Data processing method and password management system
A password management and data processing technology, applied in the electronic field, can solve the problems of leakage and low password security performance.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0087] In the embodiment of the present application, a data processing method of how the password management system modifies the password in the server is described, the method is applied to a password management system, and at least one password including the first password is stored in the password management system, At least one password is used in combination with at least one account information corresponding to the at least one password to obtain the predetermined authority of at least one server, and the first password is used in conjunction with the corresponding first account information to obtain the predetermined authority of the first server, wherein at least one server Contains the first server.
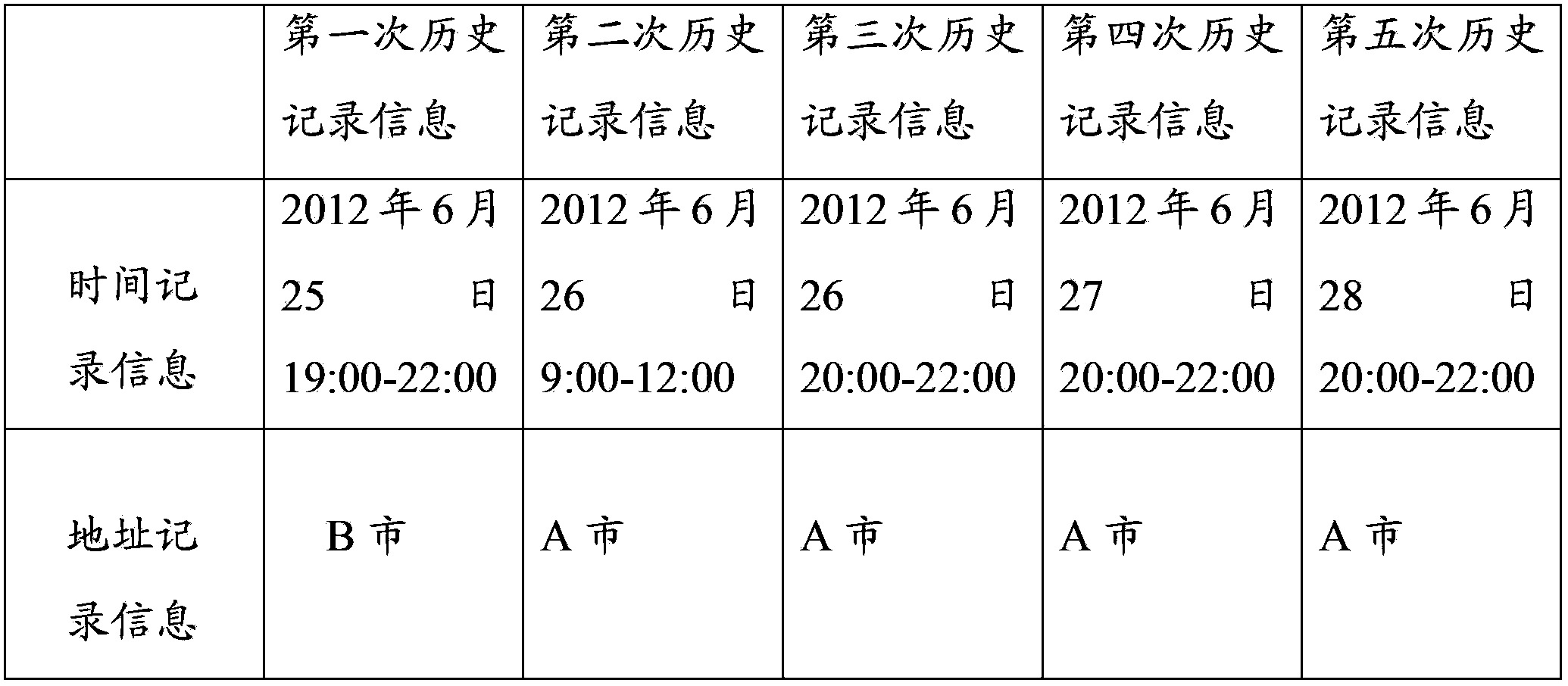
[0088] In the password management system, there are passwords and corresponding account information for obtaining the predetermined authority of multiple servers. For example, in the embodiment of this application, the password management system has the password for obtai...
