Credential protection handling method facing service
A service-oriented, protection-processing technology, applied in the direction of electrical components, transmission systems, etc., can solve problems such as unfavorable system integration, adoption of new technologies, difficulties in trust certificate management, etc., and achieve the effect of enhancing flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
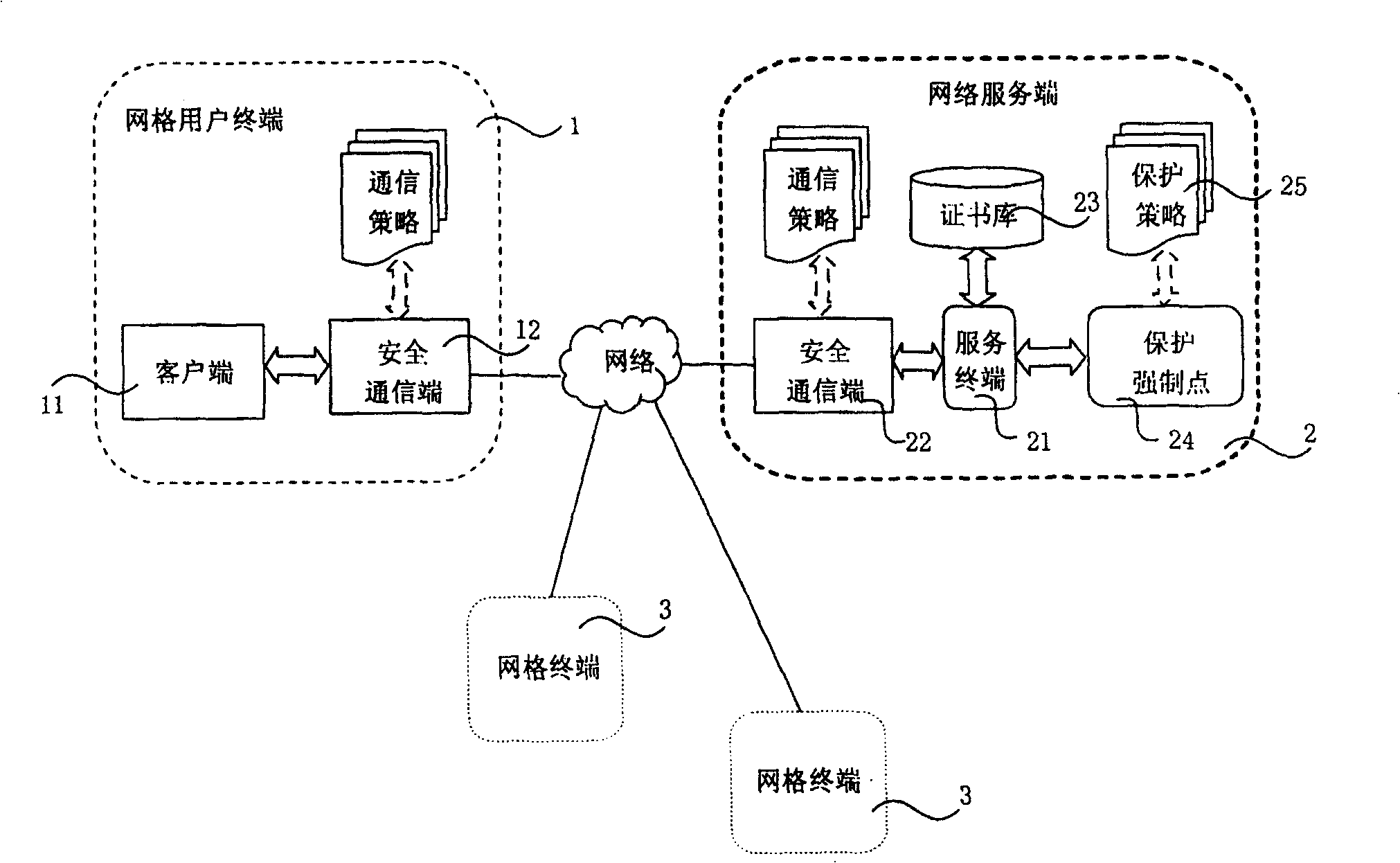
[0049] see figure 1 , is a schematic diagram of the service-oriented credential protection processing system of the present invention, which consists of a grid user terminal 1, a network server 2, and a plurality of grid terminals 3 connected through the wide area Internet.
