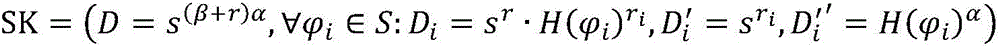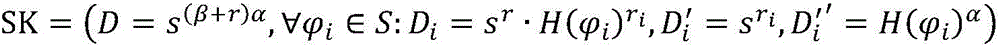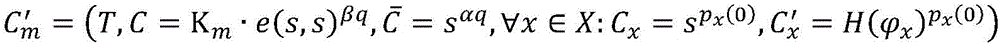Patents
Literature
53results about How to "Improve Access Control Efficiency" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
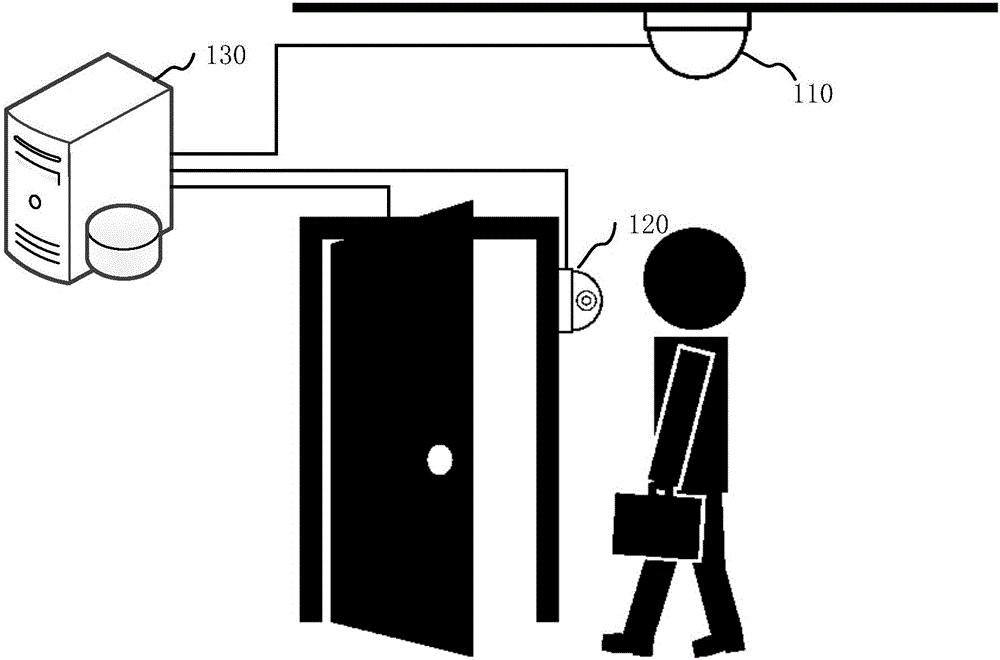
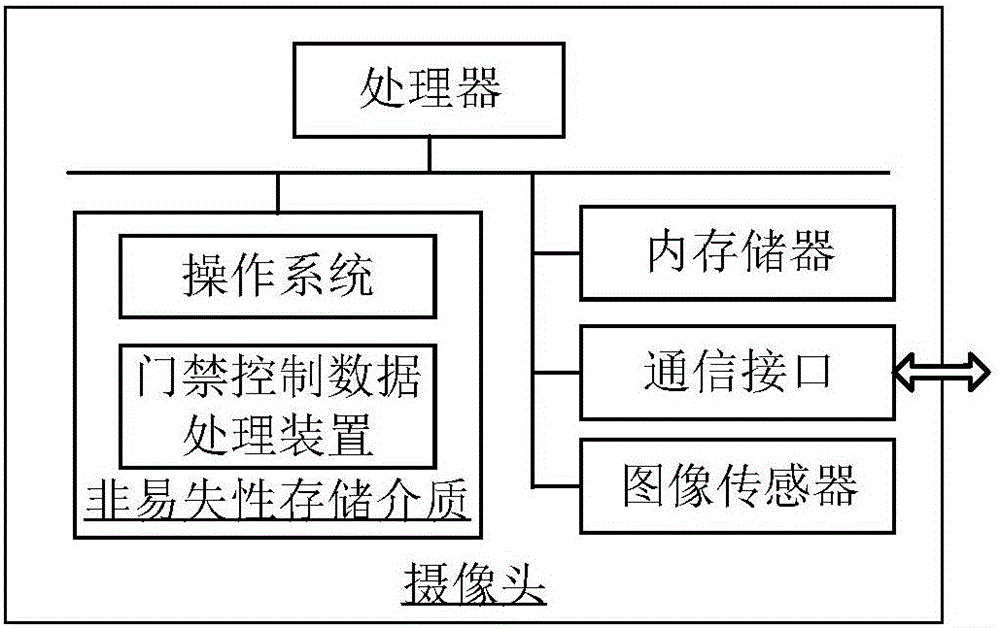
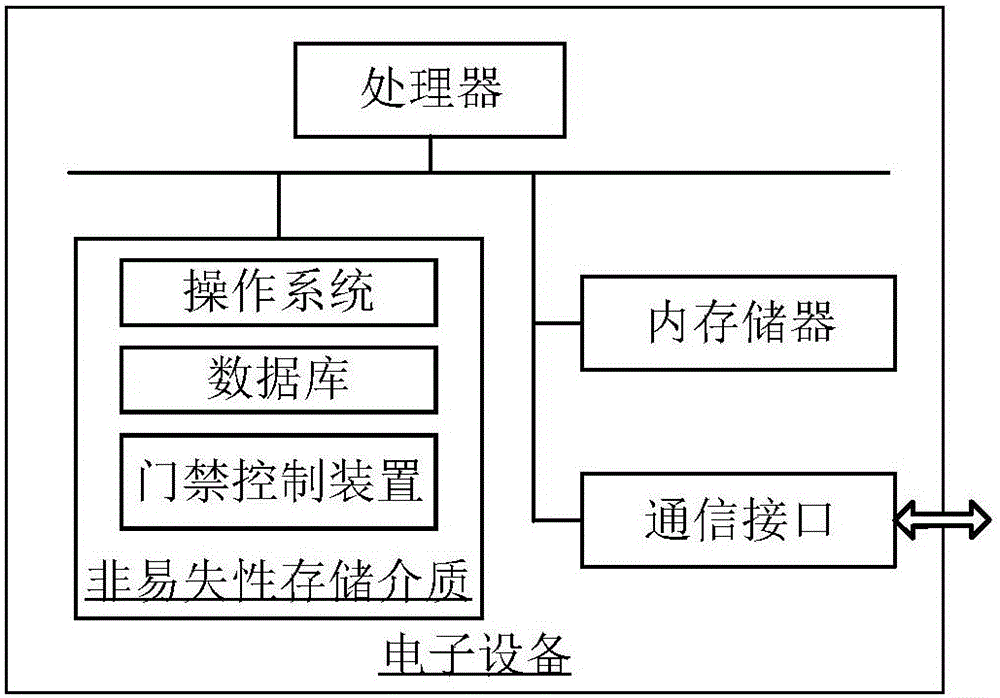
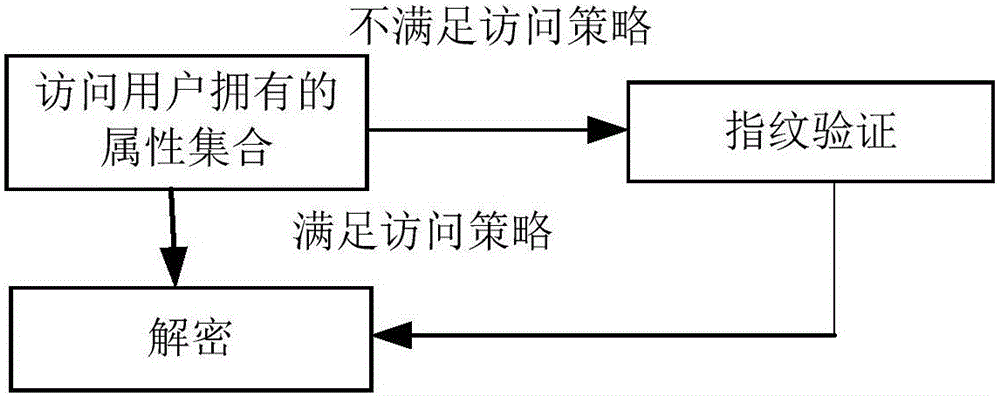
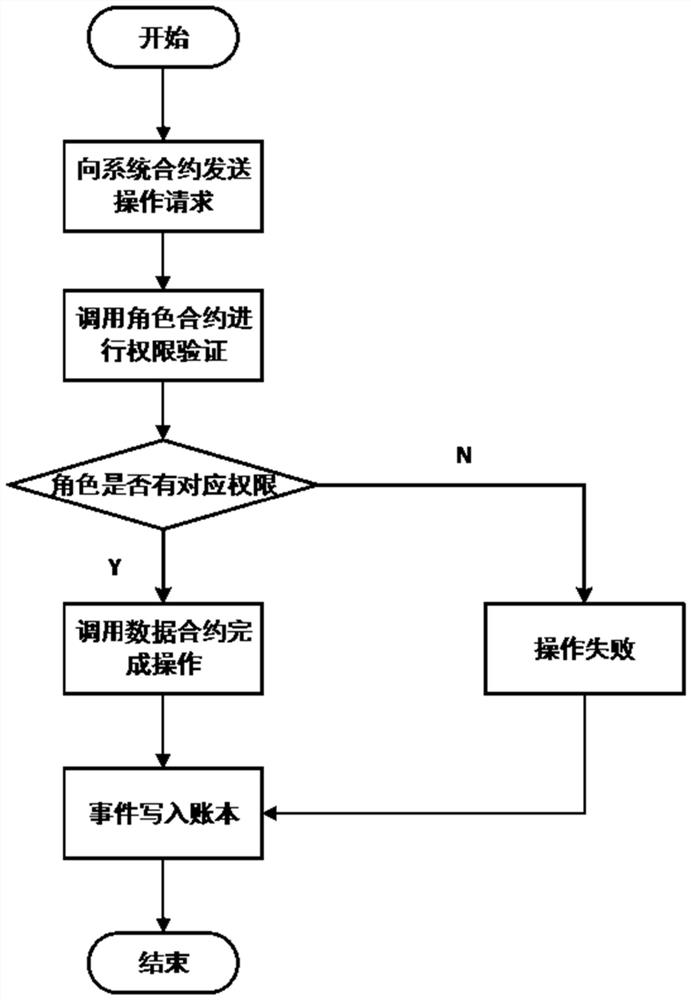
Method and device for processing access control data, method and device for access control
ActiveCN105913528AReduce time consumptionImprove Access Control EfficiencyIndividual entry/exit registersControl dataComputer science
The invention relates to a method and a device for processing access control data, a method and a device for access control. The method for processing access control data comprises the following steps: acquiring an overlook image sequence; acquiring personnel activity information according to the overlook image sequence; detecting the personnel activity information fit for the entry intention according to the personnel activity information; sending the personnel position information to an access control device, thereby recognizing face by the access control device according to the personnel position information and outputting an opening instruction when the user identification of the recognized face has the opening right. According to the method and the device for processing access control data, the method and the device for access control provided by the invention, the time consumption for waiting the personnel for actively coordinating for performing face recognition is reduced and the access control efficiency is increased.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
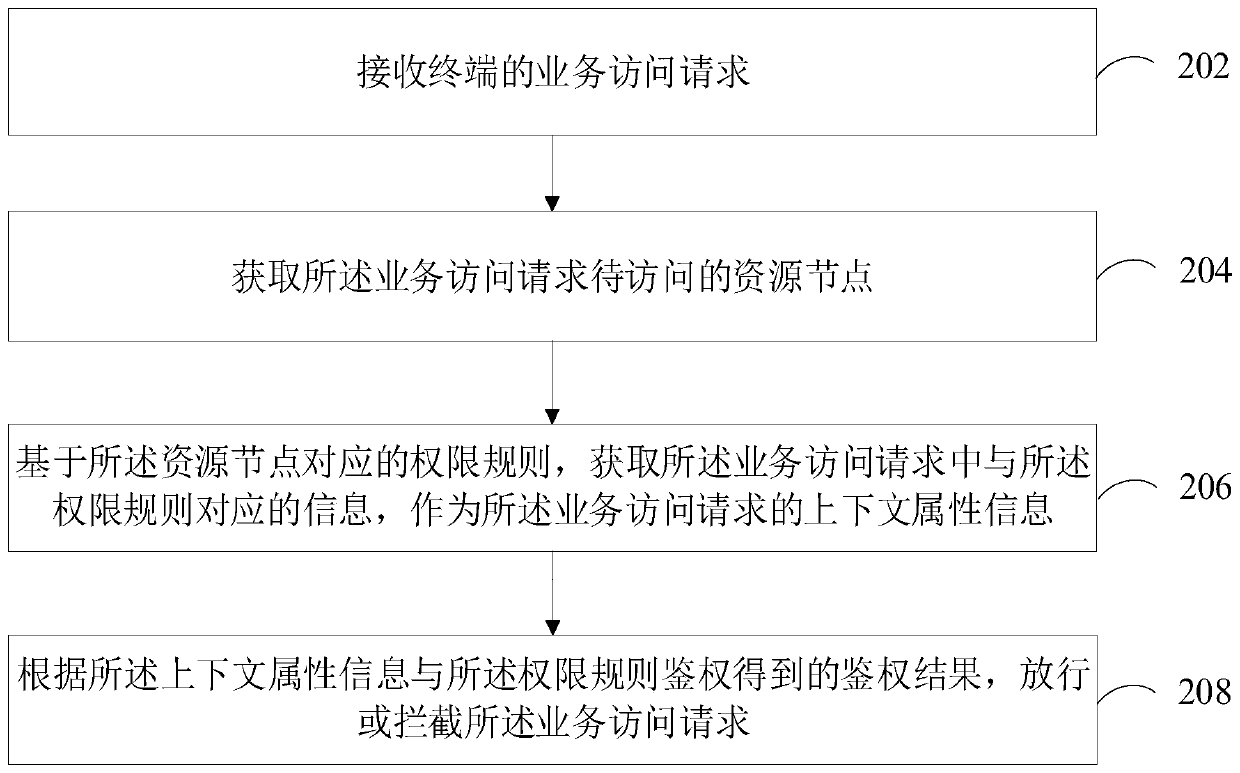
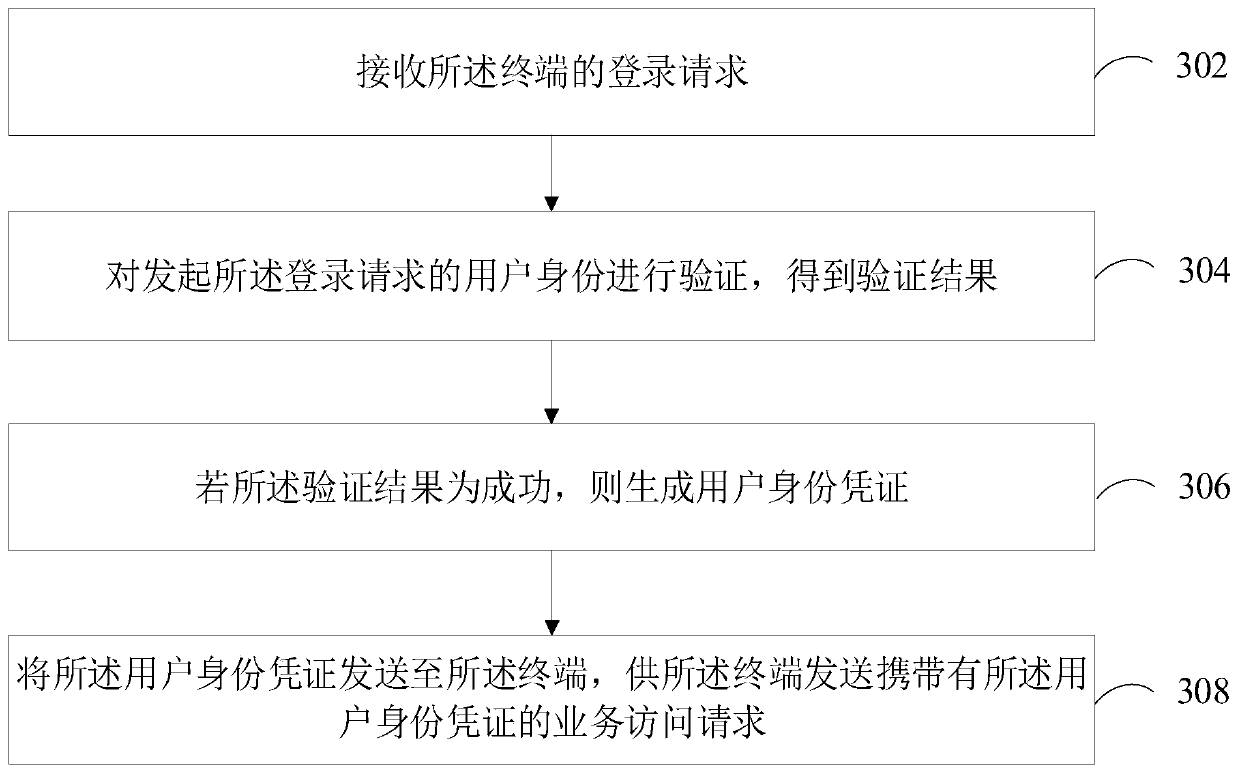
Access control method and device, computer equipment and storage medium
ActiveCN111488598AImprove securityImprove Access Control EfficiencyDigital data protectionWeb data queryingEngineeringAuthentication
The invention relates to an access control method and device, computer equipment and a storage medium. The method comprises the following steps: receiving a service access request of a terminal; obtaining a to-be-accessed resource node of the service access request; based on an authority rule corresponding to the resource node, obtaining information corresponding to the authority rule in the service access request as context attribute information of the service access request; and releasing or intercepting the service access request according to an authentication result obtained by authenticating the context attribute information and the authority rule. The security of access control can be effectively improved, and the efficiency of access control is further improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
System and method for controlling untrusted resource transmission in Internet of vehicles
The invention requests to protect a system and method for controlling untrusted resource transmission in Internet of vehicles. The method comprises the following steps: designing an access control strategy and a node trust value calculation method for nodes of a resource output vehicle, limiting fixed attributes and dynamic attributes of the resource output vehicle, and dynamically generating a fine-grained access control strategy according to the traveling track of the vehicle to ensure that the access control strategy has better extensibility and flexibility. Thereby, the anonymous directional transmission of messages can be achieved, the waste of resources can be reduced, and the identity privacy of communication vehicles can be effectively protected; the calculation of node trust values can guarantee the trust degree of resource communicators and meet the security and privacy requirements of security related messages in Internet of vehicles; and malicious nodes can be effectively identified, and the injection of malicious resources and the transmission of untrusted resources can be prevented. The method disclosed by the invention can be widely applied to the related fields of mobile Internet, wireless sensor network and the like.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Parking lot control method and system, and computer readable storage medium
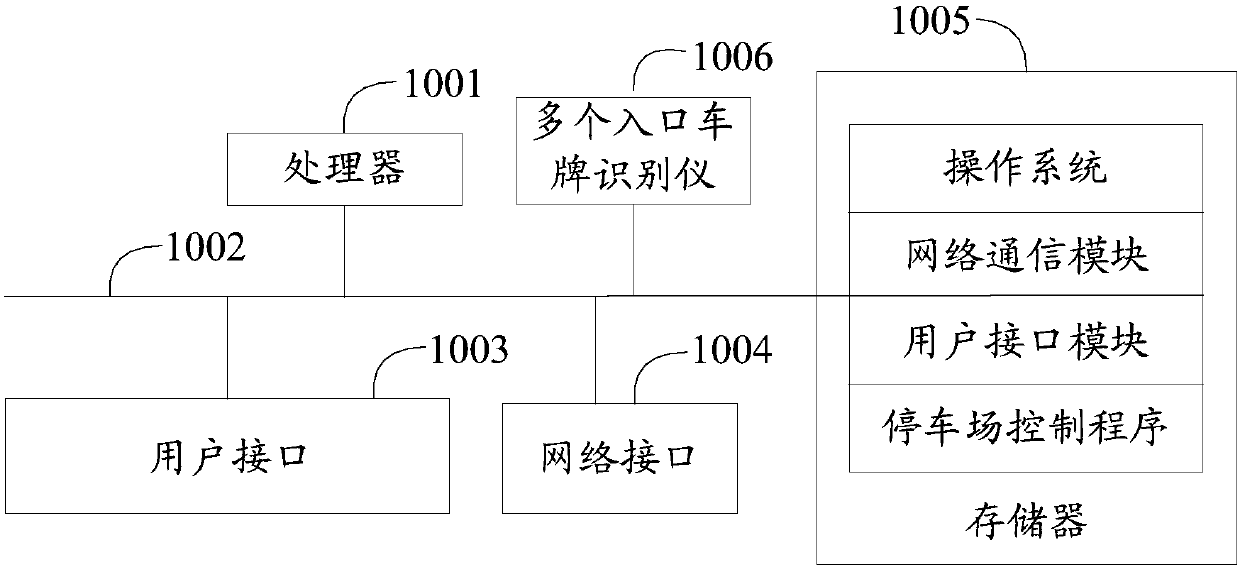
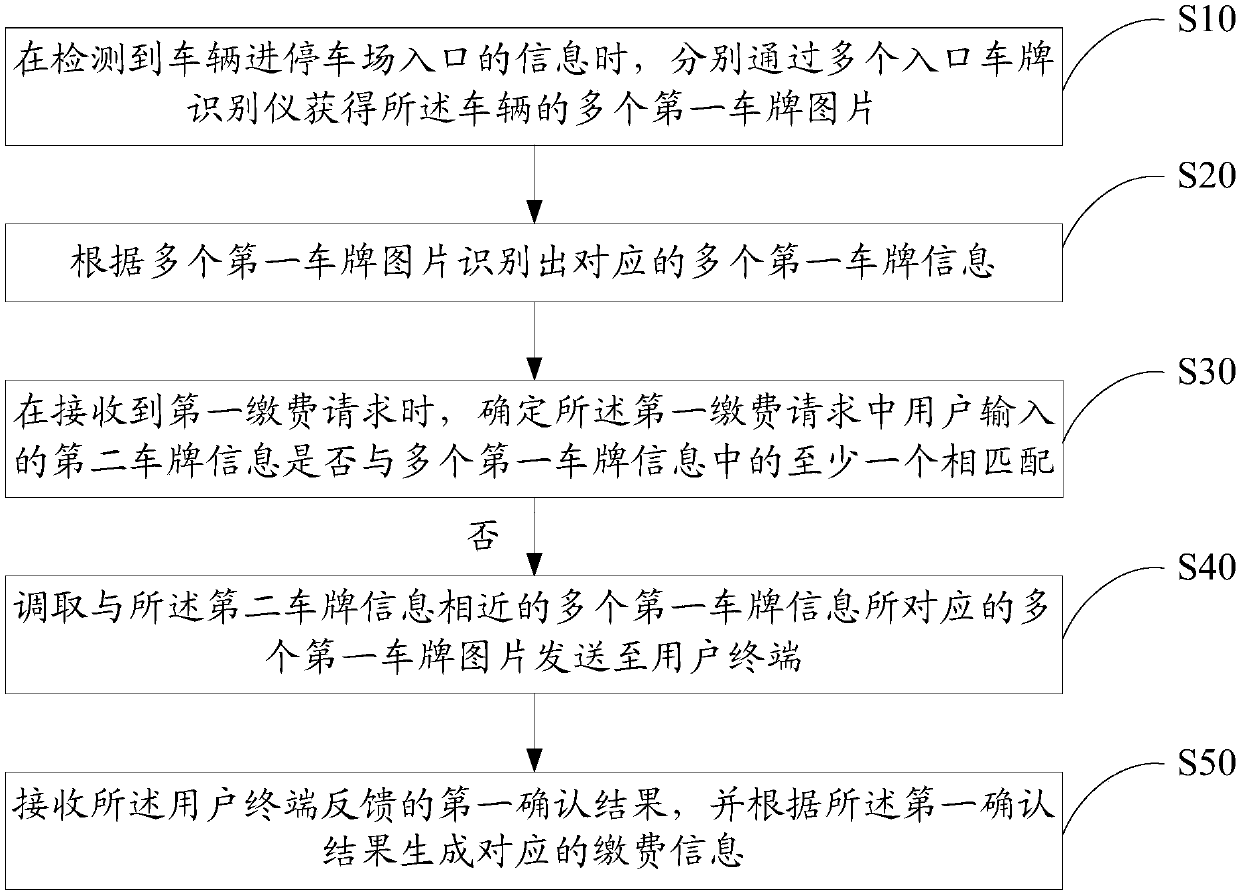
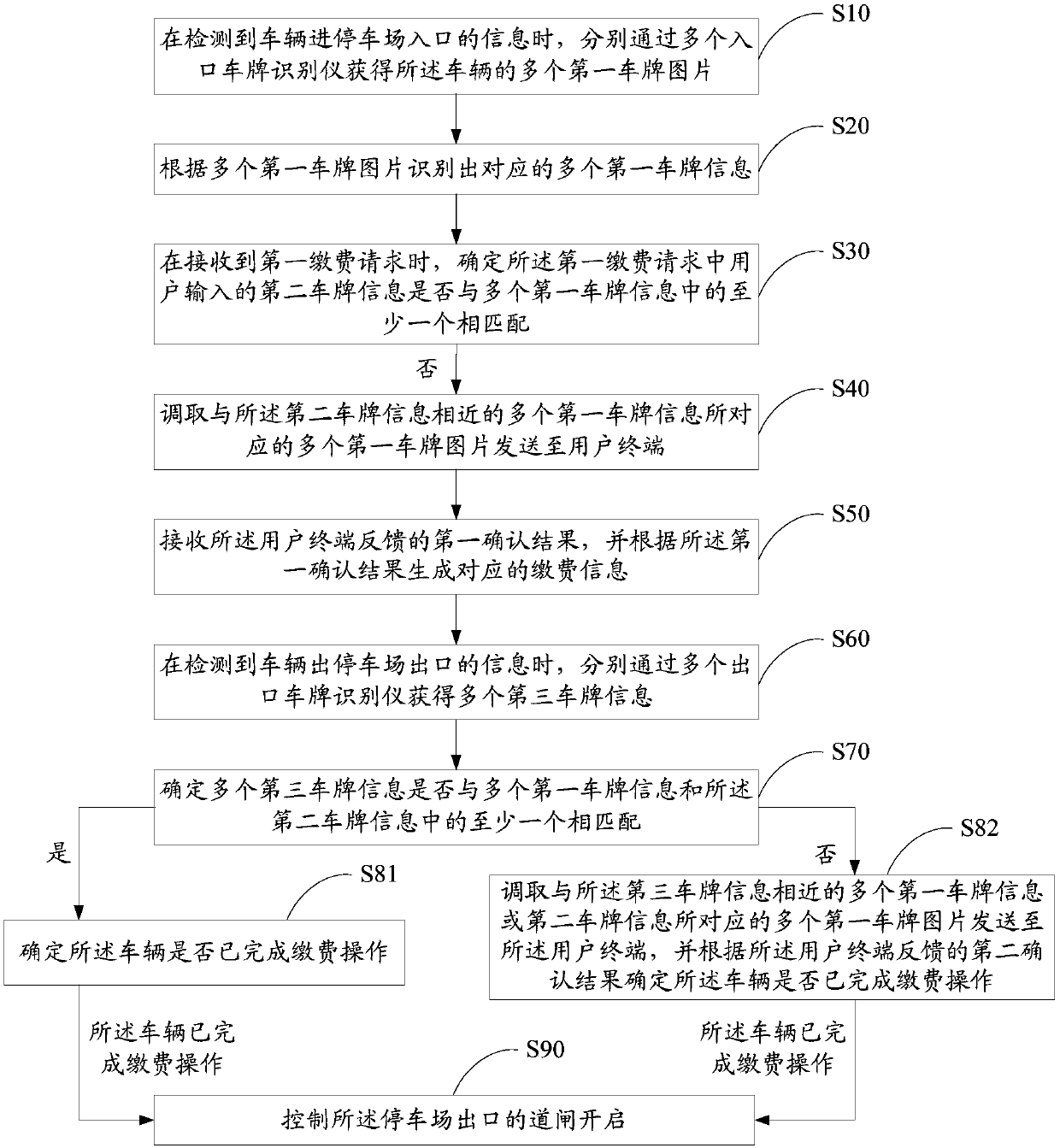
ActiveCN107909661AAvoid the situation where the license plate picture cannot be obtainedImprove match rateTicket-issuing apparatusCharacter and pattern recognitionPaymentControl system