Embodiment 2
[0166] In the embodiment of this application, as Figure 4 As shown, a password management system is described. At least one password including a first password is stored in the password management system. The at least one password is used to combine at least one account information corresponding to the at least one password to obtain predetermined authority of at least one server. The first password is used in conjunction with the corresponding first account information to obtain the predetermined authority of the first server, wherein at least one server includes the first server, including:
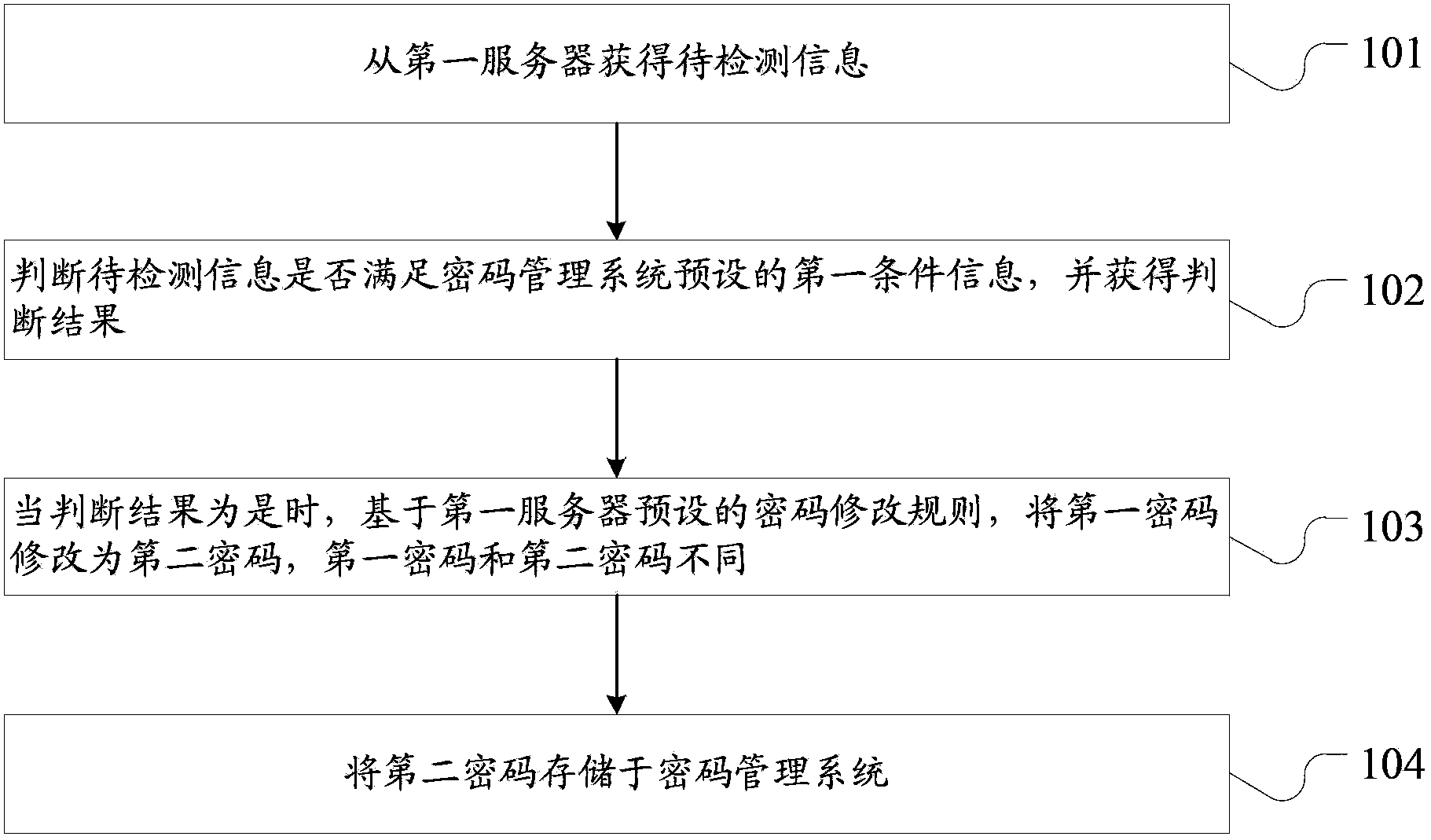
[0167] An obtaining unit 401, configured to obtain information to be detected from a first server;
[0168] A judging unit 402, configured to judge whether the information to be detected meets the first condition information preset by the password management system, and obtain a judging result;
[0169] The modifying unit 403 is configured to modify the first password to a second pass...
