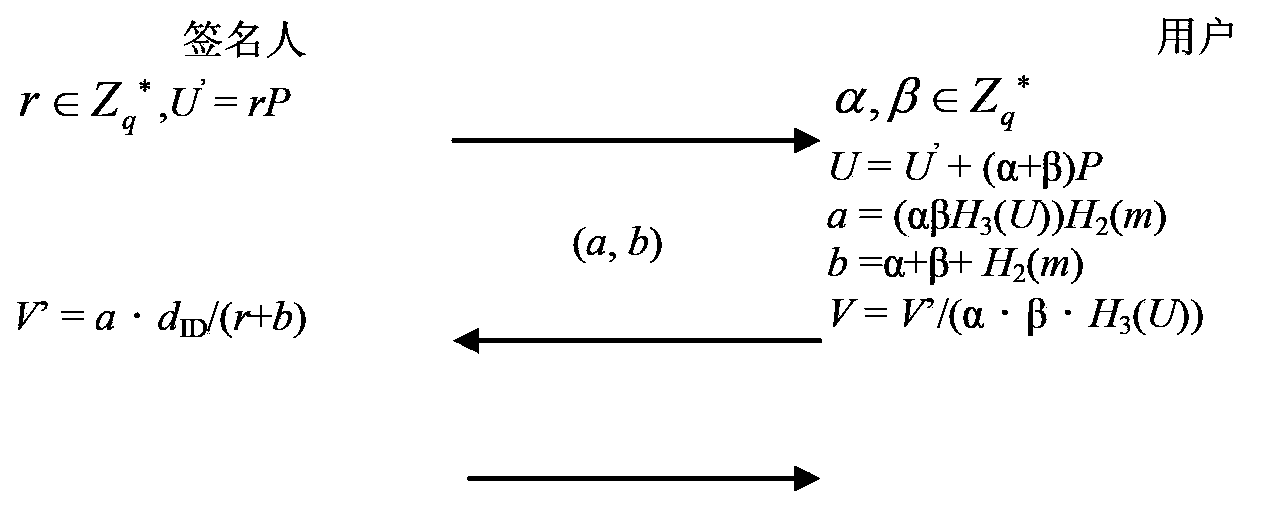Blind signature method based on identity and device thereof
A blind signature and identity technology, applied in the field of communication, can solve the problems of untraceable signed messages, the signer does not know the specific content of the message, and the signer's message is invisible, etc., to achieve the effect of increasing throughput
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
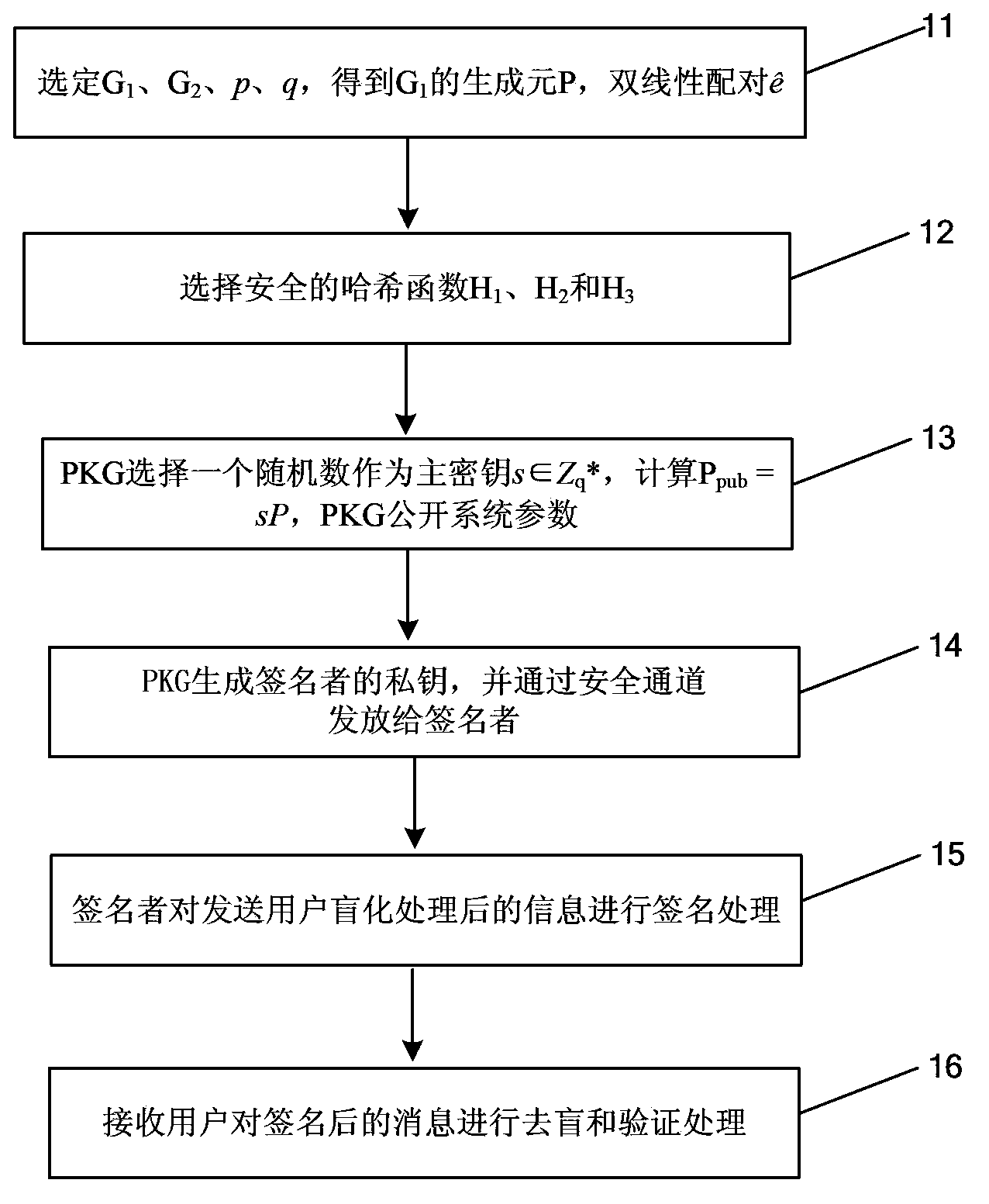
[0026] The processing flow of an identity-based blind signature method provided by this embodiment is as follows: figure 1 As shown, the following processing steps are included:
[0027] Step 11. Select G 1 , G 2 , p, q, get G 1 The generator P of the bilinear pairing
[0028] selected G 1 , G 2 are two groups of order q, p and q are two large prime numbers (where p is at least 512 bits, and q is at least 160 bits), and q is a prime factor of (p+1), and the bits of q The number is represented by n. G 1 is F p A subgroup of the additive group of elliptic curves E on the above F p Represents a domain composed of integers from 0 to (p-1), the above elliptic curve E can be shaped like: y 2 =f(x), G 2 is the domain A multiplicative group on , where by F p Obtained by the second expansion, the shape is F p [x] / f, F p [x] is F p The ring of polynomials on , f is a quadratic irreducible reduction polynomial. P is G 1 The generator of , namely q*P=O, "O" is the p...
