Implementing method of network security system capable of self-updating letter of representation
A proxy certificate and security system technology, applied in the field of grid computing software security, can solve problems such as inability to submit jobs, inability to transmit data, etc., achieve centralized and efficient management, and avoid updates
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
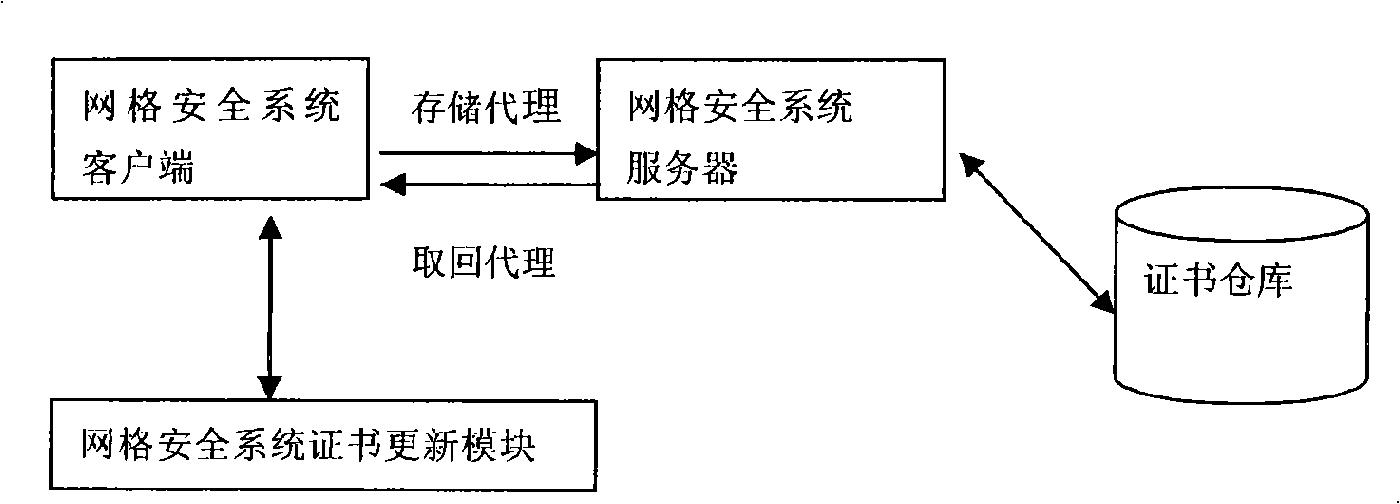
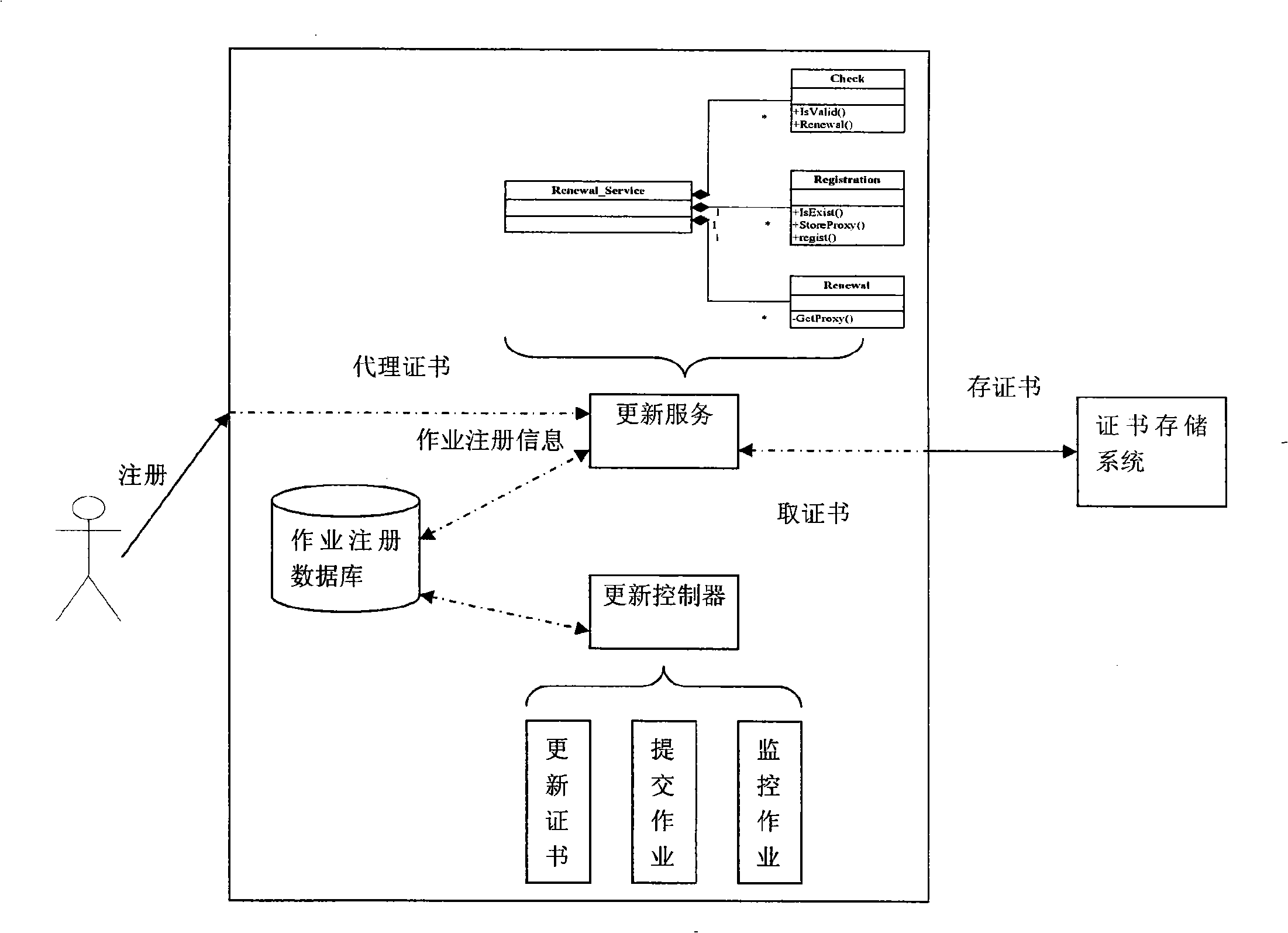
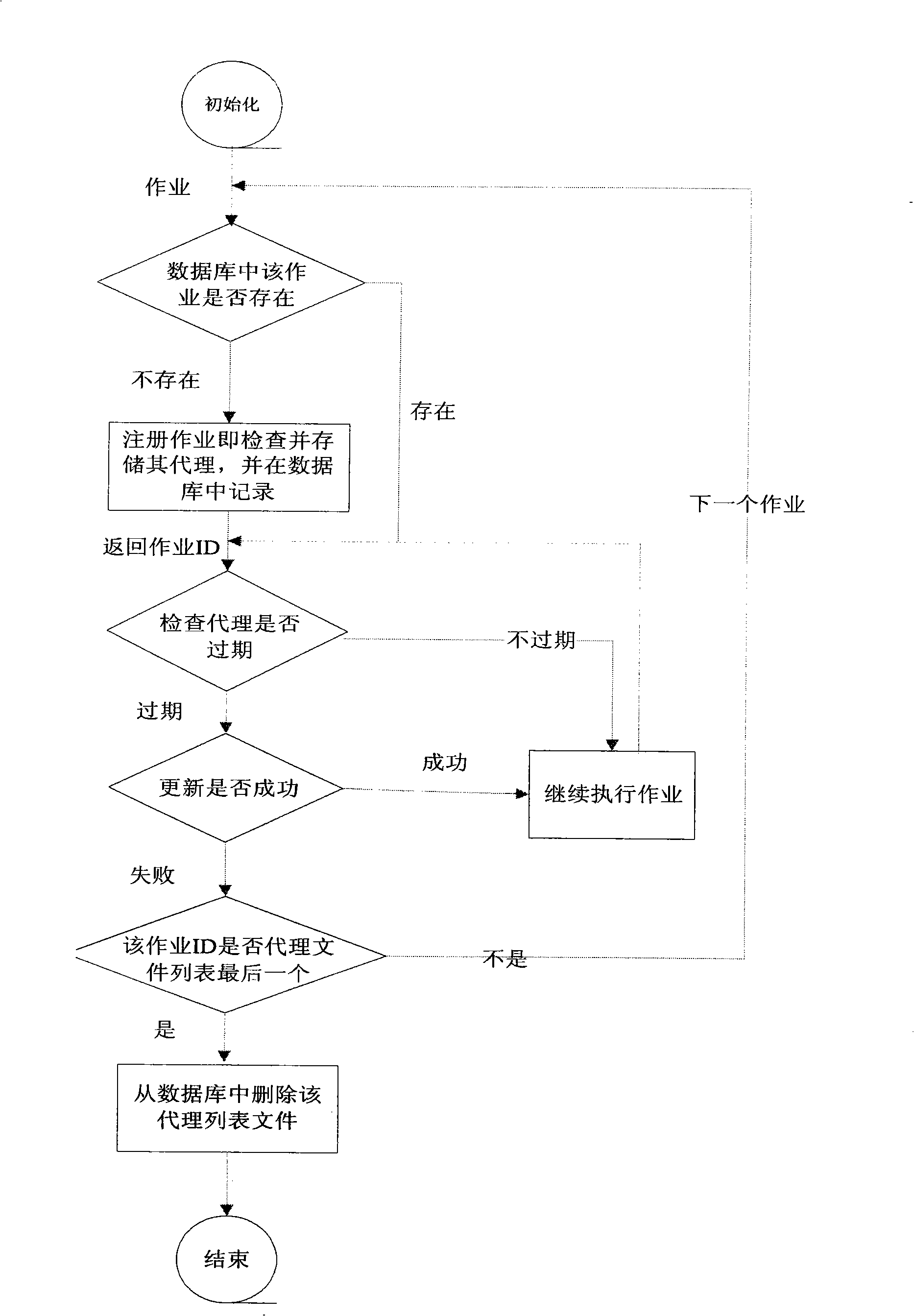
[0031]The specific implementation is divided into two parts, one is the realization of the certificate warehouse, grid security system server and grid security system client, and the other is the realization of the grid security system certificate update module.
[0032] 1. Implementation of the certificate warehouse part
[0033] 1. First, configure the Linux environment, including the installation of Globus Toolkit4 and Eclipse. And assume that the installation directory of Globus Toolkit4 is $GLOBUS_LOCATION
[0034] 2. The host running the grid security system must install a host certificate in the / etc / grid-security directory
[0035] 3. Modify the template of myproxy-server.config provided by $GLOBUS_LOCATION / share / myproxy / myproxy-server.config and copy it to / etc / myproxy-server.config. Activate them by removing the # in front of the features in the myproxy-server.config configuration file.
[0036] 4. Copy $GLOBUS_LOCATION / share / myproxy / etc.init.myproxy to / etc / rc.d / ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com