Network flow control equipment and security policy configuration method and device thereof
A technology of security policy and network traffic, applied in the field of network security, can solve the problems of difficult configuration and error-prone, and achieve the effect of reducing configuration difficulty, improving efficiency, and improving success rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
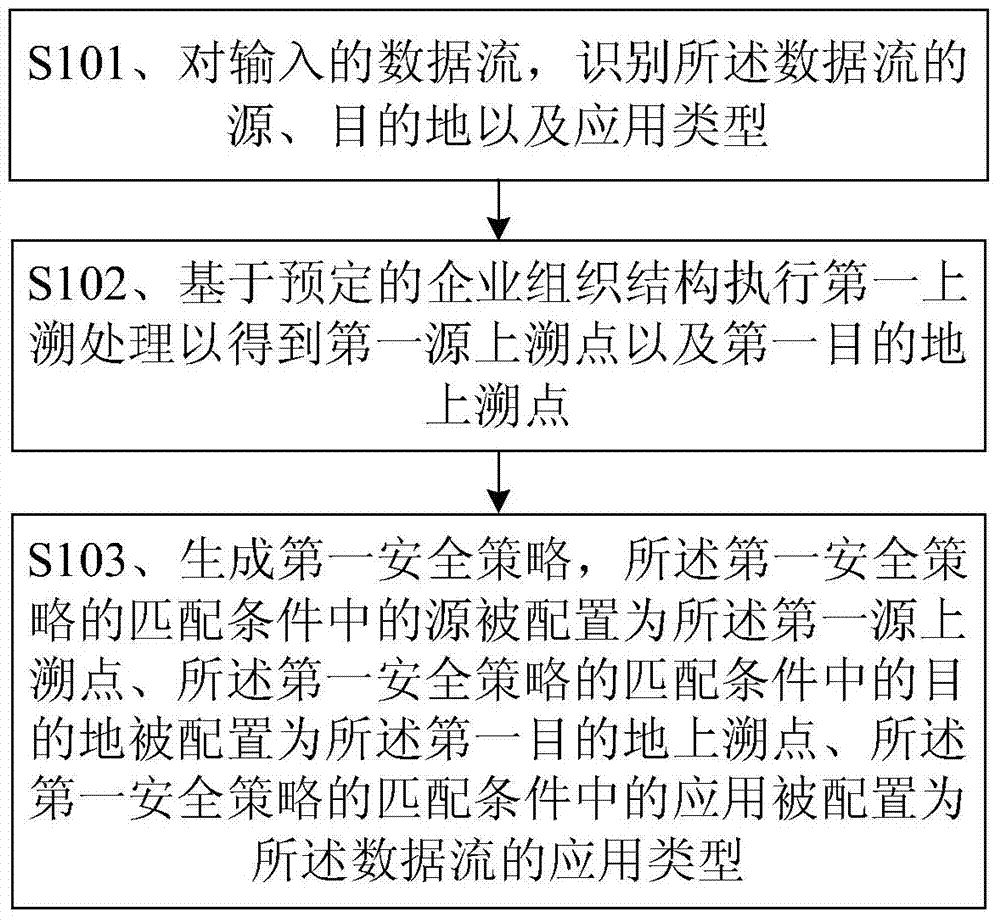
[0068] figure 1 A flowchart showing a method for configuring a security policy on a network traffic control device according to an embodiment of the present invention. The network flow control device in the embodiment of the present invention includes, but is not limited to, network devices such as firewalls, routers, and intrusion detection devices. Such as figure 1 As shown, the method mainly includes:
[0069] Step S101, for the input data flow, identify the source, destination and application type of the data flow.
[0070] Wherein, the source indicates the user or user address that sends out the data stream, such as user A or the user's network protocol address (English: Internet Protocol Address, abbreviation: IP address); the destination of the data stream indicates the recipient of the The user address, server address, or public network address of the data flow, and the application type indicates which application data the data flow includes, for example, the appl...
Embodiment 2
[0097] Figure 7 A flowchart showing a method for configuring a security policy on a network traffic control device according to another embodiment of the present invention. Figure 7 Winning mark and figure 1 The same components have the same functions, and detailed descriptions of these components are omitted for brevity. Such as Figure 7 As shown, in a possible implementation, after step S101, the method further includes:
[0098] Step S701, judging whether triplet information matching the source, destination and application type of the data flow exists in the memory.
[0099] When it is determined that there is no triplet information matching the source, destination and application type of the data flow in the memory, execute step S102;
[0100] If it is determined that there is matching triplet information, the process ends.
[0101] Step S102, and figure 1 Step S102 is similar and will not be repeated here.
[0102] Step S702, storing the first source uptrackin...
Embodiment 3
[0125] Figure 10 A schematic structural diagram of an apparatus for configuring a security policy on a network traffic control device according to an embodiment of the present invention is shown. Such as Figure 10 As shown, the device 10 includes: an identification module 110 , a first traceback processing module 120 , and a generation module 130 .
[0126] The identification module 110 is configured to identify the source, destination and application type of the data flow for the input data flow, wherein the source represents the user or user address that sends the data flow, and the destination of the data flow Indicates the user address, server address or public network address receiving the data stream, and the application type indicates which application data is included in the data stream.
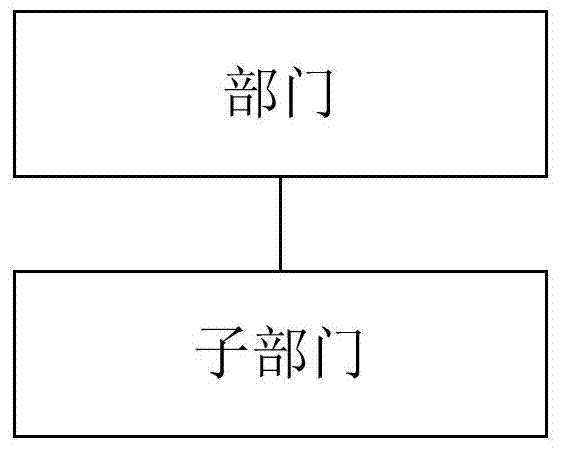
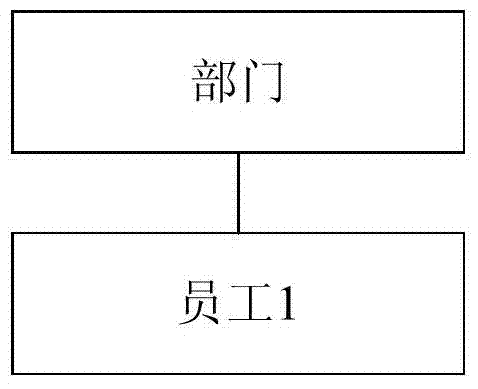
[0127] The first upward tracing processing module 120 is connected with the identification module 110, and is used to execute the first upward tracing processing based on the pre...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com