A method for service-oriented architecture authorization
A service request, first-of-its-kind technology, applied in the field of communication, can solve the problem that the service provider's network function cannot verify the legitimacy of the service request.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
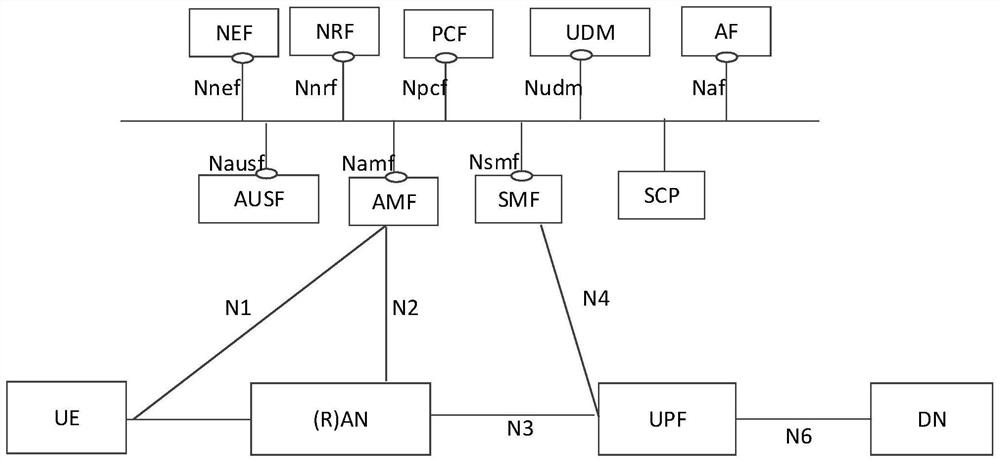
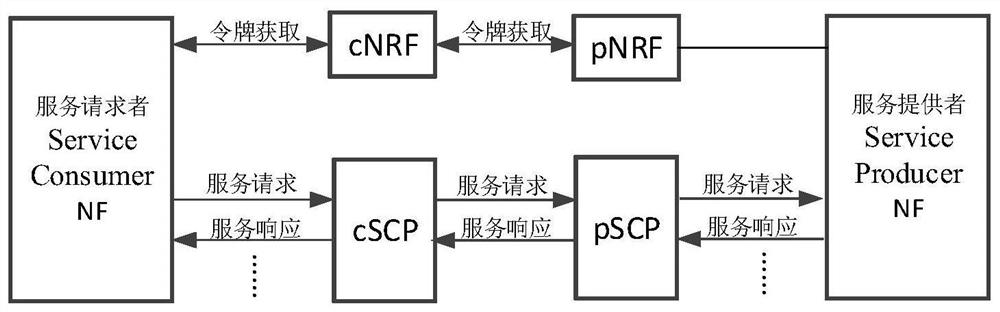
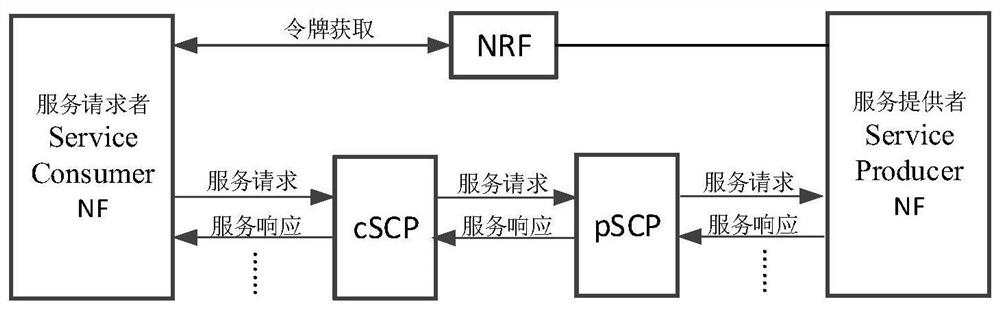
[0103]The embodiment of the application provides an authorization method and device of a service-oriented architecture, which is used to verify the legitimacy of the service request by the network function of the service provider after introducing SCP in the authorization process. Among them, the method and device are based on the same inventive concept. Since the principle of solving problems of the method and device are similar, the implementation of the device and method can refer to each other, and the repetition will not be repeated.
[0104] Some terms involved in the embodiments of the application are explained below for ease of understanding.
[0105] 1) Certificate: refers to a digital certificate, a file containing public key owner information and public key digitally signed by certificate authority (CA), which is used for identity authentication of both communication parties. The certificate includes the certificate version number (version), serial number (serialnumber)...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com