Patents
Literature
157results about How to "Reduce configuration difficulty" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Method for achieving automatic synchronization of multi-source heterogeneous data resources
ActiveCN103617176AAchieve synchronizationReduce configuration difficultySpecial data processing applicationsData synchronizationComputer science
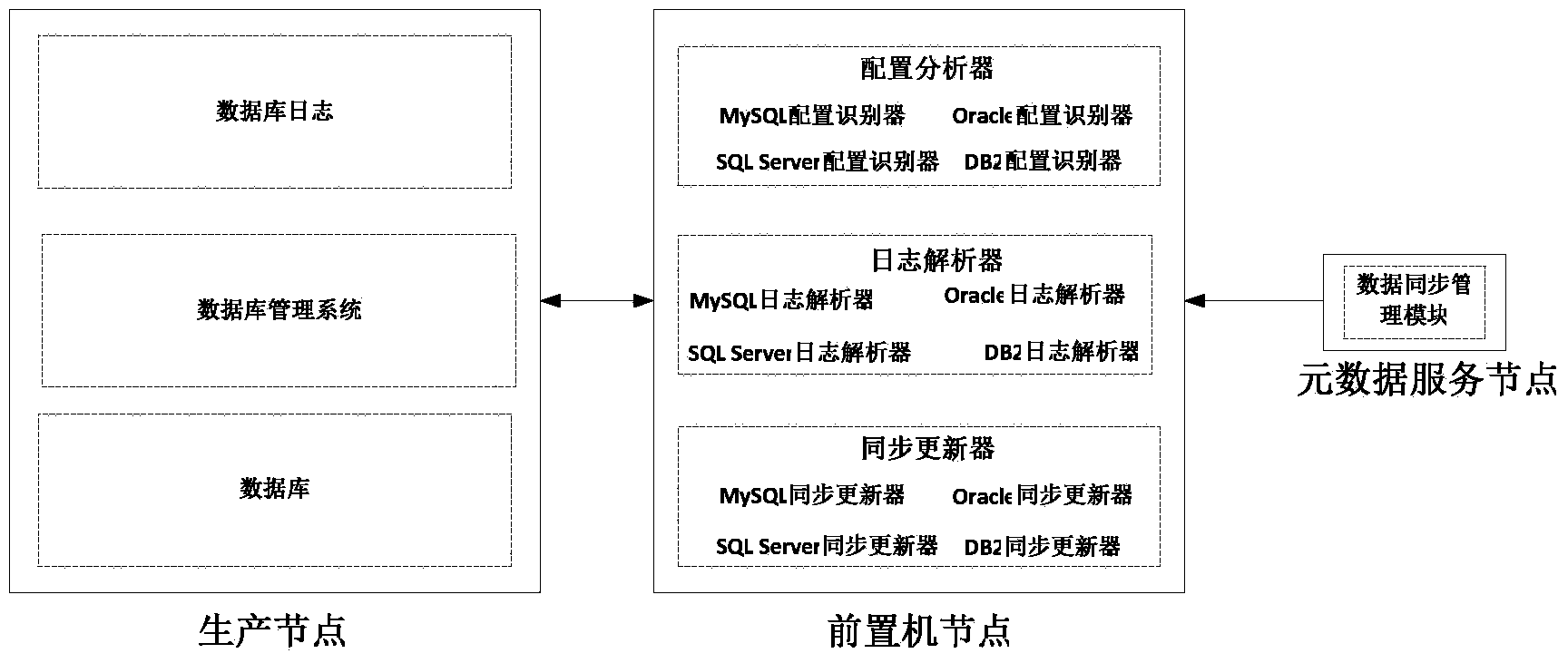
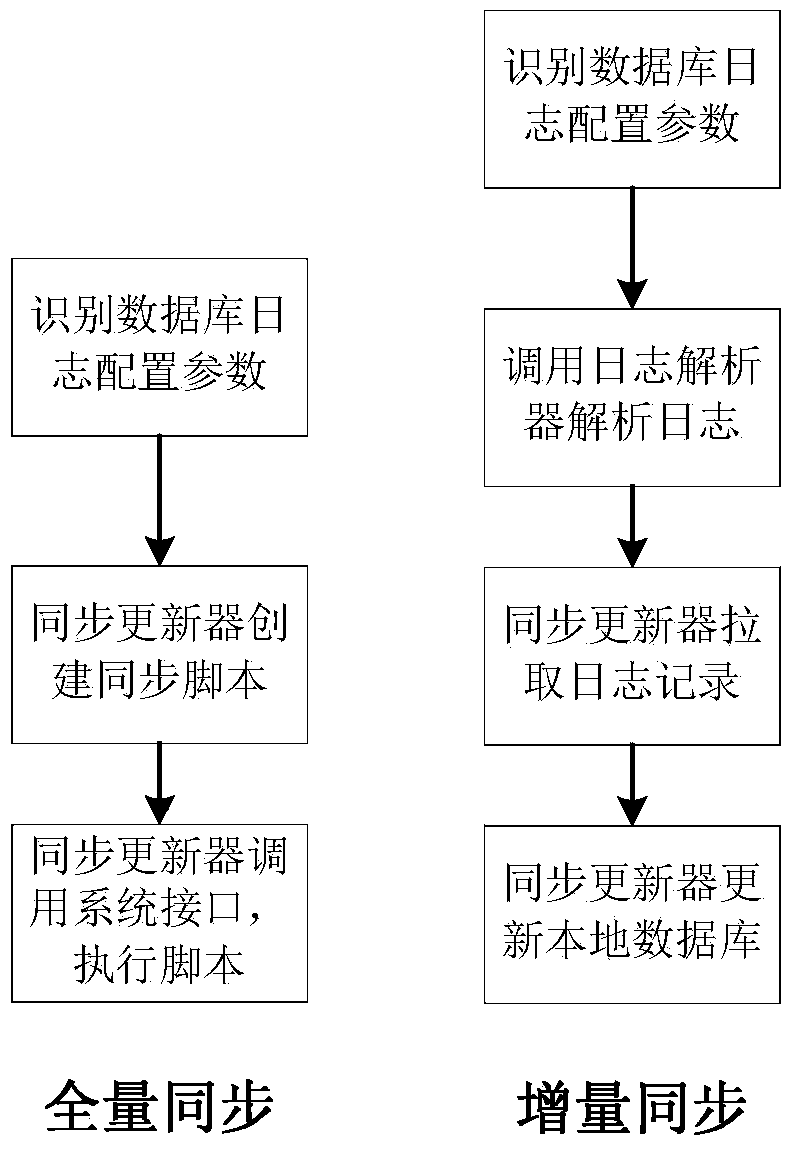
The invention relates to a method for achieving automatic synchronization of multi-source heterogeneous data resources. A metadata service node, a service node and a production node are related in the method, the metadata service node is responsible for storing a data dictionary in a distributed heterogeneous database system, the service node is responsible for analyzing user requests in the distributed heterogeneous database system and carrying out synchronization with a database on the production node periodically, and the production node is responsible for requests such as inquiring and updating in a corresponding production application system, wherein the service node is formed by a configuration recognizer, a blog parser and a data synchronizer, the configuration recognizer is used for analyzing the configuration of a source database on the production node and selecting a feasible synchronizing mode, the blog parser is used for analyzing blogs of different dataset systems and is a component for first-phase preparing work of an increment synchronization mode, and the data synchronizer carries out data synchronization according to the synchronizing mode of the configuration recognizer. The method for achieving the automatic synchronization of the multi-source heterogeneous data resources enables the automatic synchronization of the multi-source heterogeneous data resources to be achieved, and can be used in data resource processing.
Owner:GUANGDONG ELECTRONICS IND INST
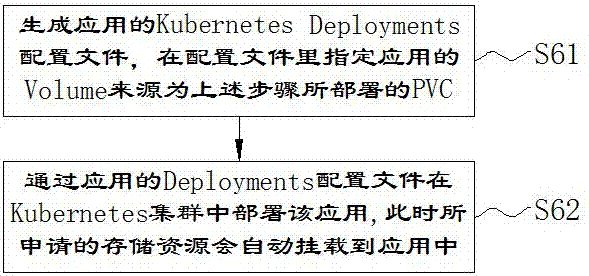
Kubernetes-based method and system for automatic allocation and creation of application storage
InactiveCN107193504APerfect storage resource management functionEasy to useInput/output to record carriersTransmissionOperating systemStorage resource management
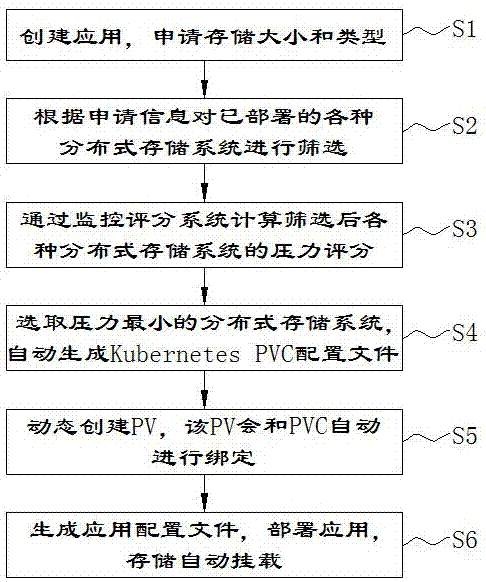
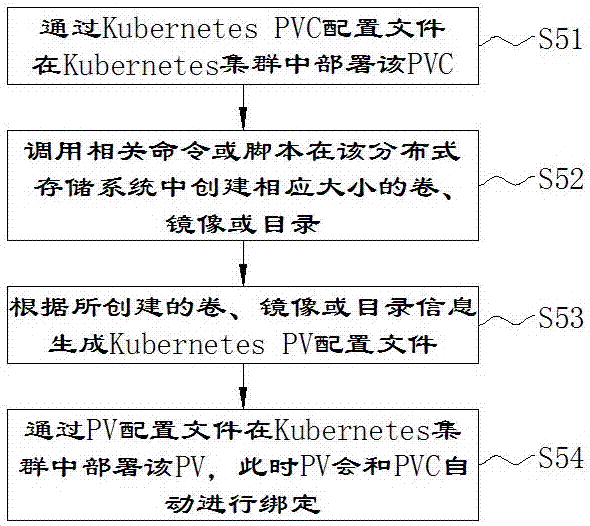
The present invention provides a Kubernetes-based method and system for automatic allocation and creation of application storage. By using a storage size and type information required by an application, various deployed distributed storage systems are screened; by using a monitoring scoring system, a pressure score of each distributed storage system that meets a requirement is calculated; a distributed storage system with a smallest pressure is selected; a Kubernetes PVC configuration file is generated; the PVC is deployed and a PV is dynamically created, and the PV is bound with the PVC; and finally an application configuration file is generated, and the PVC is designated as a Volume source, and the application is deployed, so that an applied storage resource is automatically mounted to the application. The method and system provided by the present invention are used to improve a storage resource management function of Kubernetes, and solve the problem that the application on a Kubernetes cluster is automatically mounted with persistent storage, and make creation of application storage more convenient and efficient.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
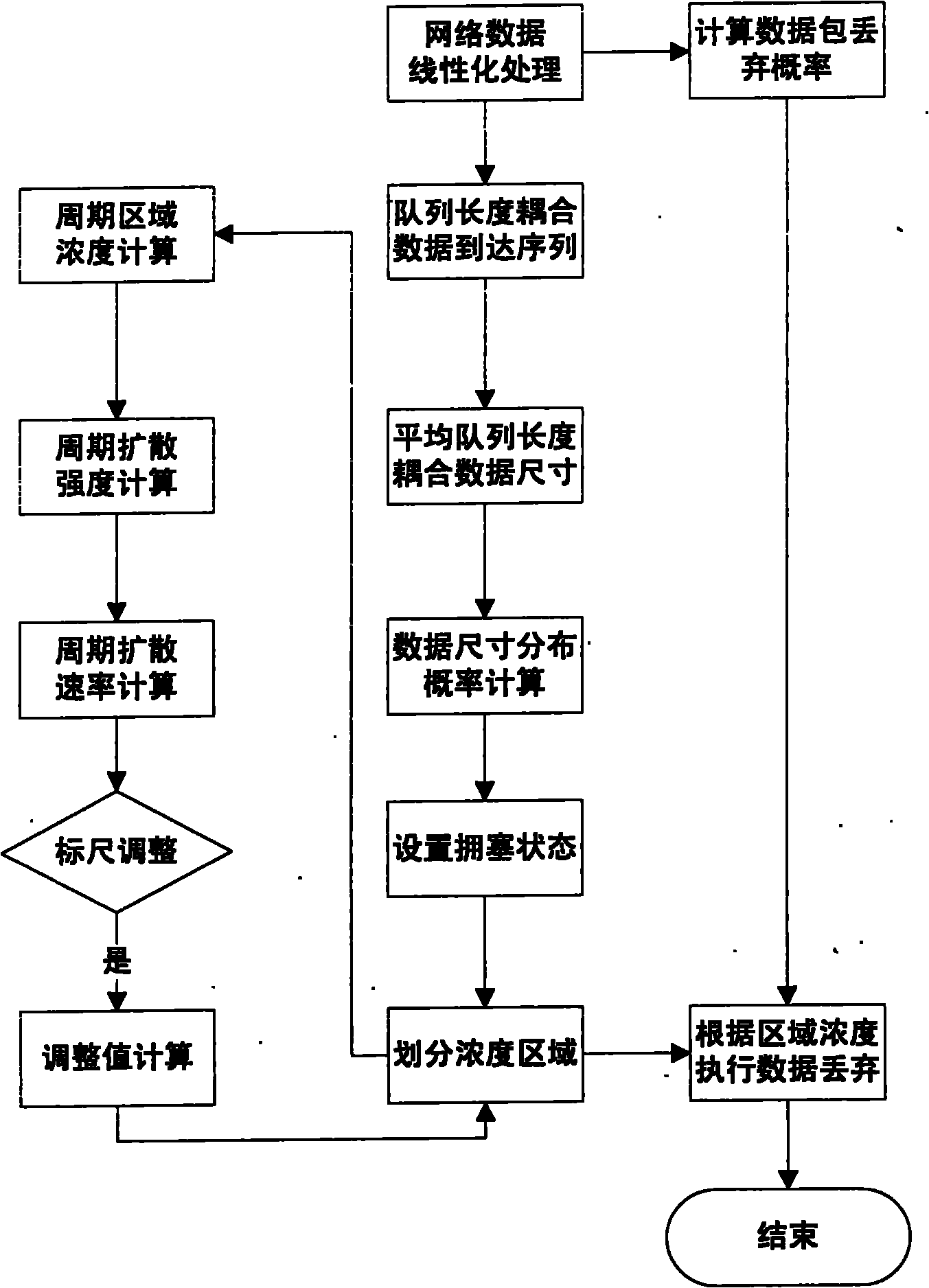
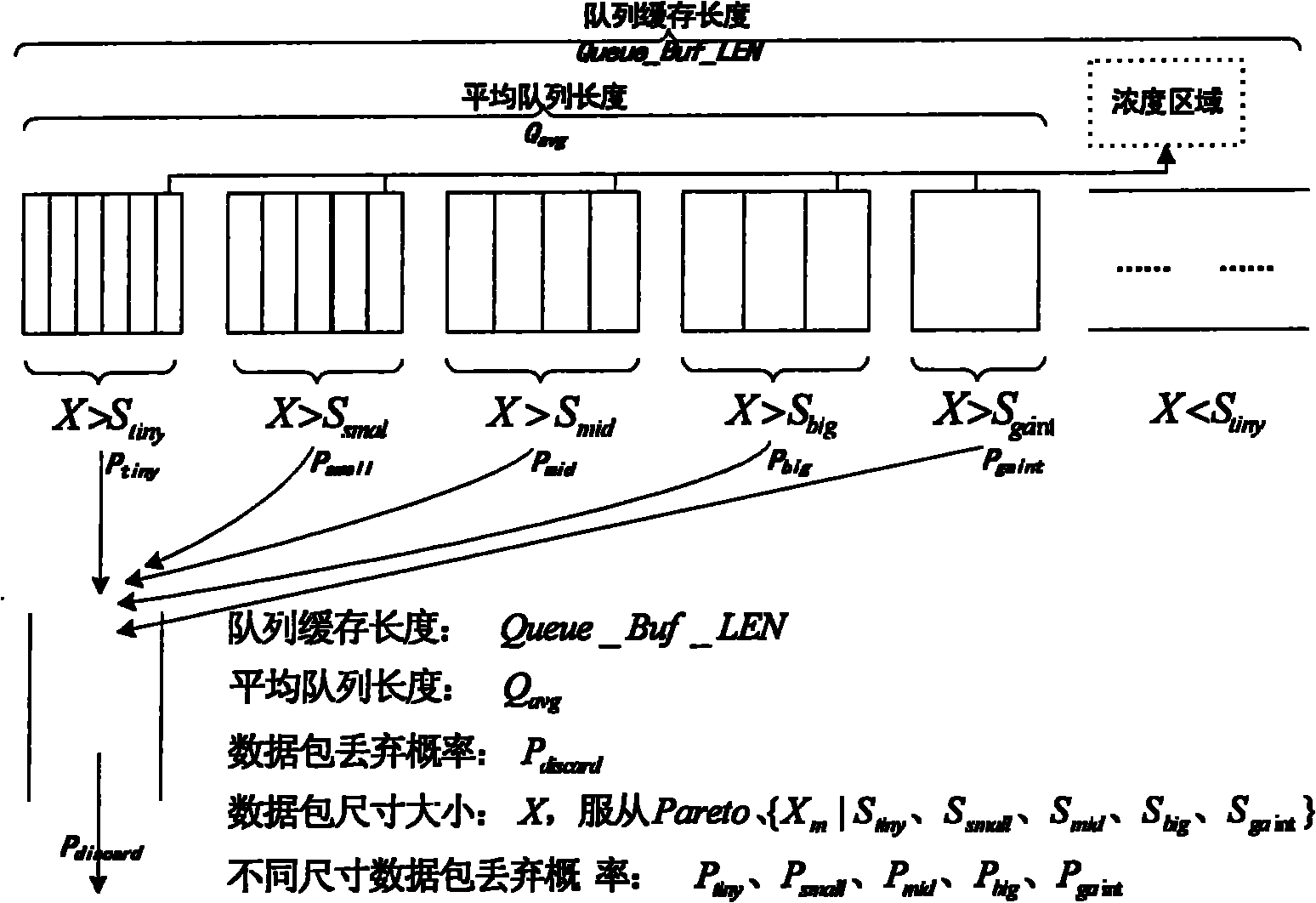
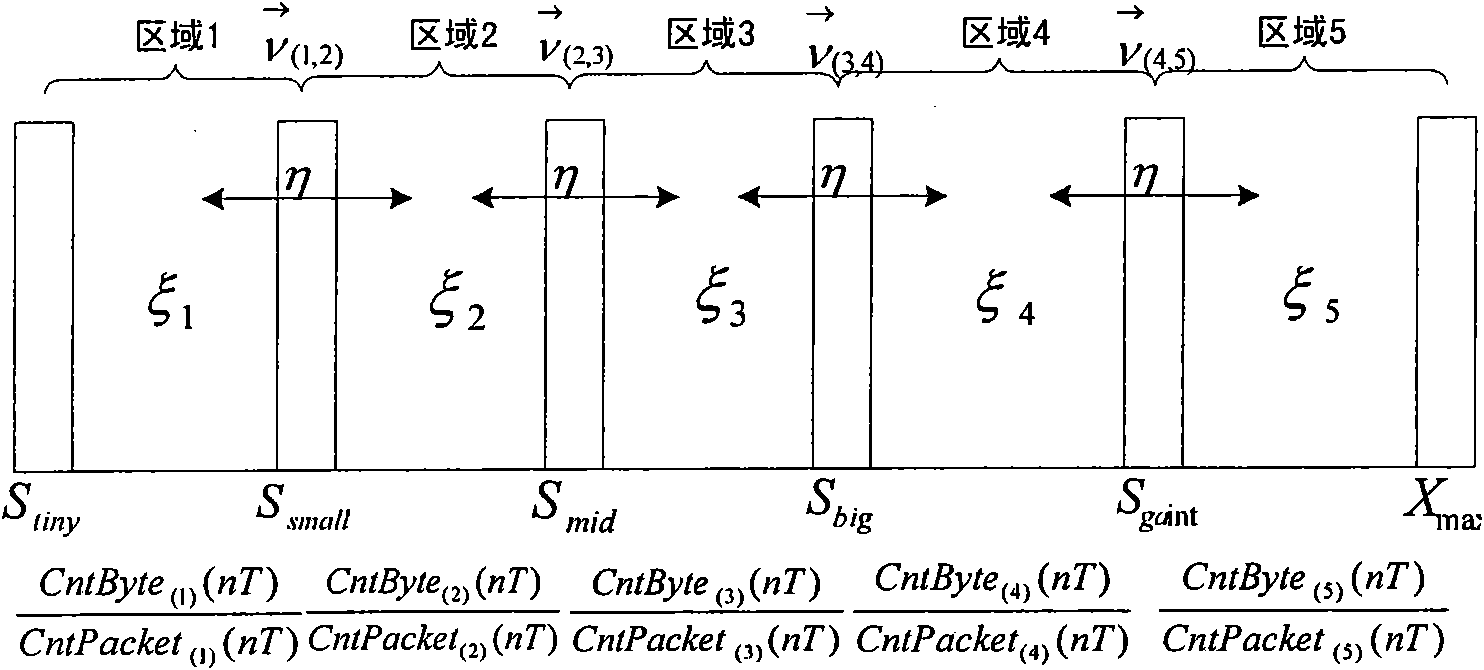
RED-based network congestion control algorithm
InactiveCN101958833AEliminate queue cacheEliminate the drop probability parameter termData switching networksPacket lossClassification methods
The invention discloses an RED-based network congestion control algorithm. The algorithm comprises the following steps of: segmentally processing different congestion states by introducing a fifth-order classification method in the statistics, dividing the network congestion states by using five indexes of weak, slight, medium, serious and severe, and dividing the average queue utilization rate into five regions, each of which corresponds to a network congestion state; calculating the discard probability of the average data size of the regions by utilizing a liner function of a data size distribution probability; and discarding data packets in corresponding regions in the probability according to the current congestion state to increase the available space of queues so as to avoid the network congestion. In the algorithm, original ten configuration parameter projects of the conventional algorithm are reduced to two, so that the configuration difficulty is obviously reduced. Under the same network scene, the average queue cache utilization rate is about 25 percent higher than that of an RED derivative algorithm. The algorithm improves the network congestion control effect, can flexibly adjust the packet loss number according to the congestion degree, and effectively inhibit network jitter.
