Architecture for protecting key data based on mimicry defense
A key data, heterogeneous technology, applied in the direction of digital data protection, electronic digital data processing, instruments, etc., can solve the problems of data encryption increase, cracking, data security depends on encryption algorithm and key, etc., to ensure normal Output, the effect of data leakage prevention
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0042] For the protection of data in information systems, different types of data should have different protection strengths according to their importance, otherwise the breakthrough of key data protection may even threaten the entire protection system. Therefore, improper protection of key data will become a weak link in the security of the entire information system. For example, if the access control lists (Access Control Lists, ACL) maintained by the firewall can be maliciously stolen and tampered with, the access control will lose its meaning, and the entire information system will also be exposed to security threats. In the following, the specific content of the present invention will be described in detail by taking the ACL protection problem as a use case.
[0043] Working Mechanism
[0044]The present invention introduces a mimic defense mechanism. There will be different degrees of differences in the specific application of mimic defense, and the final mechanism arc...
Embodiment 2
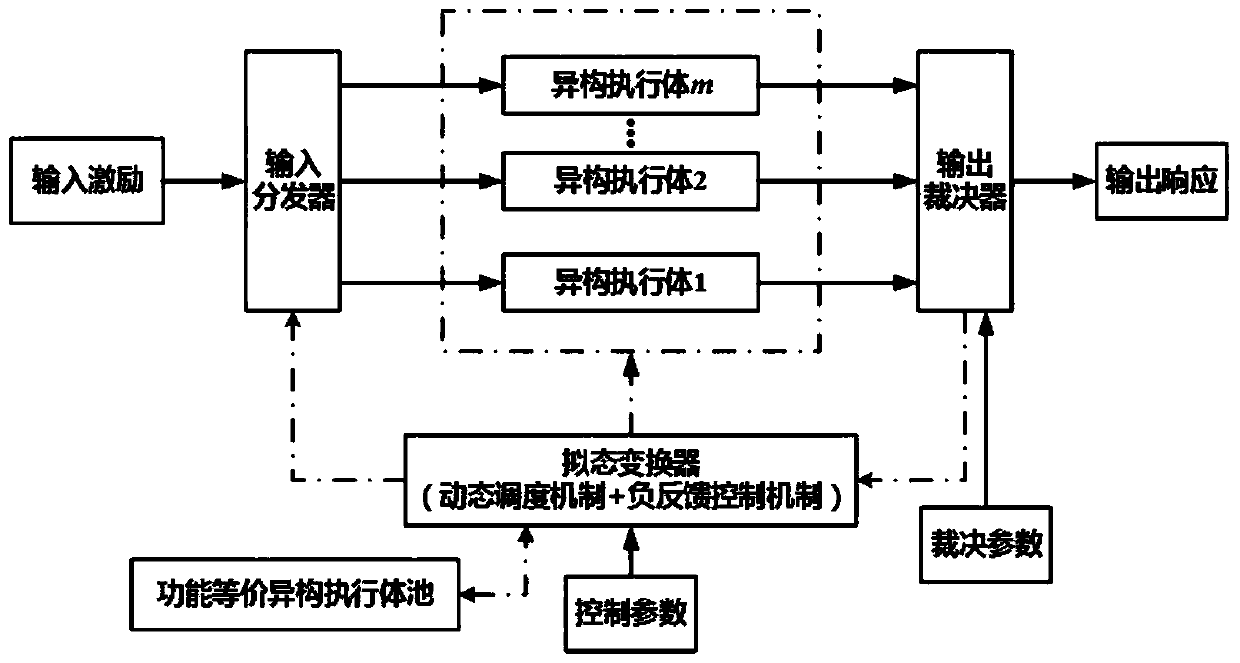
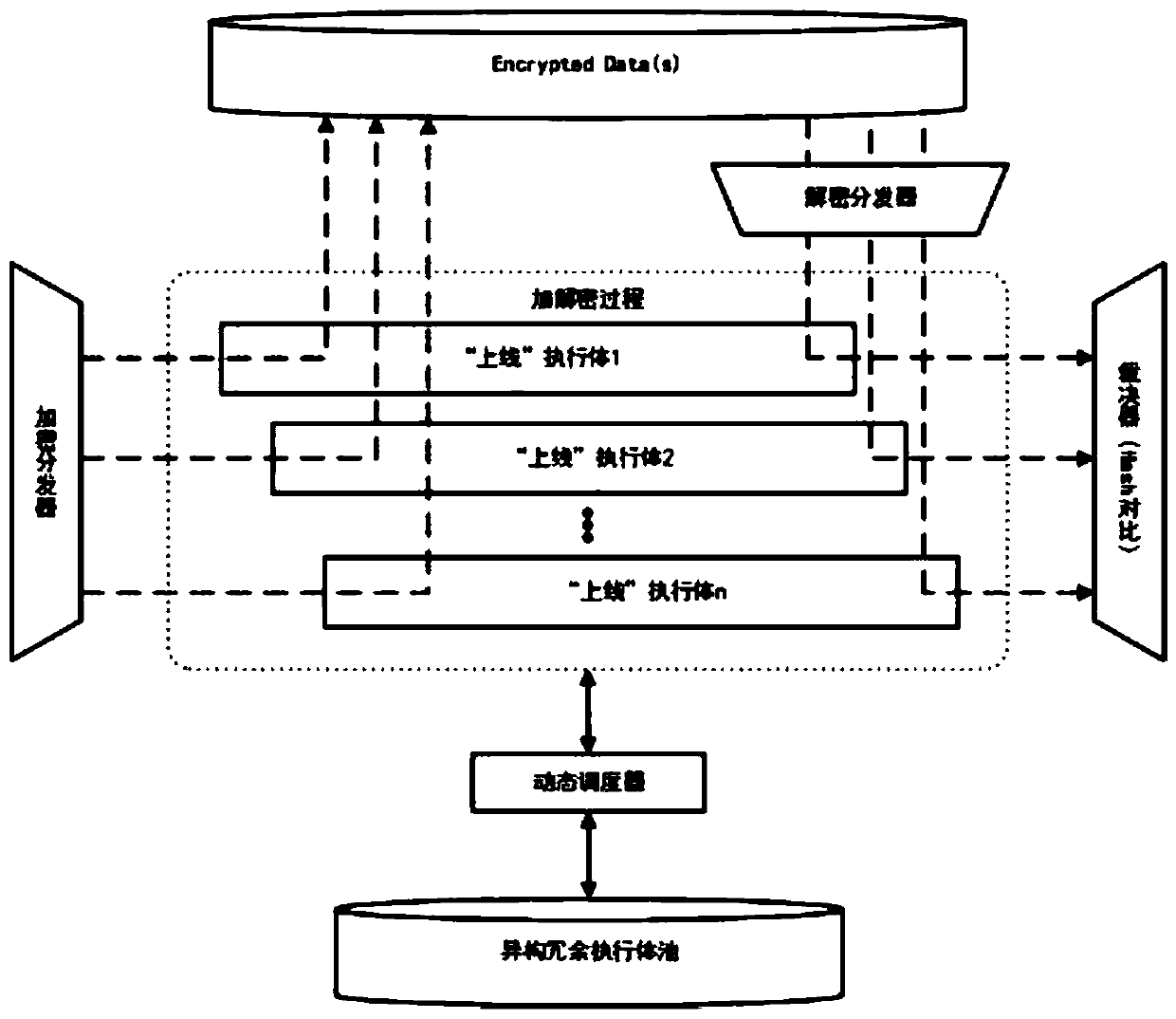
[0071] Such as Figure 1-2 As shown, an architecture based on mimic defense technology to protect key data, which includes heterogeneous redundant executives, distributors, arbitrators and dynamic schedulers; heterogeneous redundant executives: all heterogeneous redundant executives A pool of executives is formed, and the business function of these executives is to encrypt and decrypt data. It is emphasized here that the heterogeneous redundant execution body here is in an abstract sense, which will be explained later in the analysis of the heterogeneous dimension. Distributor: Contains two kinds of distributors, encrypted distributor and decrypted distributor. Arbiter: Carry out multi-mode adjudication, generate correct output and throw problem input according to the adjudication result. Dynamic scheduler: dynamically schedules heterogeneous redundant executives according to policies.
[0072] exist figure 2 In , the solid arrows represent the control flow, and the dashe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com