The invention discloses a parking lot control method. The method is applied to a parking lot control system including a plurality of entrance license plate identifiers. The method includes steps of: obtaining a plurality of first license plate images and recognizing a plurality of pieces of corresponding first license plate information through the plurality of entrance license plate identifiers when detecting the information of the entrance to the parking lot of the vehicle; when a first payment request is received, determining whether the second license plate information in the first paymentrequest matches at least one of the plurality of pieces of first license plate information; and if not, calling and sending the plurality of license plate images corresponding to the plurality of pieces of first license plate information similar with the second license plate information to a user terminal, and generating a piece of corresponding payment information according to a first confirmation result fed back by the user terminal. The invention also discloses a parking lot control system and a computer readable storage medium. When the license plate recognition is wrong, the payment information can be normally generated by sending the license plate picture for confirmation of the user, thereby improving the parking lot access control efficiency.
Owner:XIAN IRAIN IOT TECH SERVICES CO LTD
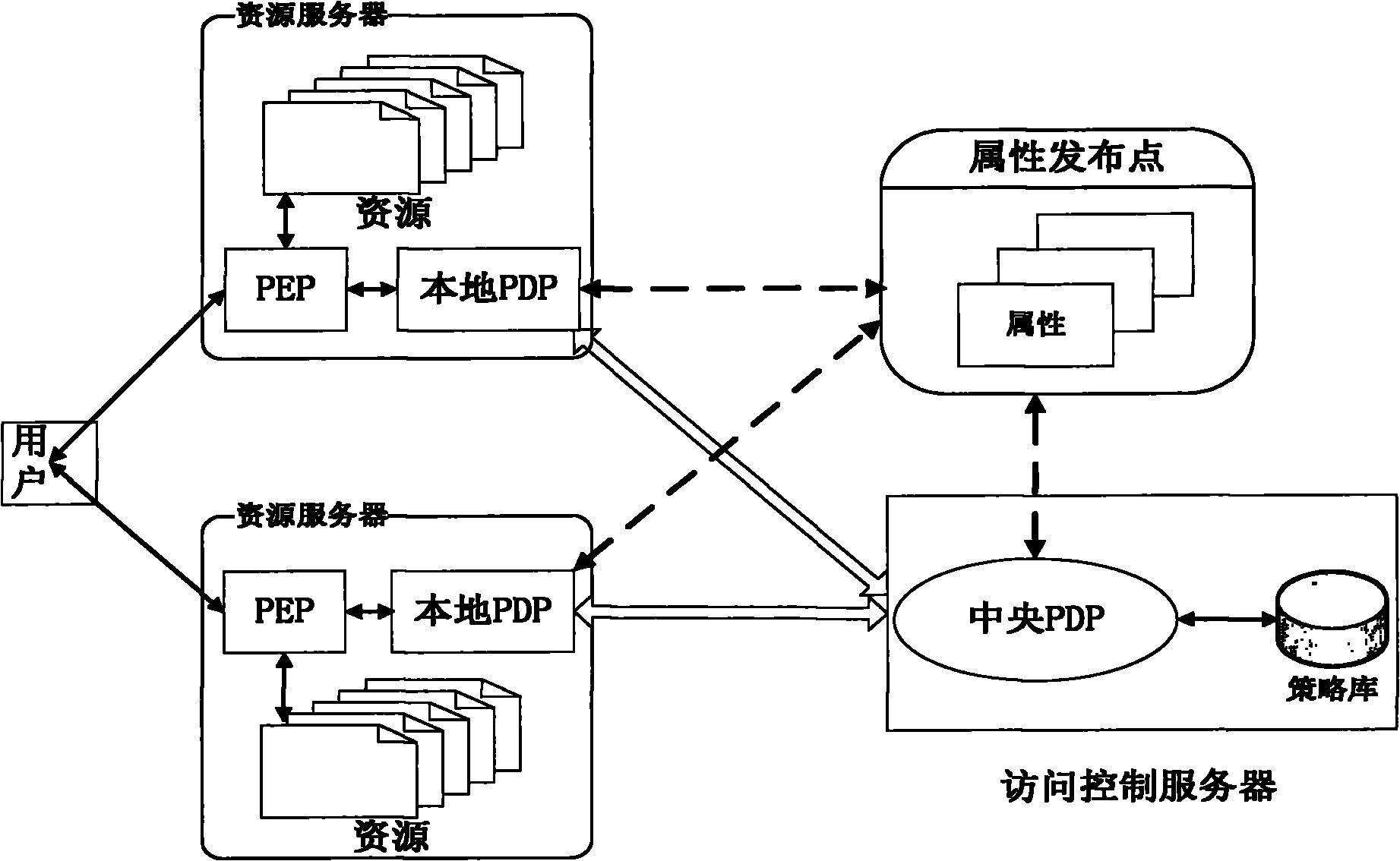
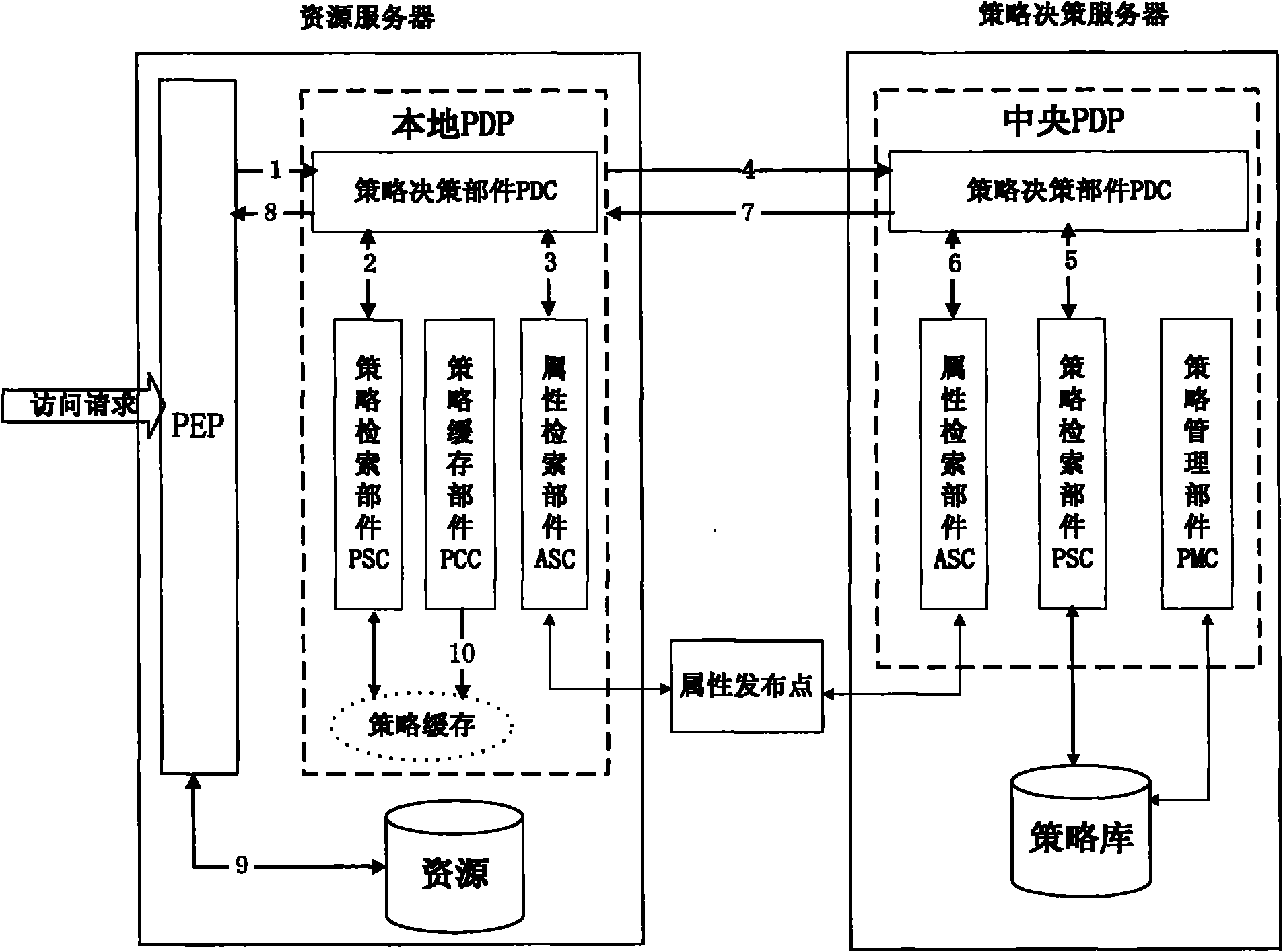
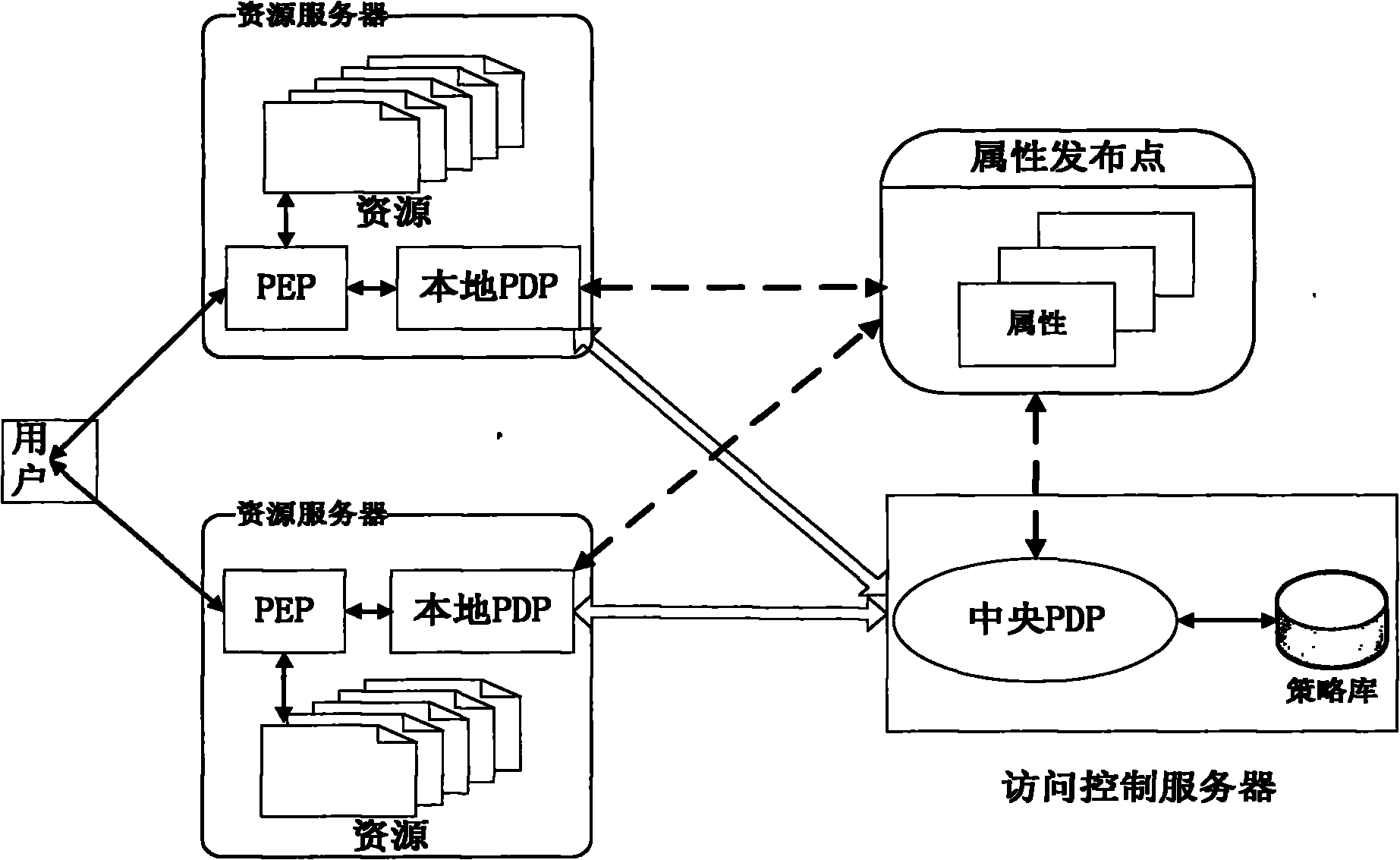
Two-level policy decision-based access control method and system
ActiveCN102006297AGuaranteed versatilityReduce the burden onTransmissionPolicy decisionAccess control matrix
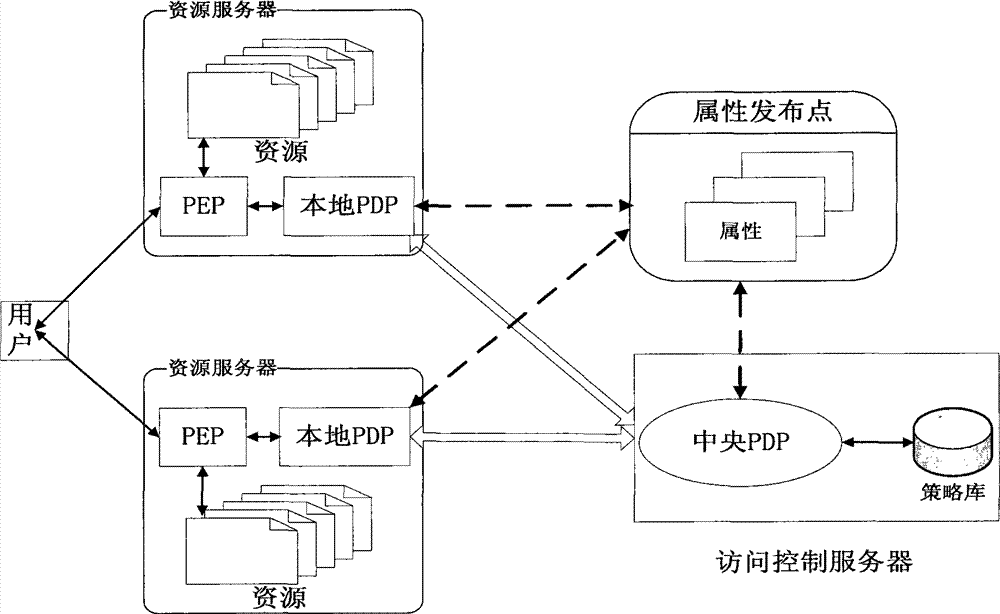
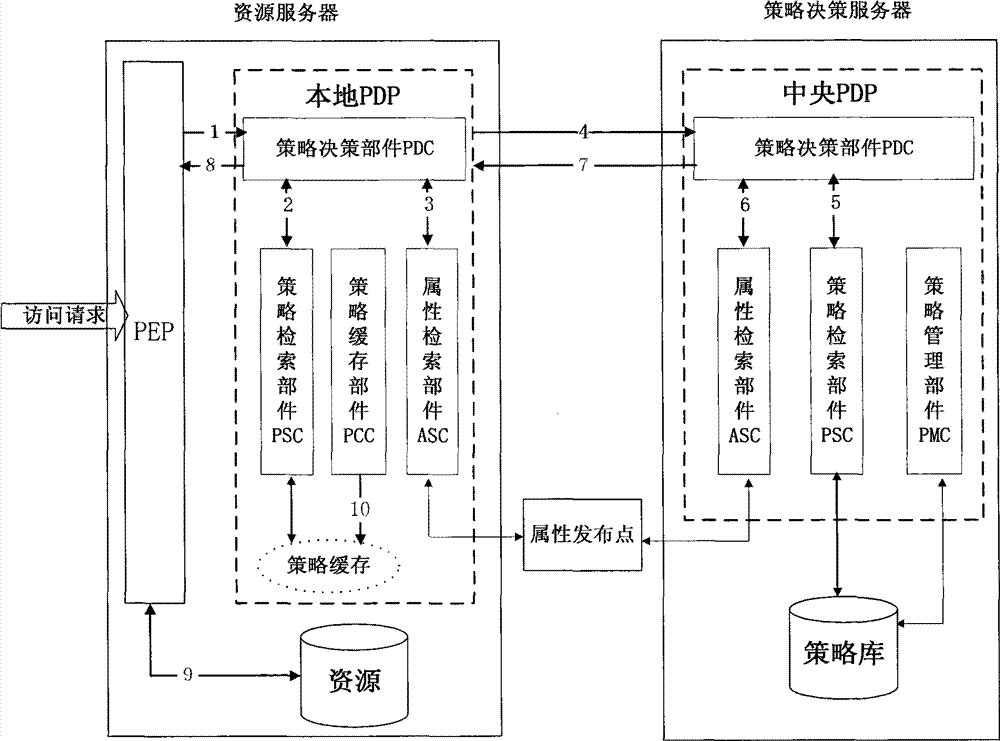
The invention discloses a two-level policy decision-based access control method and a two-level policy decision-based access control system, and belongs to the field of access control in information safety. In the method, a local policy decision point (PDP) is deployed at a policy enforcement point (PEP) end, and the local PDP makes a decision for an access request according to a local policy cache, and if the local PDP cannot determine that the decision is a deterministic decision, a central PDP finally finishes the decision according to a system policy library. The system comprises a policydecision server, an attribute publishing point and a plurality of resource servers, wherein a policy enforcement point (PEP) and a local policy decision point (PDP) are deployed on each resource server; and a central policy decision point (PDP) is deployed on the policy decision server. The invention has a good dynamically adjusted elastic system framework, fully utilizes the computing resources of the PEP end, lightens the burden of the central PDP, reduces the network transmission overhead and effectively improves the access control efficiency at extremely low policy update cost.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
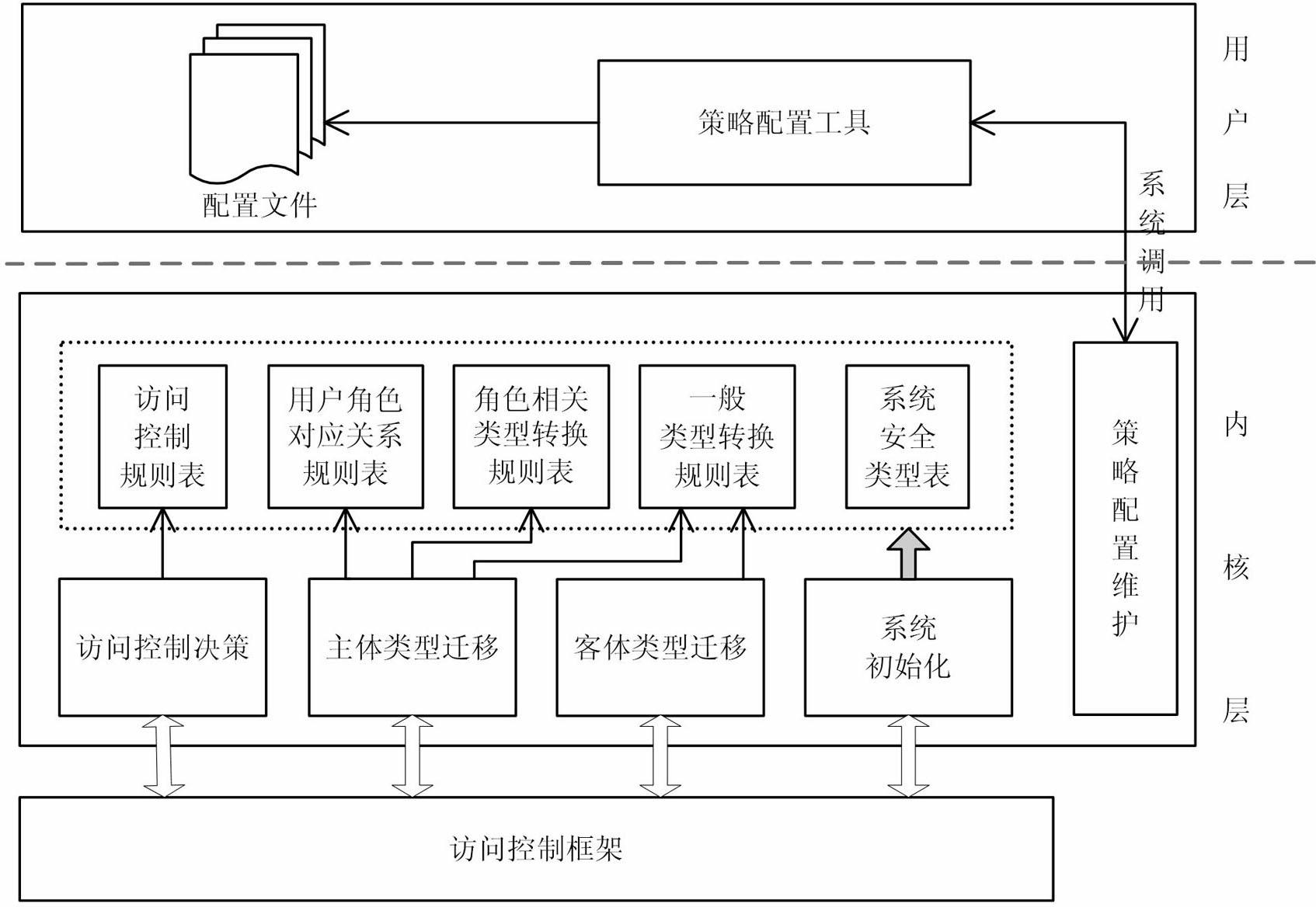
Loose coupling role authorized-type implementation access control method and system thereof
InactiveCN102222191AChange execution flowImplement featuresUnauthorized memory use protectionDigital data protectionOperational systemSecurity domain
The invention discloses a loose coupling role authorized-type implementation access control method and a system thereof. The method comprises the following steps of: adding a user role incidence relation based on a type implementation access control method; adding a related process type transformation rule definition relating to a user role and a corresponding type transformation decision mechanism; when a system process type is transformed, according to the process type transformation rule, judging whether to perform role related type transformation according to a current role of the user to change a user process execution flow; and entering a specific security domain of the user role. The system comprises a type implementation access control policy module, a policy security configuration module and a policy rule configuration module, wherein the type implementation access control policy module is operated in the kernel of an operating system; the policy security configuration module is operated on the user layer of the operating system; and the policy rule configuration module is positioned in a file system. The method and the system have the advantages of reducing the influence of user role configuration change on a type implementation rule system, reducing the security configuration difficulties, facilitating flexible configuration according to actual service conditions.
