Unentangled quantum blind signature method and system based on quantum walking
A quantum walk and blind signature technology, applied in transmission systems, digital transmission systems, and key distribution, can solve problems such as waste of resources, information leakage, and difficulty in preparation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
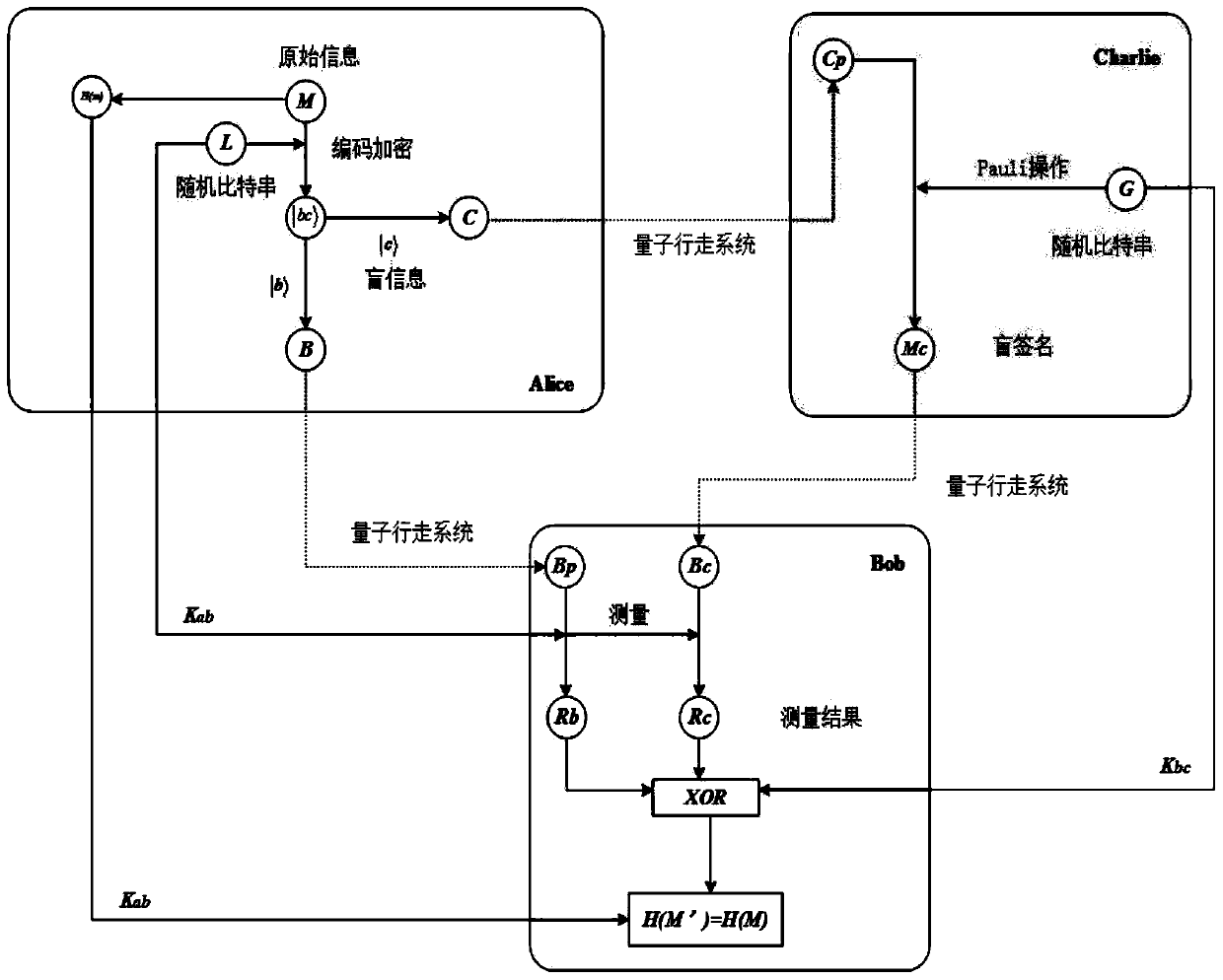
[0117] like figure 1 As shown, the quantum walk-based entanglement-free quantum blind signature method provided by the embodiment of the present invention includes three participants, the sender Alice, the signer Charlie, and the verifier Bob. The protocol involves four phases: initialization phase, blinding phase, signing phase and verification phase. Before the protocol starts, Alice and Bob share the key K in advance AB , Alice and Charlie share the key K in advance AC , Bob and Charlie share the secret key K in advance BC . These keys are distributed by the QKD protocol. Specifically include:
[0118] The first step, the initialization phase:
[0119]In the initialization phase, Alice, Charlie and Bob prepare some particles for the quantum walk system. Alice prepares a sequence of particles Ap for teleportation in the quantum walk system, where Ap=|0 1 0 2 0 3 ...0 n >. Charlie prepares a series of particle sequence Cp whose initial state is |0> state, which is...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com