Owner:云南省科学技术情报研究院
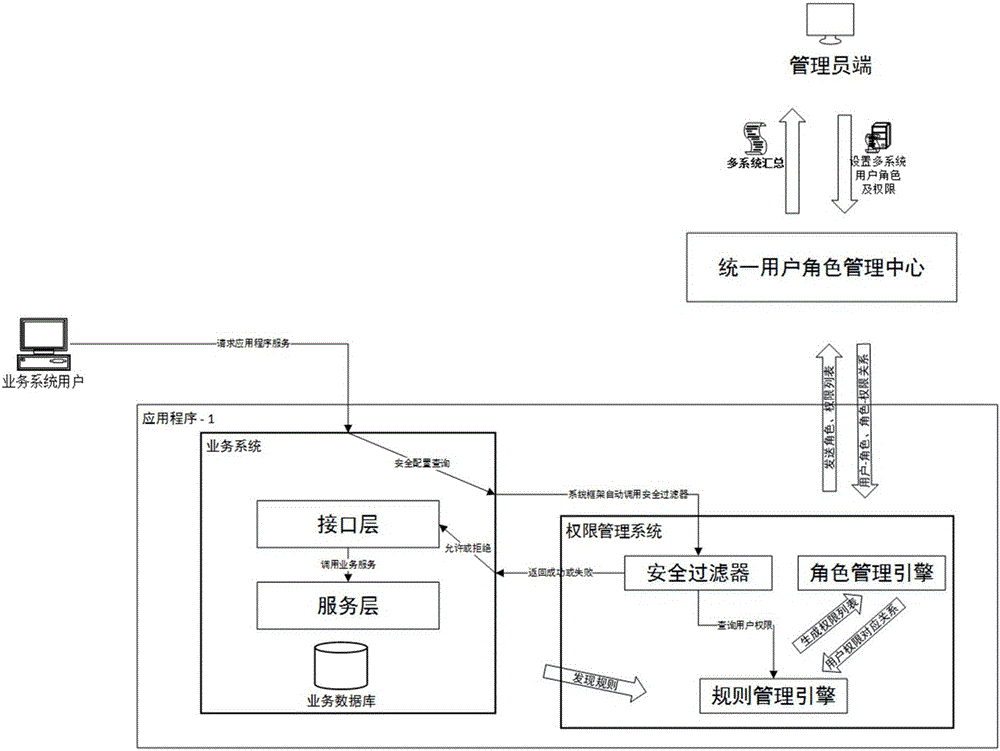
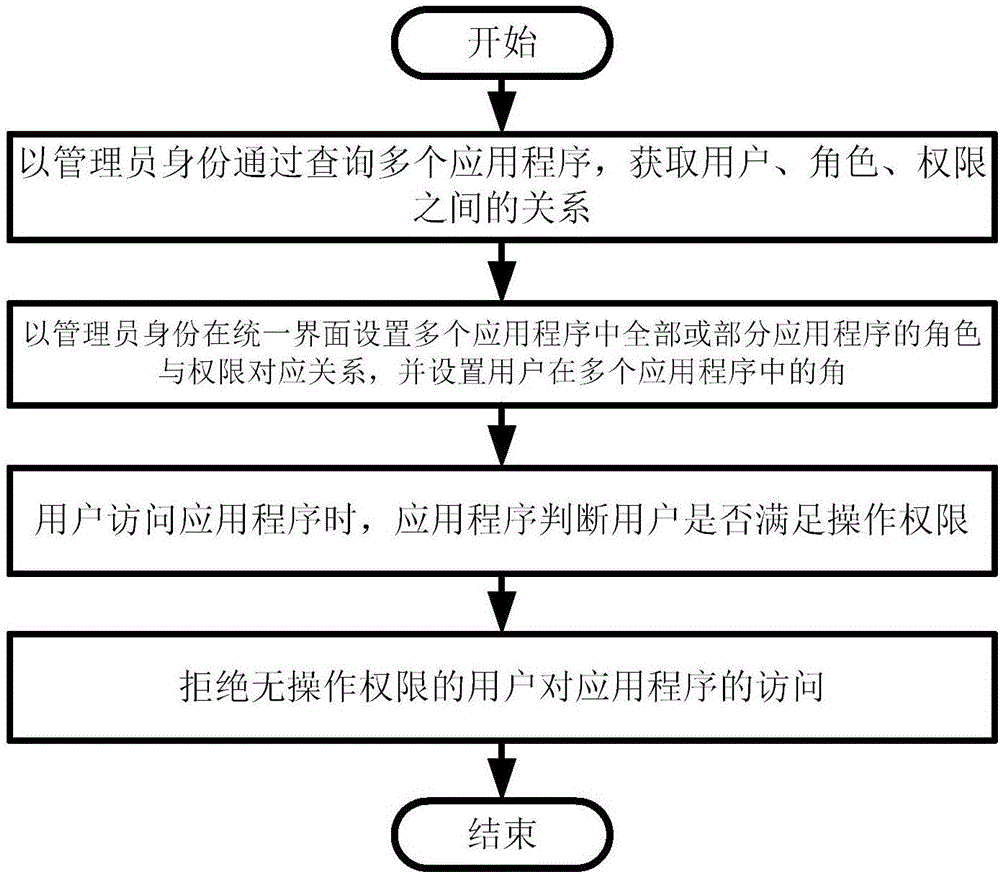
Multi-system role authority management method and system based on unified interface
ActiveCN106790001AReduce complexityImprove reliabilityData switching networksPartial applicationApplication software
The invention provides a multi-system role authority management method and system based on a unified interface. The method comprises the following steps: step 1: inquiring multiple application programs as an administrator to obtain the relationship between a user, a role and authority; step 2: setting a corresponding relation of roles and authority of all or a part of application programs in the multiple application programs on the unified interface as the administrator, and setting the roles of the user in the multiple application programs; step 3: when the user accesses the application programs, judging whether the user has operation authority by the application programs; and step 4: refusing the user having no operation authority to access the application programs.
Owner:CETC CHINACLOUD INFORMATION TECH CO LTD
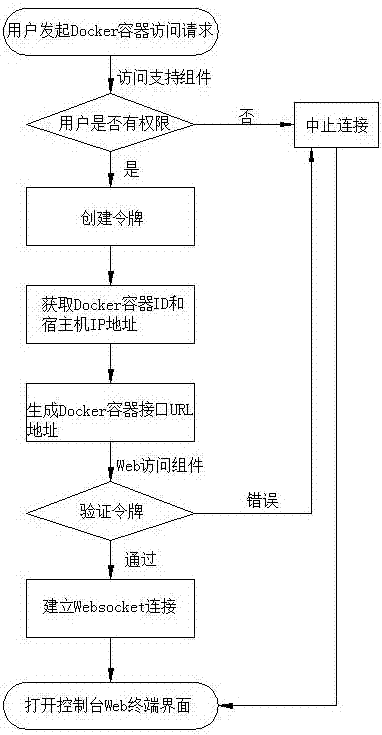
Method and system of Web for accessing Docker container
ActiveCN107493344AImplement permission controlConvenient and flexible accessTransmissionUser PrivilegeWebSocket
The invention discloses a method and a system of a Web for accessing a Docker container, and belongs to the technical field of cloud computing. The technical problems needing to be solved are that an independent SSH service for remote login and access still needs to be built for the Web to access the Docker container remotely, configuration of parameters such as a user name and a password is needed, and the remote access process is tedious. By adoption of the technical scheme, the method comprises the steps of finding a to-be-accessed Docker container at a Web page and initiating an access request by a user; judging user authority by an access support assembly; if the user has the authority, building a token for Docker container access and returning the token to the user; by the access support assembly, obtaining the ID of the Docker container and the IP address of a host machine where the Docker container is, and generating an URL address of the Docker container interface; verifying the token by a Web access assembly, and building Websocket connection through the URL address of the Docker container interface if the token passes the verification; and opening the Web page containing a console terminal of the Docker container through the Web access assembly. The method and the system of the Web for accessing the Docker container can still realize authority control on Docker container access without enabling an sshd course.
Owner:SHANDONG LANGCHAO YUNTOU INFORMATION TECH CO LTD
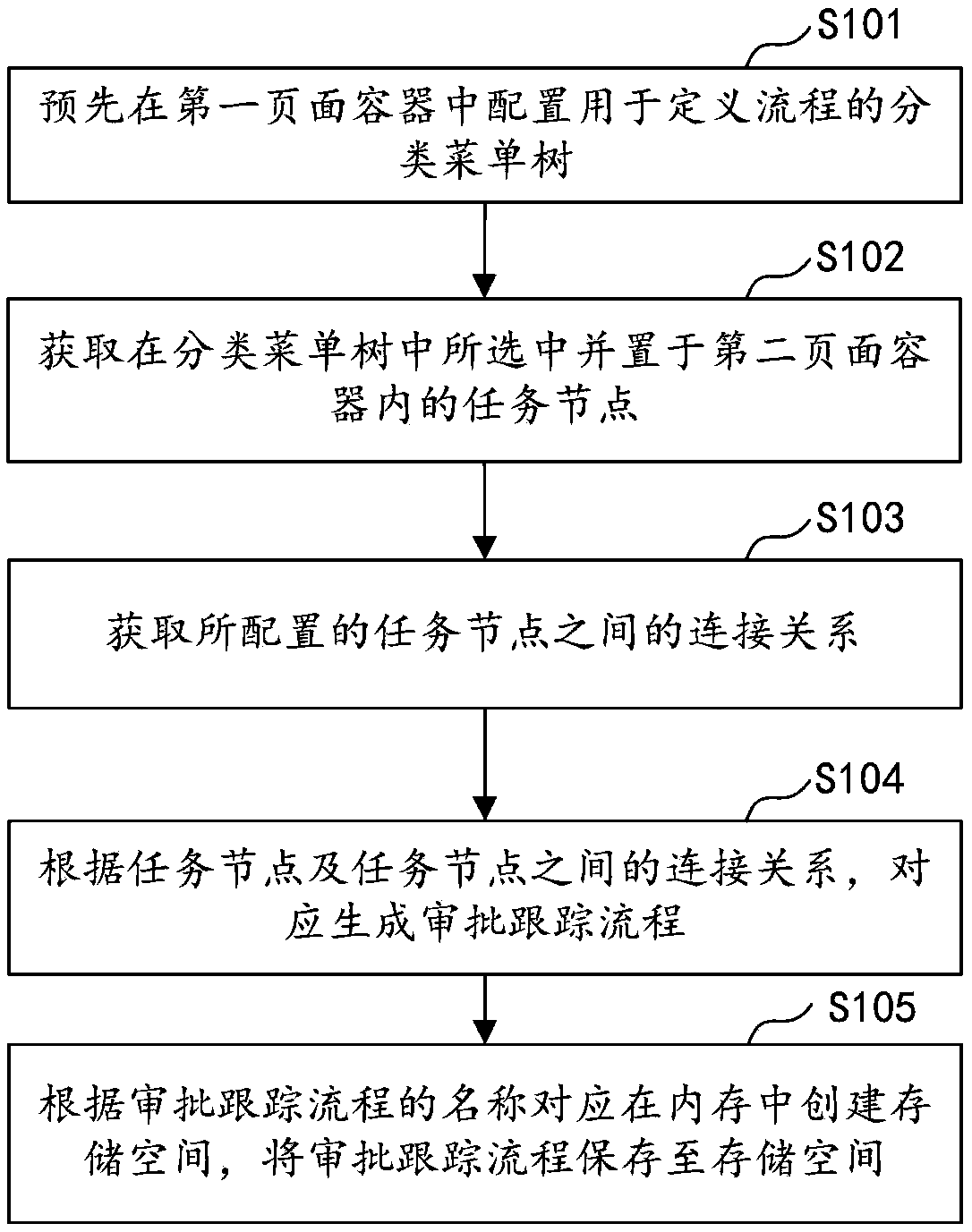
Visual flow configuration method, apparatus, computer device, and storage medium
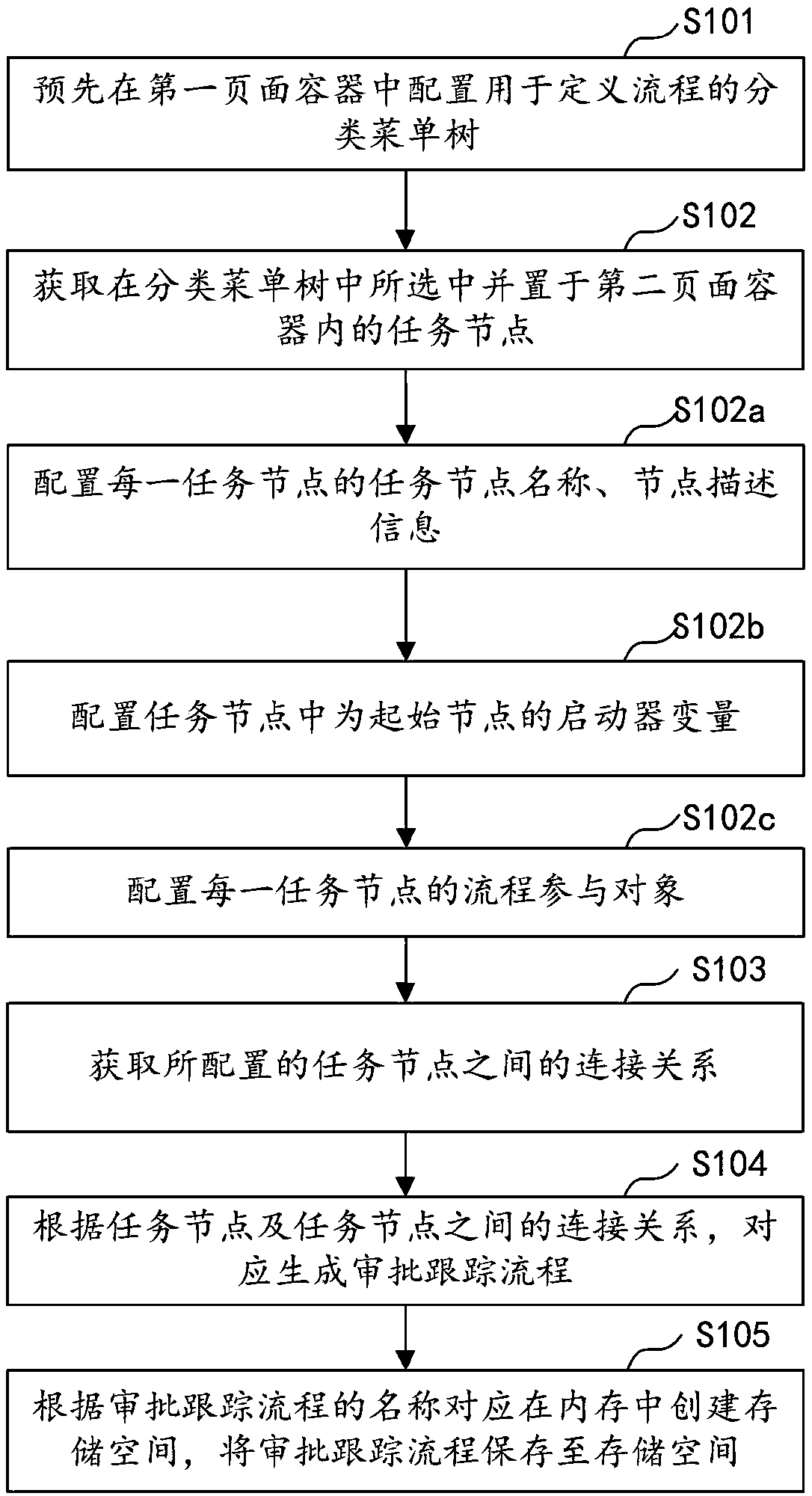
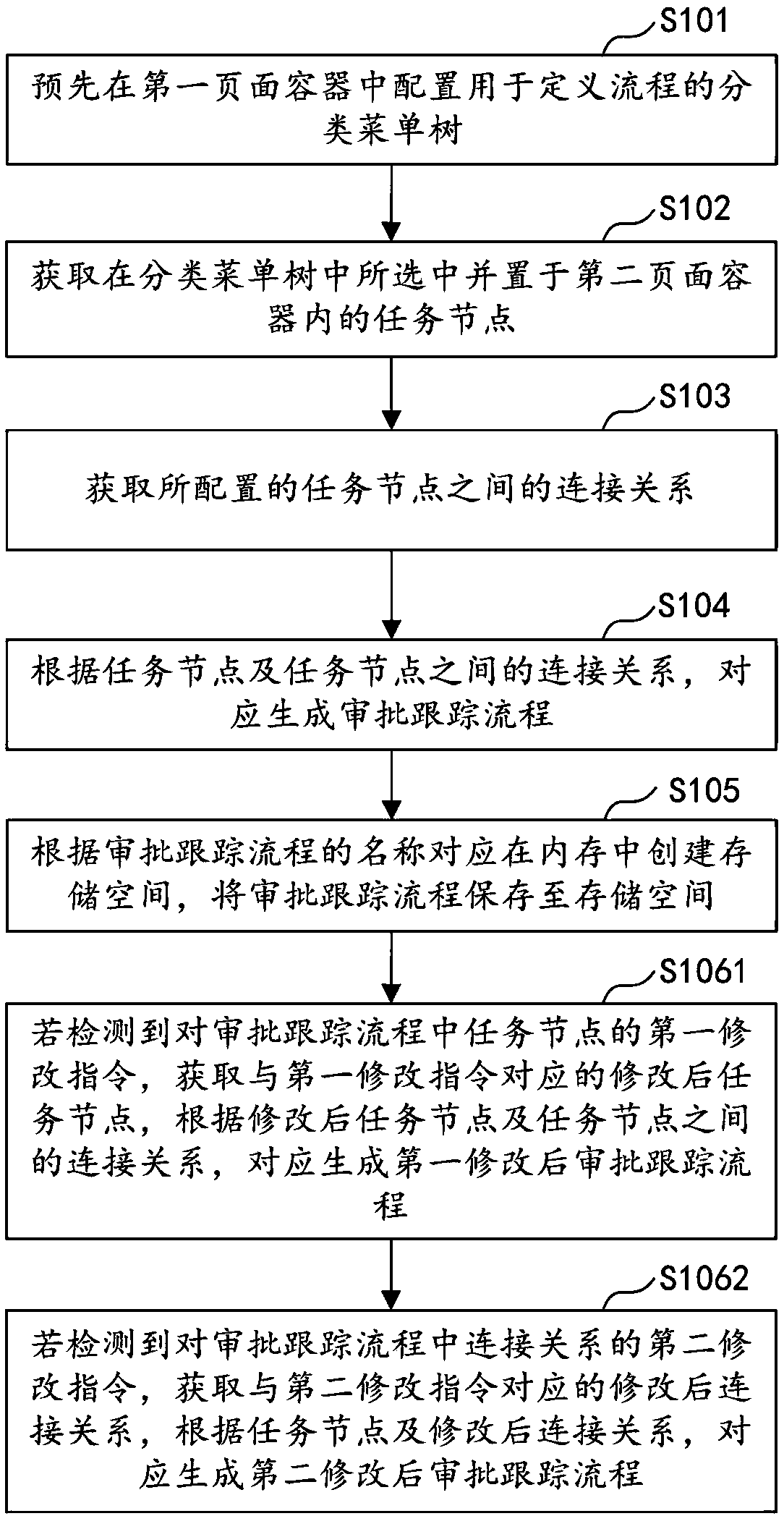
PendingCN109409835AImplement configurationImprove configuration efficiencyOffice automationProcess configurationWorkflow engine
The invention discloses a visual flow configuration method, a device, a computer device and a storage medium. The method comprises the following steps of: configuring a classification menu tree for defining a process in a first page container in advance; acquiring a task node selected in the classification menu tree and placed in a second page container; getting the connection relationship betweenthe configured task nodes; according to the task node and the connection relationship between the task nodes, the approval tracking process is generated correspondingly. Creates a storage space in memory based on the name of the approval tracking process and saves the approval tracking process to the storage space. The method configures the connection relationship between task nodes and task nodes according to the actual service requirements in the workflow engine, realizes the configuration of the visual approval tracking process, improves the configuration efficiency and reduces the configuration difficulty.
Owner:CHINA PING AN PROPERTY INSURANCE CO LTD
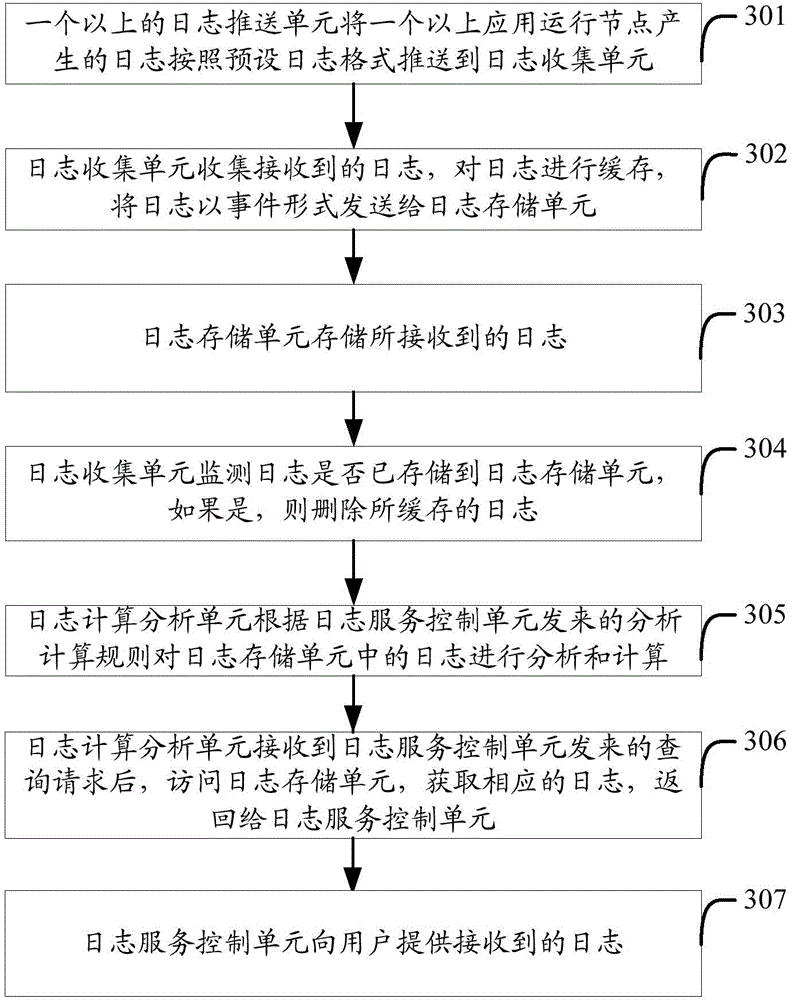
Log management system and implementation method
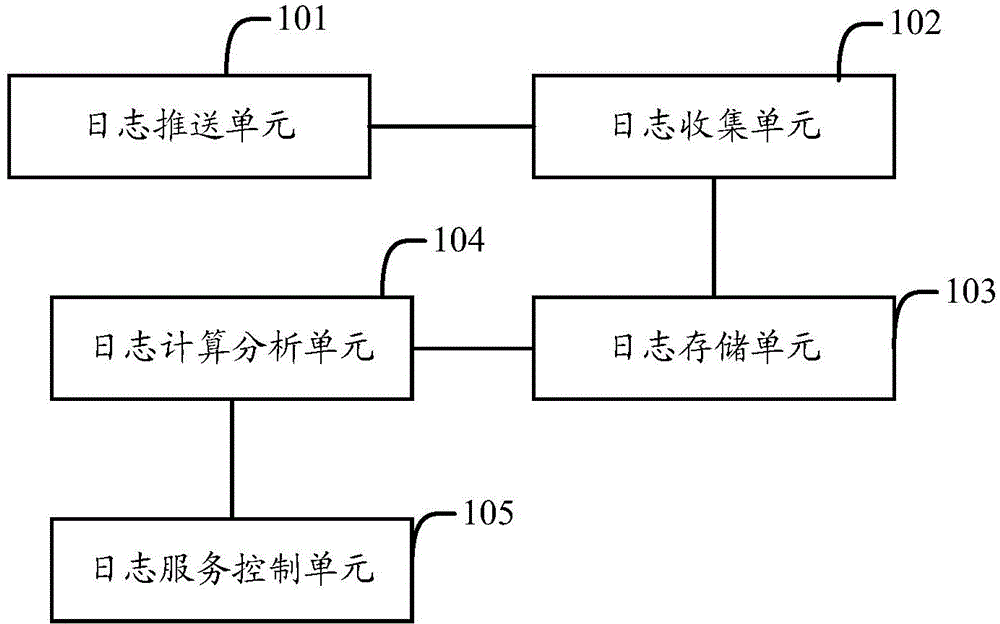
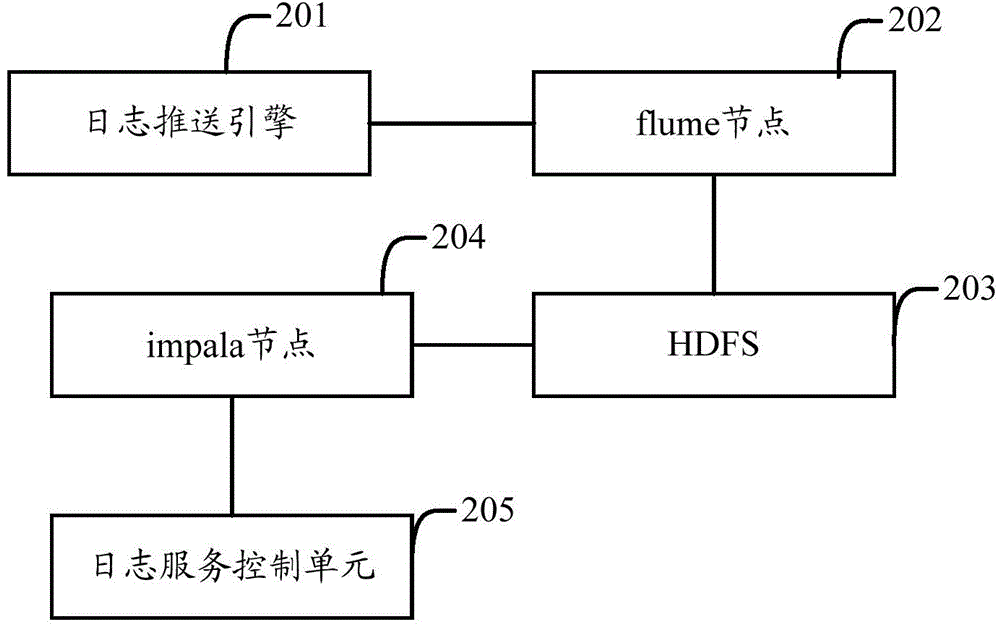
InactiveCN104579777ARealize unified collectionSolve the problem of decentralized managementData switching networksLog managementService control
The invention provides a log management system and an implementation method. The system comprises one or more log pushing units, a log collecting unit, a log calculation and analysis unit and a log service control unit, wherein the log pushing unit pushes logs generated by one or more application operation nodes to the log collecting unit; the log collecting unit is used for collecting received logs, caching the logs, sending the logs to a log storage unit in an event form and monitoring whether the logs have been stored in the log storage unit, and if the logs have been stored in the log storage unit, the cached logs are deleted; the log calculation and analysis unit is used for analyzing and calculating the logs stored in the log storage unit according to analysis and computation rules, having access to the log storage unit after receiving an inquiry request sent by the log service control unit, obtaining a corresponding log and returning the corresponding log to the log service control unit; the log service control unit sends the analysis and computation rules to the log calculation and analysis unit, sends the inquiry request and provides the received logs for users. Problems generated by decentralized management of logs can be solved according to the log management system and the implementation method.
