Concurrent queue access control method and system based on task eavesdropping
An access control and queue technology, applied in the access control field of concurrent queues, can solve problems such as performance reduction and high overhead, and achieve the effect of good performance and good scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
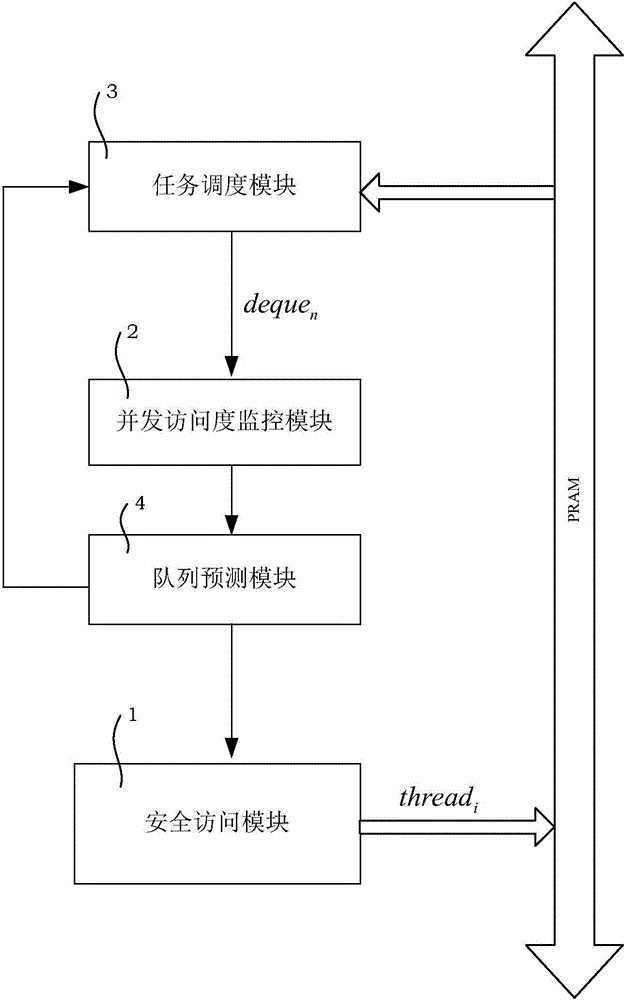
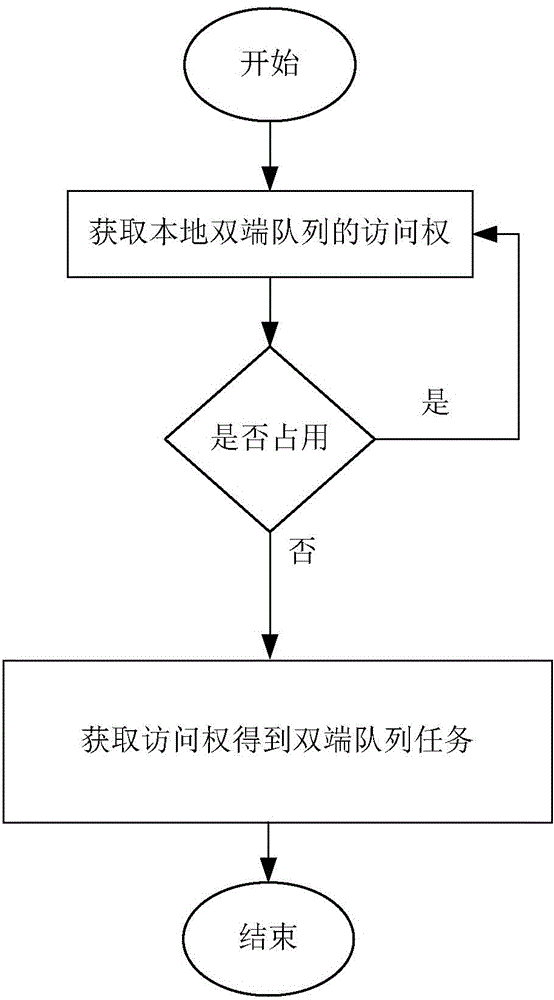
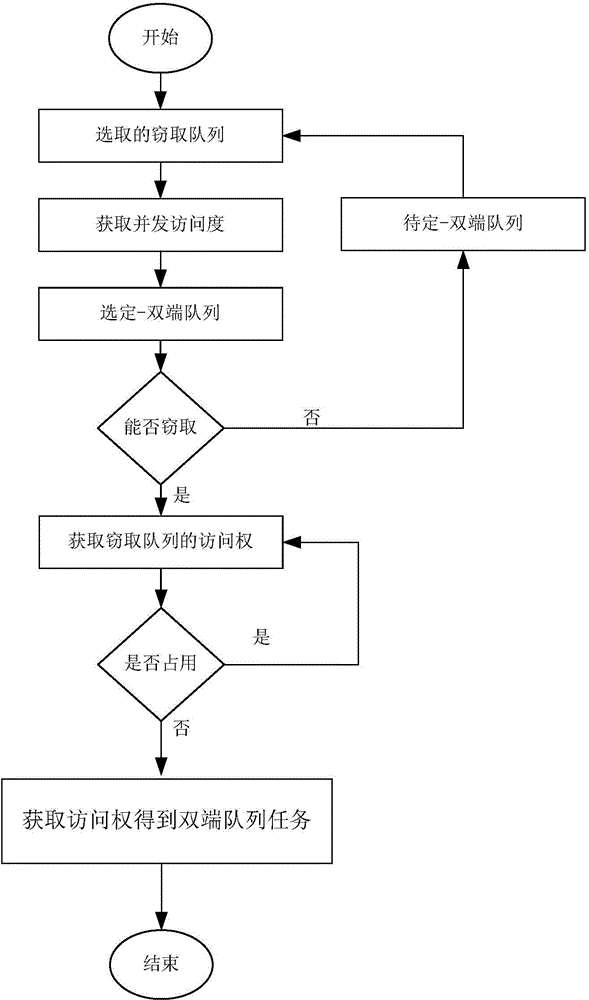
Image
Examples
Embodiment 1
[0063] By applying the access control method of the concurrent queue access control strategy PDACS in the parallel platform Cilk of shared memory multiprocessors, and making a comparative experiment with the original Cilk parallel platform, the experimental test set adopts the standard test set of MIT Cilk, and the experimental environment platform is a An Inspur server with an intel xeon phi 7110P series processor has a total of 61 processor cores. After enabling CPU hyperthreading, it has a total of 244 logical processor cores, which can support concurrent execution of 244 physical threads. Server operation The system is RedHat Linux 6.3.
[0064]Use the MIT Cilk test program to test the execution time of the test program on the Cilk parallel platform and the PDACS parallel platform under 244 threads respectively. The compiler used when compiling the test program is For C++ Composer XE 2013 SP1, the compile-time optimization level option is -O2. The test results show that t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com