Data security duplicate removal method based on threshold blind signature
A technology of data security and blind signature, applied in secure communication devices and key distribution, can solve the problem of large computational overhead for signature verification, and achieve the effect of low communication overhead and low computational overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
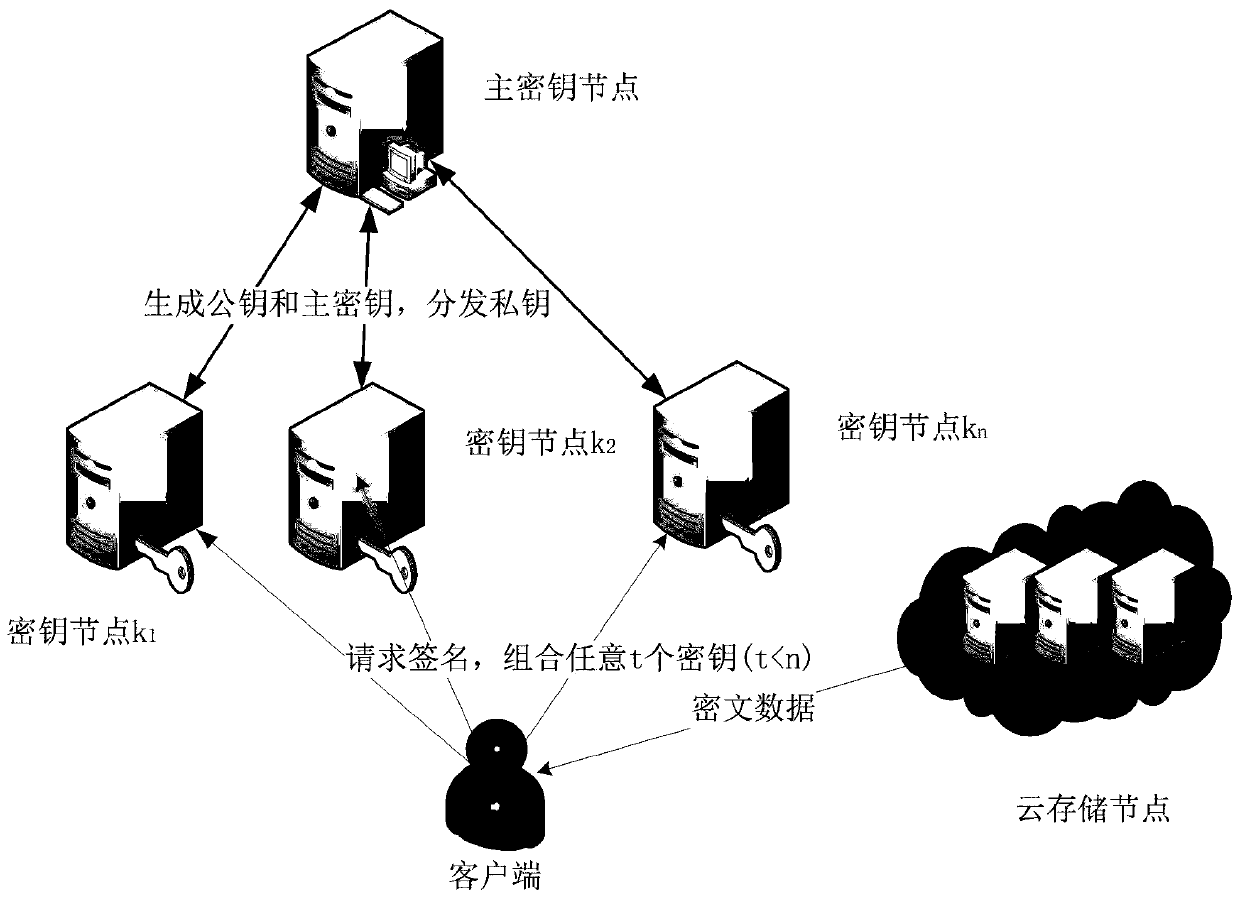
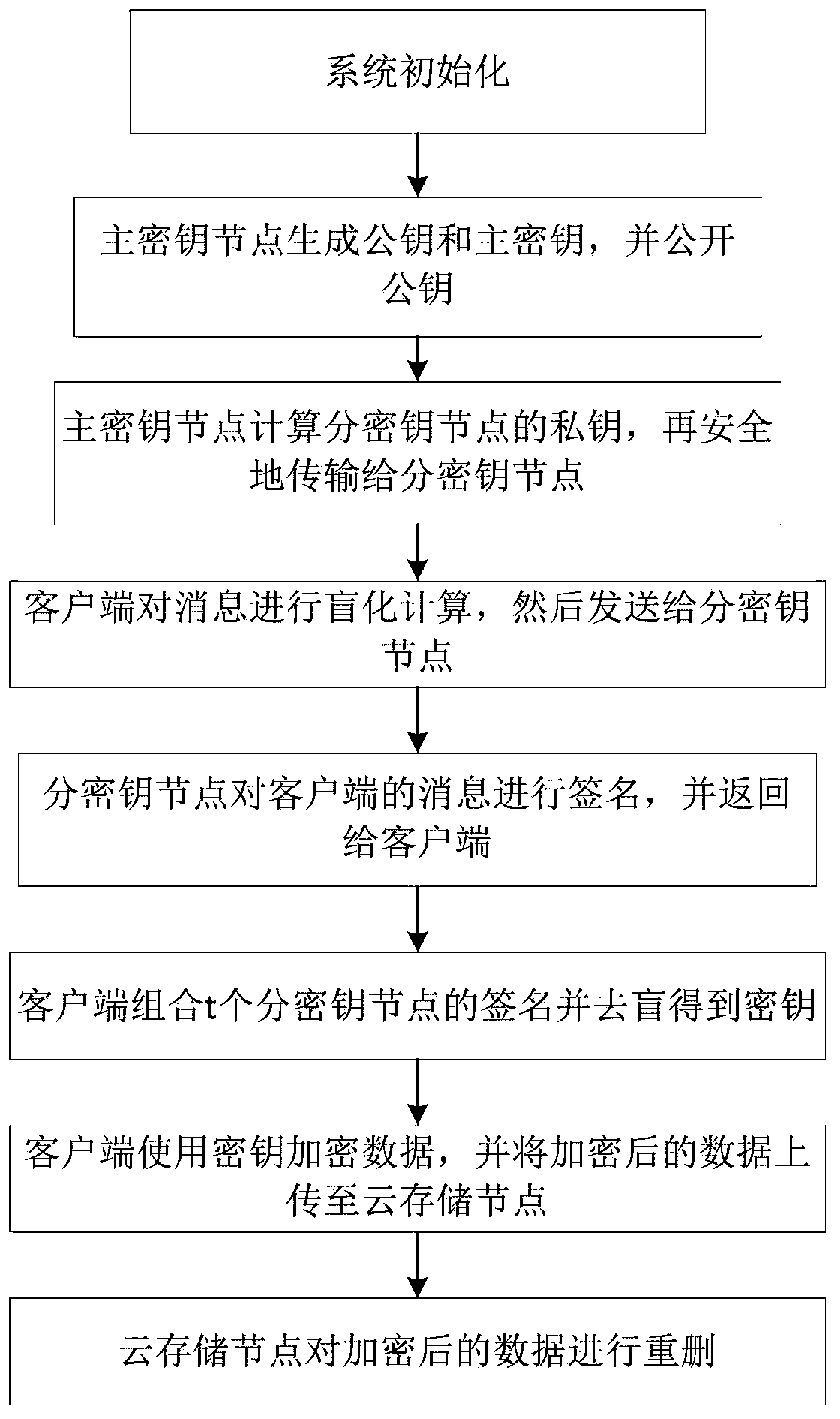
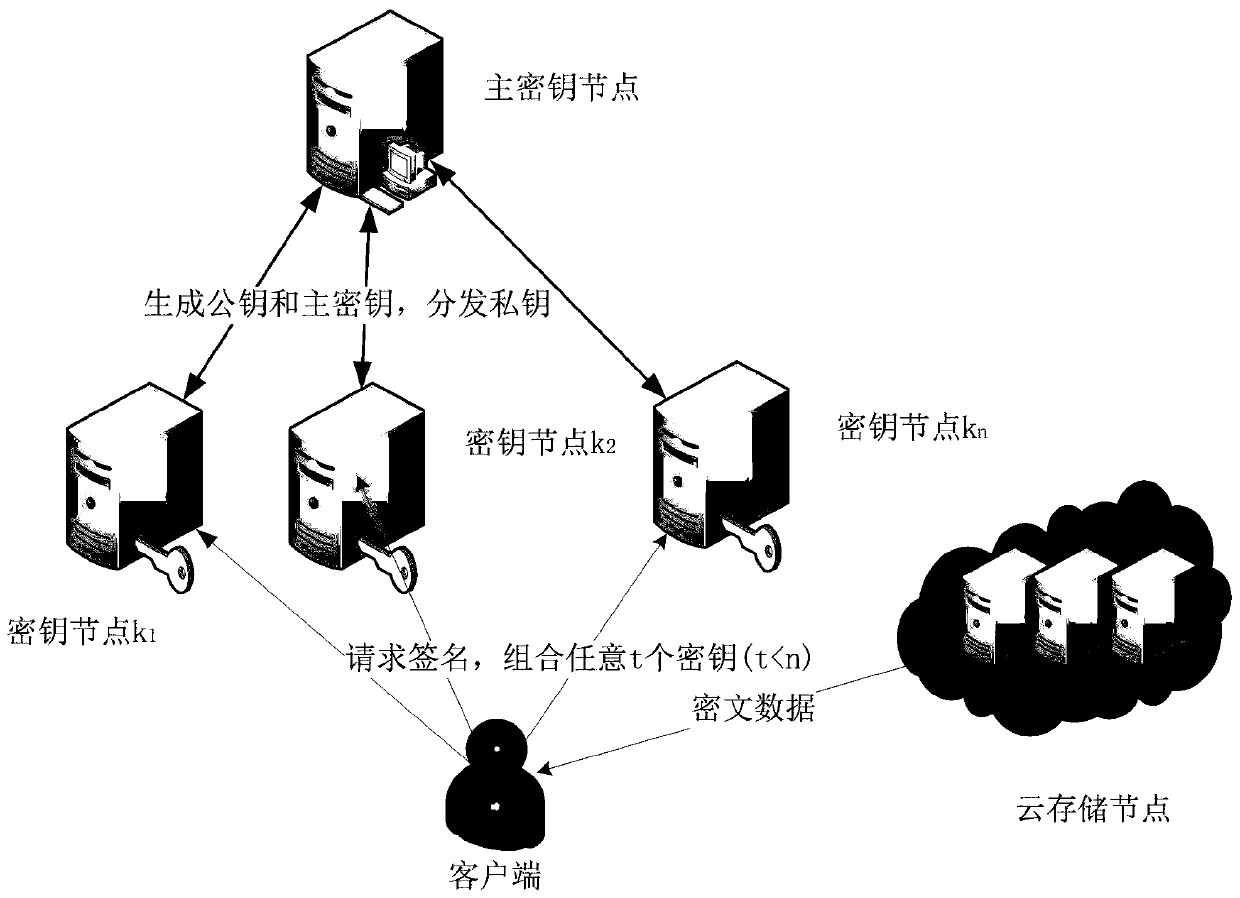
[0023] Specific implementation mode 1. Combination figure 1 and figure 2 Describe this embodiment, the data security deduplication method based on the threshold blind signature, the entities involved in the present invention: master key node, n sub-key nodes, client (user), cloud storage node.
[0024] Master key node: The master key node must be safe and reliable, generate the master key and public key, publicize the public key, generate part of the private key of each sub-key node, and share it securely with the sub-key node .
[0025] Key sub-node: There are multiple key sub-nodes, which receive part of the private key generated by the master key node, use it to sign the blinded message of the client, and return the result to the client.
[0026] Client (user): The client blinds the message, sends it to the sub-key node, then combines t (t≤n) blind signatures, obtains the encryption key after deblinding, and finally encrypts the data with the encryption key and sends it ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com