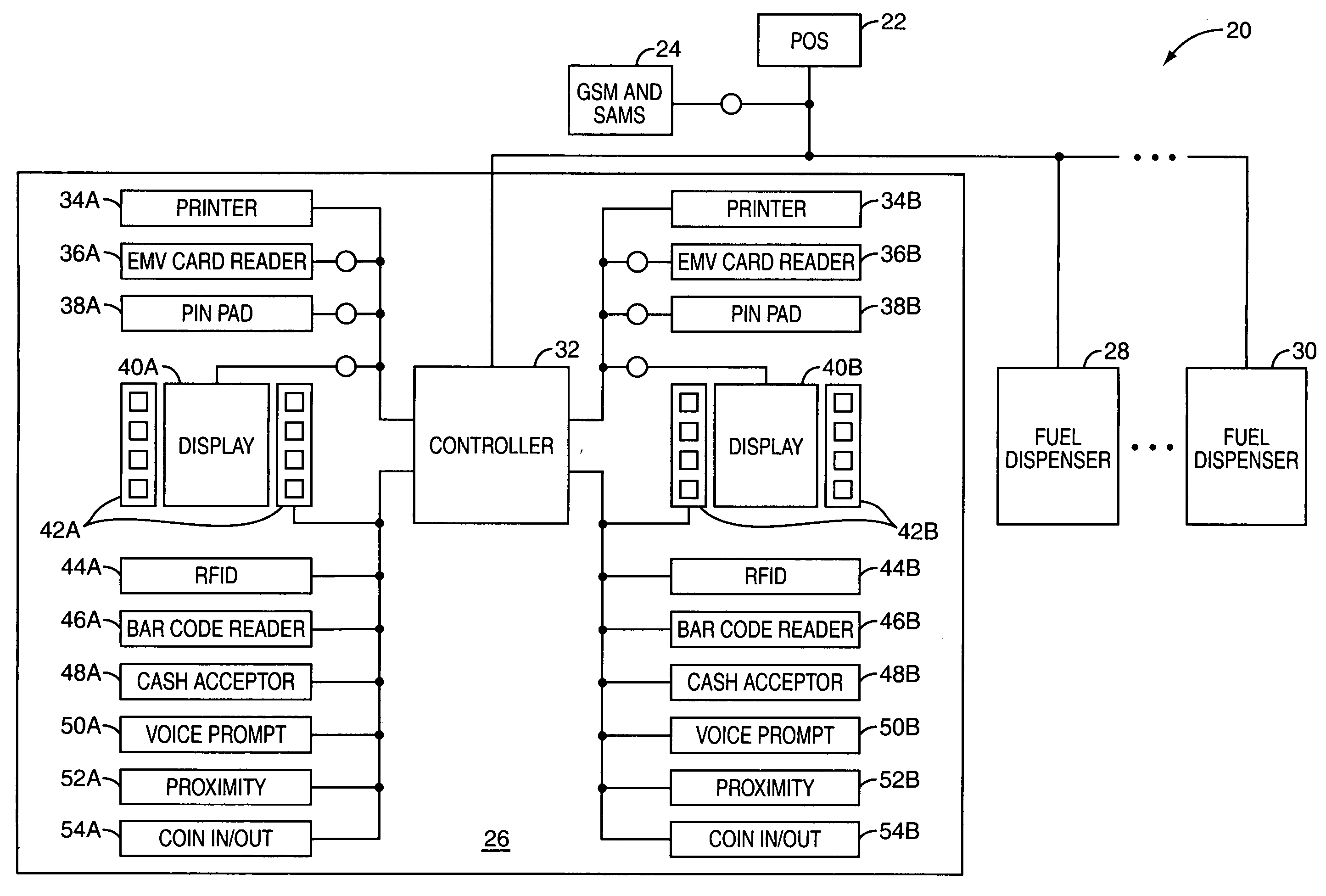
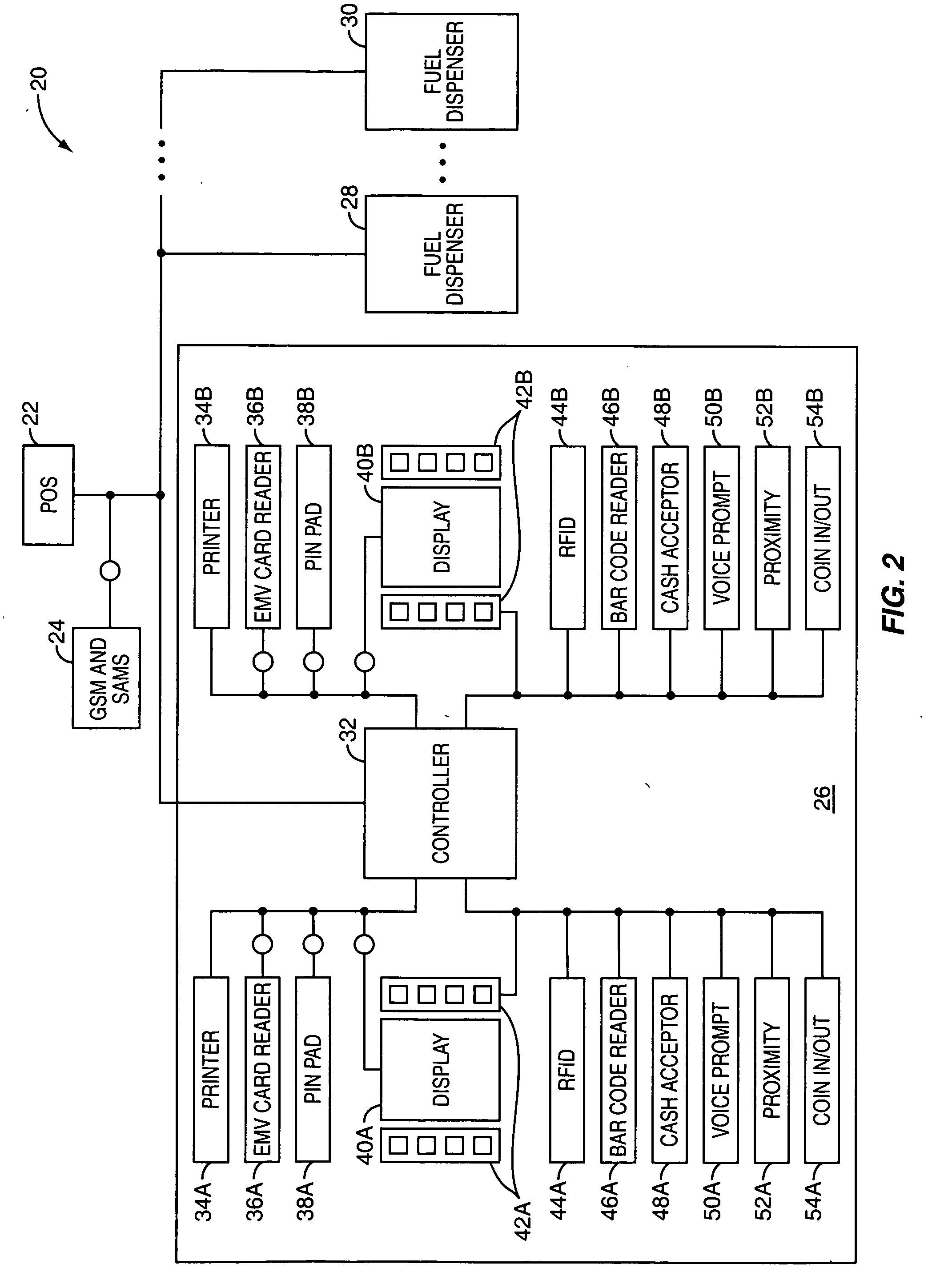
InactiveUS20050211766A1User identity/authority verificationPayment architecturePersonal identification numberOnline and offline
A security architecture for a retail environment providing both on-line and off-line personal identification number (PIN) validation for a smart card transaction using a reduced number of secure access modules (SAMs). In one embodiment, the retail environment includes and security module and numerous fuel dispensers each including a controller and one or more PINpads and card readers. The security module includes one or more SAMs for off-line PIN validation. Each of the PINpads communicates with the security module, and the security module performs either on-line or off-line PIN validation for every PINpad in the retail environment. Accordingly, the security module uses one set of SAMs for off-line validation for every PINpad in the retail environment.
Owner:GILBARCO
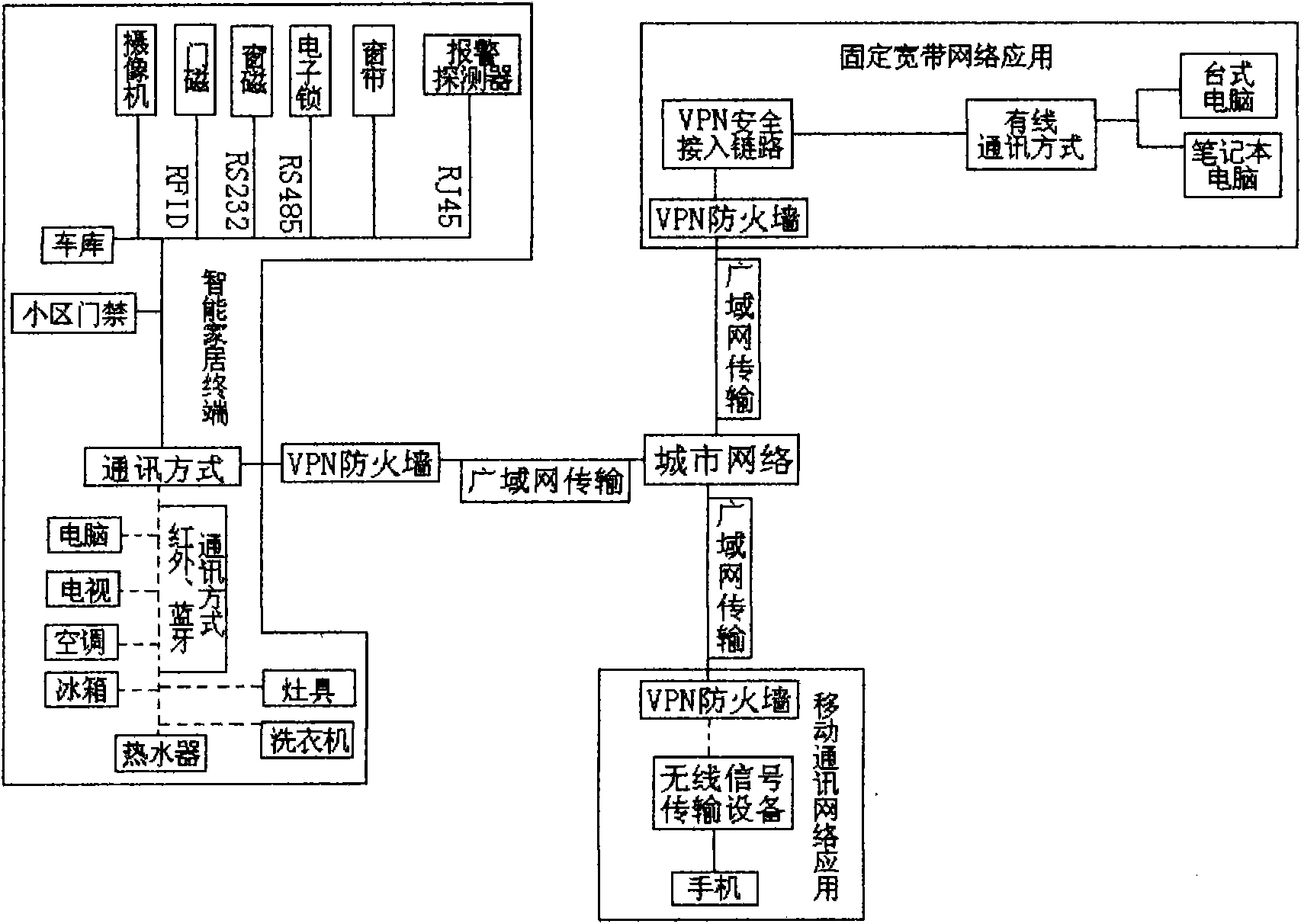
Intelligent household information system of internet of things
InactiveCN101848237ACompact designInnovative designTransmission systemsNetwork topologiesIntelligent designTime delays
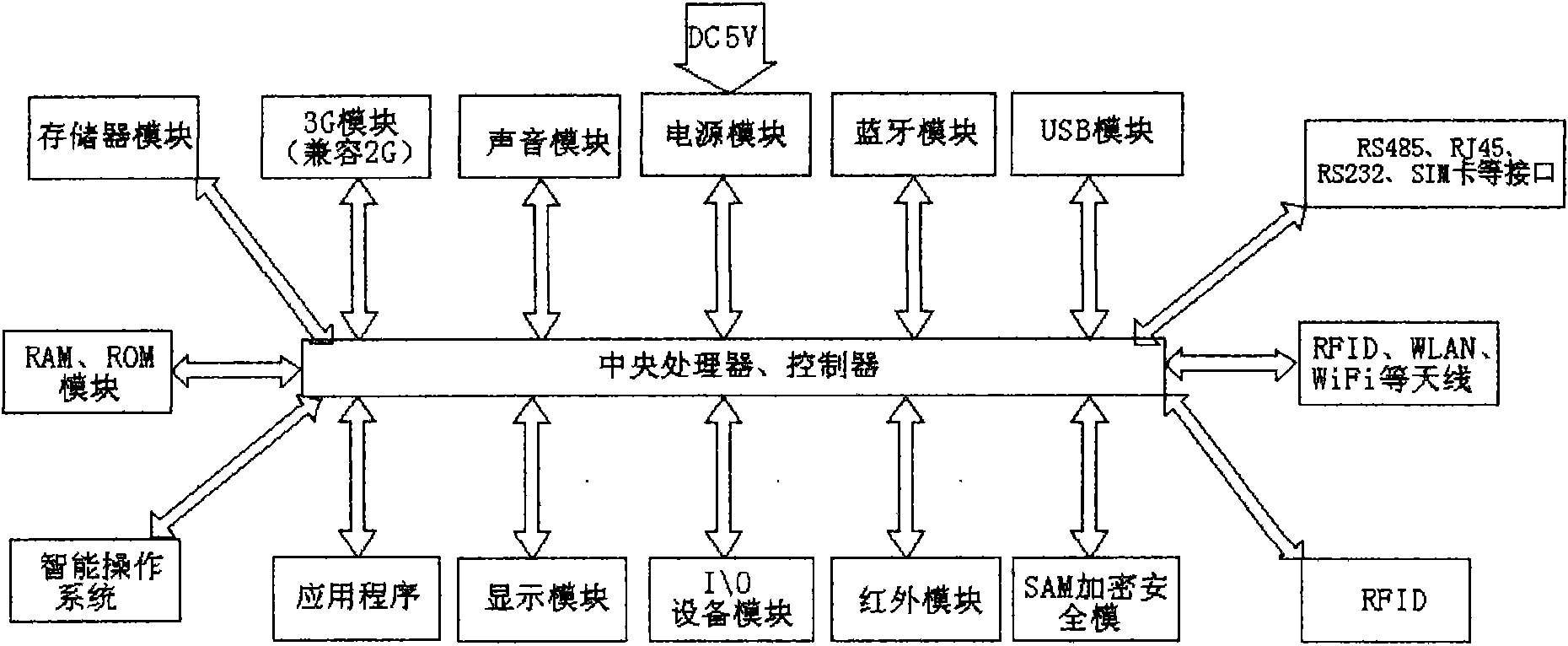
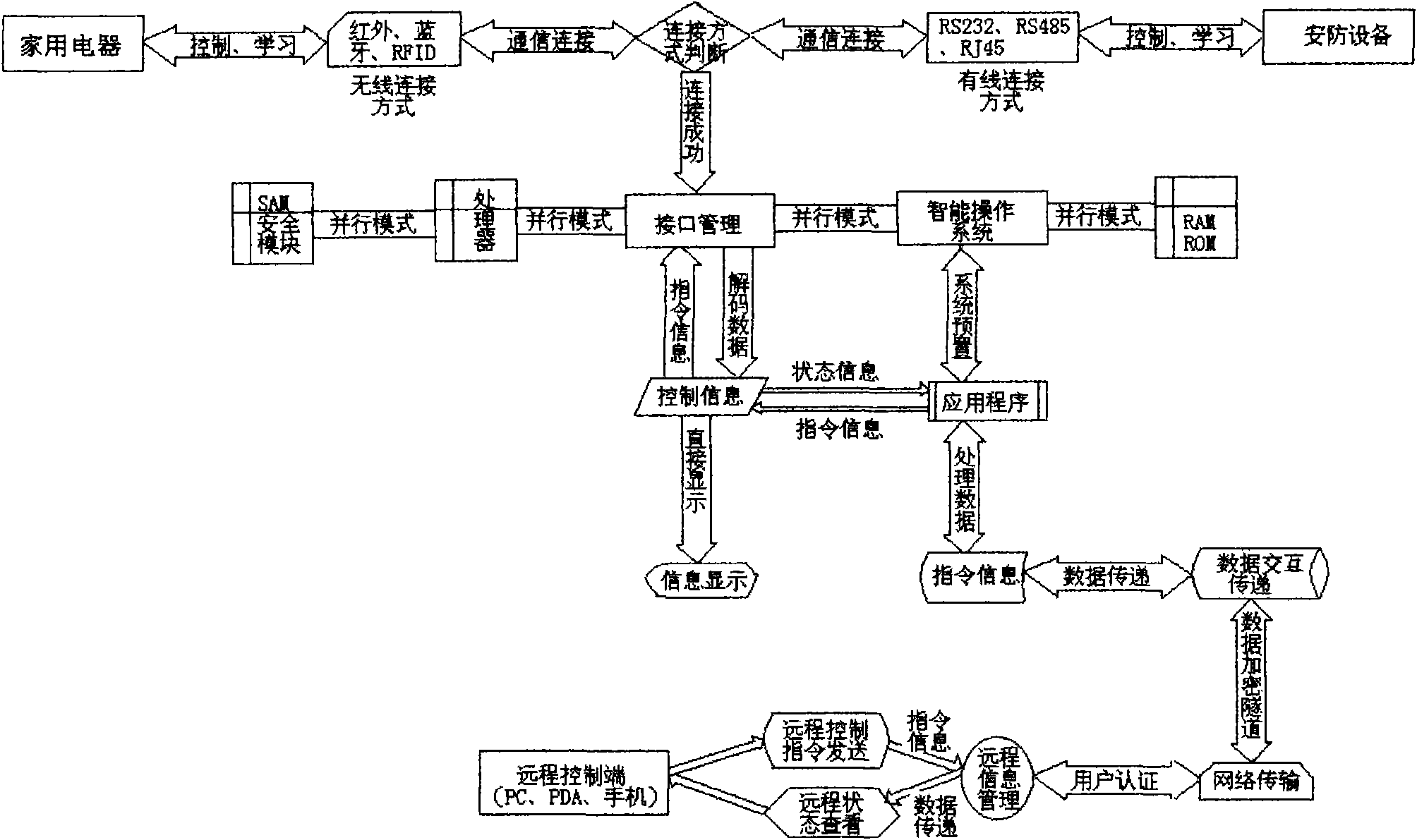
The invention discloses an intelligent household information system of an internet of things, which comprises a terminal device system, a secure transmission system, an information management system and an application system; the terminal device system consists of a hardware sub-platform, a system and software sub-platform, an internet of things sub-platform, a 3G sub-platform and an input and output sub-platform, and the system adopts delicate intelligent design, comprises an industrial automation technology, an intelligent technology and a network communication technology and realizes the fusion of two nets; and the sub-platform of the internet of things consists of infrared, Bluetooth, RFID, RS232, RS485, RJ45, USB, DB9, a DB25 common serial interface, a parallel interface, other interfaces and an SAM secure access module. The system does not need message sending or phone activation, realizes complete combination of security defense and household management, overcomes the problems of communication time delay, image effects, unitary instructions and functional defects, has low purchase, maintenance and working cost and truly realizes intelligent active household management.
Owner:BEIJING BOYA YINGJIE TECH
Entrance guard controlling method and system based on bidirectional authentication
InactiveCN102800141AEnsure safetySolving Security Authentication IssuesIndividual entry/exit registersControl systemSecure access module
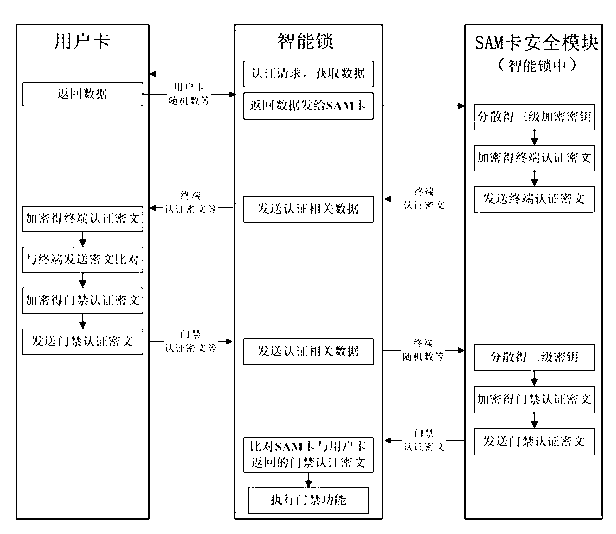
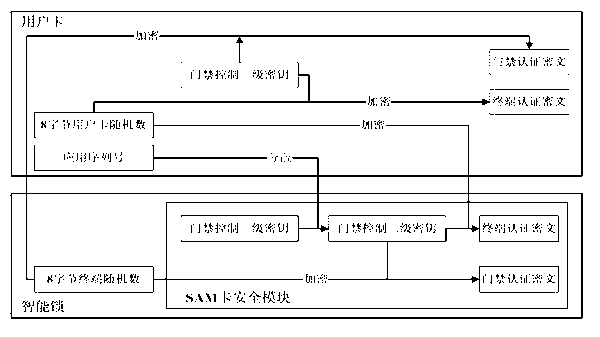
The invention provides an entrance guard controlling method and system based on bidirectional authentication. The core of the entrance guard controlling method and system is that a secure access module (SAM)-card safety module which is connected with an intelligent lock control system signal in an intelligent lock is added, can be embedded into the intelligent lock and be separated from the intelligent lock, and is used for storing a secret key and performing encryption / decryption operation. The SAM-card safety module is taken as a medium to realize the bidirectional authentication between a subscriber card and the intelligent lock, therefore, the safe authentication problem between a locket and the subscriber card in the entrance guard system is solved, the safety of the lockset is improved, the lockset or the subscriber card is prevented from being decrypted and cloned, the safety of data storage and data transmission is guaranteed, and further, the safety of the entrance guard system is guaranteed.
Owner:EASTCOMPEACE TECH +1
Decentralized secure transaction system
InactiveUS20080097924A1Easy to optimizeCo-operative working arrangementsPayment architectureControl flowSecure access module
A secure transaction system in accordance with one exemplary embodiment comprising a terminal; a secure access module coupled to the terminal; and a secure embedded device coupled to the secure access module during a transaction; wherein the business logic for controlling flow of the transaction is contained within the secure access module and the secure embedded device.