Owner:NAT UNIV OF DEFENSE TECH
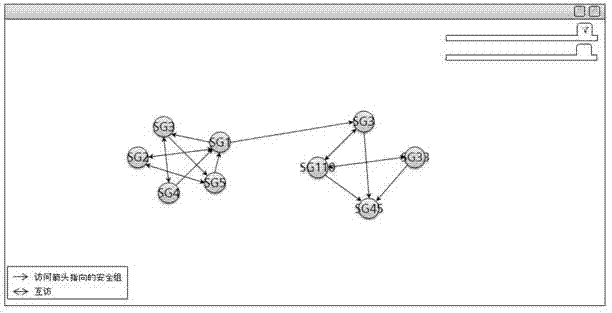
Access control method of network security group and security computer
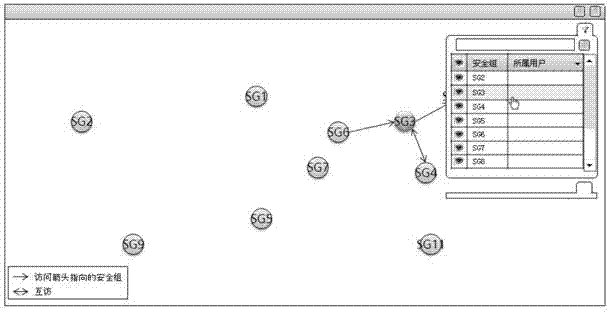
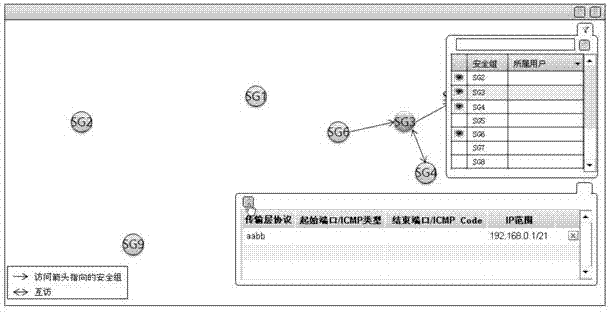
ActiveCN103164647AEfficient access to relationshipsImprove Access Control EfficiencyDigital data authenticationInteraction interfaceInformation security
The invention is applied to the field of information security, and provides an access control method and an access control device of a network security group. The access control method of the network security group comprises the steps of displaying all network security groups in a system in the same human-computer interaction interface; detecting mouse dragging operation of a user in the human-computer interaction interface; and building an access relationship of a network security group corresponding to an initial position of the mouse dragging operation, to a network security group corresponding to an end position of the mouse dragging operation. The access control method of the network security group can enable the user to being capable of rapidly, accurately and efficiently building access control relationships among the network security groups from the overall situation, and improves access control efficiency among the network security groups.
Owner:南京汇荣信息技术有限公司
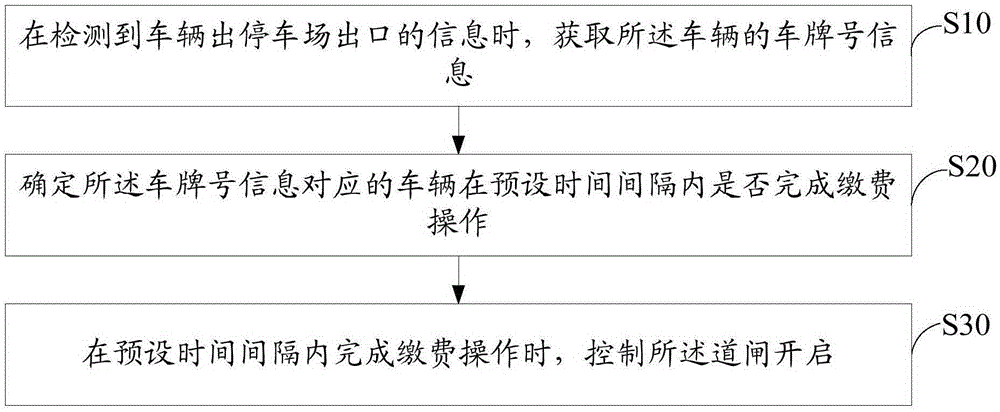
Parking lot control method and device
InactiveCN106558110AImprove control efficiencyImprove Access Control EfficiencyTicket-issuing apparatusReal-time computingLicense
The invention discloses a parking lot control method, and the method comprises the following steps: obtaining the license plate number information of a vehicle when the information that the vehicle leaves the parking lot from an exit is detected; determining whether the vehicle corresponding to the license plate number information completes the charging operation at preset time intervals or not; and controlling the gate to open when the charging operation is completed at the preset time intervals. The invention also discloses a parking lot control device. According to the invention, the user can carry out the payment in the parking lot in advance, does not need to carry out centralized payment at the exit of the parking lot, and improves the access control efficiency of the parking lot.
Owner:XIAN IRAIN IOT TECH SERVICES CO LTD
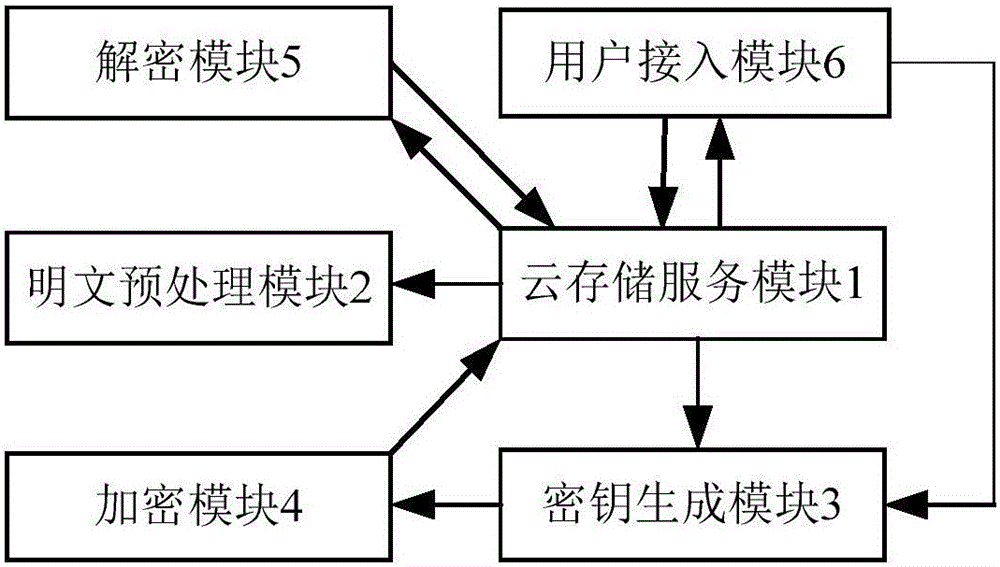
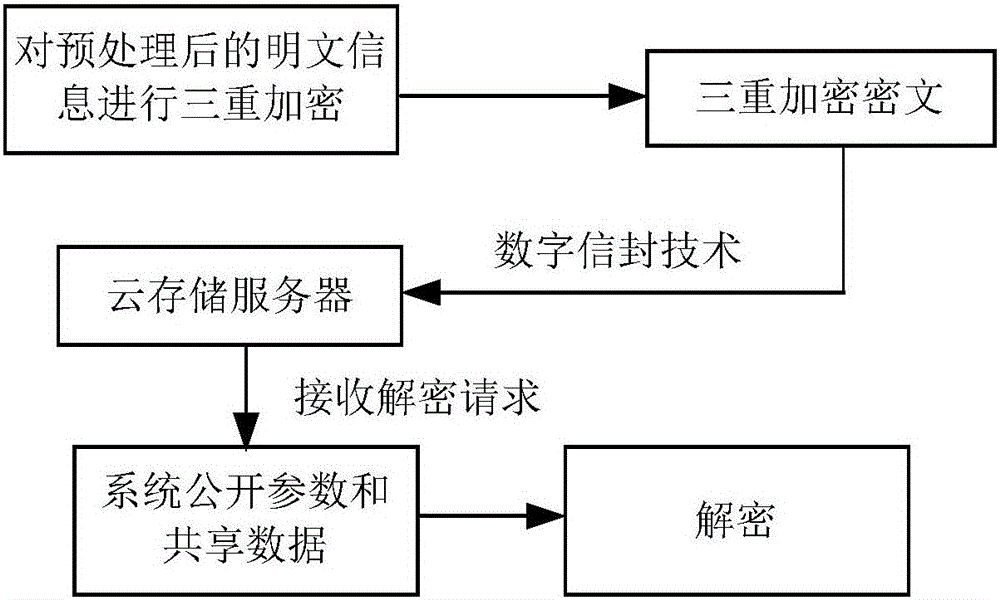
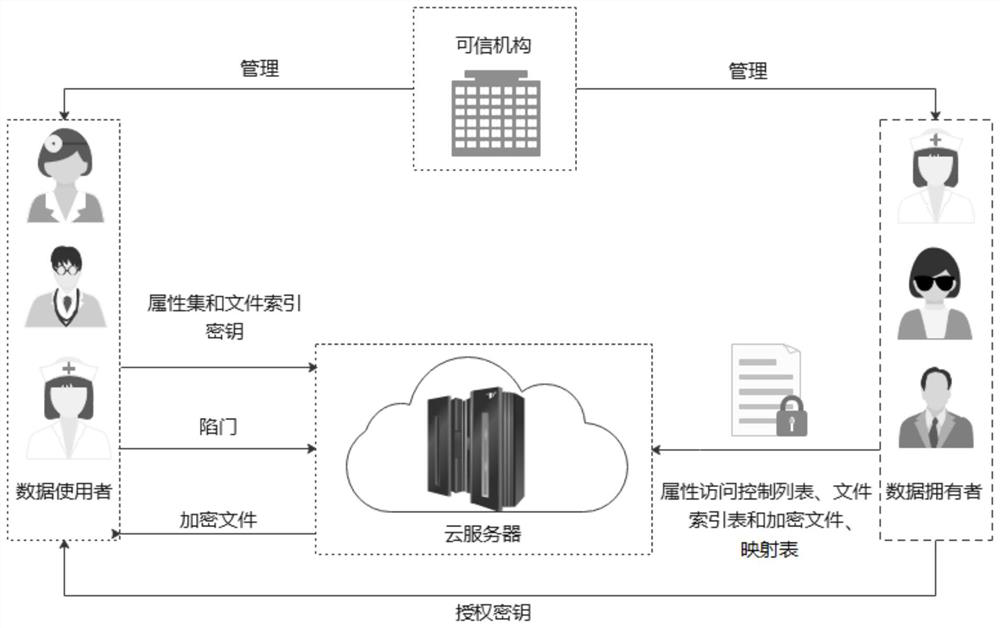
Cipher text access control system based on cloud computing platform
InactiveCN106209357ASave storage spaceImprove Access Control EfficiencyKey distribution for secure communicationHigh level techniquesPlaintextMultiplexing
The invention discloses a cipher text access control system based on a cloud computing platform. The system comprises a cloud storage service module, a plaintext preprocessing module, a secret key generation module, an encryption module, a decryption module and a user access module. A plaintext of a user owner client is encrypted in a triple manner to obtain a triple encrypted cipher text, the triple encrypted cipher text is packaged by utilizing a digital envelope technology and then stored in the cloud storage service module, and the corresponding decryption module is arranged. Fine access control can be realized, computing cost of encryption and decryption between a user owner and a user can be reduced effectively, the data confidentiality is ensured, and collusion-proof aggressivity and forward and backward safety are included; and the cipher text access control system is controlled in different levels, the efficiency of access control is improved, a code division multiplexing technology is used to code plaintext information, the cipher text storage space is reduced, and the total performance of the system is improved.
Owner:杨炳
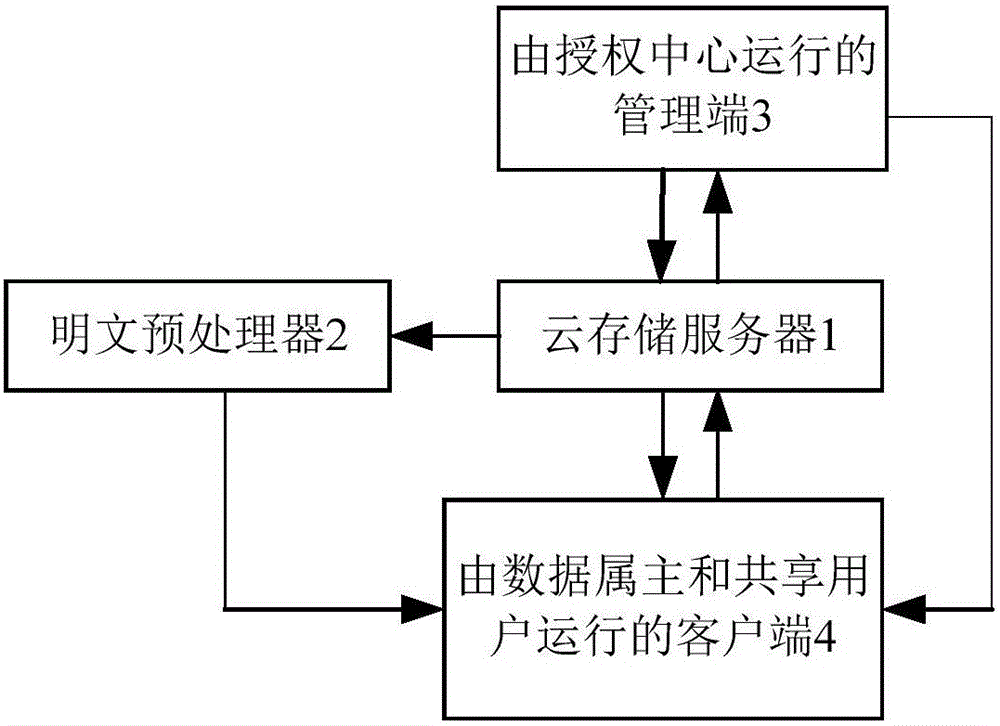
Encryption system supporting fine-grained access control
InactiveCN106101131AImprove Access Control EfficiencyReduce ciphertext storage spaceTransmissionPlaintextAccess structure
The invention discloses an encryption system supporting fine-grained access control. The encryption system comprises a cloud storage server, a plaintext preprocessor, a management end run by an authentication center and a client run by a data owner and a shared user. According to the encryption system, the computation cost for encryption and decryption of the data owner and the user can be effectively reduced, and the fine-grained access control is realized; the plaintext information after encoding is divided into different access levels according to an access structure tree, so that the efficiency for access control is improved, and furthermore, the plaintext information is encoded by utilizing a code division multiplexing technology, so that the ciphertext storage space is reduced and the overall performance of the system is improved.
