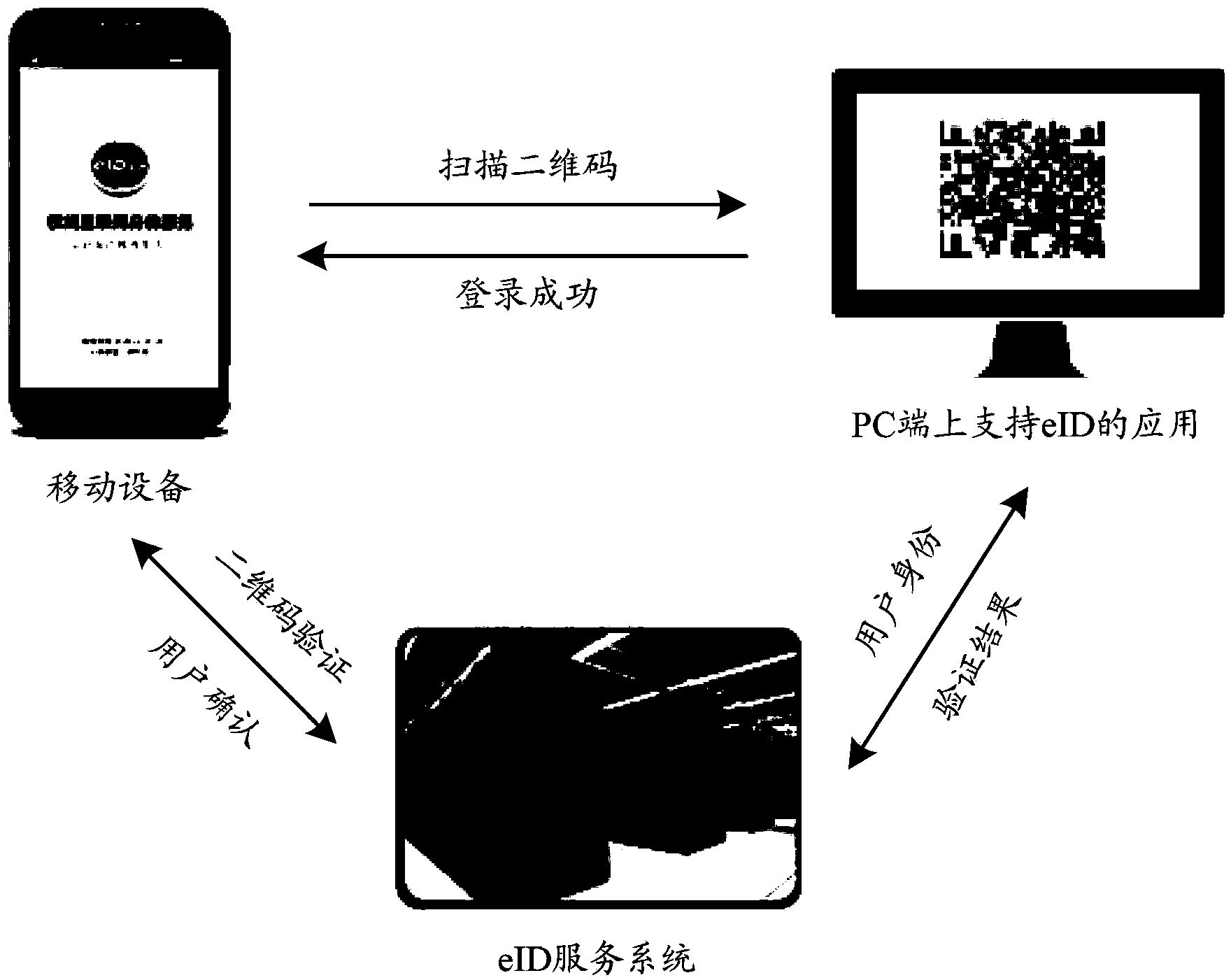
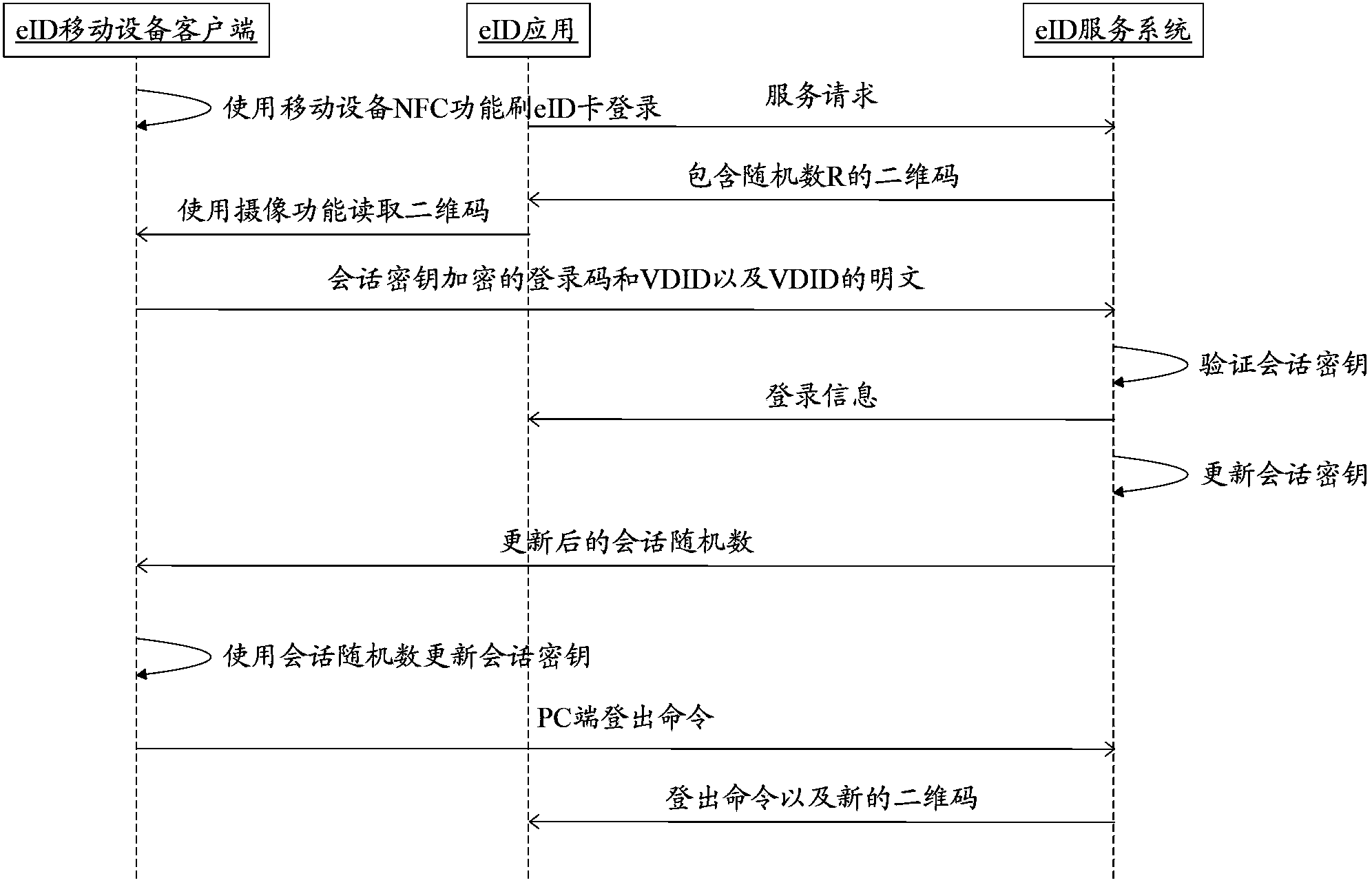
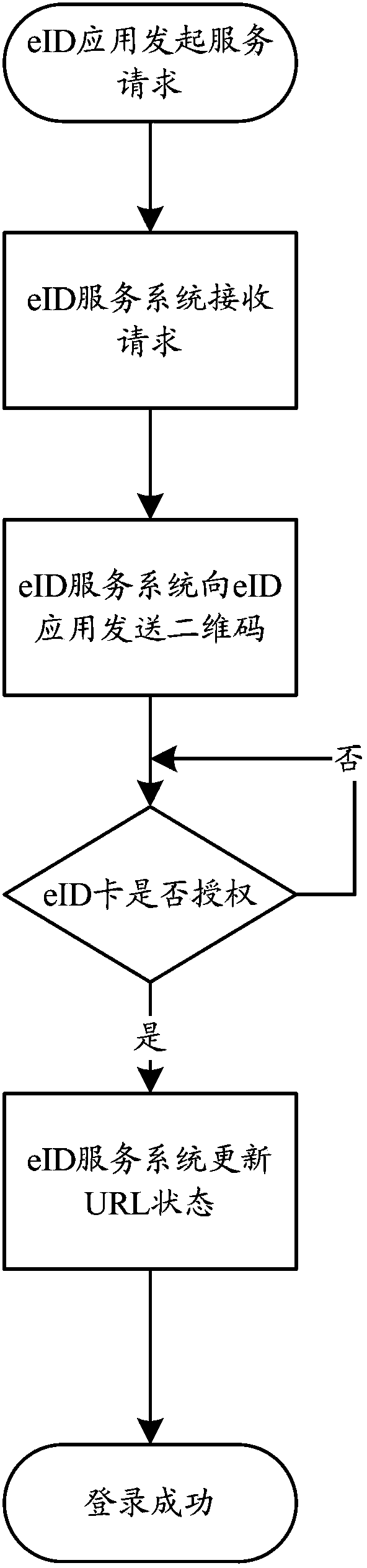
Two-dimensional code based method for realizing extended authentication control of smart card on mobile equipment
A mobile device and extended authentication technology, which is applied in the field of smart card holder identity verification and information security, can solve the problems that mobile devices and PC terminals cannot interact, semiconductors and USB slots wear out, and limit the scope of Internet applications, etc., to achieve Stable and reliable working performance, convenient use, and the effect of reducing communication overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] In order to understand the technical content of the present invention more clearly, the following examples are given in detail.
[0046] Firstly, the definitions of some symbols in the invention are given below:
[0047] ●API: Application Programming Interface (Application Programming Interface), the call interface left by the operating system to the application program, and the application program makes the operating system execute the command or action of the application program by calling it;
[0048] ●Login Type Qualifier: identifies the type of client accessing the server, and distinguishes eID mobile device clients and PC browsers;
[0049] ●SID: a globally unique number generated by the eID service system;
[0050] ●VDID: virtual device number, the number used to identify the virtual device;
[0051] ●URL: Uniform Resource Locator (Uniform Resource Locator), that is, the address of a web page, is the address of a standard resource on the Internet.
[0052] see...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com