Owner:TEC SOLUTIONS LIMITED +1
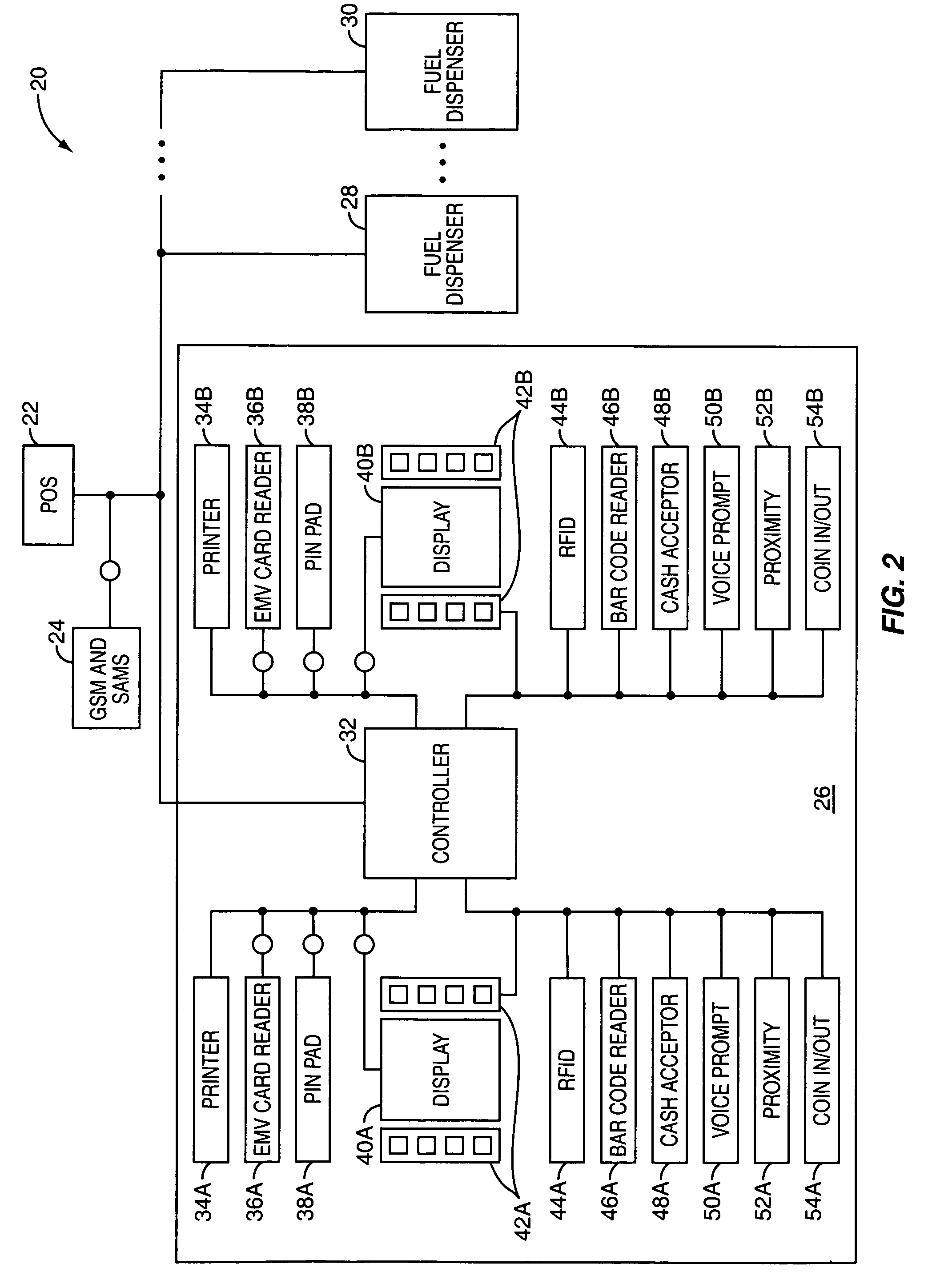
Local zone security architecture for retail environments
InactiveUS7607576B2User identity/authority verificationPayment architecturePersonal identification numberOnline and offline
A security architecture for a retail environment providing both on-line and off-line personal identification number (PIN) validation for a smart card transaction using a reduced number of secure access modules (SAMs). In one embodiment, the retail environment includes and security module and numerous fuel dispensers each including a controller and one or more PINpads and card readers. The security module includes one or more SAMs for off-line PIN validation. Each of the PINpads communicates with the security module, and the security module performs either on-line or off-line PIN validation for every PINpad in the retail environment. Accordingly, the security module uses one set of SAMs for off-line validation for every PINpad in the retail environment.
Owner:GILBARCO
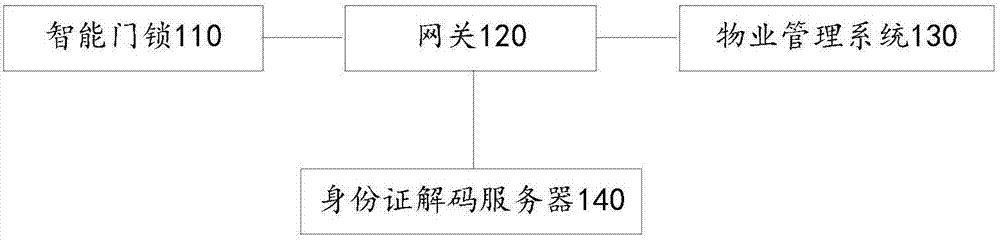
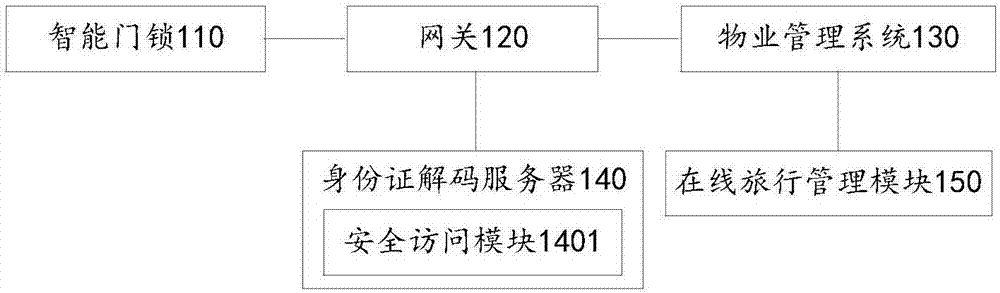
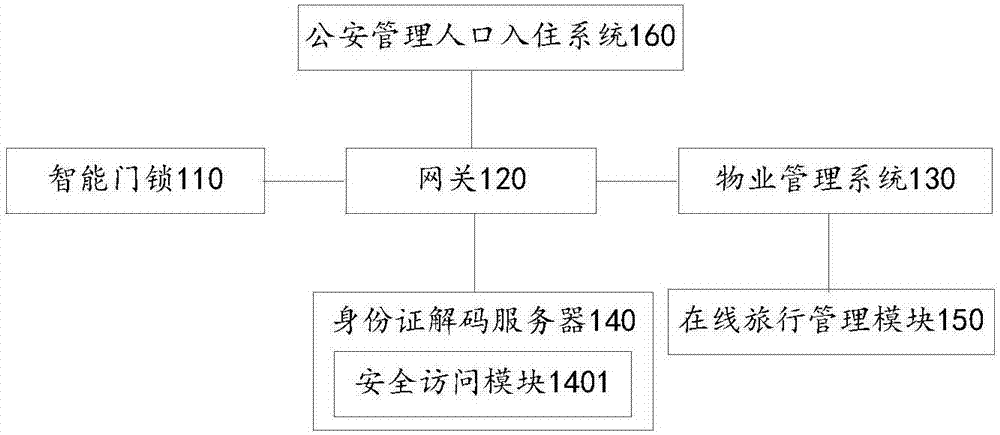
Self-service check-in management system and method, electronic equipment and storage medium
InactiveCN107993310ALow costReduce demandIndividual entry/exit registersTransmissionComputer hardwareSecure access module
The invention provides a self-service check-in management system, belongs to the field of hotel management and solves the problem of high cost of an intelligent door lock in the prior art. The self-service check-in management system comprises an intelligent door lock, a gateway, a PMS (property management system) and an identity card decoding server, wherein the PMS acquires order information andestablishes a binding relation between the identity card number of a user, room number and check-in time according to the order information; the gateway reads encrypted identity card information of acurrently card swiping user according to the intelligent door lock and further acquires the identity card number of the currently card swiping user in a cloud decoding manner; then the identity card number of the currently card swiping user is compared with the identity card number of the user in the binding relation, and the intelligent door lock is controlled to execute an opening action after comparison succeeds. According to the system, the identity card number of the currently card swiping user is acquired through the identity card decoding server, an SAM (secure access module) is not needed to be integrated on the intelligent door lock, and the cost of the intelligent door lock is reduced.
Owner:BEIJING SANKUAI ONLINE TECH CO LTD
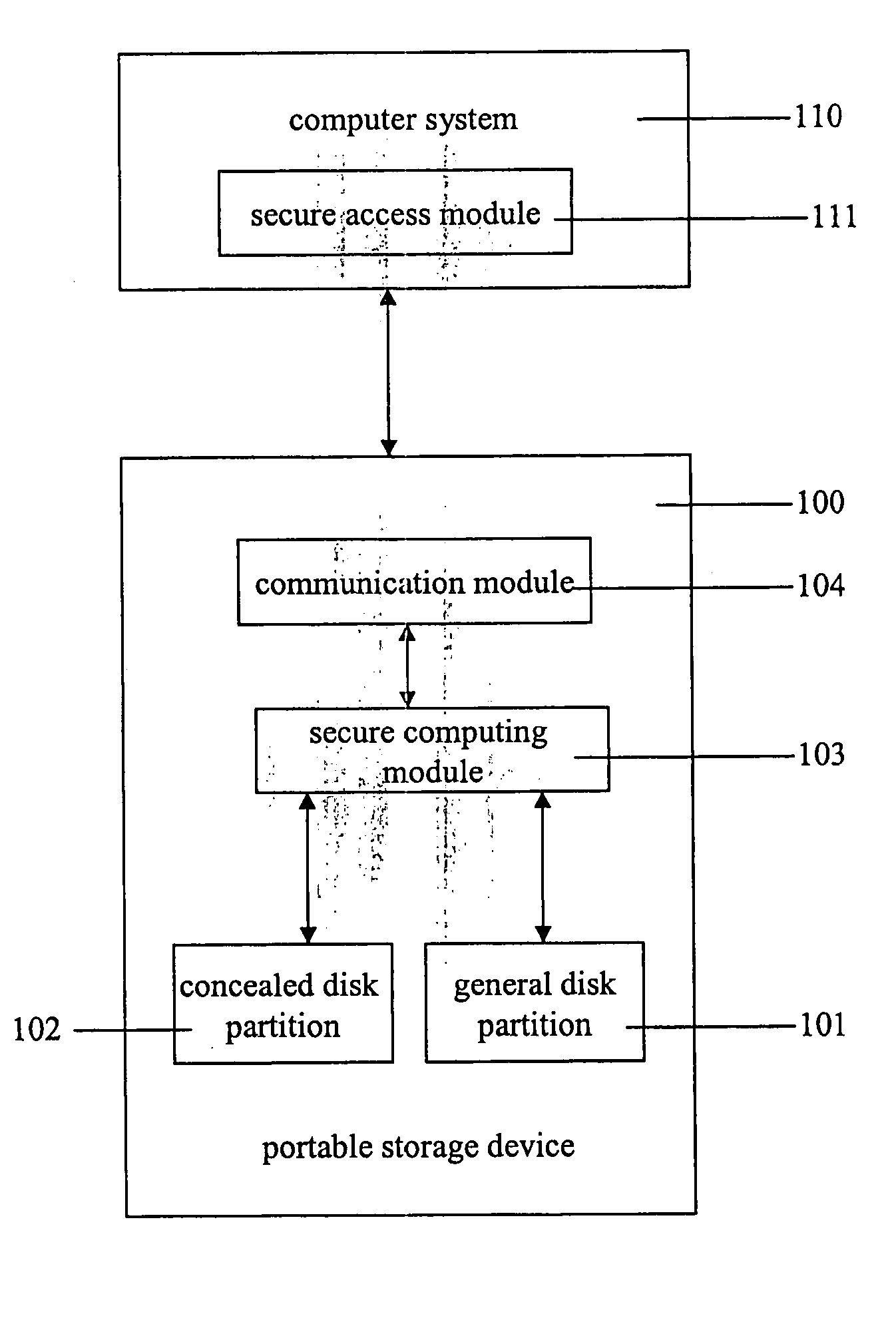
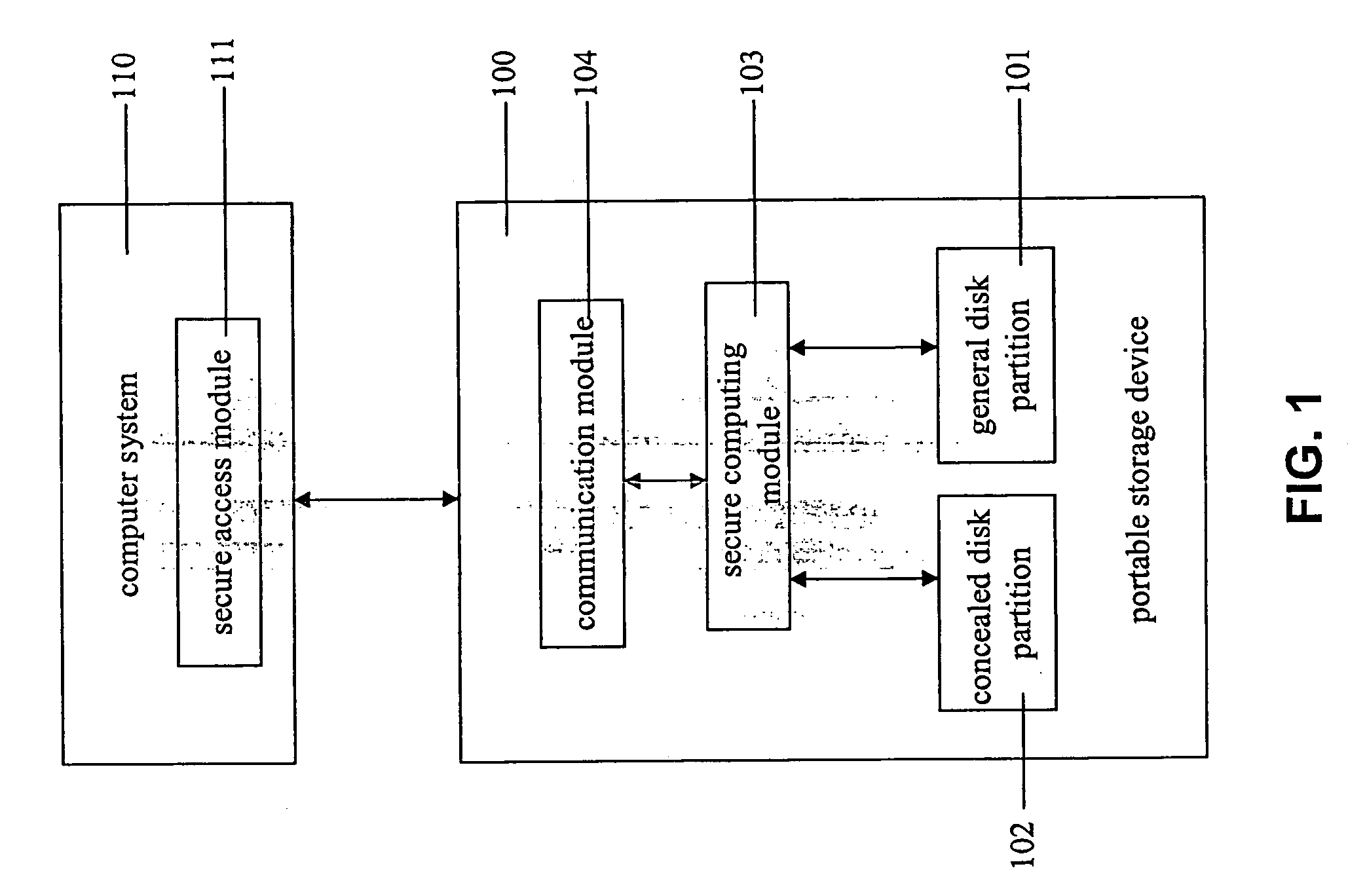
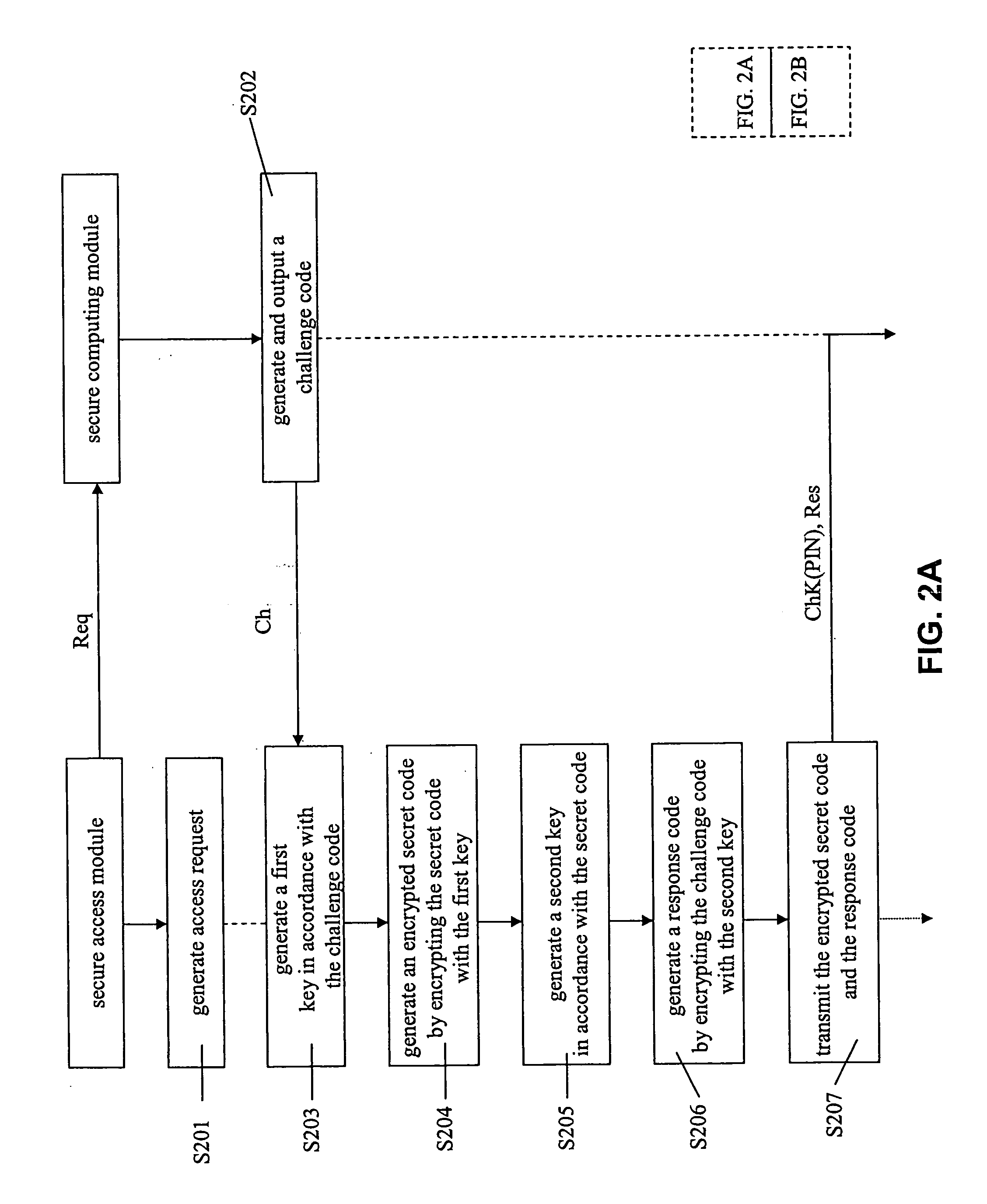
Portable secure information access system, portable storage device and access method for portable secure information
InactiveUS20050033959A1Key distribution for secure communicationDigital data processing detailsAccess methodInformation access
A portable secure information access system is disclosed. The system comprises a portable storage device and a secure access module. The portable storage device comprises a disk partition, in which a secure information is recorded, particularly in a concealed disk partition, and a secure computing module. The secure computing module generates a session key (SK) in accordance with a challenge-response mechanism. The secure access module receives the SK from the secure computing module, encrypting or decrypting the secure information stored in the disk partition in accordance with the SK so as to access the secure information.