Owner:杨炳
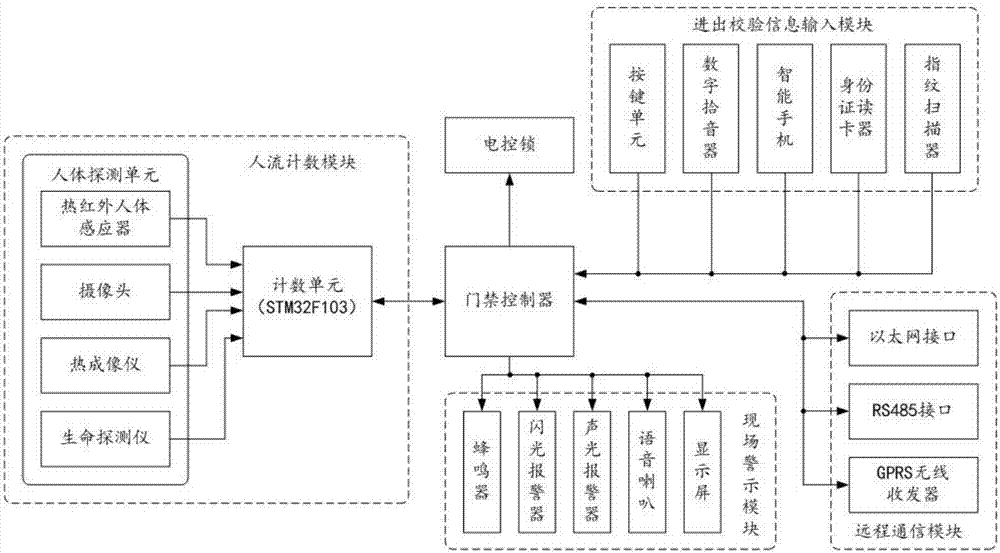
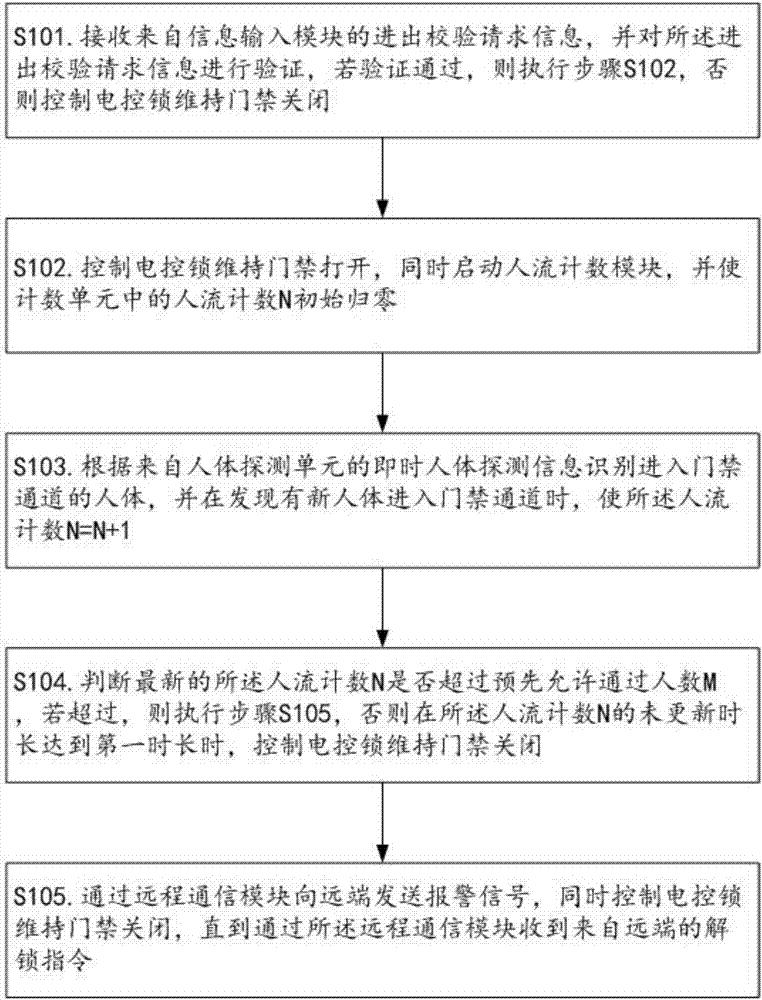
Access control system realizing people flow counting control and working method of access control system
PendingCN107341892AEliminate the situation of tailgating through the access control channelGuarantee property securityIndividual entry/exit registersMedia access controlSelf-service
The invention relates to the field of access control systems, and discloses an access control system realizing people flow counting control and a working method of the access control system. According to the access control system, a people flow counting module comprising a counting unit and a people detecting unit is arranged, people entering an access control passage can be recognized, the purpose of counting people flows is achieved, and accordingly, after the access control system is opened for a single time, only the people passing authentication can be allowed to pass through the access control passage; remote alarm can be triggered after excess people pass through the access control passage, the access control passage is blocked automatically, the system enters a management mode of site access control by a remote monitoring center, unauthorized people can be prevented from passing through the access control passage through following, accompanying security holes are eliminated, and property security of unmanned stores and self-service shops are ensured. Besides, the access control system can be used as a security access control system for the unmanned stores, the self-service shops, ticket exits and other places, and actual promotion and application are facilitated.
Owner:兰庆天
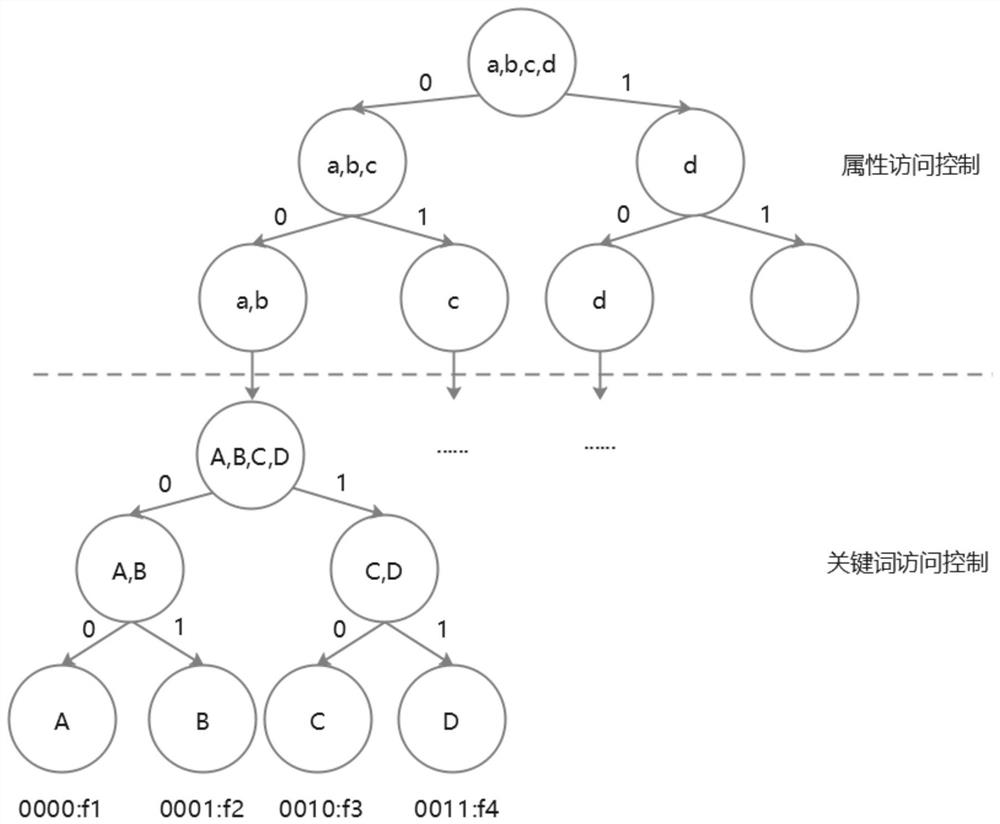
Multi-key searchable encryption method and system based on attribute access control structure
ActiveCN112380553AEfficient access control strategyImprove Access Control EfficiencyDigital data information retrievalDigital data protectionEngineeringCloud storage
The invention discloses a multi-key searchable encryption method and system based on an attribute access control structure, and the method comprises the steps: dividing an attribute set through employing a VBTree under the background of cloud storage, binding the attribute set with the access authority of a file, and effectively determining whether a user is a legal user or not and a file set which can be accessed by the user according to an attribute set submitted by the user. Huge expenditure for traversing all files of a data owner once when the user is verified to be the legal user or notis avoided; meanwhile, combined query of multiple keywords is achieved, so that a query result is more flexible and accurate; and the data owner does not need to generate an authorization key for eachauthorized user and each file which can be accessed by the authorized user, and only needs to generate an authorization key for each authorized user.
Owner:SOUTH CHINA UNIV OF TECH
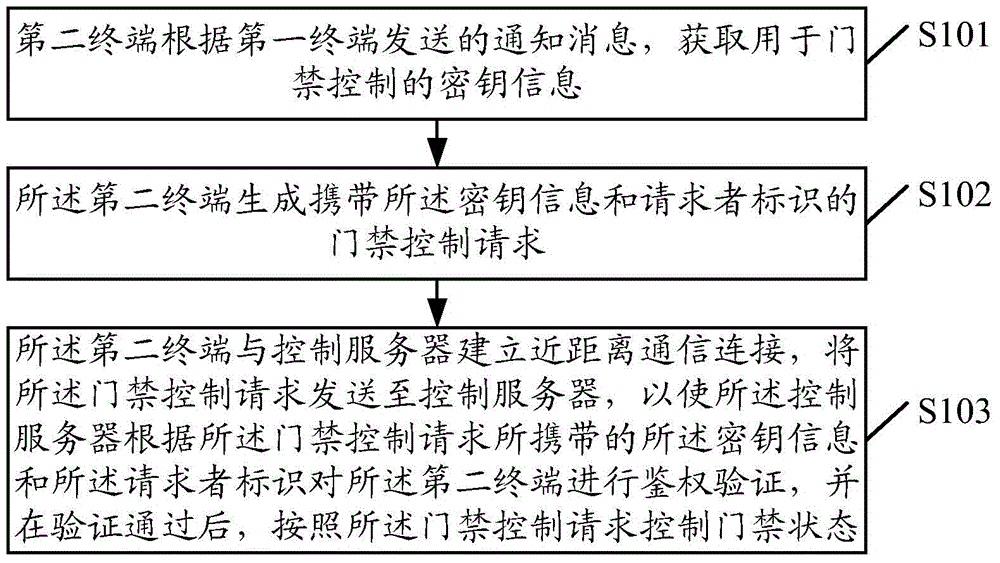
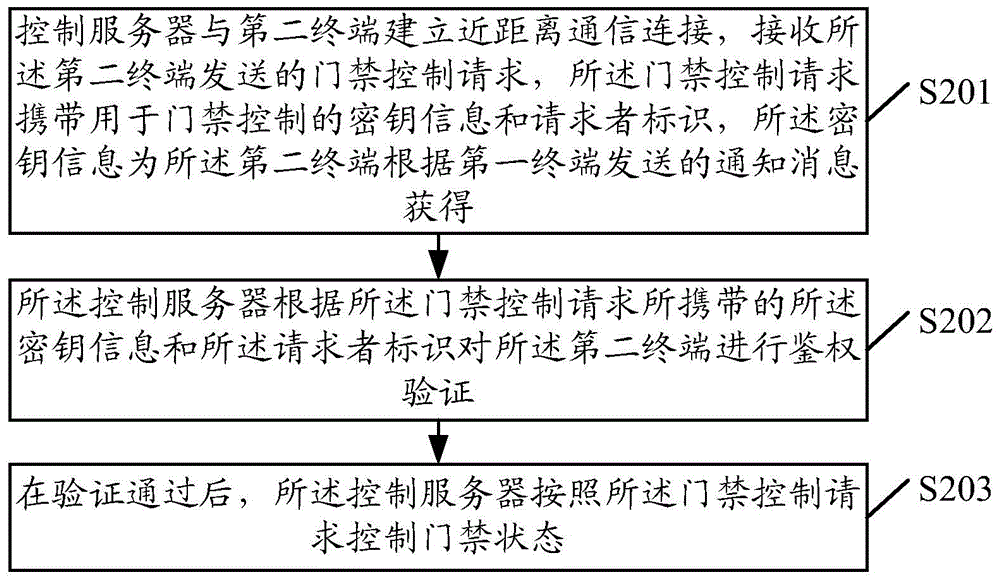
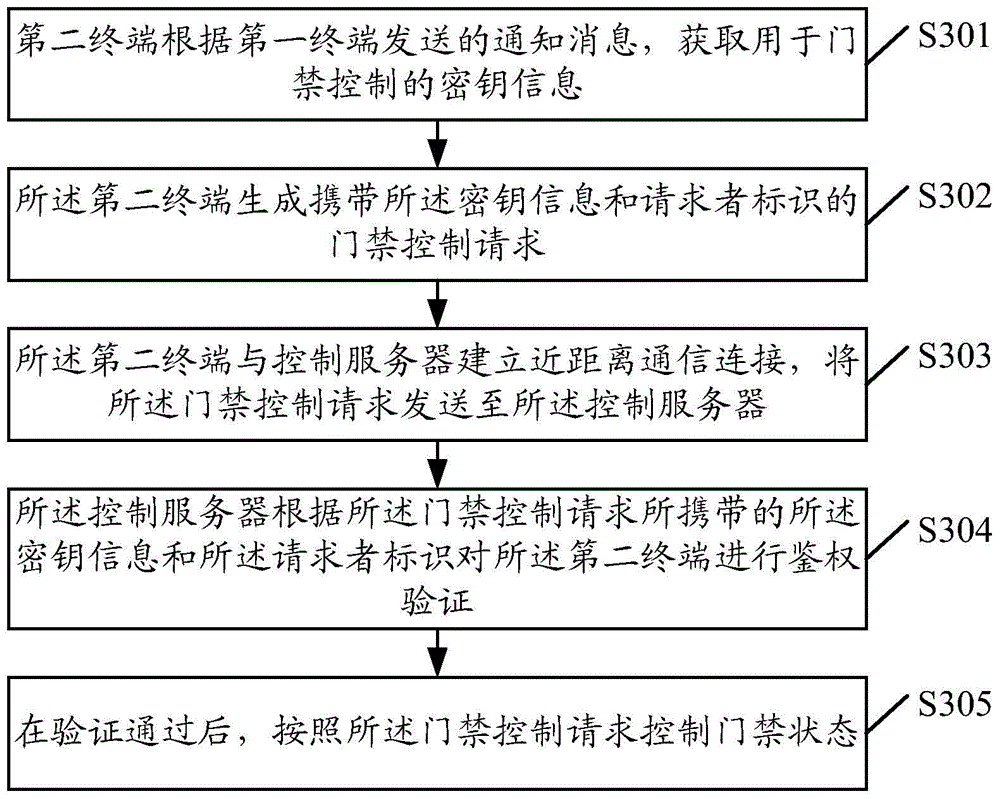
Entrance guard control method, apparatus, terminal and control server
InactiveCN105488871AImprove efficiencyImprove securityIndividual entry/exit registersComputer terminalAuthentication
The invention discloses an entrance guard control method, an apparatus, a terminal and a control server. The method comprises the following steps: a second terminal can obtain secret key information used for gate inhibition control according to a notification message sent by a first terminal; a secret key information and requester identification-carried gate inhibition control request is generated by the second terminal; the second terminal and the control server establish short-range communication connection, the gate inhibition control request is sent to the control server; the control server performs authentication verification on the second terminal according to the secret key information and the requester identification carried by the gate inhibition control request, after the verification is passed, a gate inhibition state is controlled according to the gate inhibition control request. According to the invention, gate inhibition control efficiency can be effectively increased, and security and intelligence of the gate inhibition control can be enhanced.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Access control method and device based on token and supporting object attributes
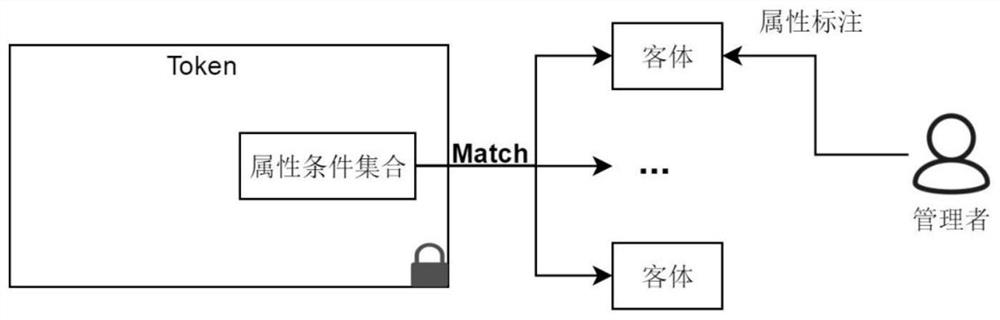
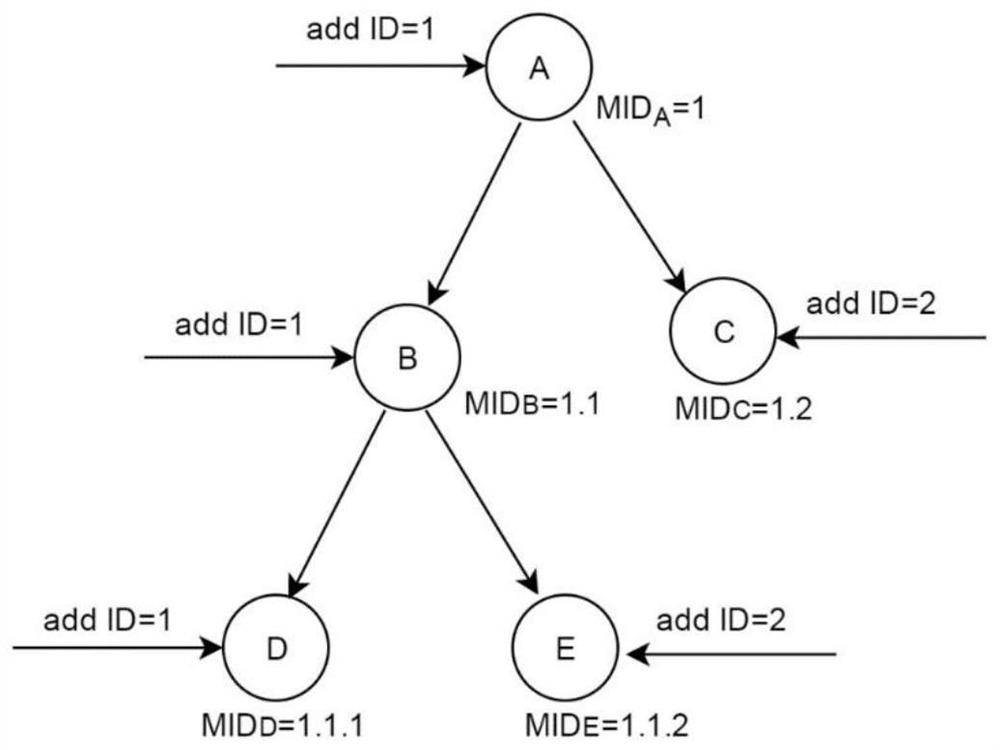
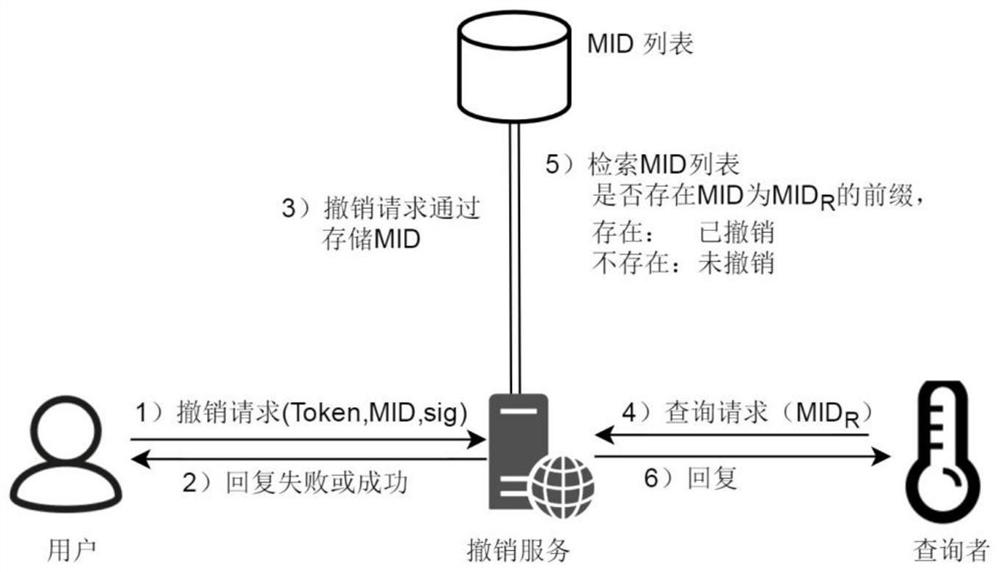
ActiveCN111669386AReduce applicationsReduce reviewUser identity/authority verificationEngineeringSerial code
The invention discloses an access control method and device based on a token and supporting object attributes. A management party predefines the category of the attribute condition and the category ofthe access permission, and carries out attribute labeling on managed equipment; the management party receives a first token request sent by an application party, takes out an attribute condition setCS, an access permission set AR and a public key PK of an applicant in the request; the management party performs identity authentication on the applicant by using the PK, evaluates the attribute condition set CS and the access permission set AR, generates a serial number of a token after the sets pass evaluation, generates a token of an applicant based on the serial number and the first token request and sends the token to the applicant; the applicant serves as a subject of access control, and sends the corresponding token to an object; and the object carries out identity authentication on the subject and verifies the received token, including the verification of the attribute condition set CS by the object according to the attribute of the object, and if the token passes verification, access is allowed.
