DNS hijack defending method, device and system based on firewall system
A firewall and domain name server technology, applied in transmission systems, electrical components, etc., can solve problems such as hazards, DNS hijacking defense methods are too passive, and low defense capabilities, to achieve the effect of avoiding hazards and reasonable and effective detection and interception
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
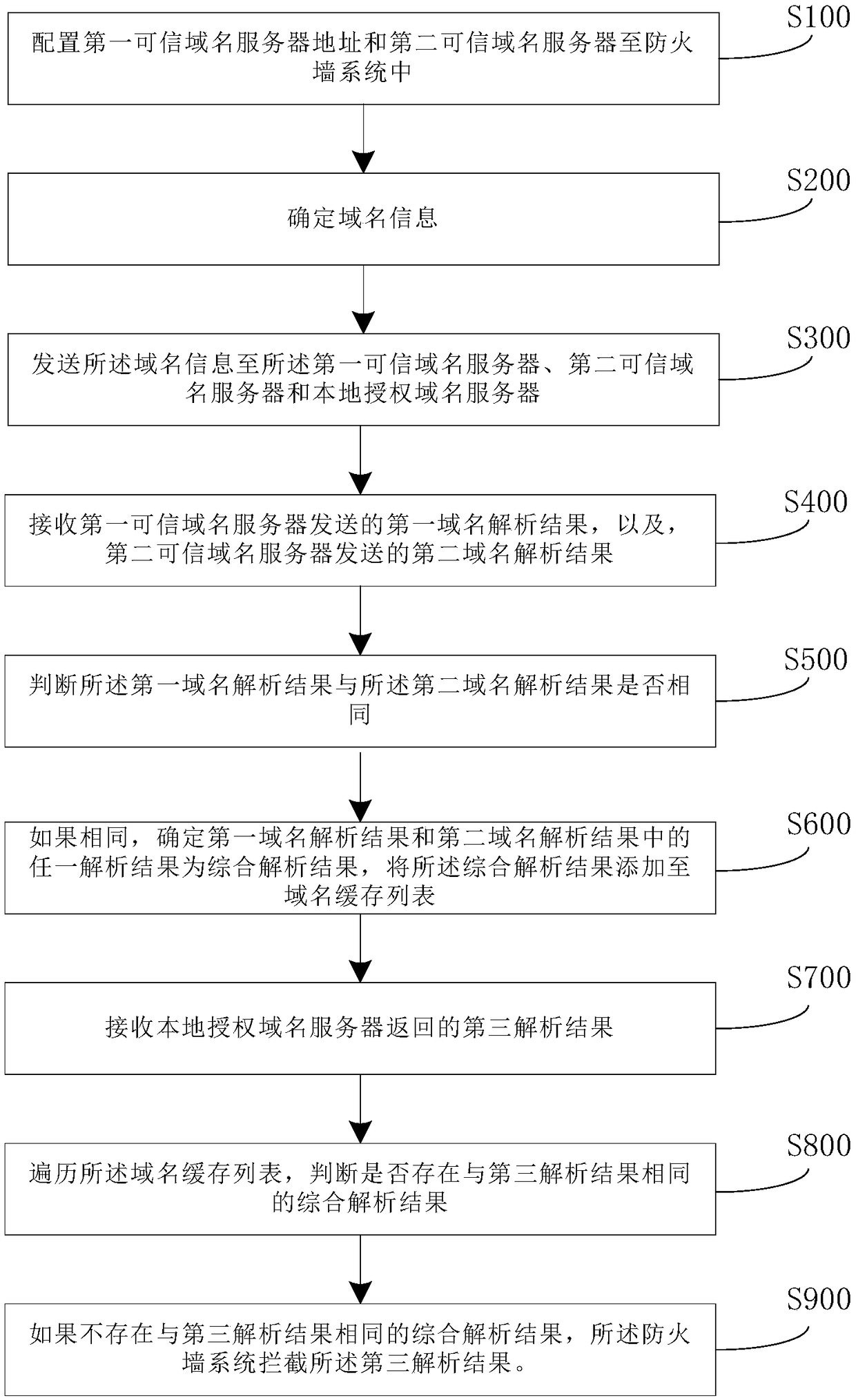
[0066] refer to figure 1 , a flowchart of a DNS hijacking defense method based on a firewall system provided by an embodiment of the present application, the method includes:
[0067] S100. Configure the address of the first trusted domain name server and the address of the second trusted domain name server in the firewall system.
[0068] Specifically, the addresses of two trusted domain name servers (the first trusted domain name server and the second trusted domain name server) can be added to the configuration of the firewall system. These two trusted domain name servers can be any other two authorized domain name servers. server or any other two DNS domain name servers with certain credibility, such as 8.8.8.8 and 114.114.114.114.
