A plug-in-based iOS security compiler and a security compiling method
A compilation method and compiler technology, applied in the direction of program/content distribution protection, etc., can solve the problems of difficulty in building a secure compilation environment, incoherent operations, and high resource overhead, and achieve significant code protection effects, high configuration freedom, and installation. Convenient and fast effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The following examples of the present invention are described in detail below. The following examples are implemented on the premise of the technical solution of the present invention, and detailed implementation methods and specific operating procedures are provided, but the protection scope of the present invention is not limited to the following the embodiment.
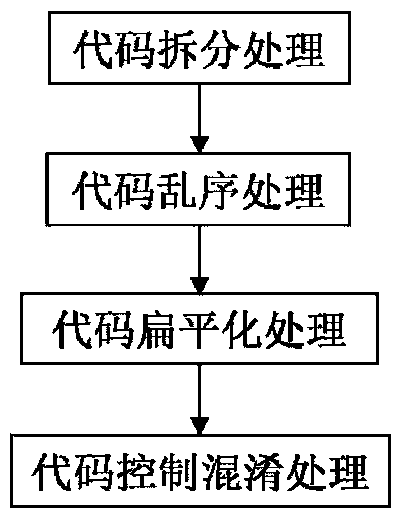
[0030] Such as figure 1 As shown, in a preferred embodiment, the plug-in-based iOS security compiling method of the present invention comprises the following steps:
[0031] Step 1. Split the code: In the process of compiling the source code to the target code, on the basis of ensuring the logic is correct, split all the basic code blocks in the function into finer-grained code blocks. The above functions include variable declaration function, loop control function, class method, object method, etc., which are divided into variable declaration block, loop control block, class method block, object method blo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com