Entrance guard control method, apparatus, terminal and control server
A control server and access control technology, applied in the Internet field, can solve problems such as low intelligence, loss or abuse of access control cards, and insufficient environmental protection, and achieve the effects of improving efficiency, improving security, and improving intelligence
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
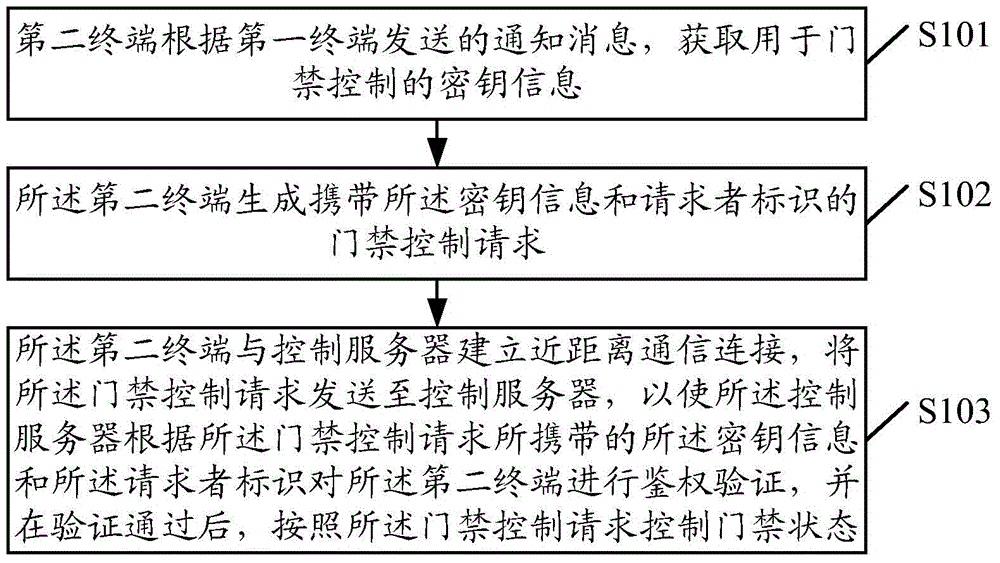
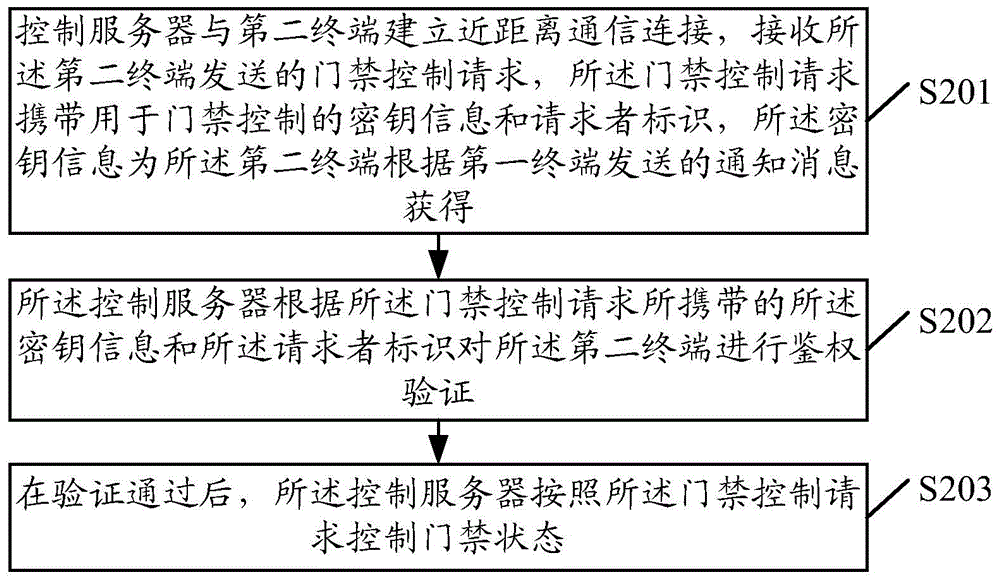
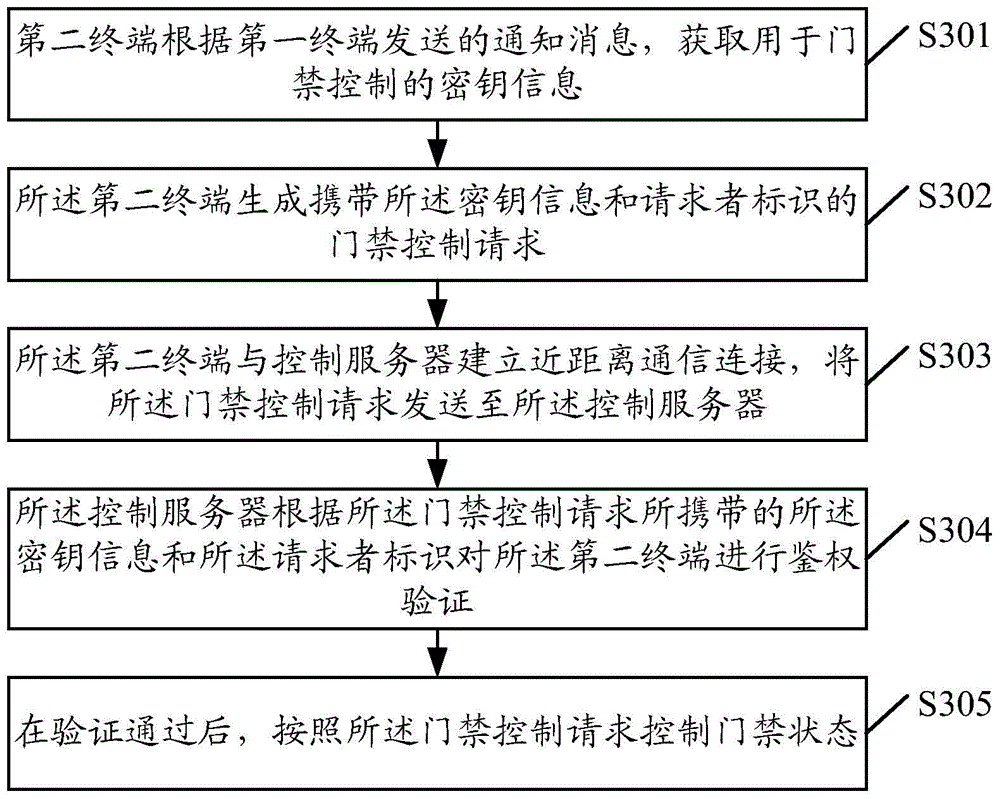
[0125] In a first feasible implementation manner, step S509 specifically includes the following steps A-B:
[0126] A. The control server judges whether the system time corresponding to the receiving moment of the access control request is the effective use time of the key information included in the aging rule.
[0127] B. If the system time is the effective use time of the key information, the control server confirms that the key information is used according to the aging rule.
[0128] If the system time is the valid time of the key information included in the aging rule, it indicates that the second terminal uses the key information within the valid time of the key information, and the control server confirms that the The key information is used according to the aging rules. Otherwise, if the system time is not the valid time of the key information included in the aging rule, indicating that the second terminal uses the key information at the expiration time of the key in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com