[0069] S200. Determine domain name information;
[0070] It should be explained that the firewall system plays a role of preventing hijacking in this embodiment of the application. Therefore, it is first necessary to determine the specific ...
Embodiment 2
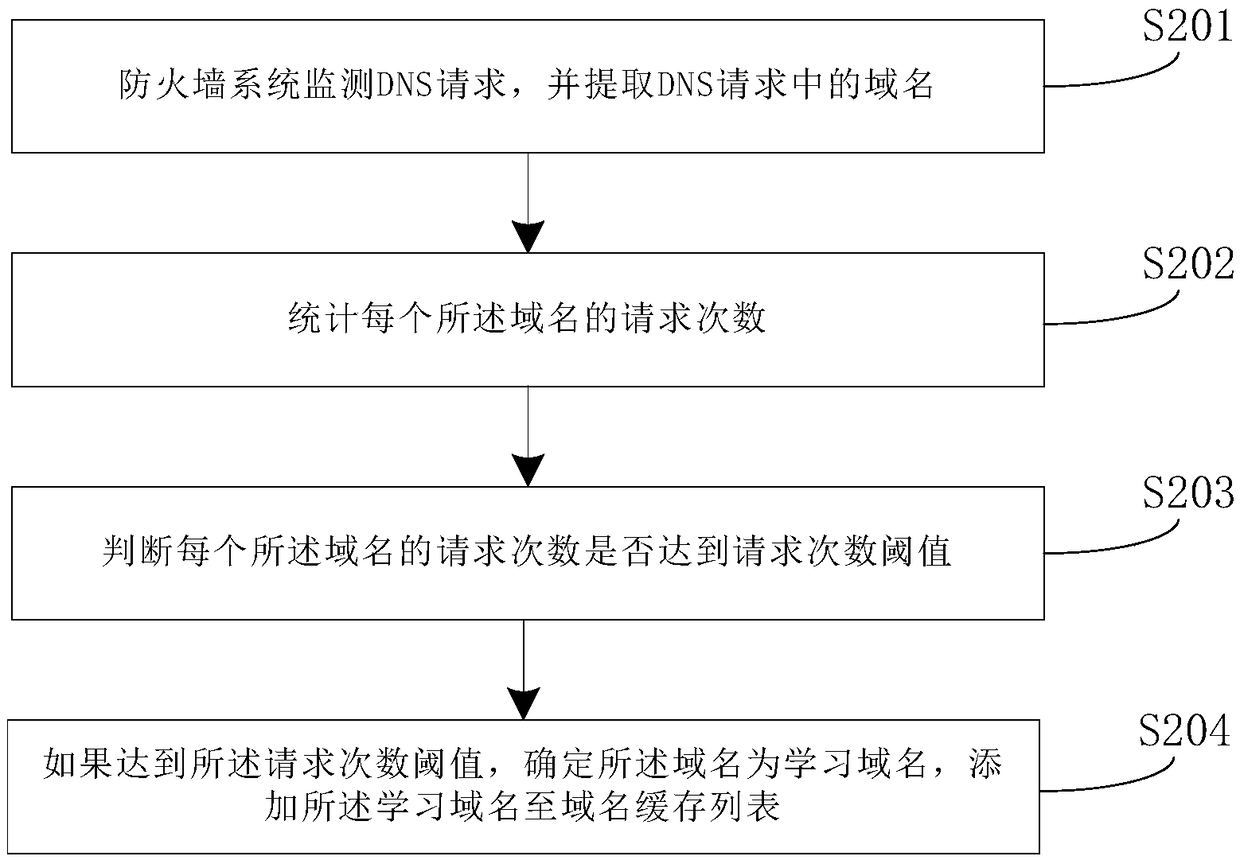
[0089] refer to figure 2 , a flow chart of another DNS hijacking defense method based on a firewall system provided by an embodiment of the present application, the step of determining domain name information includes:
[0090] S201. The firewall system monitors the DNS request, and extracts the domain name in the DNS request;
[0091] It should be noted that the firewall system monitors and extracts the domain name in the DNS request message in real time. In the embodiment of the present application, the firewall system monitors each DNS request message in real time.
[0092] S202. Count the number of requests for each domain name;
[0093] S203. Judging whether the number of requests for each domain name reaches a request number threshold;
[0094] S204. If the request times threshold is reached, determine that the domain name is a learning domain name, and add the learning domain name to a domain name cache list.
[0095] Specifically, when the number of requests for t...
Embodiment 3
[0098] The step of determining domain name information also includes:
[0099] Configure custom domain names to the domain name cache list.
[0100] In the embodiment of this application, if there is a special protection requirement for a certain domain name, manual configuration can be performed. For example, www.dfg.com is directly added to the domain name cache list.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com