Method for preventing tampering of identity information in real name authentication
A technology of identity information and real-name authentication, applied in the direction of user identity/authority verification, etc., can solve the problems of no further verification mechanism in the business system, security loopholes in real-name authentication work, etc., to achieve secure identity recognition and tamper-proof, guarantee security, and prevent The effect of illegal tampering
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
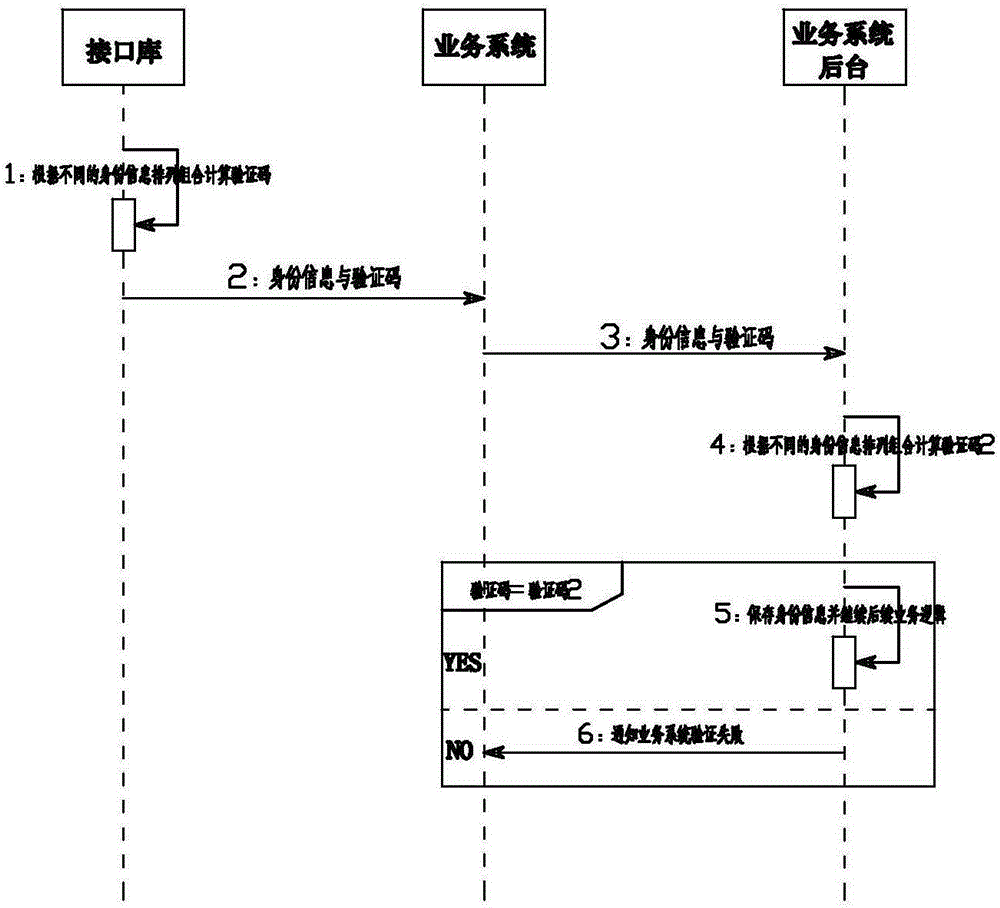
[0018] Embodiment 1: as figure 1 As shown, the method for preventing identity information tampering in real-name authentication of the present invention includes a business system, the business system is connected with a radio frequency device, and reads the encrypted identity information in the ID card through the radio frequency device, and the business system passes through the decoding device at the other end of the network. After decoding, return the decoded identity information to the business system. After the business system controls the radio frequency device through the interface library to obtain the encrypted identity information, it sends the encrypted identity information to the decoding device through the TCP / IP network. The business system includes the business system front desk located at the front desk terminal and the business system background located at the background server. The feature code is Corresponding to the unique code of the identity information,...
