Access control method and device based on token and supporting object attributes
An access control and token technology, applied in the computer field, can solve the problems of low access control efficiency, achieve the effect of improving access control efficiency, reducing applications, and reducing data volume
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
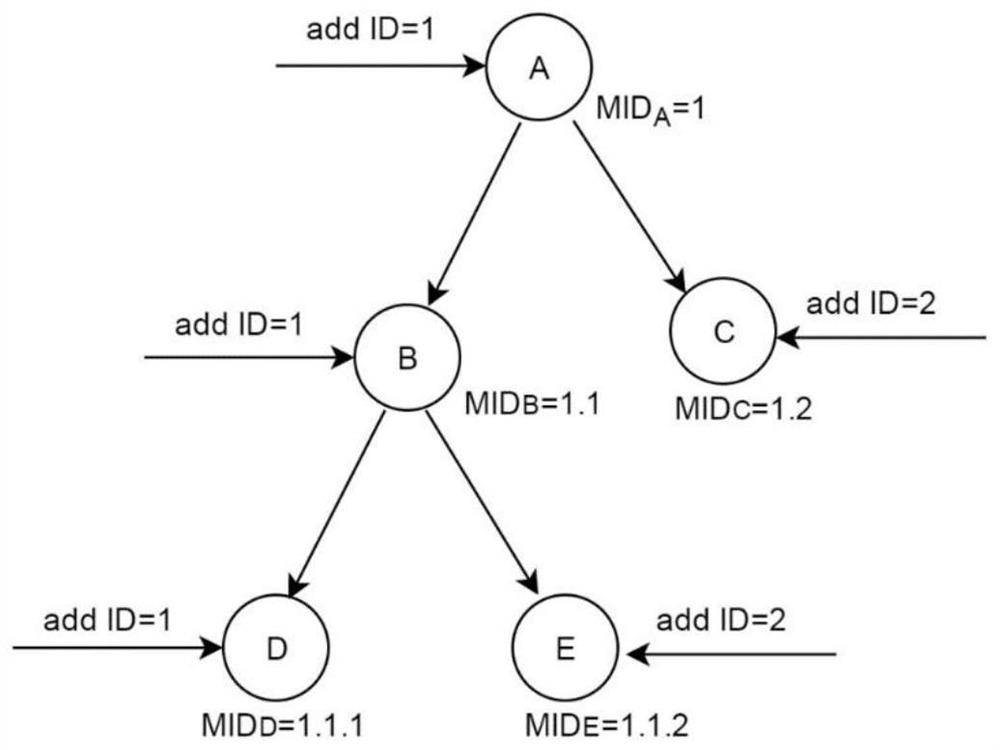
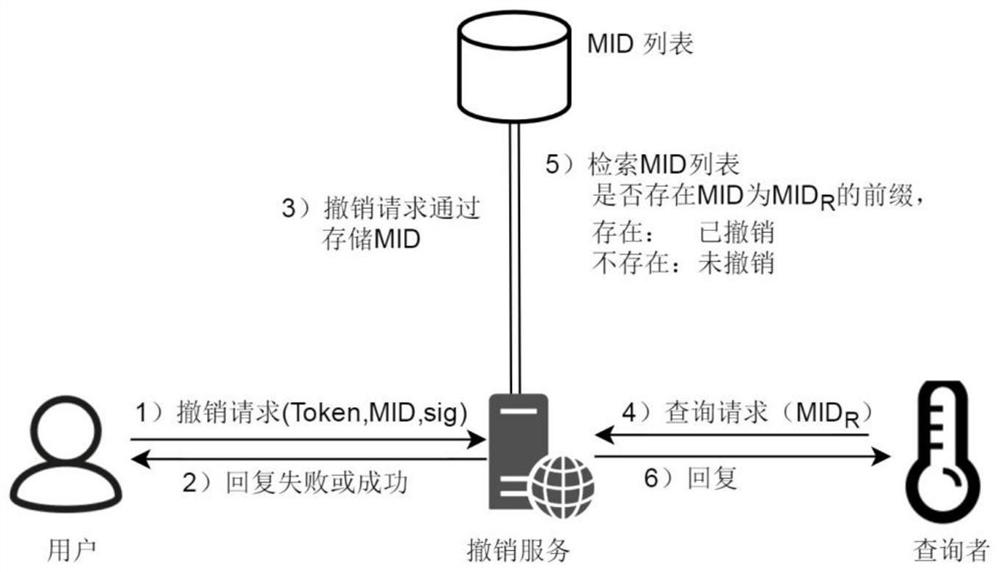
[0035] This embodiment provides a token-based access control method that supports object attributes, including the following steps:
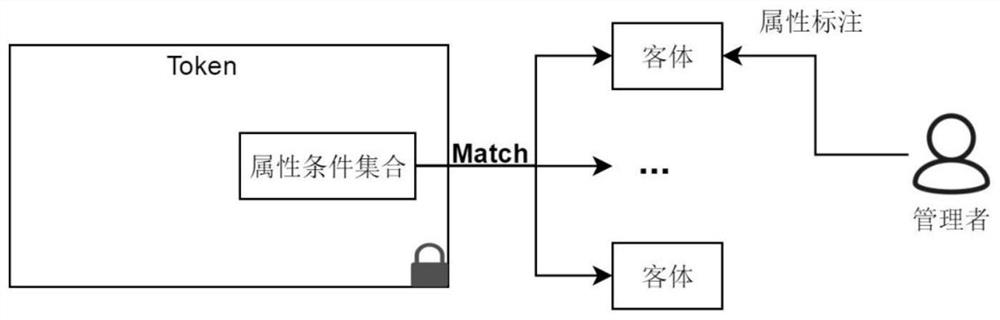
[0036]S1: The management side predefines the category of attribute conditions and the category of access rights, and marks the attributes of the managed devices. The category of attribute conditions is an abstraction of a class of attribute conditions, and an attribute condition category is set by setting specific attributes. Parameters can be transformed into an attribute condition, and multiple attribute conditions constitute the attribute condition set CS. CS represents the conditions that the object of the token needs to meet, and is used to limit the object range of the token. Selecting some access rights categories can form the access rights set AR , AR is used to represent the operations that the subject of the token can perform on the object;
[0037] S2: The management side receives the first token request sent by the applicant, and tak...
Embodiment 2
[0201] Based on the same inventive concept, the present invention also provides a token-based access control device that supports object attributes, including:
[0202] The preprocessing module is used to predefine the category of attribute conditions and the category of access rights, and perform attribute labeling on the managed devices. The category of attribute conditions is an abstraction of a class of attribute conditions. The attribute parameters of the token can be converted into an attribute condition, and multiple attribute conditions constitute the attribute condition set CS. CS represents the conditions that the object of the token needs to meet, and is used to limit the object range of the token. Selecting some types of access rights can constitute access rights Set AR, AR is used to represent the operations that the subject of the token can perform on the object;
[0203] The token request receiving module is used to receive the first token request sent by the ap...
Embodiment 3
[0207] Based on the same inventive concept, a computer device includes a memory, a processor, and a computer program stored in the memory and operable on the processor, and the processor implements the method described in Embodiment 1 when executing the program.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com