Owner:INSPUR SOFTWARE CO LTD
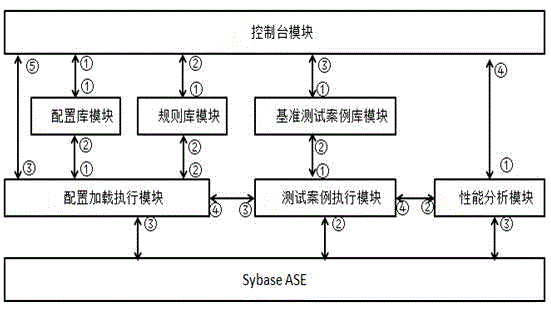
Configuration optimization system and method for Sybase ASE database
ActiveCN105138621AReduce configuration workloadEliminate explosionDatabase management systemsSpecial data processing applicationsTest performanceConfiguration optimization
The invention discloses a configuration optimization system and method for a Sybase ASE database, pertaining to the field of database configuration. The method comprises following steps: expressing expert knowledge configured by the Sybase ASE database through a configuration library, a rule base, a case library for benchmark tests; starting, stopping and dynamically adjusting parameters by configuring a loading and executing module to directly drive the Sybase ASE database; utilizing the case library for benchmark tests to test performance of the case library under specific workload; obtaining a group of configuration parameter combination in accord with the user requirement by continuously adjusting input of the configuration library and the rule base for performance analyses; and eliminating the explosion of number for parameter combinations caused by simple permutation and combination by generating combinations of configuration parameters via guidance of rules in order to greatly decrease workload for configuration of the Sybase ASE database, reduce configuration difficulty and provide guiding effect of optimizing performance of the ASE database.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
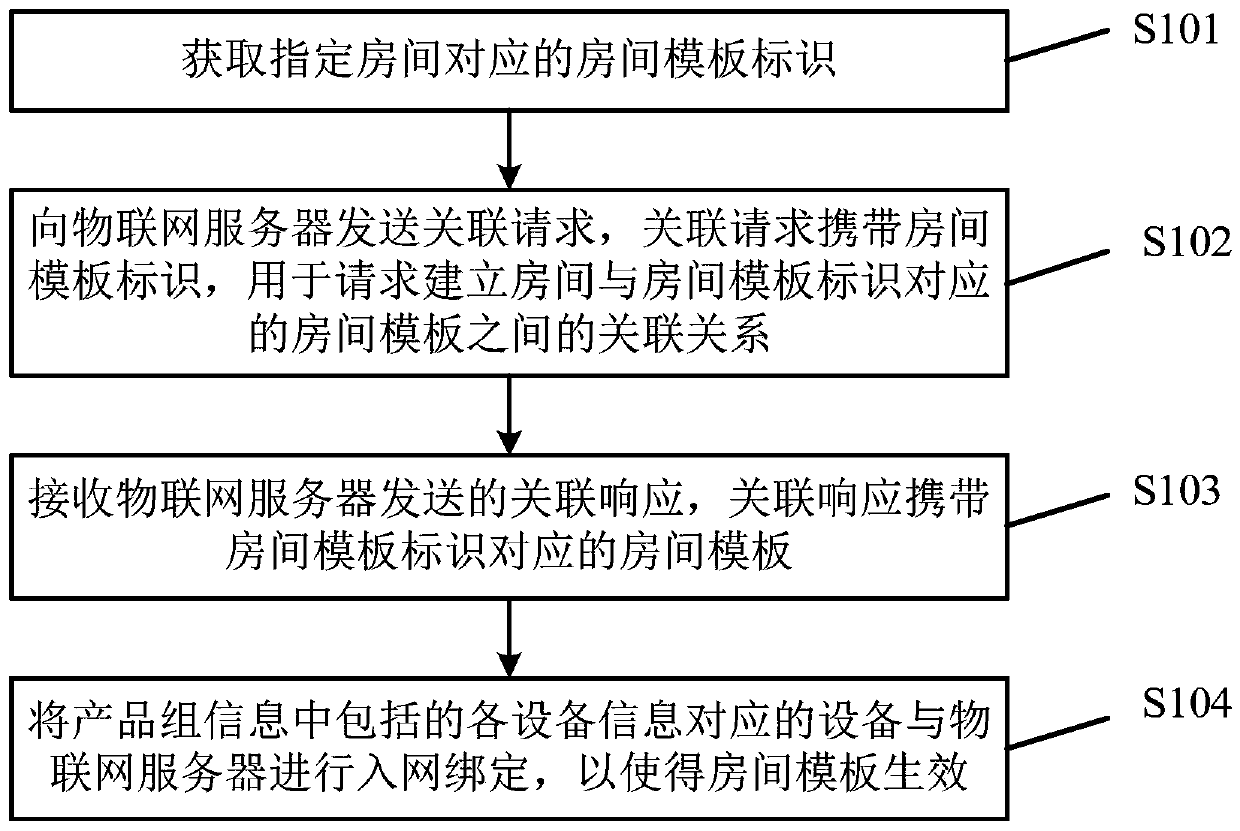
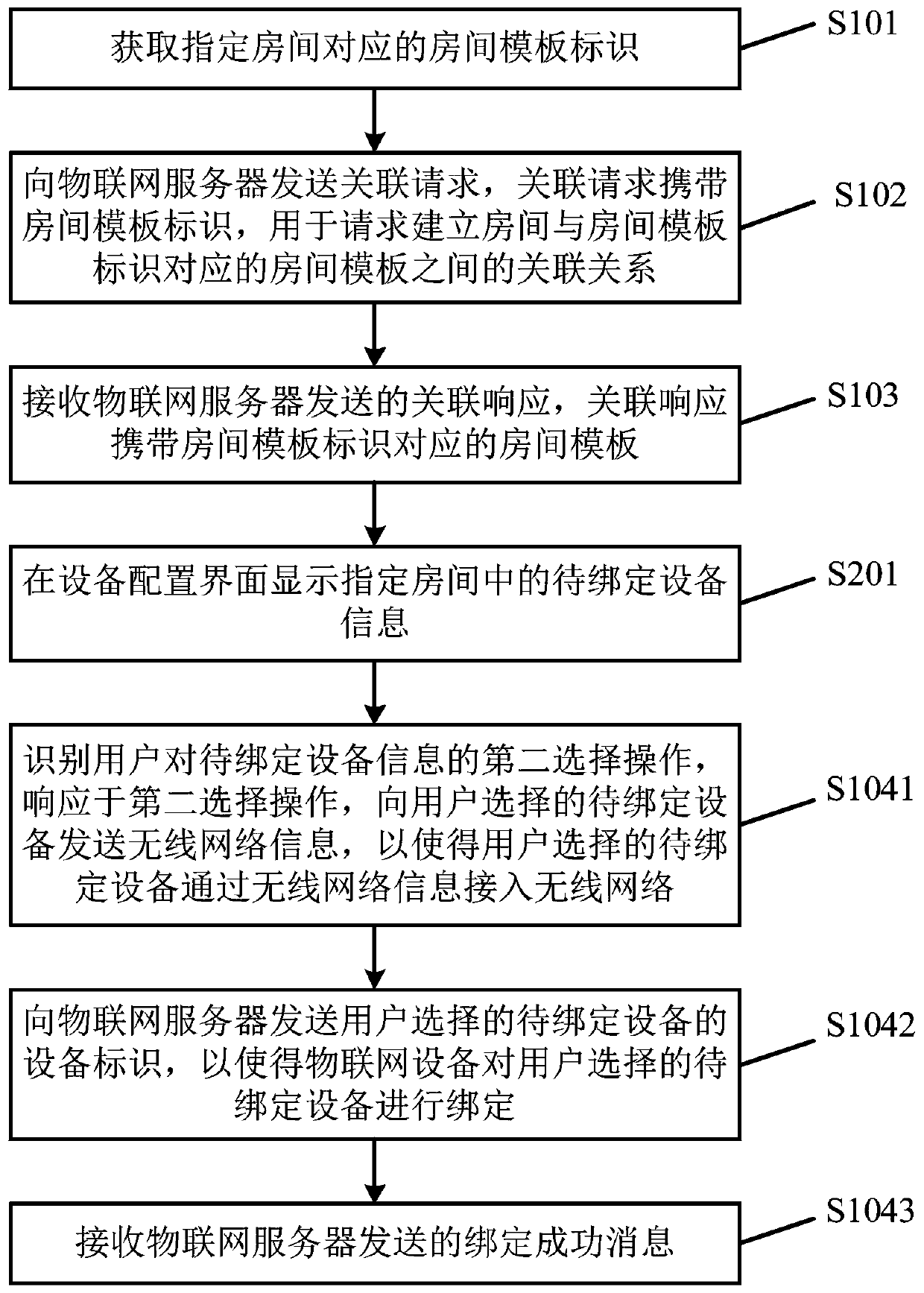
Smart home configuration method and device, electronic equipment and medium
ActiveCN111447123AShort implementation periodReduce configuration difficultyHome automation networksVoice TrainingInternet of Things
The embodiment of the invention provides a smart home configuration method and device, electronic equipment and a medium, and relates to the technical field of the Internet of Things. The embodiment of the invention comprises the following steps: obtaining a room template identifier corresponding to the specified room, sending an association request to an Internet of Things server, wherein the association request carries a room template identifier, and is used for requesting to establish an association relationship between a specified room and a room template corresponding to the room templateidentifier; receiving an association response sent by the Internet of Things server, wherein the association response carries a room template corresponding to the room template identifier, and the room template comprises product group information, a plurality of pieces of preset scene information and voice training information; and then performing network access binding on equipment correspondingto each piece of equipment information included in the product group information and the Internet of Things server to enable the room template to take effect. The implementation period of smart homecan be shortened, and the configuration difficulty is reduced.
Owner:BEIJING KINGSOFT CLOUD NETWORK TECH CO LTD
Routing information generating method, system and message routing method and system
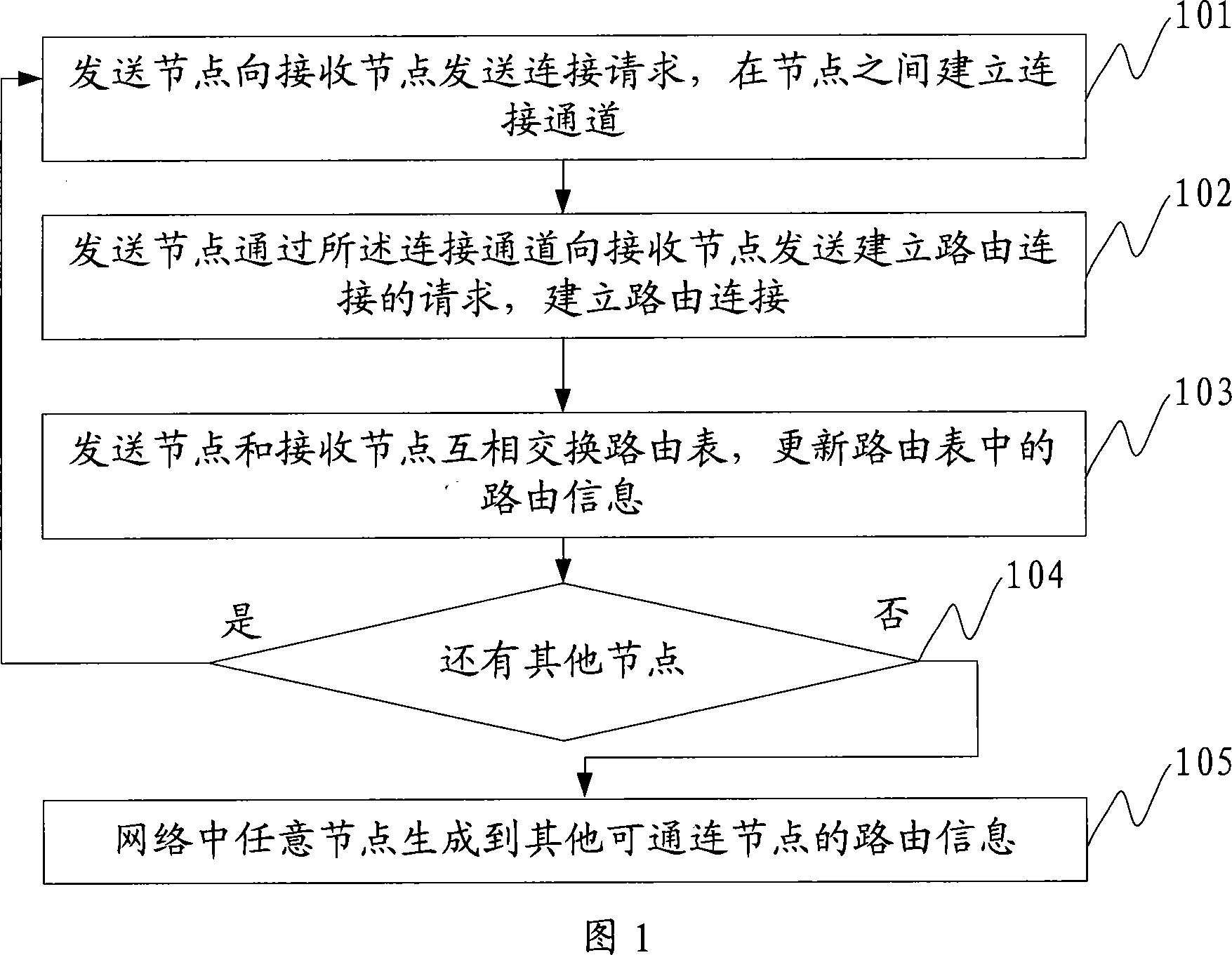
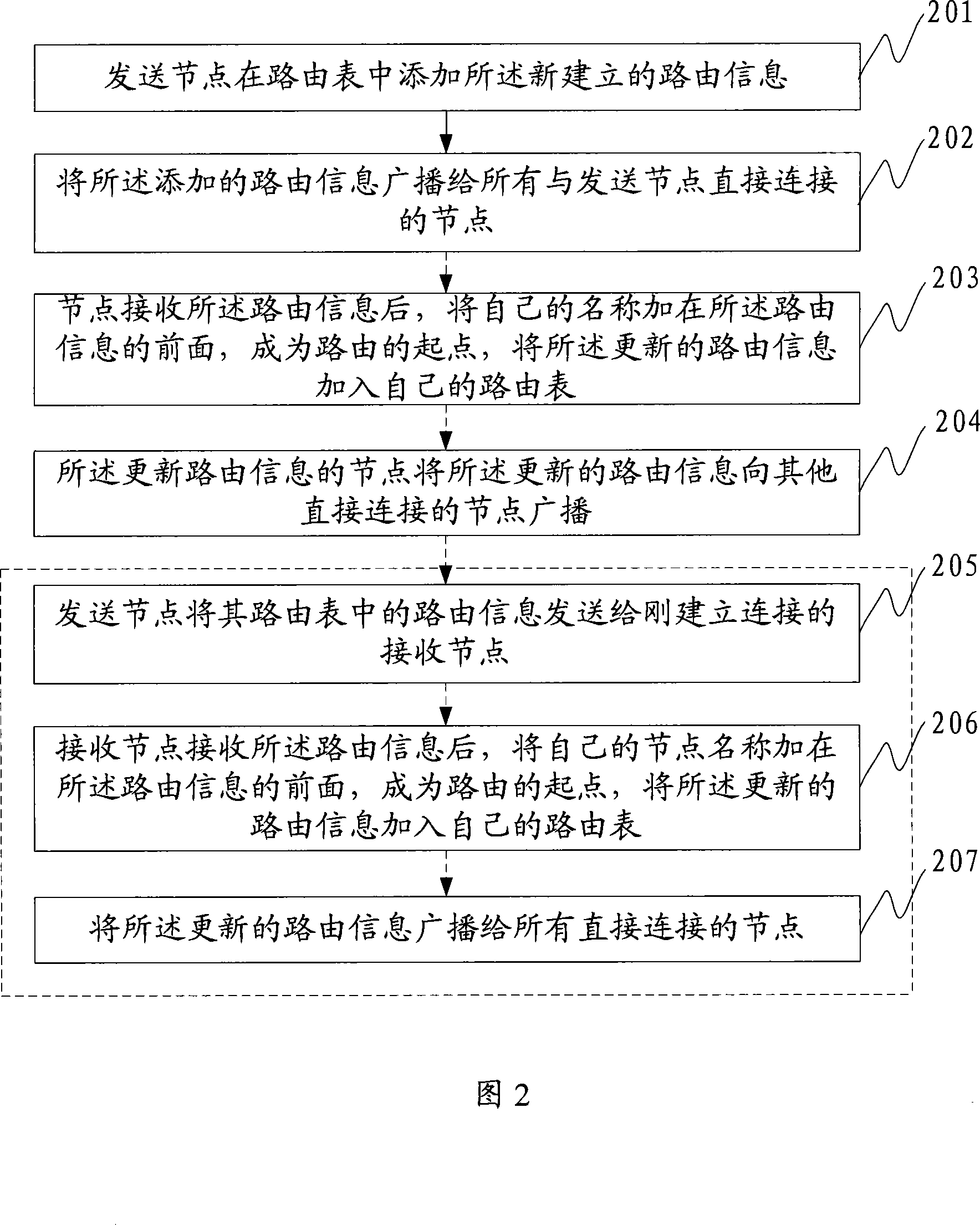
ActiveCN101136863AImprove transmission efficiencyReduce configuration difficultySpecial service provision for substationRoute generationWorkload
The method includes steps: establishing connection channels between two nodes; through the connection channel, transmission node sends request for building route connection to the receiving node, and establishing route connection; the transmission node and the receiving node exchange route table each other, and update route information in route tables; repeating the above steps for other route nodes in network so that any node in network can generate route information (RI) to other inter connectible nodes. The invention also discloses a route generation system as well as a system and method for routing message. In the invention, RI in each node is generated and updated by node self, and RI in each node saves all information of network the node is located at. The invention reduces difficulty and complexity for configuring network greatly, reduces workload for user and possibility of making a mistake by user so as to make higher efficiency for transmitting message.