Owner:YUEN FOONG PAPER
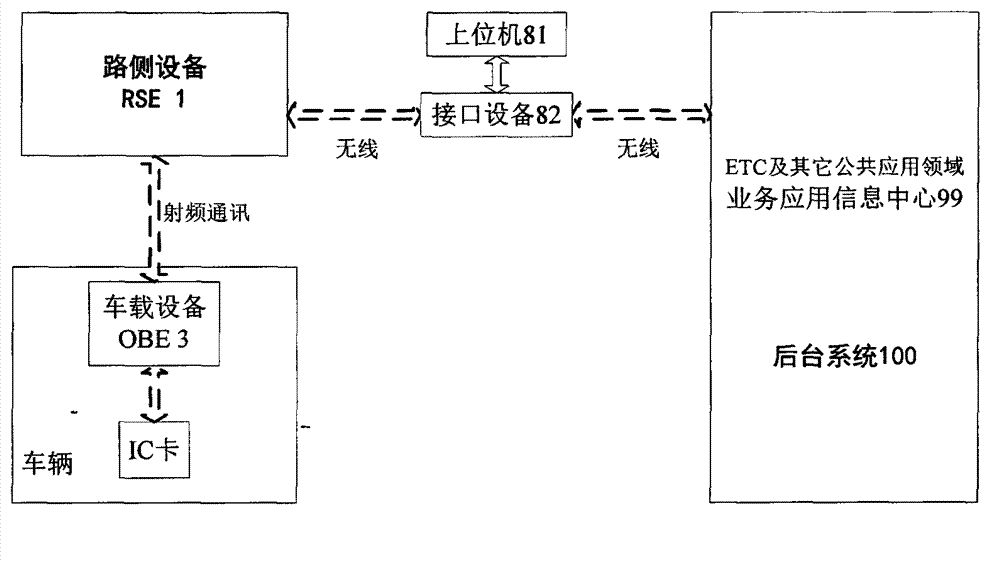
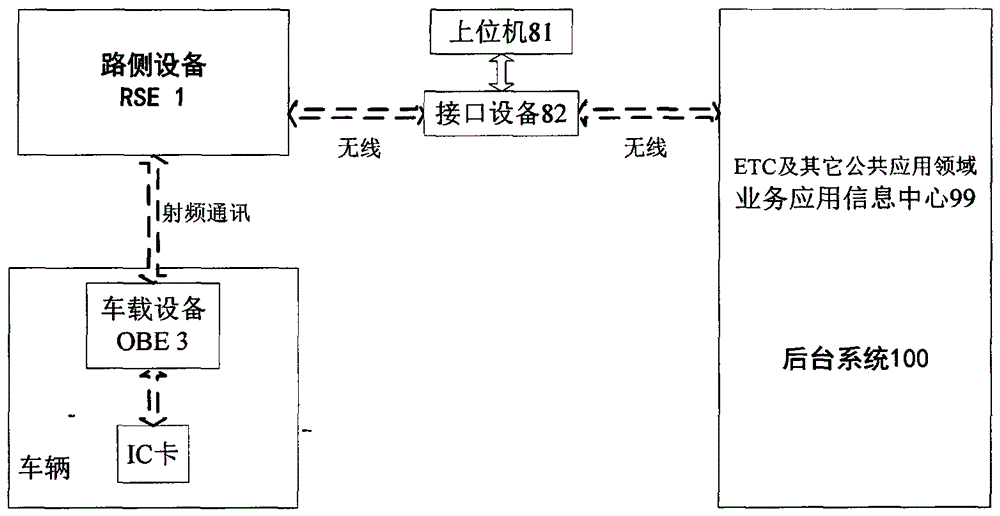
On board unit embedded secure access module (ESAM) for free stream toll collection and use method thereof
InactiveCN103150770AProcessing speedImprove work performanceTicket-issuing apparatusOn boardStructure of Management Information
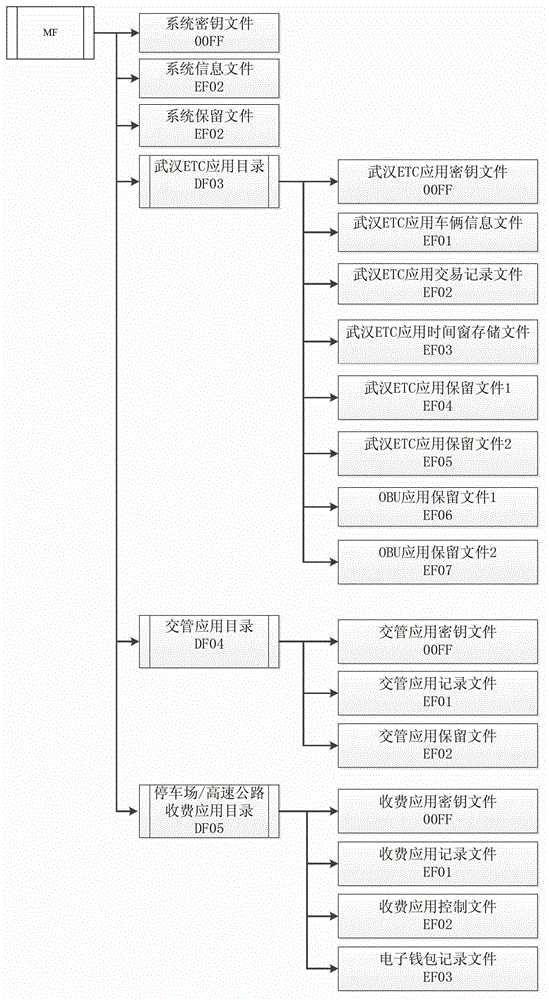
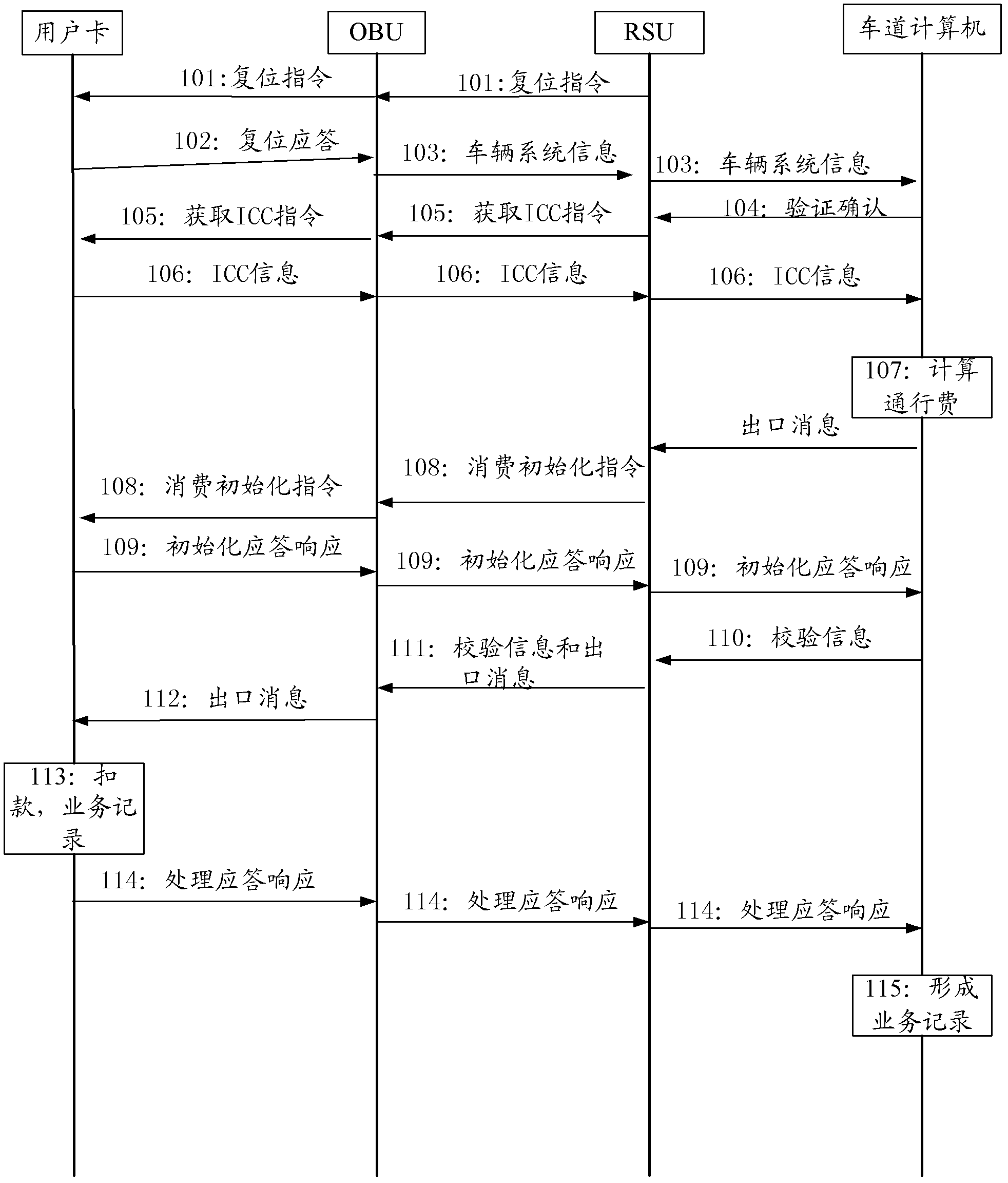
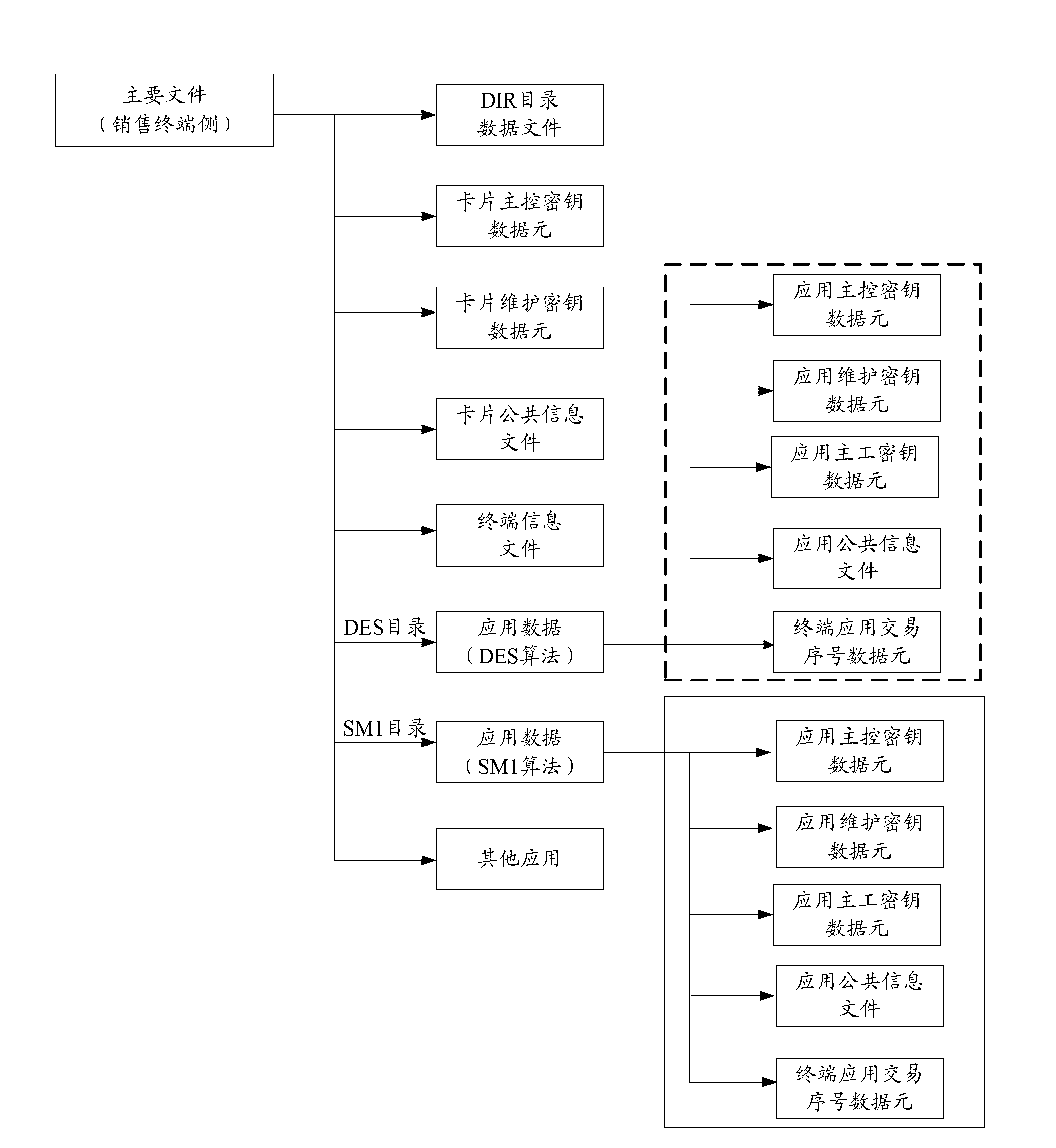
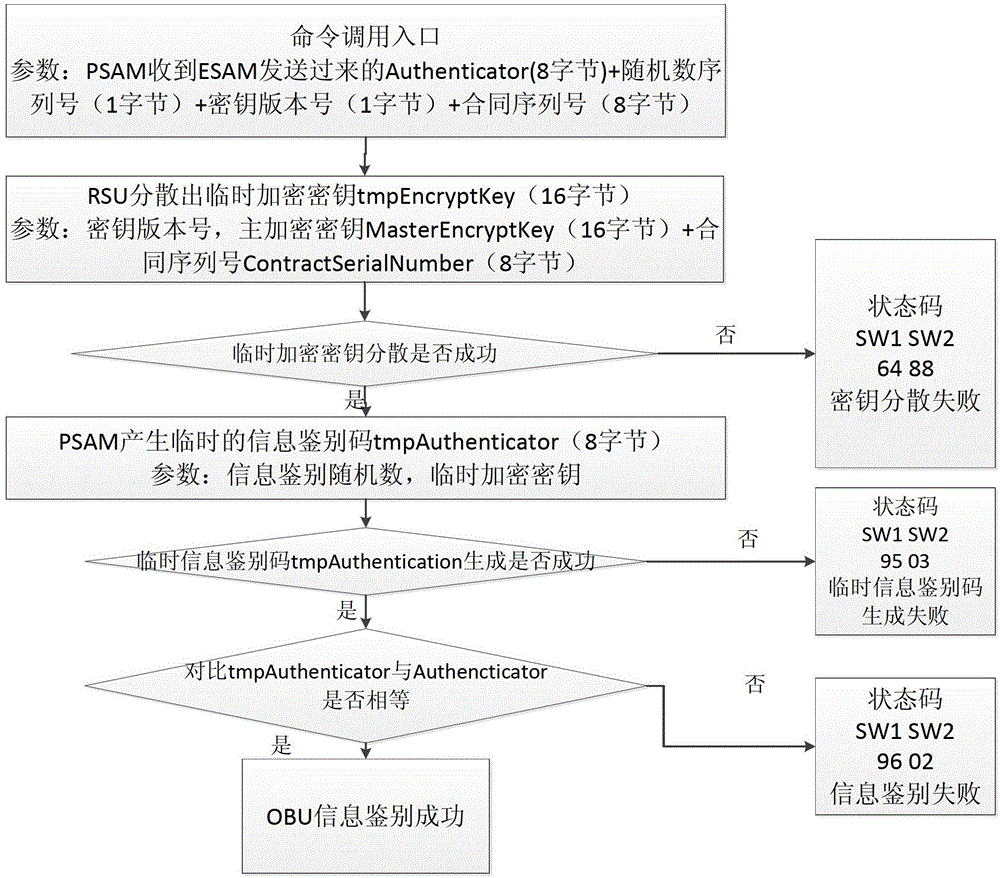
The invention provides an on board unit embedded secure access module (ESAM) for free stream toll collection and a use method of the on board unit ESAM for the free stream toll collection. An arborescence hierarchical structure is adopted by a file structure of the ESAM, a root node of the ESAM is a master control file (MF), and a child node of the ESAM comprises a system key file, a system information file, a system keep file, a free stream electronic toll collection application directory file DF03, and a traffic management application directory file DF04. The use method of the on board unit ESAM for the free stream toll collection comprises a city road bridge free stream electronic toll collection process and a free stream electronic inspection process, wherein each toll collection process comprises a process of a bidirectional safety certificate in concurrent operation which is carried out by a road side unit on an on board unit. The board unit ESAM for the free stream toll collection and the use method of the on board unit ESAM for the free stream toll collection are good in performance, and can satisfy concurrent processing of a plurality of on board units (OBUs) of city road bridge free stream toll collection.
Owner:HUAZHONG UNIV OF SCI & TECH +1
On-vehicle unit, and system and method for processing business
InactiveCN102194260AReduce processing timeIncrease traffic speedTicket-issuing apparatusEmbedded securityComputer module
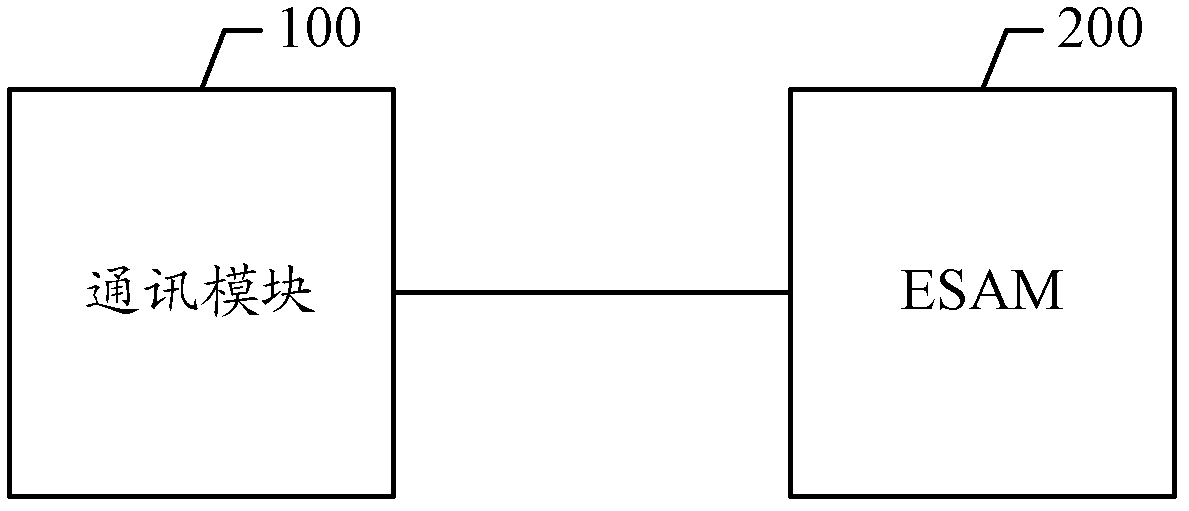
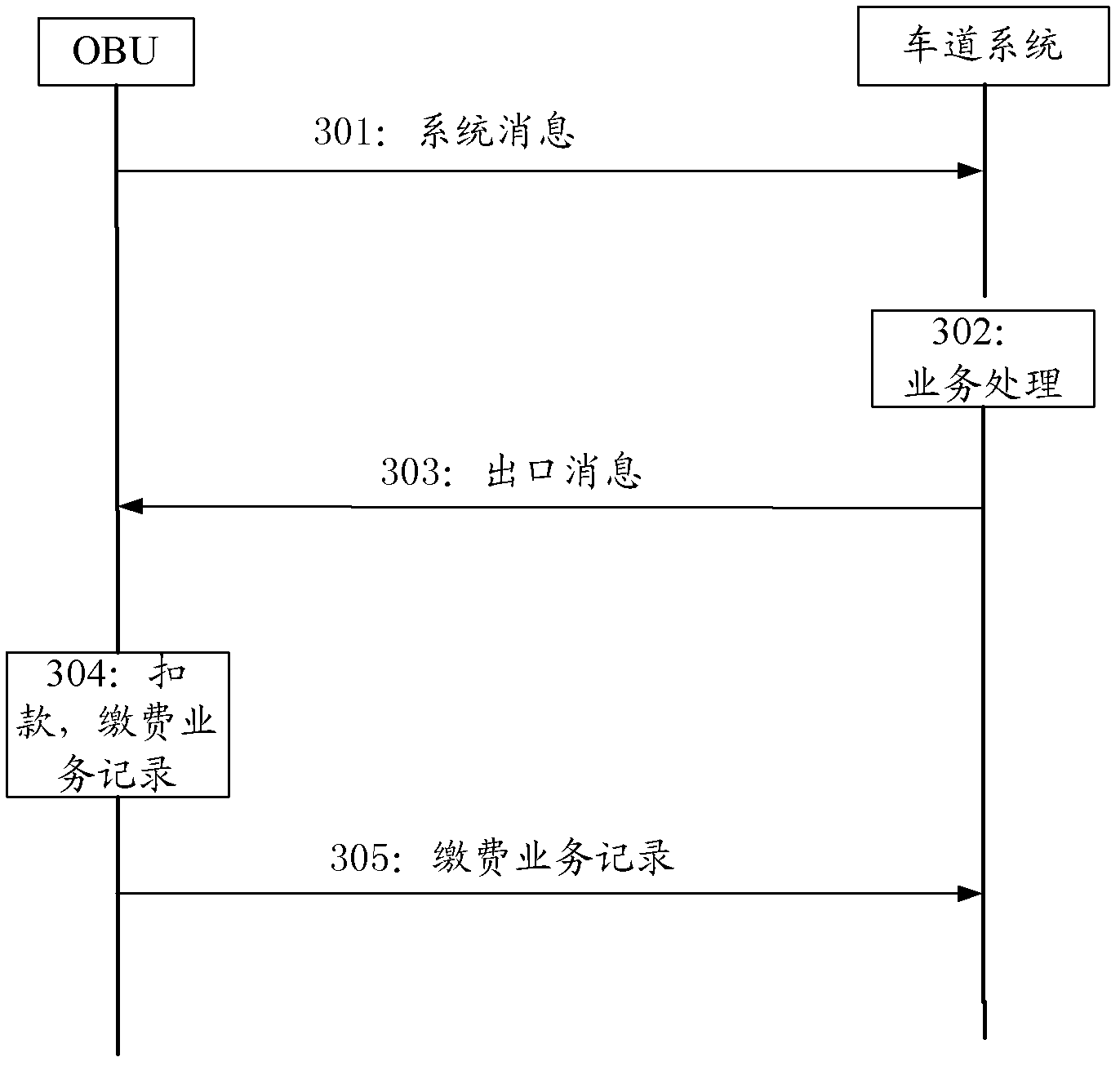
The invention discloses an on-vehicle unit, and a system and method for processing business, which are used for improving traffic rate in an intelligent transport system. The on-vehicle unit comprises a communication module and an embedded secure access module (ESAM); an electronic purse is arranged in the ESAM; the communication module is used for sending system information to a lane system of an electronic toll collection (ETC) system, and sending exit information fed back by the lane system to the ESAM, wherein the exit information comprises a toll formed through business processing according to the system information; and the ESAM is used for deducting corresponding money from the electronic purse according to the toll, and forming a business record of paying.
Owner:BEIJING WATCH DATA SYST
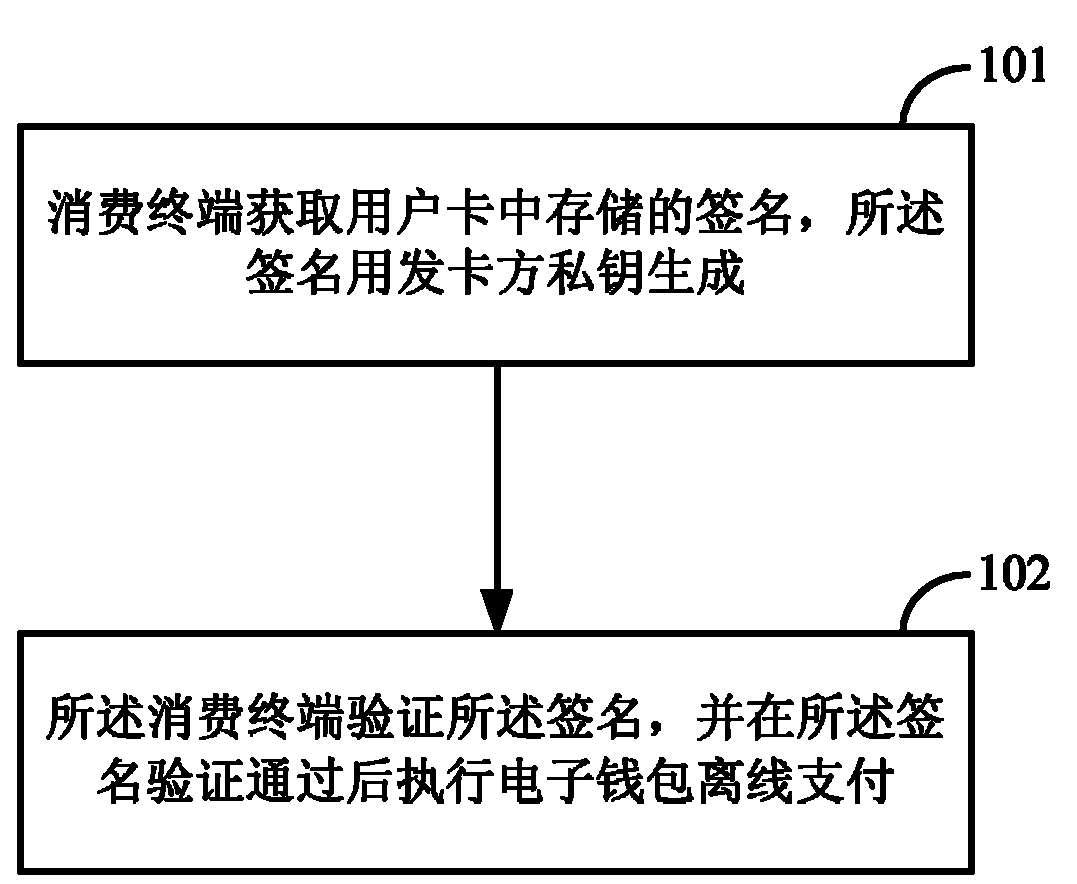
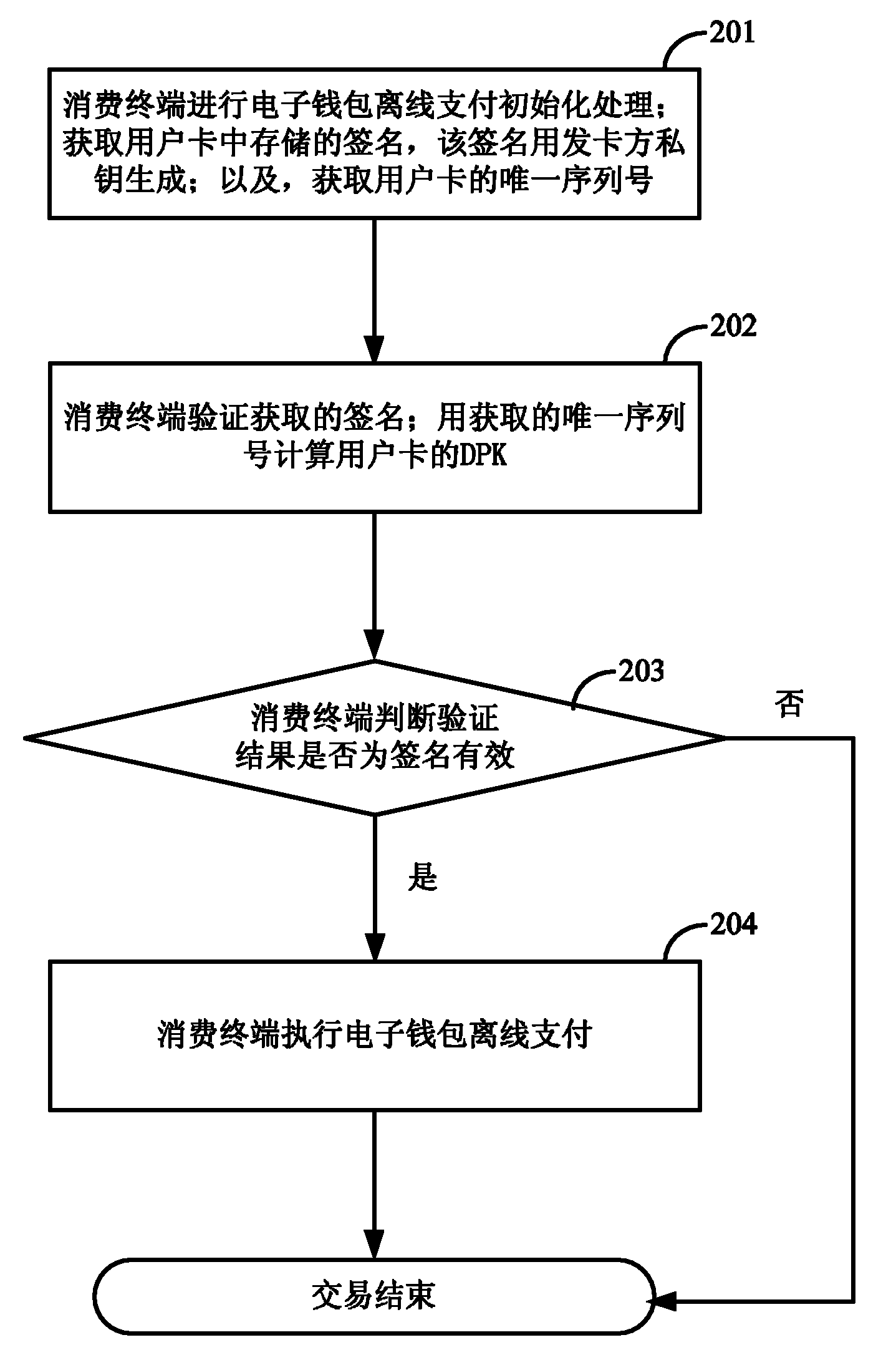
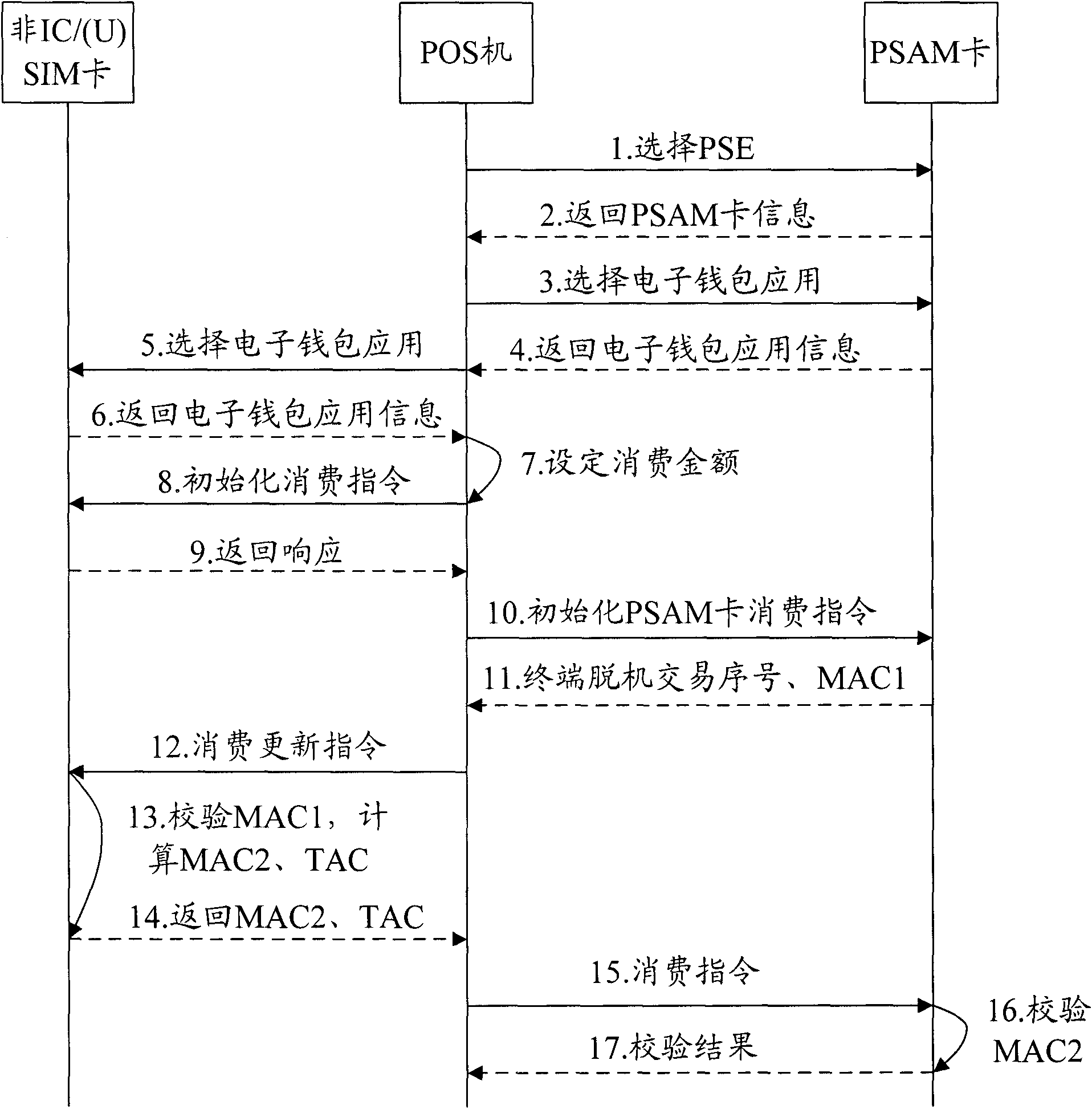
Off-line payment method and consumption terminal for electronic purse
InactiveCN102096967AStop Illegal Bulk CopyingStrengthen the weak linkCash registersCoded identity card or credit card actuationComputer moduleCard holder
The invention discloses an off-line payment method and a consumption terminal for electronic purse. The method comprises the following steps: the consumption terminal obtains a signature stored in a user card, wherein the signature is generated by the private key of a card issuing party; and the consumption terminal verifies the signature and performs off-line payment by the electronic purse after the signature is verified. In the method, the week link that only a terminal security control module PSAM (purchase secure access module) is depended to identify whether the user card is true or false can be enhanced, and the card issuing party indirectly participates in the off-line consumption certification process of the electronic purse, thereby effectively preventing attackers from illegally copying false cards on batch by utilizing the week point of the off-line transaction of the electronic card at present. Meanwhile, the system risk is burdened on the card holder, and attackers have no opportunity if the card holder appropriately keeps the self card.