Owner:WUHAN UNIV OF TECH
Dynamic distributed cooperation on demand accessing method and system
ActiveCN103298139AIncrease transfer rateReduce overheadError prevention/detection by using return channelWireless communicationData transmissionDistributed computing
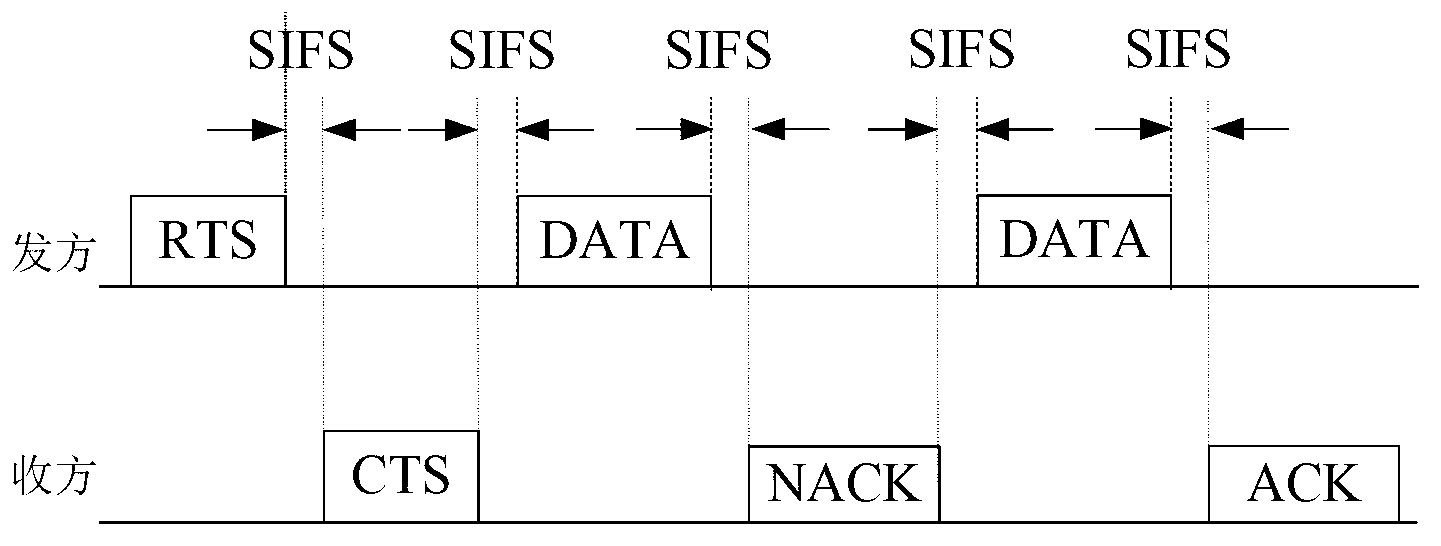
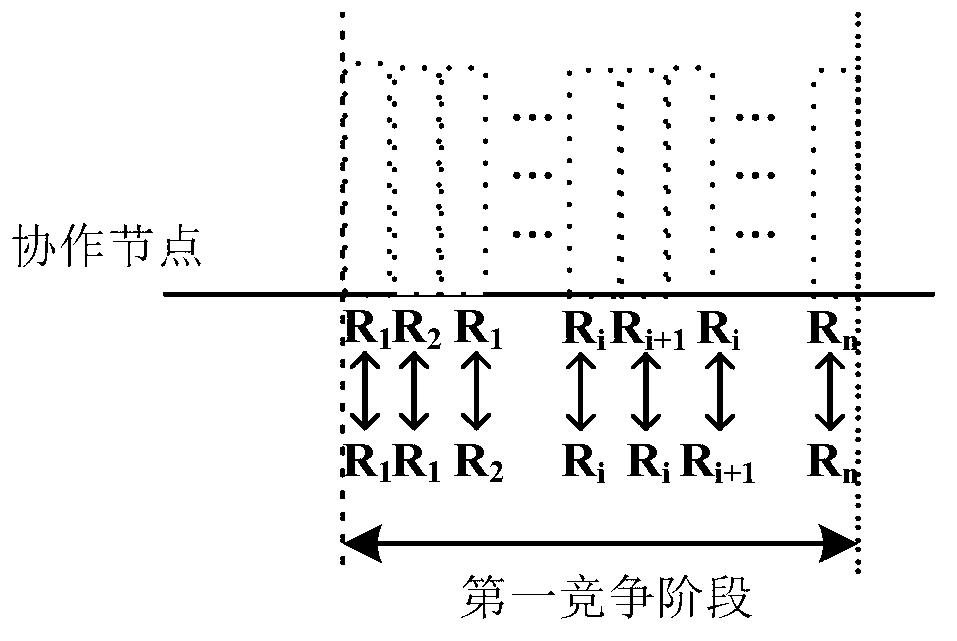
The invention provides a dynamic distributed cooperation on demand accessing method and system. The dynamic distributed cooperation on demand accessing method includes that each cooperation node competes according to the data transmission rate of the cooperation node and a transmitting party node and a receiving party node, whether having self data grouping transmitting and the times of grouping of already transmitted data of the cooperation node so that the successfully competing cooperation nodes are selected, wherein when one cooperation node has self data grouping transmitting, the winning cooperation node is selected according to the principles of first transmitting busy tones, having the longest busy tone transmitting time and not hearing other busy tones in a tiny slot time after busy tone transmitting. The dynamic distributed cooperation on demand accessing method and system reduce competition conflicts and expanses of the cooperation nodes and improve the data grouping transmission rate and the cooperation accessing control efficiency.
Owner:BEIHANG UNIV
Supply chain access control system and method based on public chain smart contract
ActiveCN111797374AMeet traceability requirementsEffective data sharingDigital data authenticationManufacturing computing systemsControl systemFinancial transaction
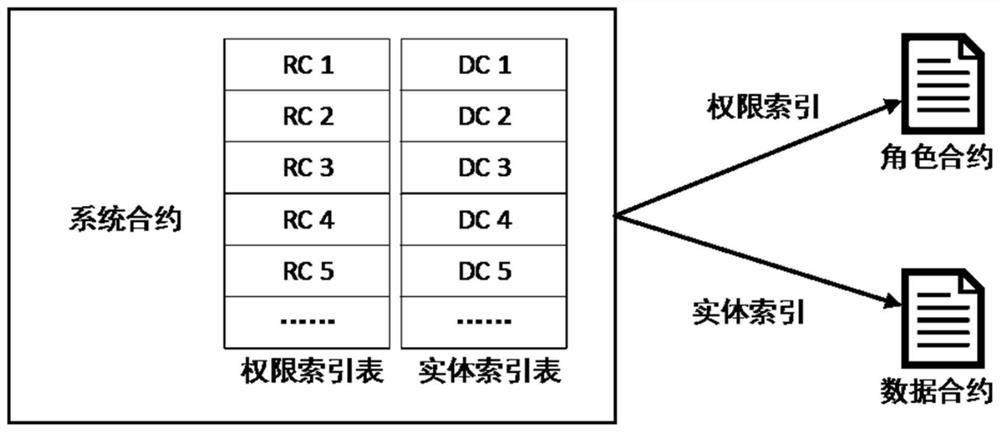
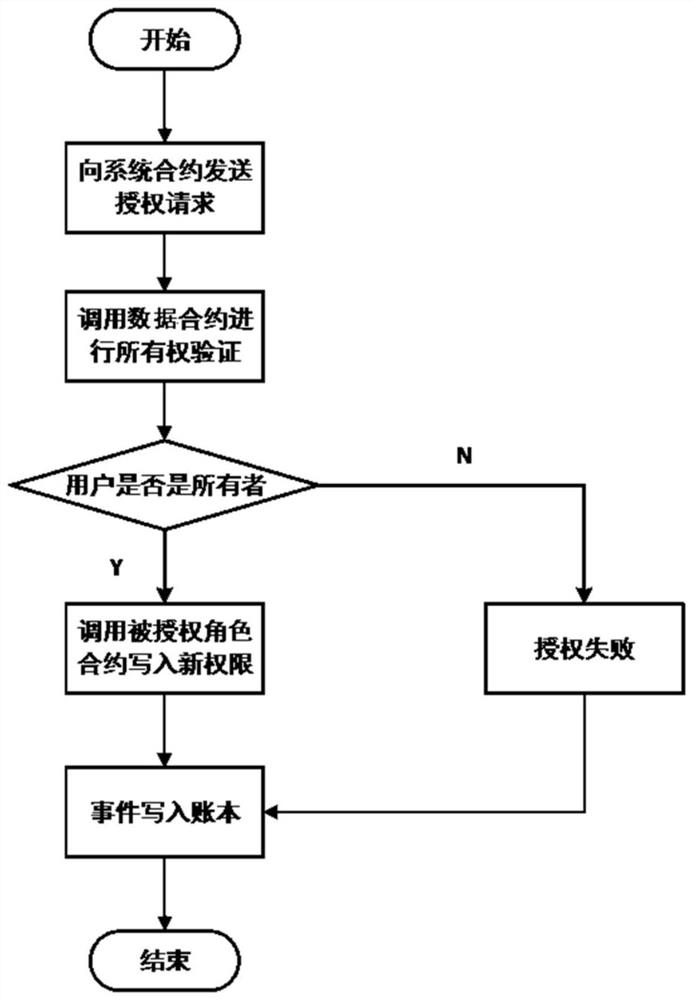
The invention relates to a supply chain access control system based on a public chain smart contract, which is used for access control in a block chain traceability scene. According to the system, anRBAC model is adopted, and the system comprises a system contract SC, role contracts RC and data contracts DC. The RBAC model comprises four types of agents which are associated with one another and an operation set OP, and the four types of agents are respectively a user agent u, a role agent r, a permission agent p and an object agent ob. The system contract SC is used for managing a user agentu, the role contracts RC are used for managing a role agent r and a plurality of permission agents p, and the data contracts DC are used for managing the object agent ob. The deployment transaction ofthe system contract SC serves as an entrance of the RBAC model and is firstly linked, and the multiple role contracts RC and the multiple data contracts DC are respectively called by the system contract SC. Compared with the prior art, the system has the advantage that data sharing convenience, data privacy security and the like are ensured at the same time.
Owner:浙江同善人工智能技术有限公司
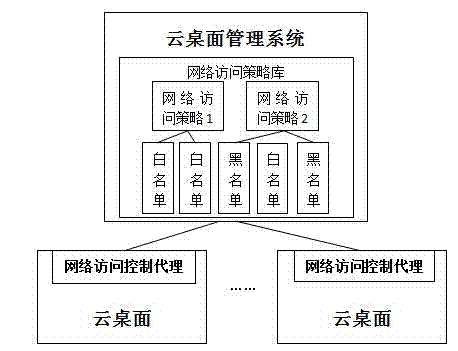
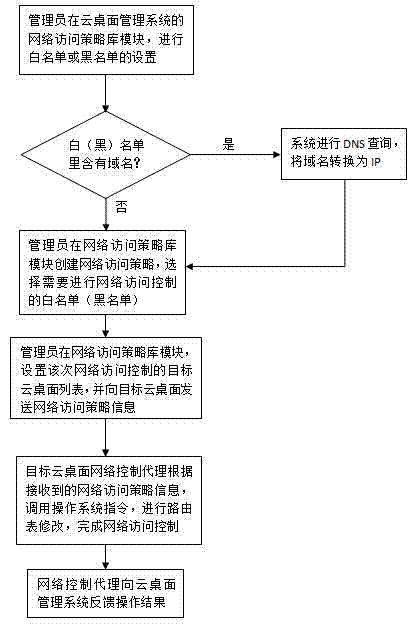
Cloud desktop network access control method
InactiveCN104283870AReduce access control costsLower control costsTransmissionNetwork access serverRouting table
The invention discloses a cloud desktop network access control method. The method includes the steps of setting network access strategies on a network access strategy library module, establishing the network access strategy module in a cloud desktop management system, storing the network access strategies in the network access strategy library module, sending the network access strategies to a target cloud desktop through a local area network or the Internet through the cloud desktop management system, installing network access control agency software on the target cloud desktop, and configuring a routing list of the target cloud desktop through the network access control agency software according to the received network access strategies. The method is suitable for network access control of the cloud desktop and has the advantages of being flexible and efficient.
Owner:SYSU CMU SHUNDE INT JOINT RES INST
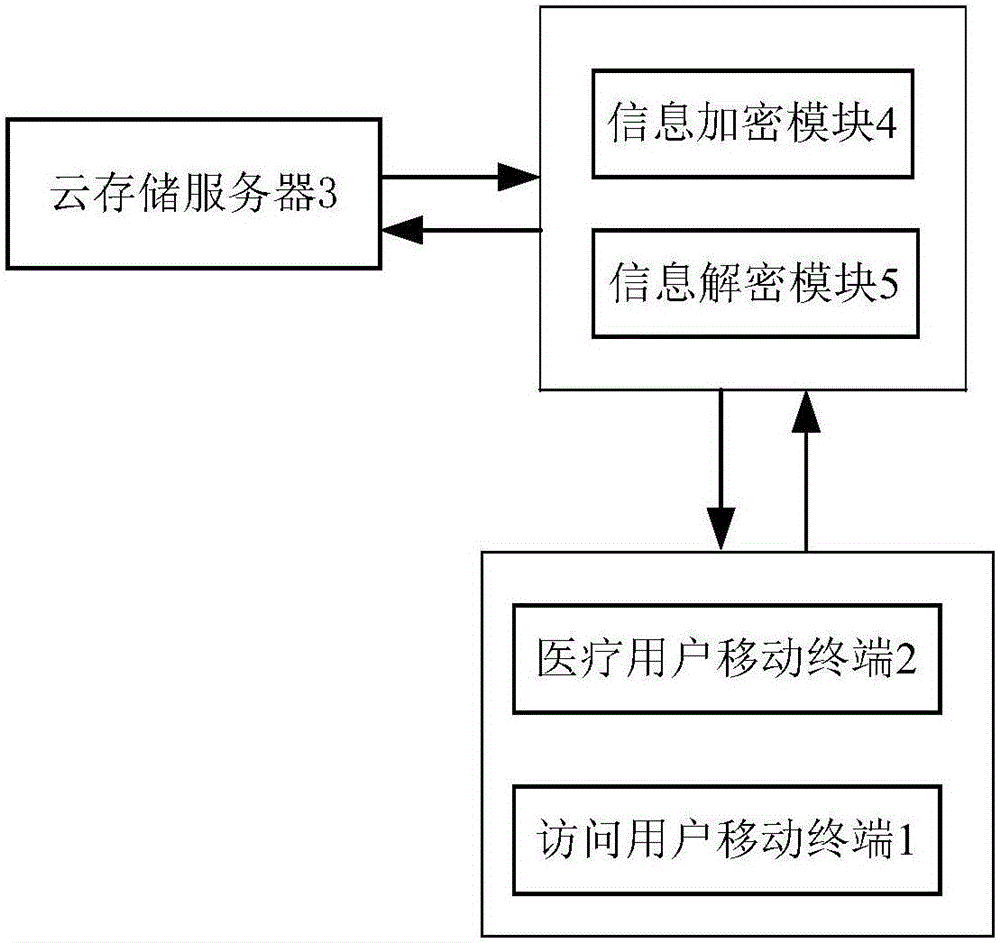
Medical case information access safety system
InactiveCN106131014APrevent leakageProtection securityData processing applicationsTransmissionSafe systemCloud storage
The invention discloses a security system for medical case information access, which includes a medical user mobile terminal, an access user mobile terminal, a cloud storage server, an information encryption module, and an information decryption module. The invention can prevent the leakage of medical medical record information, effectively protect the safety of the medical medical record information of the mobile terminal of the medical user, and has strong ease of use and practicability; the coded medical medical record information is divided into different access points according to the access structure tree Level, improve the efficiency of access control, use code division multiplexing technology to encode medical record information, reduce the storage space of cloud storage server; can realize fine-grained access control, effectively reduce the computational overhead of system encryption and decryption.
Owner:杨炳
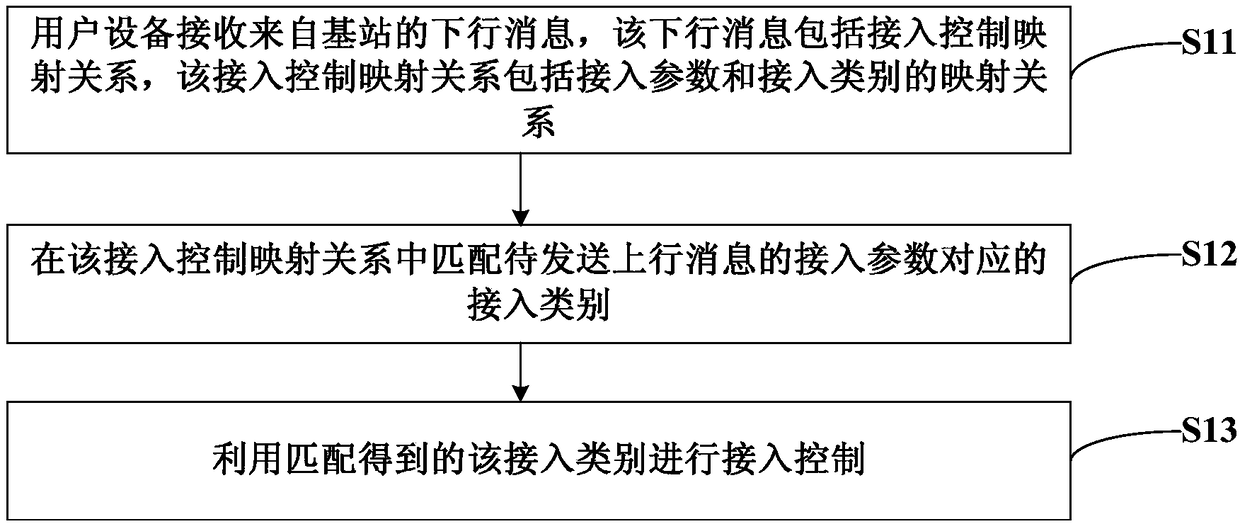
Access control method, communication equipment and equipment with storage function
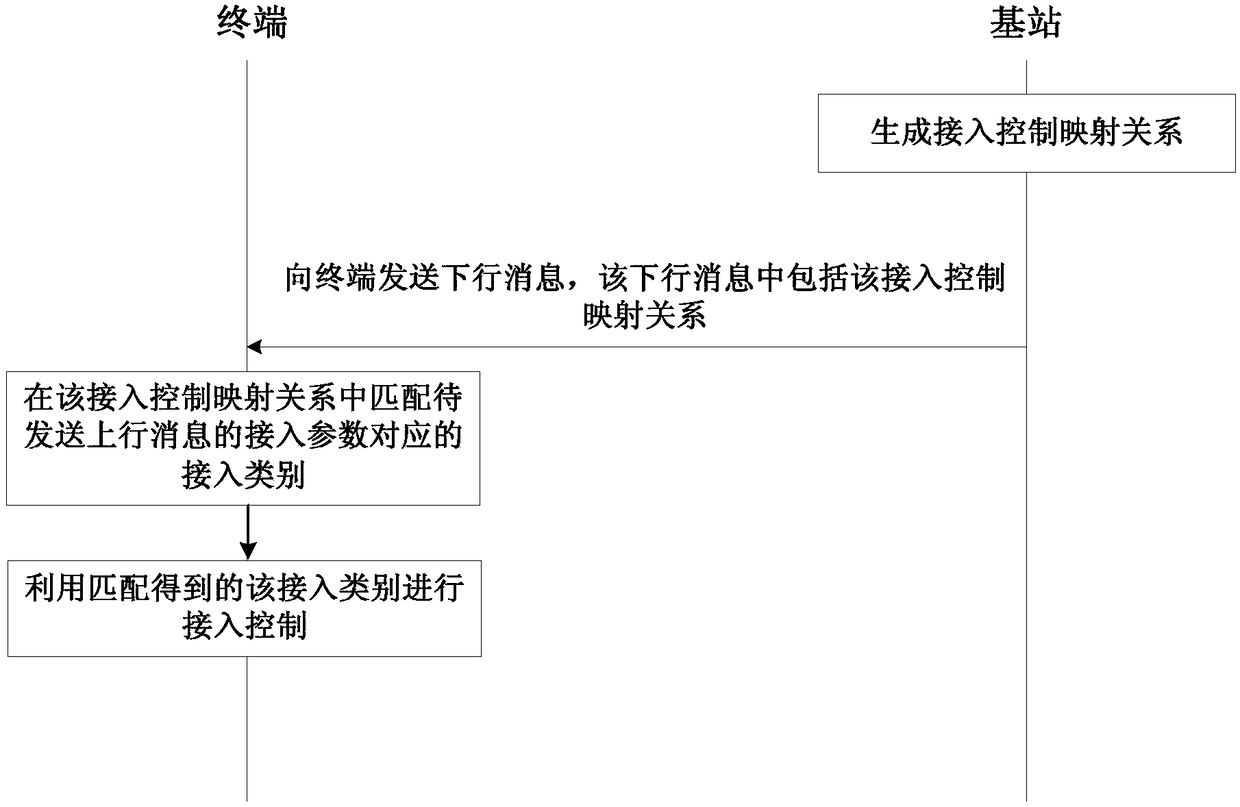
ActiveCN109327882AReduce the burden onImprove Access Control EfficiencyNetwork traffic/resource managementAssess restrictionUser equipmentReal-time computing
The invention discloses an access control method, communication equipment and equipment with a storage function. The access control method comprises the steps of: receiving a downlink message from a base station by user equipment, wherein the downlink message comprises an access control mapping relationship, and the access control mapping relationship comprises a mapping relationship between access parameters and access categories; in the access control mapping relationship, matching an access category corresponding to an access parameter of a to-be-sent uplink message; and by utilizing the access category obtained by matching, carrying out access control. In the mode, according to the invention, a load of the user equipment can be reduced, and access control efficiency can be improved.
Owner:JRD COMM (SHENZHEN) LTD
Comprehensive meteorological data acquisition system based on NB-IoT communication
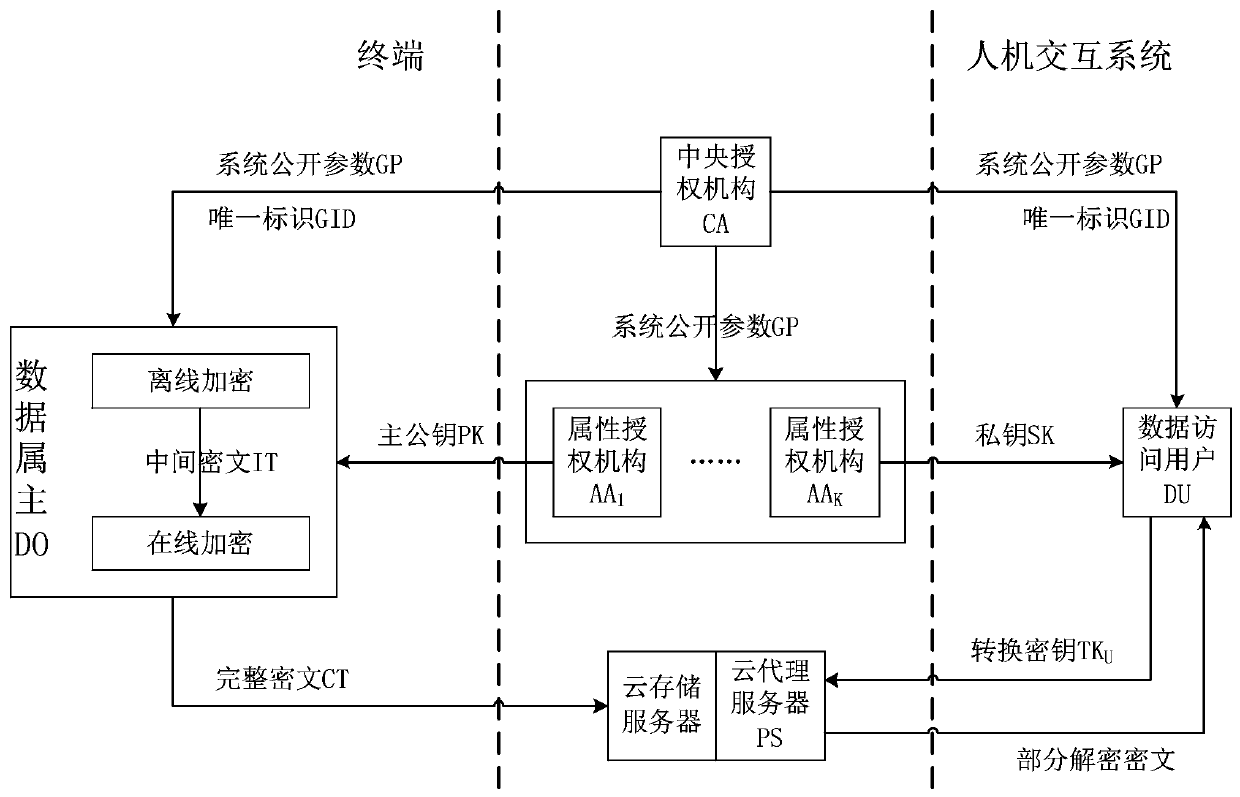
InactiveCN110300114AReduce the burden onReduce riskSoftware engineeringParticular environment based servicesAccess structurePlaintext
The invention discloses a comprehensive meteorological data acquisition system. The system comprises a man-machine interaction system, a terminal and a key acquisition module, the key acquisition module is used for generating a system public key and a first user private key; the information receiving module is used for receiving a ciphertext and a verification token which are generated based on anaccess structure and a plaintext and sent by a terminal, receiving a conversion key and a second user private key which are generated based on the system public parameter, the first user private keyand the corresponding user attribute and are sent by the user access end, the division and decryption text generation module is used for generating a partial division and decryption text based on thesystem public parameters, the unique user identifier of the user access end, the conversion key and the ciphertext; and the information sending module is used for sending the partial divided decryptedmessage to the user access end, so that the user access end decrypts the partial divided decrypted message by using the system public parameter and the second user private key to obtain a plaintext.The system mitigates the computing and storage load of the user.
