Methods and apparatuses for data encryption and decryption, method and apparatus for processing secret key request, and data encryption and decryption system
A technology for encrypting keys and decrypting keys, which is applied in the fields of key request processing, decryption, and data encryption. It can solve the problems of high risk of encryption sensitive data leakage, increase the difficulty of cracking, improve security, and solve the effects of high risk of leakage.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
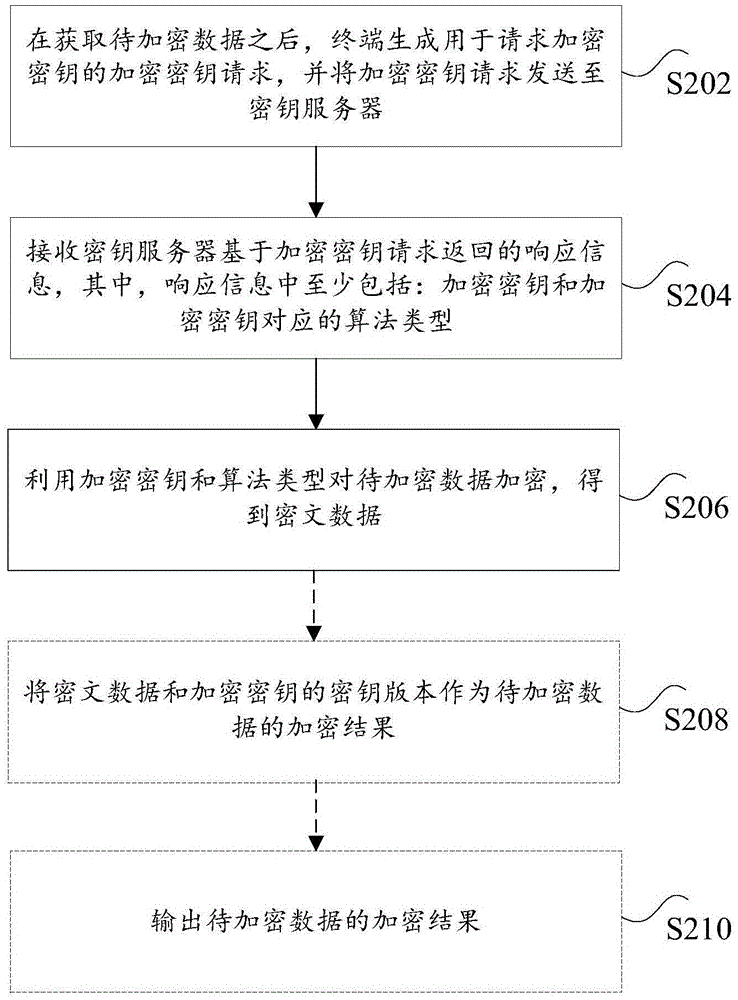
[0031] According to an embodiment of the present application, an embodiment of a data encryption method is also provided. It should be noted that the steps shown in the flow chart of the accompanying drawings can be executed in a computer system such as a set of computer-executable instructions, and , although a logical order is shown in the flowcharts, in some cases the steps shown or described may be performed in an order different from that shown or described herein.