Owner:GIESECKE & DEVRIENT (CHINA) INFORMATION TECH CO LTD
Method and device for compatible management of encryption algorithm
InactiveCN102710412AGuaranteed work performanceSmooth transitionSecuring communicationComputer hardwareWork performance
The invention relates to a computer electronic account managing technology and discloses a method and a device for compatible management of an encryption algorithm. The method comprises the following steps of: setting AID menus of different encryption algorithms in a PSAM (Purchase Secure Access Module) card and a user card; saving application data needed by an executing payment flow into each AID menu, so that no matter which encryption algorithm is supported by the user card, the PSAM card can be matched and the corresponding encryption algorithm is called to finish the payment flow; the different AID menus can be conveniently utilized and the compatible management of the different encryption algorithms under the same application flow is realized; on the premise that the payment flow is not changed, any other instruction is not added and terminal equipment is not modified, the user card and the PASM card can be guaranteed to be smoothly transited to a standard encryption algorithm formulated by National Password Bureau through a DES (Data Encryption Standard) algorithm; and the working performance of a payment system is guaranteed and the cost is minimized.
Owner:BEIJING WATCH DATA SYST
Method and device for encrypting data in ATA memory device with USB interface
InactiveCN101551784AFast encryption and decryptionImprove securityUnauthorized memory use protectionOperational systemEncryption decryption
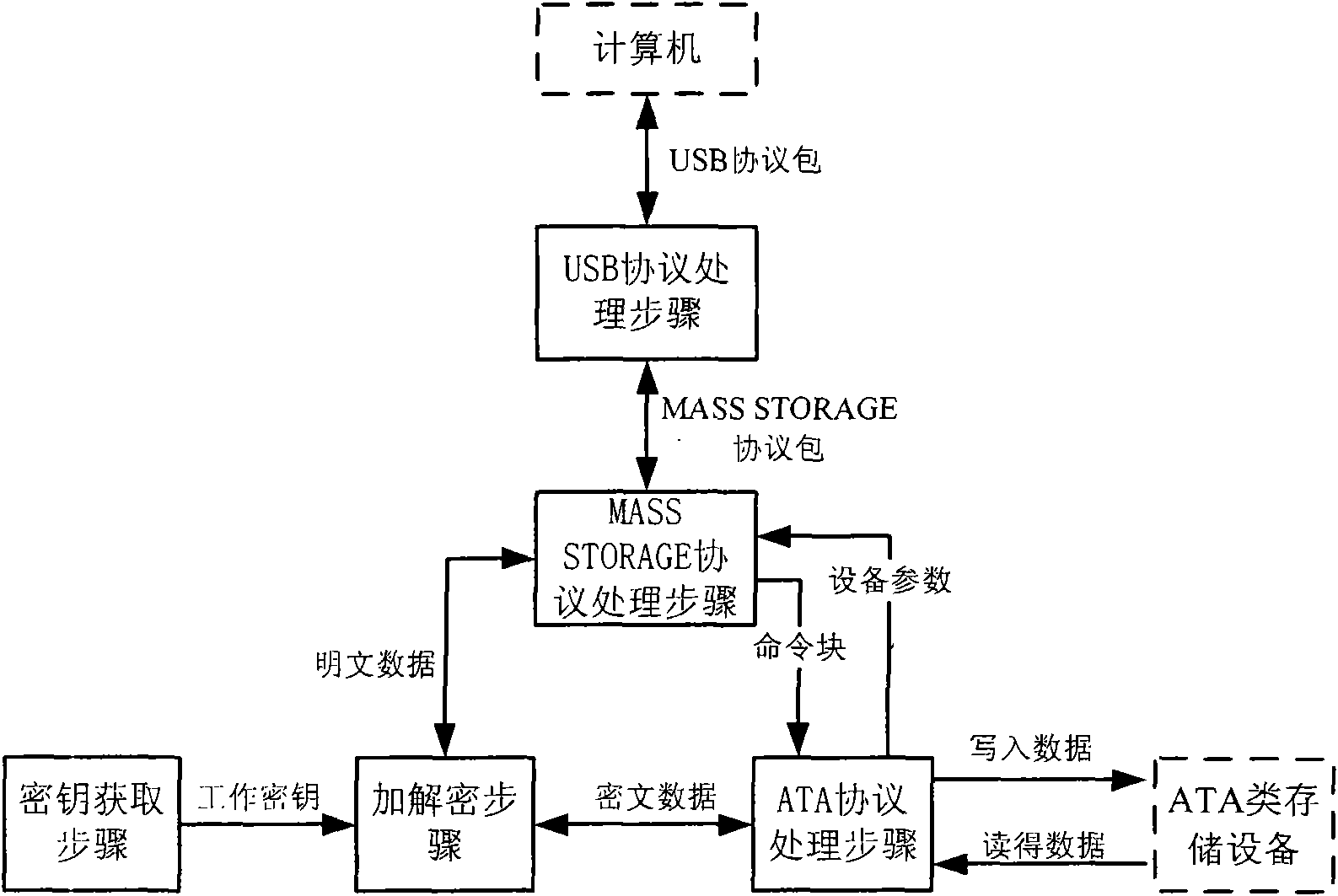
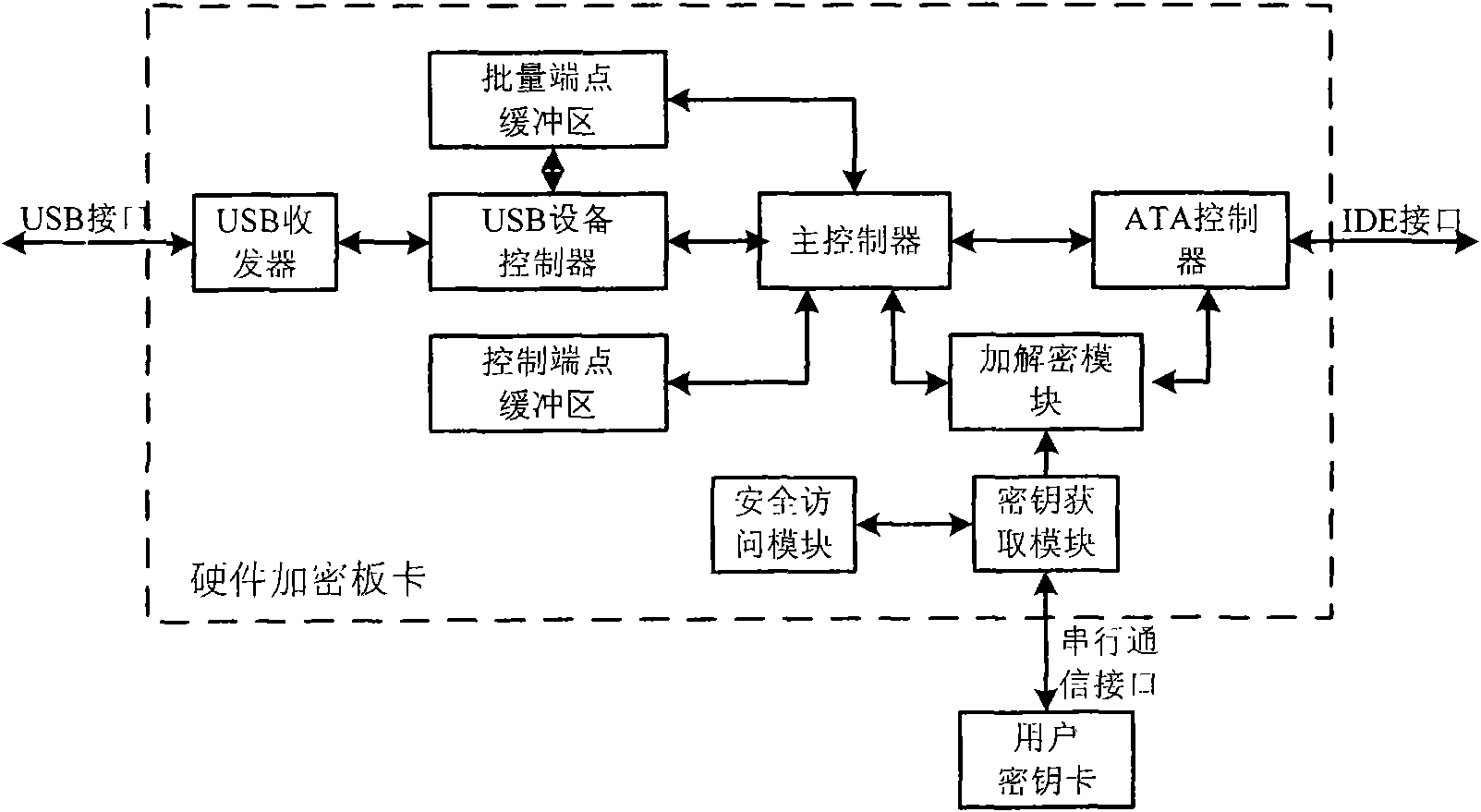
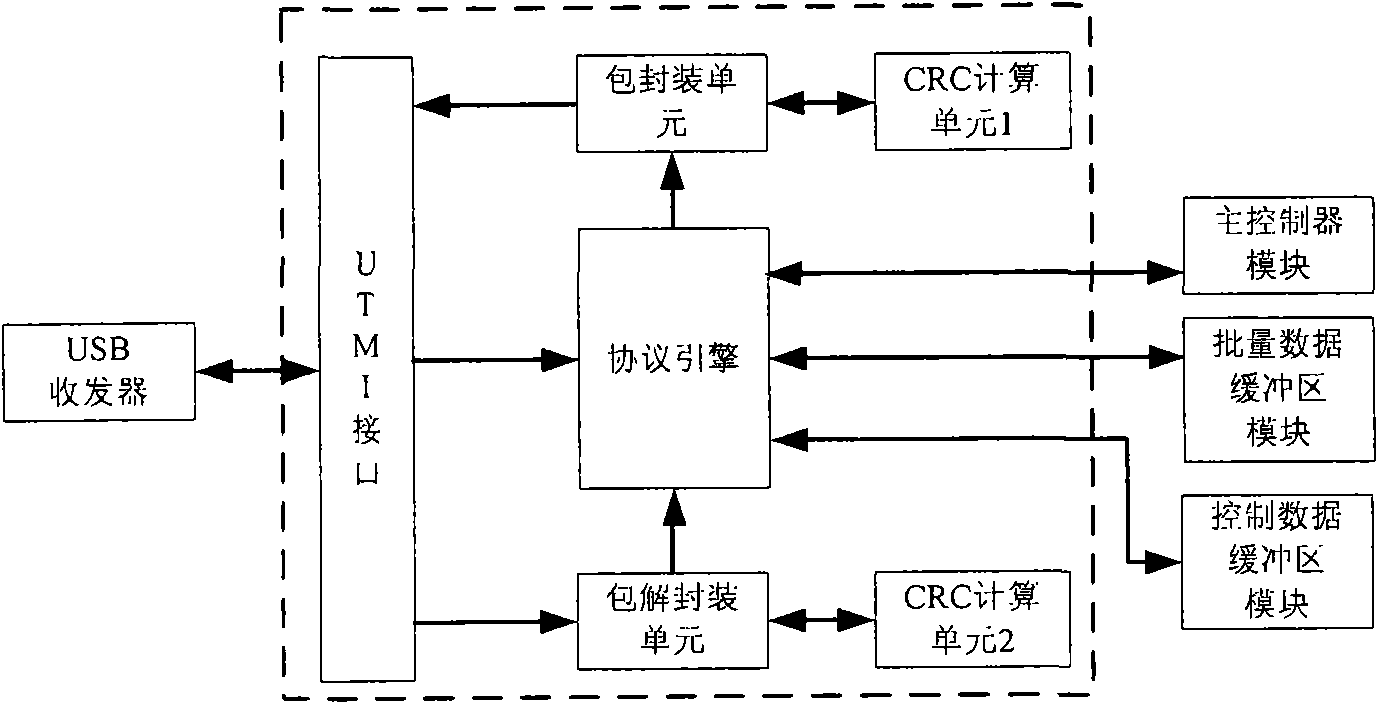
The invention relates to a method and a device for encrypting data in an ATA memory device with a USB interface. Based on the conventional ATA memory device, the device for encrypting data consisting of a user card and a hardware encryption board card encrypts data transmitted between the memory device and a USB host, thereby achieving the aim for encrypting the data in the memory device. The device for encrypting data consists of a user secret key card and a hardware encryption bard card; and the hardware encryption bard card consist of a USB transreceiver, a USB equipment controller, a control endpoint buffer area, a batch endpoint buffer area, a main controller, an encryption-decryption module, an ATA controller, a secret key acquisition module and a safe access module. The invention has the advantages that the secret key is directly read by the encryption device, without using a computer connected with the memory, thereby ensuring high security; in addition, the data can be encrypted and decrypted at high speed without using an operation system; and moreover, the secret key is stored in a special hardware secret key memory card, and the secret key and the protected data are independently stored, thereby ensuring the security of the data.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
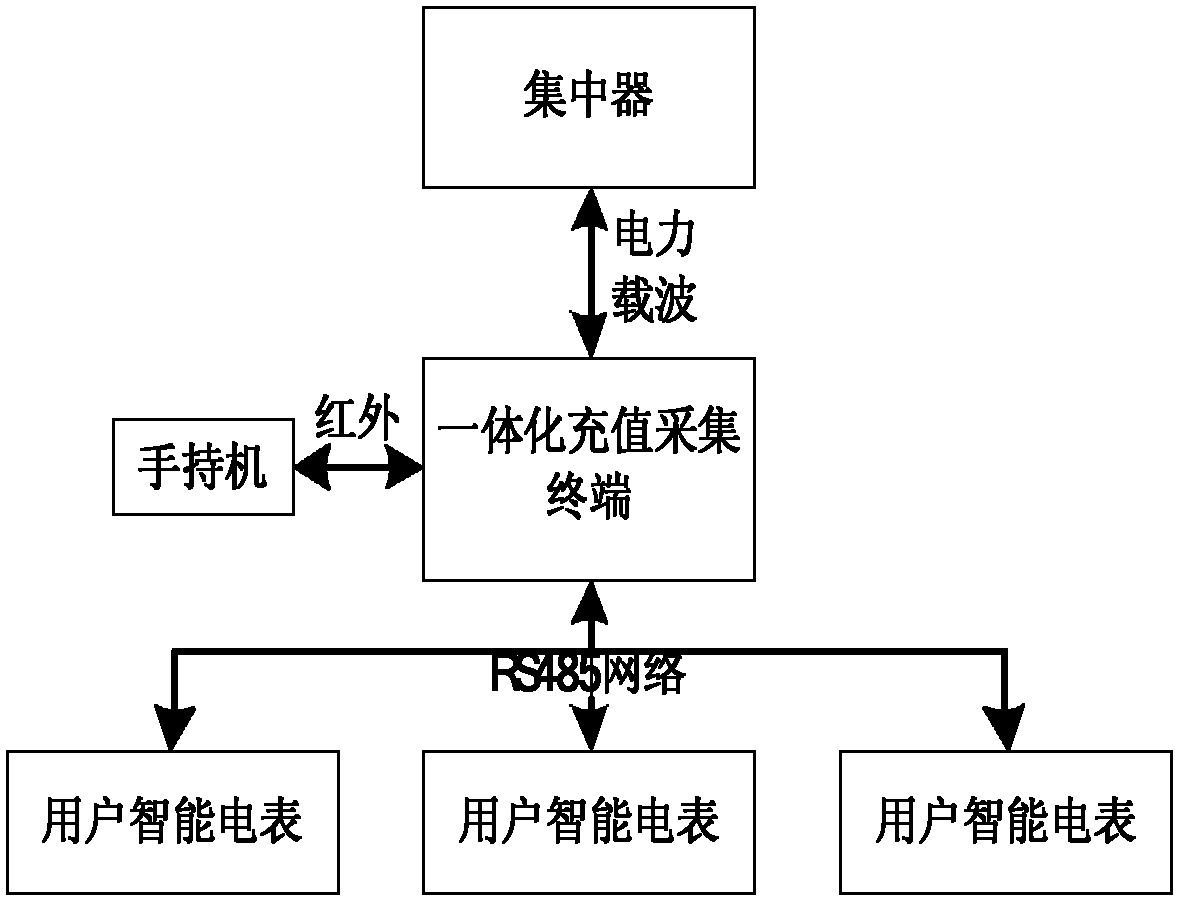
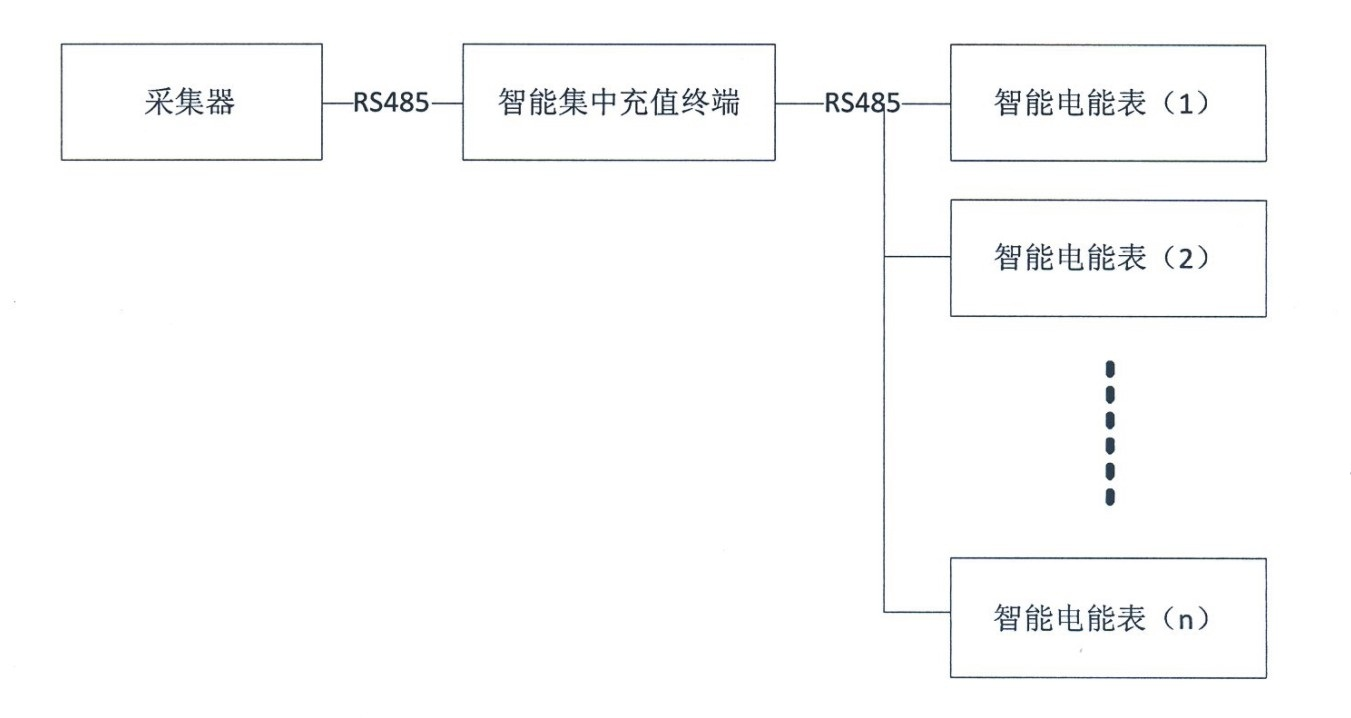
Integrated charging and acquisition terminal
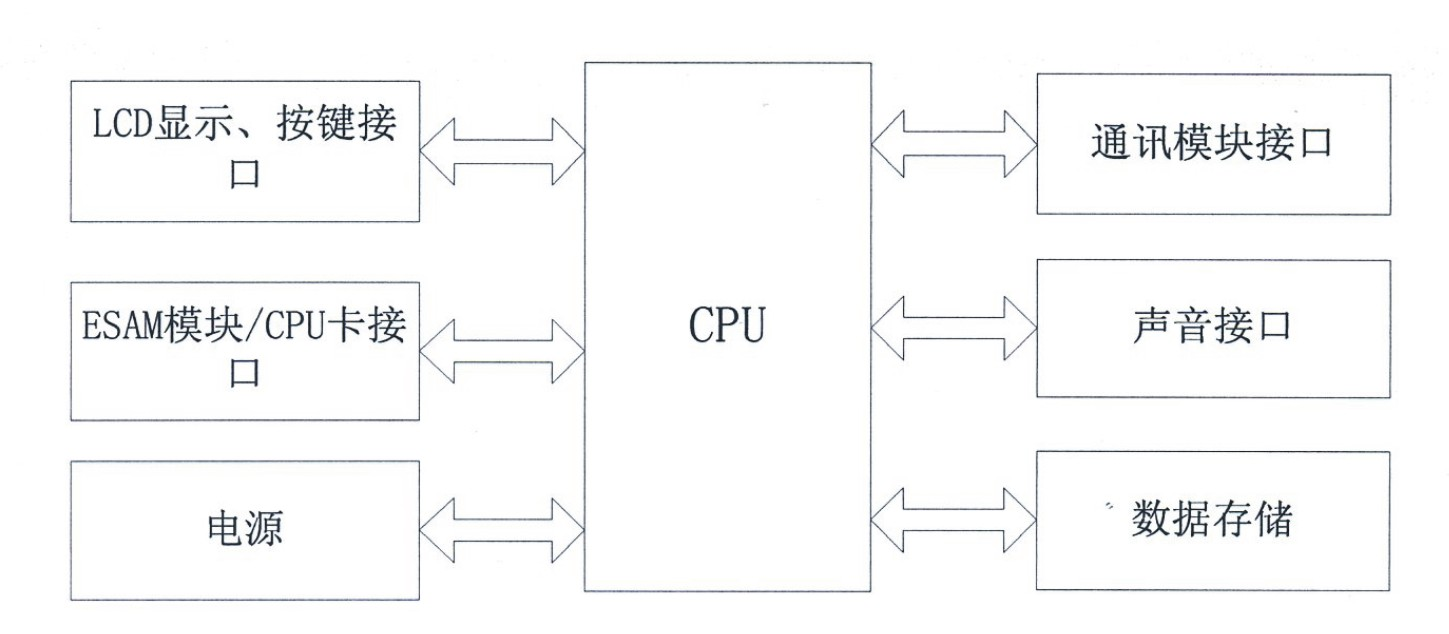
ActiveCN102426724AWith automatic switching rateWith data storage functionApparatus for hiring articlesMicrocontrollerDisplay device
The invention relates to an integrated charging and acquisition terminal, belonging to an electronic device for charging and data acquisition of an intelligent electric meter. The integrated charging and acquisition terminal mainly comprises a display unit, an IC (integrated circuit) card interface circuit, an encryption and authentication interface circuit, an RS485 interface circuit and a powercarrier circuit which are connected with a single chip microcomputer, wherein the IC card interface circuit and the encryption and authentication interface circuit are formed by adopting an electrostatic protection chip ESDA6V1-5W6 and an ESAM (embedded secure access module) chip; the RS485 interface chip in the RS485 interface circuit is connected with the single chip microcomputer by two optical coupling circuits; a thermistor, a piezoresistor and another thermistor are connected between an A end and a B end of the RS485 interface chip in sequence and in series; and the A end and the B end are respectively connected with a two-way transient diode and then are grounded; and the power carrier circuit mainly comprises a three-phase carrier module. The integrated charging and acquisition terminal integrates an IC card interface, a power carrier interface and an RS485 interface and has the characteristics of convenience in charging, electricity utilization inquiry and data forwarding fora user and the like.