Owner:SHENZHEN KINGDEE MIDDLEWARE
Loose coupling role authorized-type implementation access control method and system thereof
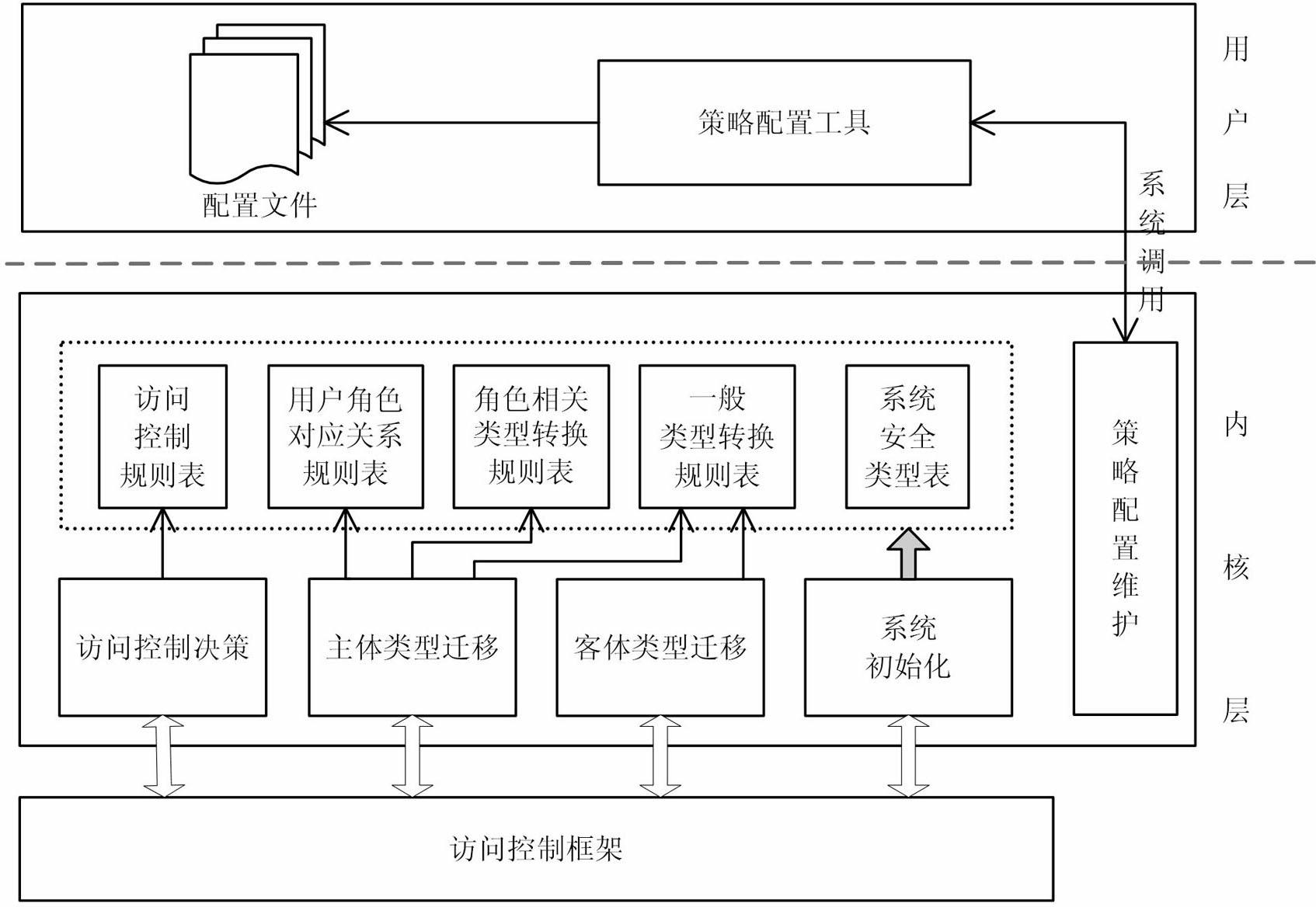
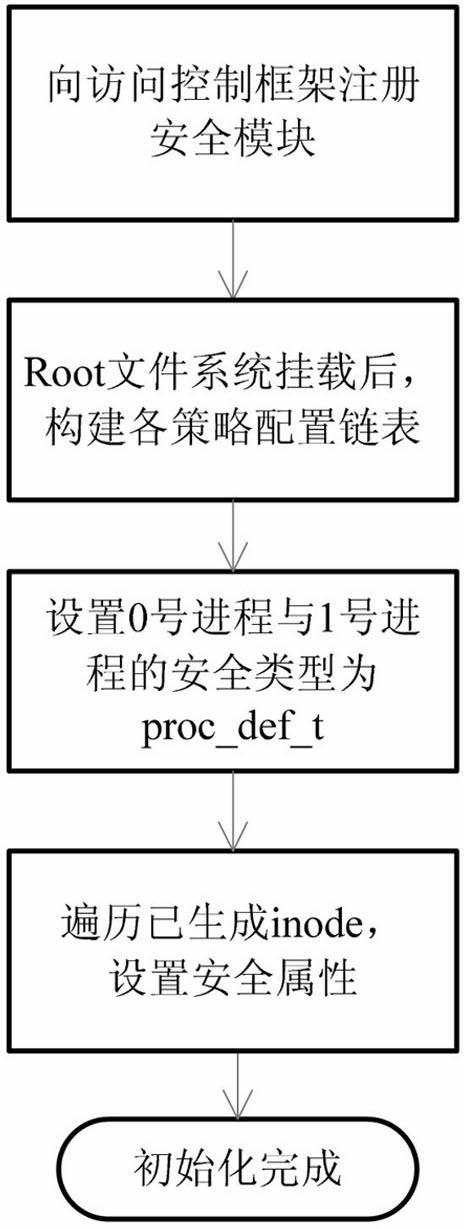
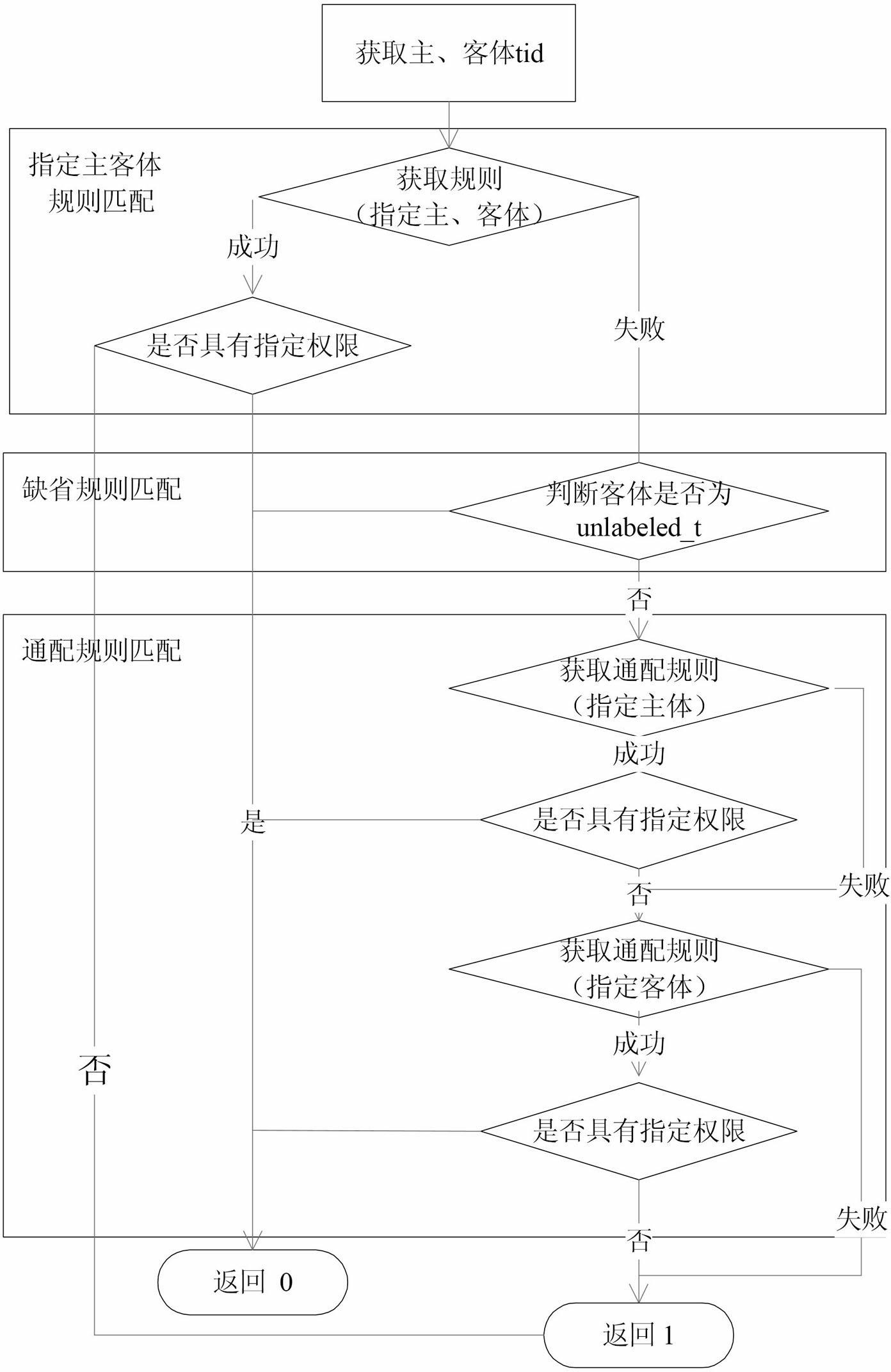
InactiveCN102222191AChange execution flowImplement featuresUnauthorized memory use protectionDigital data protectionOperational systemSecurity domain
The invention discloses a loose coupling role authorized-type implementation access control method and a system thereof. The method comprises the following steps of: adding a user role incidence relation based on a type implementation access control method; adding a related process type transformation rule definition relating to a user role and a corresponding type transformation decision mechanism; when a system process type is transformed, according to the process type transformation rule, judging whether to perform role related type transformation according to a current role of the user to change a user process execution flow; and entering a specific security domain of the user role. The system comprises a type implementation access control policy module, a policy security configuration module and a policy rule configuration module, wherein the type implementation access control policy module is operated in the kernel of an operating system; the policy security configuration module is operated on the user layer of the operating system; and the policy rule configuration module is positioned in a file system. The method and the system have the advantages of reducing the influence of user role configuration change on a type implementation rule system, reducing the security configuration difficulties, facilitating flexible configuration according to actual service conditions.
Owner:NAT UNIV OF DEFENSE TECH
Bidirectional forwarding detection method in multi-hop link on basis of BFD
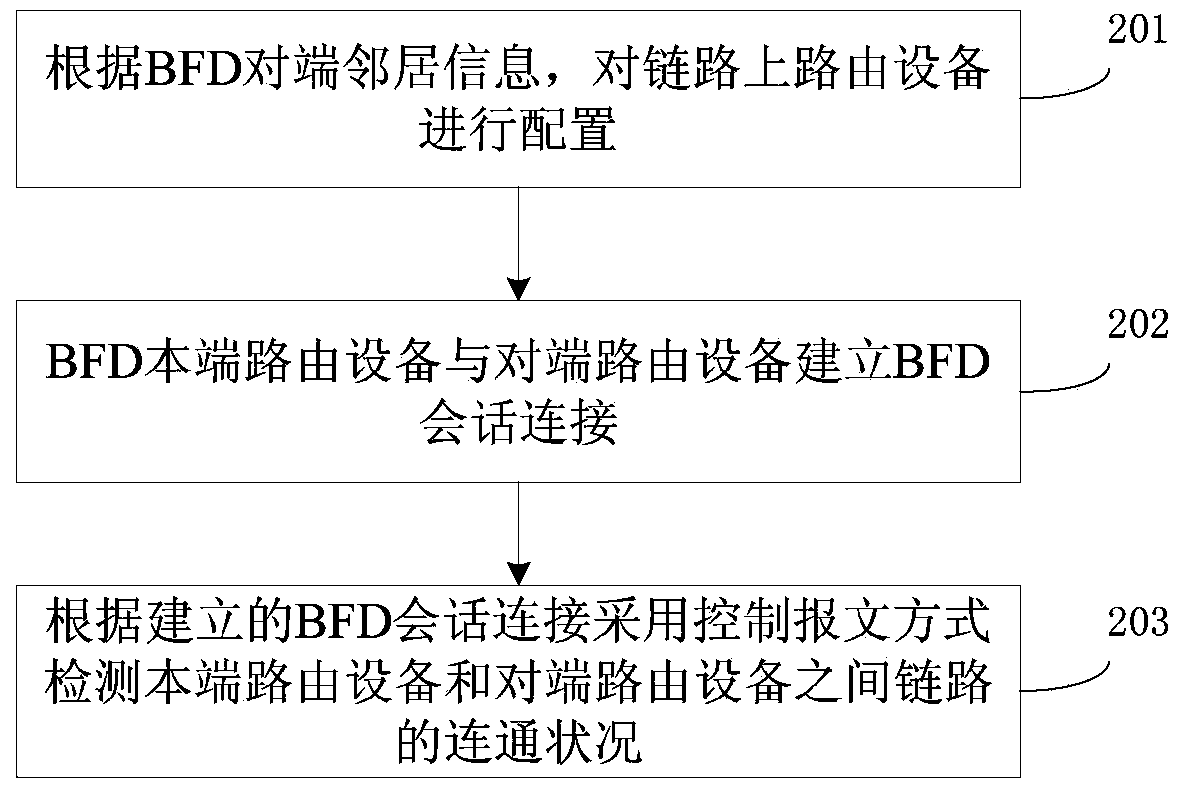
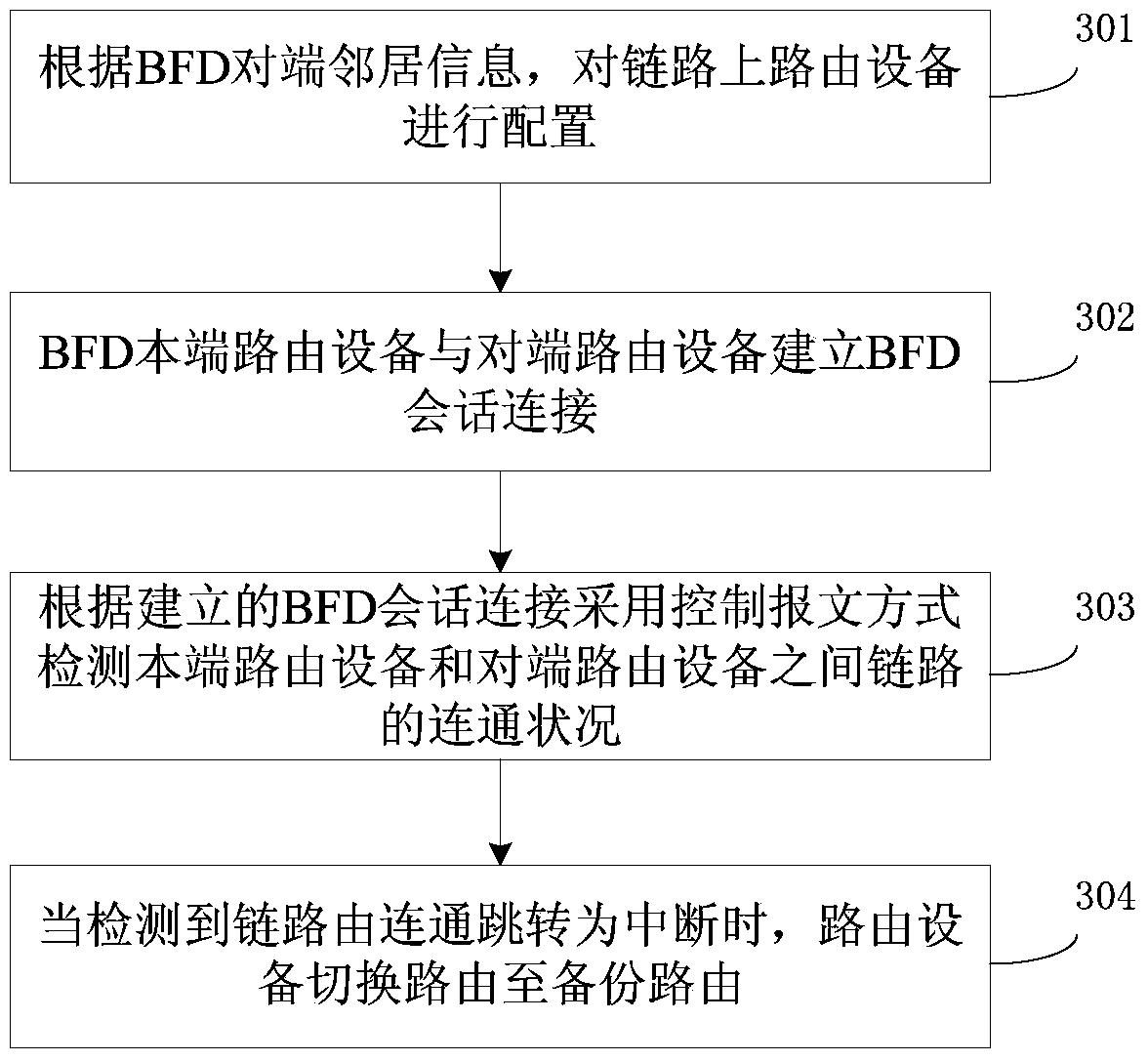
InactiveCN103490951ASimple configurationConfigure real-timeData switching networksBidirectional Forwarding DetectionNetwork communication
The invention relates to the technical field of computer network communication, in particular to a bidirectional forwarding detection method in a multi-hop link on basis of BFD. The method includes the steps that routing equipment on the link is configured according to BFD opposite end neighbor information; configuration includes the steps of configuring a target address of the routing equipment as a network segment address of a target network, configuring the next hop of the routing equipment as an opposite end neighbor building a BFD conversation with a home terminal, and identifying the next hop of the routing equipment as a BFD type; BFD conversation connection is built between BFD home terminal routing equipment and opposite end routing equipment; according to the built BFD conversation connection, the connection condition of links between the home terminal routing equipment and the opposite end routing equipment is detected by means of a message controlling method. By means of the technical scheme, BFD configuration of the links is simplified, and meanwhile achievement difficulty of BFD functions is reduced.
Owner:北京神州数码云科信息技术有限公司 +1
Method, apparatus and system for configuring APs (Access Point)
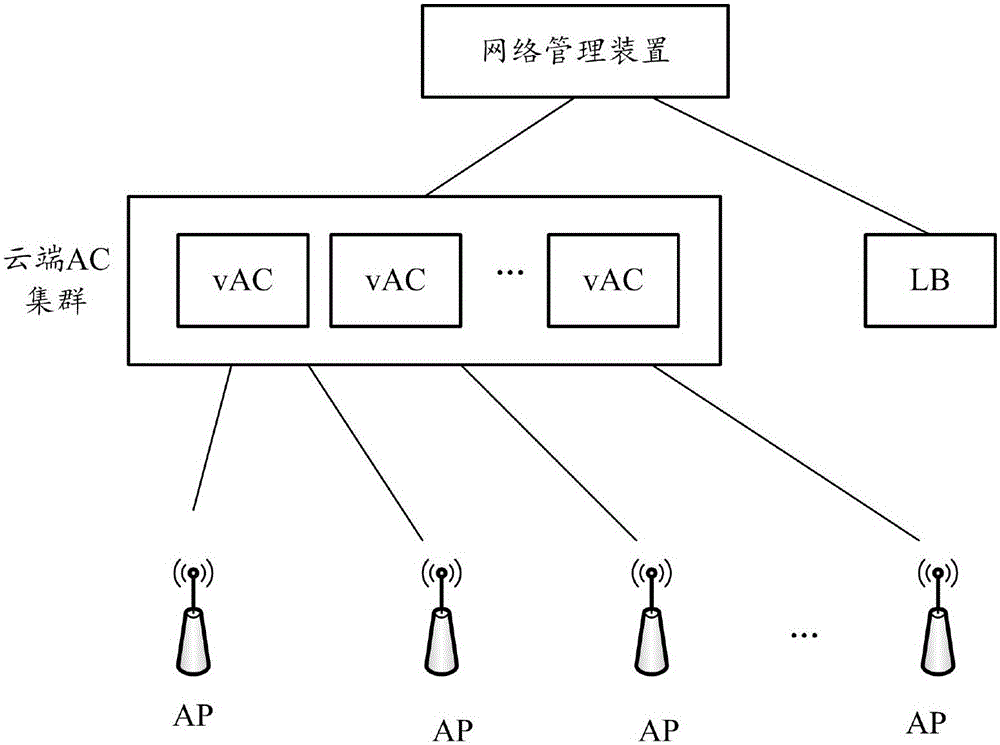
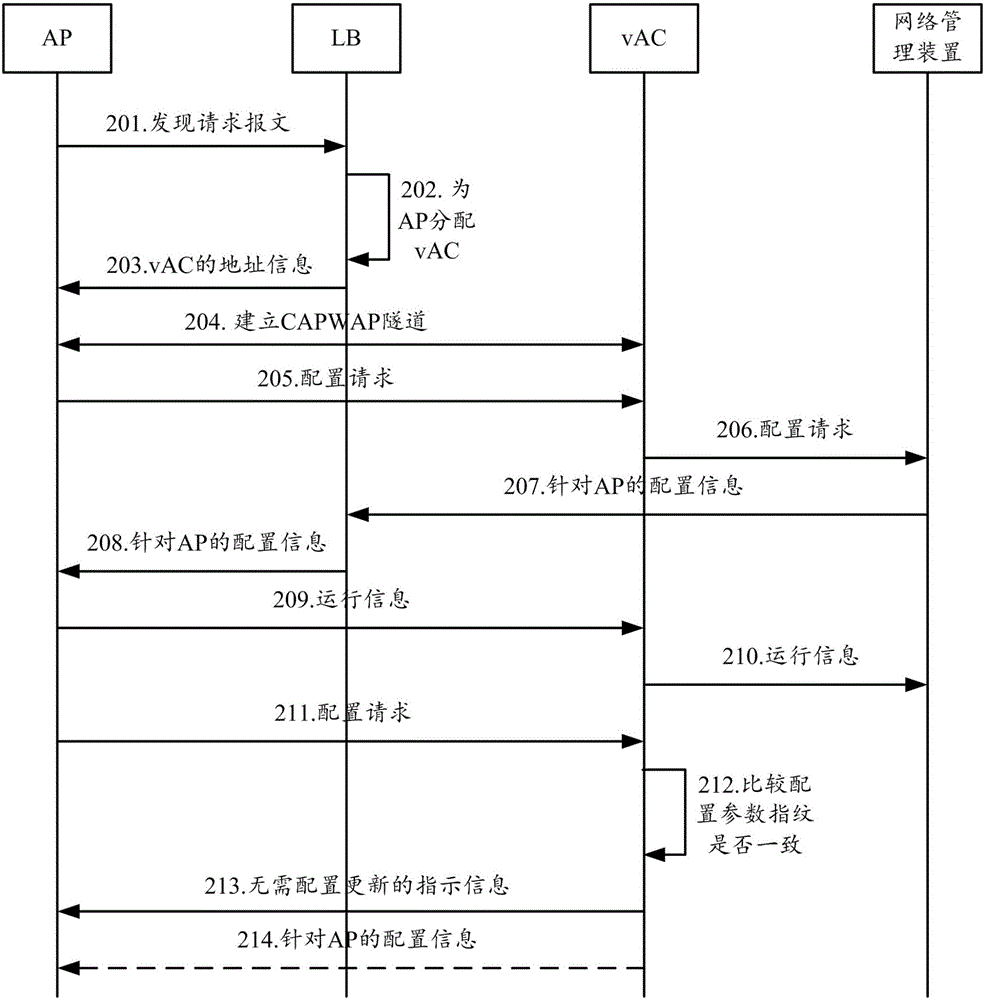
ActiveCN106301822AReduce configuration difficultyReduce maintenance costsNetwork topologiesNetworks interconnectionNetwork management
The present invention provides a method, apparatus and system for configuring APs (Access Point). The method includes the following steps that: after receiving the configuration request of the APs, cloud access controllers (AC) request a network management apparatus and obtains configuration information for the APs; and the cloud access controllers (AC) transmit the acquired configuration information to the APs through configuration responses. According to the method, apparatus and system of the invention, management on the APs is carried out by the network management device in a unified manner, the configuration information of the APs is not required to be configured on all ACs in a could AC cluster, and it only needs to configure the configuration information of the APs in the network management apparatus and issue the configuration information to the ACs associated with the APs, and therefore, configuration difficulty and maintenance cost can be decreased.
Owner:ALIBABA DAMO (HANGZHOU) TECH CO LTD
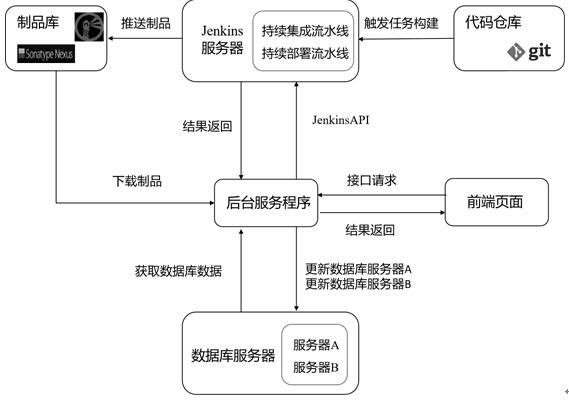
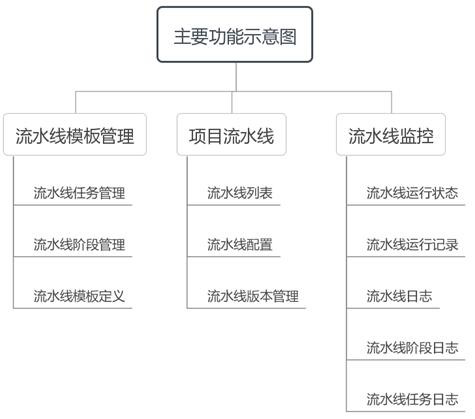
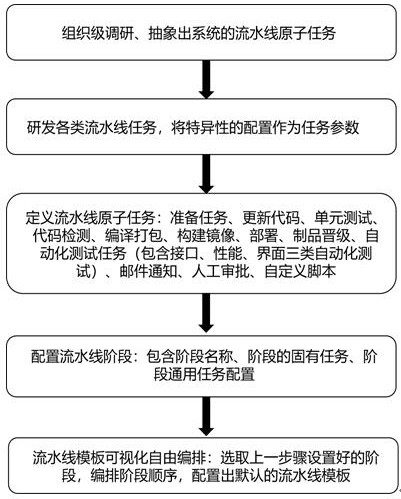
DevOps-based free arrangement monitoring system and use method thereof
PendingCN111930421AReduce configuration difficultyClear definitionVersion controlOffice automationExtensibilityMonitoring system
The invention provides a DevOps-based free arrangement monitoring system and a use method thereof. The system achieves the atomization and parameterization configuration of an assembly line task, andenables the task to be highly reusable. An assembly line template, an assembly line task and an assembly line stage are designed; a traditional CICD assembly line can be defined more clearly; pipelineconfiguration functionality is achieved, and the visual modular configuration is realized; a traditional script configuration mode is changed; the configuration difficulty of the assembly line is reduced; the use flexibility and the expandability of the DevOps assembly line can be greatly improved; the fabric grade research and development management can freely configure a plurality of assembly line templates suitable for company products; after a project team selects the templates, tasks of various types such as unit testing, code scanning, construction, automatic testing and manual approvalare arranged in the templates to form a CICD assembly line suitable for the team of the project team.
