Implementation scheme of two-factor login manner capable of opening and closing freely
A login method and two-factor technology, applied in the field of information security, can solve problems such as inconvenient, easy to crack, and insecure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
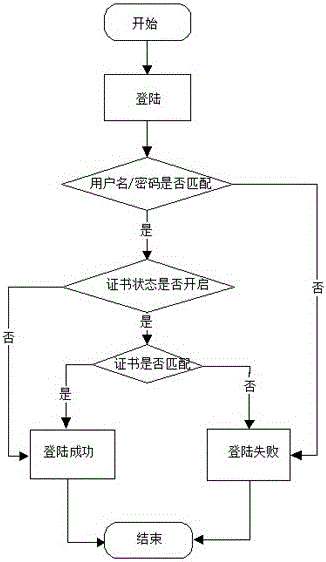
[0025] An implementation scheme of a two-factor login method that can be freely opened and closed. The two-factor login is a user name / password and a personal certificate login, and the two-factor login method can be freely opened and closed. The personal certificate uses JavaJDK. The belt tool keytool is implemented, and the process is as follows:
[0026] First, generate a trusted certificate store through the command;
[0027] After that, generate a P12 personal certificate, and export the trusted certificate cert from the P12 personal certificate;
[0028] Finally, import the trusted certificates into the certificate store.
Embodiment 2
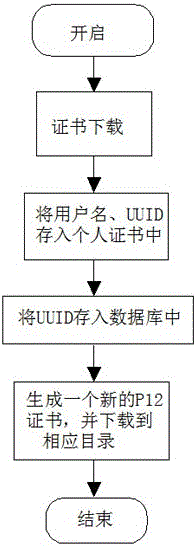
[0030] Such as figure 2 As shown, on the basis of Example 1, when generating a certificate, the solution described in this embodiment adds a unique identifier UUID to a certain field in the certificate structure, and adds a user name to another field. This field is the key to authenticating this certificate, and then, store the UUID of the certificate in the database, and store the open / closed state of a certificate.
Embodiment 3
[0032] On the basis of Embodiment 2, when managing website users in this embodiment, the administrator can modify the user's certificate status and download a new certificate through the user's information:
[0033] When the user status is turned on, then this user can only log in through two factors (username / password and personal certificate);
[0034] If the user status is closed, the user can log in with only the username and password;
[0035] If the administrator downloads a new certificate for this user, the new certificate needs to be delivered to the user by email or other means. The user can log in normally only by importing the new user certificate in the browser.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com