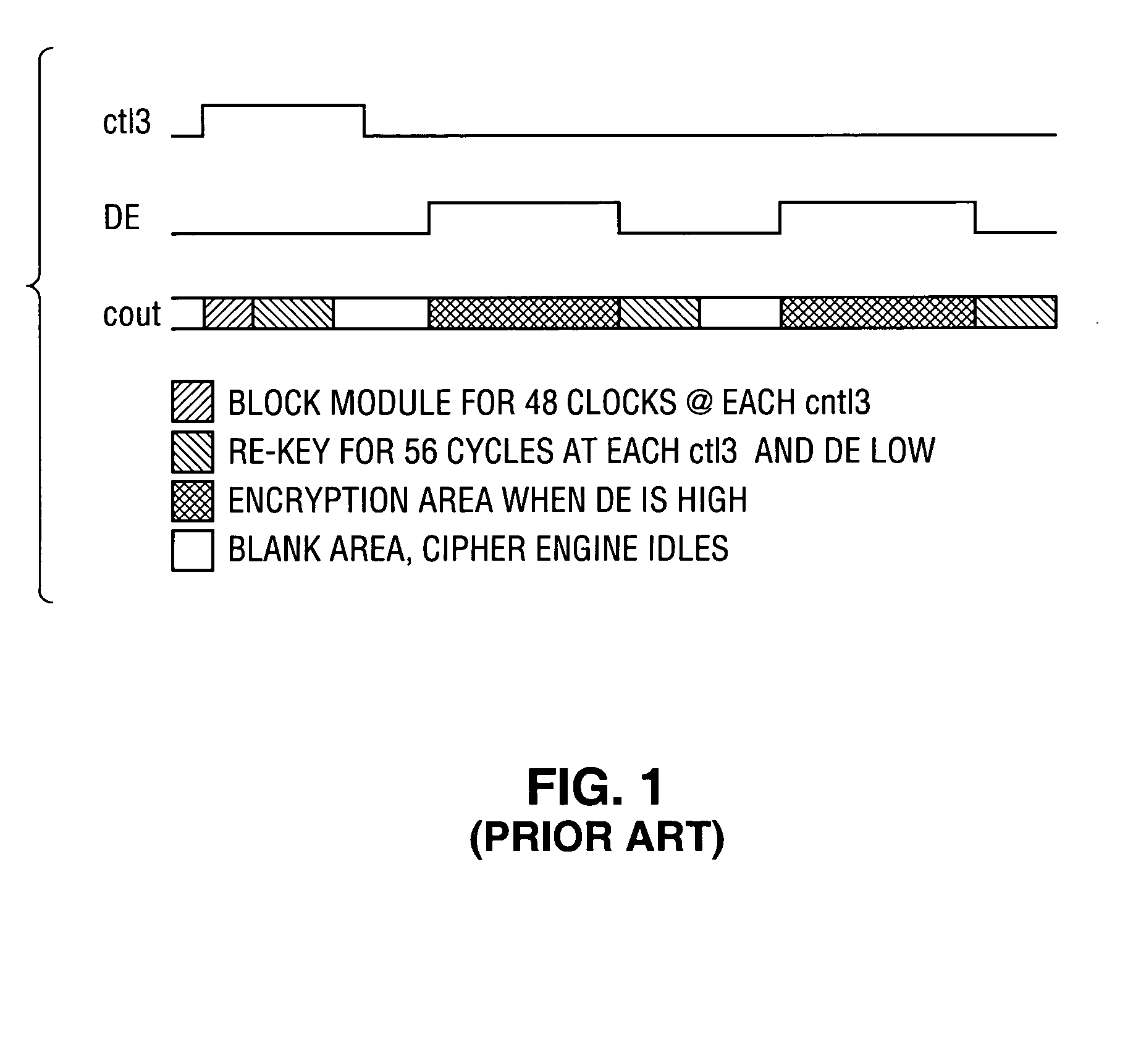
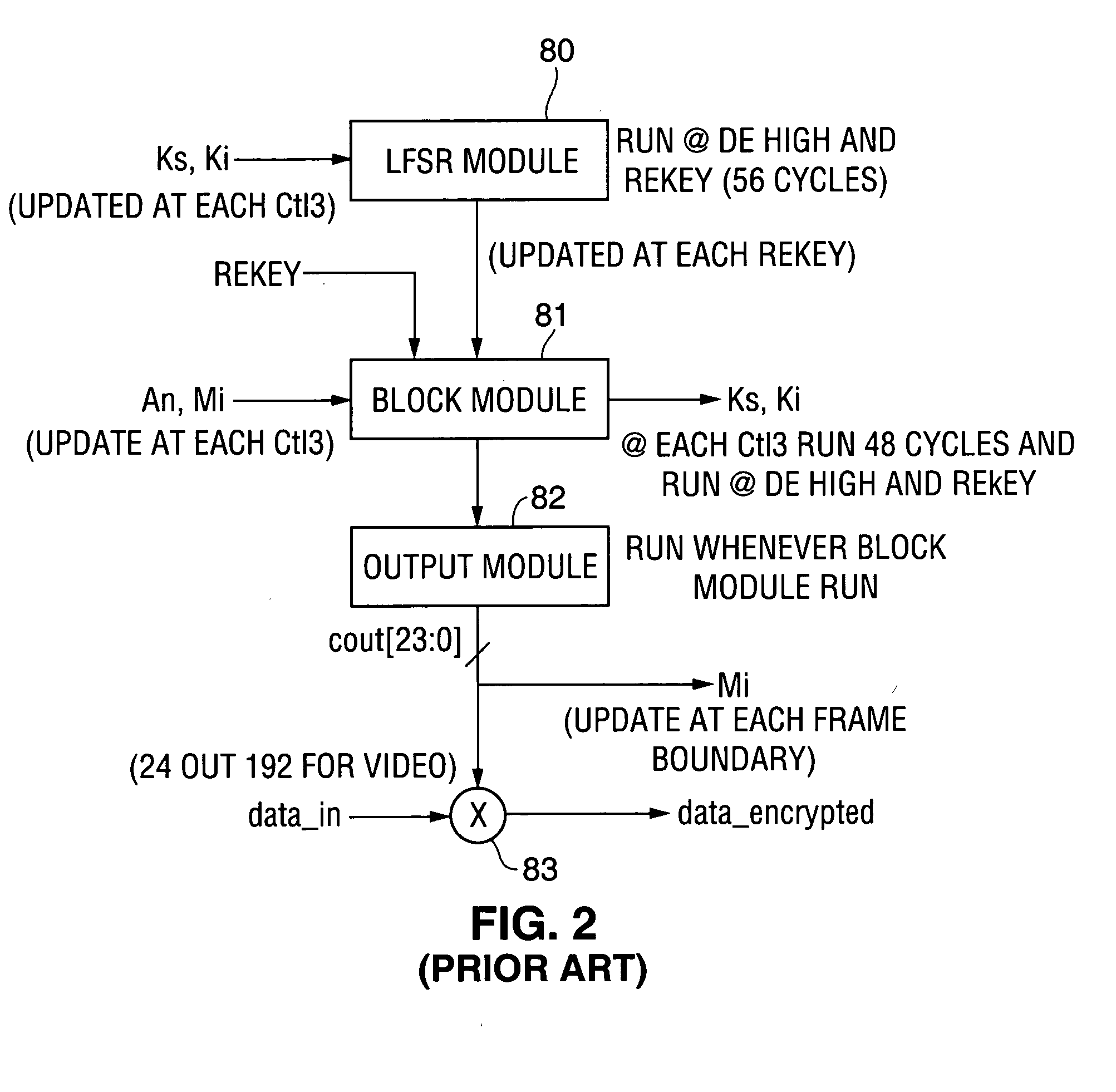
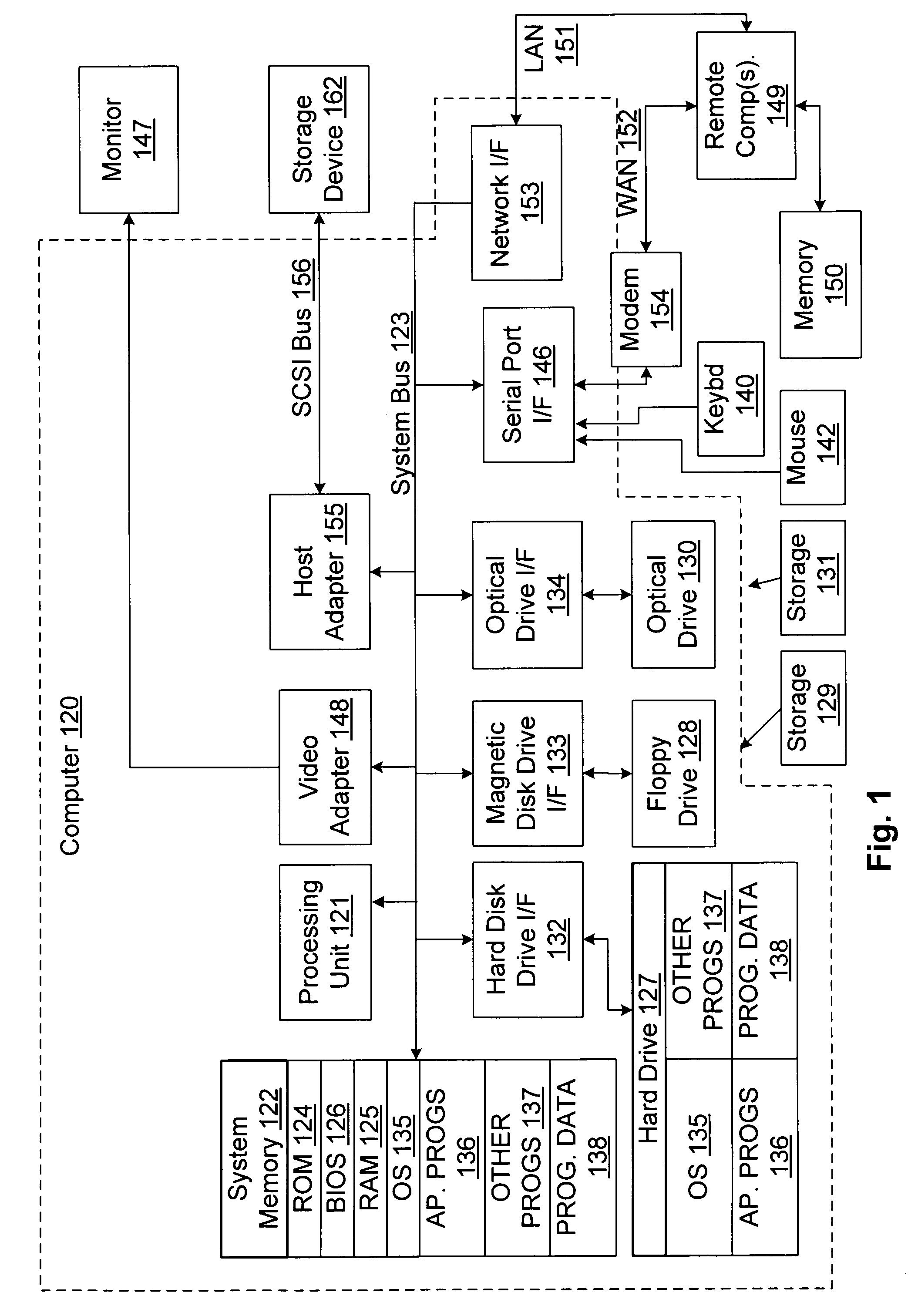
Patents
Literature
31results about How to "Level of protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
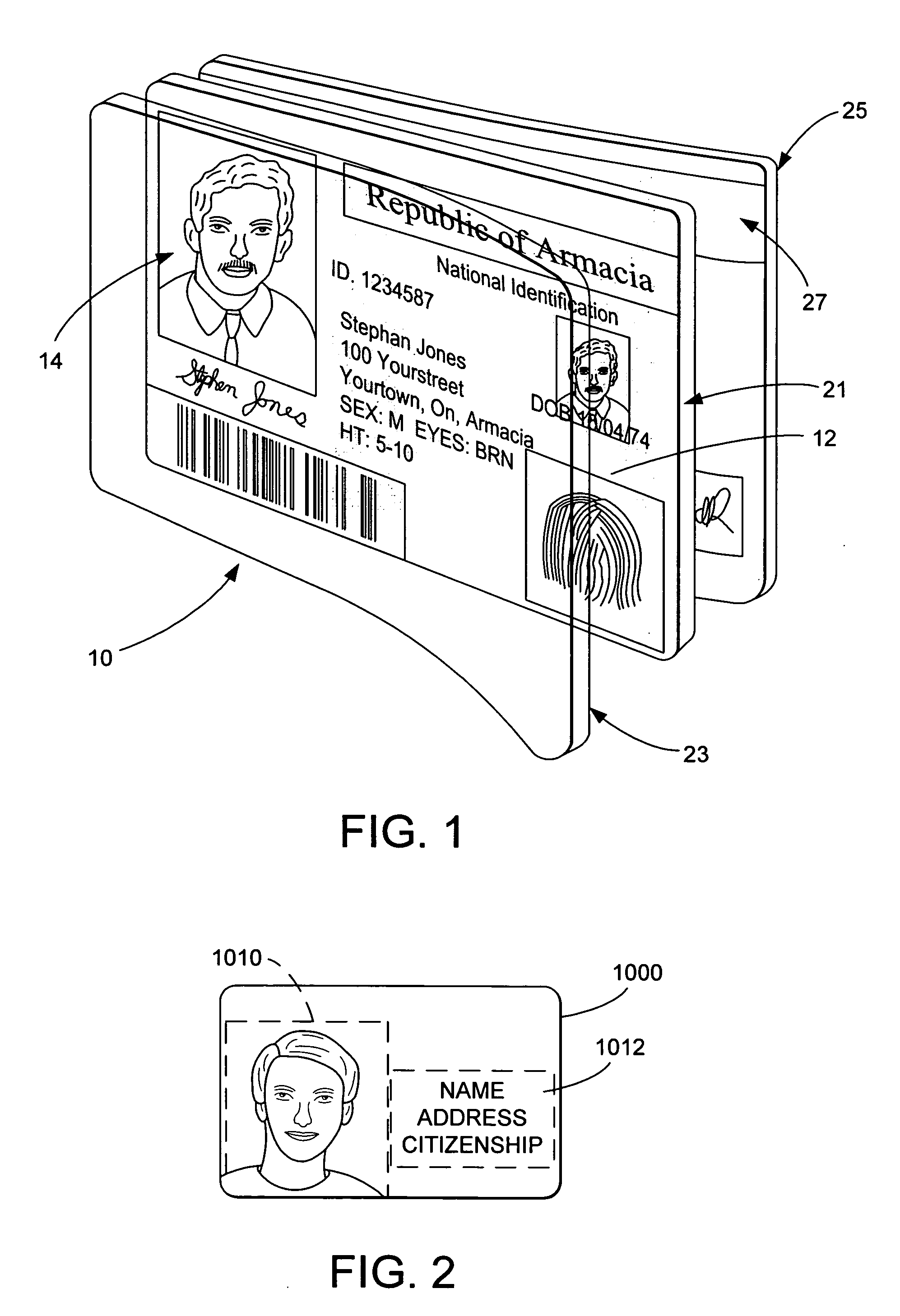
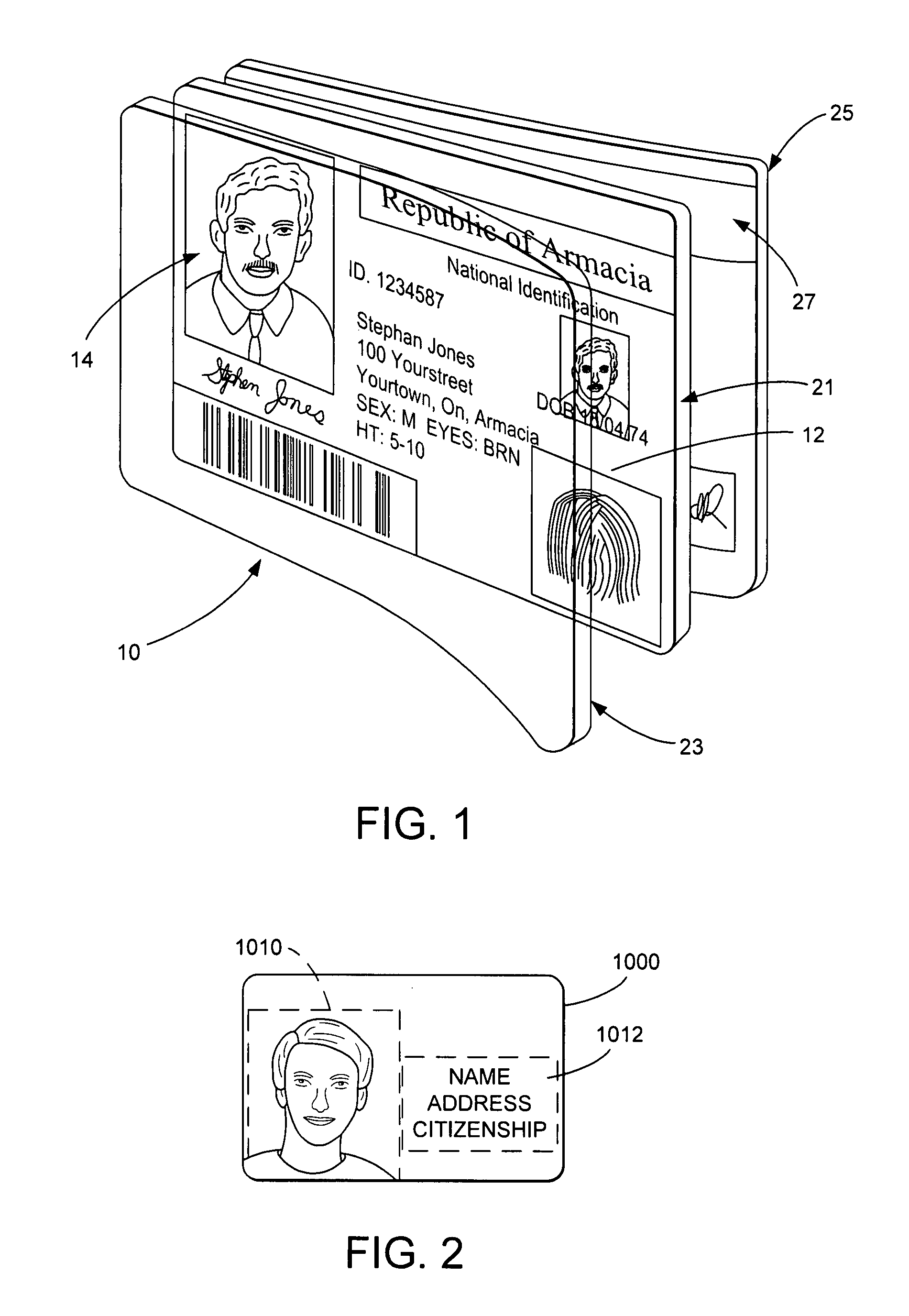
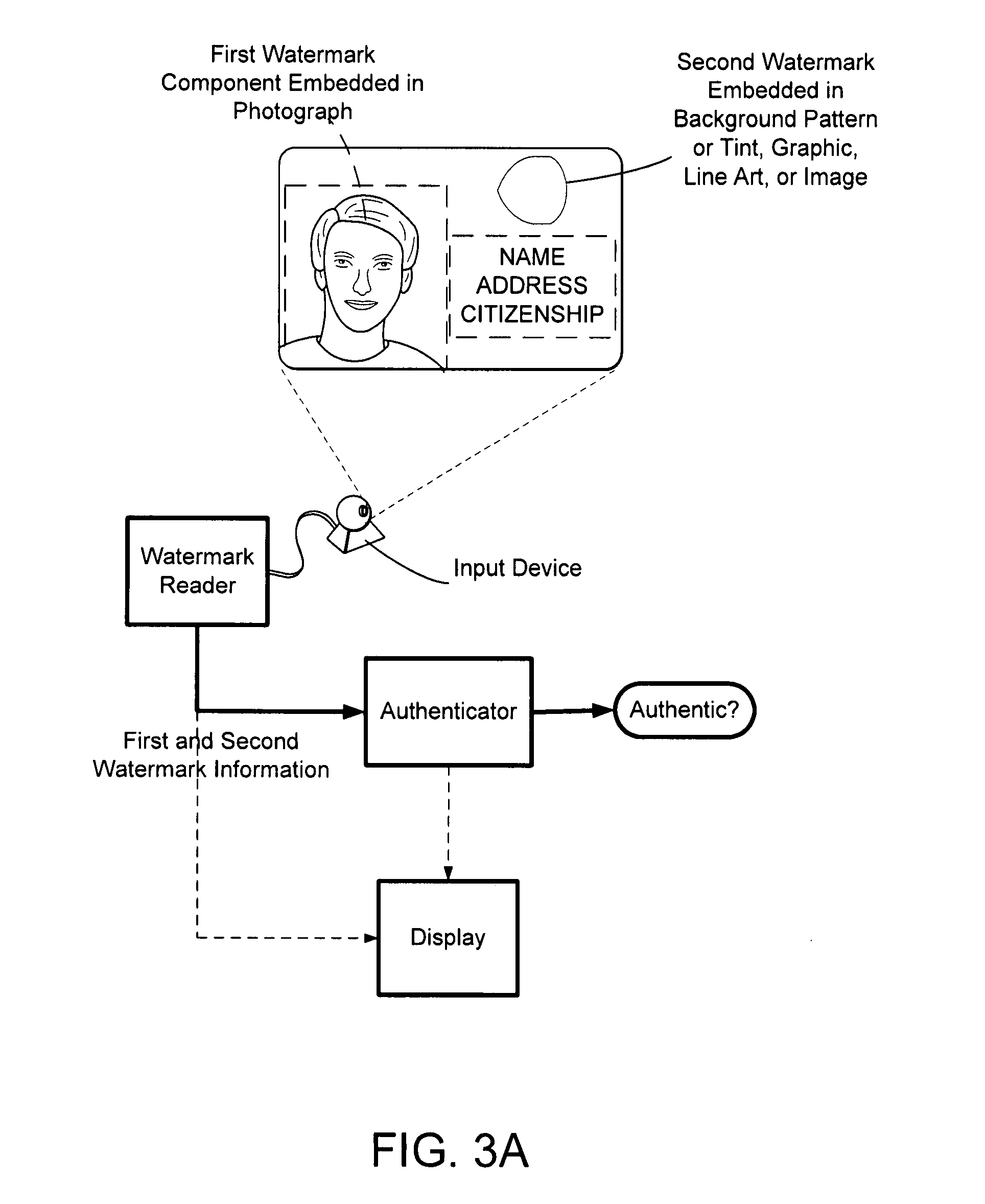
Identification document and related methods
InactiveUS20050160271A9Level of protectionEasy to useOther printing matterPaper-money testing devicesDocumentationComputer science
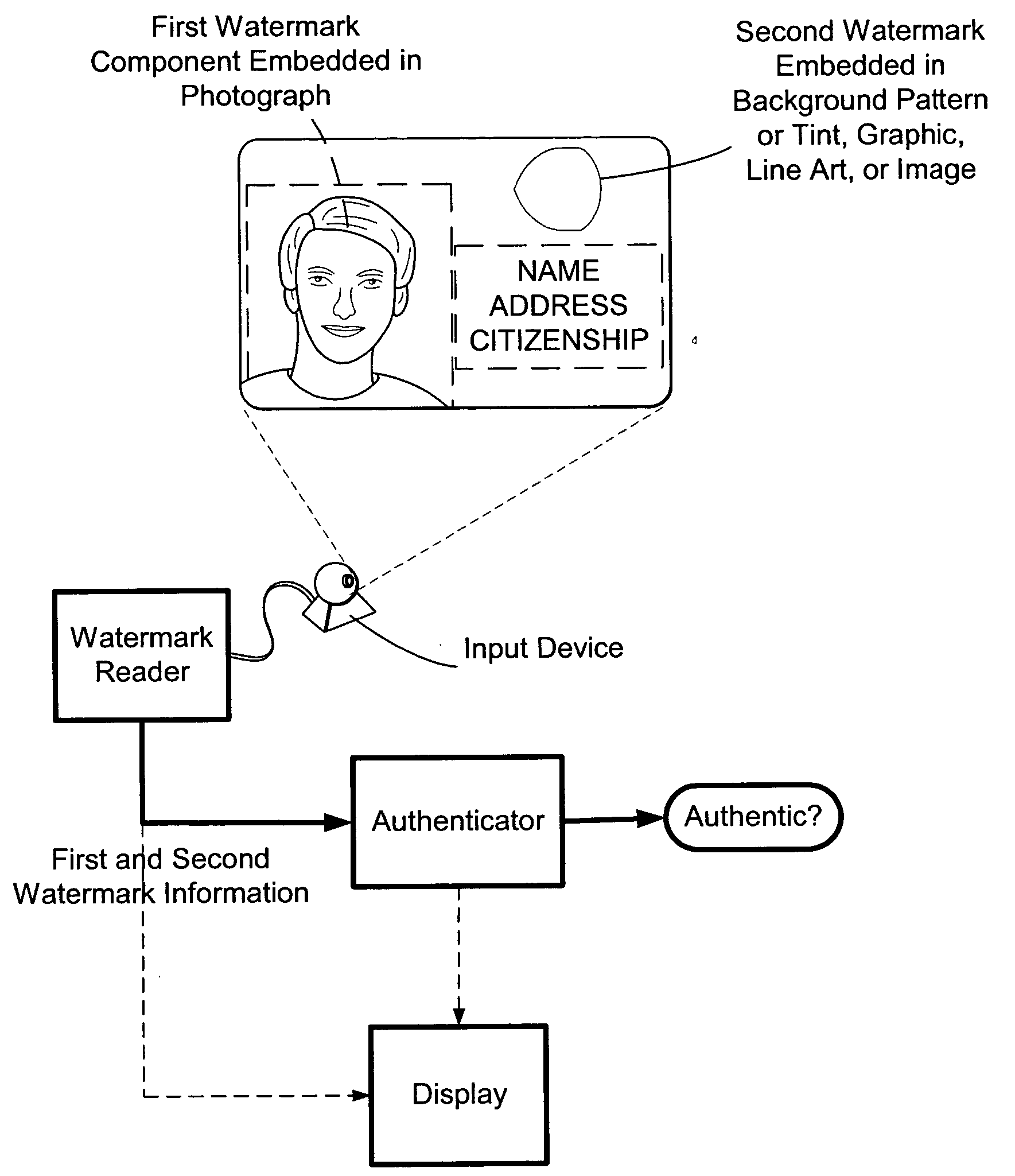
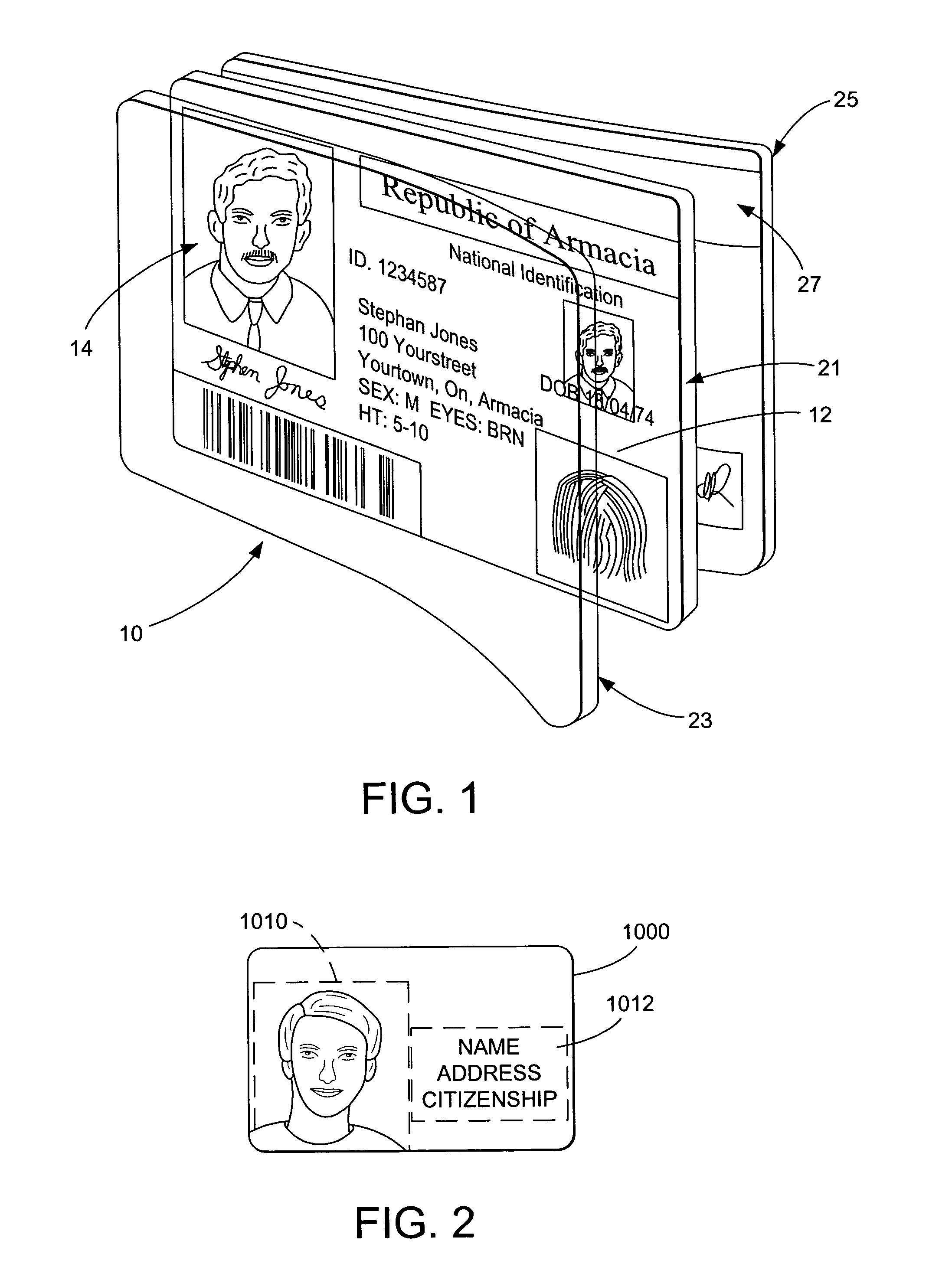
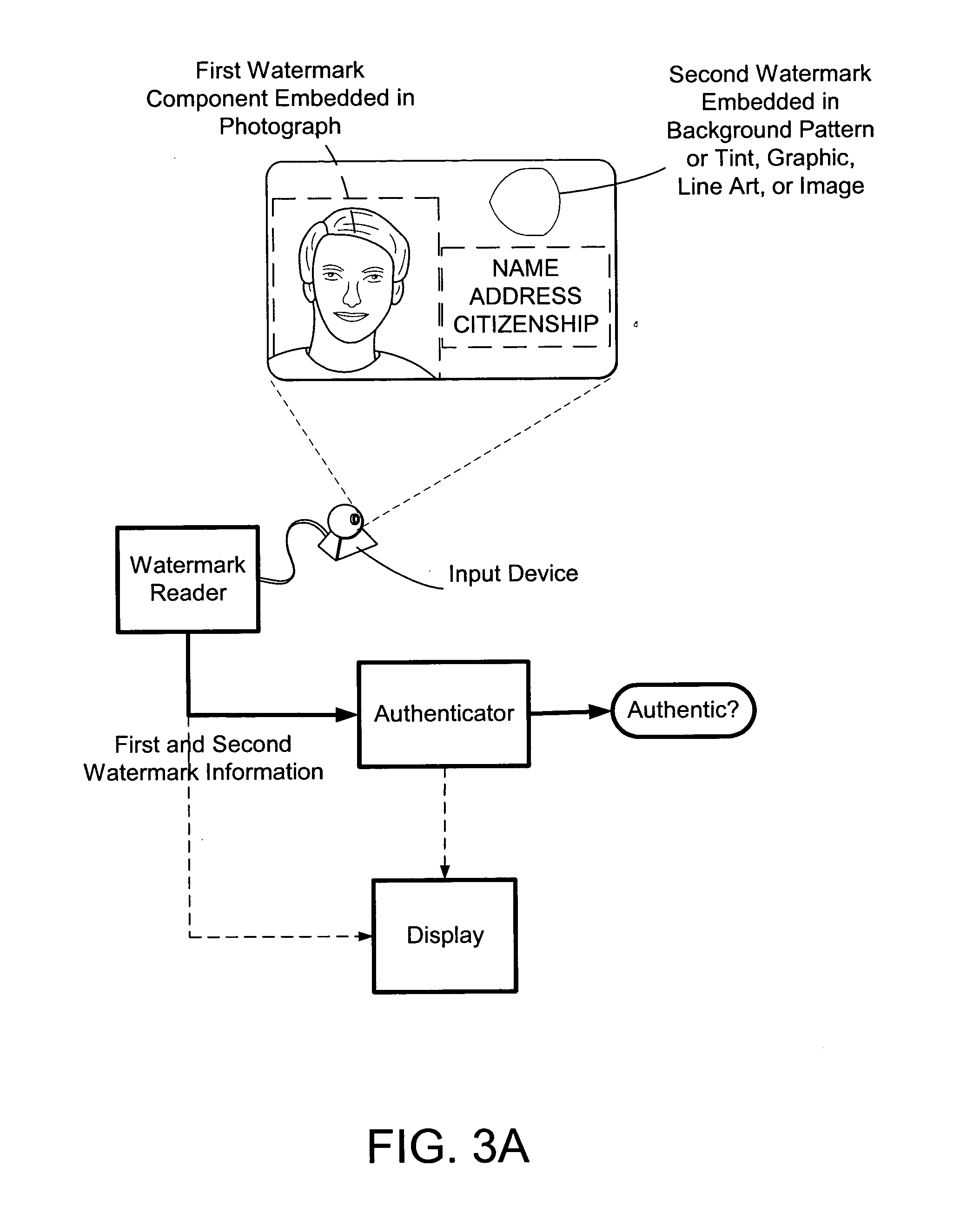