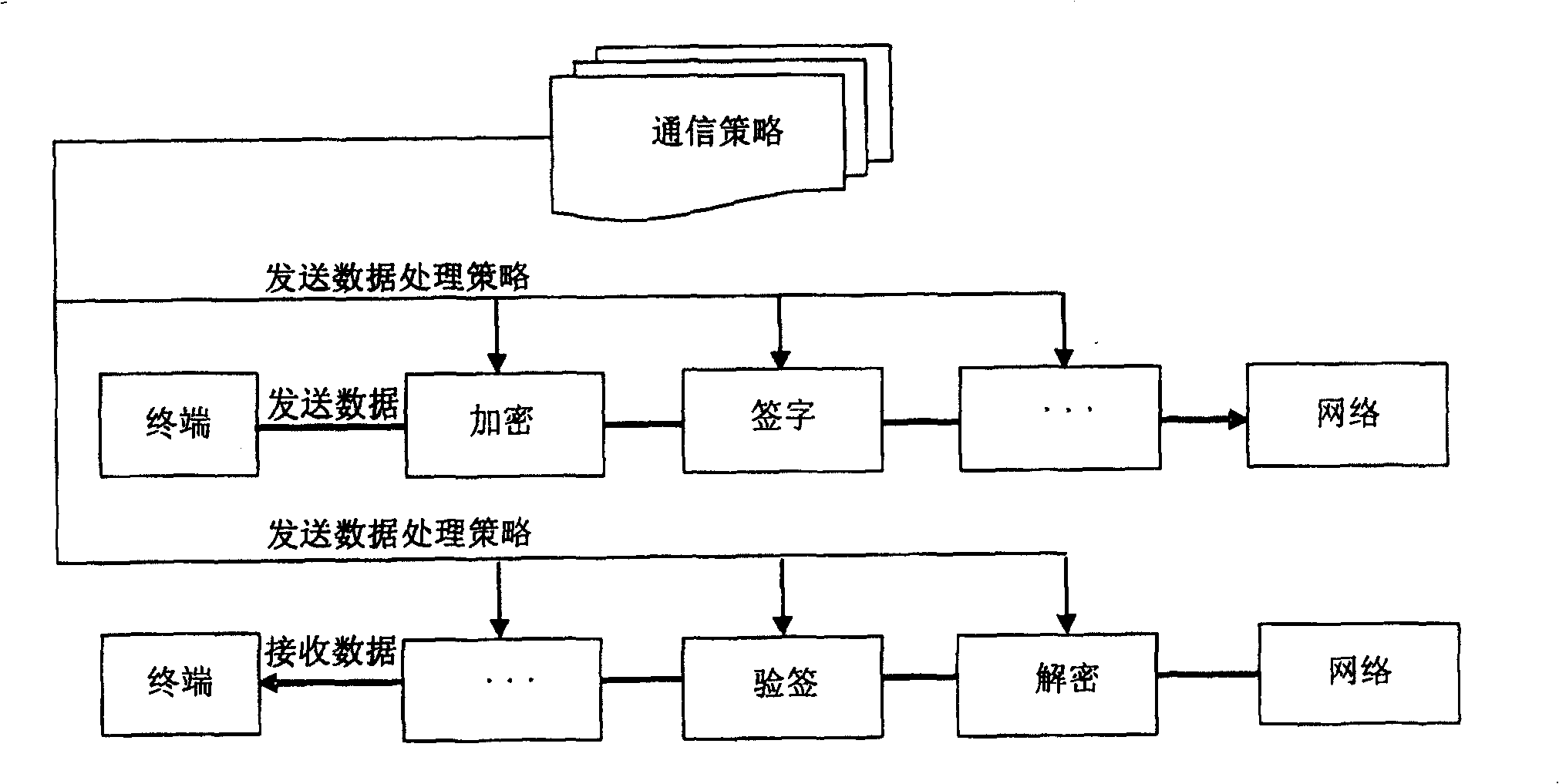
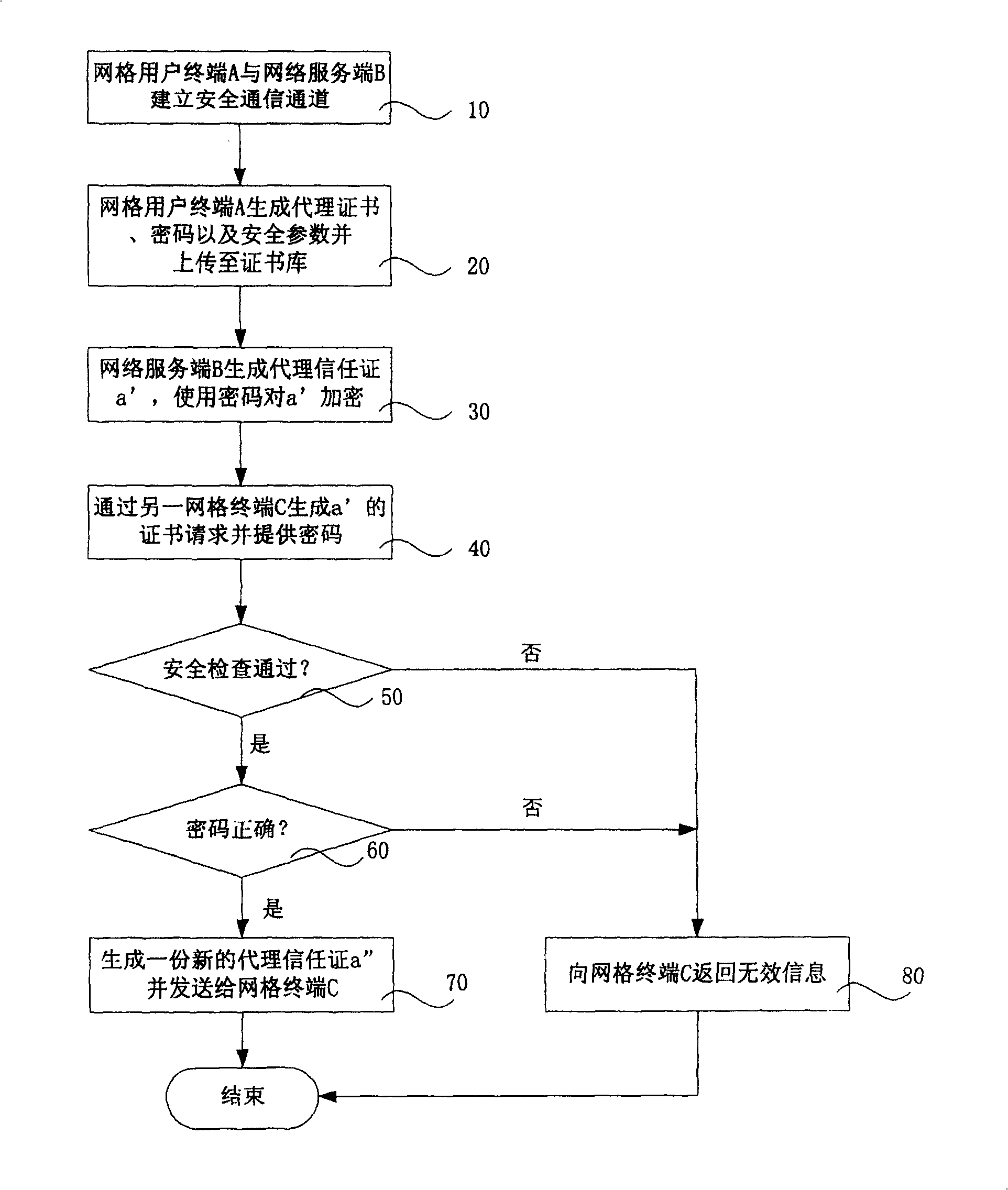
[0050] The grid user terminal 1 is the same as the grid terminal 3, the only difference is that figure 1 The grid user terminal in is the grid terminal with the trust certificate in this embodiment, so it is specially named grid user terminal. Taking the grid user terminal 1 as an example, it is composed of a client terminal 11 and a secure communication terminal 12 . The client 11 is a common business processor, such as a desktop computer or a mobile PC or a portable computer, which mainly includes the following processing functions: uploading the proxy certificate (Init), retrieving the proxy certificate (Logon), uploading the trust certificate (Store), retrieving Trust certificate (Retrieve), change ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com