Loose coupling role authorized-type implementation access control method and system thereof
An access control and loosely coupled technology, applied in the direction of preventing unauthorized use of memory, instruments, electrical digital data processing, etc., can solve the complex syntax and semantics of policy description language, the inability to flexibly adjust security policy configuration, configuration language syntax and rules Complexity and other issues, to achieve the effect of universality, improving access control efficiency, and reducing configuration difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] The present invention will be further described in detail below with reference to the drawings and specific embodiments of the specification.
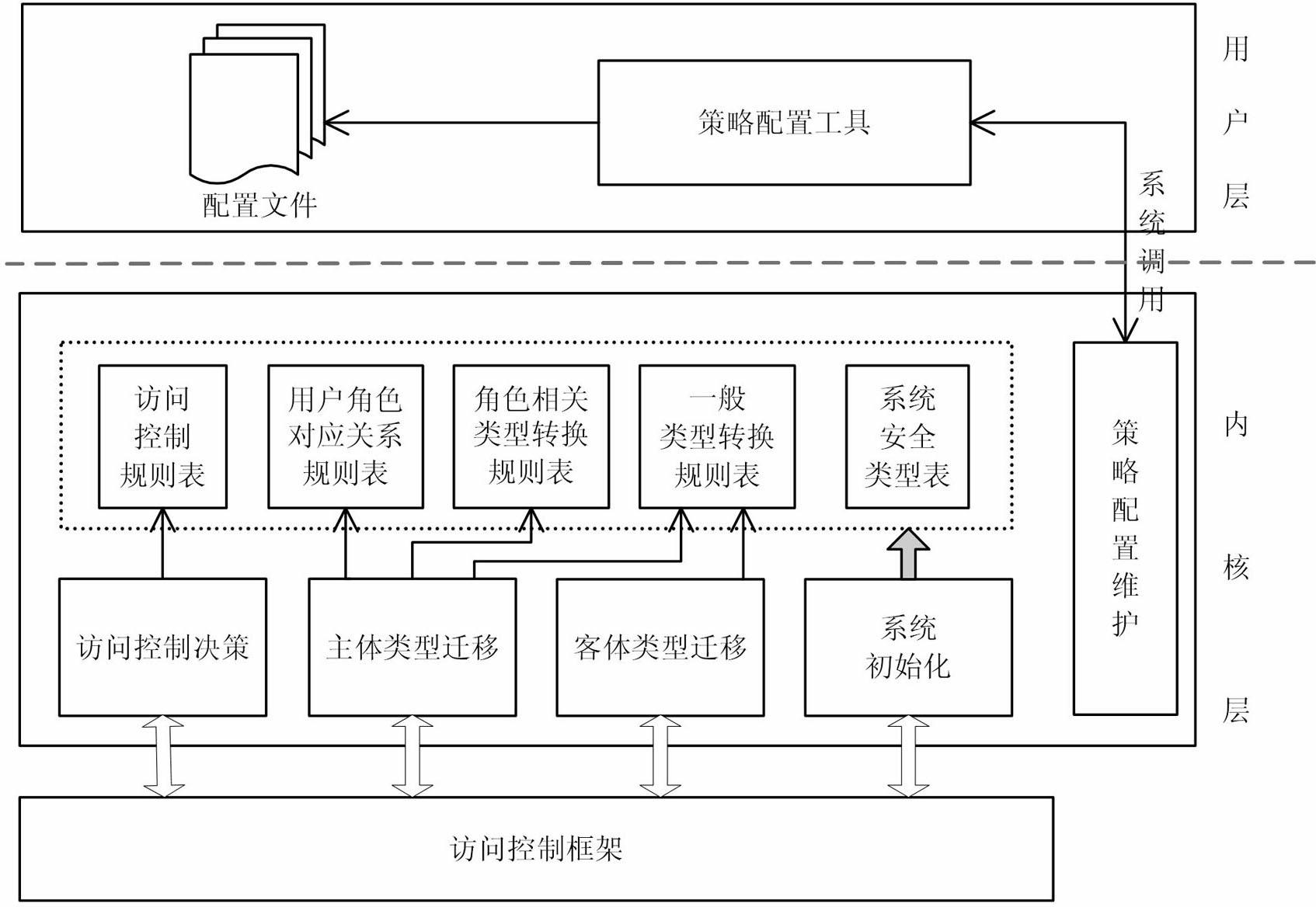
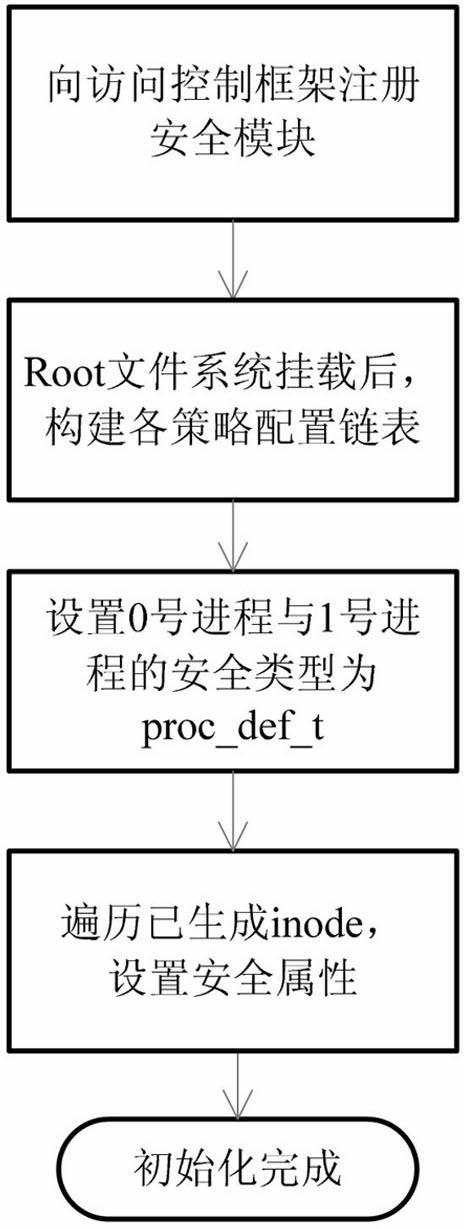
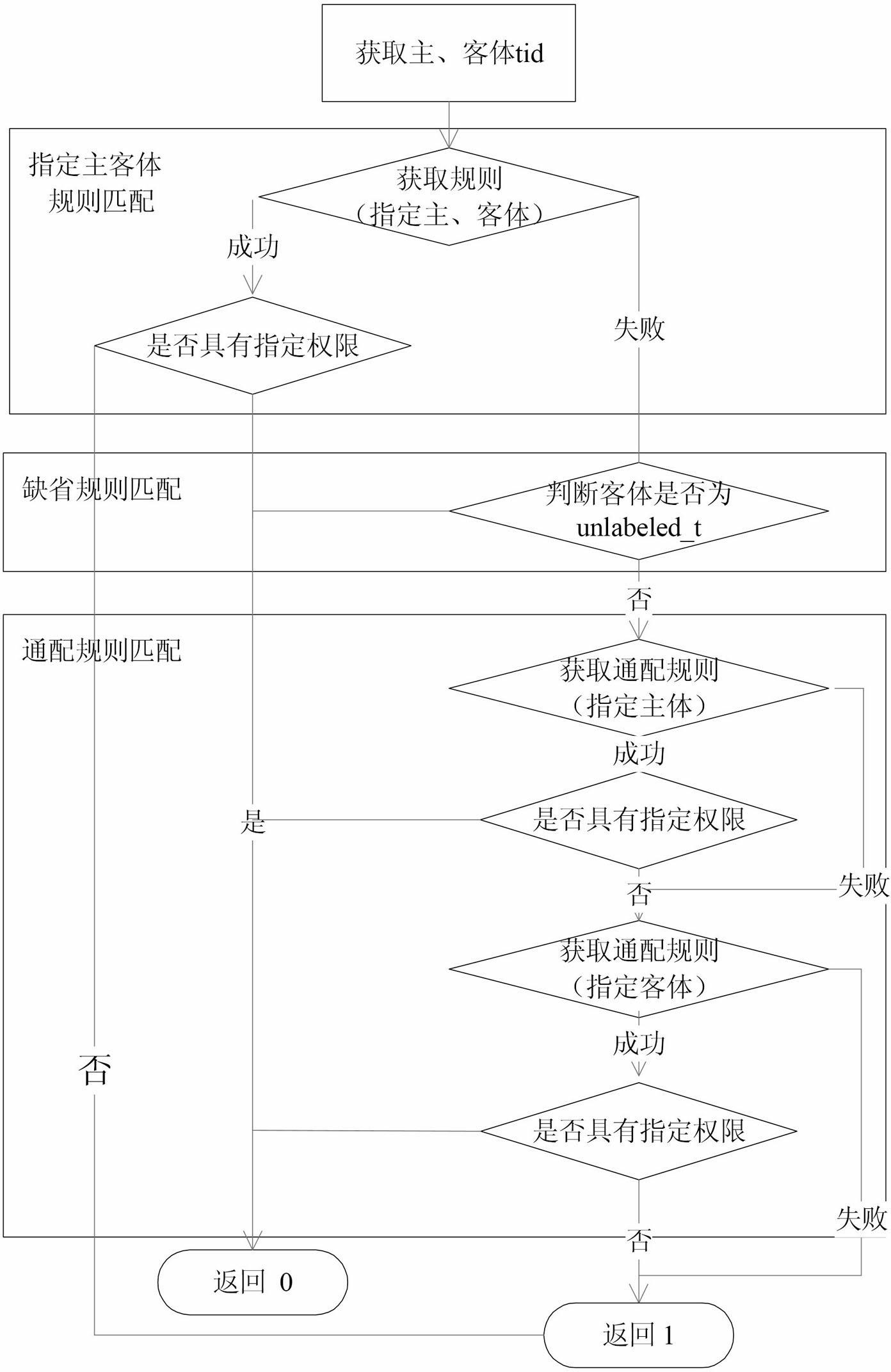
[0049] Such as figure 1 Shown is the structure diagram of the implementation system of the present invention based on the type of operating system access control framework component. The type implementation control system constructed by the present invention is connected to the operating system security access control framework in the form of a security module, mainly receives access control requests from the access control framework, and then obtains a security decision according to the current access policy configuration. The system mainly includes five sub-modules: policy initialization, subject security type migration, object security type migration, access authority check, and policy rule configuration management. The policy initialization module is mainly responsible for registering the security module with the access contro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com