Owner:SUZHOU UNIV
File segmenting method based on digital abstract
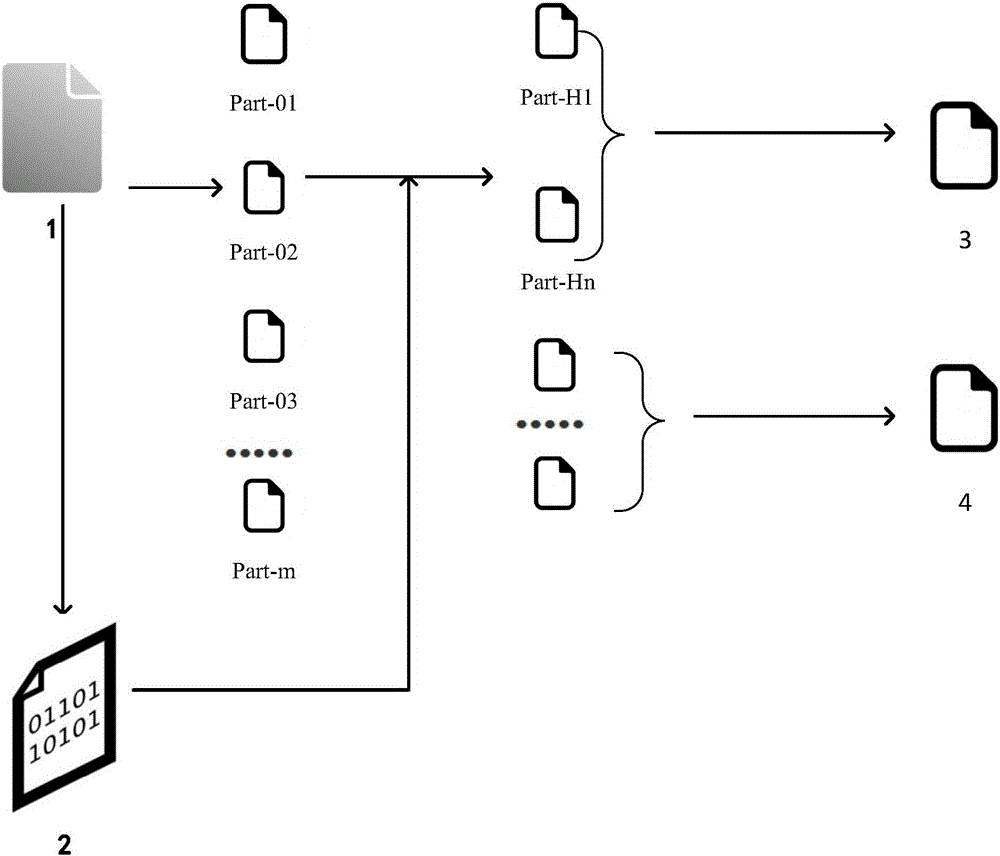
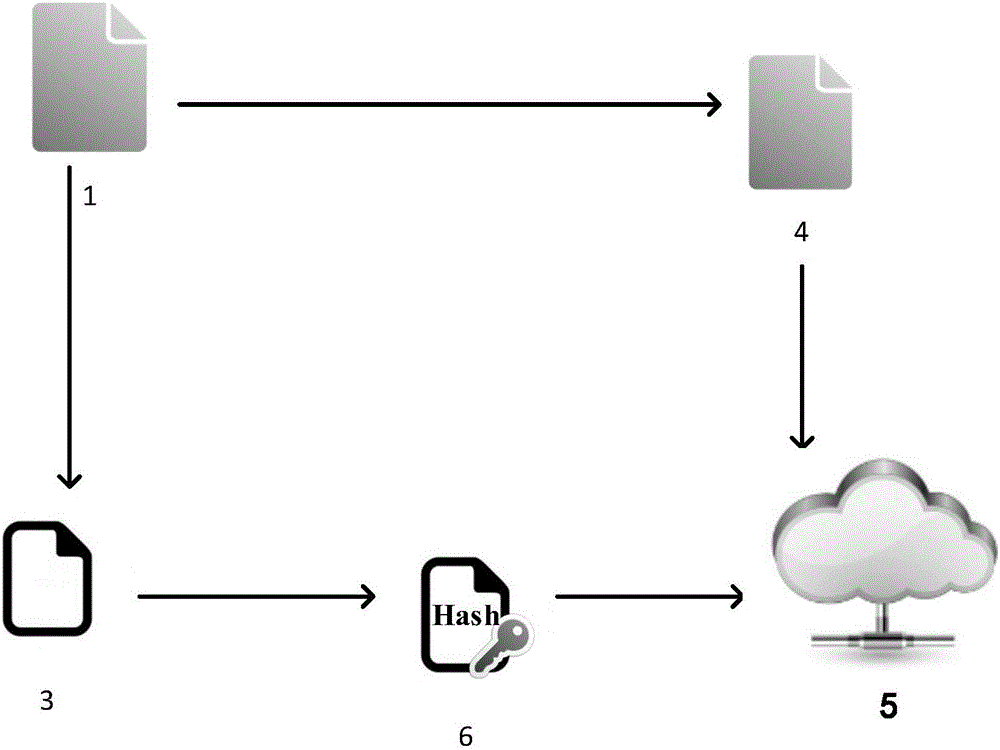
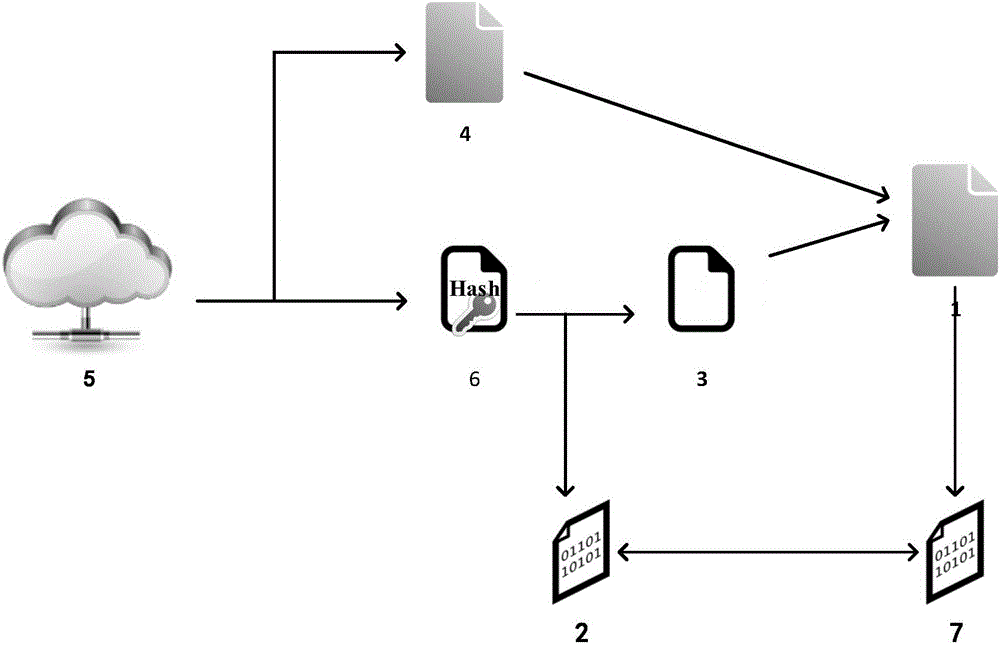
InactiveCN105790928AReduce calculationShorten the timeEncryption apparatus with shift registers/memoriesUser identity/authority verificationData integrityConfidentiality
The invention discloses a file segmenting method based on a digital abstract. The algorithm mainly comprises a digital abstract module, a file segmenting module and a file recombination module, wherein the digital abstract module extracts and converts file digital abstract, the file segmenting module converts the file into a plurality of file blocks with same size sequentially, and the file recombination module recombines different file blocks into two files. The digital abstract serves as file extraction basis. Data confidentiality is ensured, and data integrity verification can be completed. The file segmenting method is applicable to file outsourcing storage.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
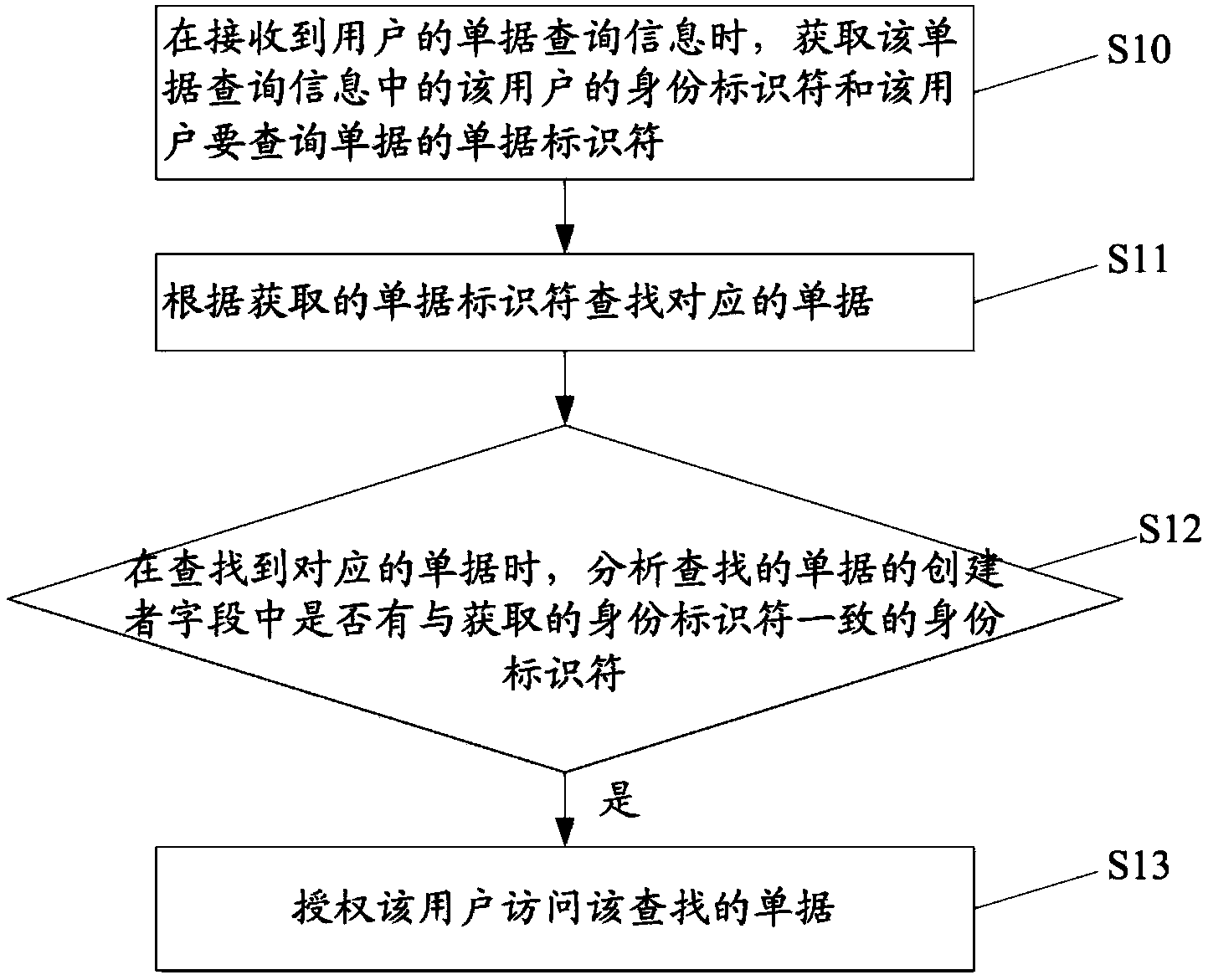
Receipt access control method and device
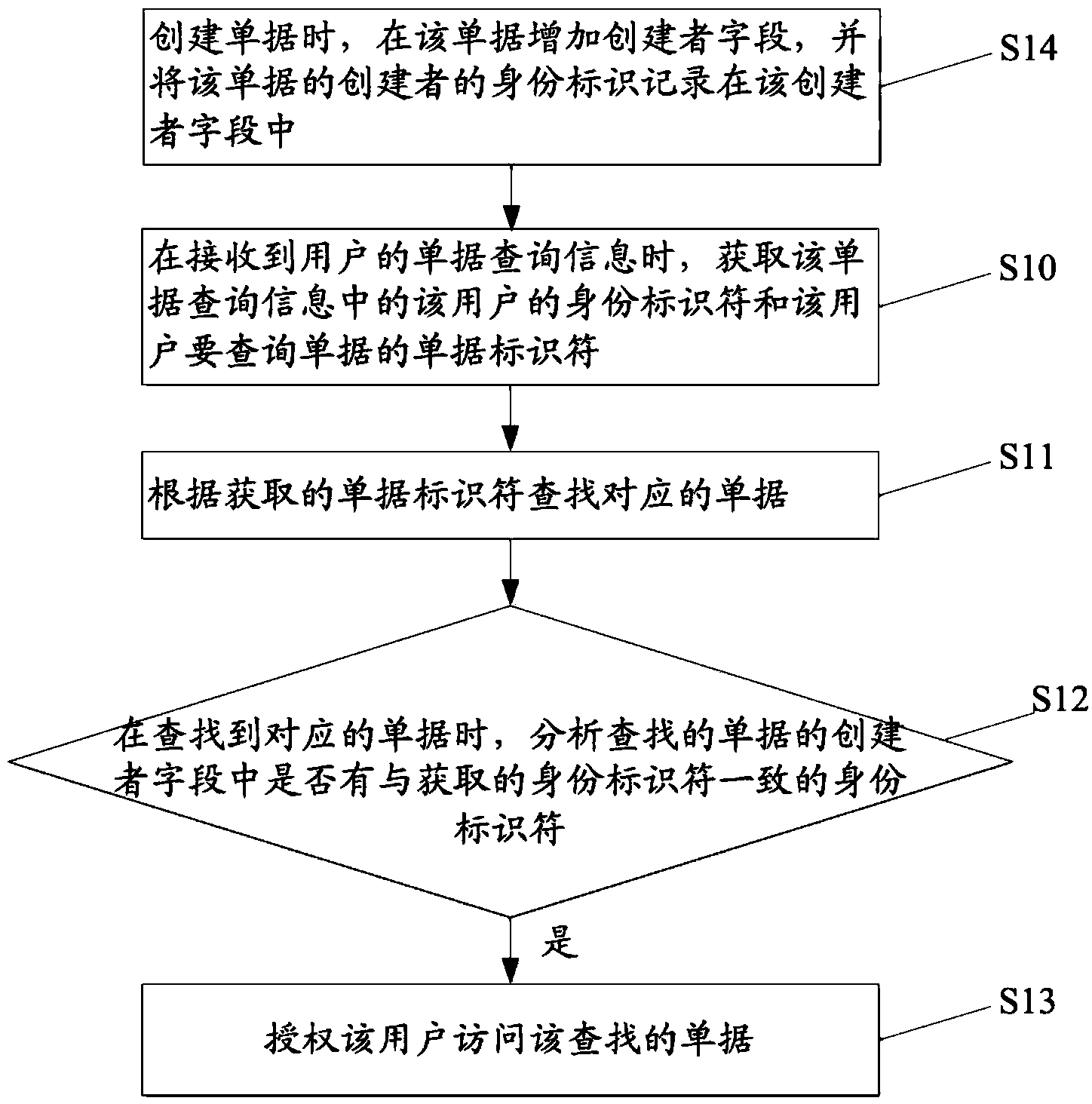
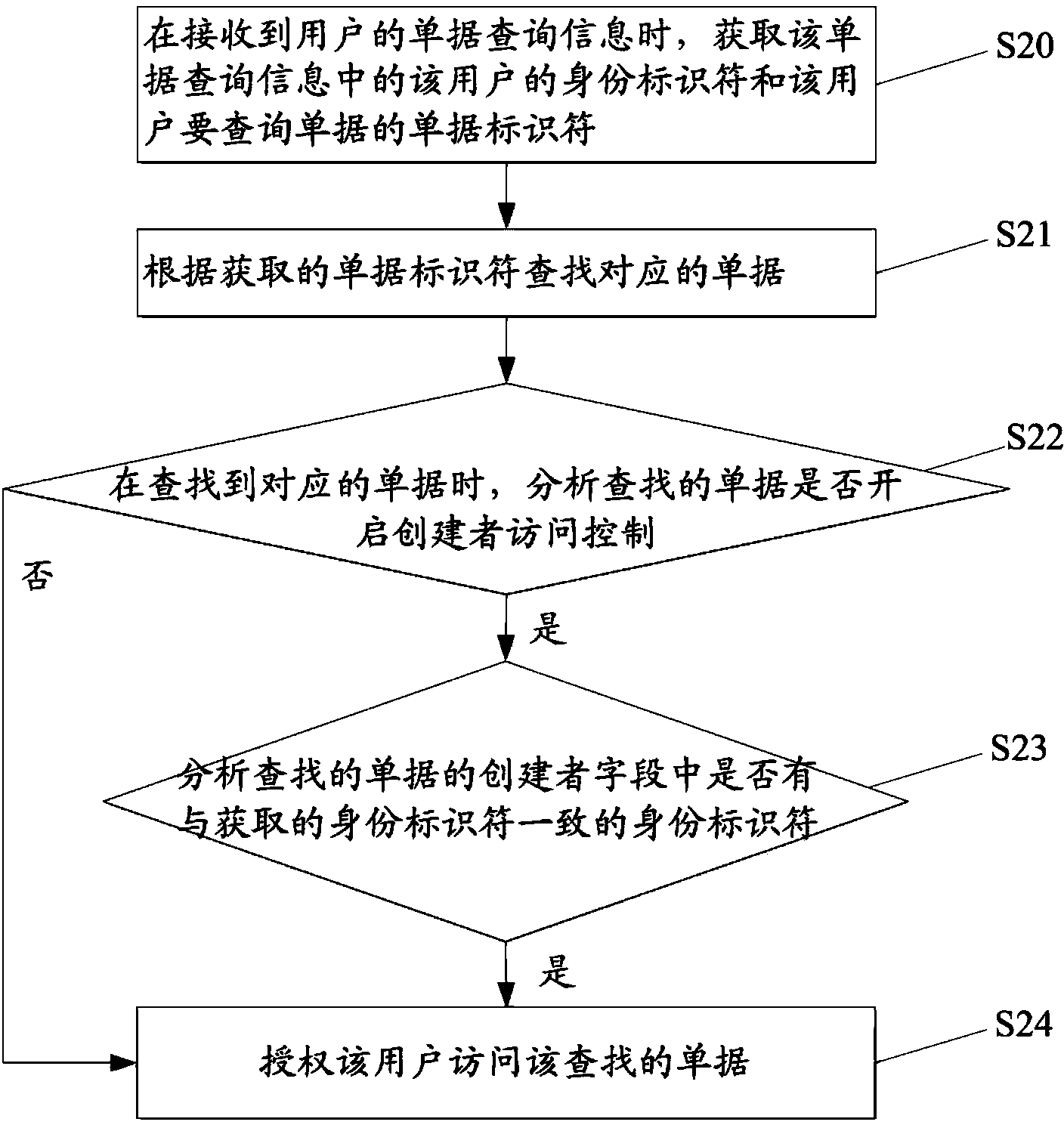
InactiveCN103678557AImprove Access Control EfficiencySpecial data processing applicationsUser needsWorld Wide Web
The invention discloses a receipt access control method and device. The receipt access control method comprises the steps that when receipt inquiry information of a user is received, an identity identifier of the user and a receipt identifier of a receipt which the user needs to inquire in the receipt inquiry information are obtained; the corresponding receipt is searched for according to the obtained receipt identifier; when the corresponding receipt is found, whether an identity identifier consistent with the obtained identity identifier exists in a creator field of the found receipt is analyzed; when the identity identifier consistent with the obtained identity identifier exists in the creator field of the found receipt, the user is authorized to access the found receipt. By means of the receipt access control method and device, access control efficiency can be improved.
