PE loader-based software packing protection method
A software and protected technology, applied in the field of software packing protection based on PE Loader, can solve the problems of illegal tampering, easy software, cracking, etc., and achieve the effect of increasing security, increasing difficulty, preventing disassembly and cracking and illegal tampering.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0014] The present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
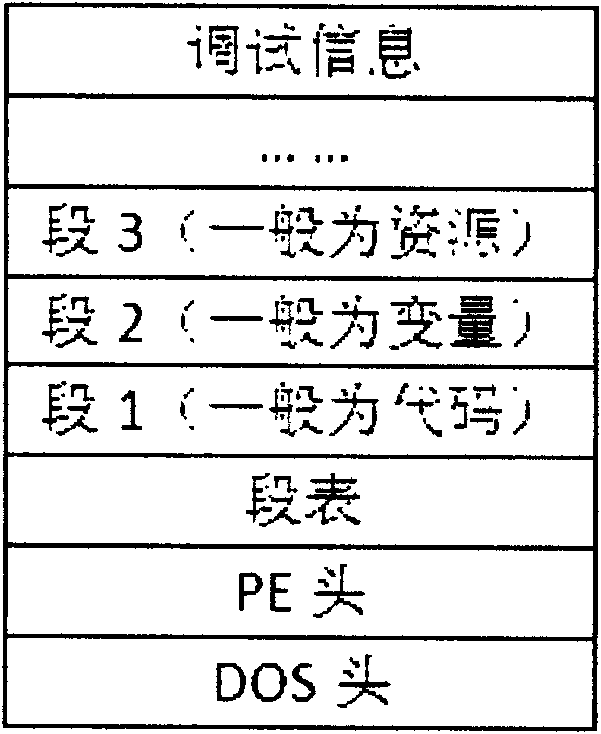
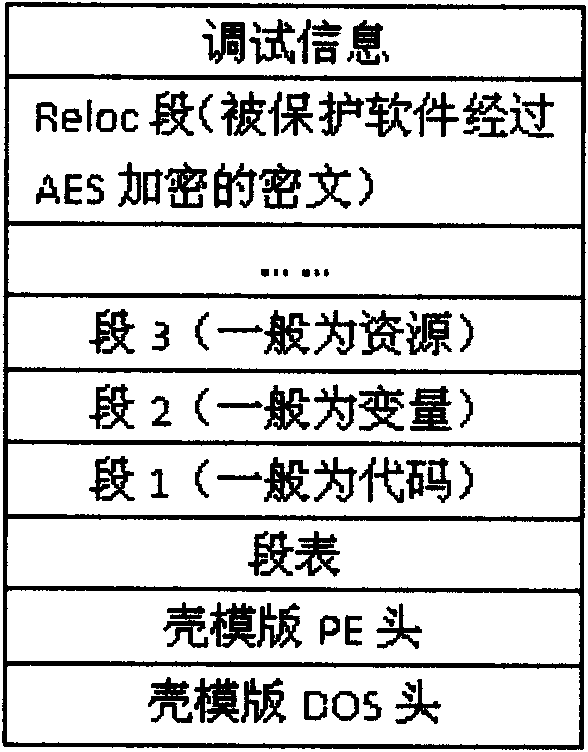
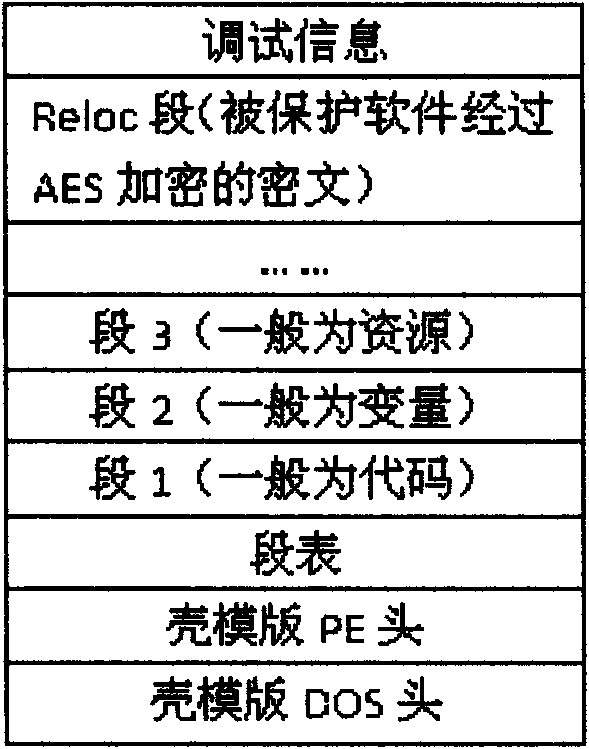
[0015] In the method of the present invention, the software to be protected by packing is first encrypted by AES, and the encrypted content is put into the Reloc segment in the shell template of the outer layer, and the encrypted key is obtained according to the code segment in the shell template The data is dynamically obtained through the SHA algorithm. If the reverse analyst debugs or modifies the code segment data of the shell template, the decryption of the program will fail and cannot be executed normally, thus effectively achieving the purpose of protecting the software.
[0016] The inventive method implements according to the following steps:
[0017] Step 1. Map the shell template to the memory, simulate the Windows PE loader to relocate the base address of the shell template, calculate the RVA (Relative Virtual Addresses) of the se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com