Owner:STATE GRID SICHUAN ELECTRIC POWER CORP ELECTRIC POWER RES INST +1
Identity card information reading method
ActiveCN104517086AShorten read timeAvoid timeout failuresSensing record carriersComputer hardwareClient-side
Owner:SHANDONG SENTER ELECTRONICS
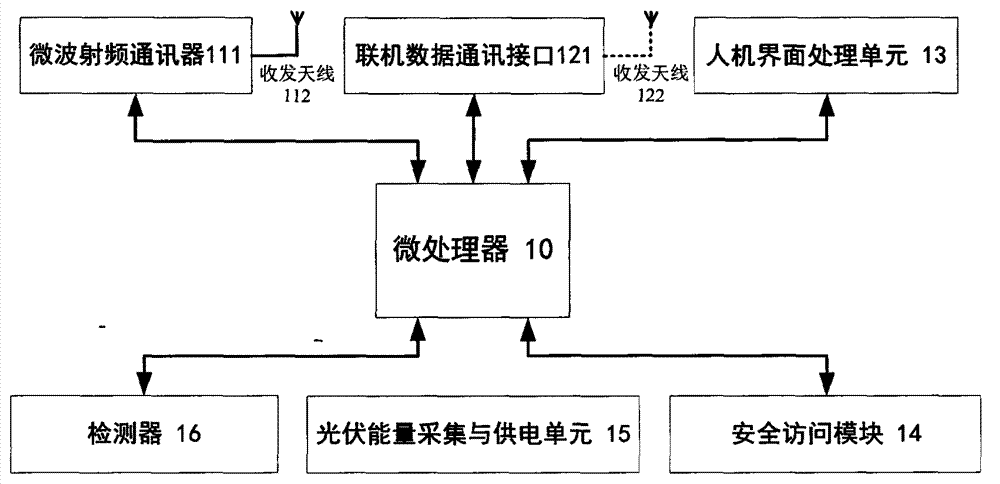
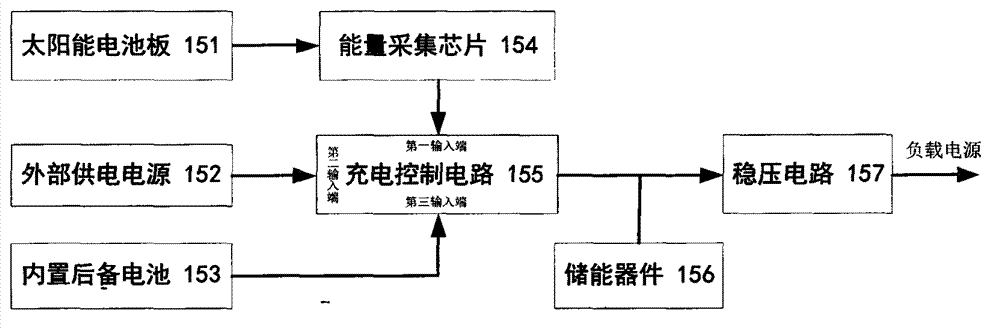
Roadside equipment with solar collection mechanism
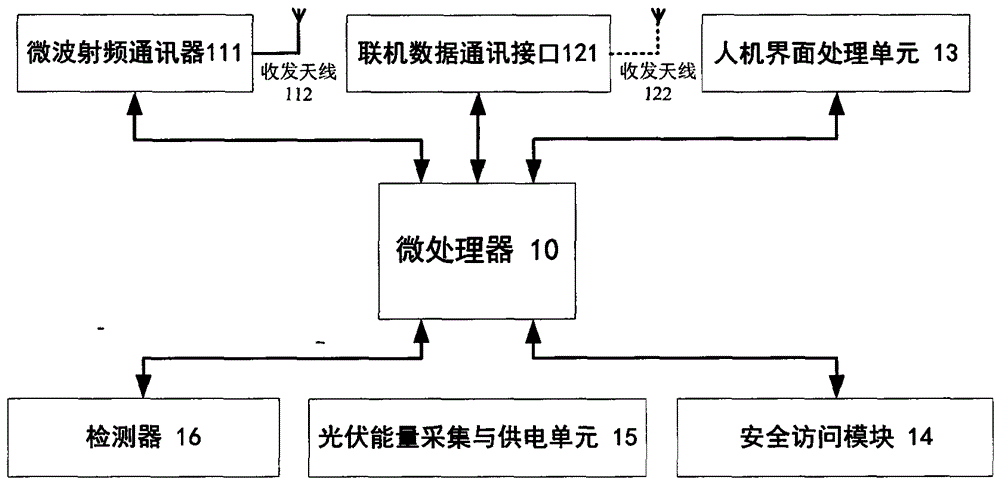
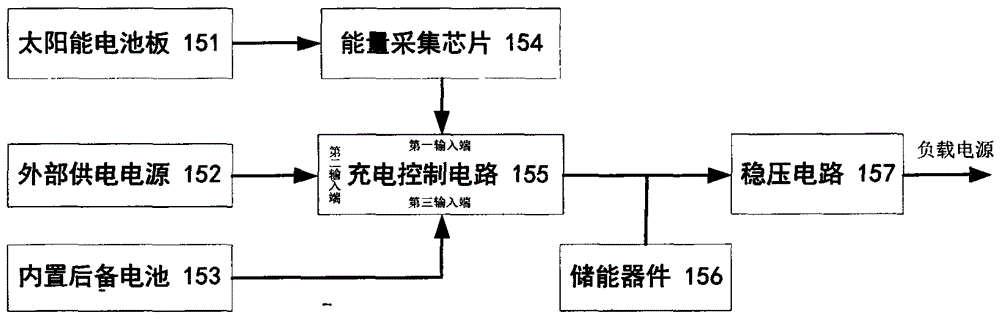
ActiveCN102881052AImprove collection utilizationLarge amount of collectionTicket-issuing apparatusHuman–machine interfaceThe Internet
The invention relates to roadside equipment with a solar collection mechanism. The roadside equipment with the solar collection mechanism comprises a photovoltaic energy and power supply unit, a microprocessor, a microwave radio frequency communicator connected with the microprocessor, receiving and transmitting antennas, an on-line data communication interface, a human-computer interface processing unit, a safety access module and a detector. Compared with the conventional technical scheme, the roadside equipment is provided with the solar collection mechanism, adopts a building block type technical framework scheme on communication frequency points and protocols and has the characteristics of energy conservation, environmental friendliness, simplicity and convenience for installation and upgrading, high compatibility and easiness in popularization. The product is applicable to various intelligent traffics and the internet of things under the urban environment, such as an electronic toll collection (ETC) system of a parking lot, an intelligent parking meter, parking management and other human, vehicle and object identification management based on radio frequency identification devices (RFID).
Owner:深圳市迅朗科技有限公司
Integrated circuit (IC) card module security authentication method for intelligent water meter
ActiveCN102881085AEnsure safetyGuaranteed reliabilityApparatus for hiring articlesComputer moduleSecurity authentication
The invention discloses an integrated circuit (IC) card module security authentication method for an intelligent water meter. The water meter, a user card and a purchase secure access module (PSAM) card are involved. The authentication method comprises an authentication flow between the user card and the PSAM card and an authentication flow between the user card and the water meter. The authentication flow between the user card and the PSAM card comprises the following steps of: (1) performing corresponding operation on the user card through external authentication between the user card and the PSAM card; (2) checking a water purchase information file of the user card by using the water meter; and (3) performing information file rewriting operation on the user card by using the water meter after the authentication flow between the user card and the water meter succeeds. According to the security authentication method, the requirement of information security can be met by the intelligent water meter on the premise of no use of an embedded secure access module (ESAM) security chip, and the application cost of the intelligent water meter is also lowered.
Owner:BEIJING JOYO SMART WATER METER
Encrypted banner overlays
InactiveUS20120271769A1Digital data protectionDigital data authenticationComputer SessionSecure access module
A computer session management system operates in conjunction with a host computer, and comprises: i) a safe access module to facilitate safe access to a computer-based application, particularly a network-based application, in conjunction with said host computer; and ii) an advertising module providing advertisements associated with the computer-based application.
Owner:ISPFORCE
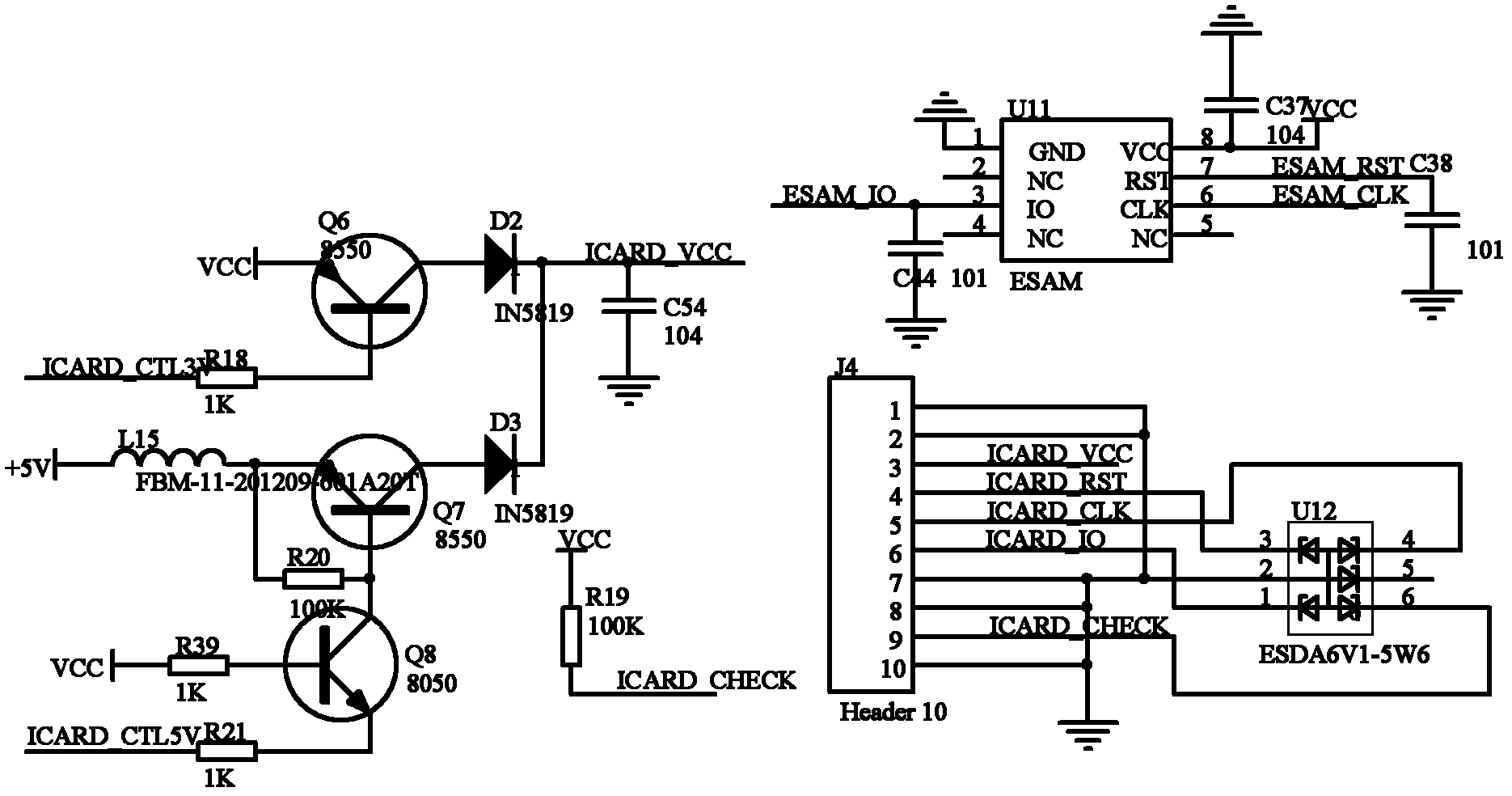
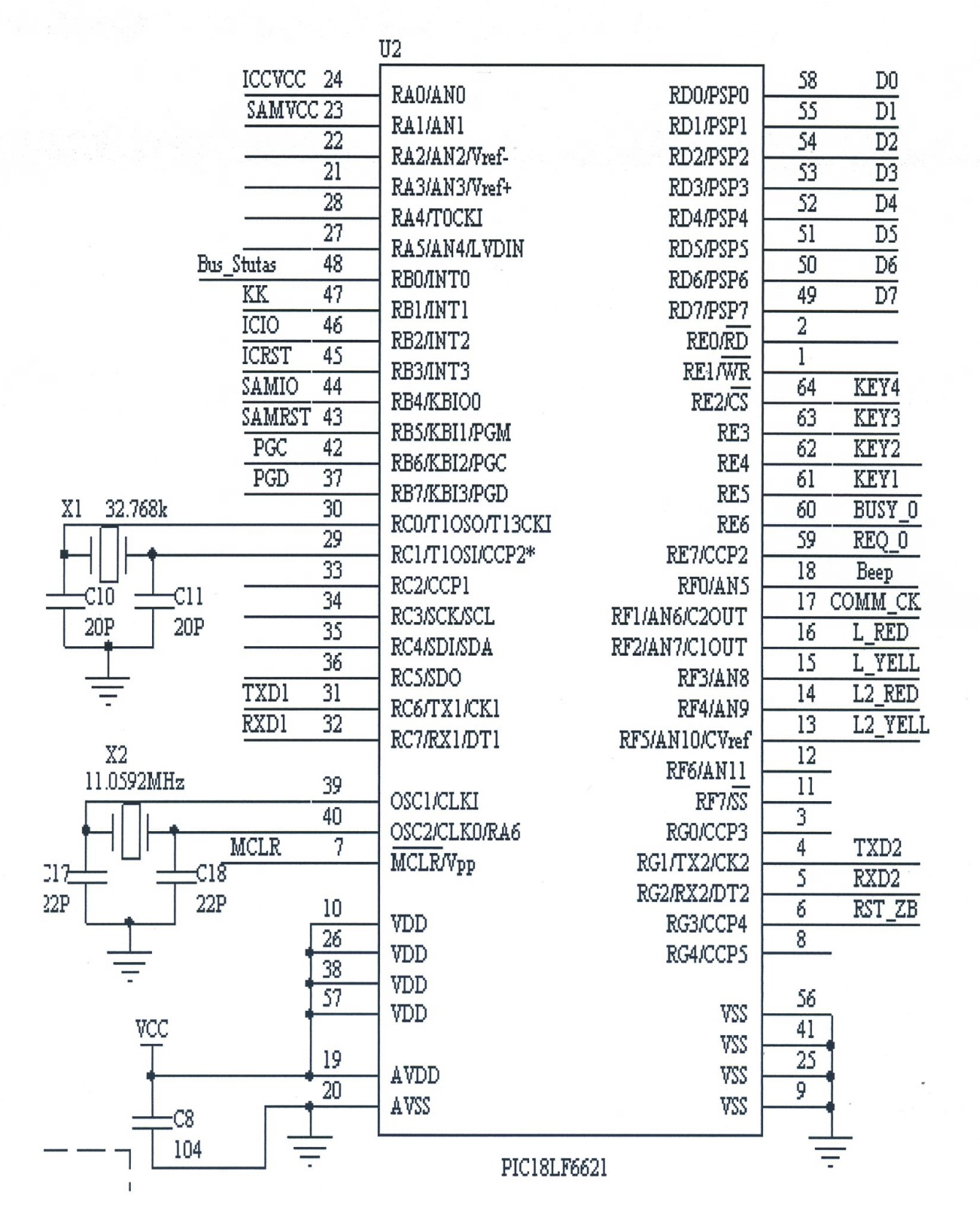
Intelligent electric meter centralized recharging terminal and control method thereof
ActiveCN102074076AEnsure safetyImprove reliabilityElectrical measurement instrument detailsApparatus for hiring articlesComputer moduleE communication
The invention provides an intelligent electric meter centralized recharging terminal and a control method thereof, relating to the technical field of combination of electrical equipment and computers. The terminal comprises an IC card interface circuit, an embedded secure access module (ESAM) circuit and two communication module interface circuits, wherein the IC card interface circuit is connected with a CPU via ICREST and ICIO pins; the ESAM circuit is connected with the CPU via data and reset pins SAMIO and SAMRST; the two communication module interface circuits are respectively connected with the CPU, realize communications with an intelligent electric meter and a collector and can monitor communication data between the collector and the electric meter in real time and forward the data; the IC card interface circuit completes communications with user card interfaces; and the ESAM circuit completes data exchange and reset operations and various safety certification operations such as encryption, decryption and operation. A program module for the intelligent electric meter centralized recharging terminal is also designed. The terminal has the following advantages and beneficial effects: normal communications of the system are ensured; and the operations are convenient, simple, safe and reliable.
Owner:STATE GRID SICHUAN ELECTRIC POWER CORP ELECTRIC POWER RES INST +1
Intelligent mobile terminal with on-site payment function
The invention provides an intelligent mobile terminal with an on-site payment function. The mobile terminal comprises a main body and a shell, wherein the main body comprises a main controller, and a wireless communication module, an SIM (subscriber identity module) card module and a near-field communication module which are connected with the main controller respectively; a PSAM (purchase secure access module) card, a magnetic stripe card decoding chip and an IC (integrated circuit) card decoding chip are embedded into the main body; the PSAM card, the magnetic stripe card decoding chip and the IC card decoding chip are connected with the main controller respectively; a magnetic stripe card slot and a contacted type IC card slot are further arranged in the shell; a magnetic stripe card reading head connected with the main controller is arranged inside the magnetic stripe card slot; and an IC card reading head connected with the main controller is arranged inside the contacted type IC card slot. According to the intelligent mobile terminal provided by the embodiment of the invention, mobile phone functions, bank card functions and POS (point-of-sale) functions are integrated together, so that various types of bank cards are supported; and the mobile terminal can be used for replacing an existing dedicated POS machine; and the mobile terminal is convenient to carry over, low in cost and improved in the convenience in use of users.