Owner:KINGDEE SOFTWARE(CHINA) CO LTD
Two-level policy decision-based access control method and system
The invention discloses a two-level policy decision-based access control method and a two-level policy decision-based access control system, and belongs to the field of access control in information safety. In the method, a local policy decision point (PDP) is deployed at a policy enforcement point (PEP) end, and the local PDP makes a decision for an access request according to a local policy cache, and if the local PDP cannot determine that the decision is a deterministic decision, a central PDP finally finishes the decision according to a system policy library. The system comprises a policydecision server, an attribute publishing point and a plurality of resource servers, wherein a policy enforcement point (PEP) and a local policy decision point (PDP) are deployed on each resource server; and a central policy decision point (PDP) is deployed on the policy decision server. The invention has a good dynamically adjusted elastic system framework, fully utilizes the computing resources of the PEP end, lightens the burden of the central PDP, reduces the network transmission overhead and effectively improves the access control efficiency at extremely low policy update cost.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Intelligent access control management method and system based on Internet of Things
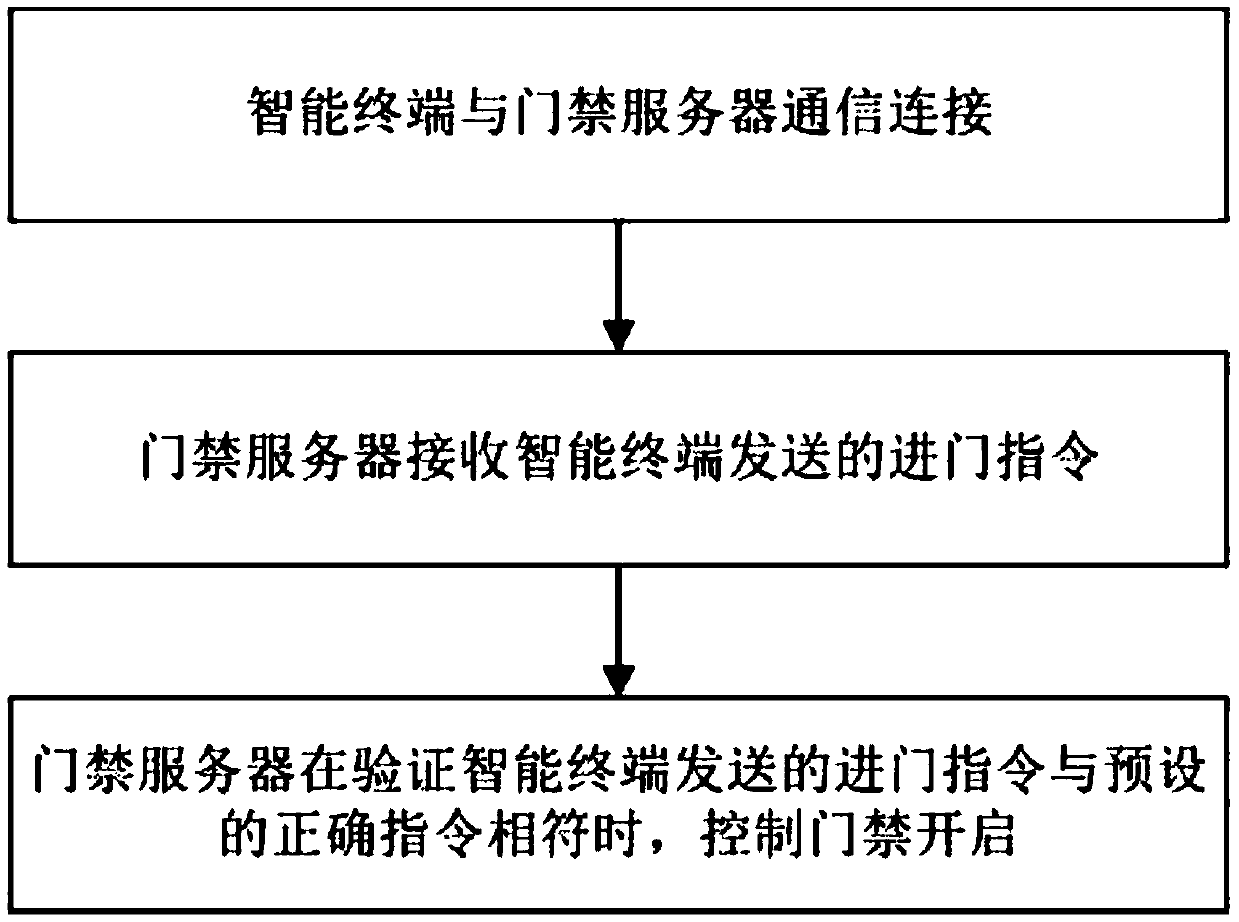
InactiveCN109615748AImprove securityPrevent plagiarismIndividual entry/exit registersUser inputSocial internet of things
The invention discloses an intelligent access control management method and system based on the Internet of Things. The method comprises the steps that an intelligent terminal is connected with an access control server in a communicating mode; the access control server receives an access instruction sent by the intelligent terminal; when the access control server verifies that the access instruction sent by the intelligent terminal is consistent with a preset correct instruction, the access control server controls the access control opening, so that an user is connected with the access controlserver by scanning an access control QR code in a communicating mode, then the user can input the access control instruction directly on the intelligent terminal, when the access control instructioninput by the user is correct, the access control opens, and the user can enter; inputting the instruction before the access control is not required, plagiarism by illegal persons is prevented, card wiping to enter the access control is not required, forgetting or loss of a card is not required to worry about, and manual management is not required; and labor costs are reduced, the efficiency of theaccess control is improved, convenience is brought to the user, and meanwhile, the security of the access control is improved.
Owner:合肥凌极西雅电子科技有限公司
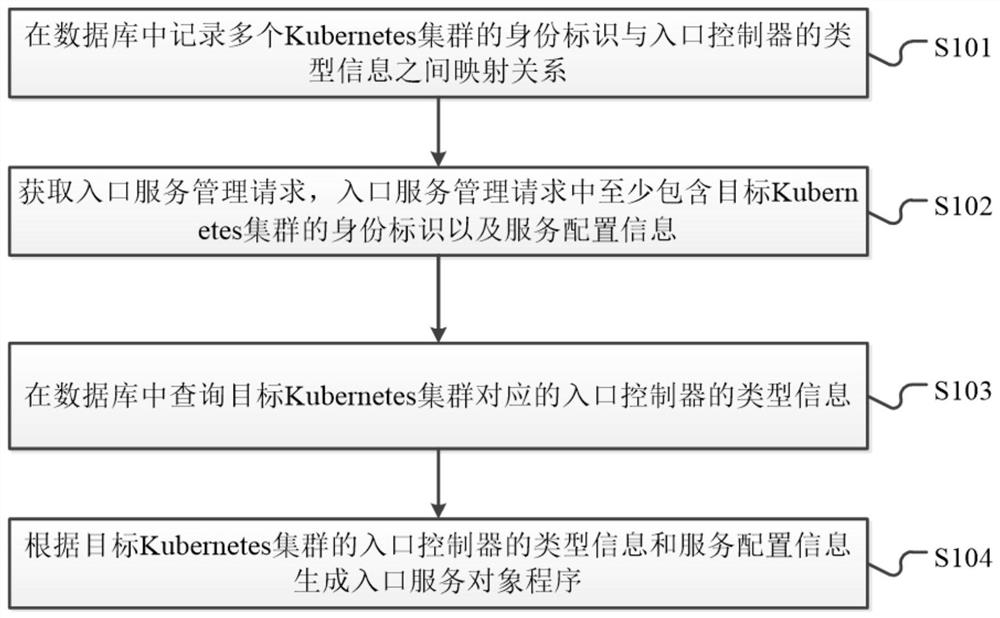
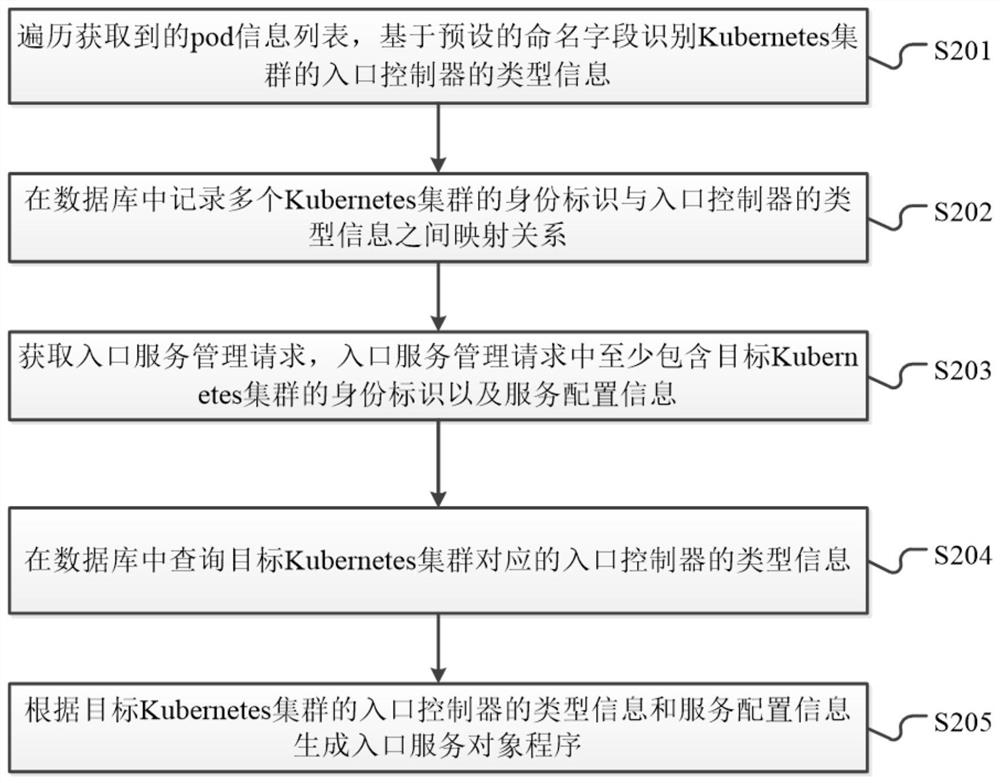
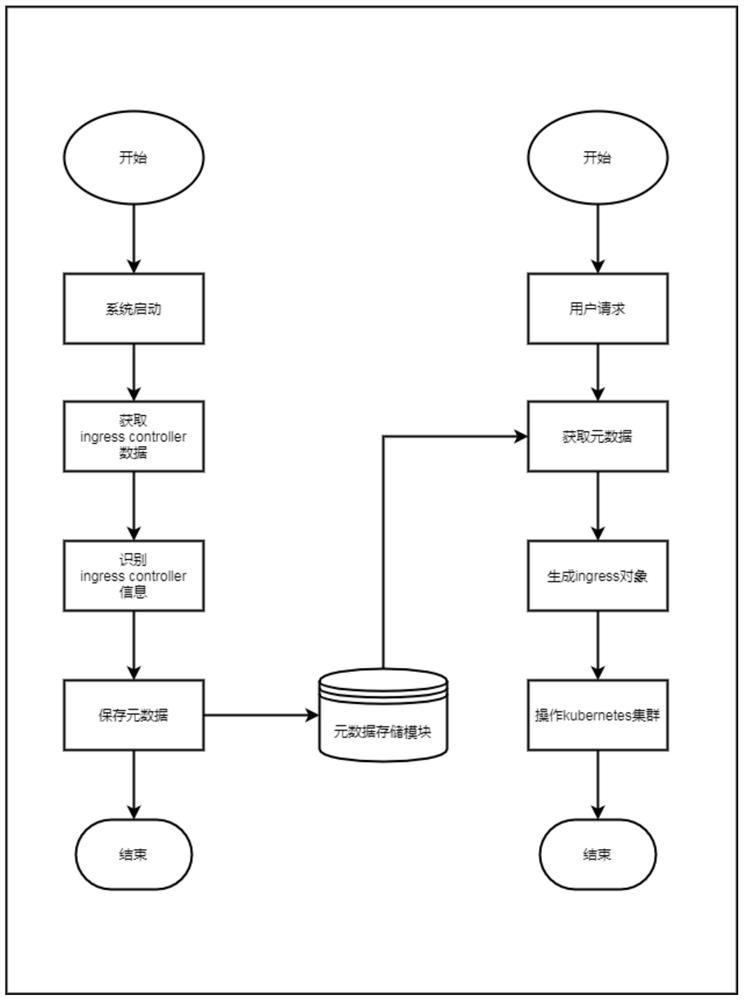
Kubernetes cluster access control method, Kubernetes cluster access control system and related equipment
PendingCN113032105AImprove Access Control EfficiencyDatabase management systemsRelational databasesService configurationData library
The embodiment of the invention provides a Kubernetes cluster access control method, a Kubernetes cluster access control system and related equipment, which are used for improving the efficiency of Kubernetes cluster access control management. The method provided by the embodiment of the invention comprises the following steps: recording a mapping relationship between identities of a plurality of Kubernetes clusters and type information of an entry controller in a database; obtaining an entry service management request, wherein the entry service management request at least comprises an identity label of a target Kubernetes cluster and service configuration information; inquiring the type information of an entry controller corresponding to the target Kubernetes cluster in the database; and generating an entry service object program according to the type information of the entry controller of the target Kubernetes cluster and the service configuration information.
Owner:KINGDEE SOFTWARE(CHINA) CO LTD
Fingerprint identification access control system based on wireless network
InactiveCN107492176AQuick identificationSimple structure and principleCharacter and pattern recognitionIndividual entry/exit registersMicrocontrollerElectricity
The invention discloses a fingerprint identification access control system based on a wireless network. The fingerprint identification access control system based on the wireless network comprises an outer shell, wherein an LCD display screen is arranged at the front end surface of the outer shell, a high-definition camera is mounted above the LCD display screen, an IC identification area and a fingerprint identification chip are arranged below the LCD display screen, a human body infrared pyroelectric sensor is arranged on the lower end edge of the outer shell, a core circuit board is arranged in an inner cavity of the outer shell, and a single chip microcomputer, a signal acquisition module, an FLASH memory module, a clock module, a display module, a wireless transmission module, a fingerprint identification module and an IC identification card are arranged on the core circuit board. The fingerprint identification access control system based on the wireless network disclosed by the invention is simple in structure principle, capable of realizing fingerprint identification quickly and high in intelligent degree, and improves the access control efficiency.
Owner:BEIJING JUNXIU CONSULTATION CO LTD
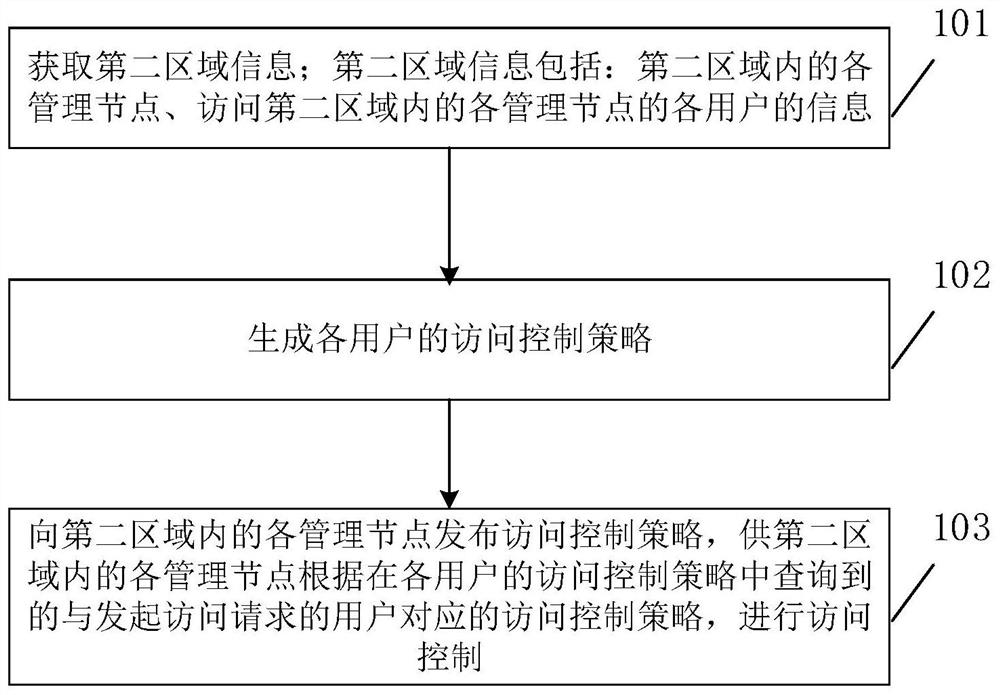
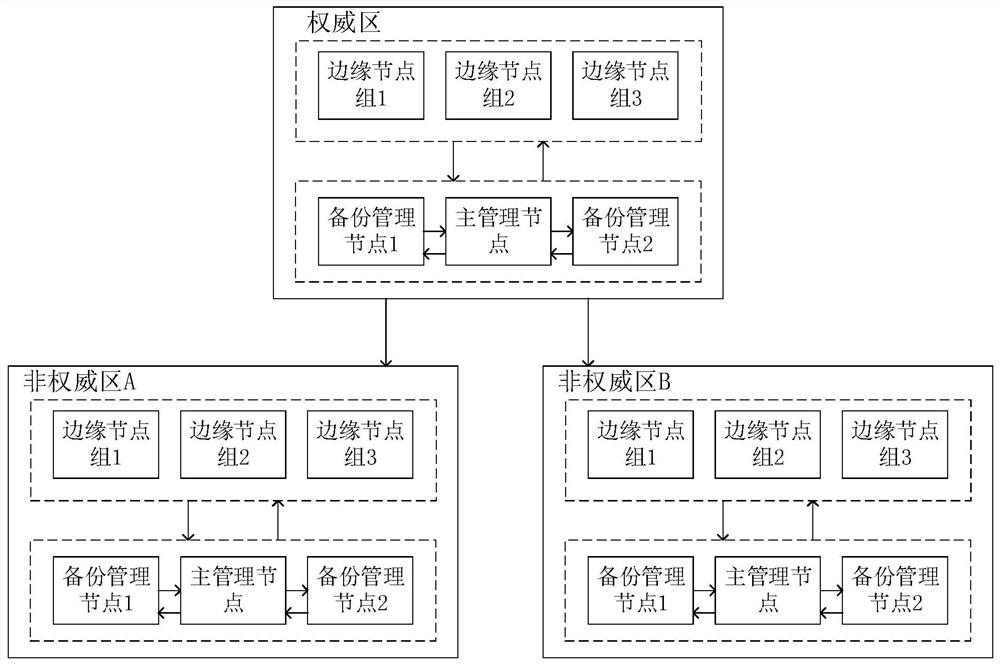
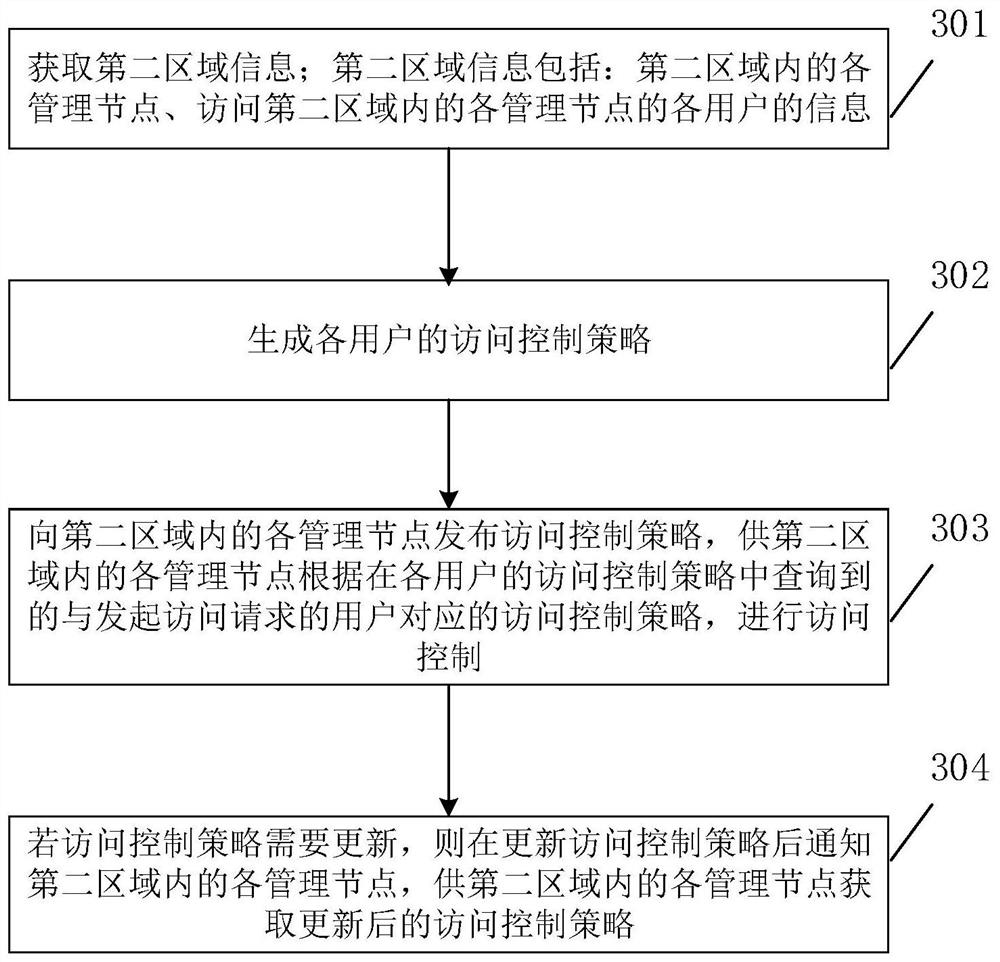
Access control method, electronic equipment and storage medium
ActiveCN112243003ASimplify the access control processImprove Access Control EfficiencyUser identity/authority verificationEngineeringDatabase
The embodiment of the invention relates to the field of communication, and discloses an access control method, electronic equipment and a storage medium. The access control method comprises the following steps: acquiring second region information, wherein the second region information comprises each management node in the second region and information of each user accessing each management node inthe second region; generating an access control strategy of each user; and issuing an access control strategy to each management node in the second area, so that each management node in the second area performs access control according to the access control strategy corresponding to the user initiating the access request inquired in the access control strategy of each user. The access control method provided by the embodiment of the invention can simplify the access control process and improve the access control efficiency.
