Trusted computing-based dynamic management service system and method
A dynamic management and trusted computing technology, applied in the field of information security, can solve problems such as the lack of practical and perfect solutions, and achieve the effects of improving configurability, preventing system tampering, and preventing data leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] In order to describe the technical content of the present invention more clearly, further description will be given below in conjunction with specific embodiments.
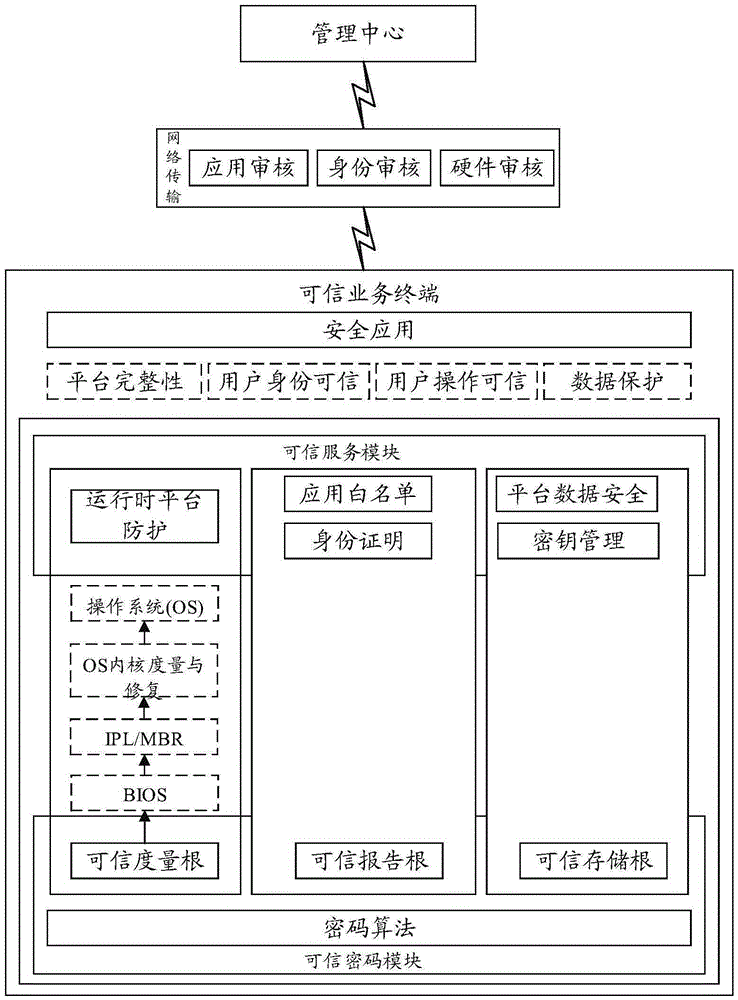
[0046] The present invention provides a dynamic management service system based on trusted computing, the basic structure is as follows figure 1 , including the following parts:
[0047] 1. Trusted password module
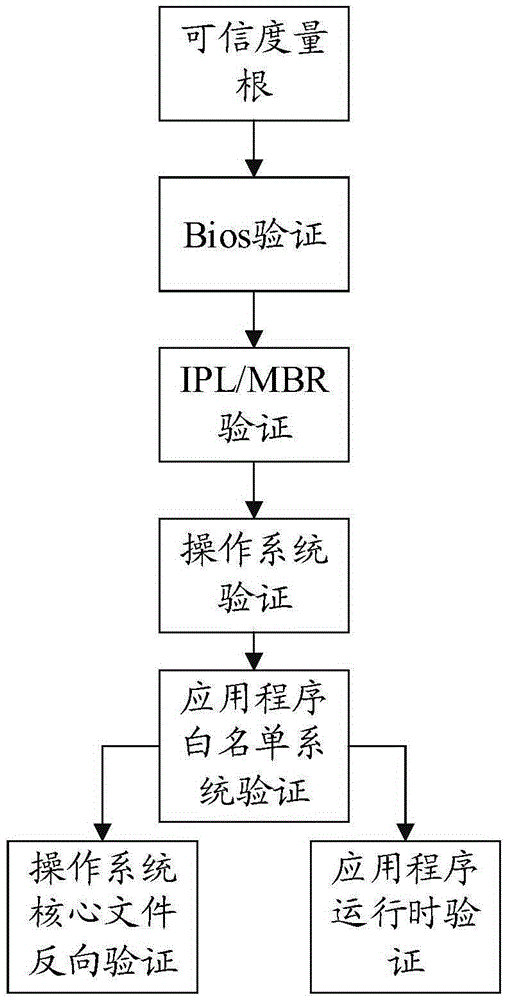
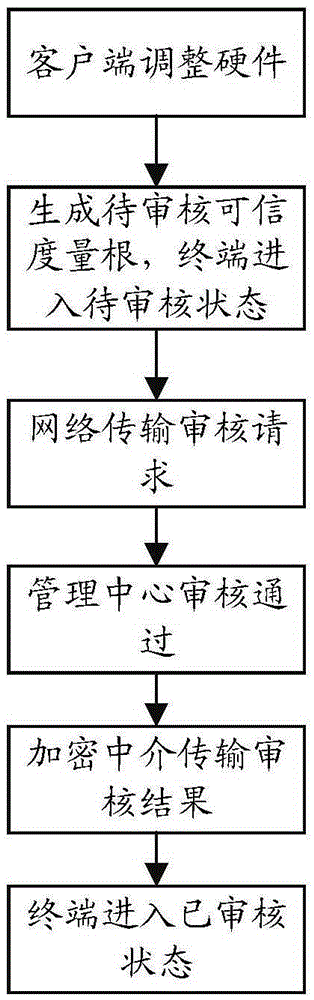
[0048] The trusted cryptographic module provides cryptographic calculation functions for the trusted business system to access the client. It has a protected storage space. It is actually a small system-on-chip containing cryptographic calculation components and storage components. processor, independent memory space, permanent storage space and independent bus input and output system. Using cryptographic algorithms that meet the standards, it provides externally with asymmetric key generation operations, asymmetric algorithm encryption and decryption operations, hash function operations, digi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com