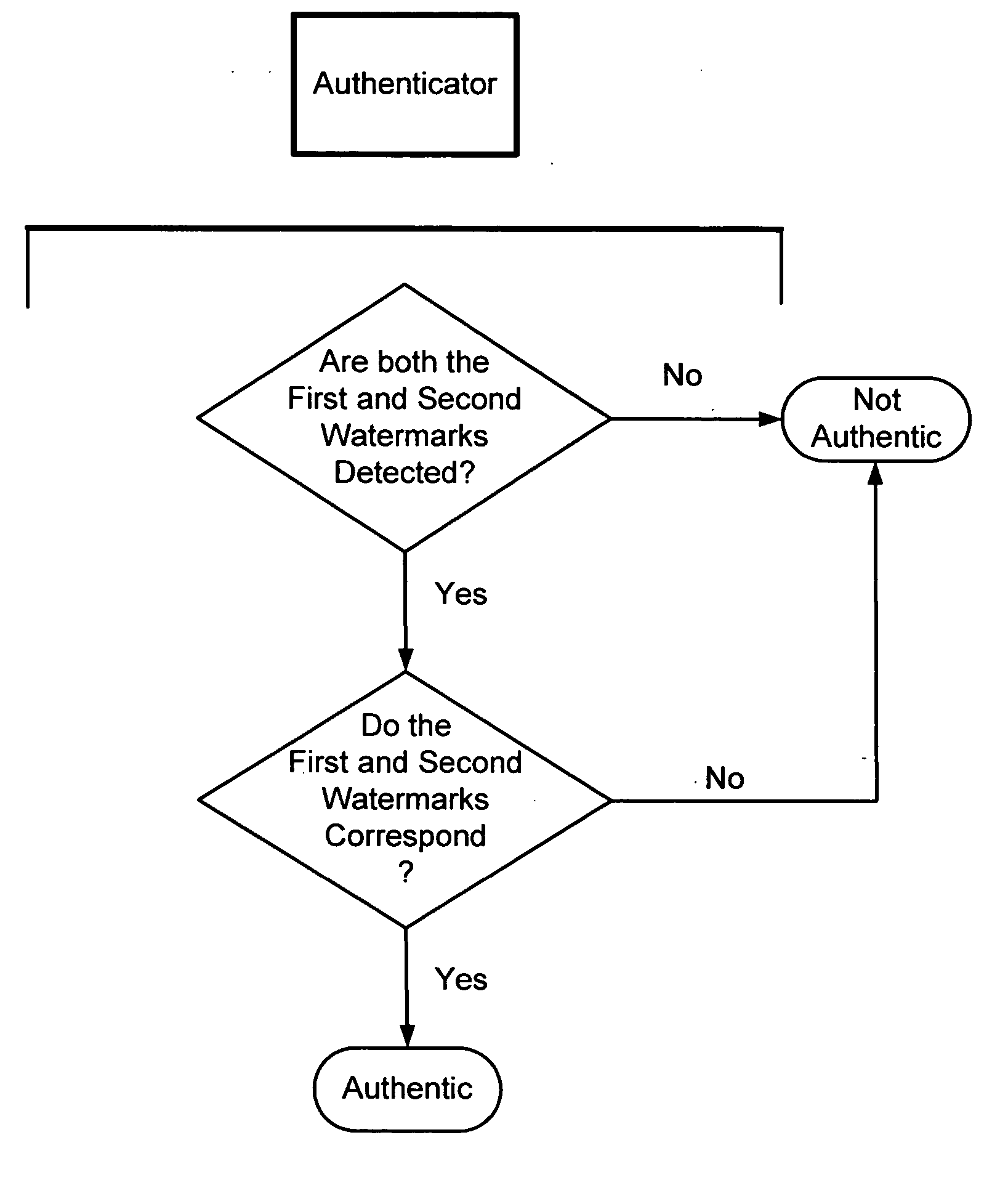
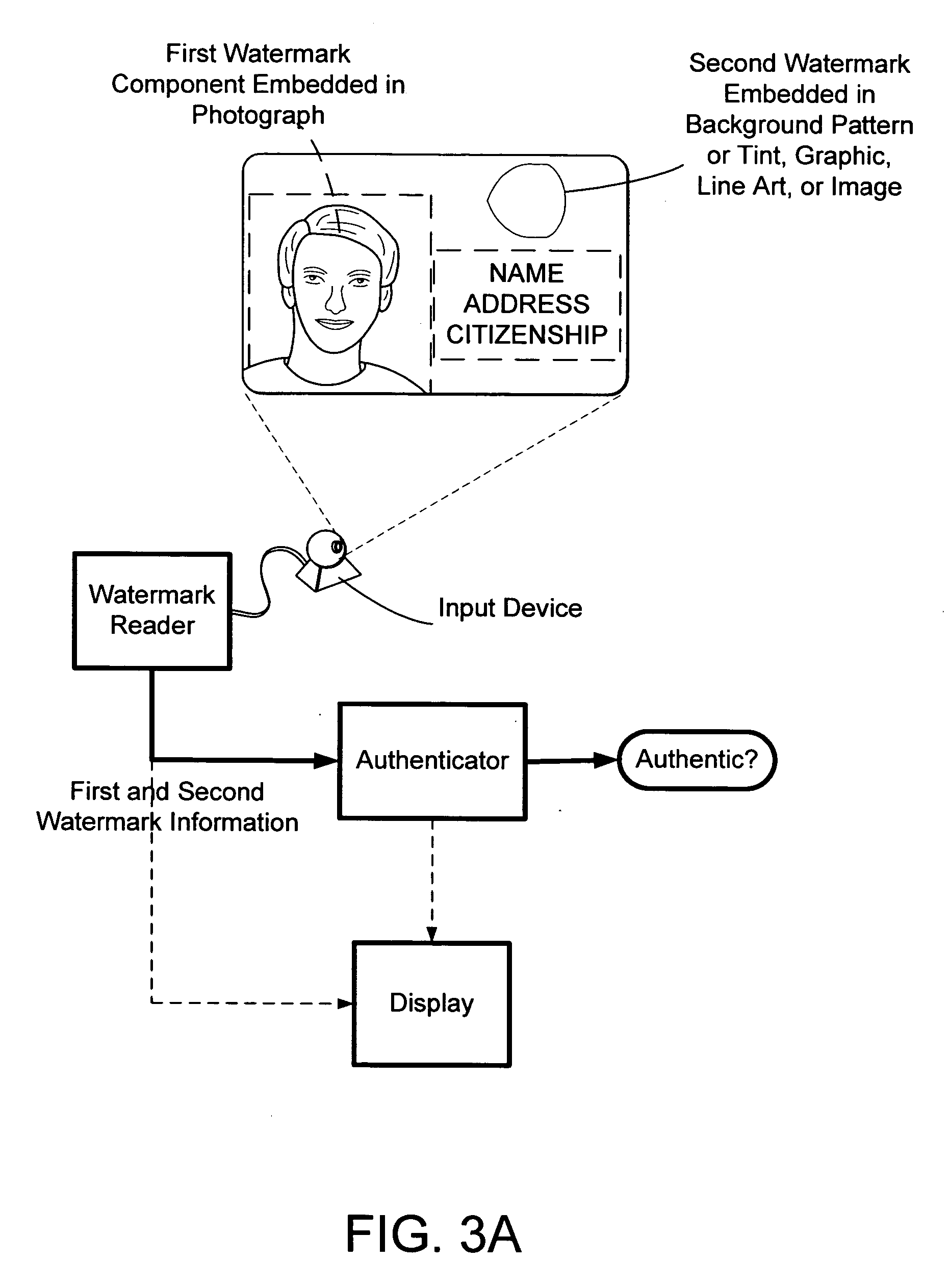
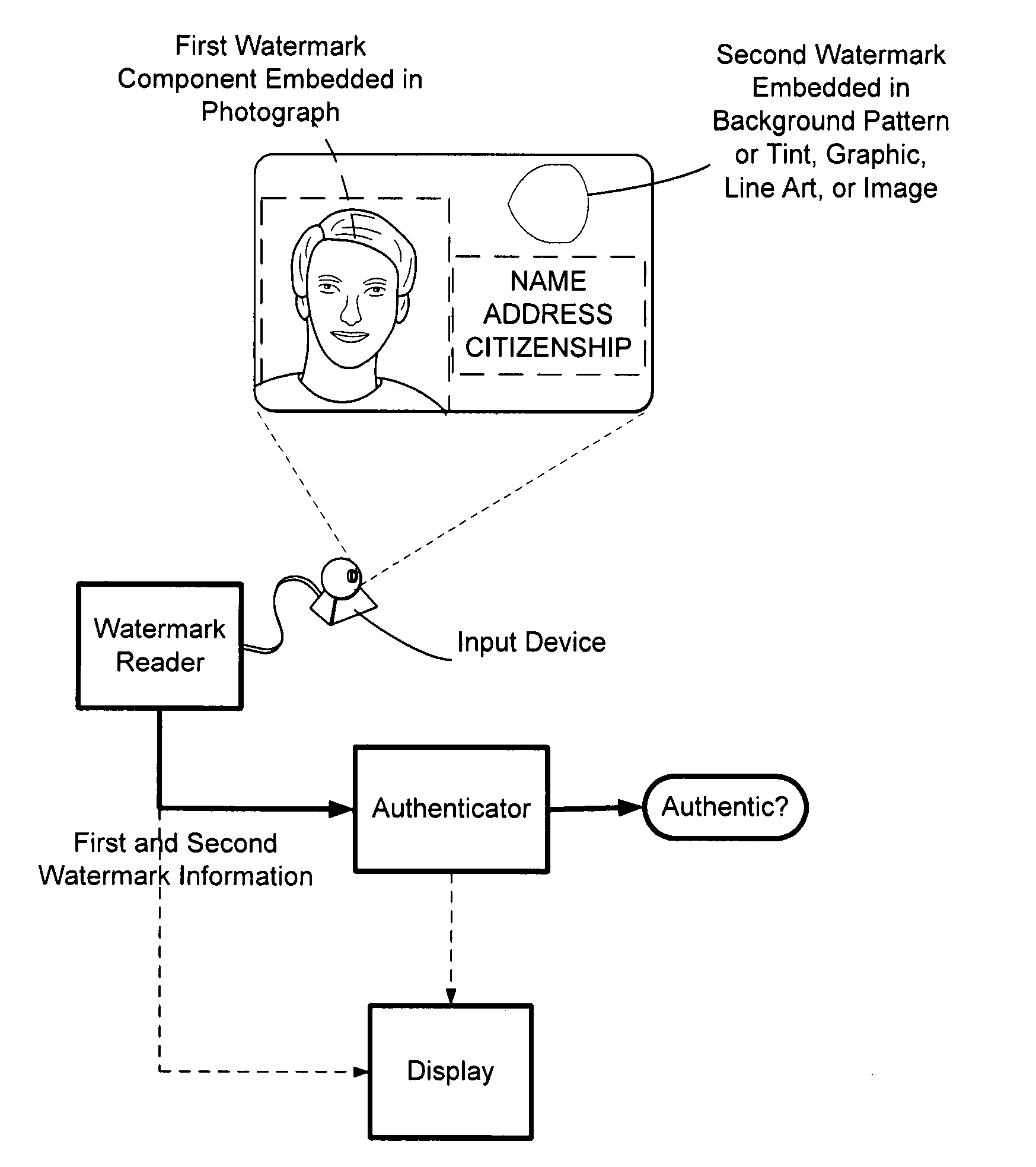
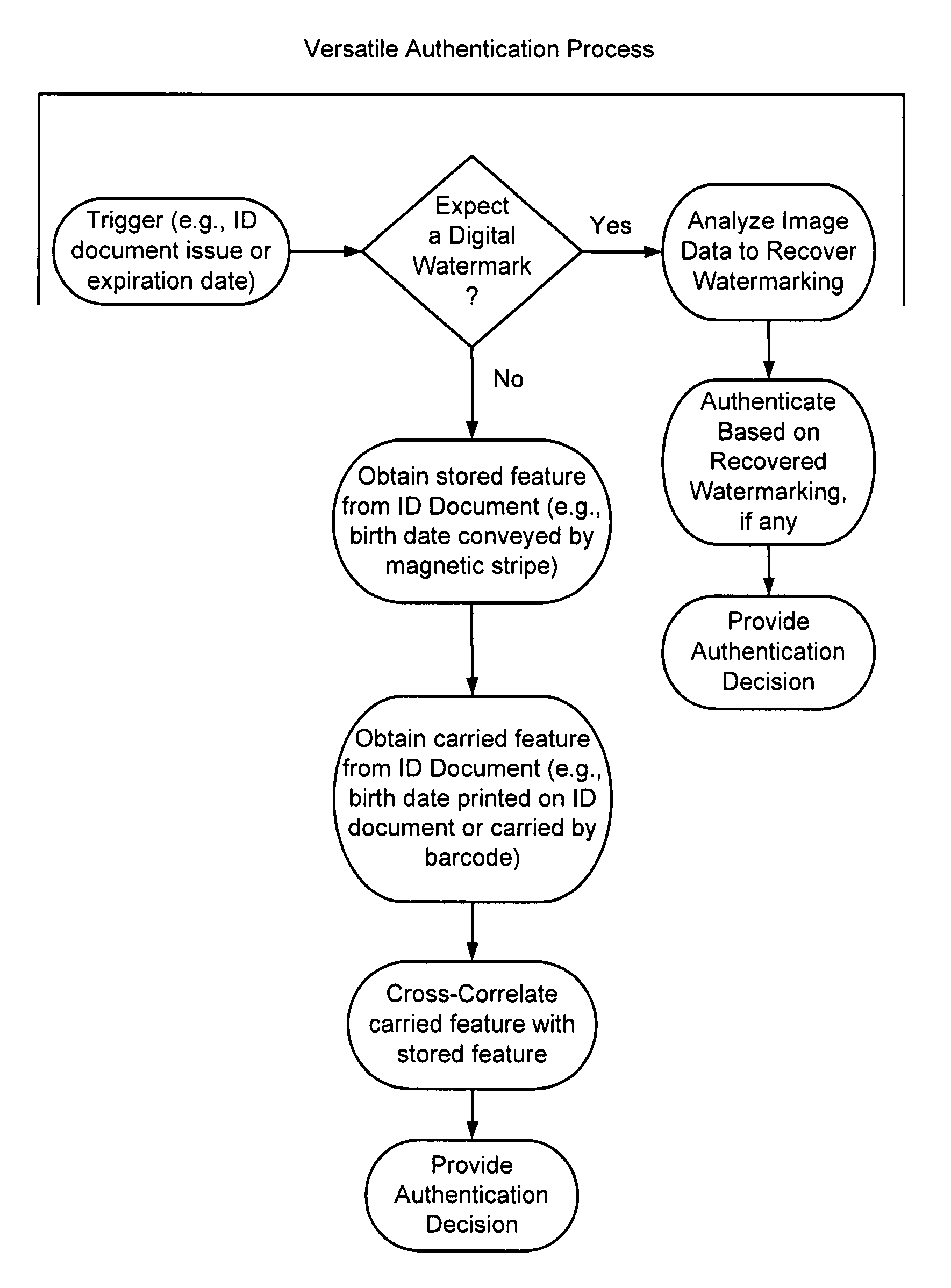
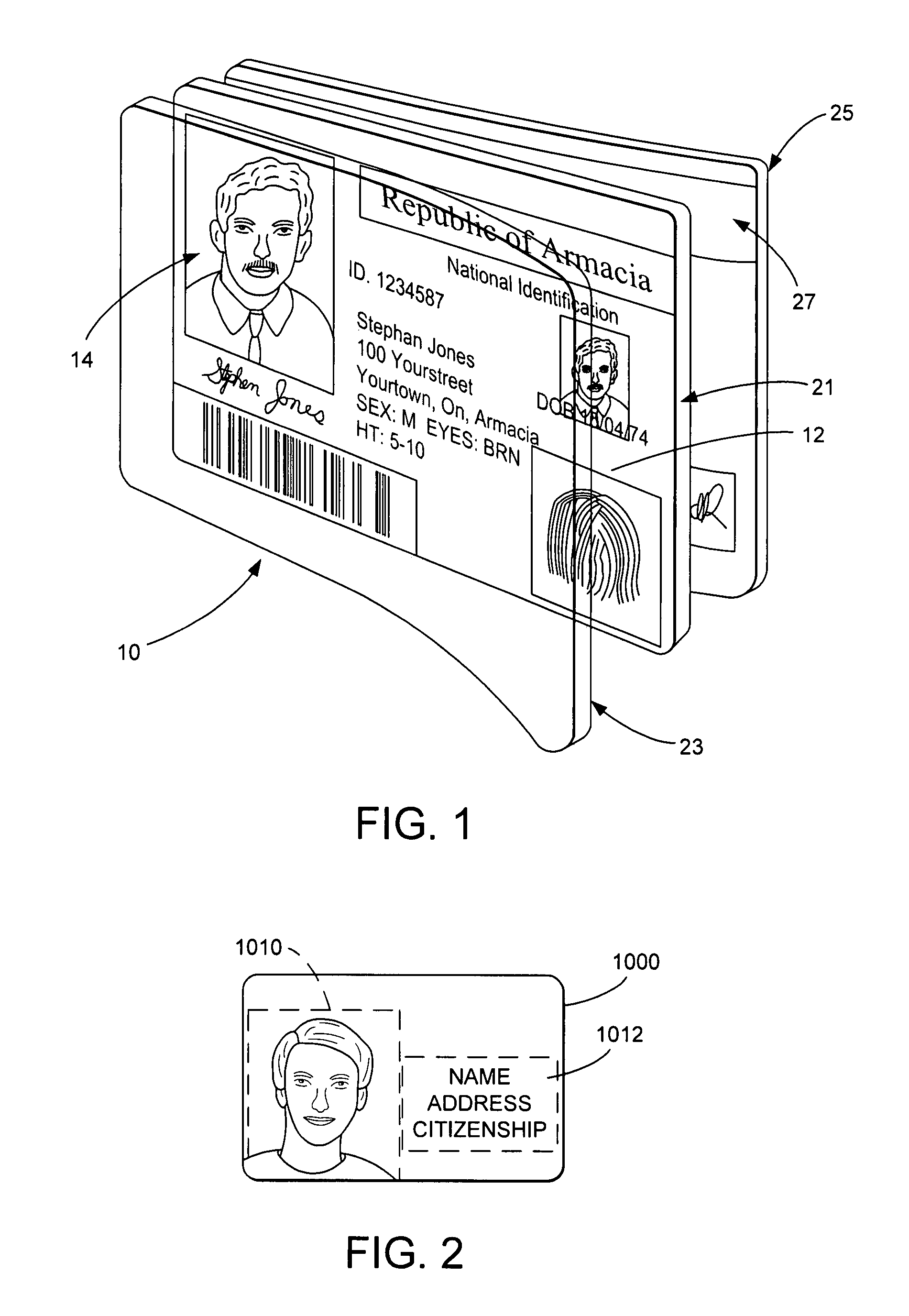
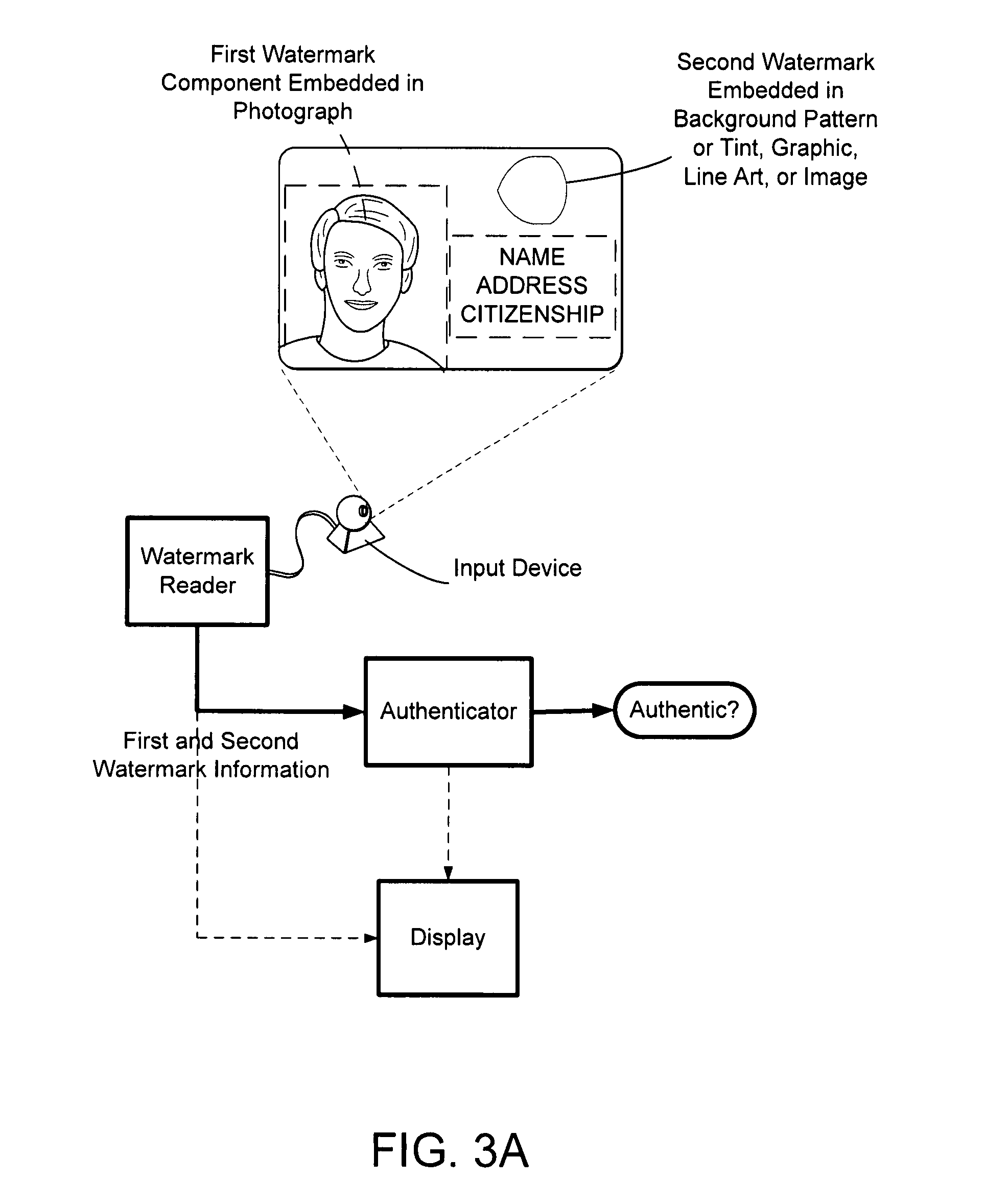
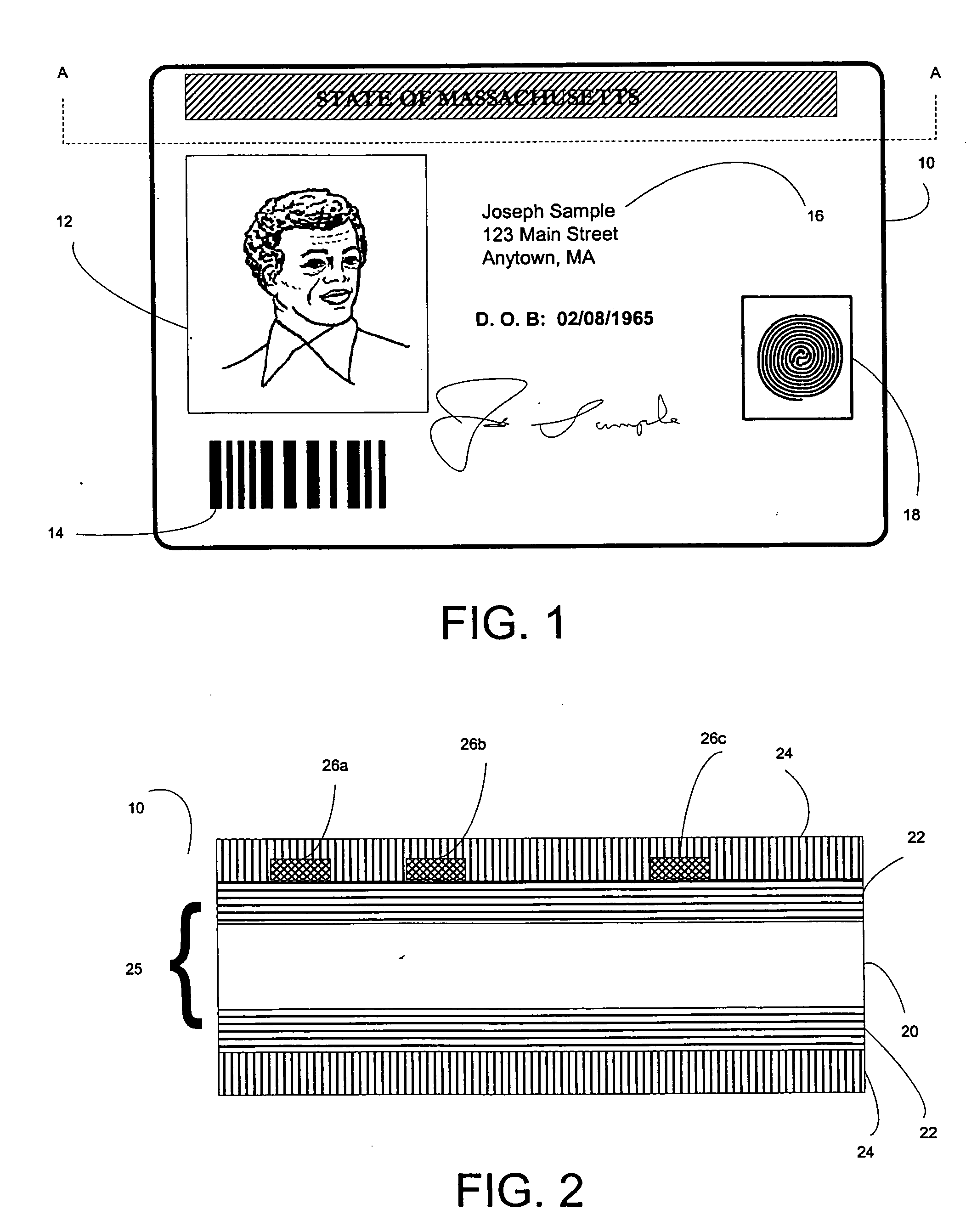
The present invention provides methods and systems for authenticating identification documents. We also teach an identification document including two or more digital watermarks. The watermarks correspond with each other or with indicia carried by the identification document. The correspondence can be verified to determine authenticity. We also provide digital watermark detection methods and systems to identify the different watermarks through embedded orientation components. We then focus watermark message-decoding efforts on areas identified as likely including watermark orientation components. In one implementation we provide a watermark detection trigger to identify so-called legacy documents. The trigger may indicate the presence or expected absence of a digital watermark. In other implementations we provide a versatile document authenticator to toggle between watermarking and non-watermarking authentication processes depending on a detection trigger.