Owner:CHINA MOBILEHANGZHOUINFORMATION TECH CO LTD +1
Comprehensive meteorological data acquisition system based on NB-IoT communication
ActiveCN110784493AReduce the burden onReduce riskSoftware engineeringParticular environment based servicesPlaintextAccess structure
Owner:SUZHOU UNIV
Access control method and access control device for USB mass storage device
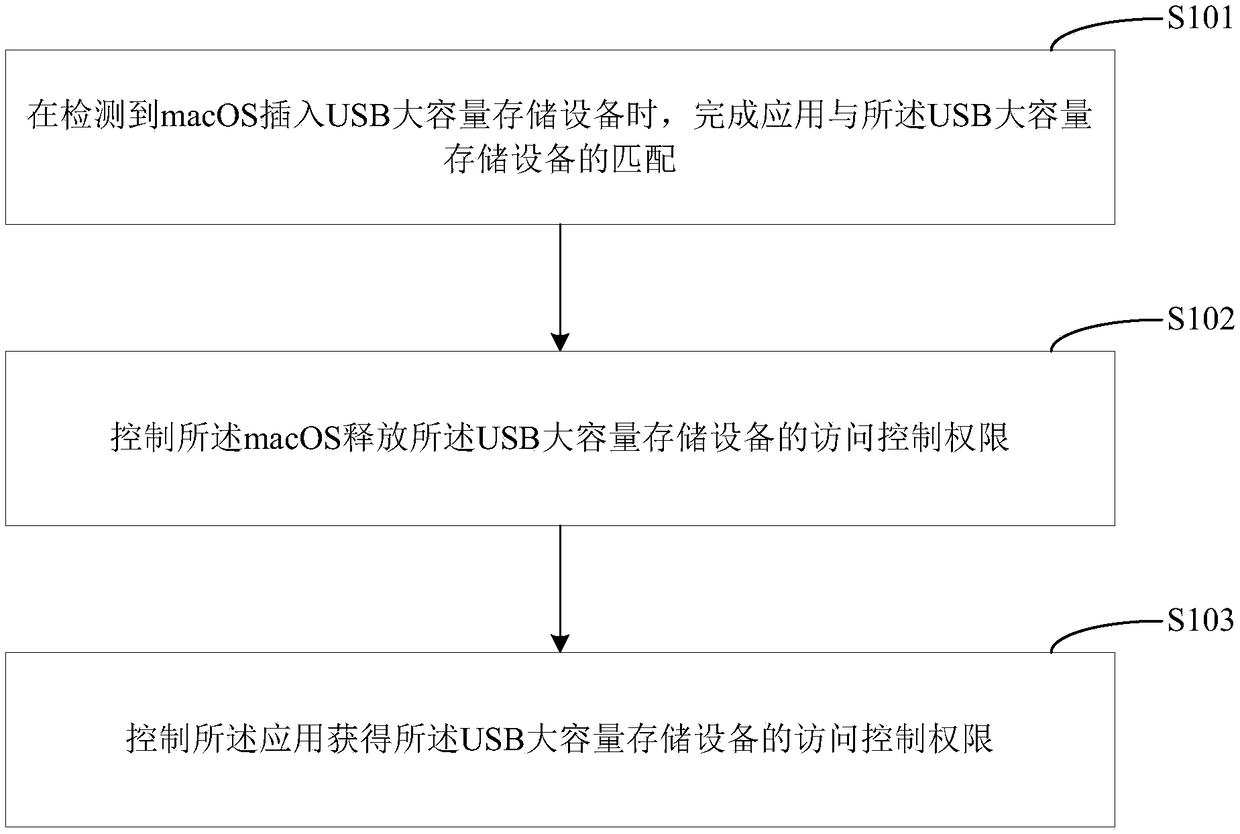
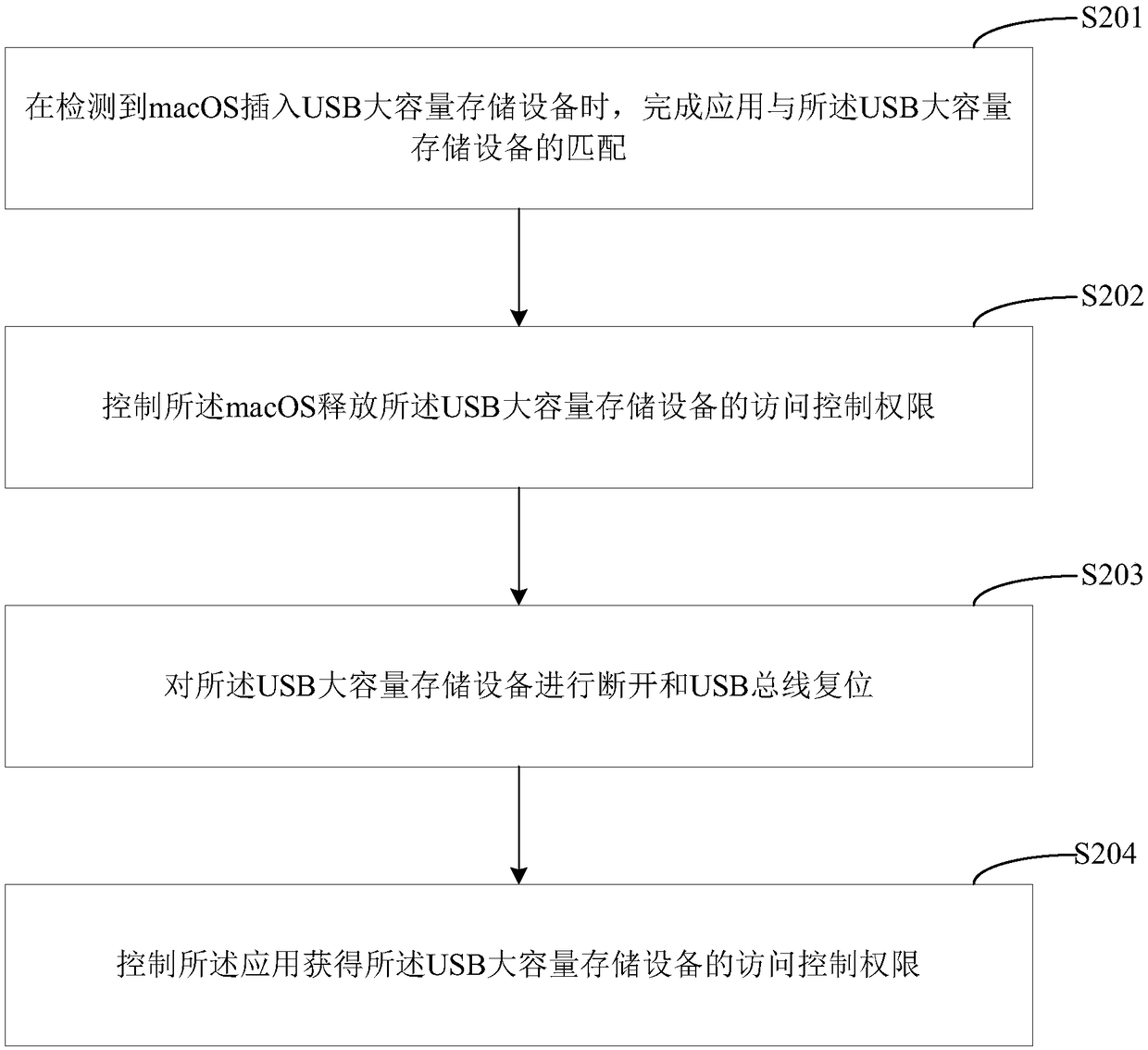
ActiveCN108629175AImplement access controlImplementation of access control permissionsDigital data authenticationMass storageTerminal equipment
The invention provides an access control method , an access control device, a terminal device and a computer-readable storage medium for an USB mass storage device. The access control method comprisesthe following steps of: when a macOS cut in USB mass storage device is detected, completing the matching of the application with the USB mass storage device; controlling the macro OS to release the access control authority of the USB mass storage device; and controlling the application to obtain the access control authority of the USB mass storage device. The method can solve the problem that theprior art can not control the access control to the USB mass storage device on the macOS.
Owner:SHENZHEN NETCOM ELECTRONICS CO LTD
Shared space management system
PendingCN108492480AMeet the needs of access control managementAvoid damageApparatus for meter-controlled dispensingIndividual entry/exit registersCouplingIdentity recognition
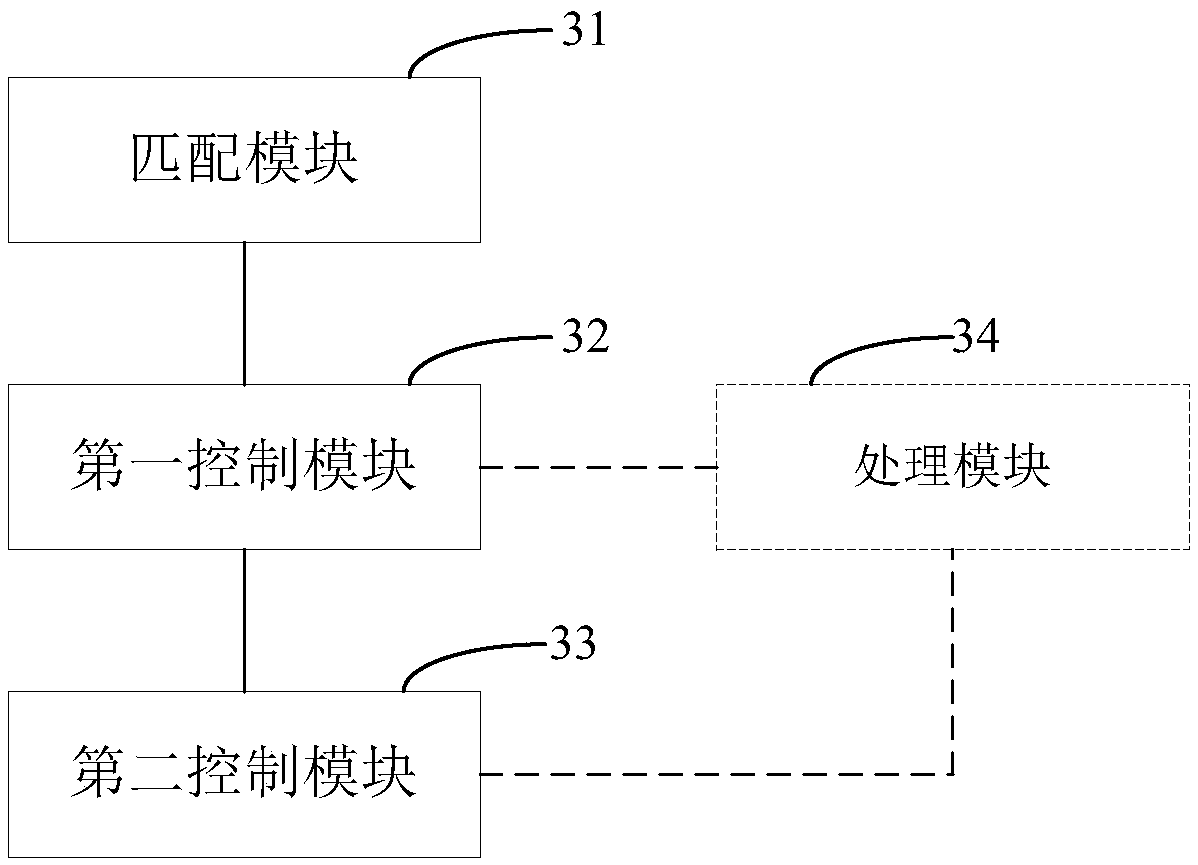
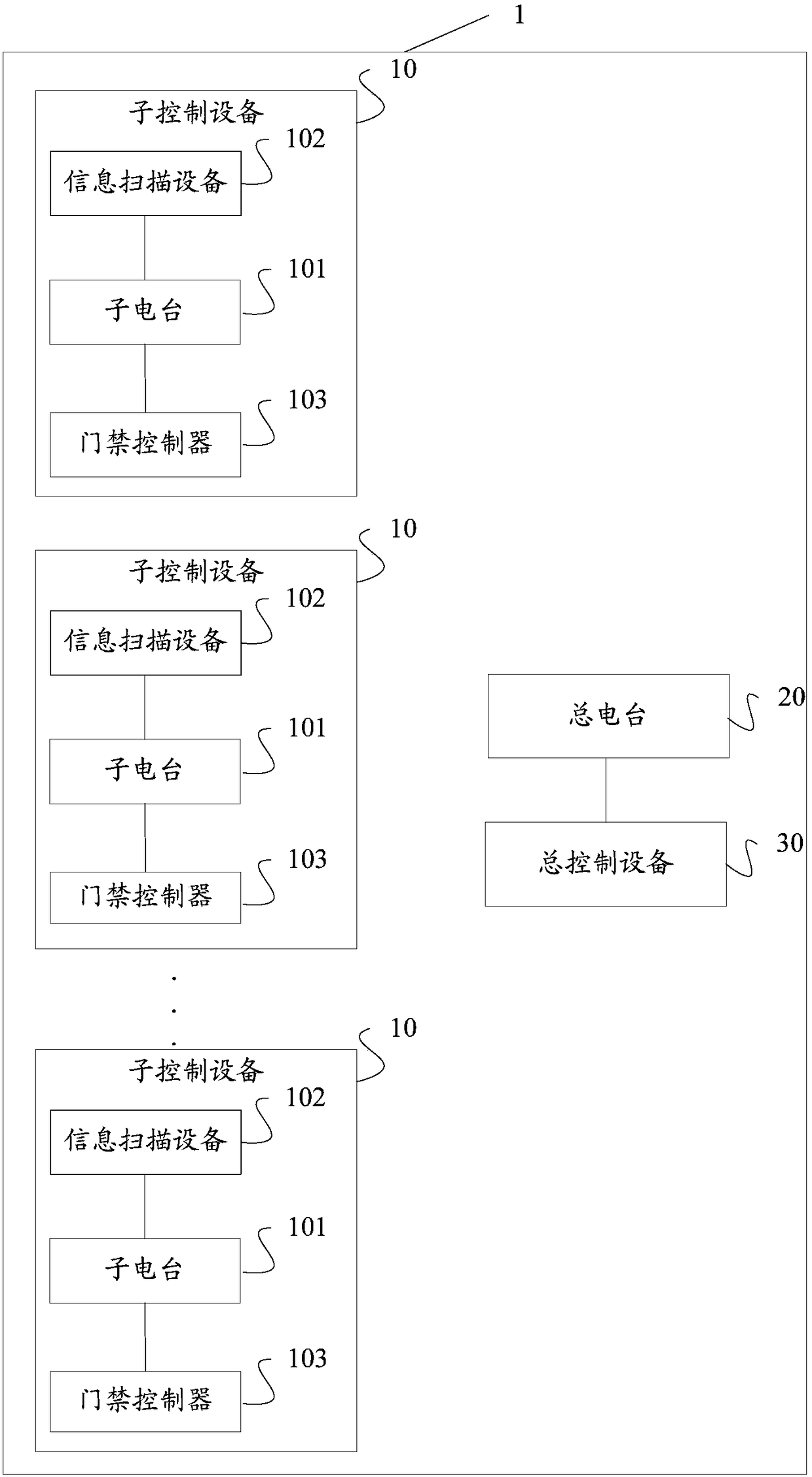
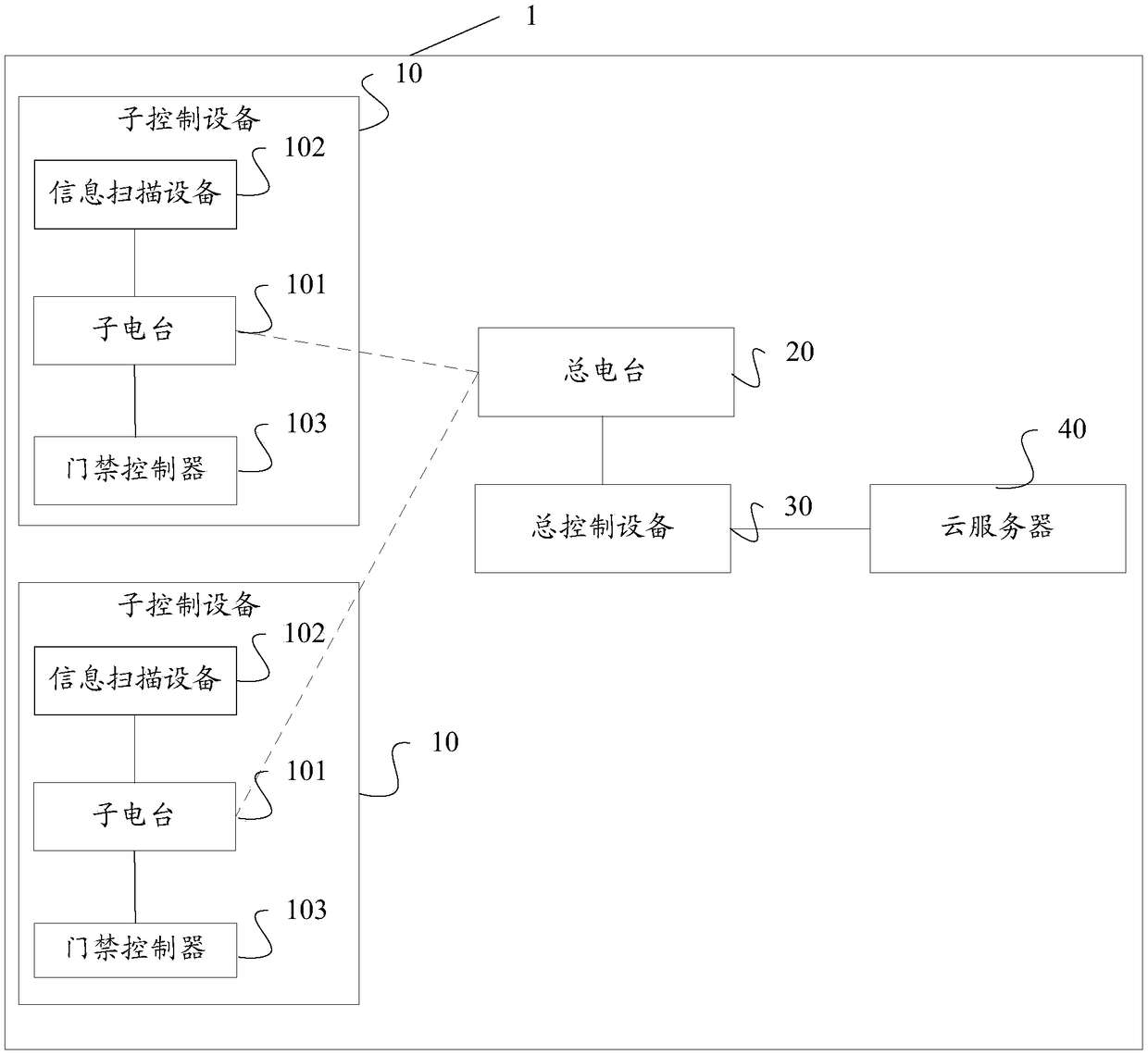
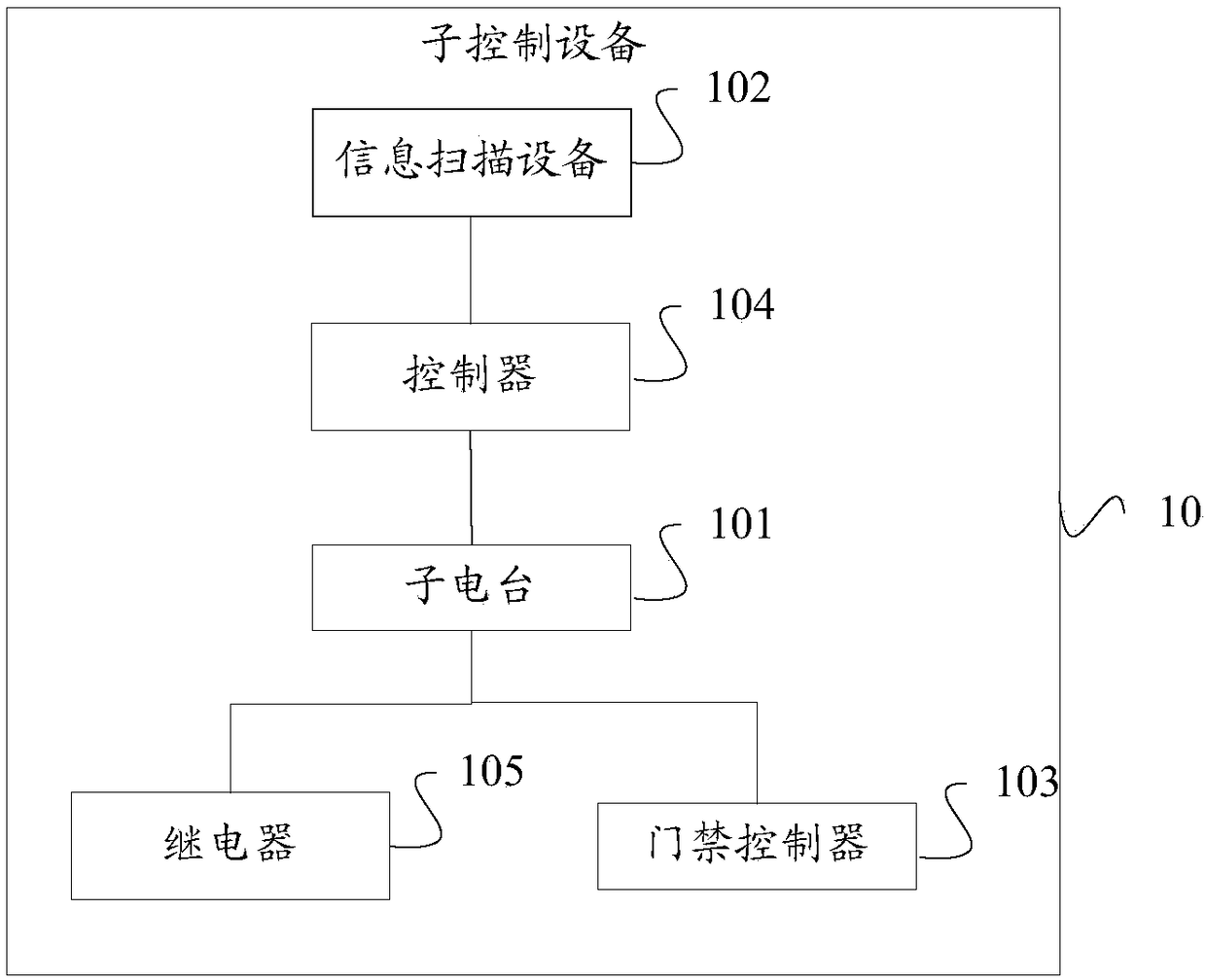
A shared space management system which comprises sun control equipment arranged in each shared space, information scanning equipment, an access control controller coupled with the radio stations, a master radio station and master control equipment. The sub control equipment comprises a sub radio station, the information scanning equipment is suitable for scanning identity recognition information on user terminal equipment to acquire user information and sending the same out through the radio stations, the master radio station is in wireless coupling with each sub radio station in the sub control equipment, and the mster control equipment is in coupling connection with the master radio station communicates with the information scanning equipment and the access control controller through themaster radio station and the sub radio stations. By the system, access control of the shared spaces can be controlled efficiently and safely.
Owner:SHANGHAI DOBE INNOVATION TECH DEV CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com