Embodiment 2
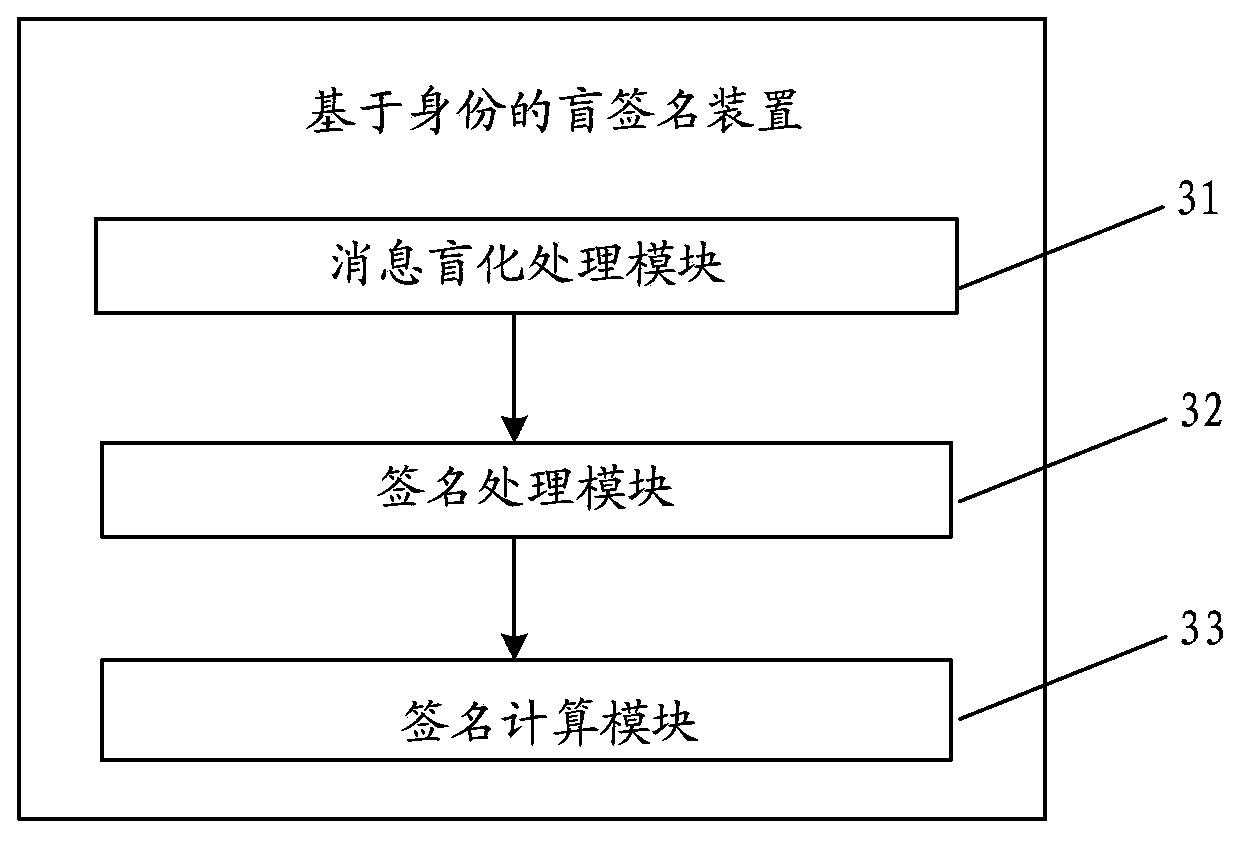
[0085] This embodiment provides an identity-based blind signature device, and its specific structure is as follows image 3 As shown, the following modules are included:
[0086] The message blinding processing module 31 is used to select the random number r∈Z through the signer q * , calculate U’=rP, the Z q * Represents an integer within the range of 1 to (q-1), the q is a set large prime number, and the P is G 1 The generator of , said G1 is a subgroup of order q of the elliptic curve E additive group on Fp, said Fp is a field composed of integers from 0 to (p-1), and said p is set A large prime number, and said q is a prime factor of (p+1);
[0087] Randomly select the blinding factor α,β∈Z by sending the user q * , calculate U=U'+(α+β)P, a=(α·β·H3(U))H2(m), b=α+β+H2(m), the H2 and H3 are a single To the Hash function, H2: {0,1} * → Z q * , H3:G 1 → Z q * , the m is the plaintext information to be signed encrypted, m∈Zq * , the sending user sends the message...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com