Method and device for safely consulting session key
A session key and security technology, applied in security devices, secure communication devices, and key distribution, can solve the problems of simple algorithm, unfeasible, easy to be cracked, etc., to ensure the security of voice calls, not easy to be stolen, The effect of reducing system overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] In order to make those skilled in the technical field of the present invention understand the present invention more clearly, the implementation process of the present invention will now be described in detail in conjunction with the accompanying drawings.
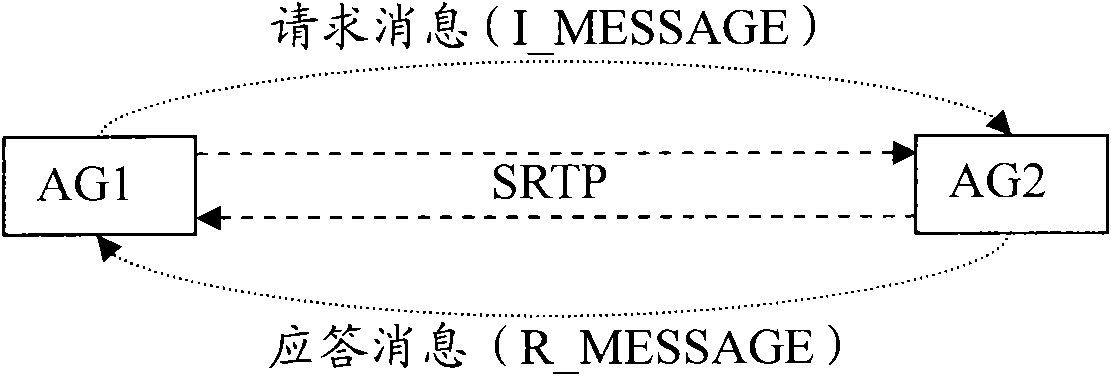
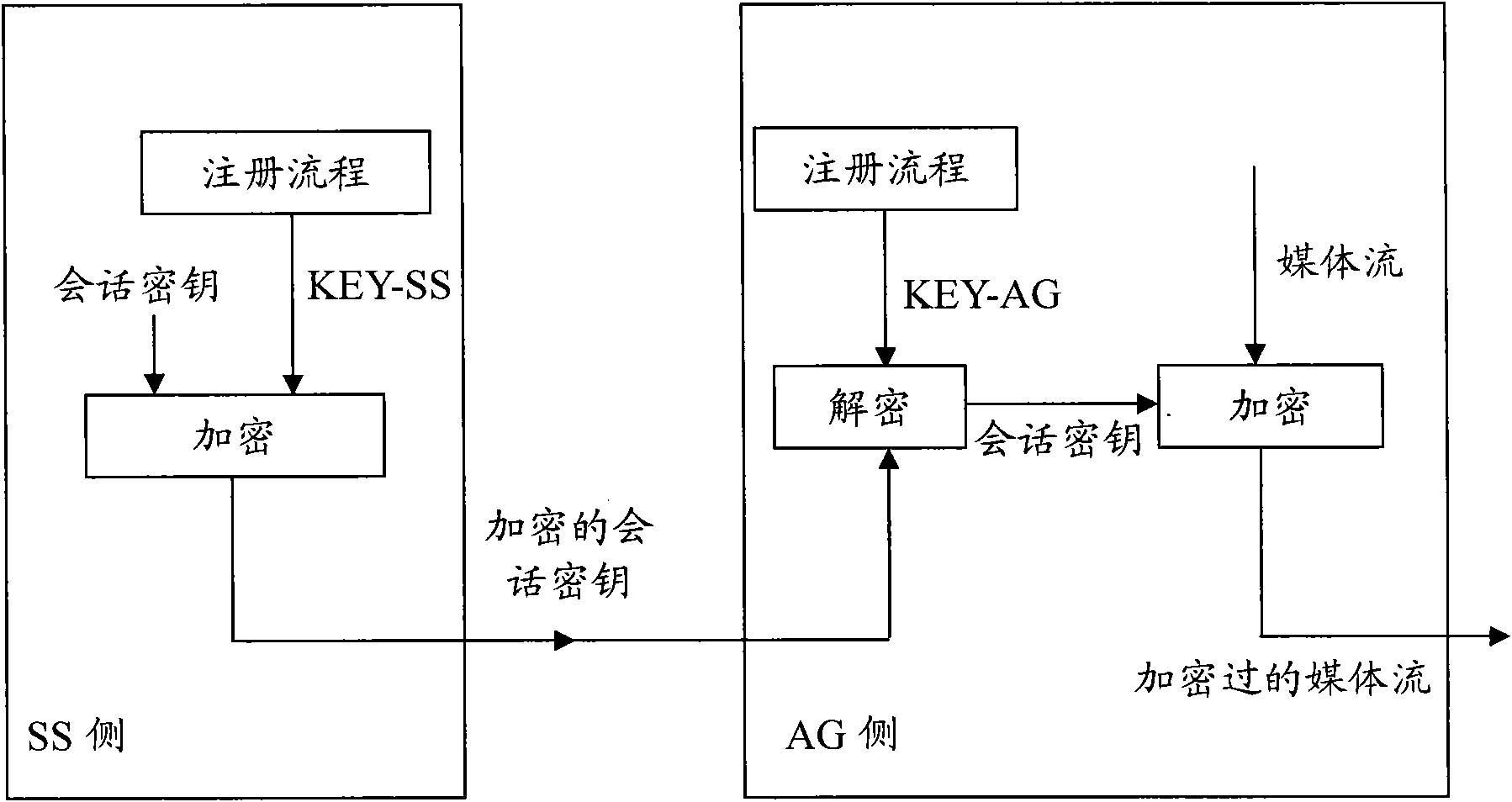