Owner:SHENZHEN CHINAKING MOBILE TECH
Cipher text access control system based on cloud computing platform
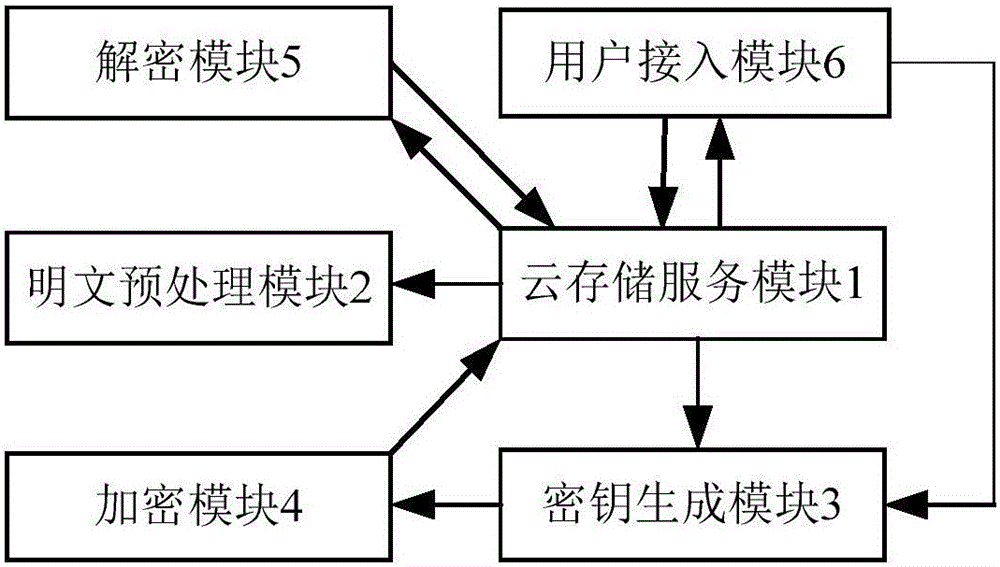
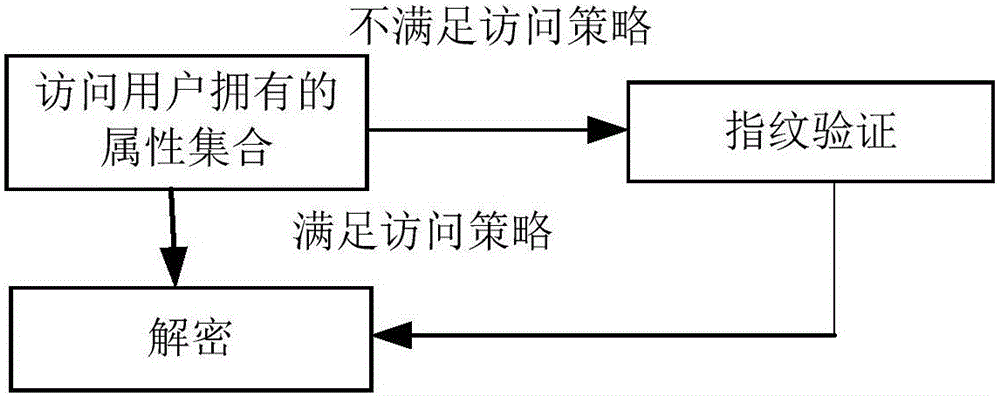
InactiveCN106209357ASave storage spaceImprove Access Control EfficiencyKey distribution for secure communicationHigh level techniquesPlaintextMultiplexing
The invention discloses a cipher text access control system based on a cloud computing platform. The system comprises a cloud storage service module, a plaintext preprocessing module, a secret key generation module, an encryption module, a decryption module and a user access module. A plaintext of a user owner client is encrypted in a triple manner to obtain a triple encrypted cipher text, the triple encrypted cipher text is packaged by utilizing a digital envelope technology and then stored in the cloud storage service module, and the corresponding decryption module is arranged. Fine access control can be realized, computing cost of encryption and decryption between a user owner and a user can be reduced effectively, the data confidentiality is ensured, and collusion-proof aggressivity and forward and backward safety are included; and the cipher text access control system is controlled in different levels, the efficiency of access control is improved, a code division multiplexing technology is used to code plaintext information, the cipher text storage space is reduced, and the total performance of the system is improved.
Owner:杨炳
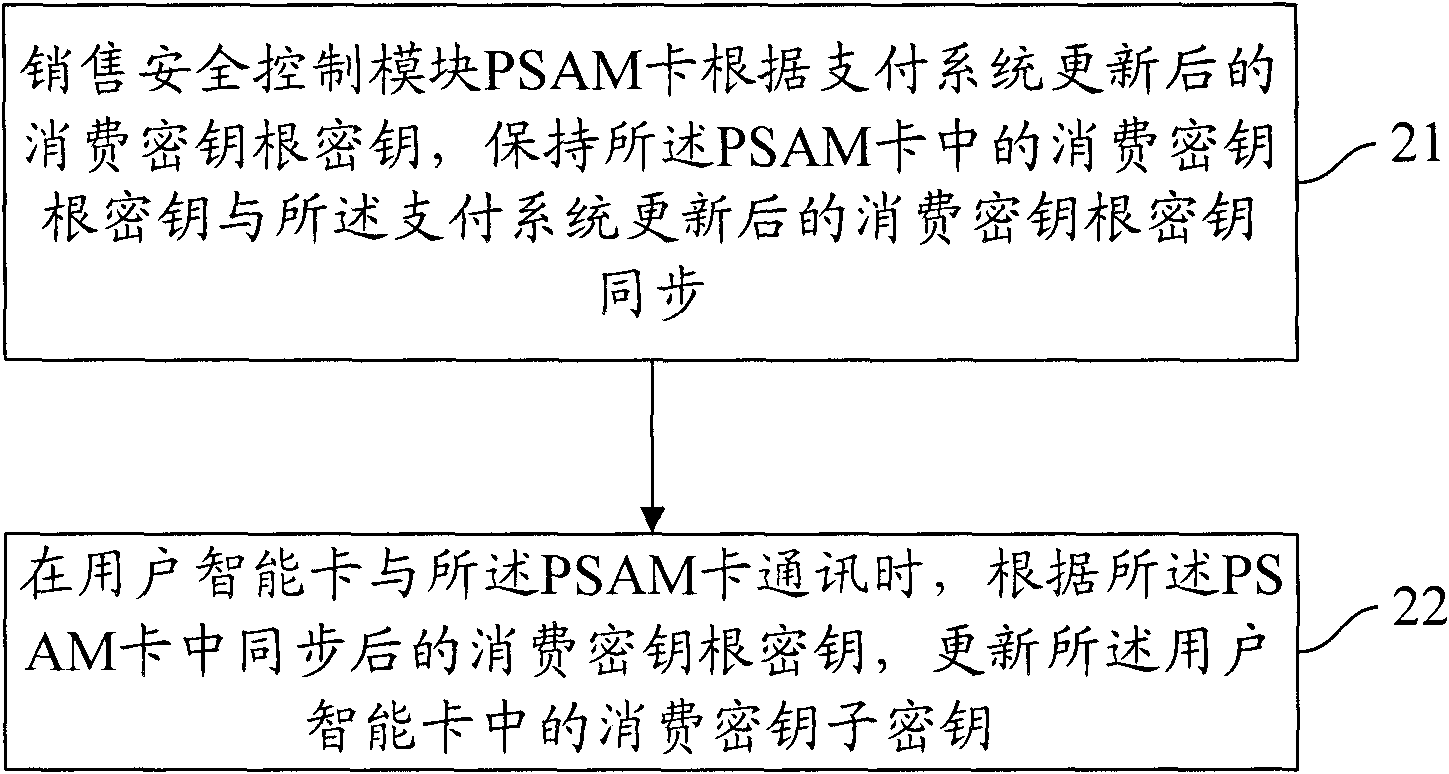
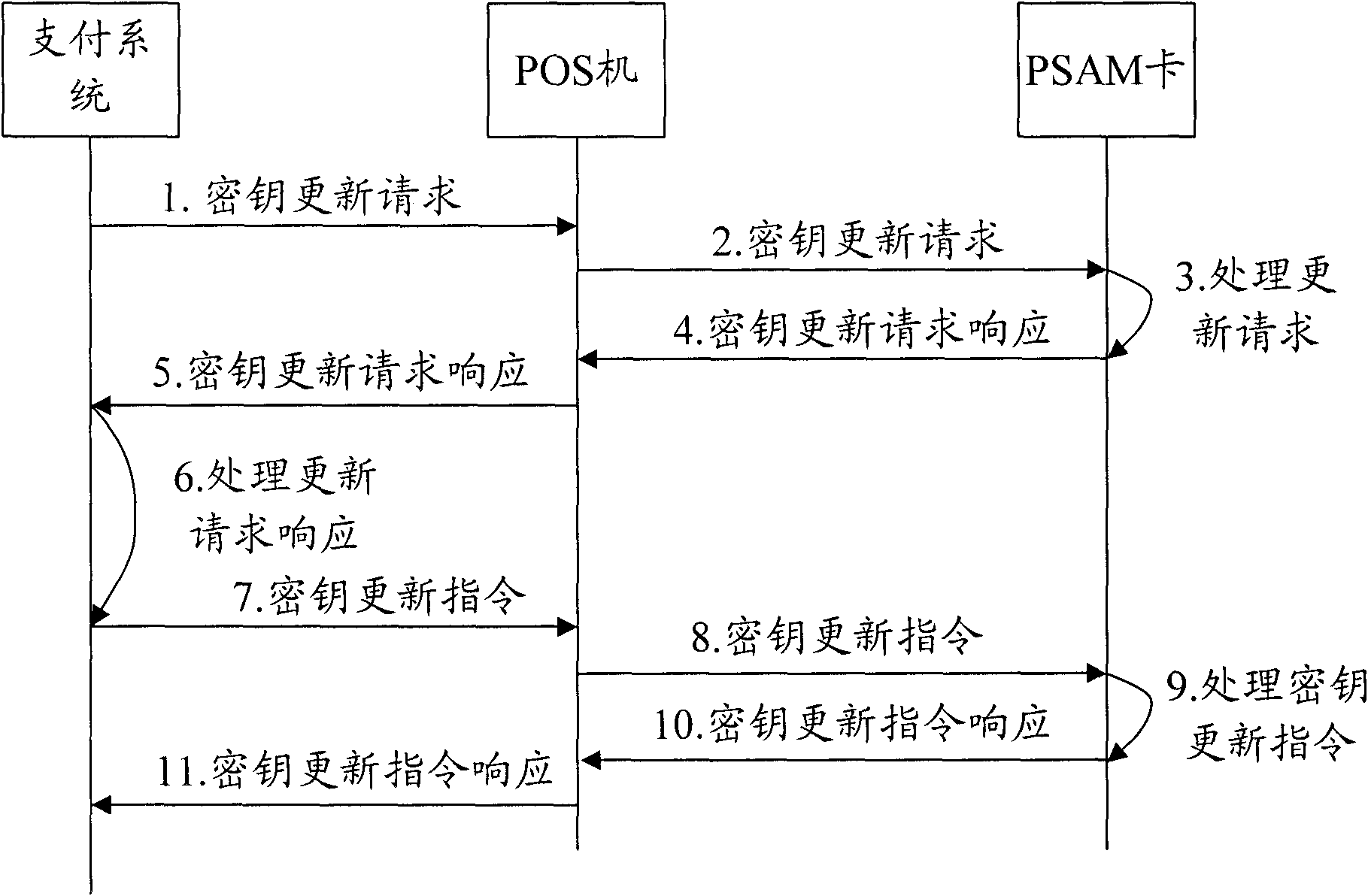
Method, system and PSAM (Purchase Secure Access Module) card for updating encryption key of smart card
ActiveCN102063767AEfficient discoveryIncrease success rateComplete banking machinesSecure access modulePayment system
The invention provides a method, system and PSAM (Purchase Secure Access Module) card for updating an encryption key of a smart card, wherein the method comprises: according to the updated consumption encryption key root encryption key of a payment system, the PSAM card keeps synchronization of the consumption encryption key root encryption key in the PSAM card and the updated consumption encryption key root encryption key of the payment system; and a user smart card updates a consumption encryption key sub key in the user smart card according to the consumption encryption key root encryptionkey after synchronization in the PSAM card when the user smart card and the PSAM card are communicating. By adopting the scheme of the invention, the consumption encryption key sub key of an electronic wallet is easy to update and the update success ratio is high.
Owner:CHINA MOBILE COMM GRP CO LTD
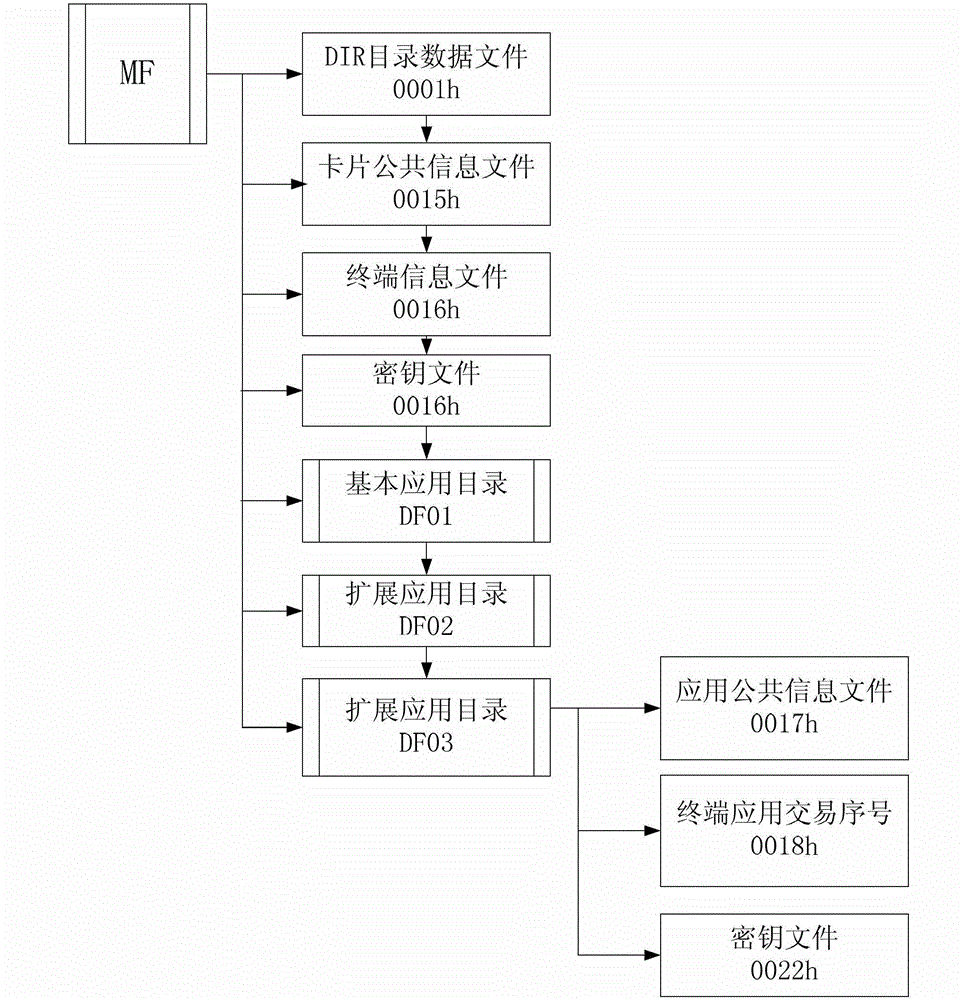
Lane purchase secure access module (PSAM) for city road bridge free stream toll collection and use method thereof
InactiveCN103150771AProcessing speedImprove work performanceTicket-issuing apparatusOn boardStructure of Management Information
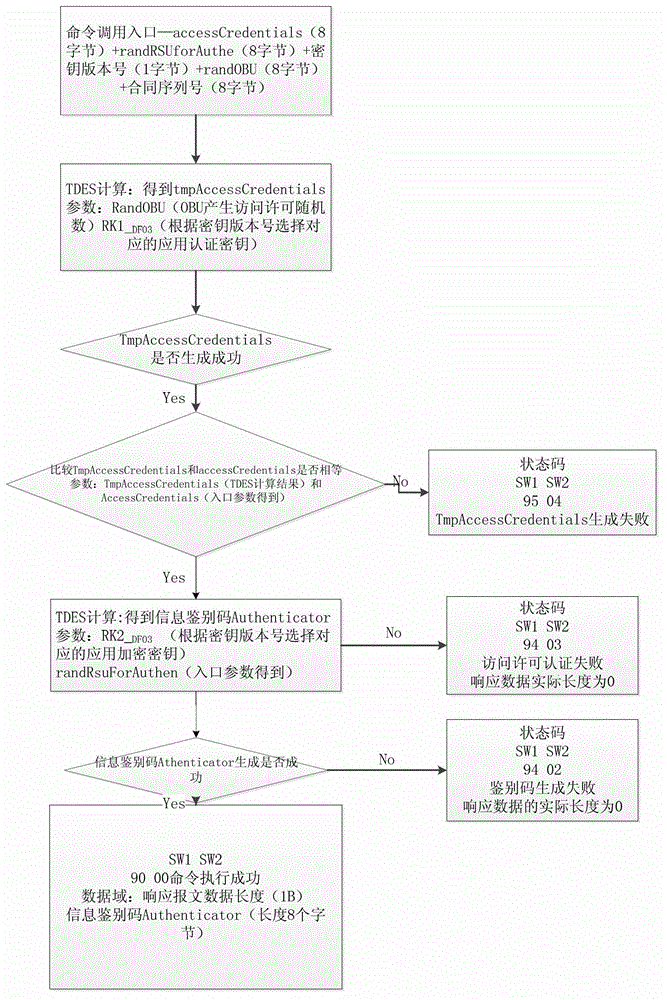
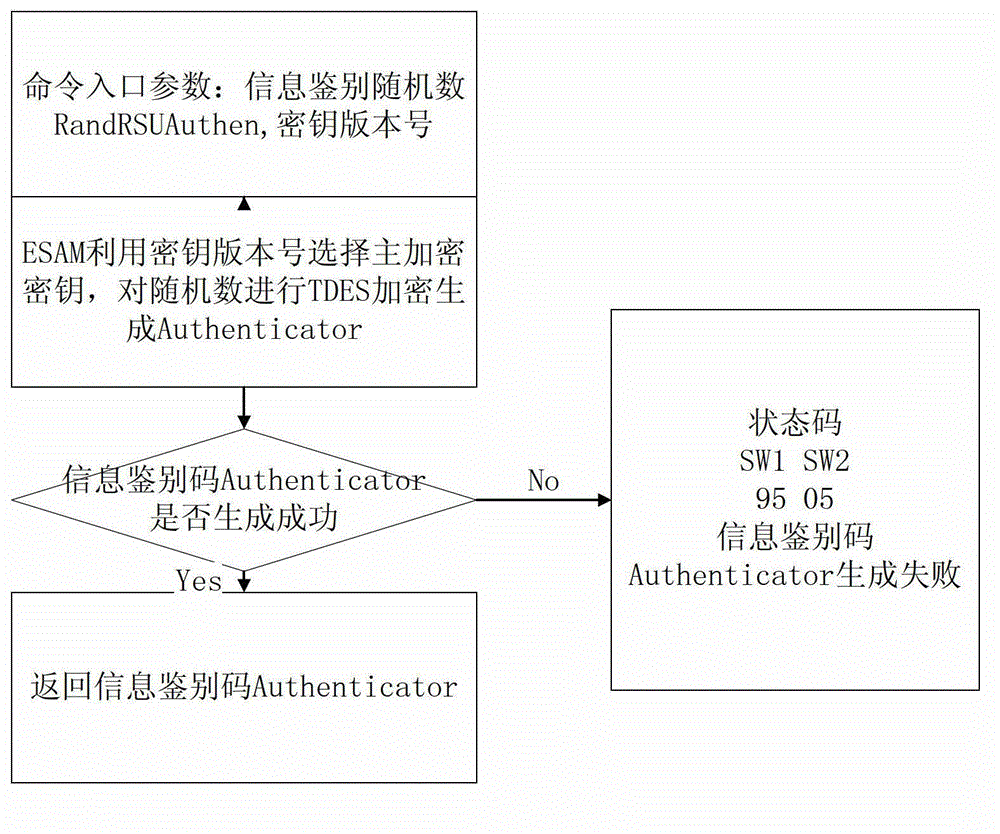
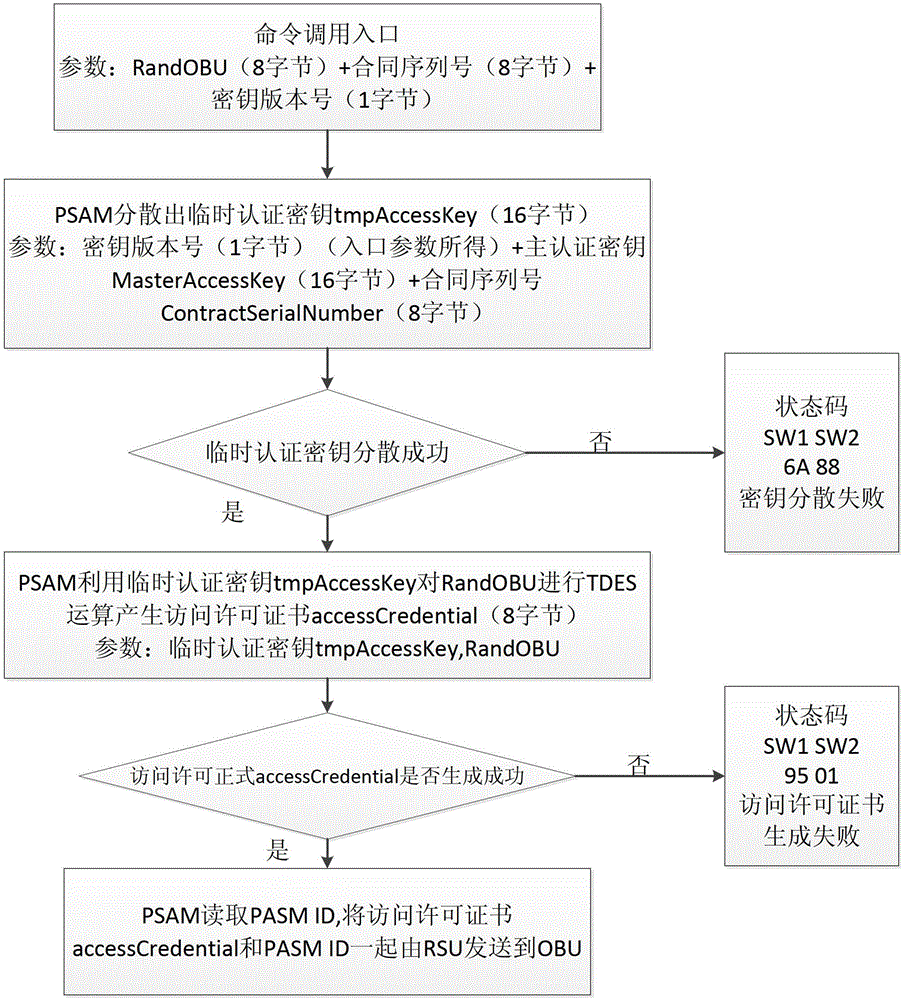
The invention provides a lane purchase secure access module (PSAM) card for city road bridge free stream toll collection and a use method of the lane PSAM card for the city road bridge free stream toll collection. An arborescence hierarchical structure is adopted by a file structure of the PSAM card, a root node of the PSAM card is a master control file, a child node of the PSAM card comprises a directory data file, a card public information file, a terminal information file, a master key file, a basic application directory, a first extensive application directory and a second extensive application directory, wherein the second extensive application directory comprises an application public information file, a terminal application trade serial number and a second key file. The use method of the lane PSAM card for the city road bridge free stream toll collection comprises a bidirectional safety certification process in concurrent operation of a road side unit to an on board unit, wherein the bidirectional safety certification process comprises an information identification process of the road side unit to the on board unit, and an access permission certification process of the on board unit to the road side unit in sequence.
