Penetration test method in allusion to mobile geographic information security of underground pipelines
A penetration testing and geographic information technology, applied in computer security devices, electrical digital data processing, instruments, etc., can solve problems such as inability to penetrate testing, and inability of scanner crawlers to crawl links, to prevent data leakage and ensure system security. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] In order to illustrate the present invention more clearly, the present invention will be further described below in conjunction with preferred embodiments and accompanying drawings. Similar parts in the figures are denoted by the same reference numerals. Those skilled in the art should understand that the content specifically described below is illustrative rather than restrictive, and should not limit the protection scope of the present invention.
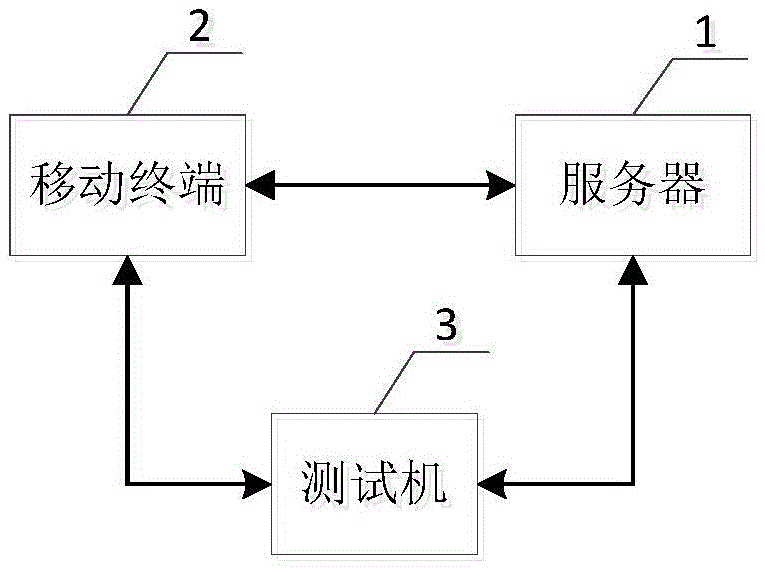
[0030] Such as figure 1 As shown, the testing system adopted in the penetration testing method for underground pipeline mobile geographic information security provided in this embodiment includes a server 1 , a mobile terminal 2 and a testing machine 3 . The mobile terminal 2 is usually a mobile phone or a tablet computer held by a professional professional engaged in mobile geographic information security work of underground pipelines. The testing machine 3 is used for testers to perform penetration testing on the securi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com