Owner:DIGIMARC CORP
Identification document and related methods
ActiveUS20070016790A1Level of protectionEasy to useOther printing matterPaper-money testing devicesPaper documentDocument preparation
The present invention provides methods and systems for authenticating identification documents. We also teach an identification document including two or more digital watermarks. The watermarks correspond with each other or with indicia carried by the identification document. The correspondence can be verified to determine authenticity. We also provide digital watermark detection methods and systems to identify the different watermarks through embedded orientation components. We then focus watermark message-decoding efforts on areas identified as likely including watermark orientation components. In another implementation we provide a watermark detection trigger to identify so-called legacy documents. The trigger may indicate the presence or expected absence of a digital watermark. In other implementations we provide a versatile document authenticator to toggle between watermarking and non-watermarking authentication processes depending on a detection trigger. Other implementations are provided as well.
Owner:DIGIMARC CORP
Detecting Media Areas Likely of Hosting Watermarks
ActiveUS20080149713A1Enhance security and certaintyLevel of protectionAcutation objectsPaper-money testing devicesDigital watermarkingDigital data
The present invention relates generally to digital watermarking and steganographic encoding. One claim recites a method including: receiving data corresponding to at least a portion of digital data; separating the data into a plurality of portions; determining a measure relative to a predetermined measure for each of the portions, wherein the measure comprises a measure related to a predetermined digital watermark signal; based at least in part on the measure, identifying which out of the plurality of portions are likely to host digital watermarking therein. Of course, other combinations are provided as well.
Owner:DIGIMARC CORP (FORMERLY DMRC CORP) +1
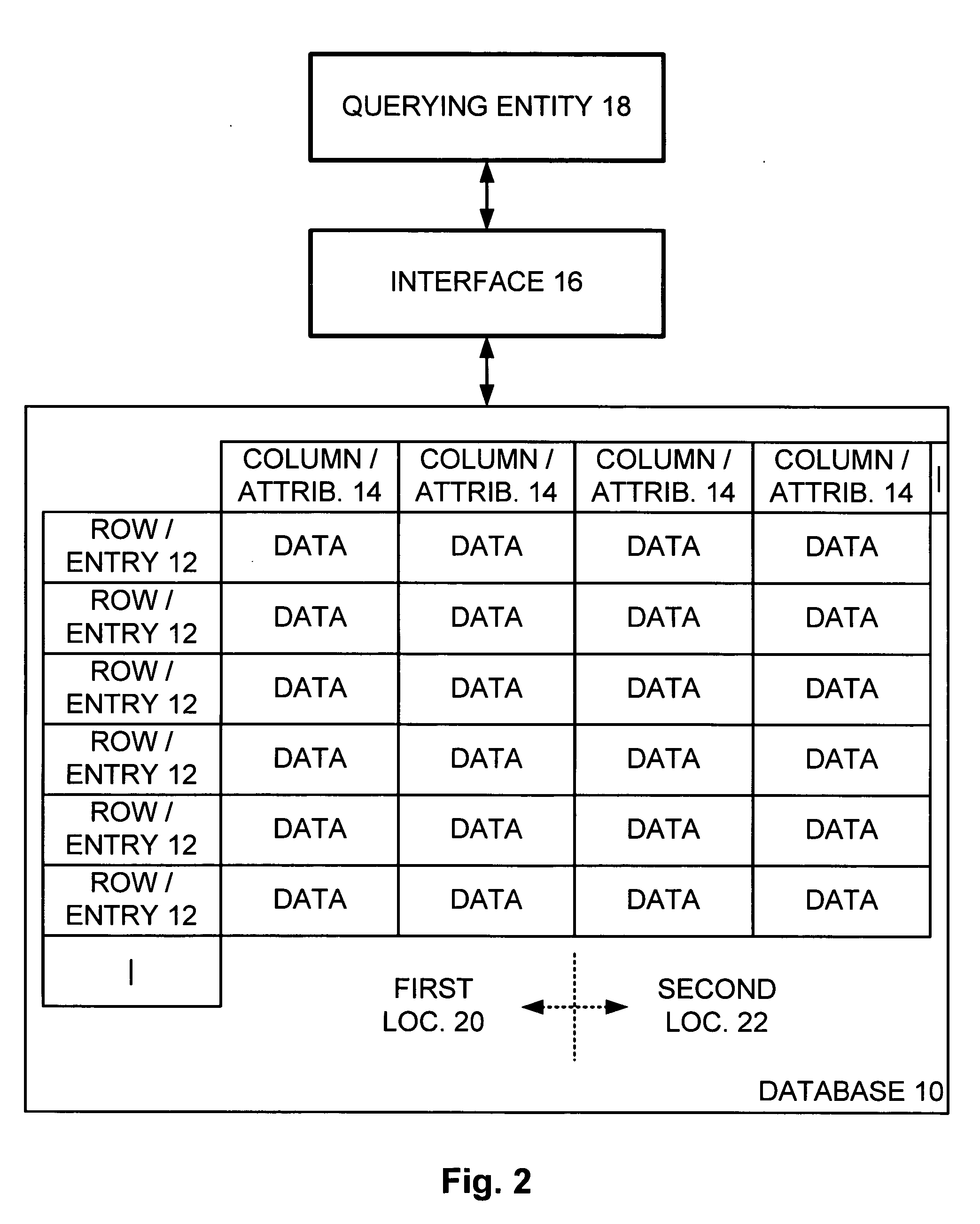
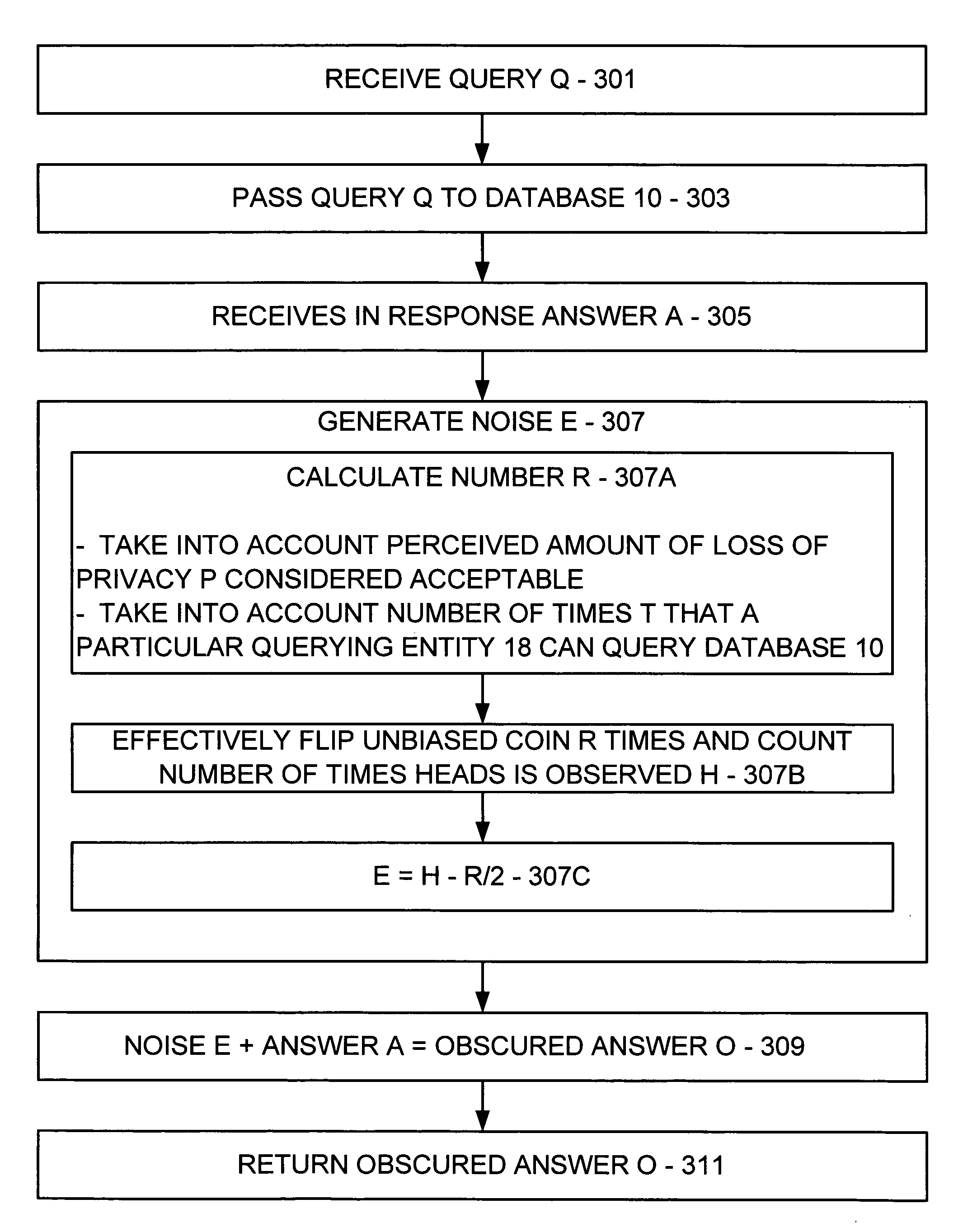
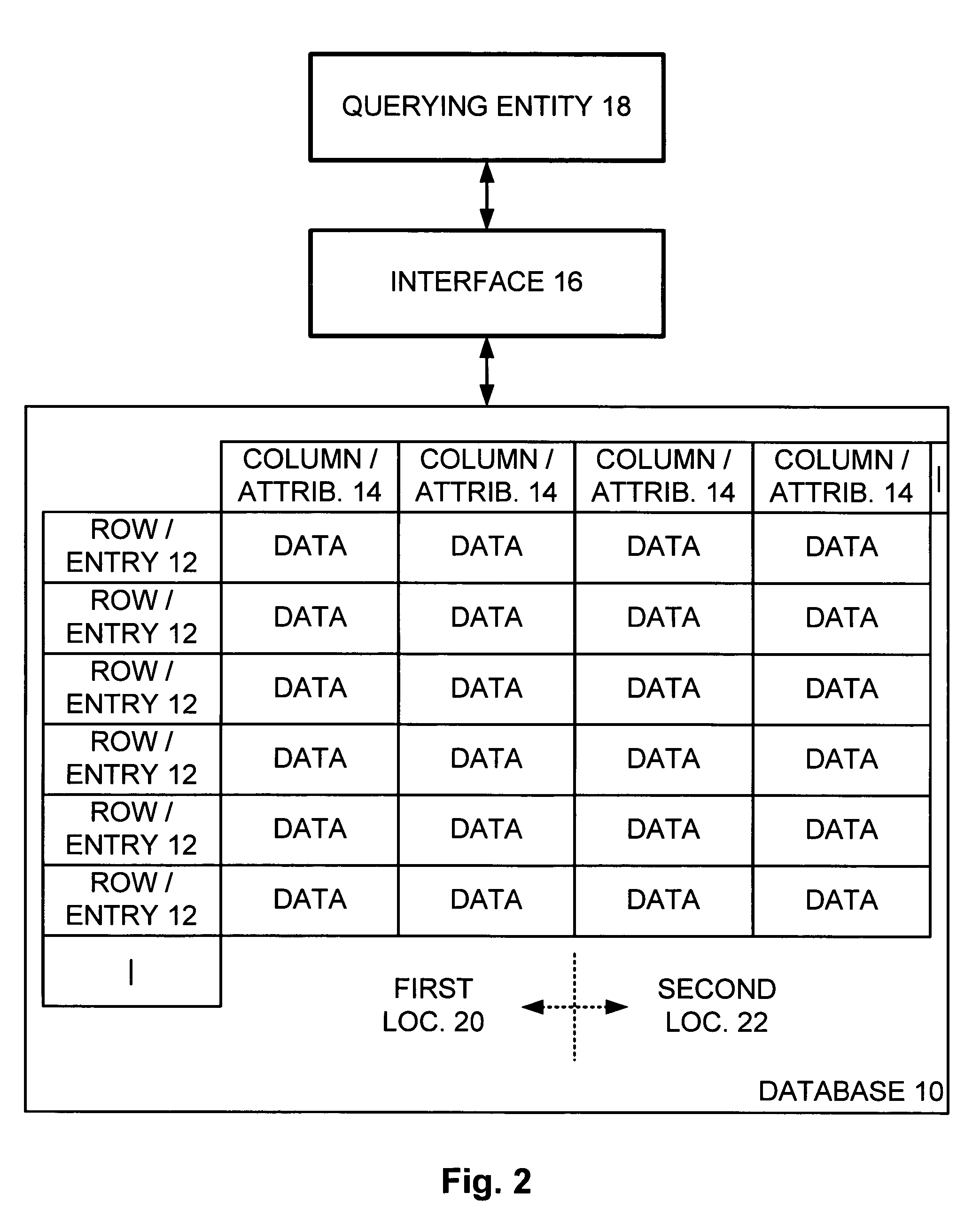
Preserving privacy when statistically analyzing a large database
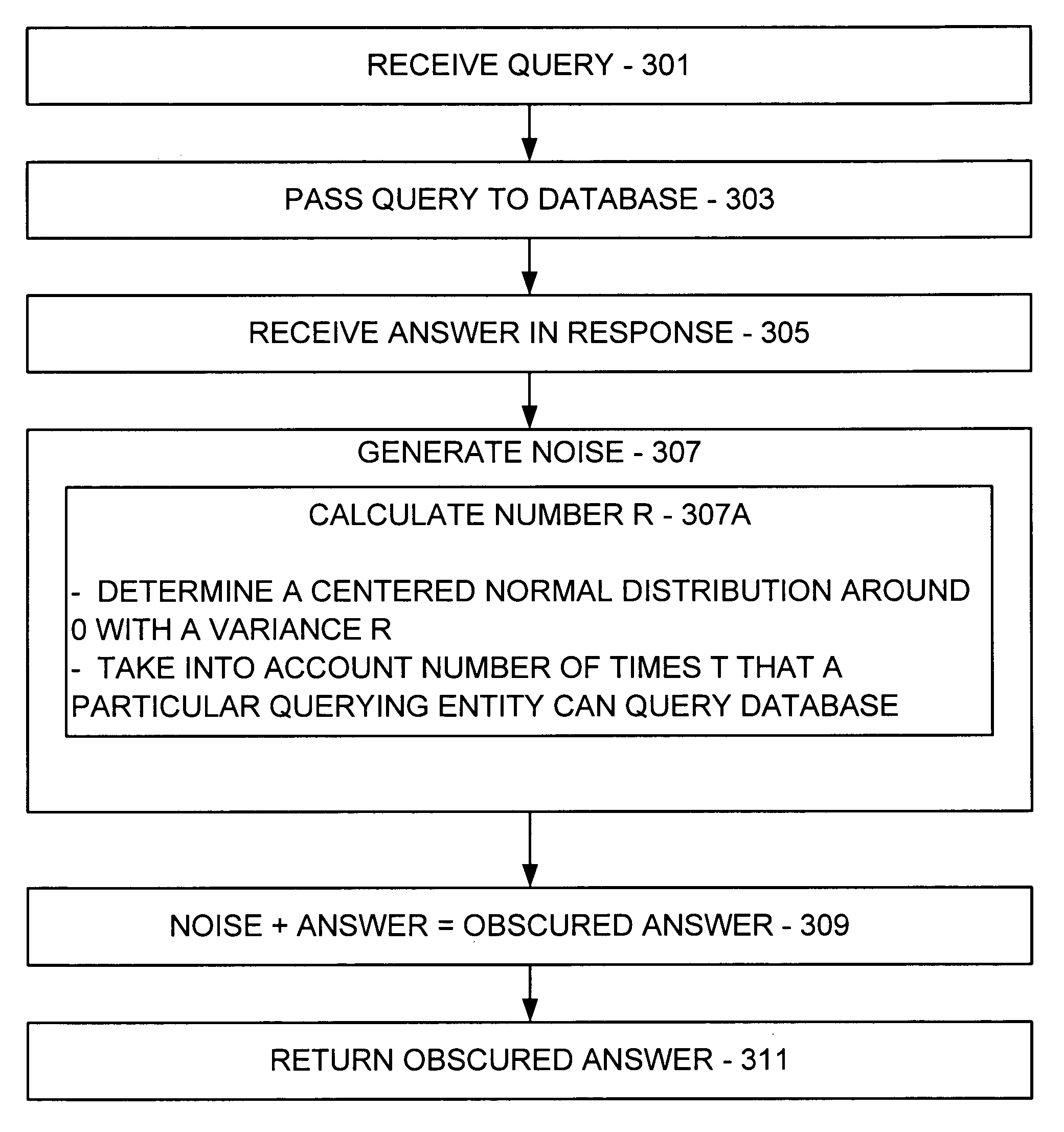
InactiveUS20060161527A1Level of protectionComputer security arrangementsSpecial data processing applicationsStatistical analysisPrivacy protection
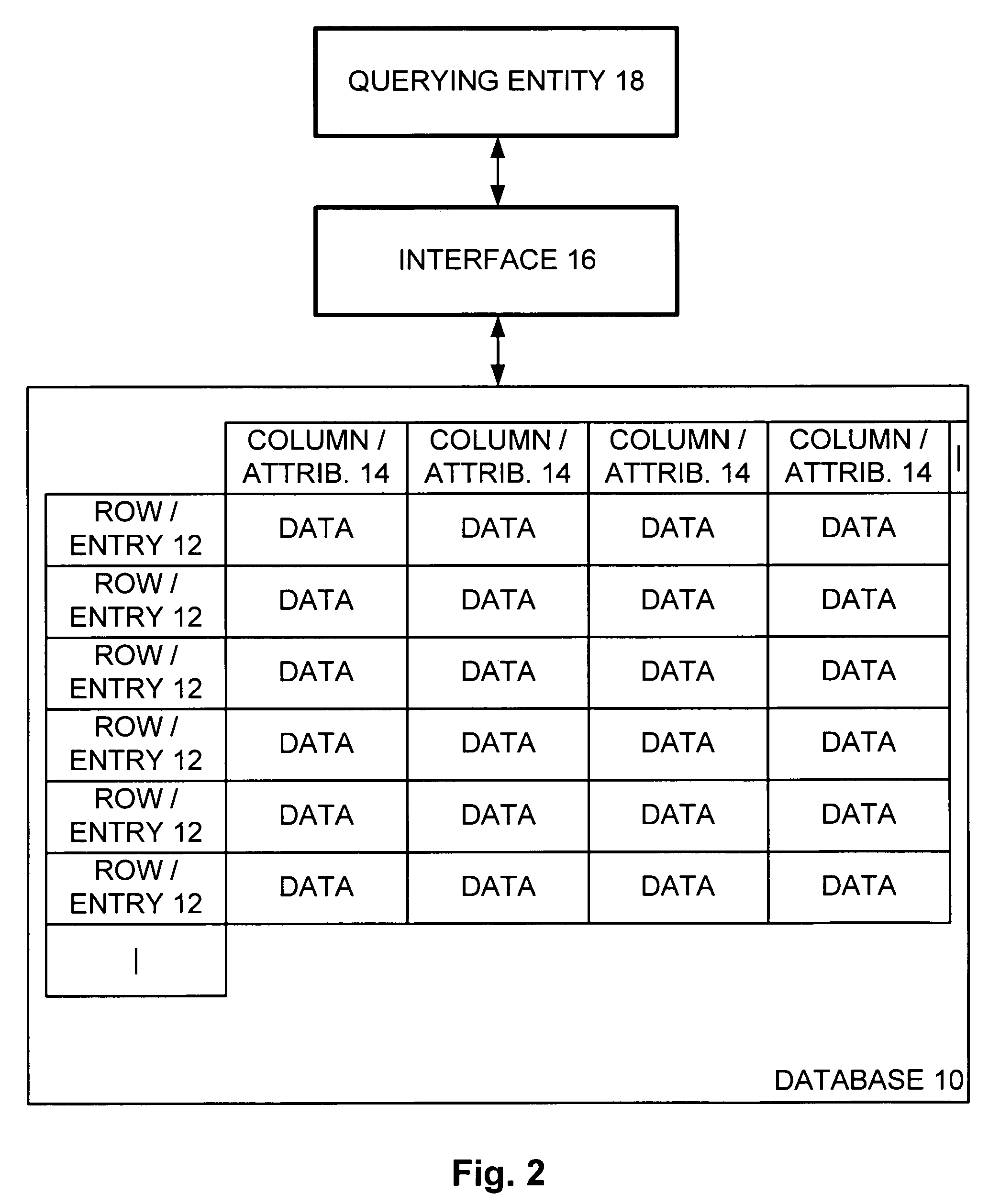
A database has a plurality of entries and a plurality of attributes common to each entry, where each entry corresponds to an individual. A query q is received from a querying entity query q and is passed to the database, and an answer a is received in response. An amount of noise e is generated and added to the answer a to result in an obscured answer o, and the obscured answer o is returned to the querying entity. Thus, a level of protection of privacy is provided to each individual represented within the database.