Owner:武汉市城市路桥收费管理中心 +1
A roadside device with solar energy harvesting mechanism
ActiveCN102881052BImprove collection utilizationLarge amount of collectionTicket-issuing apparatusHuman–machine interfaceThe Internet
Owner:深圳市迅朗科技有限公司
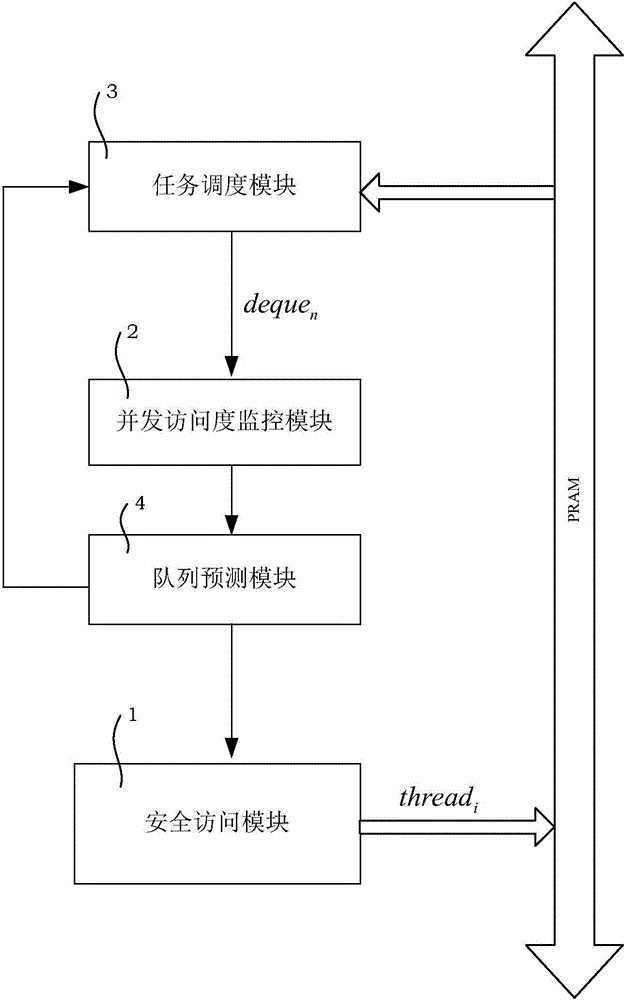
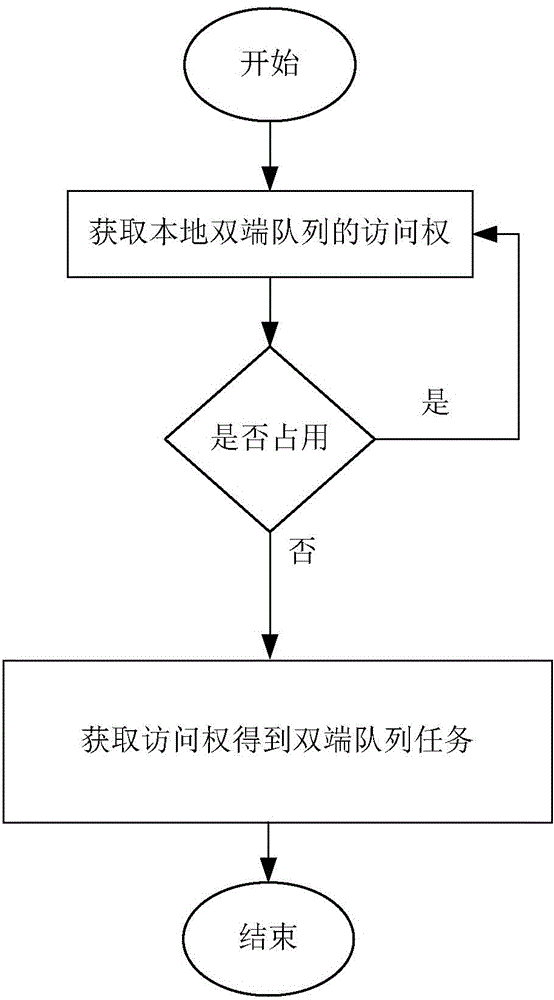
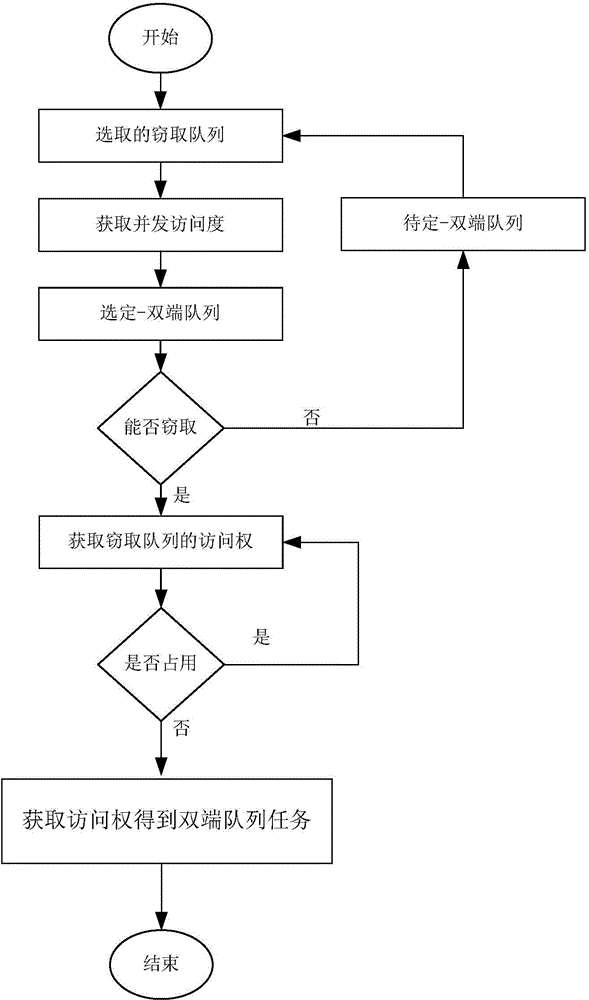
Concurrent queue access control method and system based on task eavesdropping
InactiveCN104156260AFlexible operationImprove performanceMultiprogramming arrangementsRandom-access machineControl system
The invention discloses a concurrent queue access control method and system based on task eavesdropping. The concurrent queue access control system based on task eavesdropping comprises a safe access module (1), a concurrent access degree monitoring module (2), a task scheduling module (3) and a prediction module (4). By means of the method, operations of double-end queues are separated from access control, a queue concurrent access degree monitoring mechanism is built, in the task eavesdropping process, the queues are dynamically selected in a self-adaptation mode for operation according to the queue concurrent access degree, accordingly concurrent access of the double-end queues is evenly distributed to the double-end queues, and thread safety of execution operations of the double-end queues is guaranteed in a blocking mode in terms of access of each double-end queue. The method supports different task eavesdropping strategies, and as for applications using task eavesdropping and operating on a concurrent random access machine, a higher throughput rate and the acceleration effect are achieved.
Owner:凯习(北京)信息科技有限公司
Vehicle electronic information card safety protection system and method
InactiveCN103336977AAchieving dynamismImprove read and write speedEncryption apparatus with shift registers/memoriesCo-operative working arrangementsComputer hardwareData center
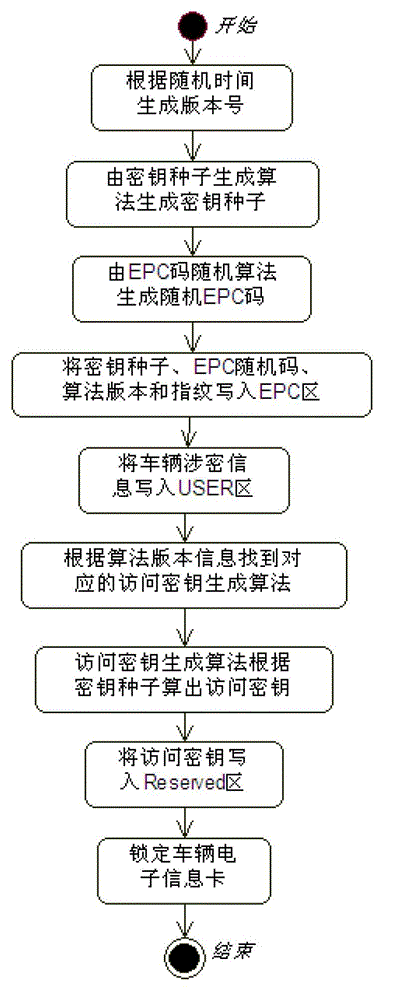
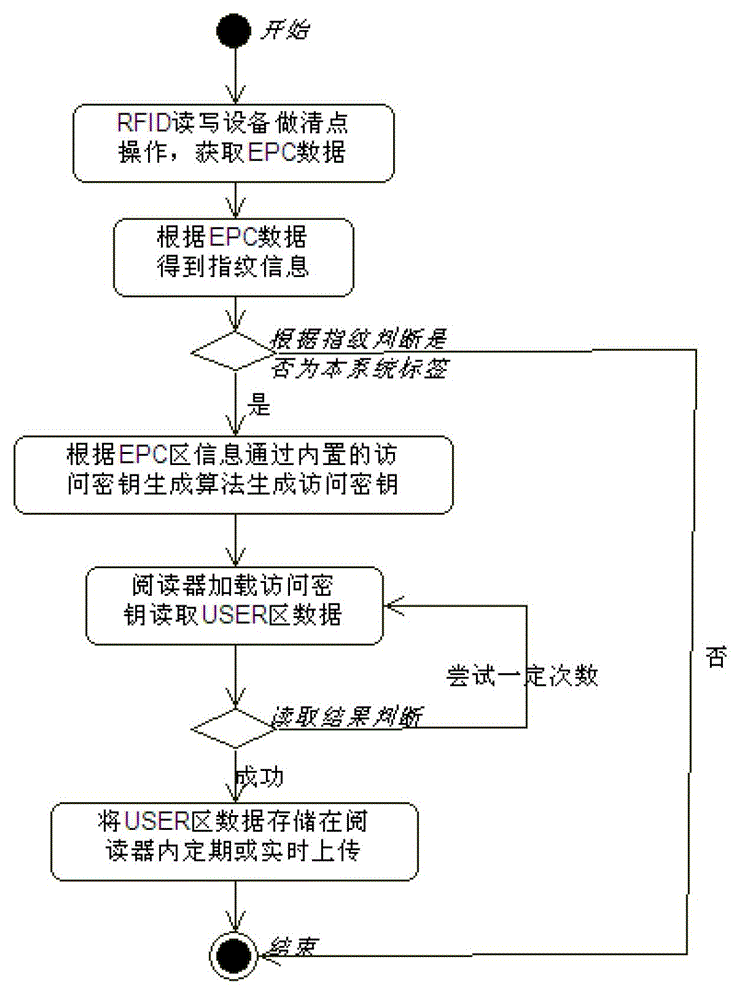
The invention discloses a vehicle electronic information card safety protection system and a method. The system comprises an RFID (radio frequency identification devices) reader-writer, a PSAM (purchase secure access module) card inserted into the RFID reader-writer, a vehicle electronic information card, and a soft PSAM card. The soft PSAM card includes an initialization module, an authentication module and an access secret key dynamic generation module. The initialization module is used for an initialization setting of the PSAM card; the authentication module is used for authentication of the PSAM; the access secret key dynamic generation module generates an access secret key of the vehicle electronic information card; the access secret key is returned to the system by the RFID reader-writer; and the safety protection of vehicle electronic information card data is realized. Compared with the prior art, the safe and reliable "the soft PSAM + the hard PSAM" double safety kernels architecture method is provided in the invention; the access secret key of the vehicle electronic information card is not required to be stored in the RFID reader-writer, an acquisition device or a data center; the data safety in the vehicle electronic information card is improved; the read-write speed and efficiency of the RFID reader-writer is increased; and the dynamic feature of the access secret key generation is realized.
Owner:天津广行科技有限公司
Vehicle entering/exiting control system and method based on semi-online key
ActiveCN105610871ASolve the stolenSolve usabilityIndividual entry/exit registersTransmissionControl systemSecure access module
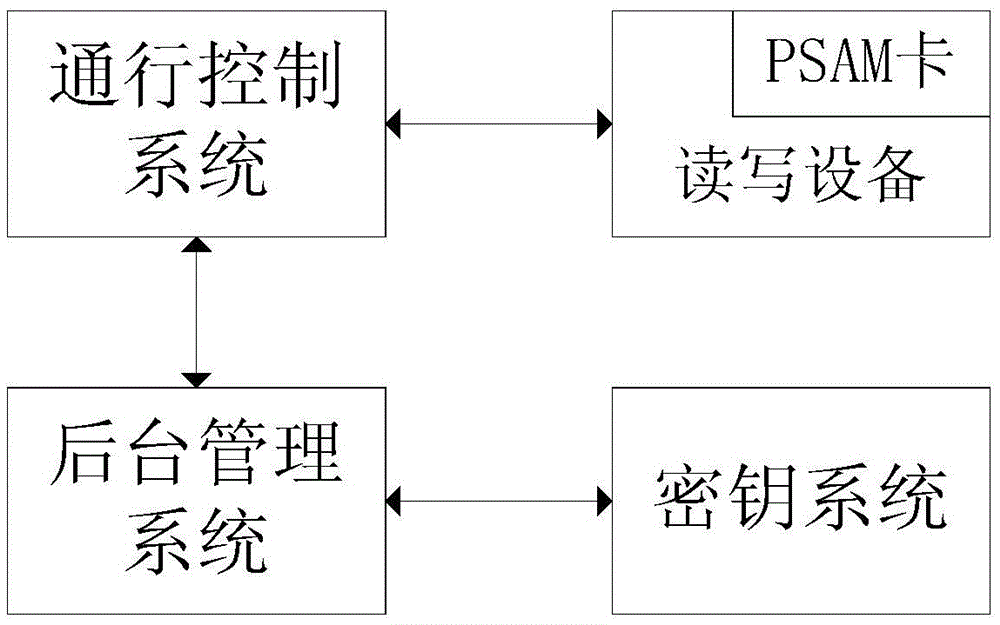
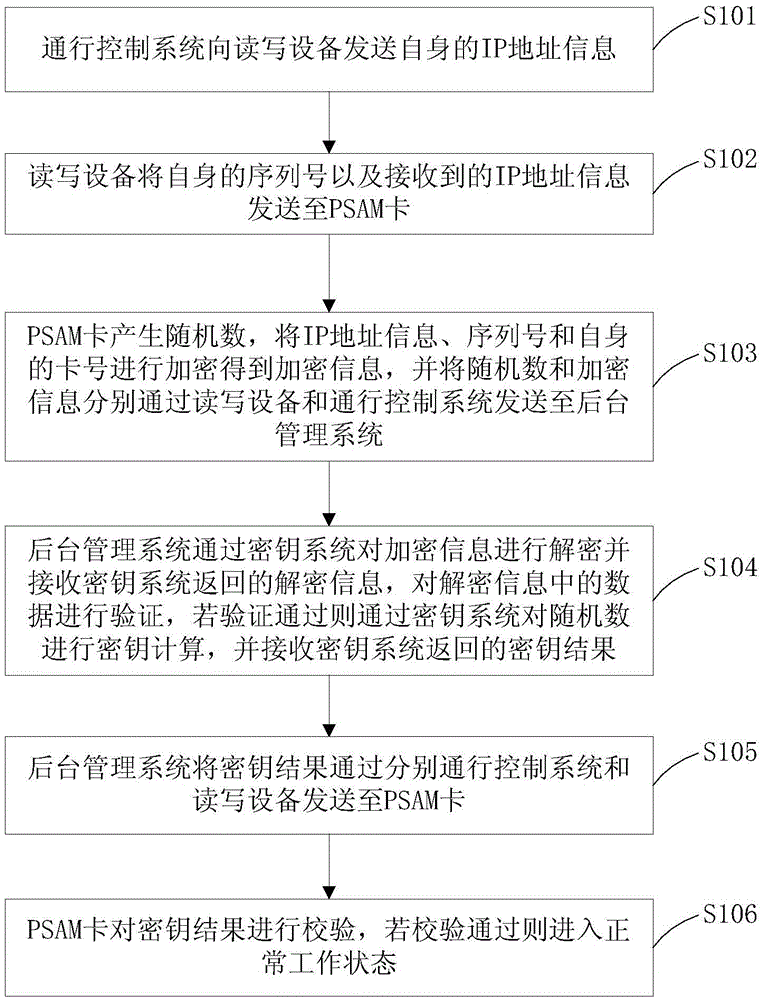
The invention discloses a vehicle entering / exiting control system and control method based on a semi-online key. The system comprises a PSAM (Purchase Secure Access Module) card, reading-writing equipment, a pass control system, a background management system and a key system, wherein the PSAM card is arranged inside the reading-writing equipment and electrically connected with the reading-writing equipment; the reading-writing equipment is electrically connected with the pass control system; the pass control system is connected with the background management system through a network; and the background management system is connected with the key system through the network. According to the control system, the PSAM card is arranged in the reading-writing equipment and combined with the background management system and the key system, and authentication and authorization are finished through communication interaction among the PSAM card, the background management system and the key system, so that the problem of dependence on the network quality is solved; the problem that the PSAM card is stolen and used maliciously is solved; and a balance point between the network demand and safety is found.
Owner:广州益车益路软件科技有限公司
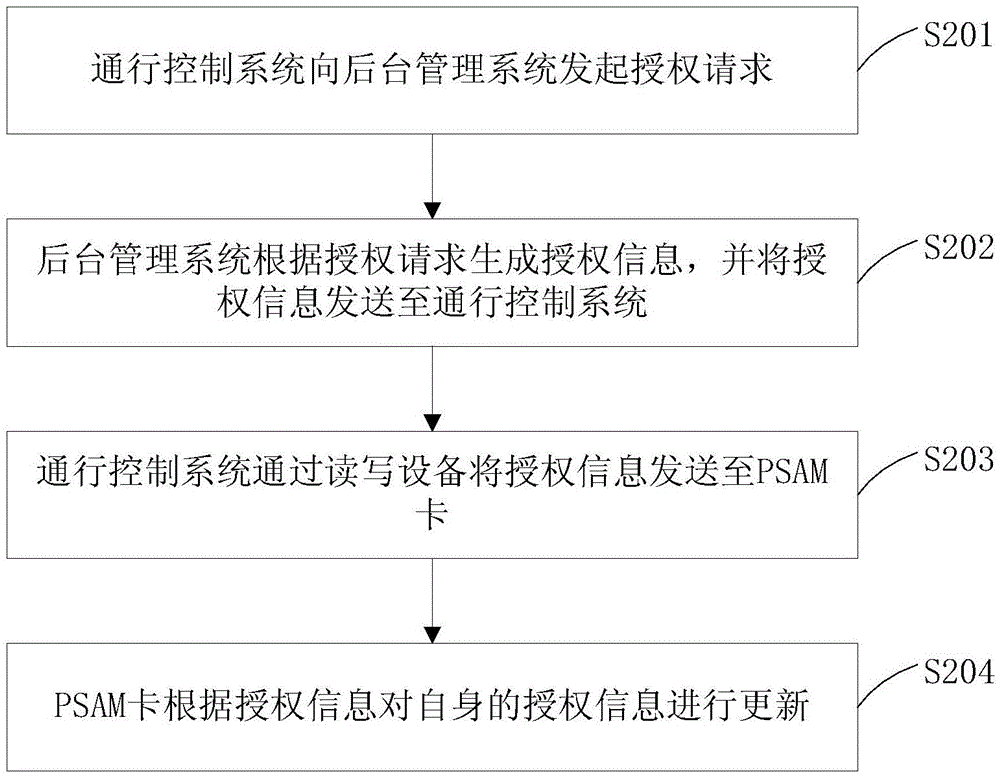
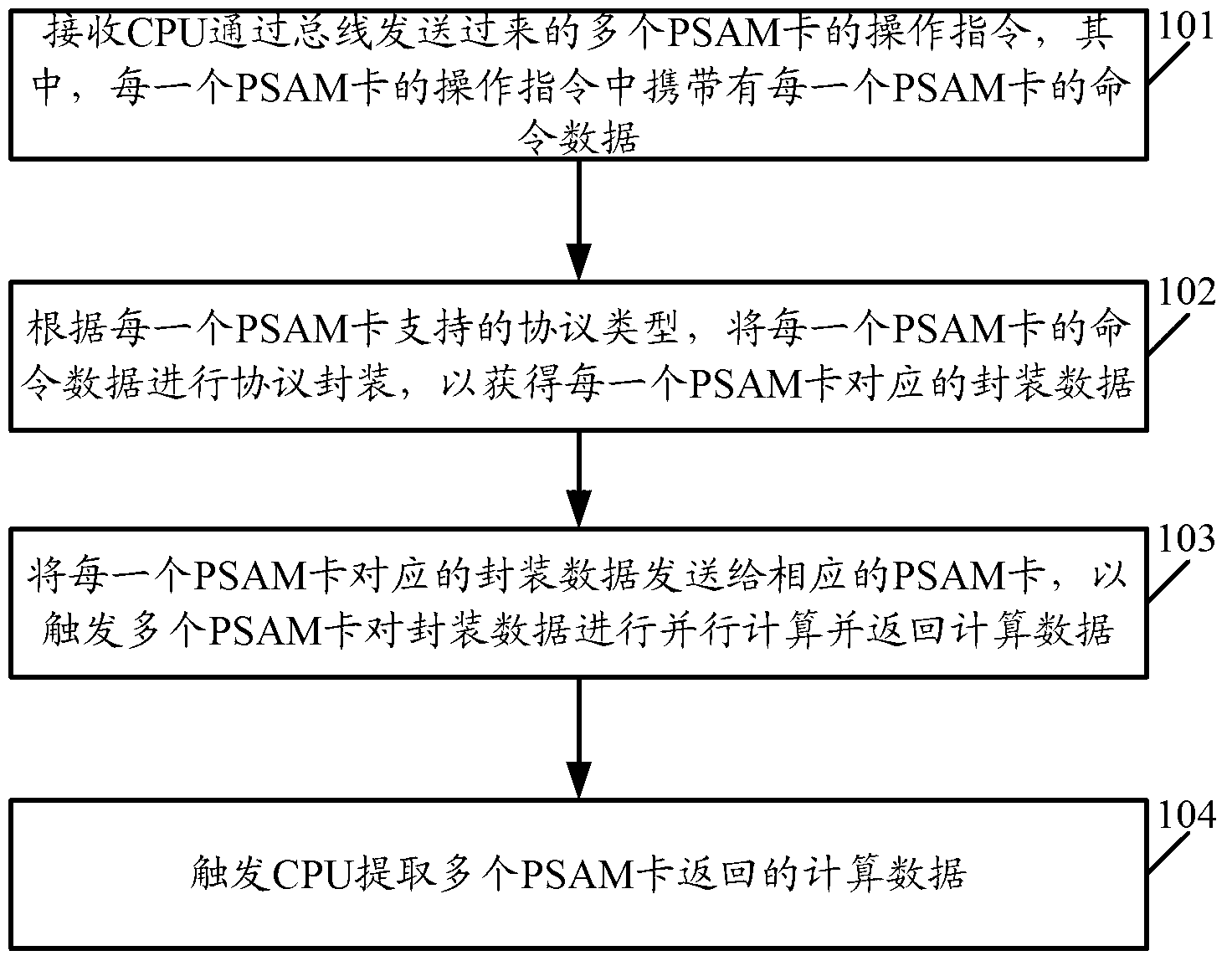
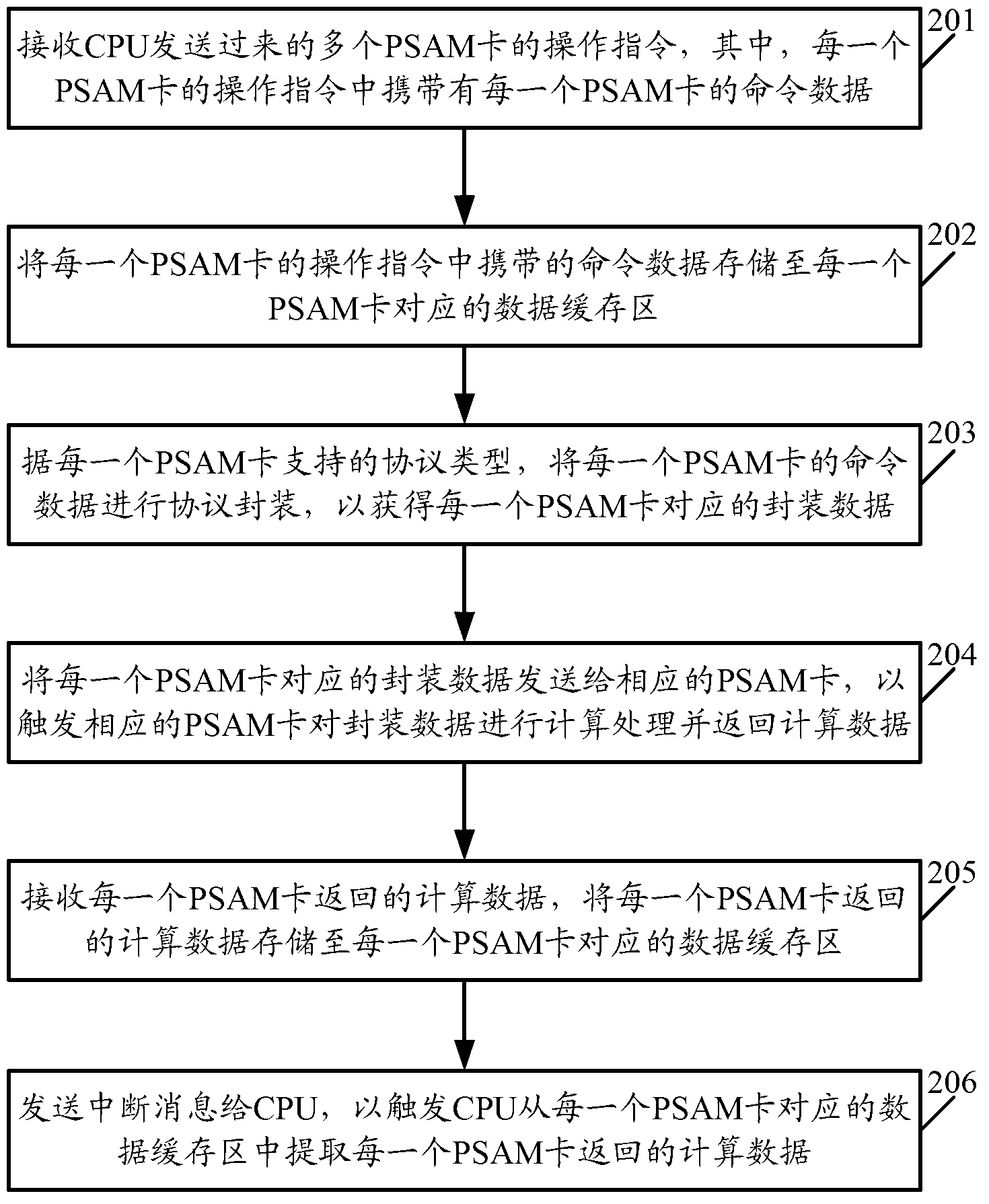
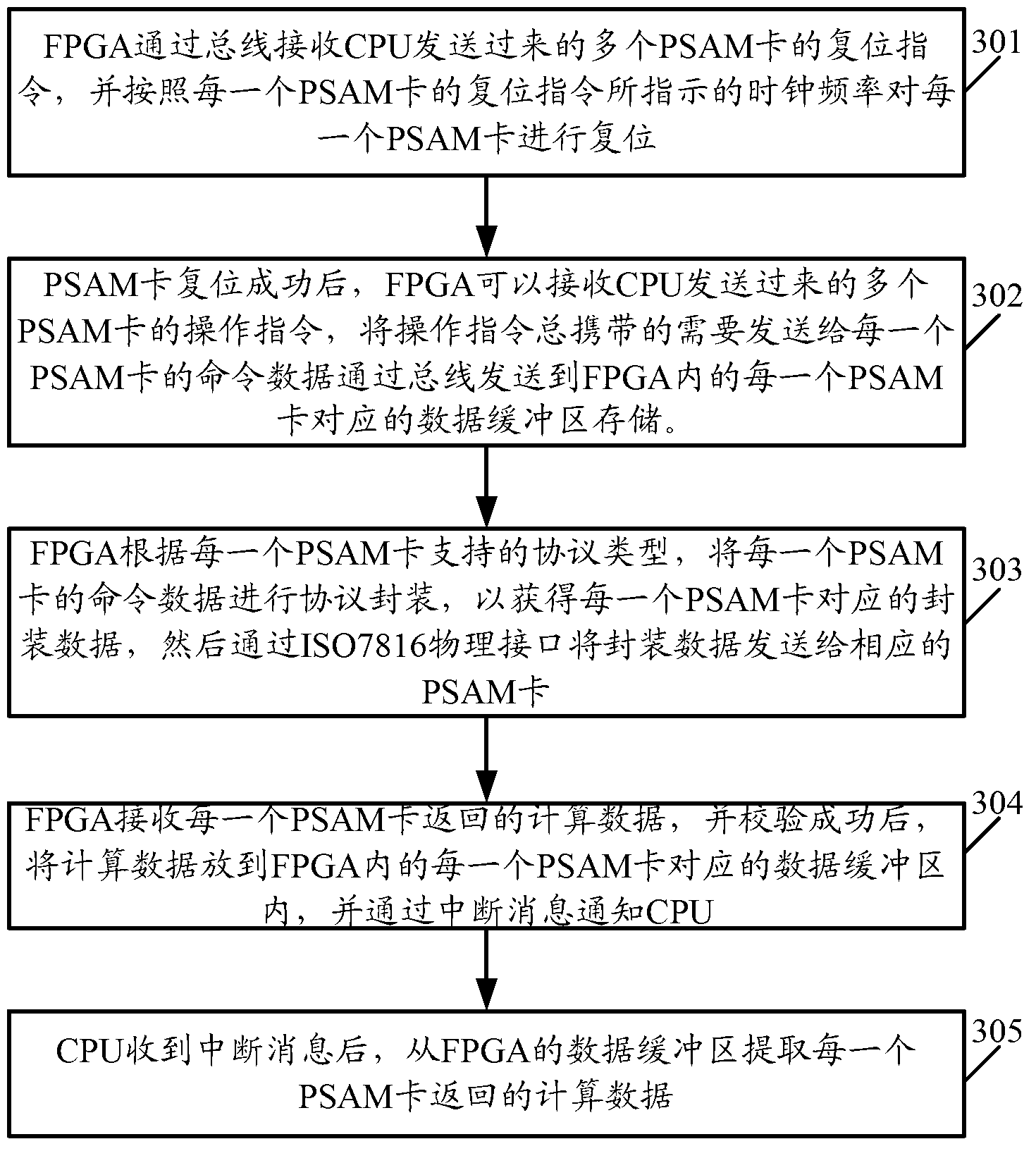
Method, equipment and system for implementing parallel calculation of purchase secure access module (PSAM) card
ActiveCN102929822AFlexible and configurable featuresEasy to switchElectric digital data processingEncapsulated dataData rate
The invention discloses a method, equipment and a system for implementing parallel calculation of a purchase secure access module (PSAM) card. The method comprises the following steps of: receiving operation instructions, which is sent by a central processing unit (CPU) through a bus, of a plurality of PSAM cards, wherein the operation instruction of each PSAM card carries command data of each PSAM card; performing protocol encapsulation on the command data of each PSAM card to acquire encapsulated data corresponding to each PSAM card; sending the encapsulated data corresponding to each PSAM card to the corresponding PSAM card, triggering the PSAM cards to perform parallel calculation on the encapsulated data, and returning calculated data; and triggering the CPU to extract the calculated data returned by the PSAM cards. By the method, the equipment and the system, real physical parallel calculation of the PSAM cards can be realized; the method, the equipment and the system have flexible configurable characteristics; the data rate of a physical interface is high; working loads of the CPU can be realized; the interface is stable and reliable; the number of PSAM cards is convenient to configure; and the PSAM cards is easy to transplant.