Owner:JIANGSU HONGXIN SYST INTEGRATION
A method for flow configuration of robot multi-round conversation
InactiveCN109308320AQuick configurationEfficient configurationText database queryingSemantic tool creationWorkloadDistributed computing
A method for flow configuration of multi-round dialogue of robot includes the following steps: S1: Configuration node, A node includes a plurality of function nodes, a plurality of intermediate nodesand a plurality of system nodes, each function node is configured to receive a question initially input by a user and extract entity variables therein, If the entity variables extracted from the function node are complete, further returning a result to the user, if the entity variable extracted by the function node is incomplete, further counting the missing entity variable, wherein each intermediate node is used for initiating a question to the user according to at least one missing entity variable, and each system node is used for constructing a document returned to the user according to theresult of a plurality of rounds of dialogues; S2: Configure the flow, select the nodes according to the actual dialog processing flow and establish the procedural relationship between the nodes. Theinvention can quickly and efficiently configure the response flow of the intelligent dialogue robot in multiple dialogues, and greatly reduces the workload and the configuration difficulty in the configuration process.
Owner:杭州光云科技股份有限公司
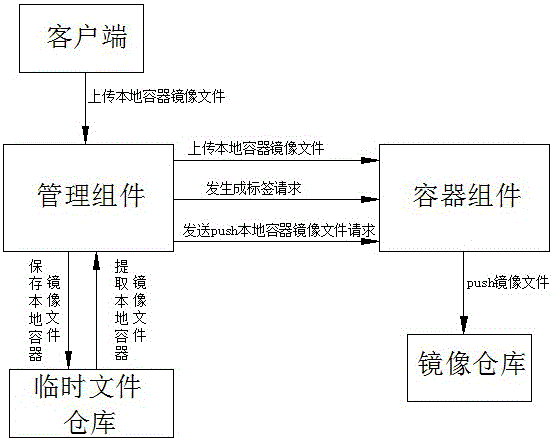
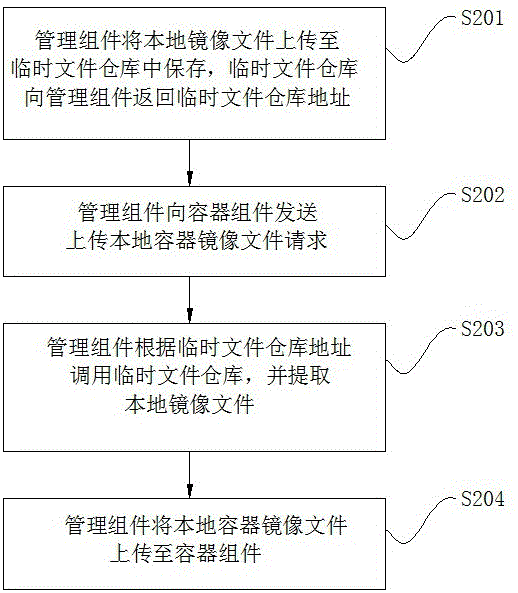
Method and system for uploading mirror images in local container to mirror image warehouse
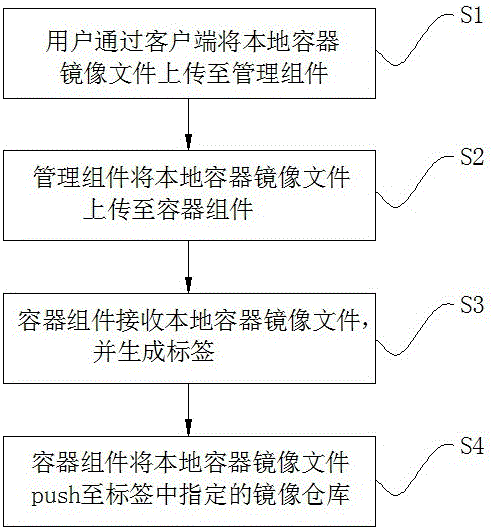
InactiveCN106776149ARealize unified managementReduce maintenance difficultyRedundant operation error correctionComputer softwareMirror image
The invention discloses a method and a system for uploading mirror images in a local container to a mirror image warehouse, belongs to the technical field of computer software application and aims to solve the technical problem of how to uploading the mirror images in the local container into the mirror image warehouse to realize unified management of mirror images in a container management system. The method includes steps: S1, uploading mirror image files of the local container to a management component by a user; S2, uploading the mirror image files of the local container to a container component by the management component; S3, receiving the mirror image files of the local container and generating a label by the container component, wherein the label is used for designating an address of the mirror image warehouse for storing the mirror image files of the local container; S4, pushing the mirror image files of the local container into the mirror image warehouse designated in the label by the container component. The system comprises a client, the management component, a temporary file warehouse, the container component and the mirror image warehouse.
Owner:SHANDONG LANGCHAO YUNTOU INFORMATION TECH CO LTD
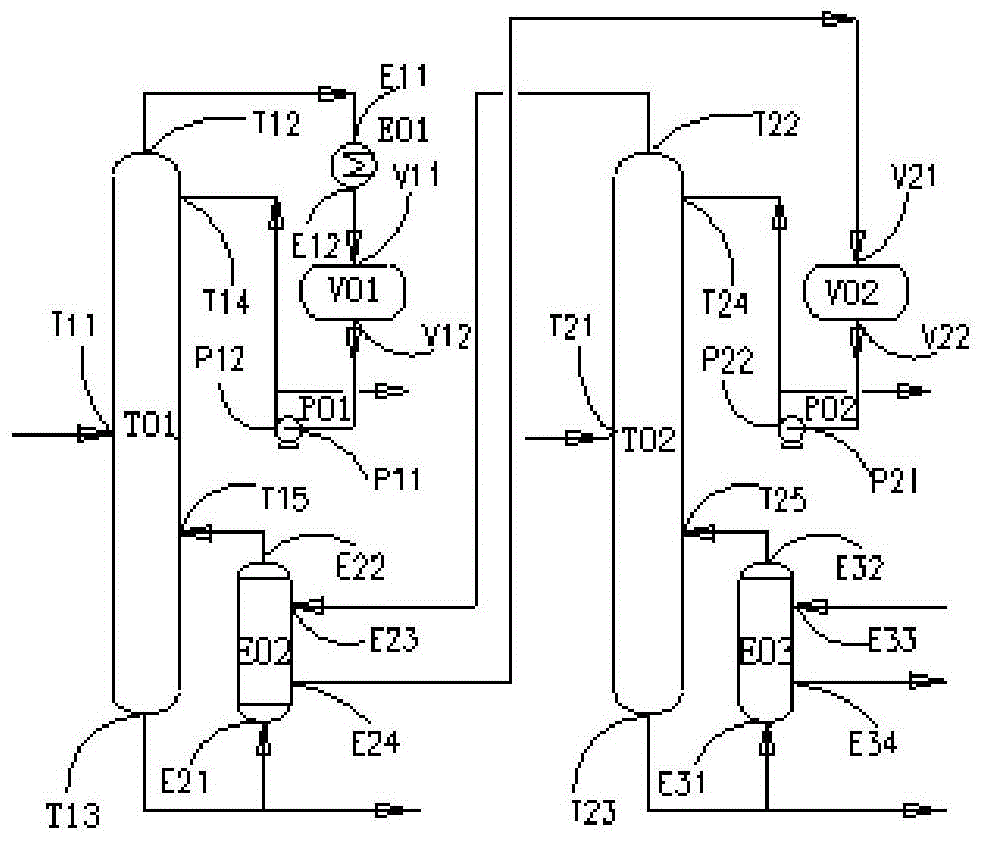
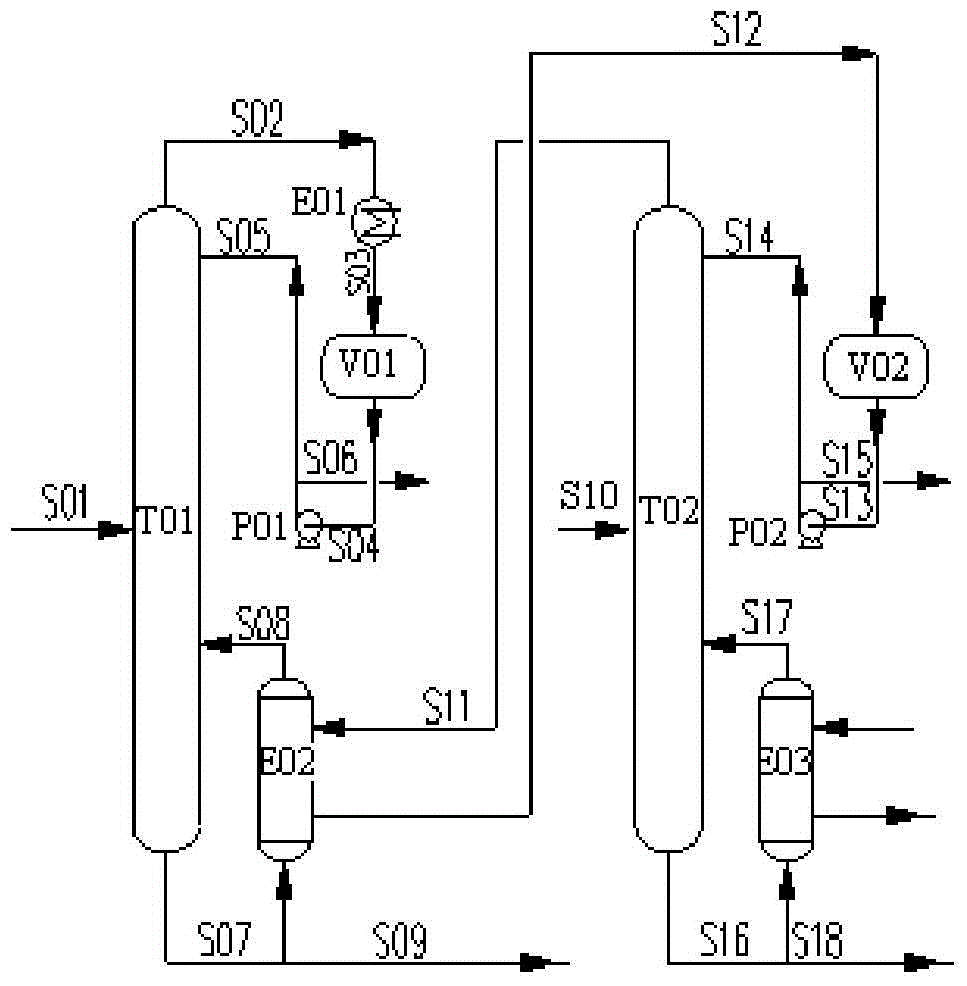
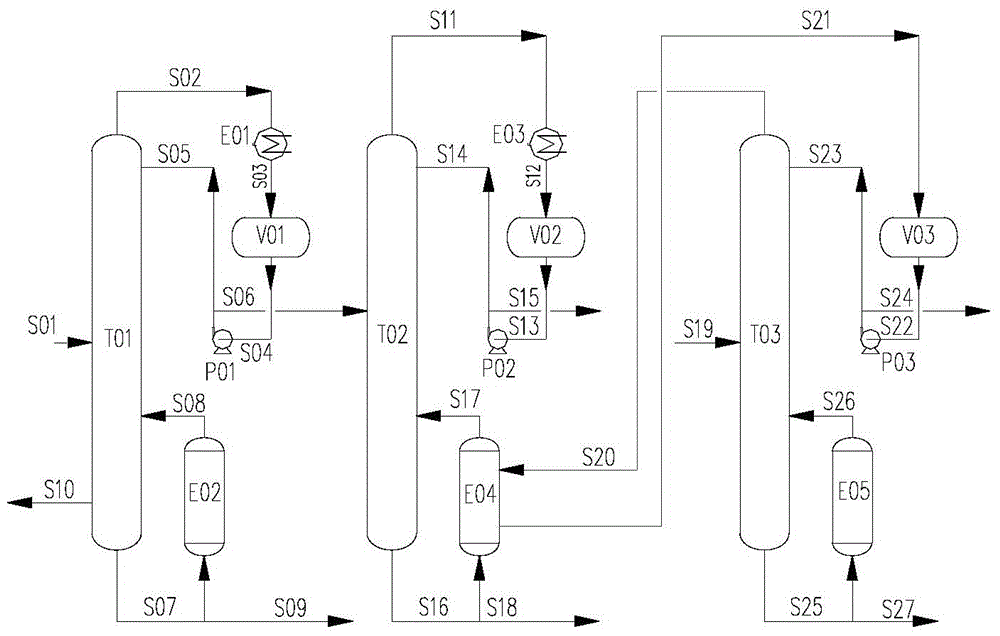
System for purifying chlorosilane through non-relevant tower differential pressure thermal coupling
ActiveCN103950935AReduce energy consumptionLow costFractional distillationHalogenated silanesRefluxReboiler
The invention discloses a system for purifying chlorosilane through non-relevant tower differential pressure thermal coupling. The system comprises: a first rectifying tower and a second rectifying tower, wherein each of the first rectifying tower and the second rectifying tower has a material inlet, a gas outlet, a liquid outlet, a liquid inlet and a gas inlet; a first reboiler and a second reboiler, wherein each of the first reboiler and the second reboiler has a liquid inlet, a gas outlet, a steam inlet and a condensate liquid outlet; a first reflux pump and a second reflux pump, wherein each of the first reflux pump and the second reflux pump has an inlet and a pump outlet; a first reflux tank and a second reflux tank, wherein each of the first reflux tank and the second reflux tank has a tank inlet and a tank outlet; and a condenser having a gas inlet, a liquid outlet, a cold source inlet and a cold source outlet. Compared with routine serial or parallel differential pressure thermal coupling rectifying towers, the chlorosilane purification system disclosed in the invention can realize the tower differential pressure thermal coupling between / among different tower sets, enlarges the application range of the differential pressure thermal coupling, and solves a problem of high energy consumption of a purifying process of a polysilicon system.
Owner:CHINA ENFI ENGINEERING CORPORATION
Distribution method and apparatus of AP addresses in WLAN
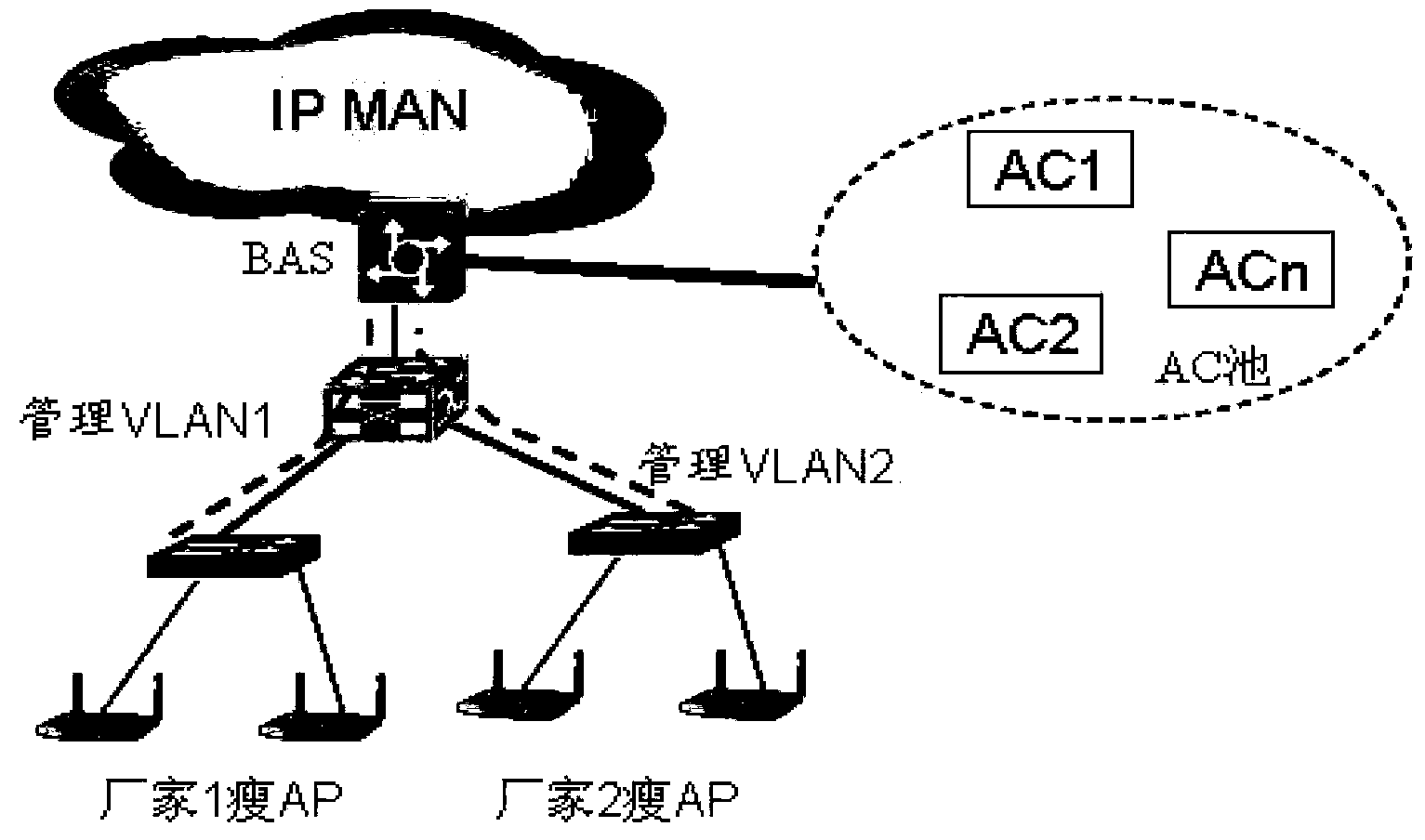
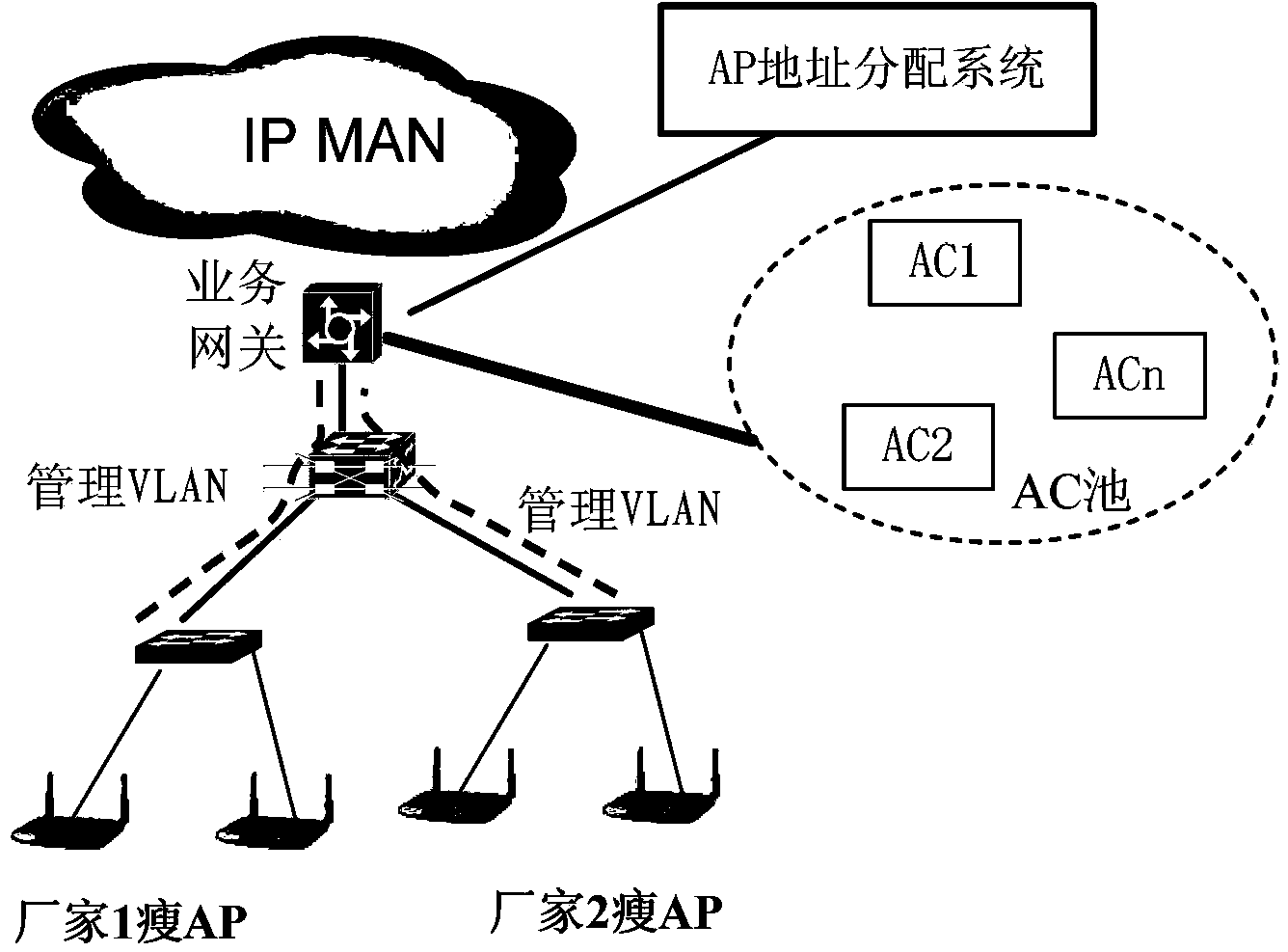
ActiveCN104349511AFlexible accessIncrease profitNetwork topologiesNetworks interconnectionDistribution methodComputer science
The invention relates to a distribution method and apparatus of AP addresses in a WLAN. The method comprises the following steps: synchronizing configuration data of registered APs; receiving DHCP packets forwarded by BASs, the packets bearing attribute information of APs sending the DHCP packets; comparing the attribute information of the APs sending the DHCP packets with the attribute information in the configuration data; if the configuration data comprises the attribute information of the APs sending the DHCP packets, determining that the APs sending the DHCP packets are the registered APs, and otherwise, determining that the APs sending the DHCP packets are unregistered APs; if the APs sending the DHCP packets are the registered APs, obtaining information of ACs corresponding to the APs sending the DHCP packets from the configuration data; and distributing the addresses to the APs sending the DHCP packets, and issuing the obtained AC information. According to the invention, VLAN resources can be reduced, maintenance difficulties are lowered, the APs can be flexibly accessed to specific ACs, and the utilization rate of the ACs is improved.