Owner:MICROSOFT TECH LICENSING LLC
Detecting media areas likely of hosting watermarks
ActiveUS8301893B2Level of protectionEasy to useAcutation objectsPaper-money testing devicesPattern recognitionDigital data
The present invention relates generally to digital watermarking and steganographic encoding. One claim recites a method including: receiving data corresponding to at least a portion of digital data; separating the data into a plurality of portions; determining a measure relative to a predetermined measure for each of the portions, wherein the measure comprises a measure related to a predetermined digital watermark signal; based at least in part on the measure, identifying which out of the plurality of portions are likely to host digital watermarking therein. Of course, other combinations are provided as well.
Owner:DIGIMARC CORP
Method and apparatus for content protection within an open architecture system
ActiveUS20080148063A1Level of protectionProtected contentTelevision system detailsPulse modulation television signal transmissionGraphicsDigital video
In a class of embodiments, the invention is an open computing system (e.g., a PC) in which a protected, closed subsystem is embedded. The closed subsystem typically includes multiple parts that ensure that content protection keys and protected content are never revealed outside the closed subsystem. Content (e.g., high-definition digital video) that enters the closed subsystem (and is typically decrypted and re-encrypted within the closed subsystem) is afforded a similar level of protection within the open system as can be obtained in standalone closed systems. Other aspects of the invention are methods for protecting content within an open computing system, a closed system (or disk drive thereof) configured to be embedded in an open computing system, and circuitry configured to be embedded in an open computing system for combining the output of a closed subsystem with other output (e.g., graphics and / or audio output) of the open computing system.
Owner:OPTIMUM CONTENT PROTECTION
Private clustering and statistical queries while analyzing a large database
ActiveUS20060200431A1Level of protectionData processing applicationsDigital data information retrievalKernel principal component analysisNoise generation