[0043] image 3 A schematic diagram of securely negotiating a session key for the present invention, such as image 3 As shown, the method for safely negotiating a session key of the present invention includes the following steps:
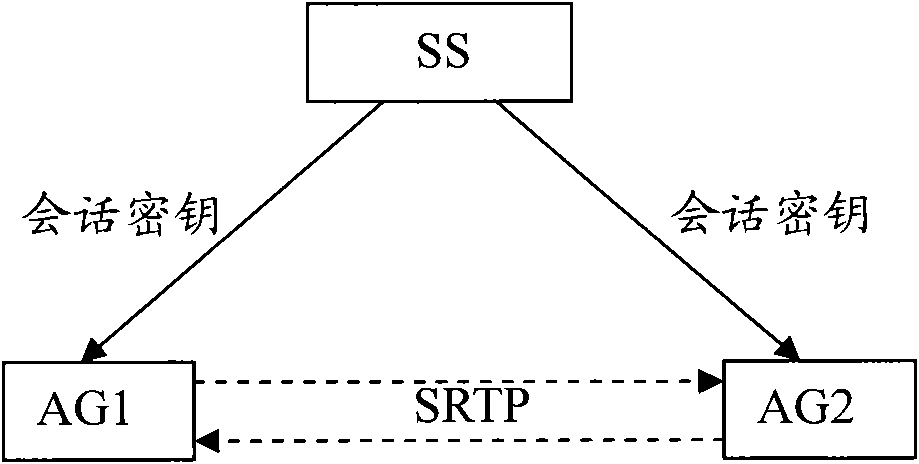
[0044] In step A, after AG successfully registers with SS, the two obtain shared keys KEY-AG and KEY-SS respectively, and store the shared keys in themselves.
[0045] Step B, before each session of the registered AG, the SS allocates an SK for the session according to the request of the AG, and encrypts the allocated SK with the shared key KEY-SS;
[0046] Among them, the SS side encrypts the SK according to the formula (1):
[0047] KEY-SALT=MD5(KEY-SS, SK) (1)
[0048] The encrypt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com