Owner:CHINA TELECOM CORP LTD
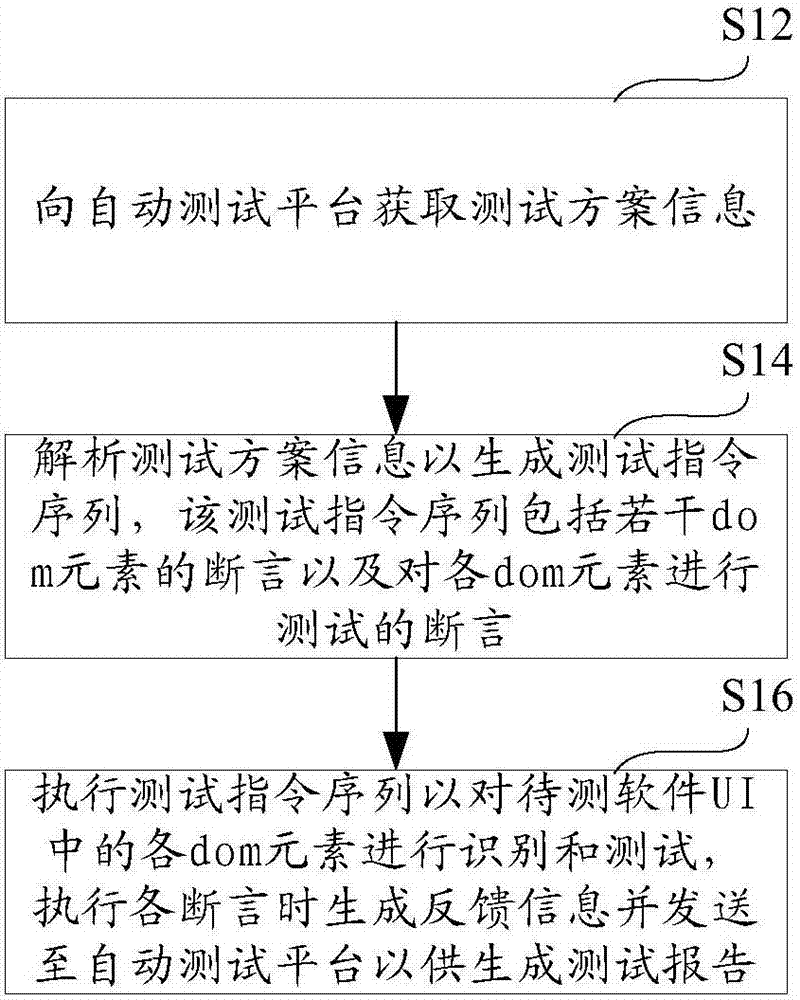
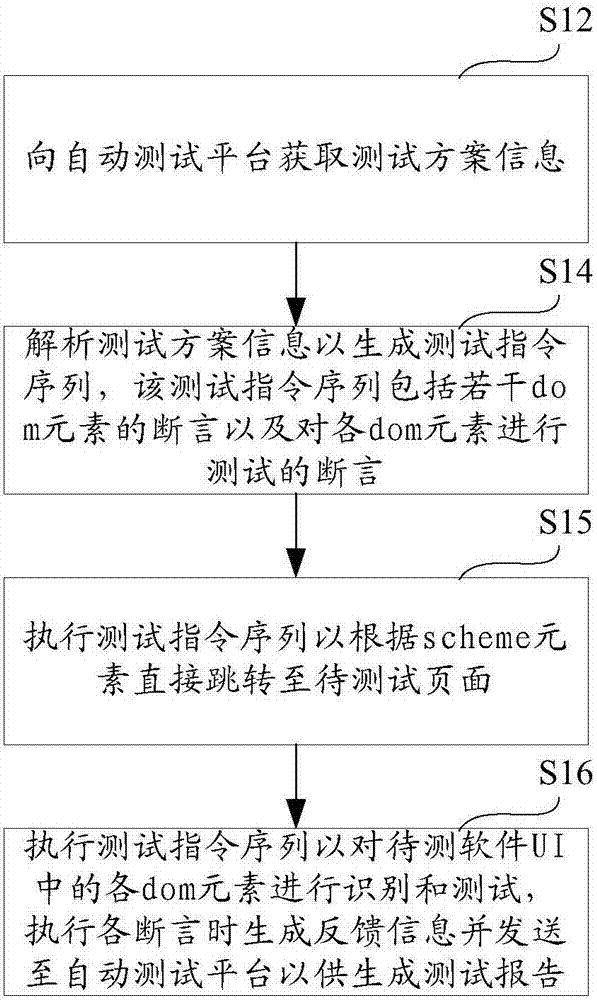
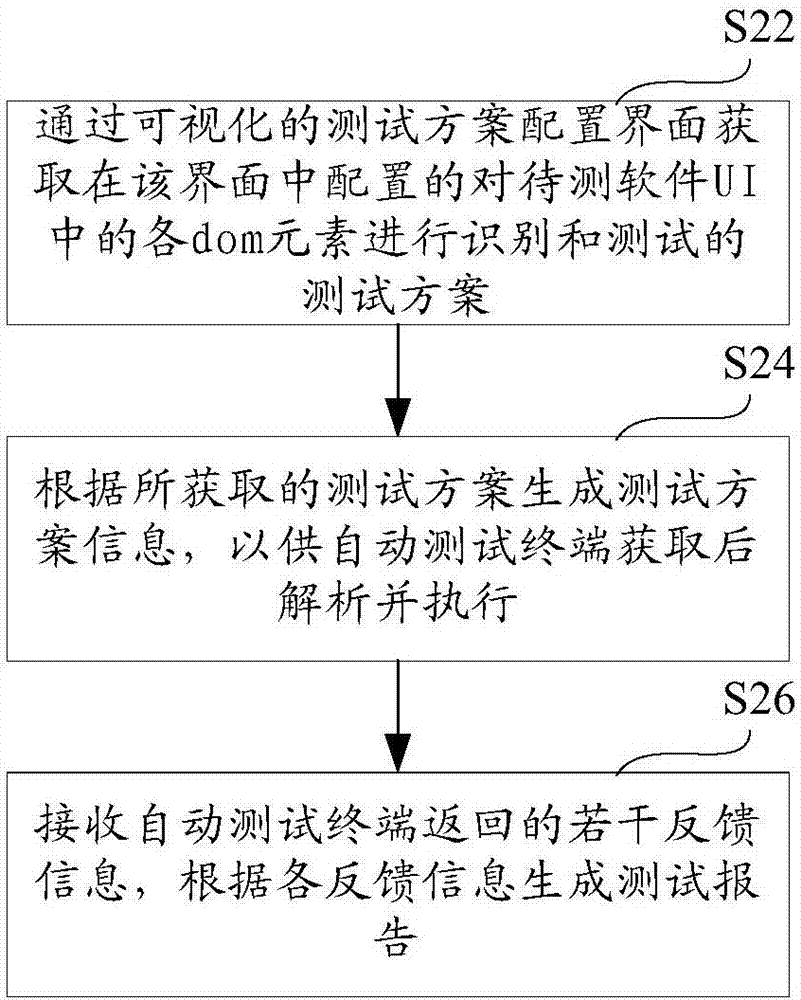
Automatic test method, terminal, platform and system
InactiveCN106959921AReduce testing costsEnhance the stability of automated testingSoftware testing/debuggingAutomatic test equipmentSoftware engineering
The invention provides an automatic test method, terminal, platform and system. The method comprises the steps of obtaining test scheme information from the automatic test platform; analyzing the test scheme information to generate a test instruction sequence, wherein the test instruction sequence comprises a plurality of assertions for identifying document object model (dom) elements and the assertions for testing the dom elements; and performing the test instruction sequence to identify and test the dom elements in a user interface (UI) of to-be-tested software, and when the assertions are performed, generating feedback information and sending the feedback information to the automatic test platform, thereby generating a test report. According to the method, the terminal, the platform and the system, through utilization of a feature that the structures of the dom elements in an Android system and an IOS system are completely consistent, only the same set of test scheme is required for an Android version and an IOS version, so the test cost is reduced, the automatic test stability is enhanced, and moreover, the method, the terminal, the platform and the system have the advantages that the platform can adapt to various terminals wirelessly, multithread tests can be carried out at the same time, and the test report is generated automatically.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
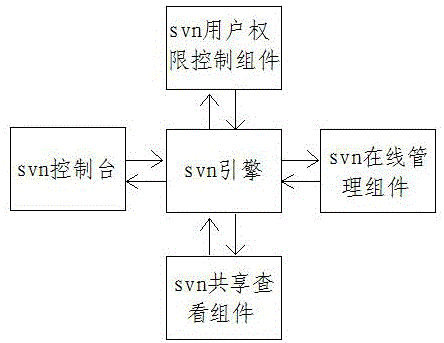
Svn source code online management and shared viewing system and method
ActiveCN106648589AReduce couplingReduce dependenceSoftware maintainance/managementSpecific program execution arrangementsMaintenance managementComputer software
The invention discloses an svn (subversione) source code online management and shared viewing system and method, and belongs to the technical field of computer software application. The svn source code online management and shared viewing method comprises the steps that an svn control console is in charge of user interaction, obtains a user instruction and transmits the obtained user instruction to an svn engine; and the svn engine is used for analyzing and processing the received instruction of the svn control console, calling an svn shared viewing component, an svn user right control component and an svn online management component to perform directory addition, directory deletion, check-in, check-out and branch creation management on an svn. According to the svn source code online management and shared viewing method, the dependency on the environment can be reduced, the working stability can be enhanced, the configuration difficulty can be lowered, and the operation and maintenance management difficulty can be lowered; and the method has very high promotion and application values.
Owner:SHANDONG LANGCHAO YUNTOU INFORMATION TECH CO LTD
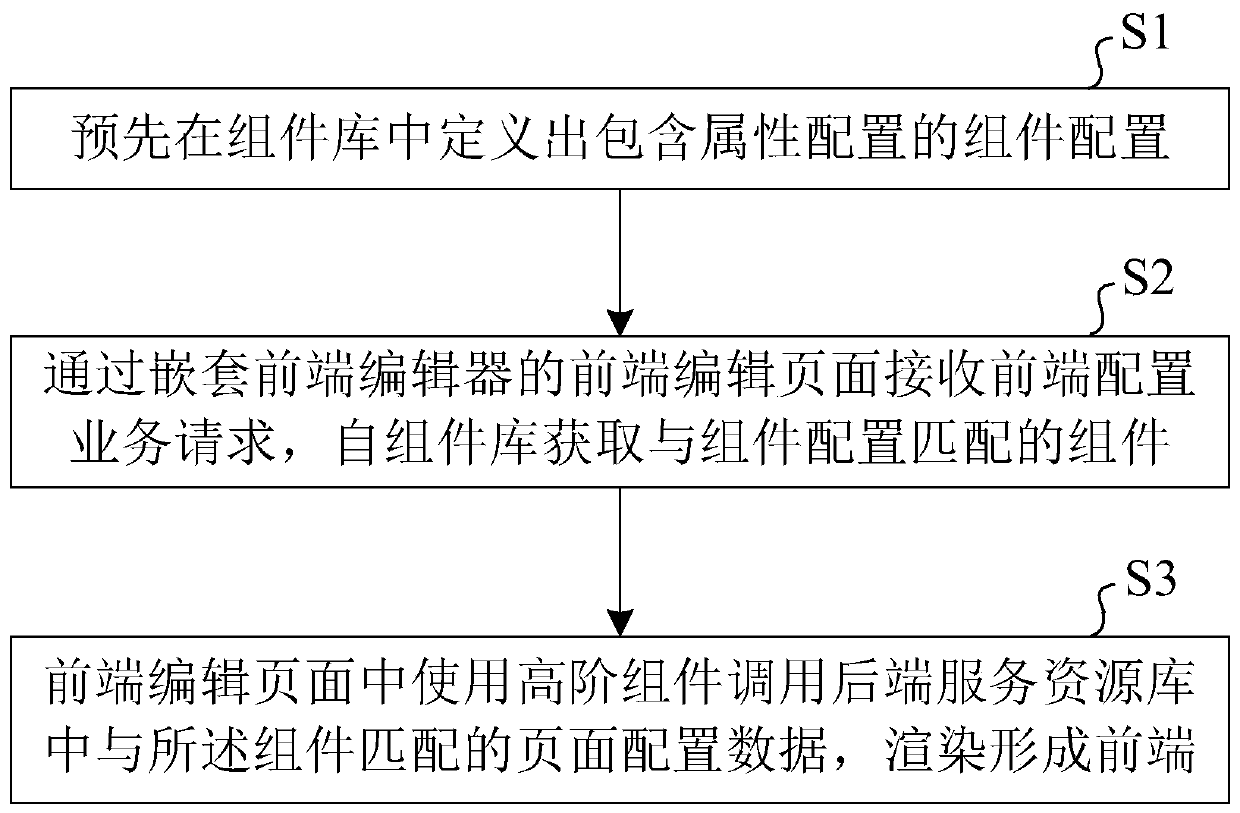
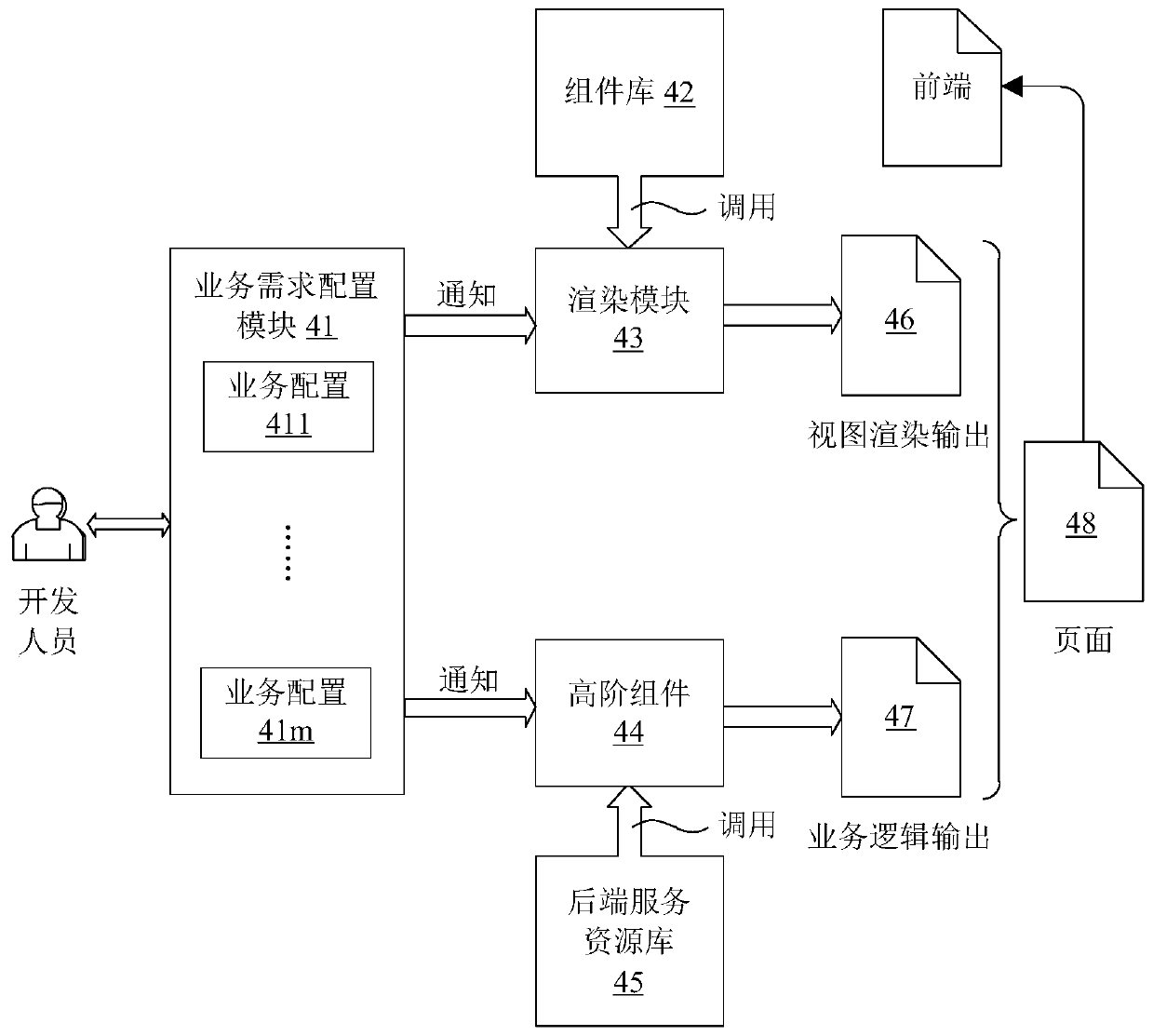
Front-end configuration method and system and electronic equipment
PendingCN111124477AReduce configuration difficultyReduce maintenance difficultyVersion controlSoftware reuseBase classReusability
The invention provides a front-end configuration method and system and electronic equipment. The front-end configuration method comprises the following steps: S1, defining component configuration containing attribute configuration in a component library in advance; s2, receiving a front-end configuration service request through a front-end editing page of the nested front-end editor, and obtaininga component matched with component configuration from a component library; and S3, calling page configuration data matched with the component in a back-end service resource library by using a high-order component in the front-end editing page, and performing rendering to form a front end. According to the front-end configuration method, the front-end configuration system and the electronic equipment disclosed by the invention, service code separation and code reuse are realized; the reusability and readability of codes forming the front end are remarkably improved, frequent switching betweensubclasses and base classes by developers is avoided, the development difficulty of the developers to the front end is reduced, and therefore the development efficiency of the front end is remarkablyimproved.
Owner:华云数据有限公司
Closed-loop control method and system for magnetizing state of variable-flux permanent magnet motor
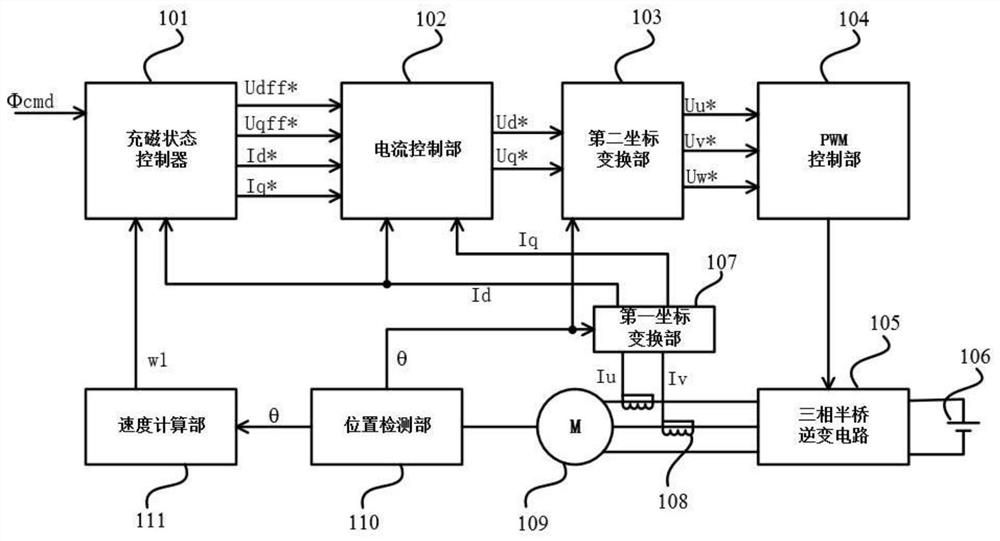
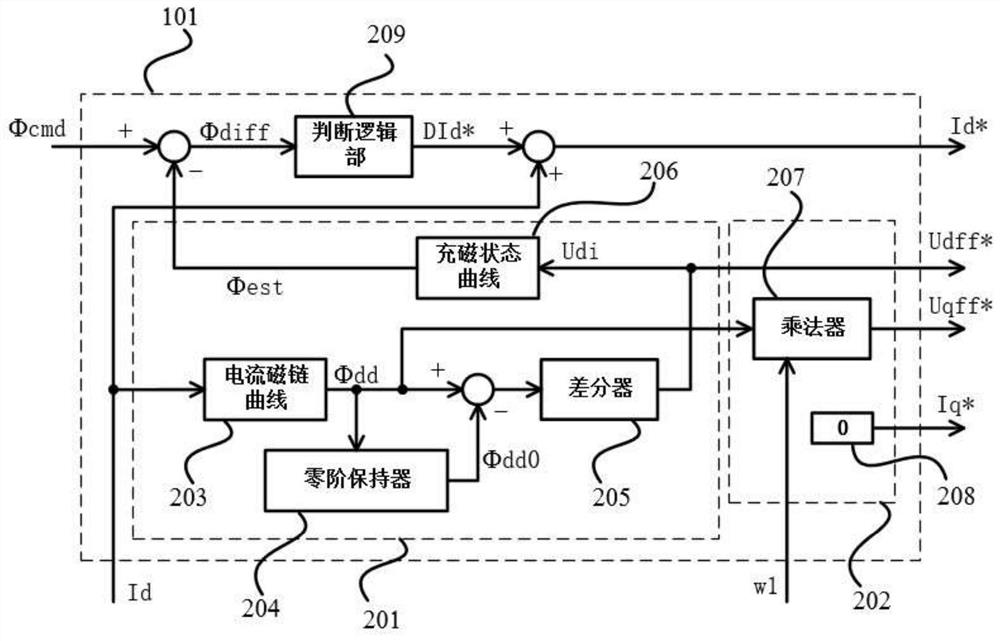
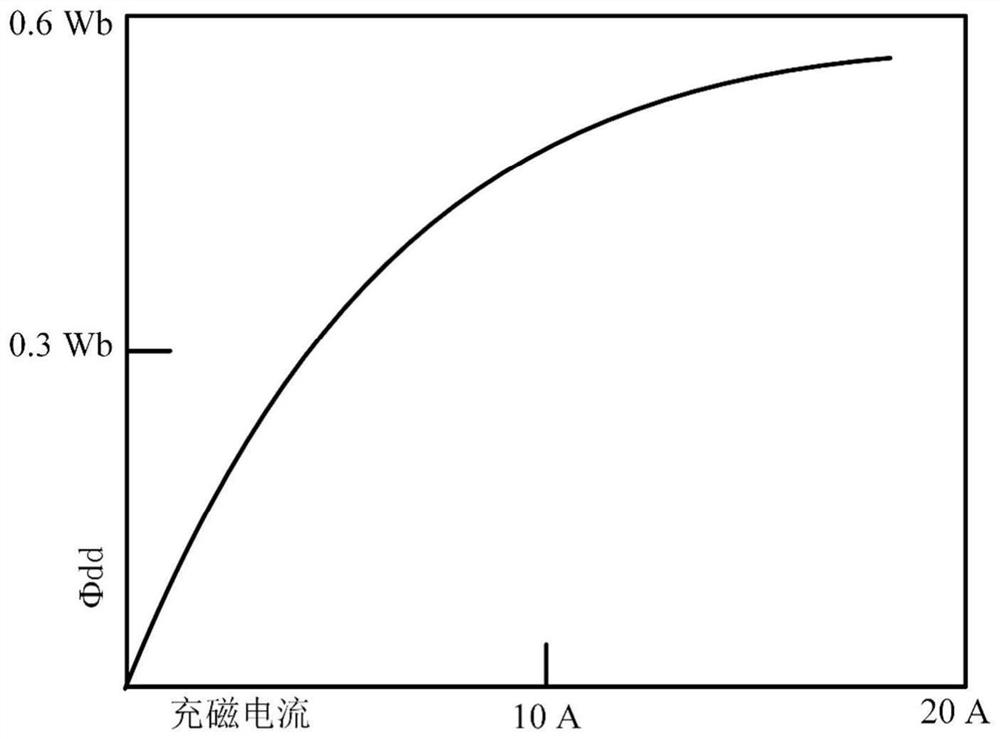
InactiveCN111697899AReduce configuration difficultyExtended application speed rangeMotor control for very low speedsMagnetic bodiesLoop controlElectric machine
The invention discloses a closed-loop control method and system for the magnetizing state of a variable-flux permanent magnet motor, and belongs to the field of driving control of variable-flux permanent magnet motors. The method comprises the steps of firstly, detecting a d-axis current feedback value, obtaining a d-axis armature flux linkage by utilizing a current flux linkage curve, and calculating the change of the d-axis armature flux linkage in combination with the d-axis armature flux linkage of the previous control period so as to obtain an induced voltage Udi; obtaining a magnetizingstate estimated value [phi]est by utilizing the induced voltage Udi based on a relation curve between the induced voltage and the magnetizing state; and then carrying out error comparison on a magnetizing state instruction [phi]cmd and the magnetizing state estimated value [phi]est, then generating a d-axis current instruction difference value through logic judgment, and then updating a d-axis current instruction Id* for carrying out current closed-loop control. According to the invention, the magnetizing state is estimated based on the induced voltage change generated by the d-axis current inthe magnetizing and demagnetizing process, and a voltage decoupler is introduced, so that the magnetizing state of the motor can be accurately controlled under the static and rotating states of the variable-flux permanent magnet motor.