A database has a plurality of entries and a plurality of attributes common to each entry, where each entry corresponds to an individual. A query is received from a querying entity query and is passed to the database, and an answer is received in response. An amount of noise is generated and added to the answer to result in an obscured answer, and the obscured answer is returned to the querying entity. The noise is normally distributed around zero with a particular variance. The variance R may be determined in accordance with R>8 T log2(T / δ) / ε2, where T is the permitted number of queries T, δ is the utter failure probability, and ε is the largest admissible increase in confidence. Thus, a level of protection of privacy is provided to each individual represented within the database. Example noise generation techniques, systems, and methods may be used for privacy preservation in such areas as k means, principal component analysis, statistical query learning models, and perceptron algorithms.
Owner:MICROSOFT TECH LICENSING LLC
Securable cover apparatus for trade show booths
Owner:BOOTHSEAL
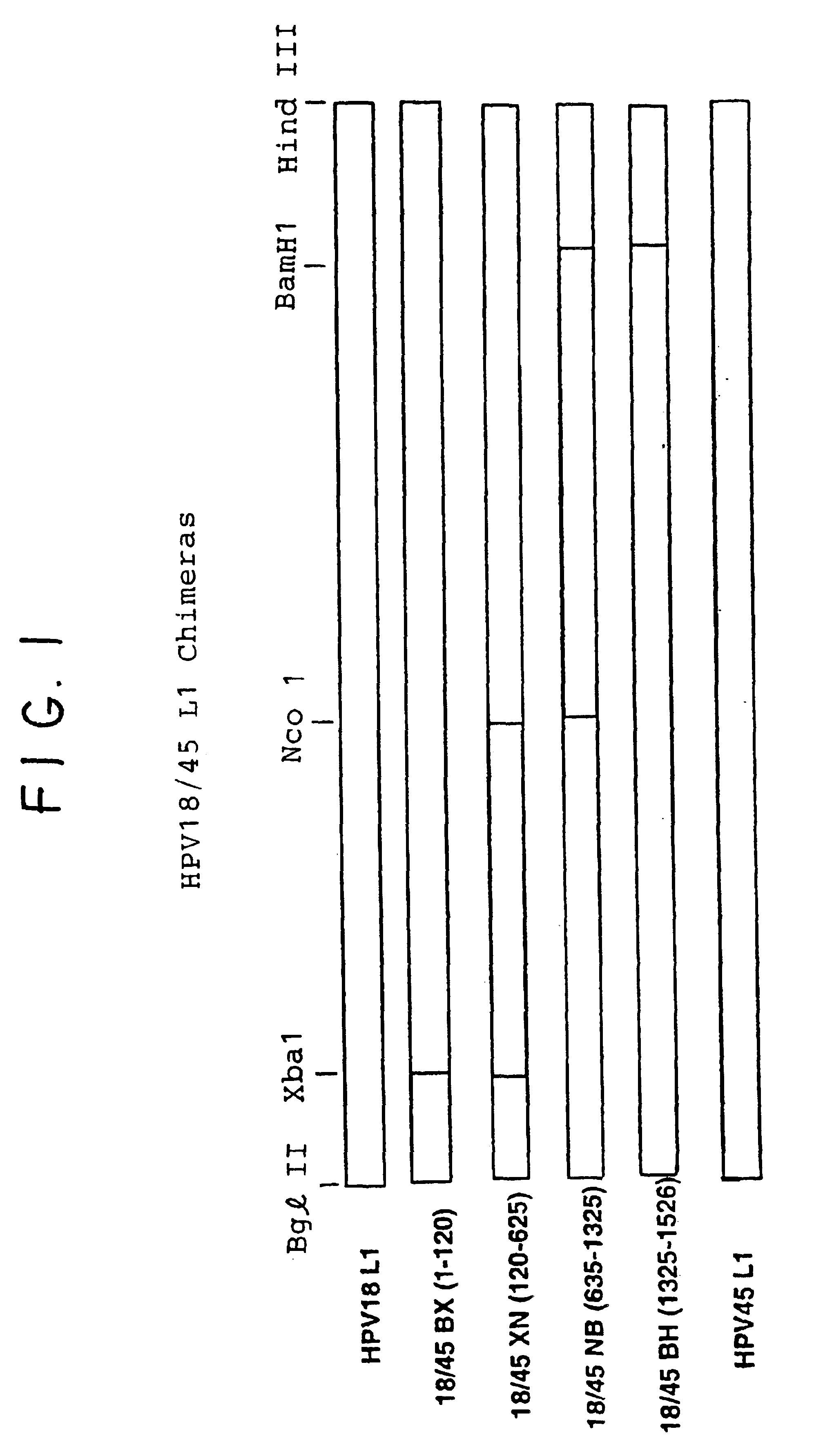
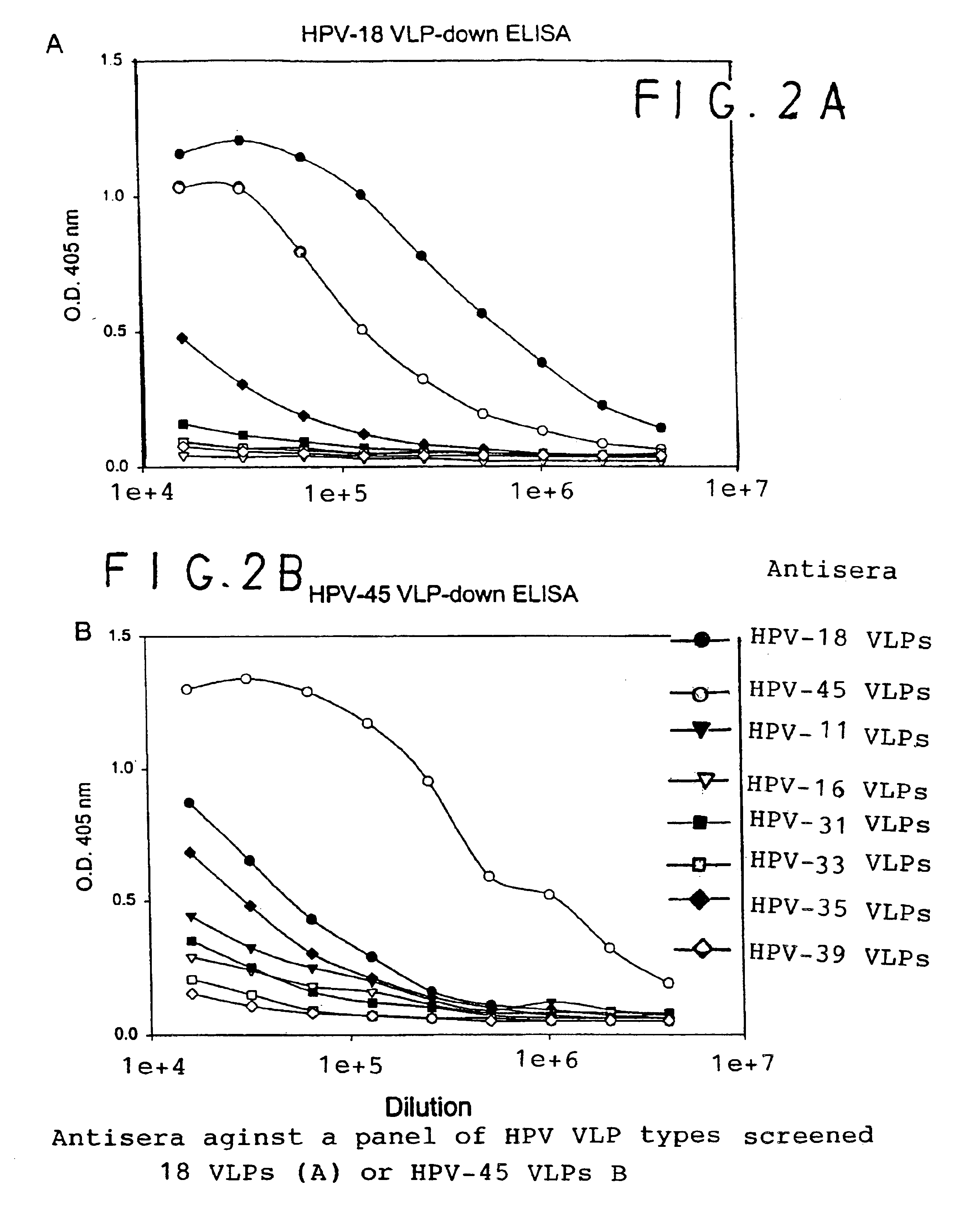
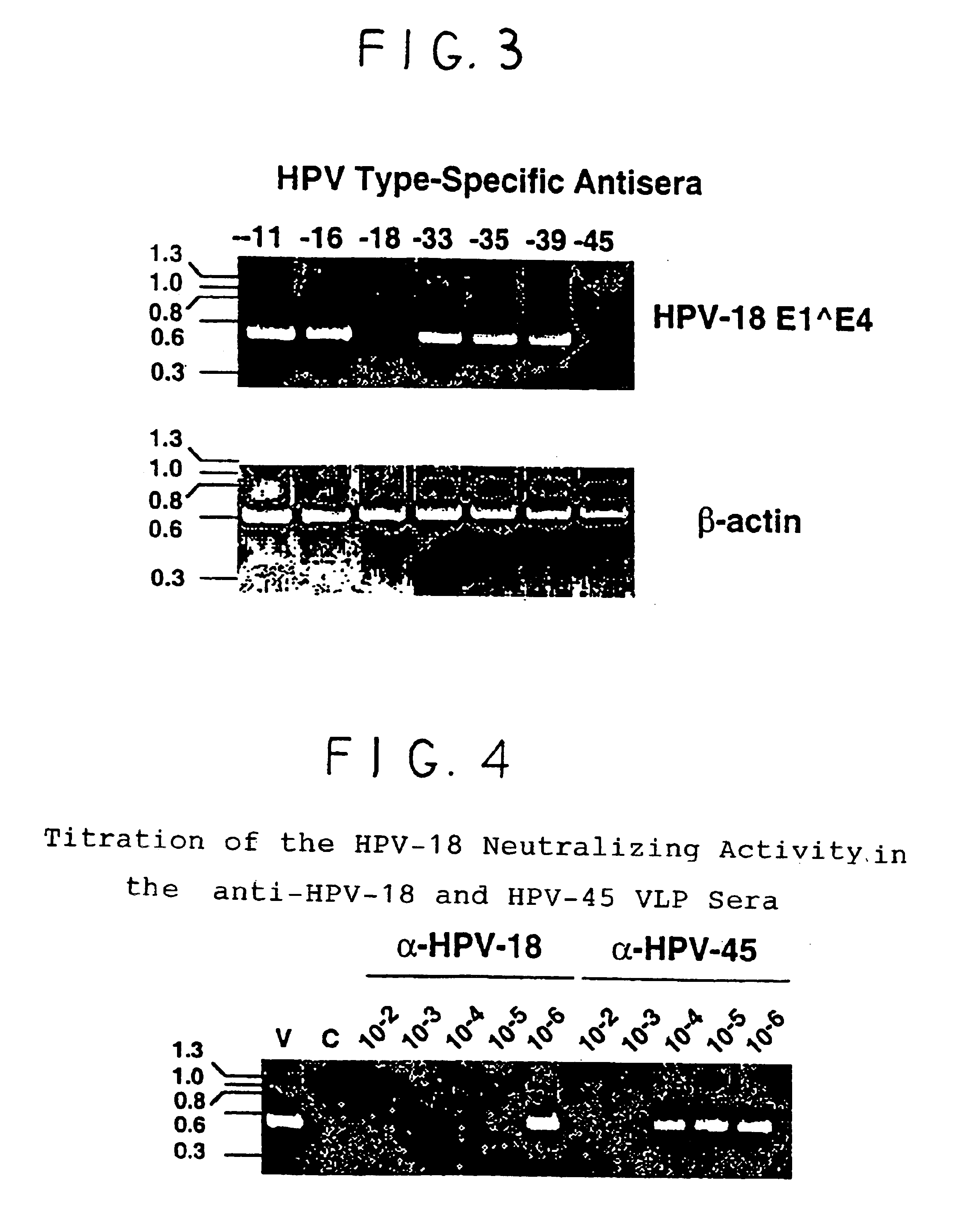
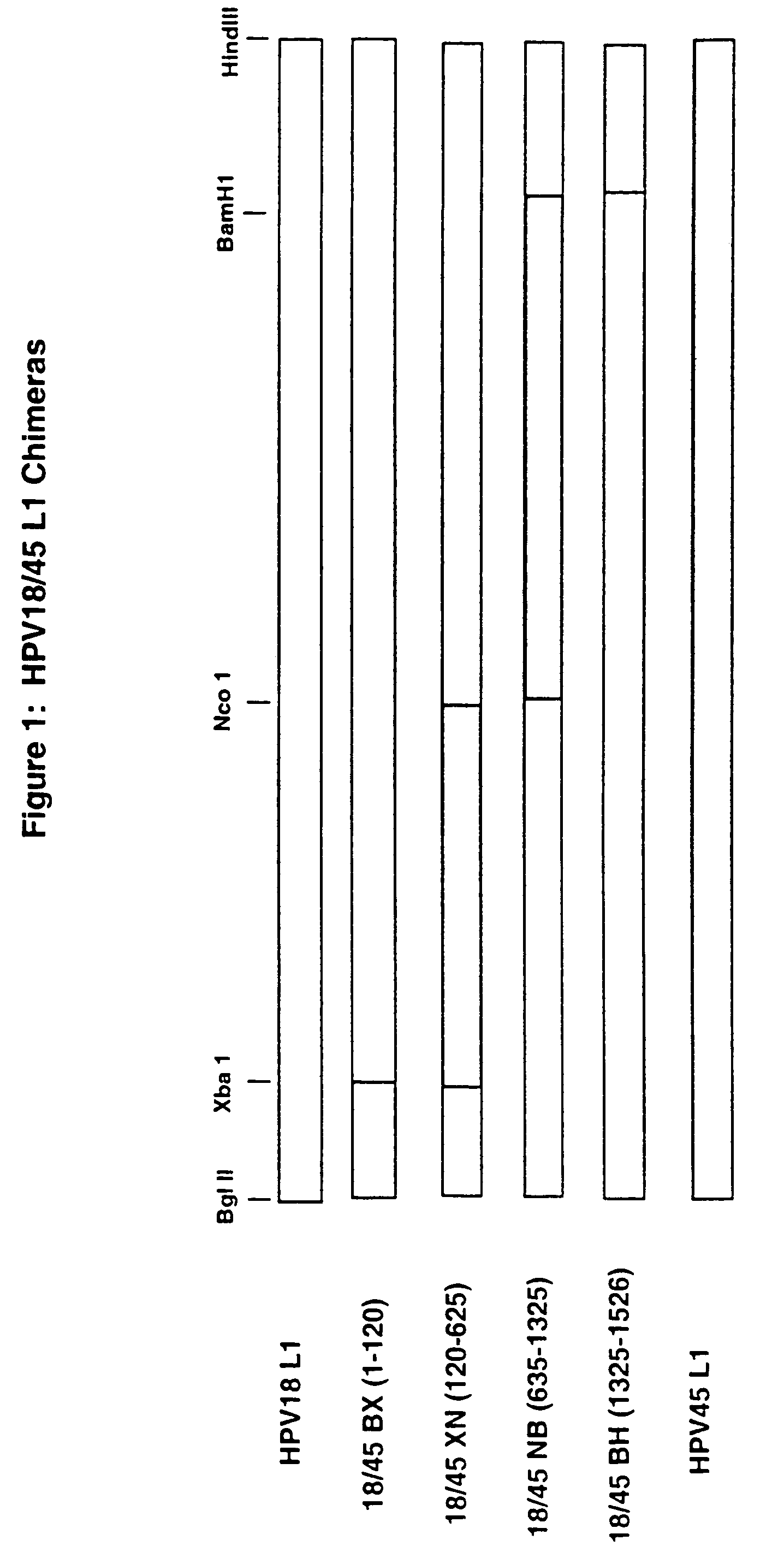
Chimeric human papillomavirus (HPV) L1 molecules and uses therefor
InactiveUS6908613B2Need can be quite largeLevel of protectionPeptide/protein ingredientsAntibody mimetics/scaffoldsHuman papillomavirusVirus-like particle
Owner:MEDIMMUNE LLC
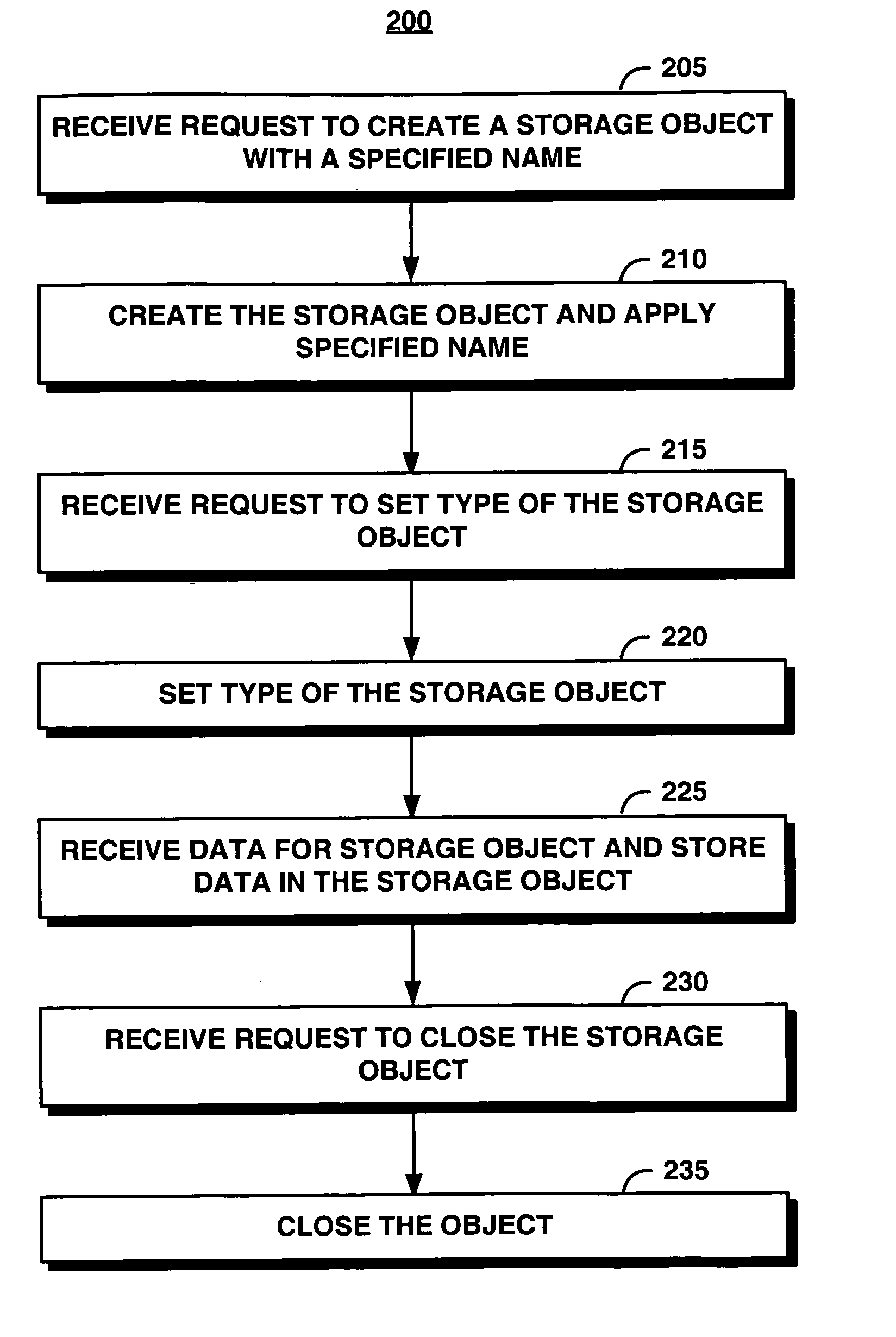
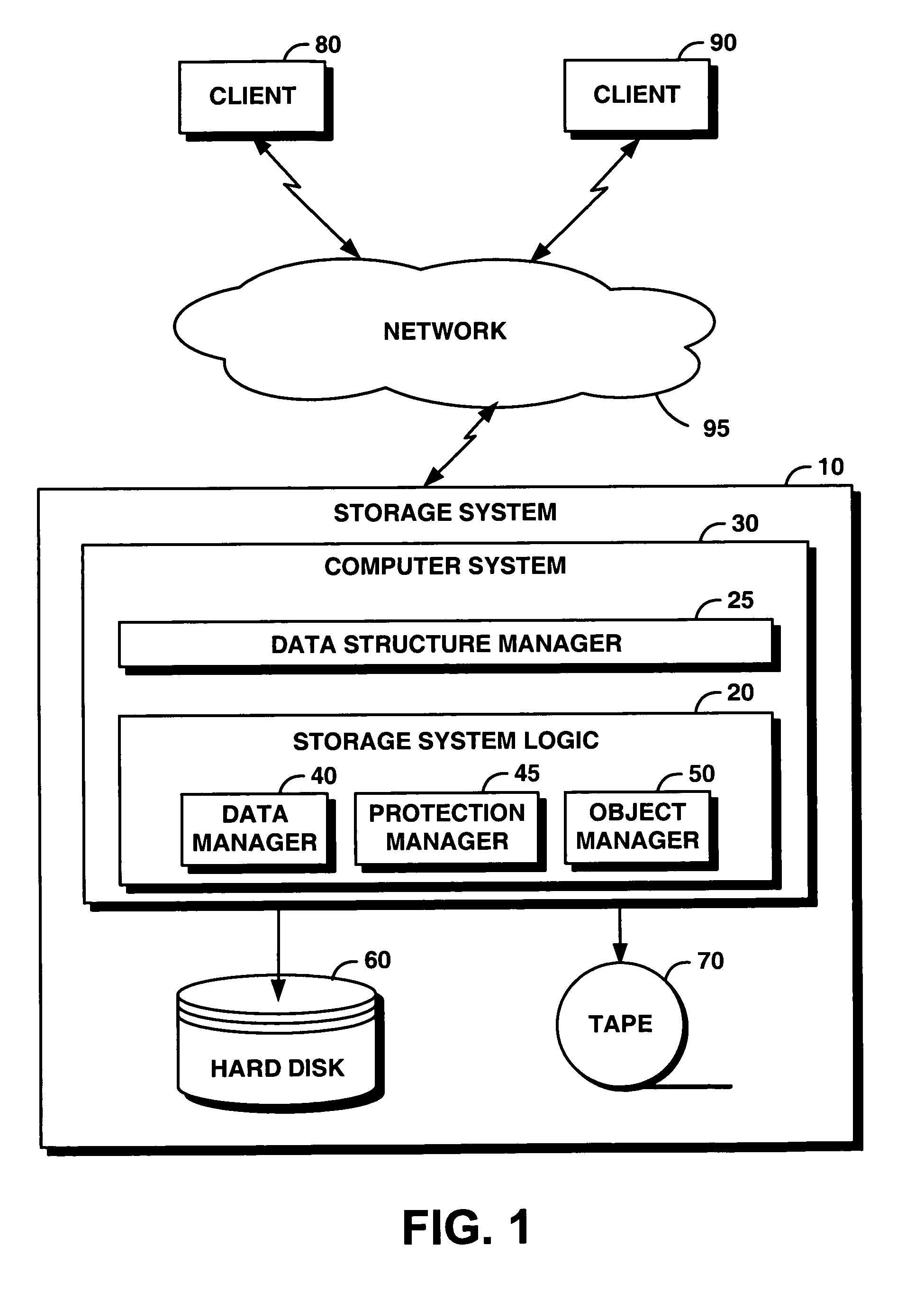
System and method for providing an object to support data structures in worm storage
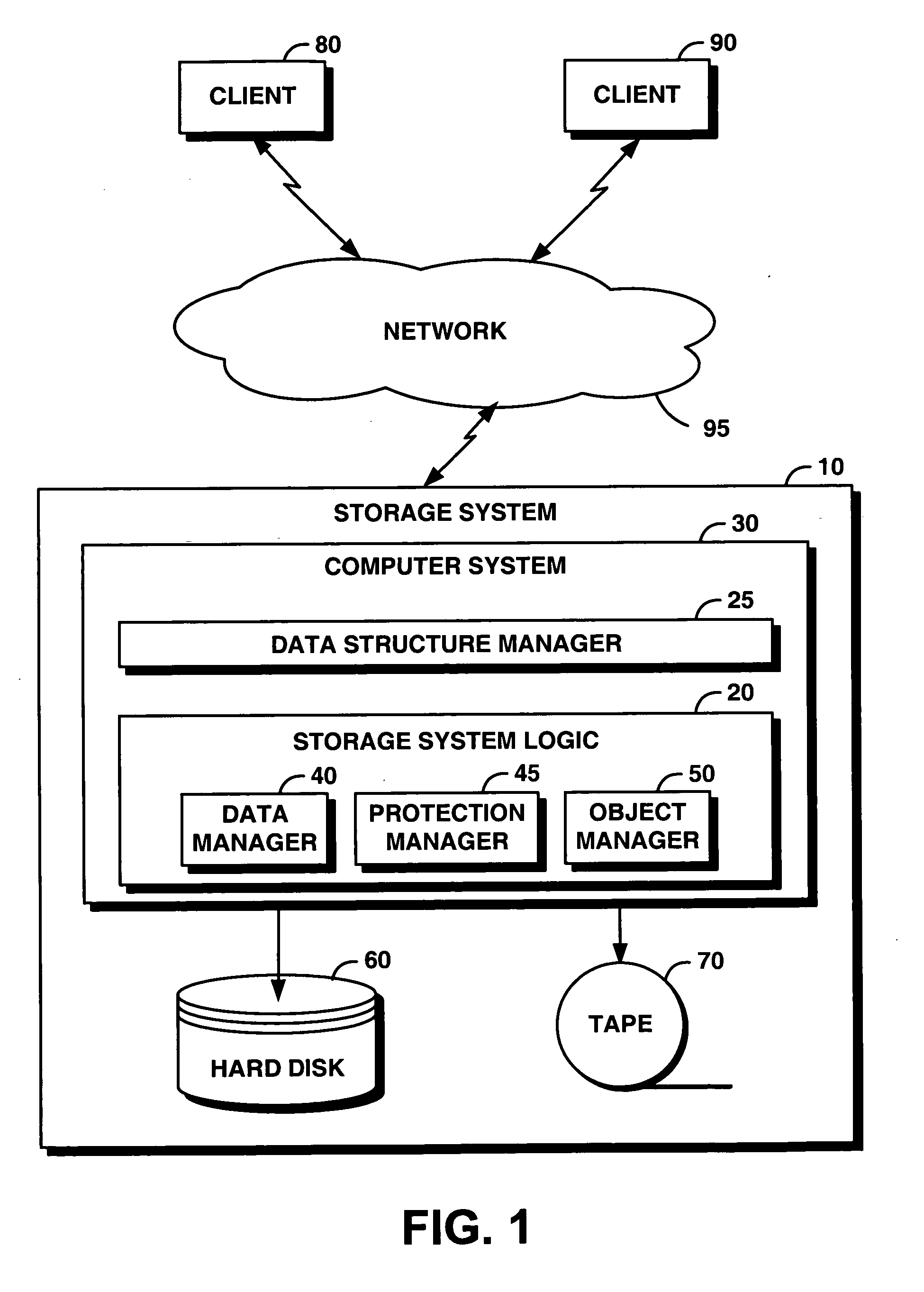
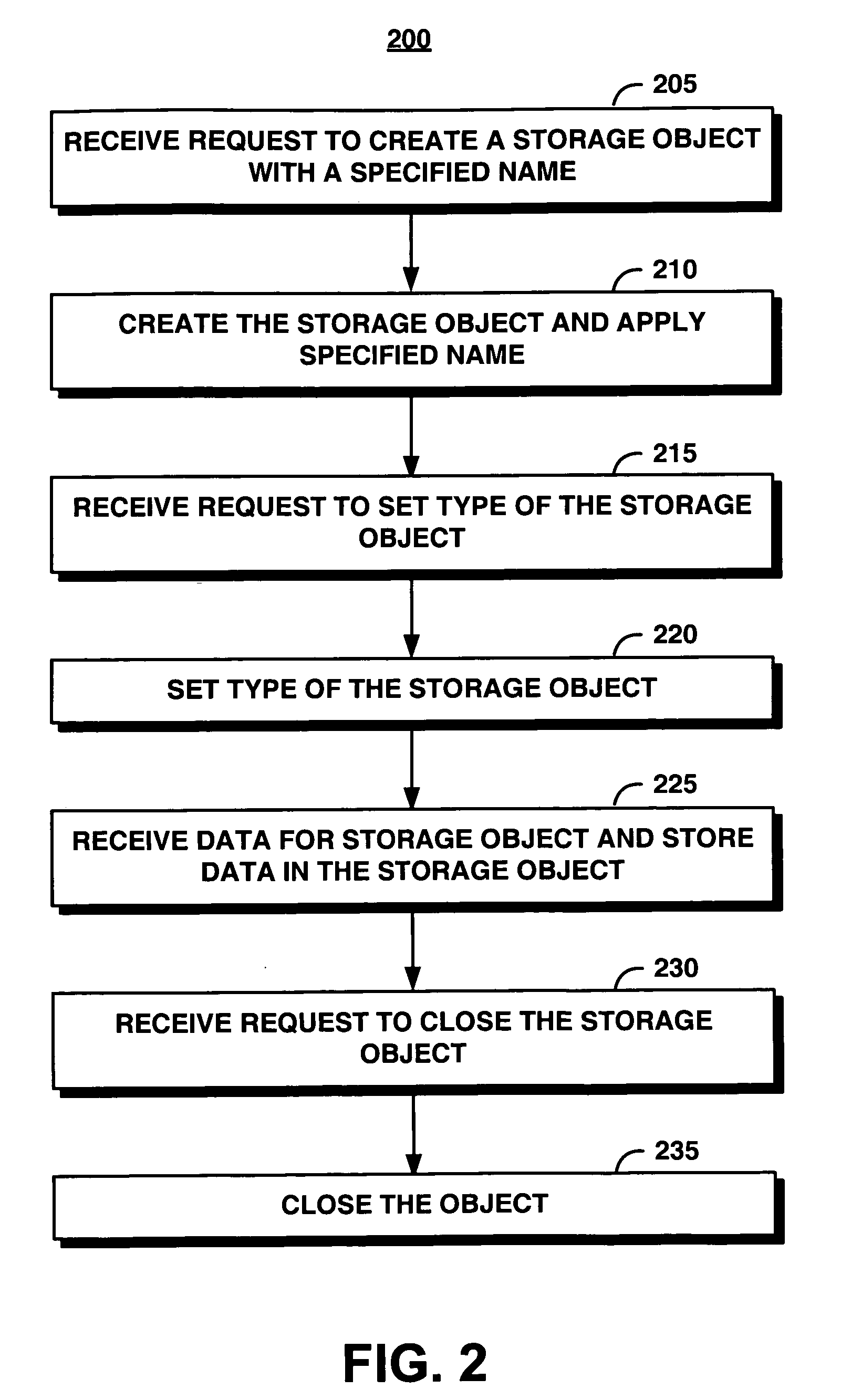
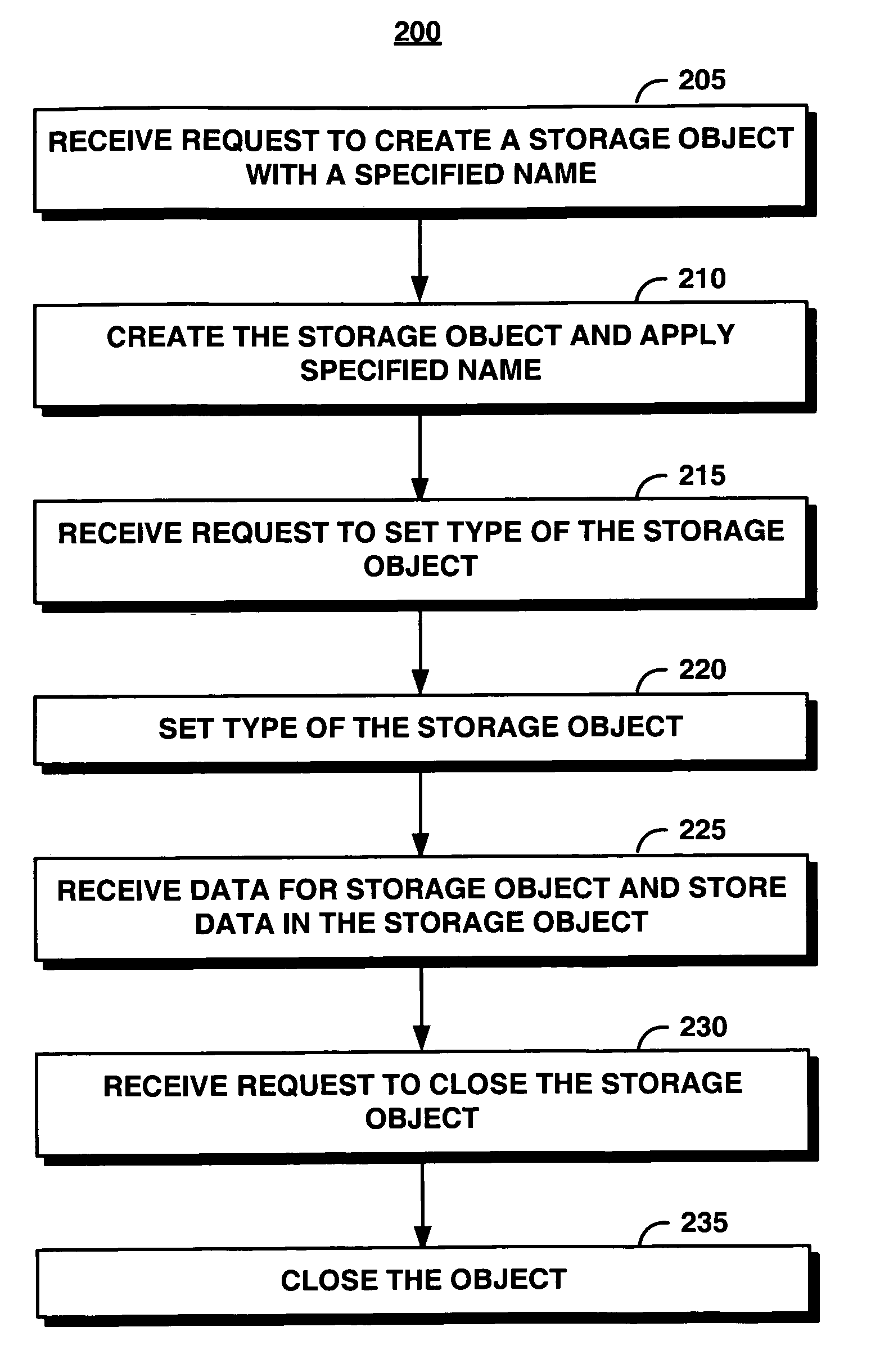
InactiveUS20070078890A1Level of protectionSupporting structureData processing applicationsComputer security arrangementsObject storageObject system
An object storage system provides a storage object to support index structures, logs, and audit trails in WORM storage. The storage object includes a mutable object, an immutable object, or an appendable object. For each storage object, the system maintains an indication of type, such as mutable, immutable, or appendable object type. A mutable object can be arbitrarily modified, an immutable object cannot be modified, and the contents of the appendable object cannot be modified but can be appended with new data. Appended data becomes immutable. The system enables a protection level represented by the object type to be upgraded but not downgraded. Consequently, data committed to be immutable cannot be changed by changing the type of the storage object.