Embodiment 2
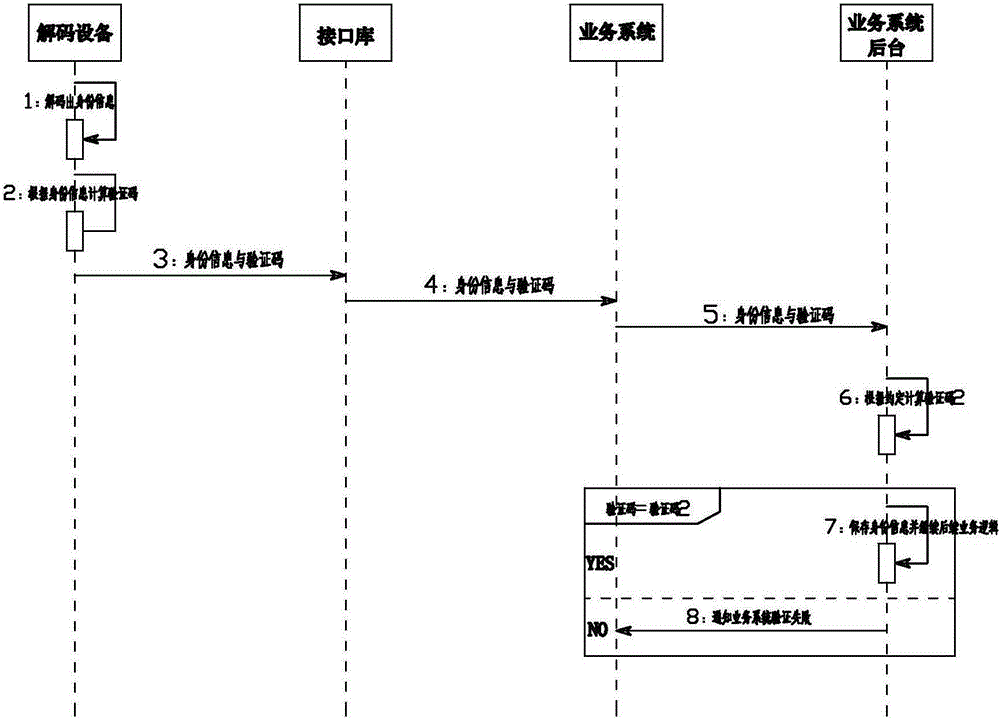
[0019] Embodiment 2: as figure 2 and image 3 As shown, the method for preventing identity information tampering in real-name authentication according to the present invention includes a business system. The business system is connected with a radio frequency device, and reads the encrypted identity information in the ID card through the radio frequency device. After decoding by the dedicated decoding device, the decoded identity information is returned to the business system. After the business system controls the radio frequency device through the interface library to obtain the encrypted identity information, it sends the encrypted identity information to the decoding device through the TCP / IP network. The business system includes the business system front desk located at the front desk terminal and the business system background located at the background server. The feature code is Corresponding to the unique code of the identity information, the decoding device decodes ...
Embodiment 3
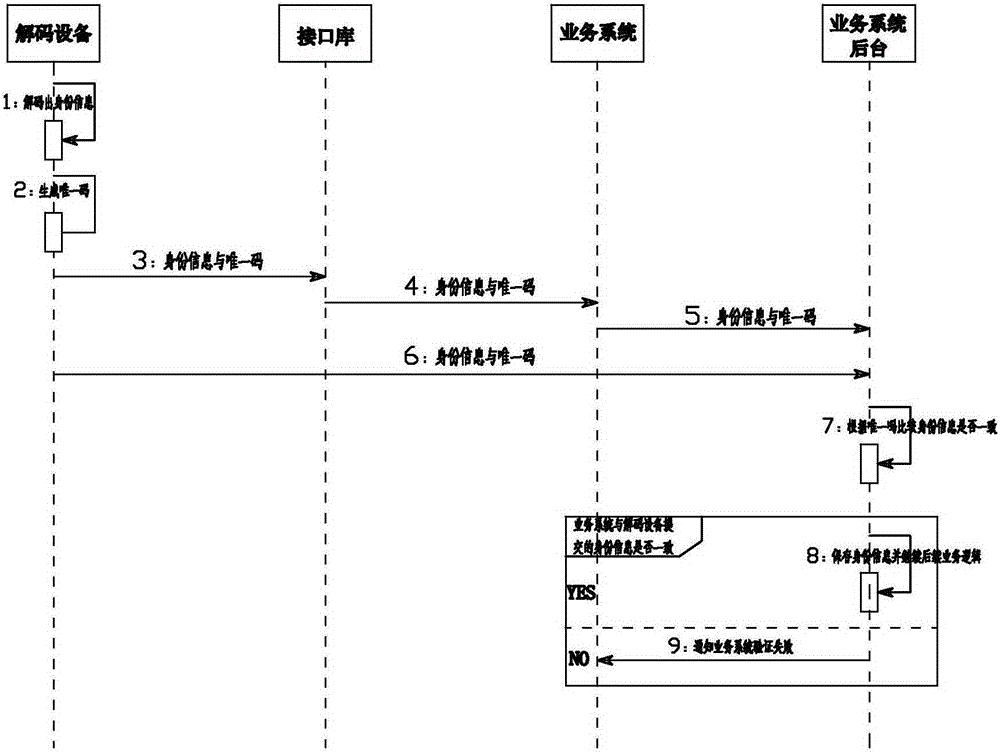
[0027] Embodiment 3: as Figure 4 As shown, the method for preventing identity information tampering in real-name authentication of the present invention includes a business system, the business system is connected with a radio frequency device, and reads the encrypted identity information in the ID card through the radio frequency device, and the business system passes through the decoding device at the other end of the network. After decoding, return the decoded identity information to the business system. After the business system controls the radio frequency device to obtain the encrypted identity information through the interface library, it sends the encrypted identity information to the decoding device through the TCP / IP network. The decoding device decodes the received identity information and uses the name, gender, and ethnicity in the identity information. , date of birth, address, citizen identity number, issuing authority, validity period, validity period, photo da...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com