Owner:HUAZHONG UNIV OF SCI & TECH
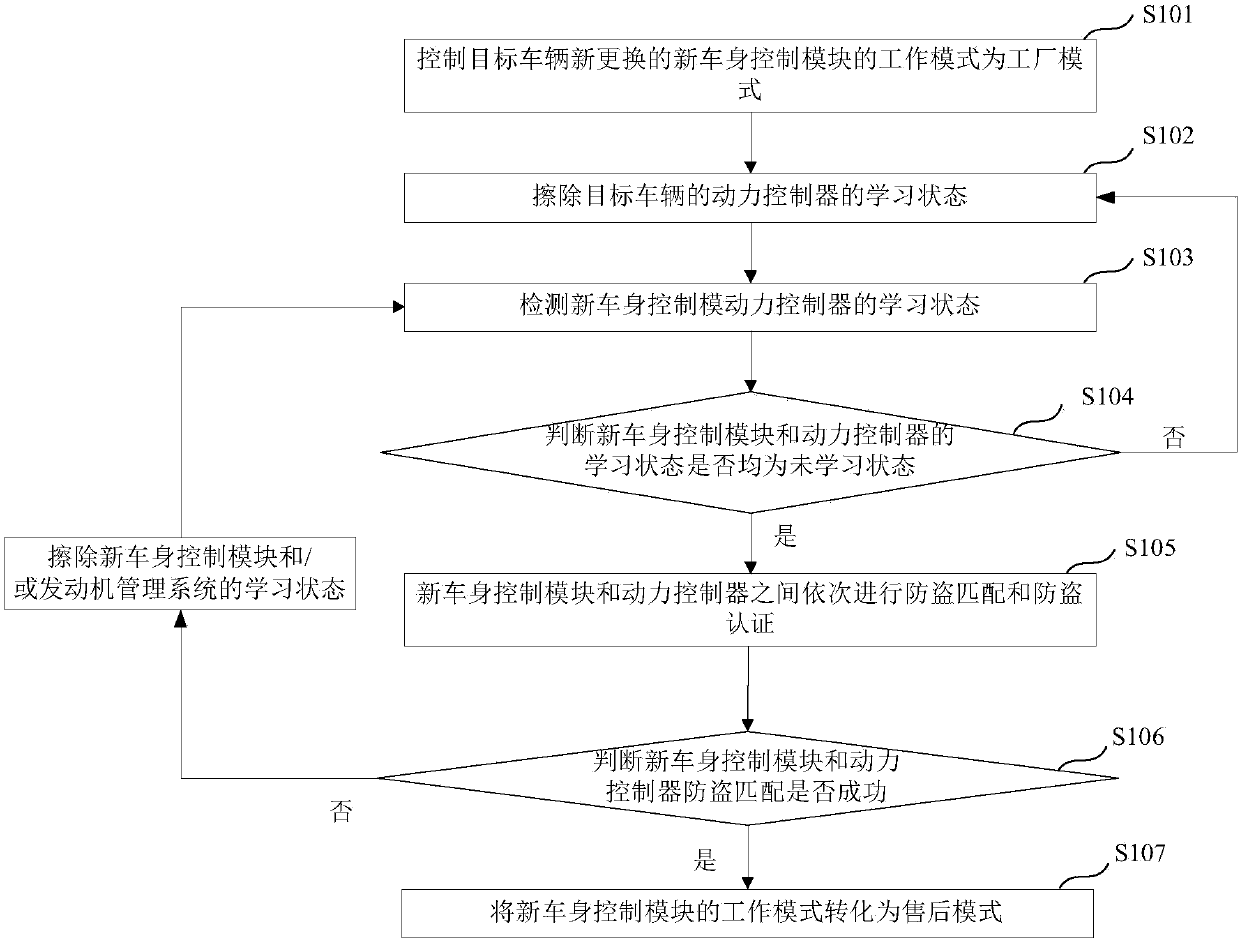
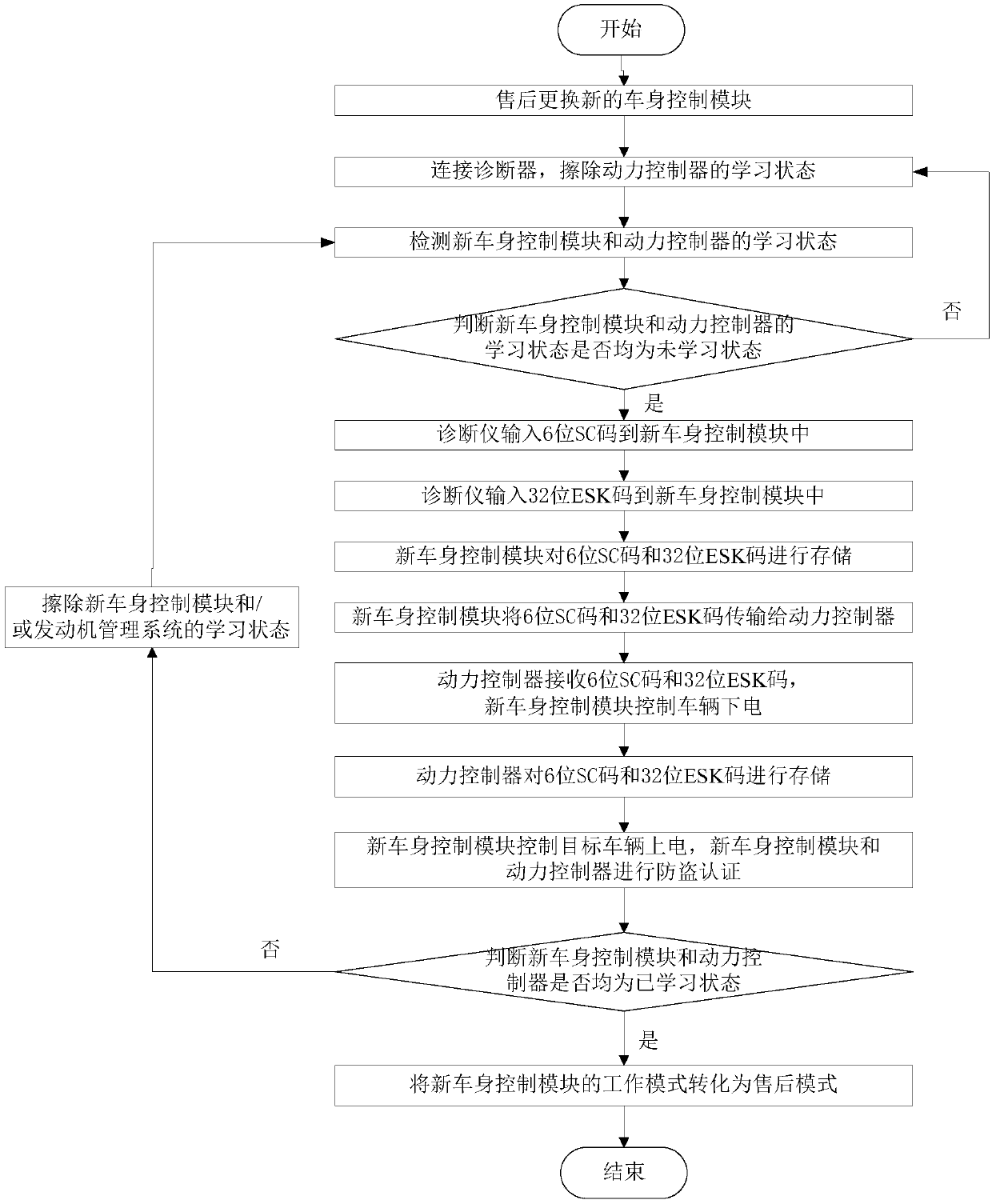
Vehicle anti-theft system configuration method, computer readable storage medium and terminal
ActiveCN109624919AAvoid anti-theft matching failureReduce configuration difficultyAnti-theft devicesAnti theftControl objective
The invention provides a vehicle anti-theft system configuration method, a computer readable storage medium and a terminal. A vehicle anti-theft system comprises a vehicle body control module and a power controller. The configuration method comprises the steps that the work mode of a new replaced vehicle body control module of a target vehicle is controlled to be a factory mode; the learning stateof the power controller of the target vehicle is erased; the learning state of the new vehicle body control module and the learning state of the power controller are detected; when the learning states of the new vehicle body control module and the power controller are both unlearning states, anti-theft matching and anti-theft authentication are conducted in sequence; whether the anti-theft matching of the new vehicle body control module and the power controller is successful or not is judged, if yes, the work mode of the new vehicle body control module is transformed into an after-sale mode,and if not, anti-theft matching and anti-theft authentication are conducted again. By means of the method, the situation that due to the problems of the power controller or insufficient early verification, anti-theft matching is failed is effectively avoided, the vehicle anti-theft system configuration difficulty is reduced, and the vehicle anti-theft system configuration efficiency is improved.
Owner:AIWAYS AUTOMOBILE CO LTD
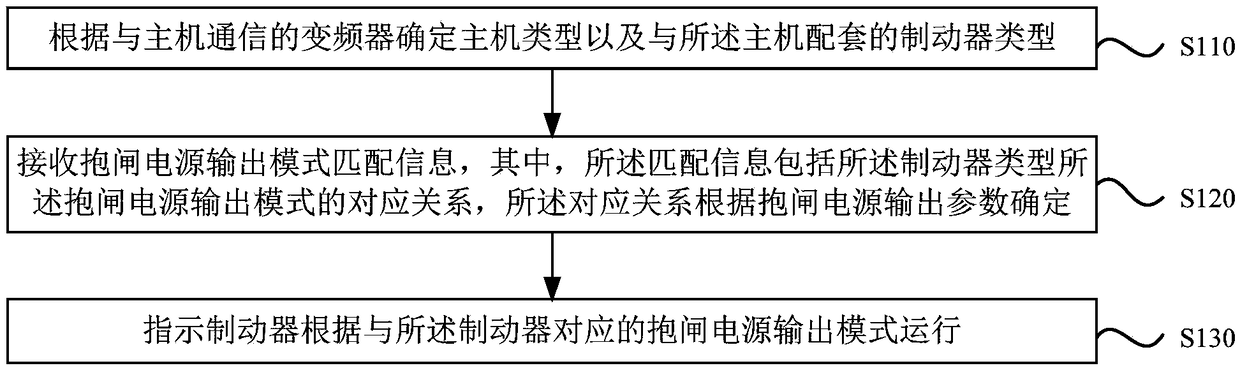
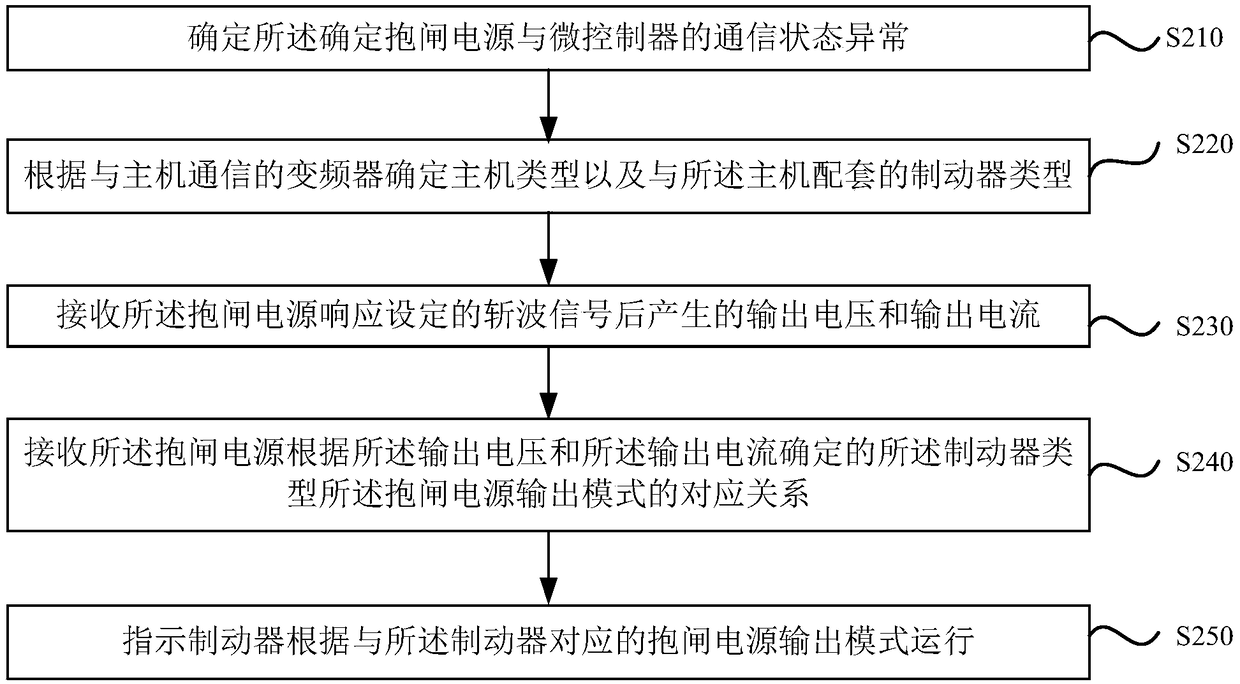
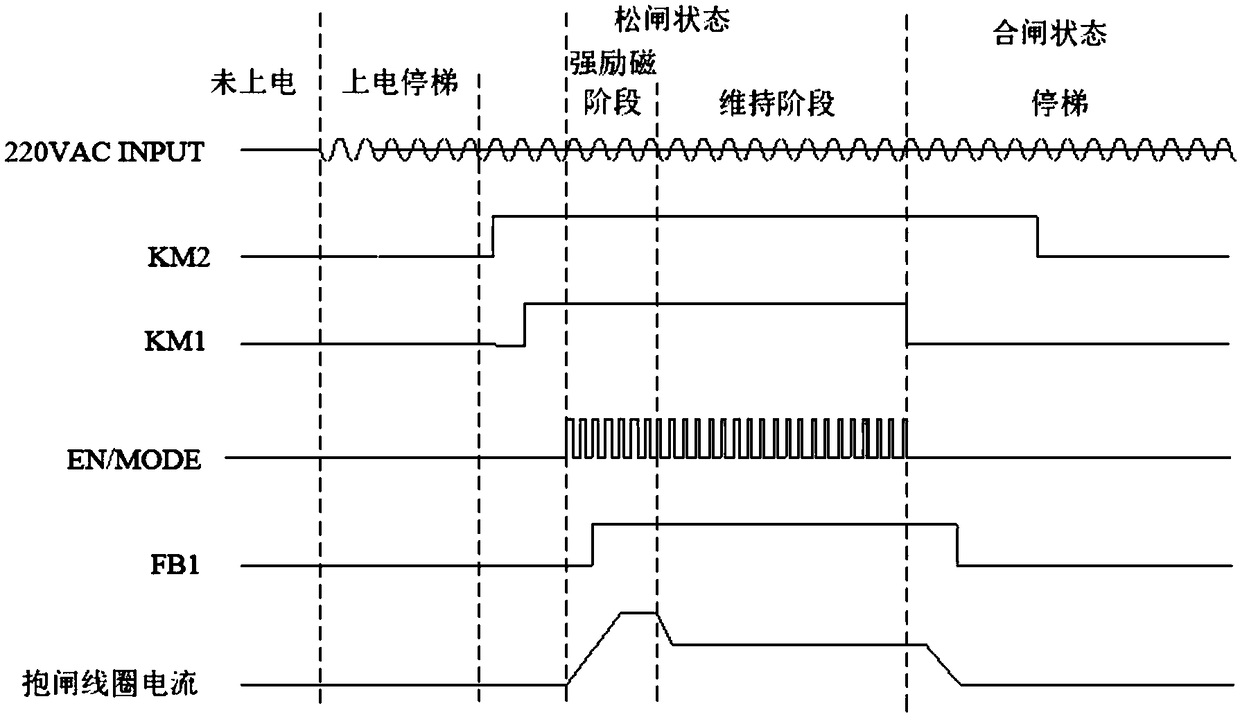
Control method and device of elevator brake, brake, equipment and storage medium
ActiveCN108639881AImprove versatilityReduce configuration difficultyElevatorsHoisting equipmentsAutomotive engineeringVariable-frequency drive
The embodiment of the invention discloses a control method and device of an elevator brake, the brake, equipment and a storage medium. The model of a host and the model of the brake matched with the host are determined according to a frequency converter in communication with the host; matched information of an output mode of a brake power source is received, wherein the matched information comprises the correspondence relationship between the model of the brake and the output mode of the brake power source, and the correspondence relationship is determined according to output parameters of thebrake power source; and the brake is instructed to run according to the output mode, corresponding to the brake, of the brake power source. It is achieved that a same elevator brake device is applicable to various brakes, the universality of the elevator brake device is improved, and the configuration difficulty of an electrical system is lowered.
Owner:HITACHI BUILDING TECH GUANGZHOU CO LTD
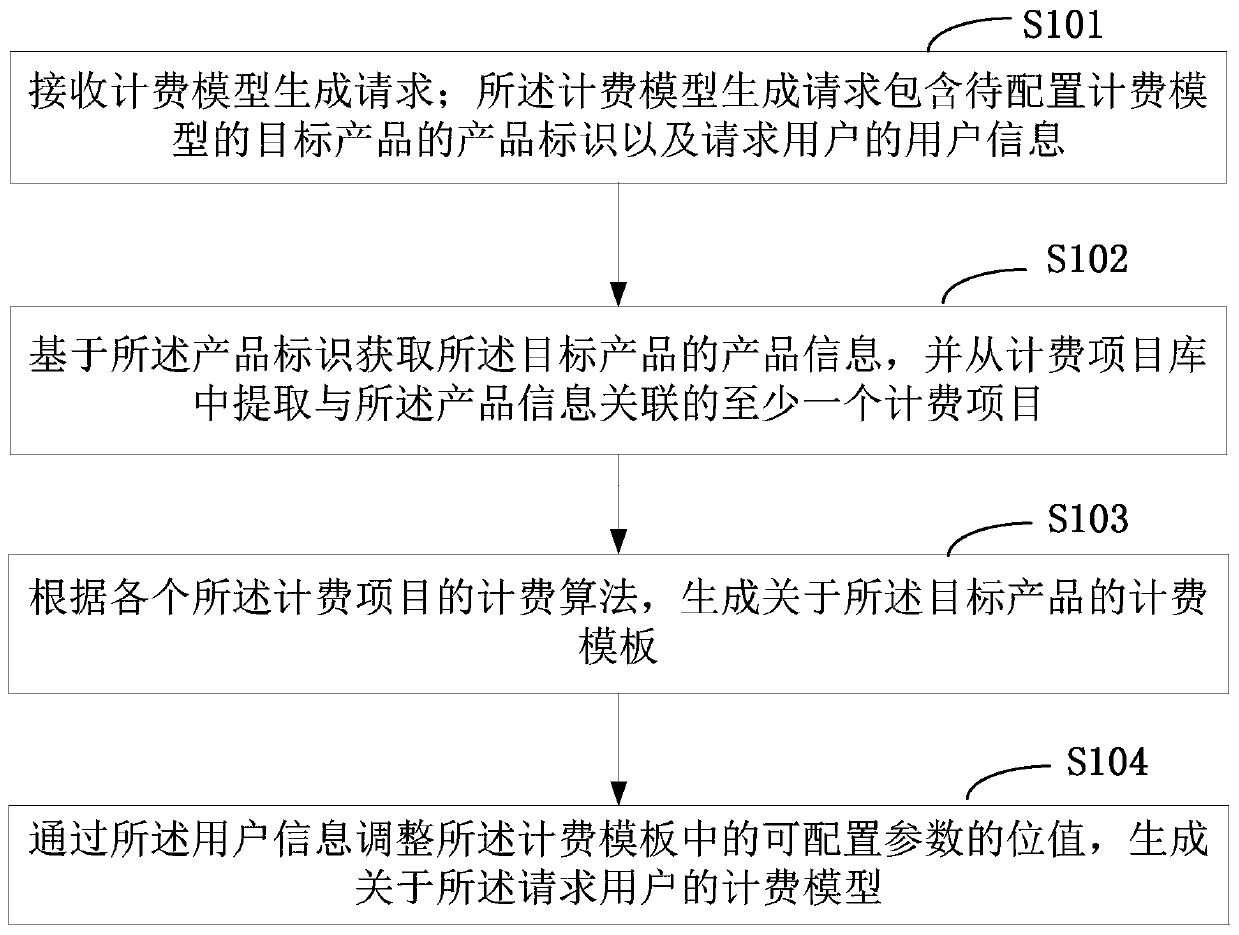
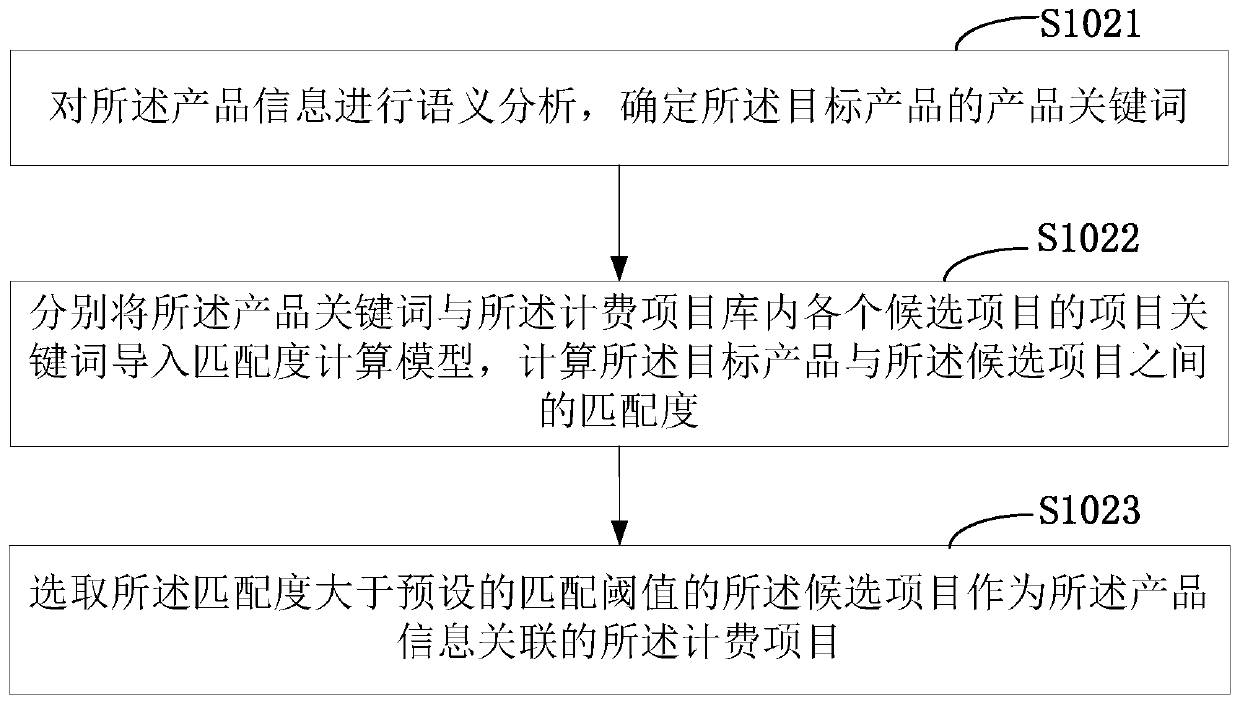
A calculation model generation method and device
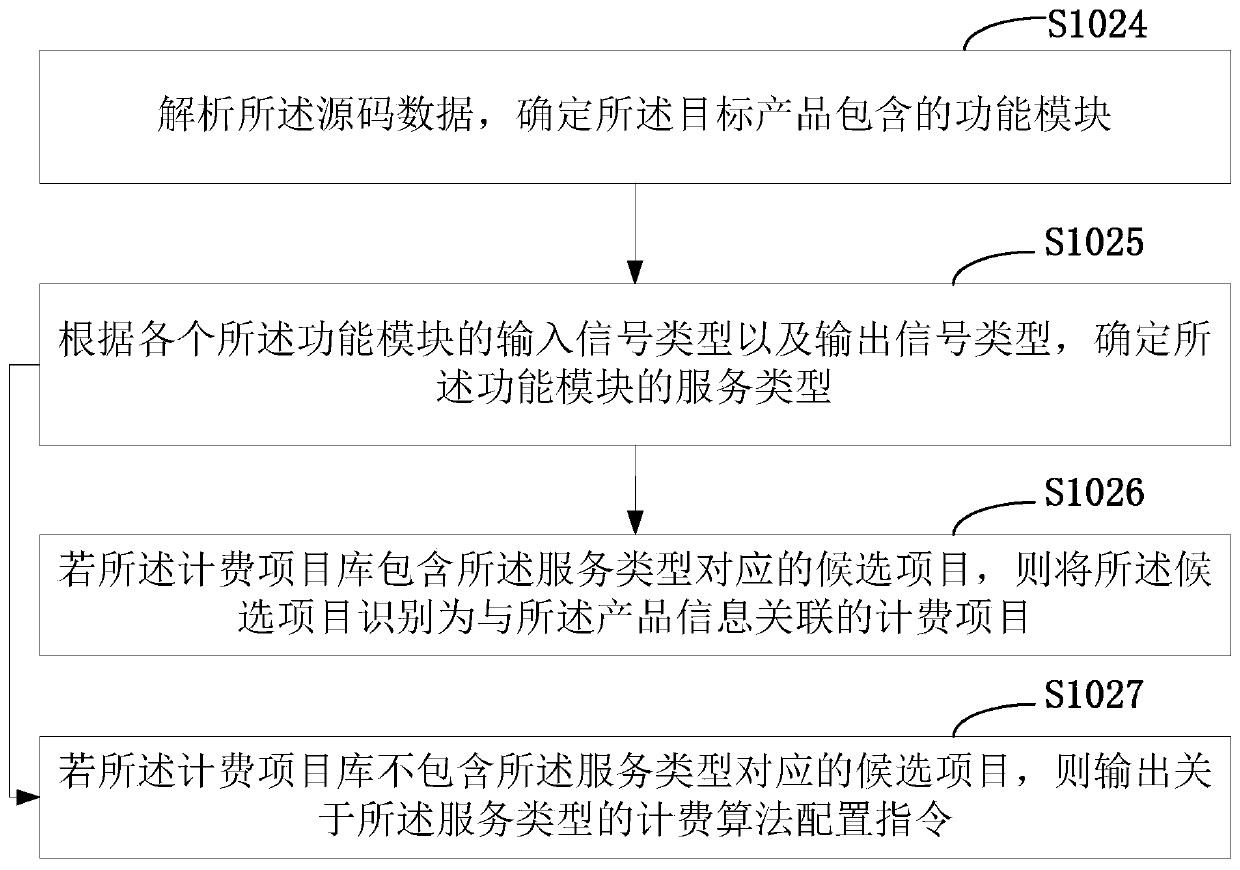
PendingCN109741086ARealize automatic generationImprove production efficiencyMarketingProduct baseProduct Identifier
The invention is suitable for the technical field of data processing, and provides a calculation model generation method and device, and the method comprises the steps: receiving a charging model generation request; obtaining product information of the target product based on the product identifier, and extracting at least one charging project associated with the product information from a charging project library; generating a charging template about the target product according to the charging algorithm of each charging project; and adjusting the bit value of the configurable parameter in the charging template through the user information, and generating a charging model about the requesting user. The matched charging model can be automatically generated according to the user informationand the product information, the generation efficiency of the charging model is improved, and the configuration difficulty is reduced.
