Encryption system supporting fine-grained access control
An access control and encryption system technology, applied in the field of information security, can solve problems such as high overhead, poor security, and complex cloud storage server management, and achieve the effect of reducing ciphertext storage space, fine-grained access control, and improving overall performance.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
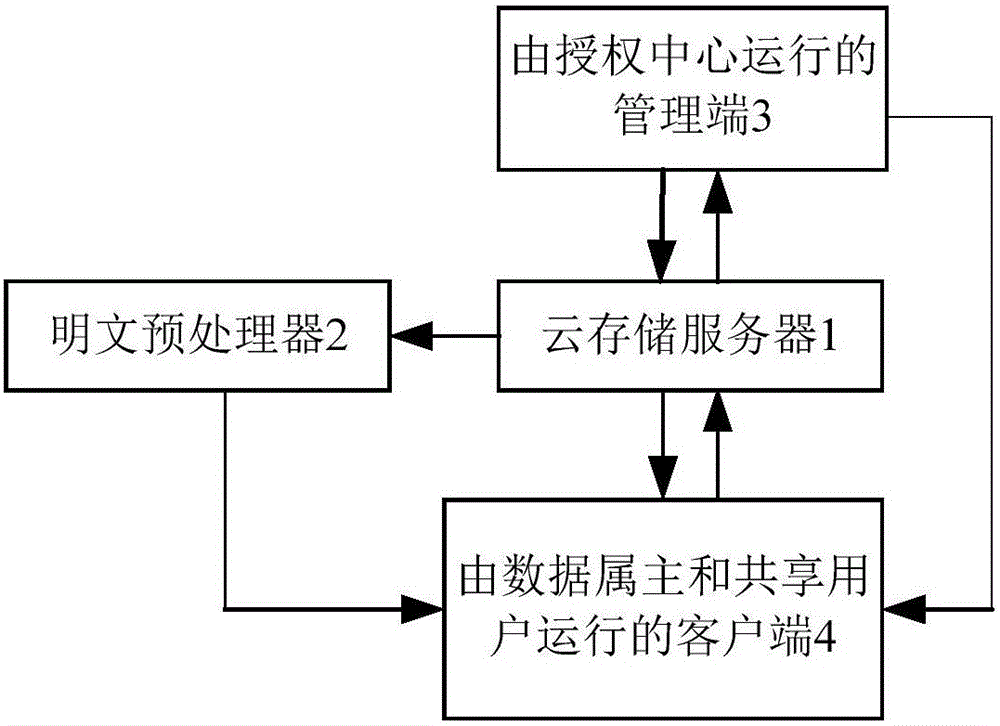
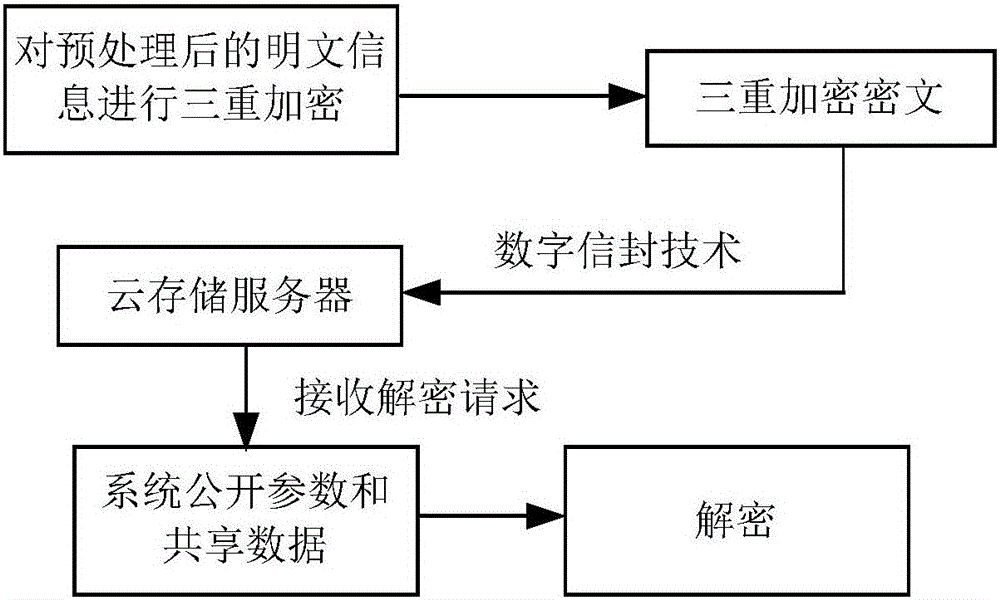
[0046] see figure 1 , figure 2 , the implementation of this embodiment supports fine-grained access control encryption system, including cloud storage server 1, plaintext preprocessor 2, management terminal 3 operated by authorization center, client 4 operated by data owner and shared user:
[0047] (1) cloud storage server 1, used to provide data storage services for access users, and control external users to access the cloud storage server;
[0048] (2) The management terminal 2 operated by the authorization center is used to generate the initial public parameters and master key of the system. When receiving the request from the access user, it is distributed to the client 4 operated by the data owner and shared user The system publicizes the parameters, and generates a corresponding private key for each access user, and participates in the connection between the cloud storage server 1 and the access users accessed by the client 4 run by the data owner and shared user at ...
Embodiment 2
[0079] see figure 1 , figure 2 , the implementation of this embodiment supports fine-grained access control encryption system, including cloud storage server 1, plaintext preprocessor 2, management terminal 3 operated by authorization center, client 4 operated by data owner and shared user:
[0080] (1) cloud storage server 1, used to provide data storage services for access users, and control external users to access the cloud storage server;
[0081] (2) The management terminal 2 operated by the authorization center is used to generate the initial public parameters and master key of the system. When receiving the request from the access user, it is distributed to the client 4 operated by the data owner and shared user The system publicizes the parameters, and generates a corresponding private key for each access user, and participates in the connection between the cloud storage server 1 and the access users accessed by the client 4 run by the data owner and shared user at ...
Embodiment 3
[0112] see figure 1 , figure 2 , the implementation of this embodiment supports fine-grained access control encryption system, including cloud storage server 1, plaintext preprocessor 2, management terminal 3 operated by authorization center, client 4 operated by data owner and shared user:
[0113] (1) cloud storage server 1, used to provide data storage services for access users, and control external users to access the cloud storage server;
[0114] (2) The management terminal 2 operated by the authorization center is used to generate the initial public parameters and master key of the system. When receiving the request from the access user, it is distributed to the client 4 operated by the data owner and shared user The system publicizes the parameters, and generates a corresponding private key for each access user, and participates in the connection between the cloud storage server 1 and the access users accessed by the client 4 run by the data owner and shared user at ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com