Owner:IBM CORP
Securable cover apparatus for trade show booths
Owner:BOOTHSEAL
Inventory management system and methods for secure identification document issuance
InactiveUS20050156035A1Improve security levelUltimate in durabilityHand manipulated computer devicesPayment architectureDocument preparationDocumentation
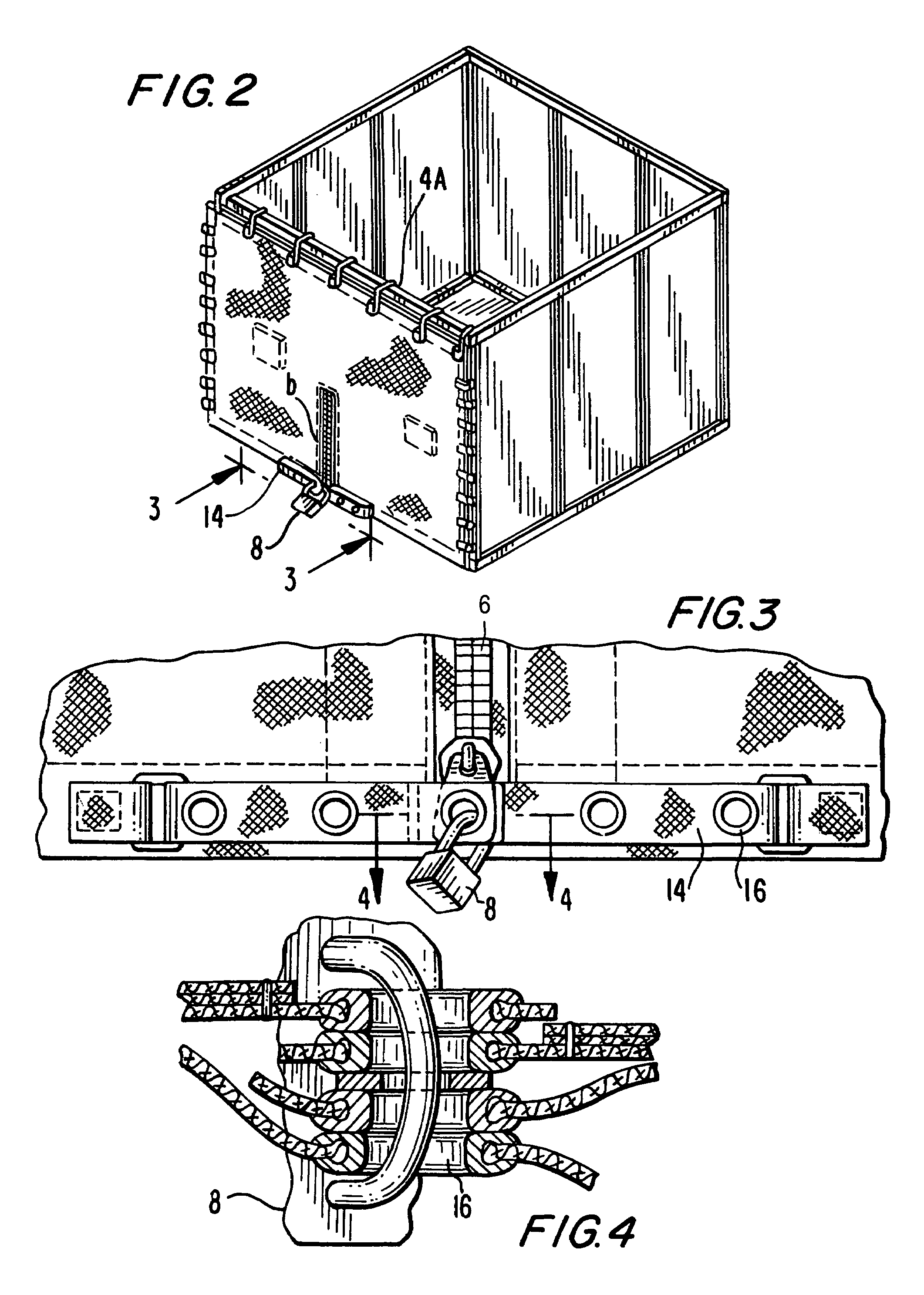
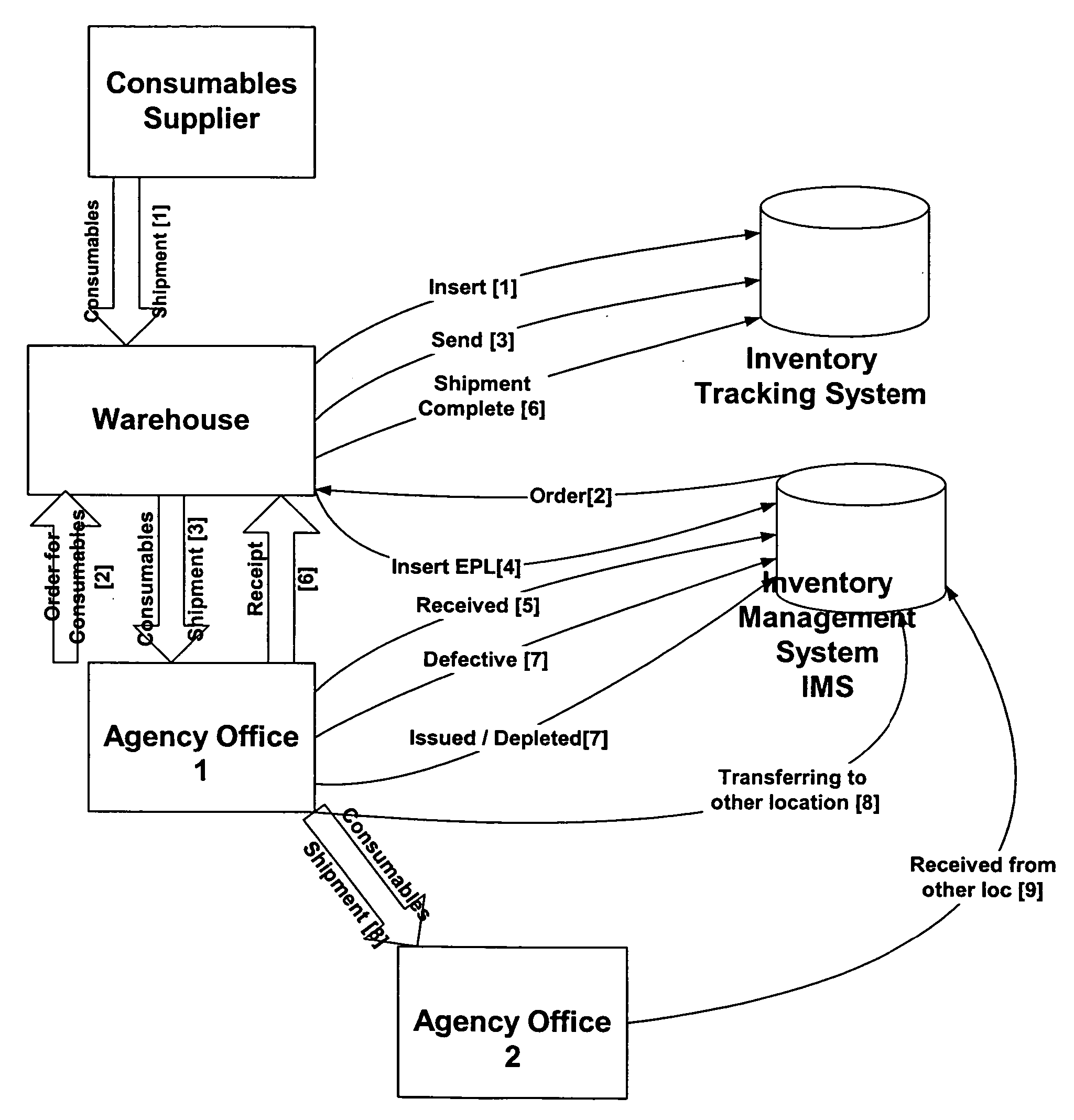
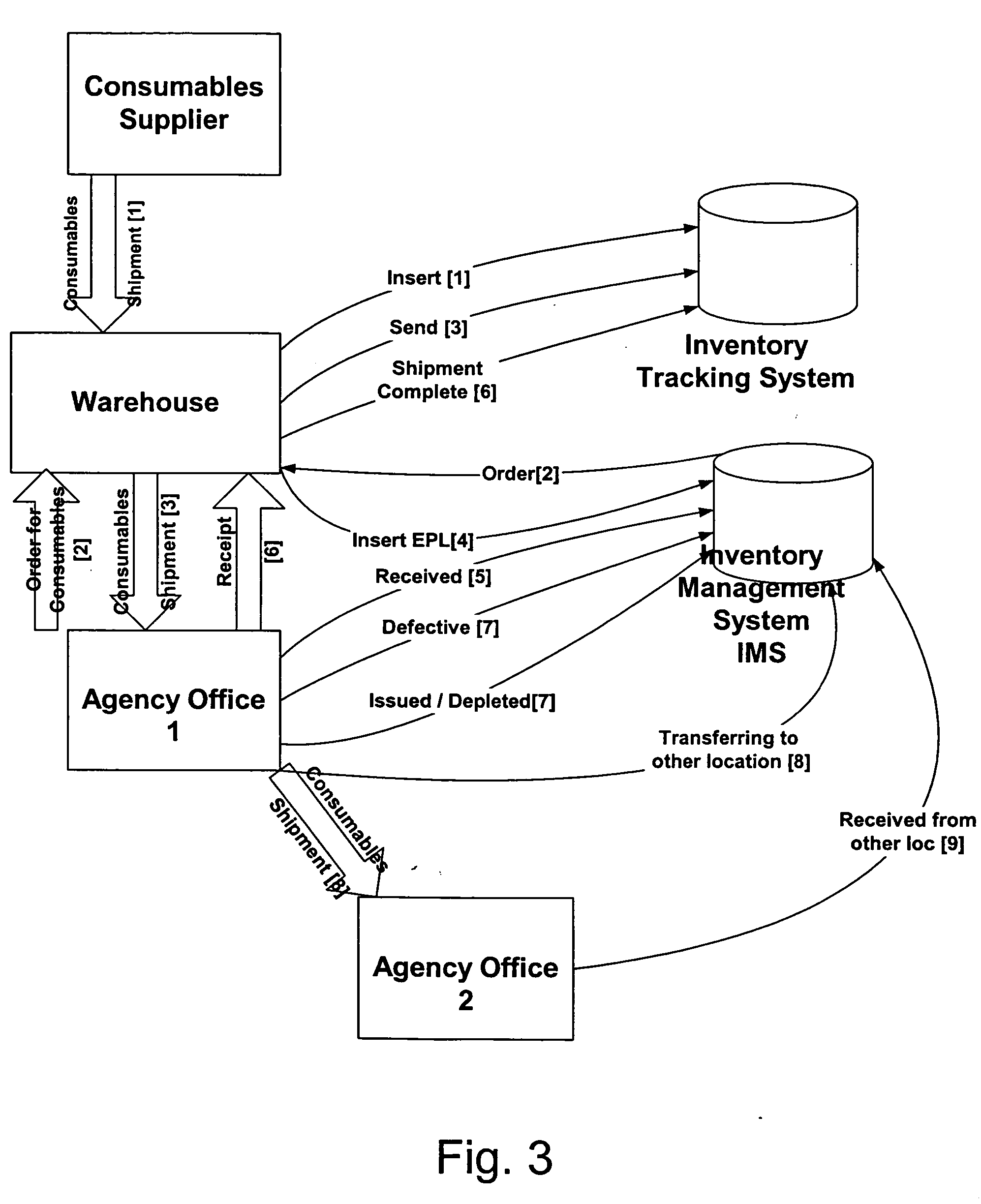
An inventory management system tracks consumables used in creation of secure documents through an identification document issuance process. The system assigns states to card and non-card consumables, and these states are used to track consumables from the vendor's inventory to the issuer's inventory. The system includes functions for managing inventory, shipping and receiving, use management, inventory auditing and secure material destruction. Electronic packing lists are transmitted between vendor and issuer systems to verify shipments. Embedded identification numbers, carried in machine readable codes on consumables, are used to track consumables through the document creation and issuing process.