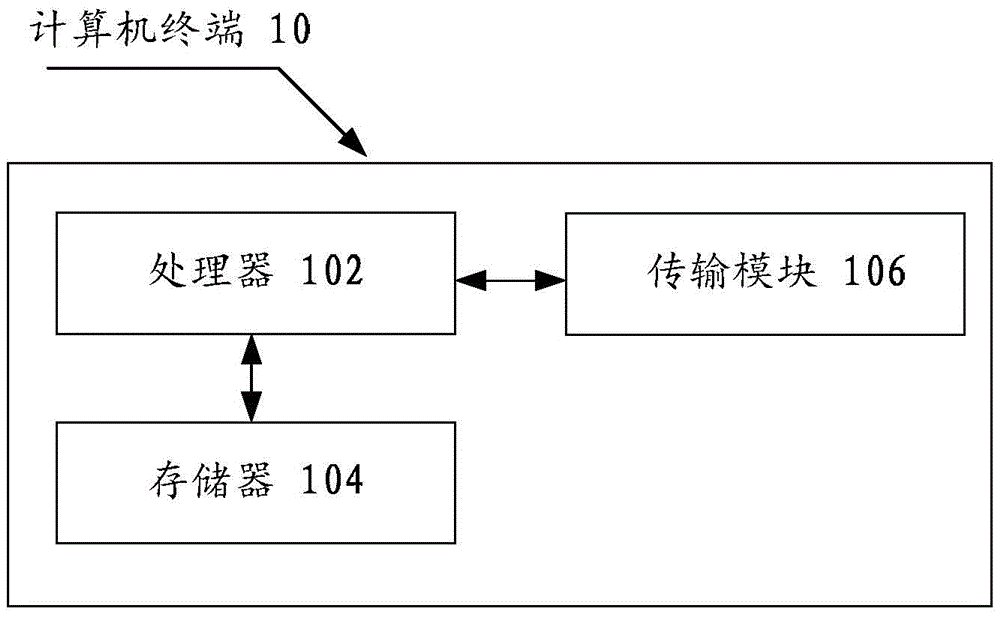
[0032]The method embodiments provided in the embodiments of the present application may be executed in mobile terminals, computer terminals or similar computing devices. Take running on a computer terminal as an example, figure 1 It is a block diagram of the hardware structure of a computer terminal for a data encryption method according to the embodiment of this application.
[0033] like figure 1 As shown, the computer terminal 10 may include one or more (only one is shown in the figure) processors 102 (t...
Embodiment 2
[0081] in the above figure 1 Under the operating environment shown, this application also provides Figure 4 The method for decrypting the data is shown. Figure 4 is a flowchart of a data decryption method according to an embodiment of the present application.
[0082] like Figure 4 The method shown includes the following steps:
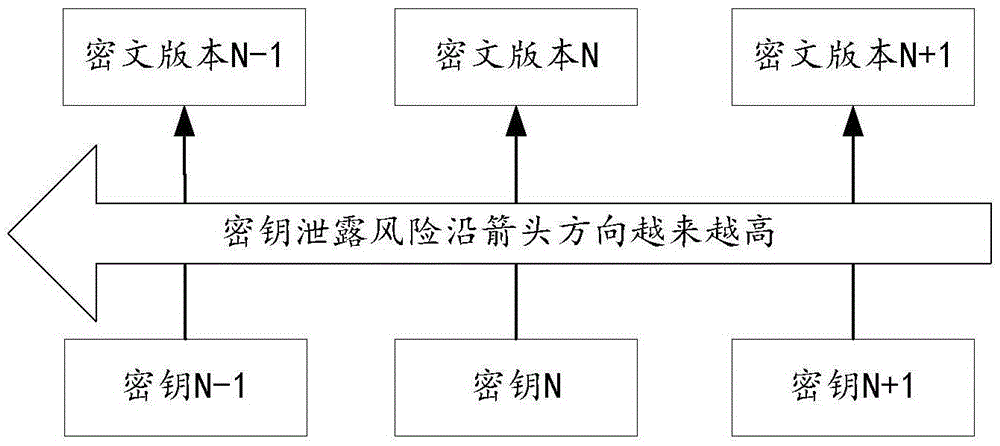
[0083] Step S402: The terminal obtains a decryption request for decrypting data to be decrypted, wherein the data to be decrypted is an encryption result including ciphertext data and a key version.
[0084] Step S404: Analyzing the data to be decrypted to obtain the ciphertext data and the key version.
[0085] Step S406: Generate a decryption key request carrying the key version, and send the decryption key request to the key server, where the decryption key request is used by the key server to find the decryption key corresponding to the key version and decrypt The algorithm type of the key.
[0086] Step S408: Receive the decryption key a...
Embodiment 3
[0103] in the above figure 1 Under the operating environment shown, this application also provides Figure 5 The processing method for the key request shown. Figure 5 is a flow chart of a key request processing method according to an embodiment of the present application.
[0104] like Figure 5 Shown, this embodiment comprises the following steps:
[0105] Step S502: receiving a key request sent by the terminal for obtaining a key, where the key request includes an encryption key request and a decryption key request.
[0106] Step S504: If the key request is an encryption key request, read the latest version of the encryption key and the algorithm type of the encryption key from the database, and return to the terminal based on the encryption key and the algorithm type of the encryption key.
[0107] Step S506: If the key request is a decryption key request, then obtain the key version from the decryption key request, read the decryption key and the algorithm type of the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com