Owner:SHENZHEN GENVICT TECH
Intelligent lock system based on NFC (Near Field Communication) and unlocking method for intelligent lock system
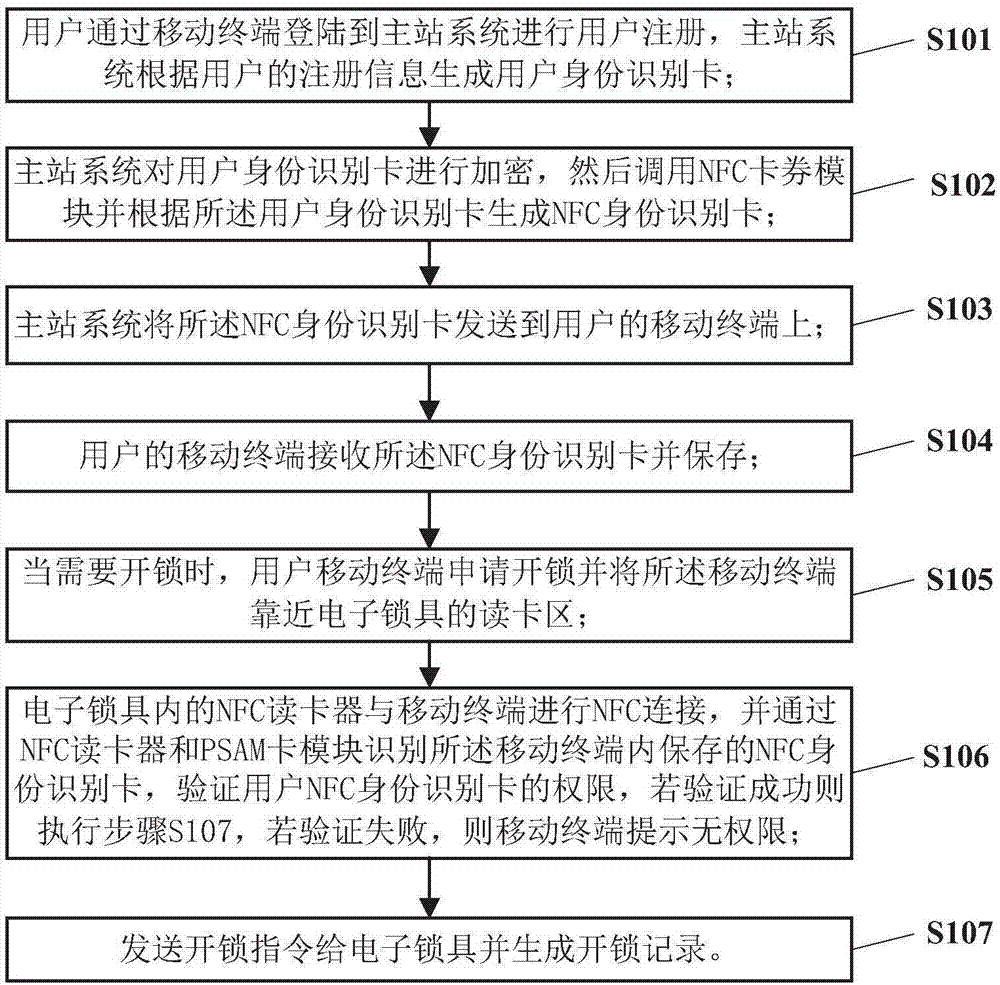
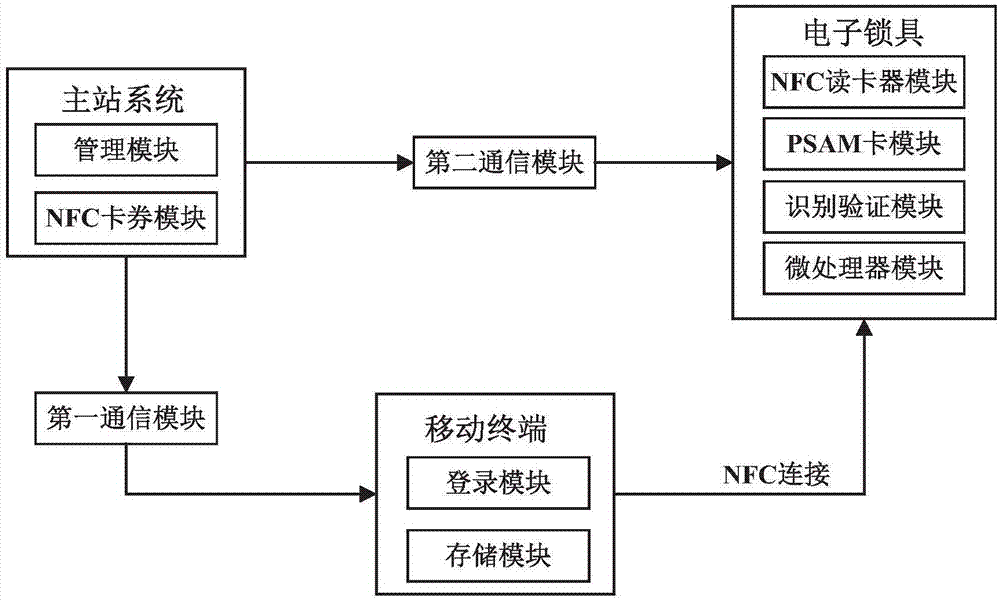
InactiveCN107248212AEasy to operateUnlocking does not affectIndividual entry/exit registersGeneral Packet Radio ServiceMaster station
The invention provides an intelligent lock system based on NFC (Near Field Communication) and an unlocking method for the intelligent lock system. The intelligent lock system comprises a main station system, a mobile terminal and an electronic lock. The unlocking method comprises the following steps: logging in the main station system for registering by a user; generating a user identity identification card according to registration information of the user by the master station system; calling an NFC card coupon module and generating an NFC identity identification card according to the user identity identification card; transmitting the NFC identity identification card to the mobile terminal of the user by the main station system; receiving the NFC identity identification card and saving the NFC identity identification card by the mobile terminal of the user; during unlocking, applying to unlock by the mobile terminal of the user and enabling the mobile terminal to be close to a card reading area of the electronic lock; carrying out NFC connection on an NFC card reader in the electronic lock and the mobile terminal; identifying the NFC identity identification card saved in the mobile terminal by the NFC card reader and a PSAM (Purchase Secure Access Module) card module; verifying the permission of the NFC identity identification card of the user; and if verification is successful, transmitting an unlocking instruction to the electronic lock and generating unlocking records. The intelligent lock system based on the NFC and the unlocking method for the intelligent lock system, provided by the invention, do not depend on a GPRS (General Packet Radio Service) network and are simple in operation and high in safety performance.
Owner:深圳消费物联科技有限公司
Compound multifunctional IC card reader-writer
InactiveCN102402704AFriendly human-computer interfaceImplement data storageCo-operative working arrangementsData memorySecure access module
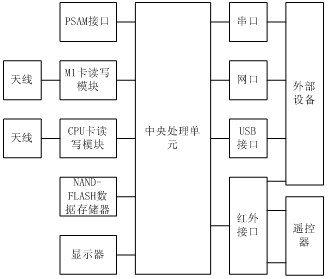
The invention discloses a compound multifunctional IC card reader-writer, which comprises a central processing unit and a data storage device, a display, a communication interface group, one or more PSAM (Pilot Symbol Assisted Modulation) interfaces electrically connected therewith, as well as one or more card reading-writing modules. The PSAM interface is used for placing the PSAM card or SAM (Secure Access Module) card. The card reading-writing module is used for reading and writing M1 card and CPU card. The communication interface group comprises one or more serial ports, one or more net ports, one or more USB (Universal Serial Bus) interfaces as well as one or more infrared interfaces. The communication interface group is used for realizing the connection between the central processing unit and the external equipment. The compound multifunctional IC card reader-writer provided by the invention allows the CPU card compatible with the M1 card, which not only has the function of reading card but has the functions of card issuing, recharging and consuming under offline situation. With the communication interfaces of multiple forms, the invention can be connected to different external equipments and realize the data exchange with external equipment and has the advantage of high security.
Owner:四川久远新方向智能科技有限公司
PSAM (Purchase Secure Access Module) and management method and system thereof as well as vehicle charge management method and system
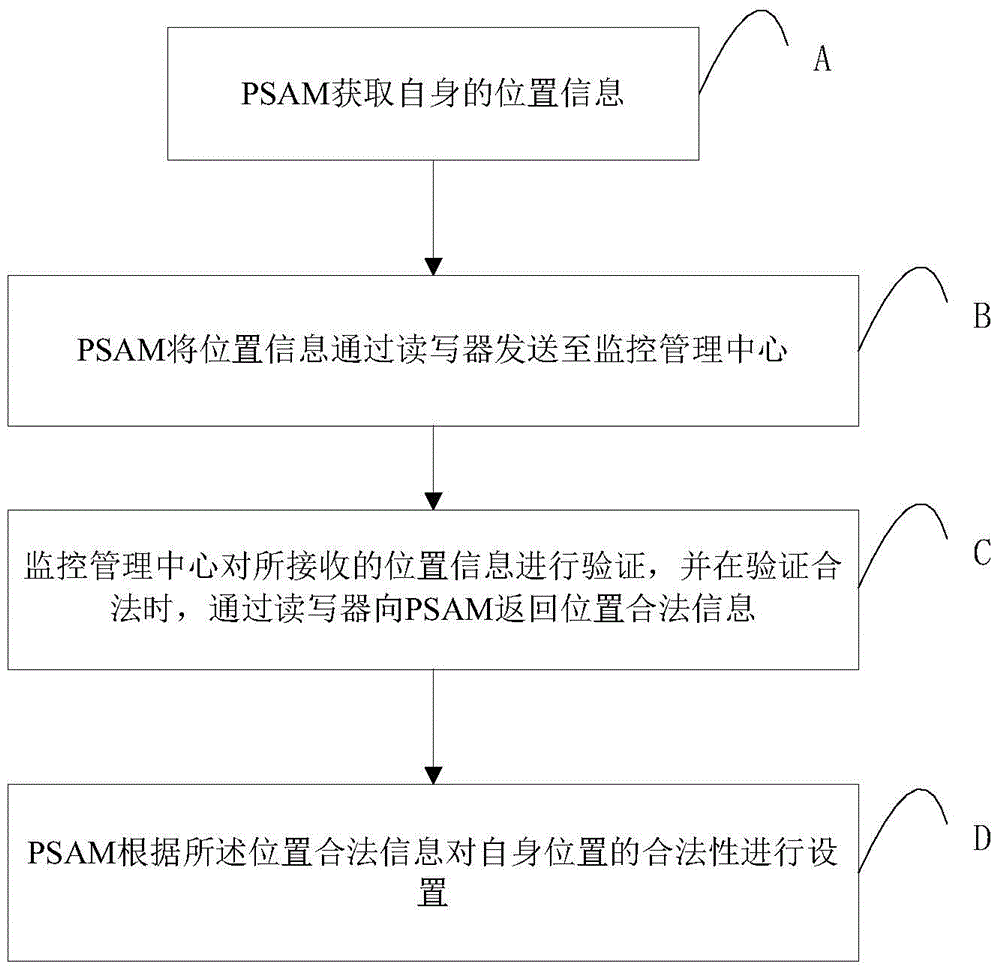
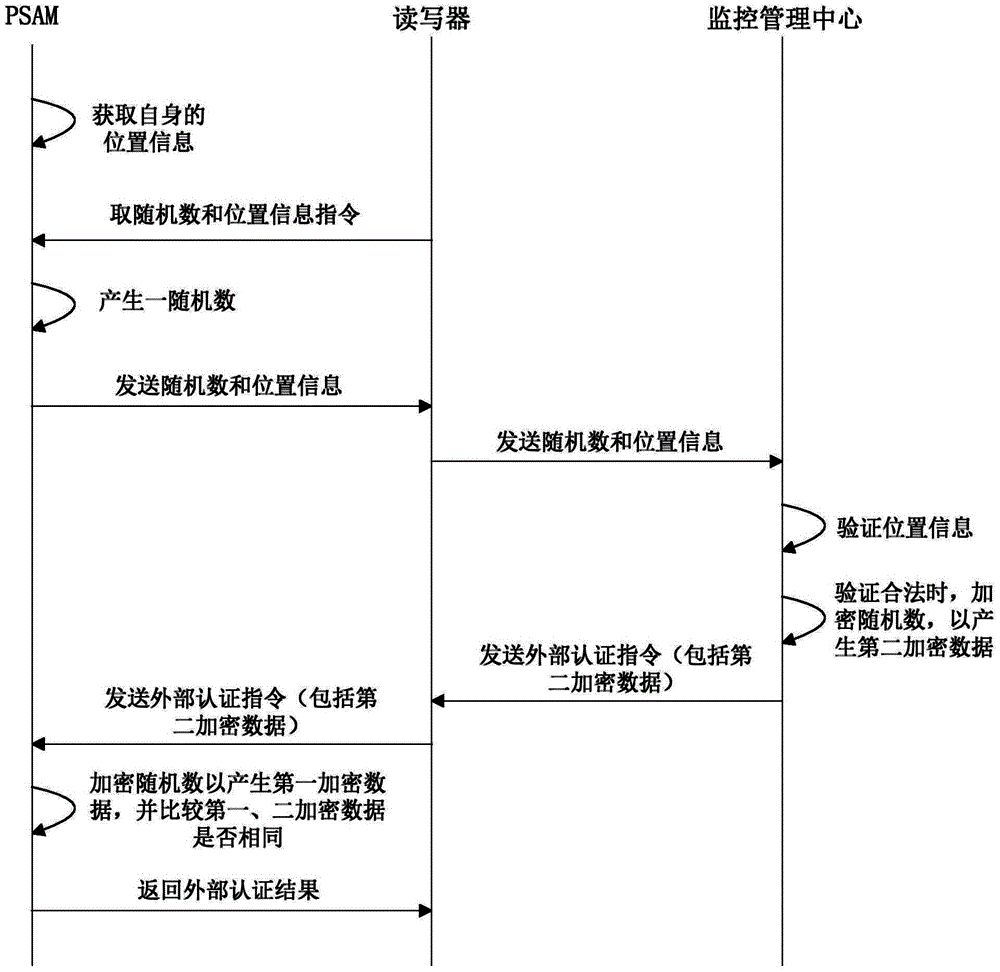
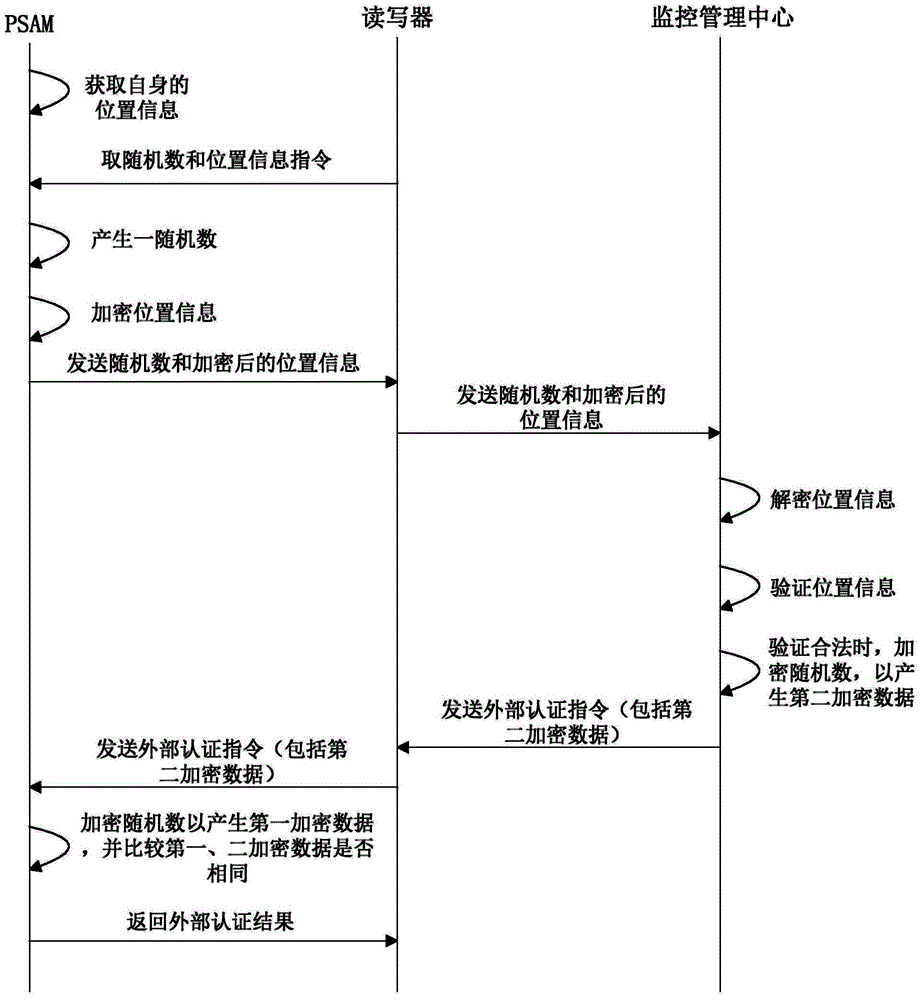
InactiveCN104574535ARestricted locationAvoid diversionTicket-issuing apparatusSecure access moduleReader writer
The invention discloses a PSAM (Purchase Secure Access Module) and a management method and system thereof as well as a vehicle charge management method and system. The PSAM management method comprises the following steps: obtaining position information of a PSAM by the PSAM; sending the position information to a monitor management center through a reader-writer unit by the PSAM; verifying the received position information by the monitoring management center, and returning legal position information to the PSAM through the reader-writer unit when the verification is legal; setting the legality of the position of the PSAM according to the legal position information by the PSAM. By implementing the technical scheme of the PSAM management method, the operating position of the PSAM is limited by the monitoring management center, so that an attacker is prevented from transferring the PSAM and matched programs to other places for use and the potential safety hazards are eliminated.
Owner:SHENZHEN GENVICT TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com