A method and device for implementing secure interaction between systems
A technology for realizing system and security, which is applied in the computer field to achieve the effect of improving scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0059] The present invention will be specifically described below in conjunction with a specific embodiment, but it should be noted that this specific embodiment is only for better describing the present invention, and does not constitute an improper limitation of the present invention.
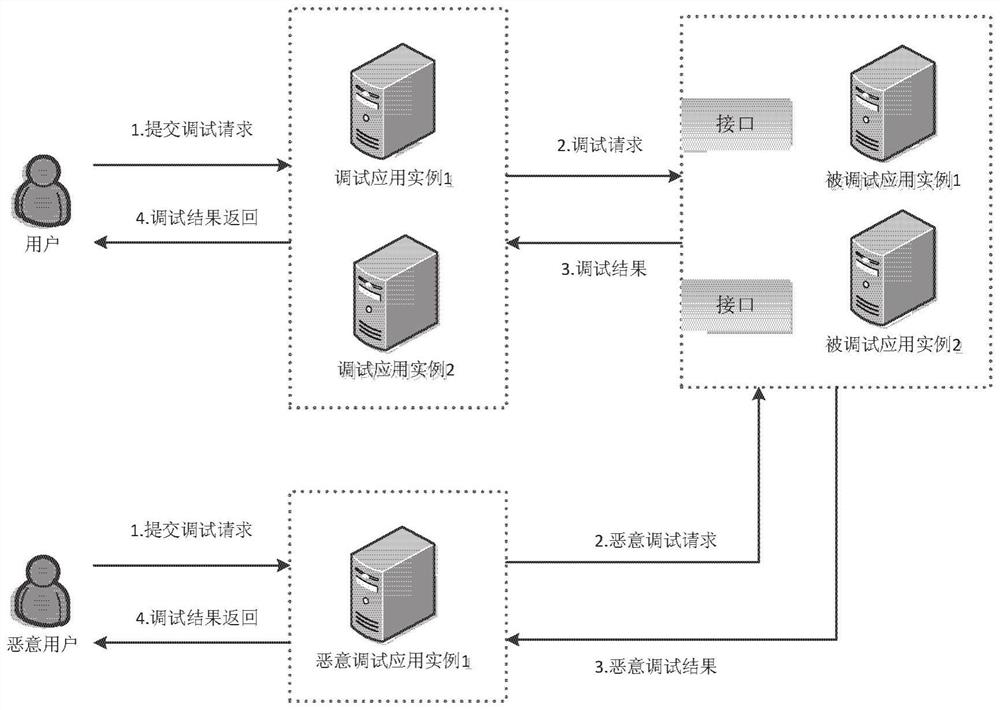
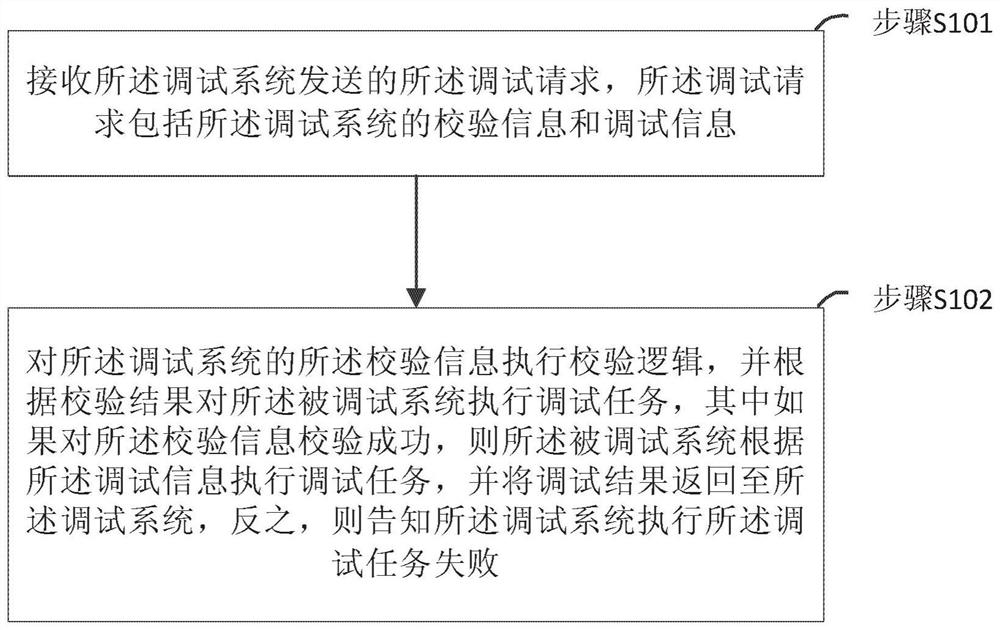
[0060] Step S201: the user initiates a debugging request, and the debugging system receives the debugging request from the user;
[0061] Step S202: The debugging system acquires the Token value of the debugged system from the local cache, if it does not exist in the local cache, then execute step S203; if it exists, then execute step S204;
[0062] Step S203: The monitoring system obtains the Token value list of the debugged system, finds the Token value of the currently called system, and stores the Token value in the local cache, and then executes Step S204;
[0063] Step S204: Set the acquired Token value of the debugged system into the set in the request header of the debug request, and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com