Embodiment 3
[0184] In the embodiment of the present application, after the password management system modifies the password in the first server, it is a process of using the modified password to obtain a predetermined authority in the first server.
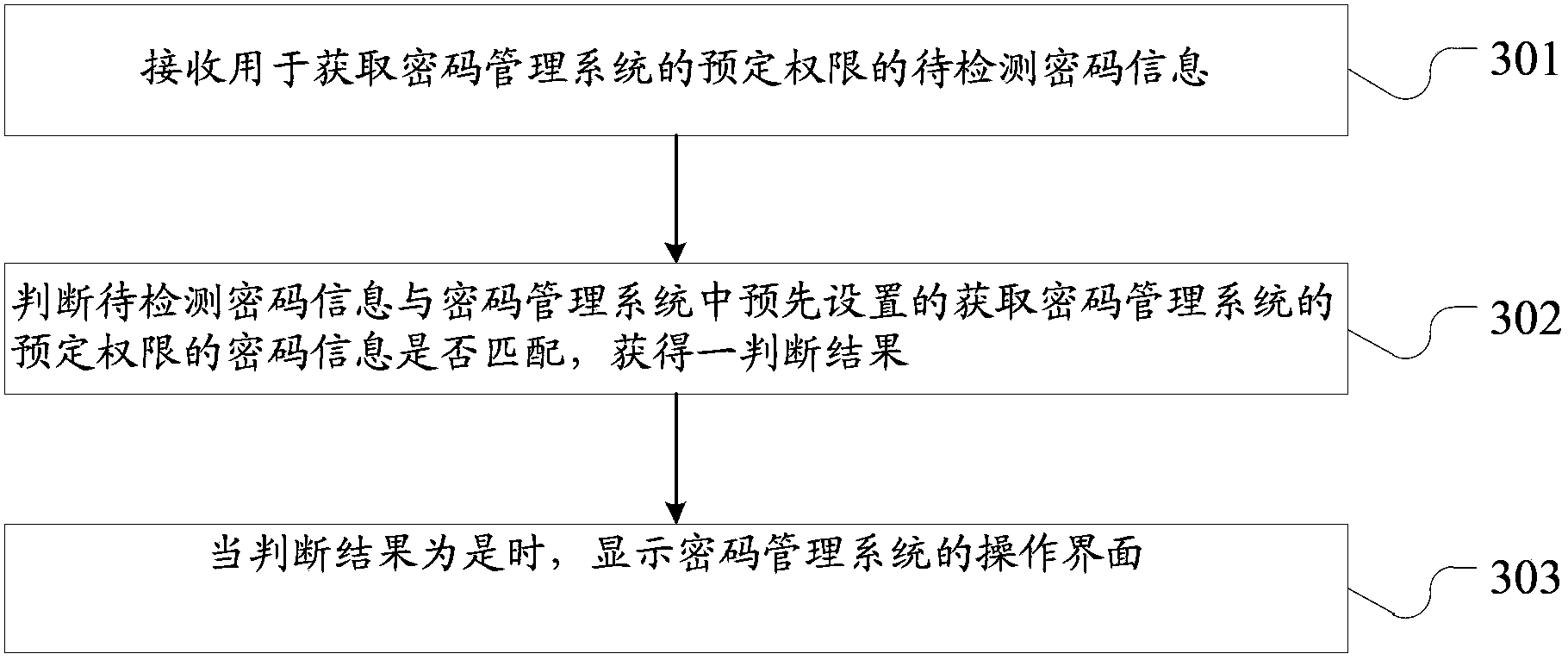
[0185] The method for obtaining the predetermined authority of the password management system has been introduced in Embodiment 1. Therefore, the embodiment of the present application does not repeat the method for obtaining the predetermined authority of the password management system. Therefore, when the password management system is in the working state, please see Figure 9 ,in, Figure 9 A data processing method is described in , and the method is applied to a password management system, including:
[0186] In step 901, it is detected on the operation interface of the password management system whether there is a link operation that triggers the acquisition of the predetermined authority of the first server.
[0187] Wherein, the opera...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com