Owner:PING AN TECH (SHENZHEN) CO LTD
Method and apparatus for configuration of virtual local area network
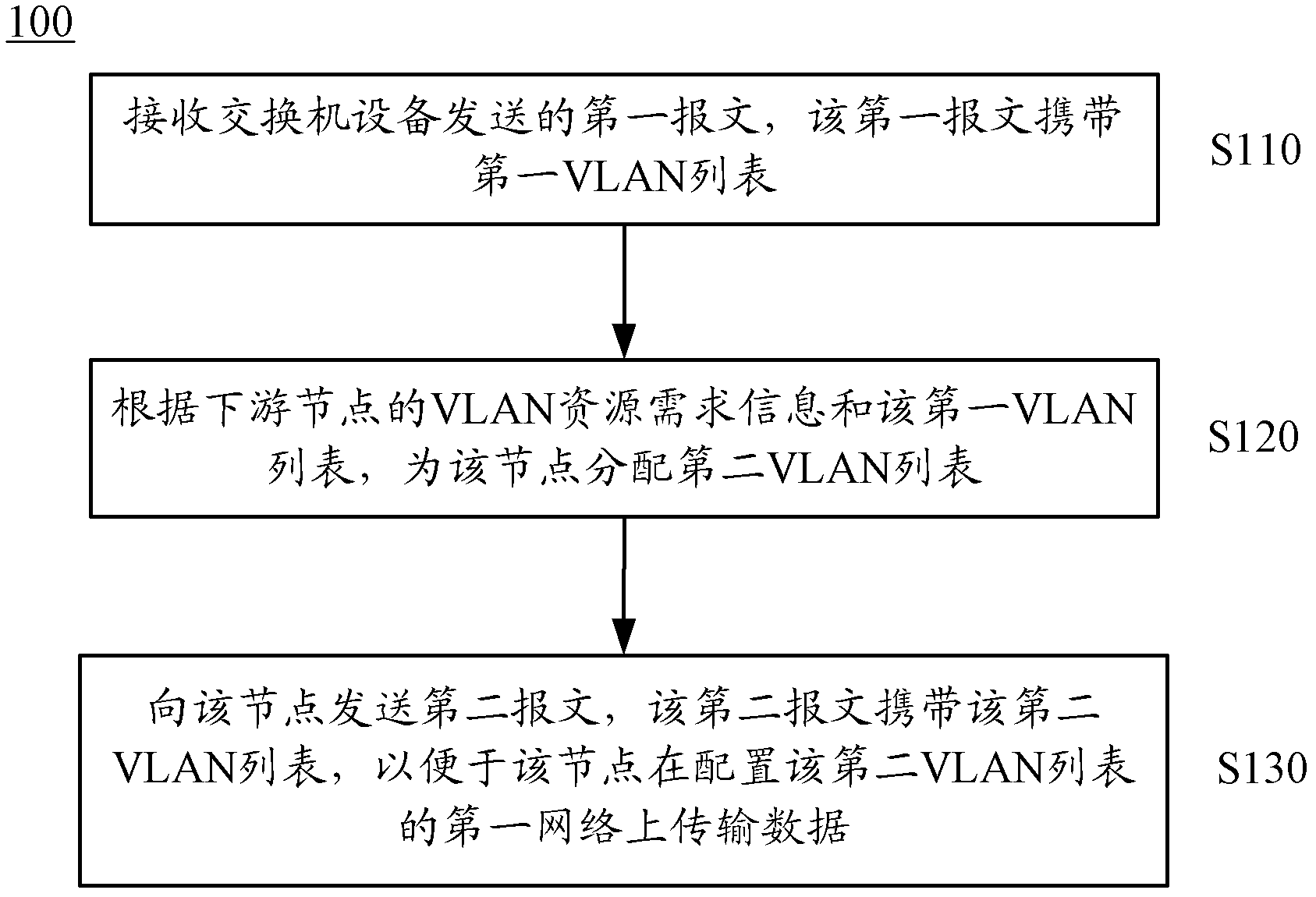
ActiveCN102316002AReduce configuration difficultyReduce networking costsNetworks interconnectionVirtual LANNetworked system
The embodiment of the invention provides a method and an apparatus for configuration of a virtual local area network. The method comprises the following steps that: a first message that is sent by forwarder equipment is received, wherein the first message carries a first virtual local area network (VLAN) listing; according to VLAN resource demand information of a downstream node and the first VLAN listing, a second VLAN listing is distributed to the node; and a second message is sent to the node and the second message carries the second VLAN listing, so that it is convenient that the node transmits data on a first network that is configured to the second VLAN listing. According to the method and the apparatus for configuration of the virtual local area network provided in the embodiment of the invention, a VLAN is distributed to a node according to VLAN resource demand information based on the node; therefore, a configuration difficulty is reduced and networking costs are saved; meanwhile, a risk that is brought by dynamically obtaining lots of VLAN information on networking can be avoided, so that market competitiveness of a network system can be substantially improved.
Owner:HUAWEI TECH CO LTD
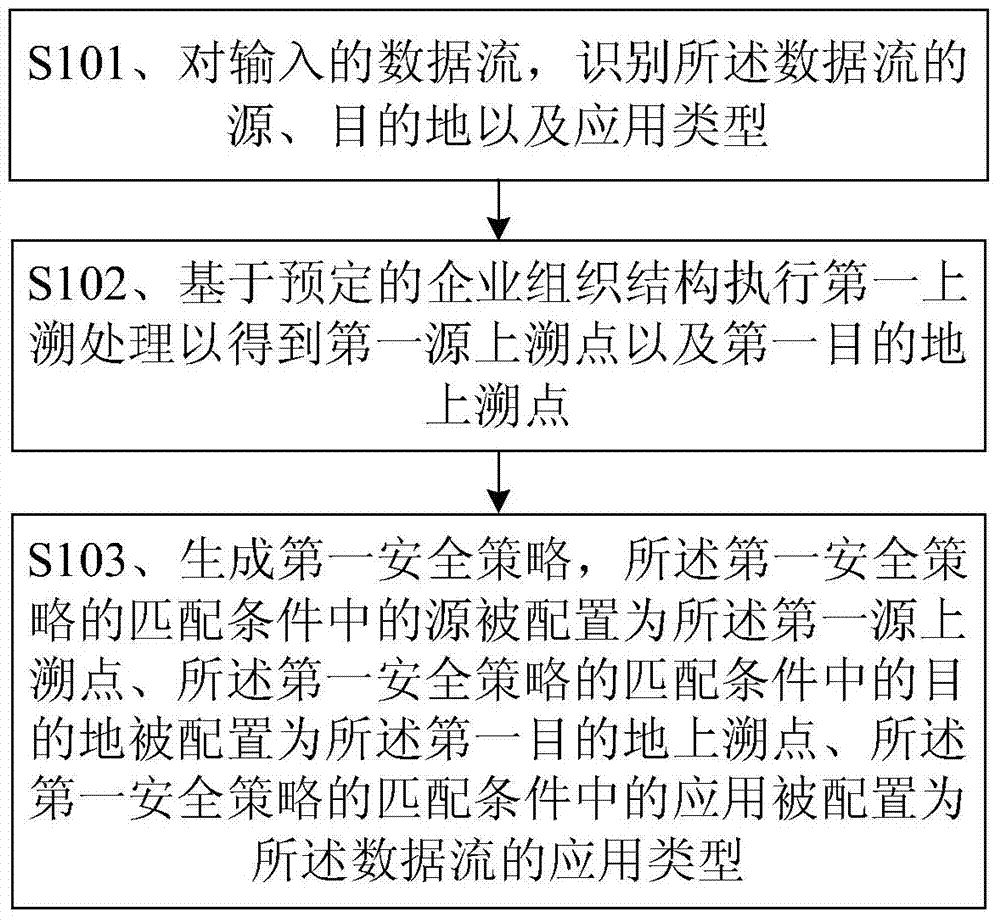
Network flow control equipment and security policy configuration method and device thereof
ActiveCN104753857AReduce configuration difficultyIncrease success rateTransmissionData streamSecurity policy
The present invention relates to a network flow control device, and security strategy configuration method and device thereof, the method comprising: identifying the source, destination and application type of an input data stream; conducting first back tracing based on a predetermined enterprise organizational structure to obtain a first source back trace point and a first destination back trace point; and generating a first security strategy, the source in the matching condition of the first security strategy being configured as the first source back trace point, the destination in the matching condition of the first security strategy being configured as the first destination back trace point, and the application in the matching condition of the first security strategy being configured as the application type of the data stream. The first back tracing is executed via the predetermined enterprise organizational structure to obtain the first source back trace point and the first destination back trace point so as to generate the first security strategy. The security strategy configuration method and device on a network flow control device in an embodiment of the present invention can automatically generate a security strategy, thus reducing the configuration difficulty of the security strategy, and improves the configuration success rate.
Owner:HUAWEI TECH CO LTD
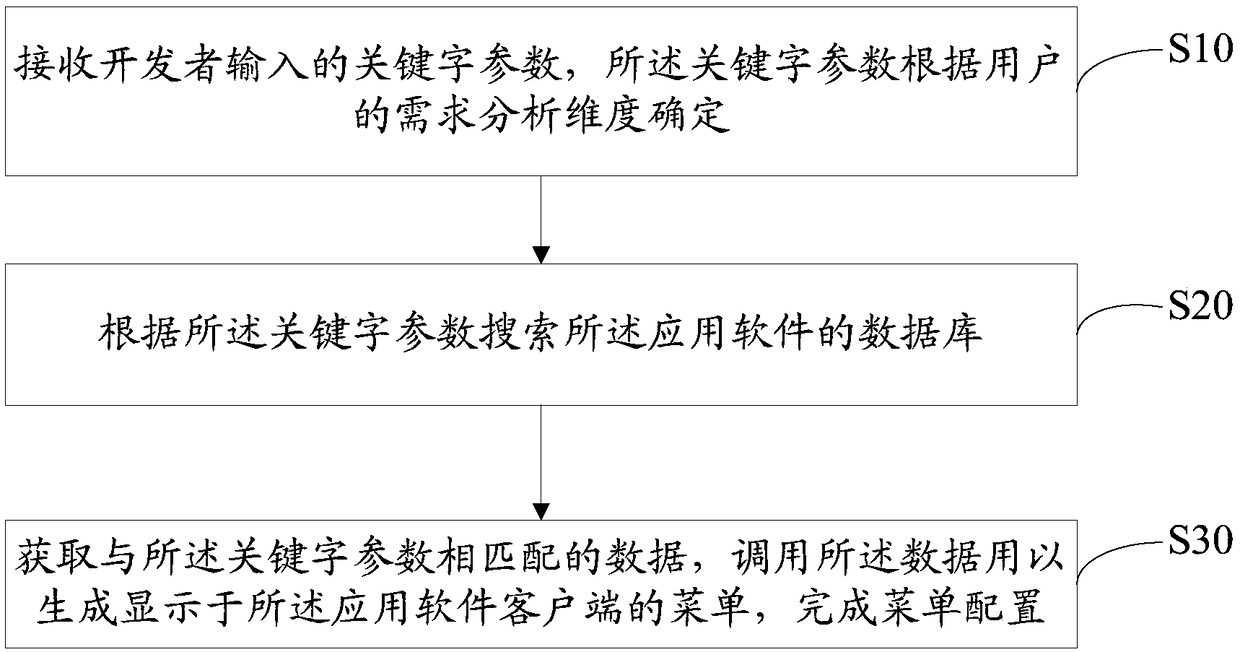
Application software menu configuration method, mobile terminal and computer readable storage medium
ActiveCN109165053ASimplify operational complexityReduce difficultyProgram loading/initiatingText database queryingDynamic displayData matching
The invention discloses an application software menu configuration method, a mobile terminal and a computer readable storage medium. The method is applied to the mobile terminal. The method comprisesthe following steps: a keyword parameter input by a developer is received, wherein the keyword parameter is determined by demand analysis dimension of a user; the database of the application softwareis searched according to the keyword parameters; data matching with the keyword parameters is obtained, and the data is called to generate a menu displayed on the application software client, therebycompleting menu configuration. A keyword search data source generation menu is prepared by the user according to the need, the system realizes that menus can display the operation trajectory of the service from multiple different dimensions, the dynamic display functions such as process link and life cycle can meet the requirements of different customers and different businesses for different datadimensions, and the technical problems of a single fixed menu page function, high configuration difficulty, complex program coding, fixed menu options, and single business information dimension displayed by the user interface of the existing application software are solved.
Owner:康美健康云服务有限公司
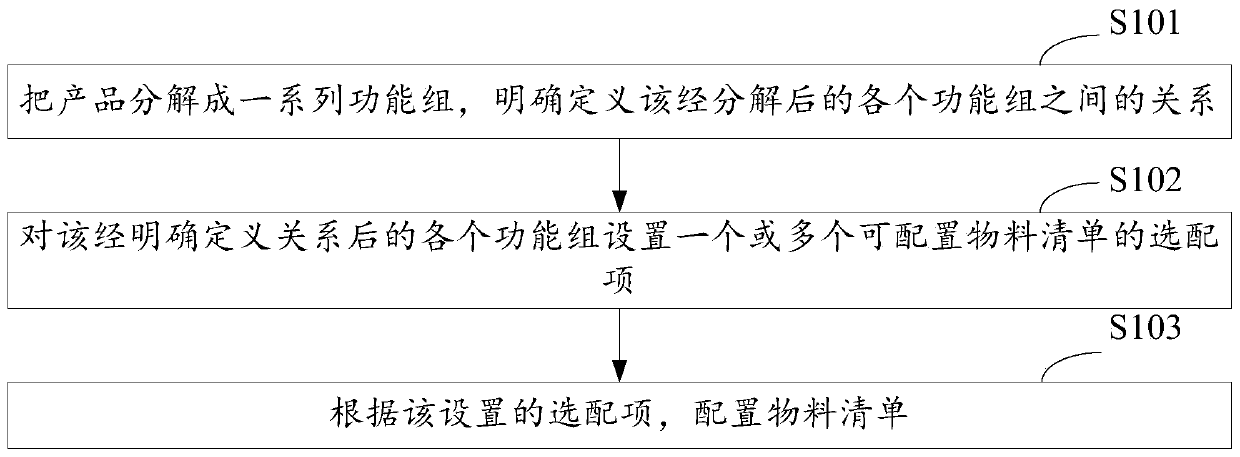
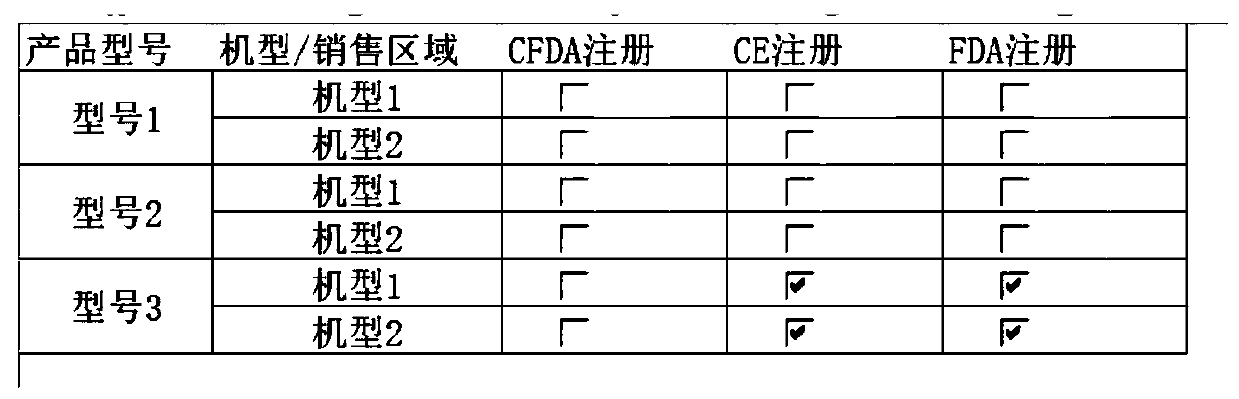
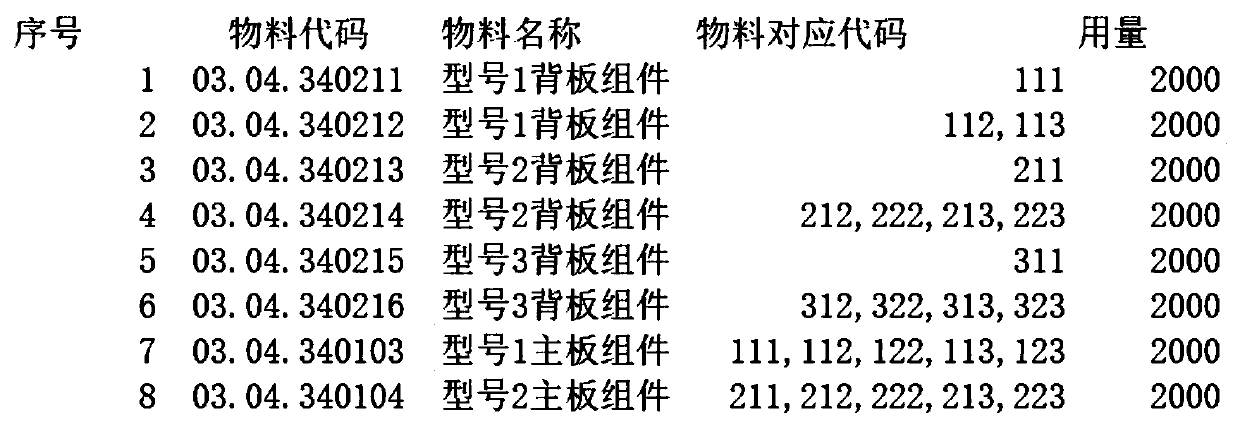
A bill of material configuration method, device and equipment of an enterprise resource planning system
PendingCN109948938AReduce CODEasy to customizeResourcesLogisticsBill of materialsEnterprise resource planning
The invention discloses a bill of material configuration method, device and equipment for an enterprise resource planning system. The method comprises the following steps of: decomposing a product into a series of functional groups, clearly defining the relationship among the decomposed functional groups, setting one or more matching items capable of configuring a bill of material for each functional group subjected to the clear definition of the relationship, and configuring the bill of material according to the set matching items. Through the mode, the bill of material configuration processis simple, the operation is convenient, and the accuracy is high.
Owner:SHENZHEN POLYTECHNIC
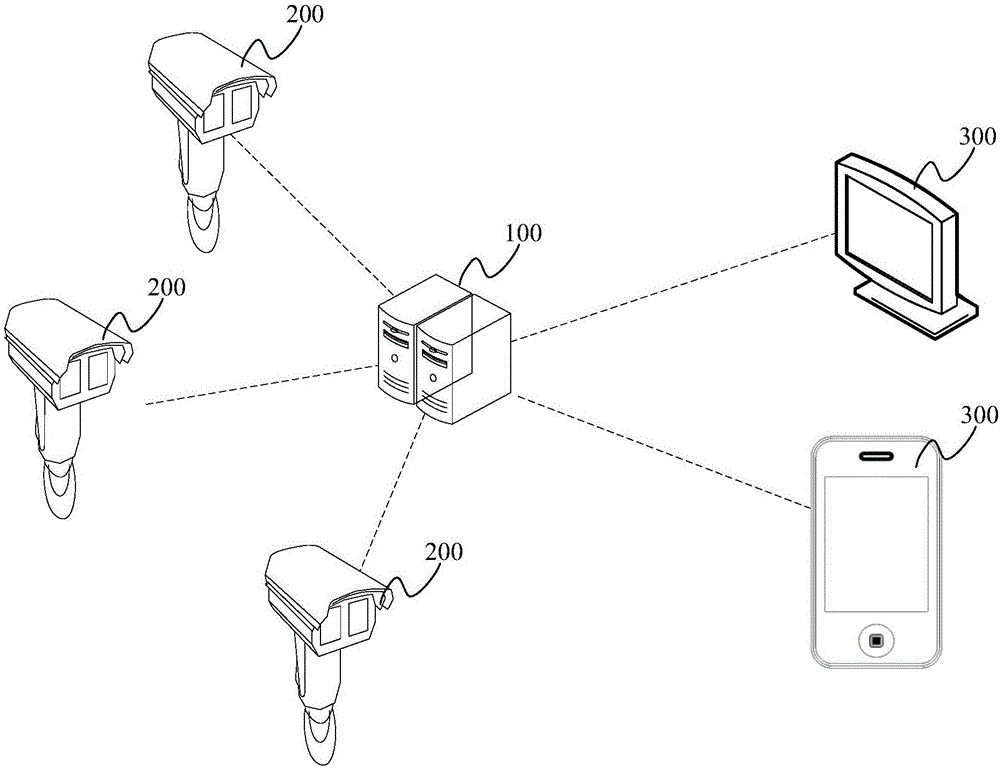
Monitoring system
InactiveCN106603992AReduce configuration difficultyReduce difficulty of useTelevision system detailsColor television detailsMonitoring systemEmbedded system
The application discloses a monitoring system. When the monitoring system is utilized to configure a camera, a user only needs to send registration information containing a corresponding relationship between user information and the camera to a server through a terminal, a permission relationship between the user information and the camera is generated and stored according to the corresponding relationship between user information and the camera contained in the registration information after the server receives the registration information, and then camera configuration is completed. After the camera configuration is finished, the user can send query information through the terminal to obtain shooting images of a target camera so as to monitor the shooting images of the target camera in real time. It is less difficult to configure the camera of the monitoring system, and it is less difficult for the user to use. Moreover, the user can check monitoring situations anytime and anywhere in different forms through the monitoring system. Furthermore, videos obtained by the monitoring system can be stored in a network hard disk, and requirements of equipment used by the user are not strict.
Owner:SHENZHEN IPANEL TECH LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com