Owner:L 1 SECURE CREDENTIALING
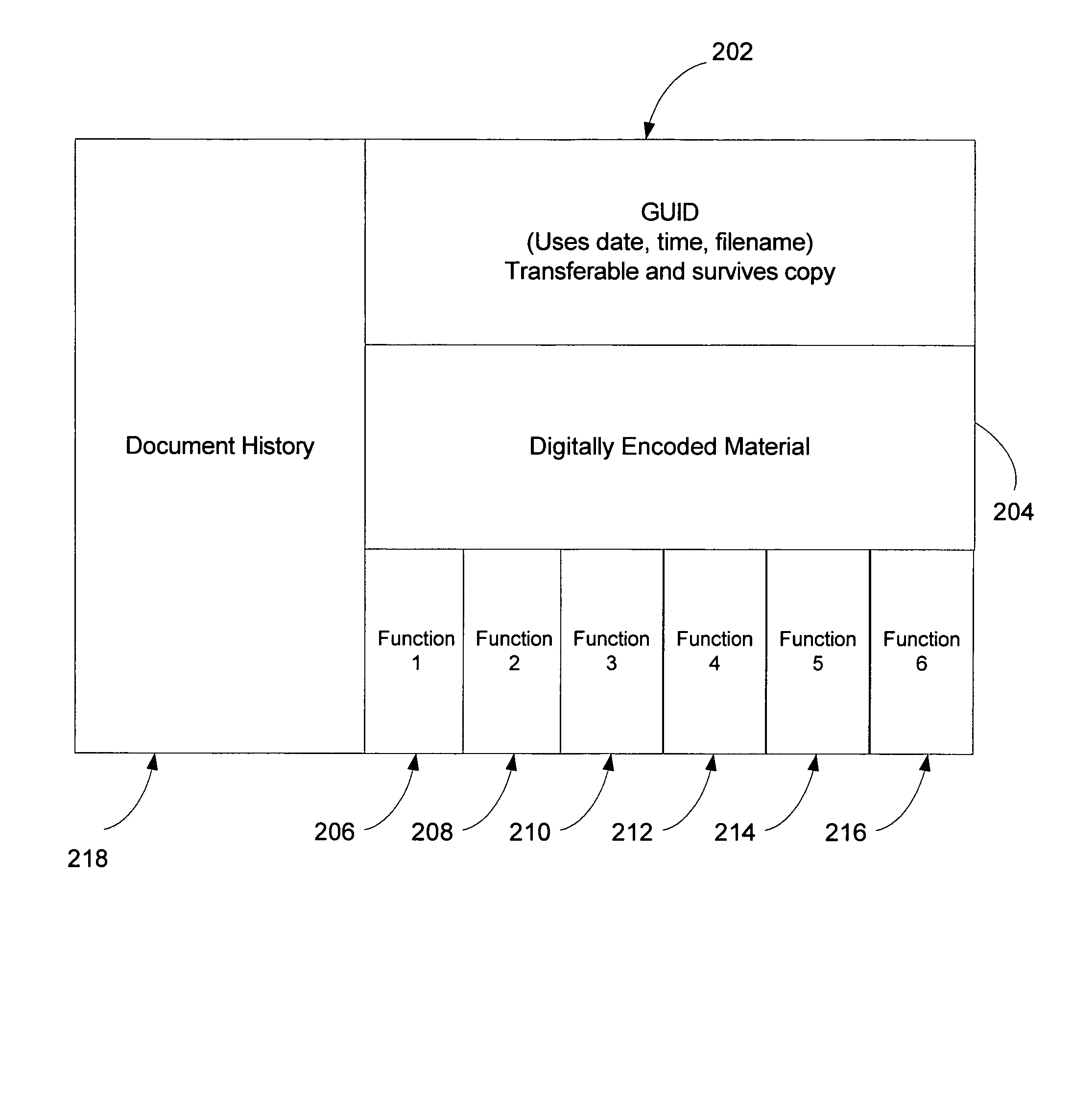
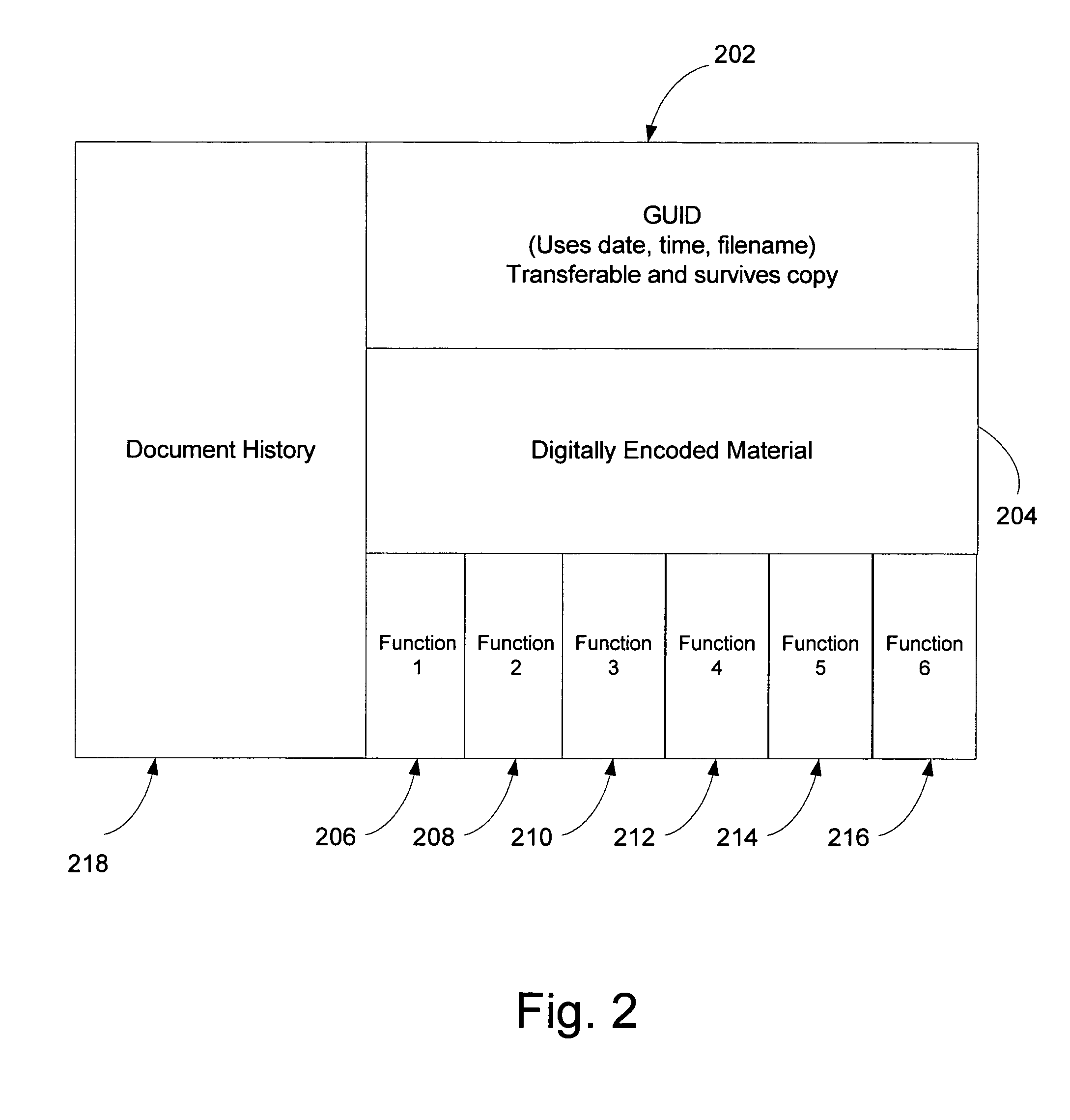
Method for lifetime tracking of intellectual property
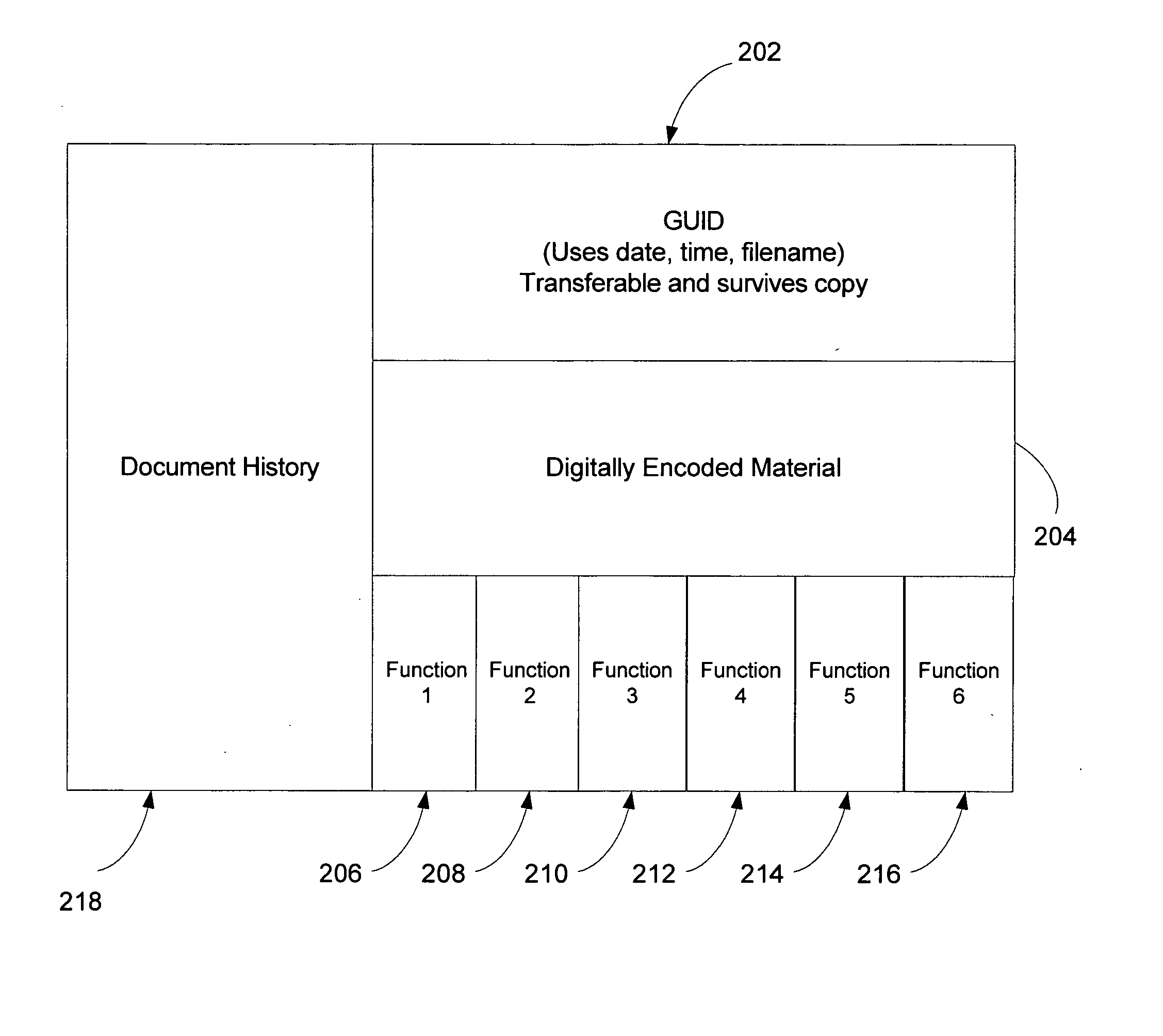
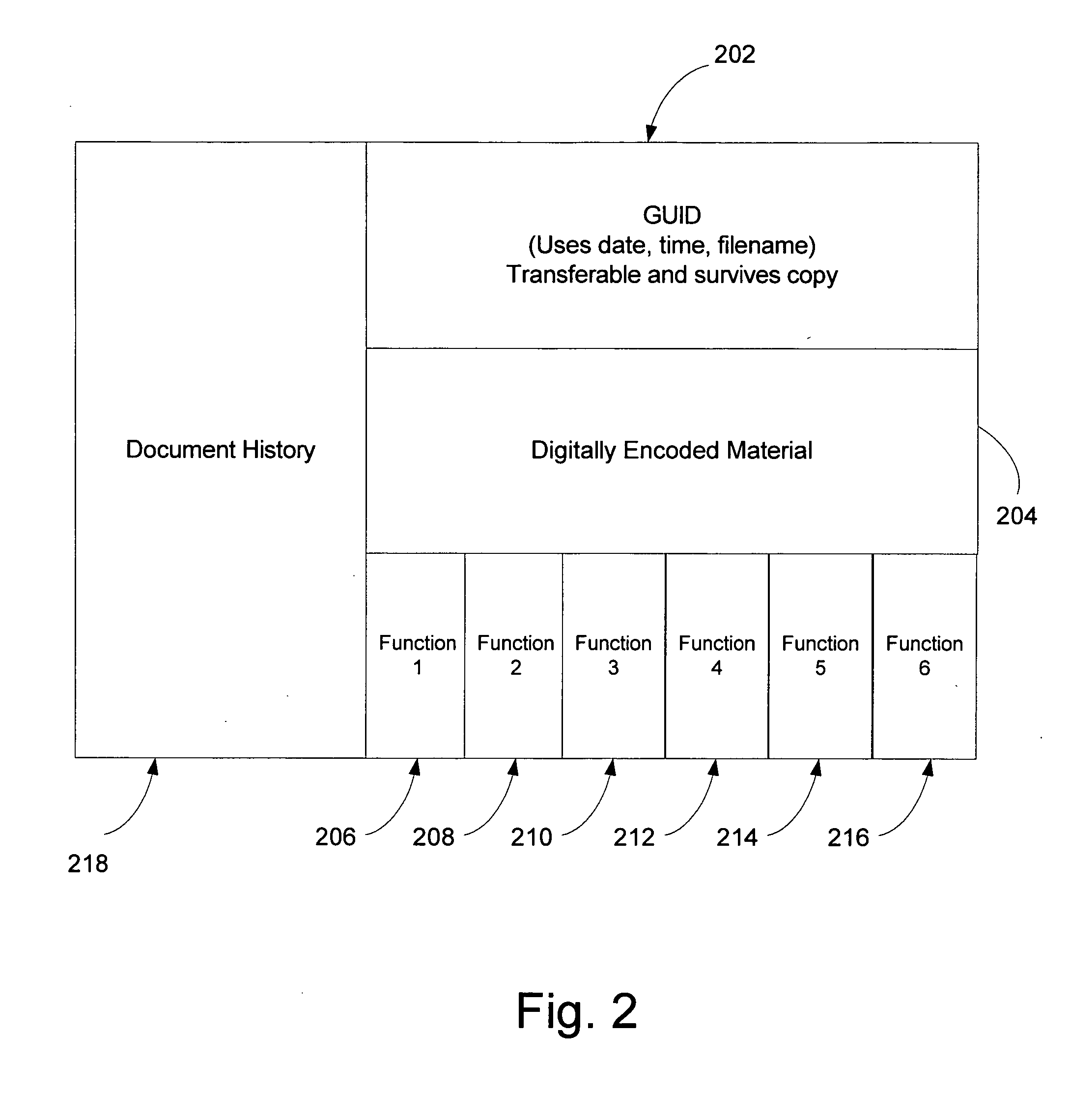
ActiveUS20050125352A1Level of protectionIncrease flexibilityDigital data processing detailsAnalogue secracy/subscription systemsOperational systemIntellectual property
A method of storing and tracking digitally-encoded material includes associating a unique identifier with the digitally-encoded material, associating one or more built-in functions with the digitally-encoded material so that the unique identifier and the built-in functions are coupled to the digitally-encoded material. The built-in functions can govern transforms and rendering of the digitally-encoded material. The tracking is performed by associating a history of the digitally-encoded material with the digitally-encoded material. The history can be associated with the digitally-encoded material or kept in a database that communicates with the digitally-encoded material via the identifier. The built-in functions enable the digitally-encoded material to be stored in RAM in an encrypted form. A method for tracking can include encrypting a combination including the digitally-encoded material and the unique identifier and appending built-in function source code and the encrypted combination to form an executable entity executable independent of any particular operating system.
Owner:MICROSOFT TECH LICENSING LLC
System and method for providing an object to support data structures in worm storage
InactiveUS7487178B2Level of protectionSupporting structureData processing applicationsComputer security arrangementsArray data structureSystem maintenance
An object storage system provides a storage object to support index structures, logs, and audit trails in WORM storage. The storage object includes a mutable object, an immutable object, or an appendable object. For each storage object, the system maintains an indication of type, such as mutable, immutable, or appendable object type. A mutable object can be arbitrarily modified, an immutable object cannot be modified, and the contents of the appendable object cannot be modified but can be appended with new data. Appended data becomes immutable. The system enables a protection level represented by the object type to be upgraded but not downgraded. Consequently, data committed to be immutable cannot be changed by changing the type of the storage object.
Owner:IBM CORP
Protective disk for dumbbell weights
A disk to be installed on a dumbbell around the middle bar and adjacent the weight at one end to protect the user's hand(s) from contact with the weight. A slot allows the disk to be installed without removing the weights. A cavity on the weight side of the disk provides clearance for the shoulder or collar which hold the weights in position on some dumbbells. The inner surface of the disk is convex while the outer is generally planar to lie flat against the weights.
Owner:SMITHBERG CHRISTOPHER J
Securable cover apparatus for trade show booths
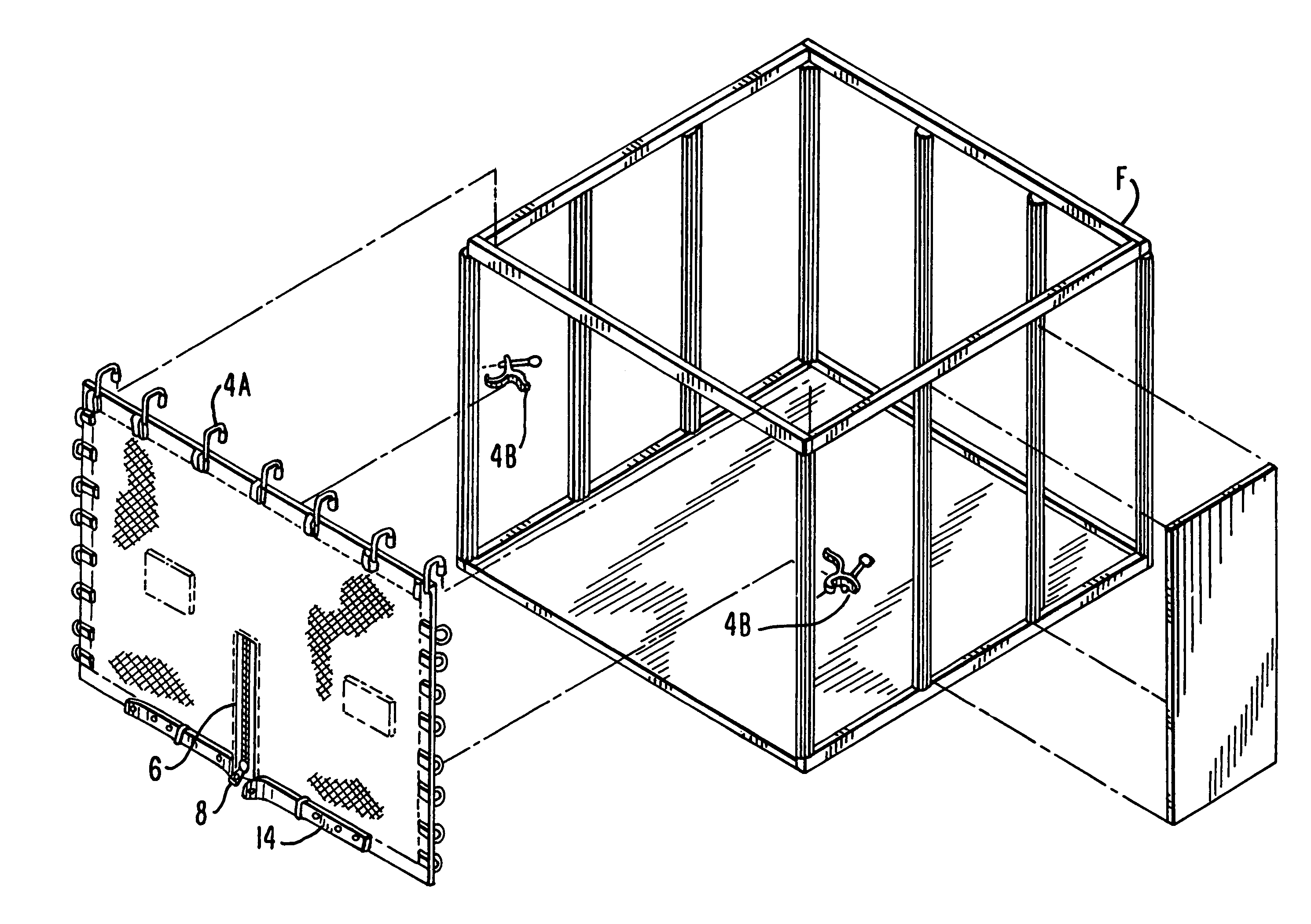
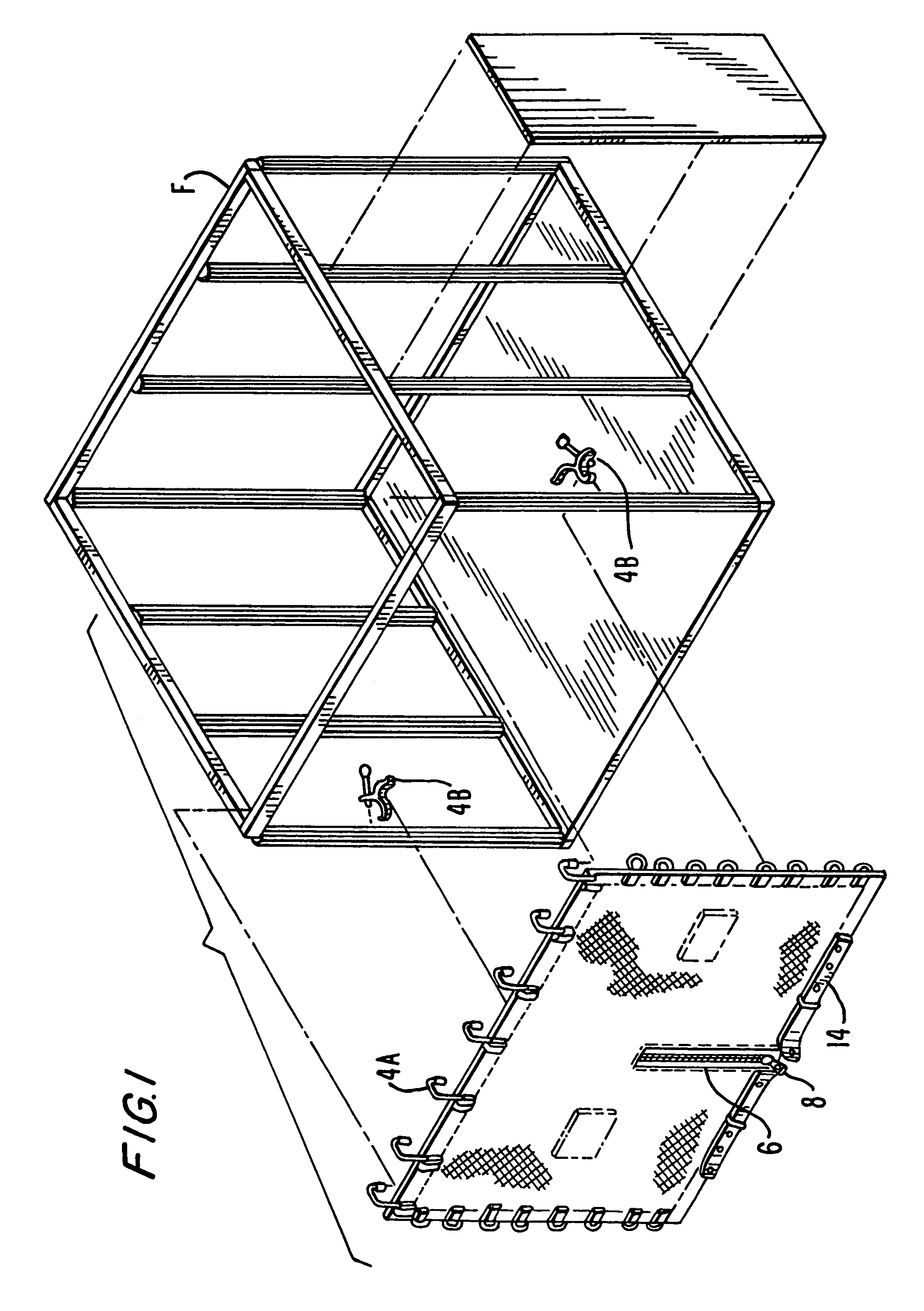
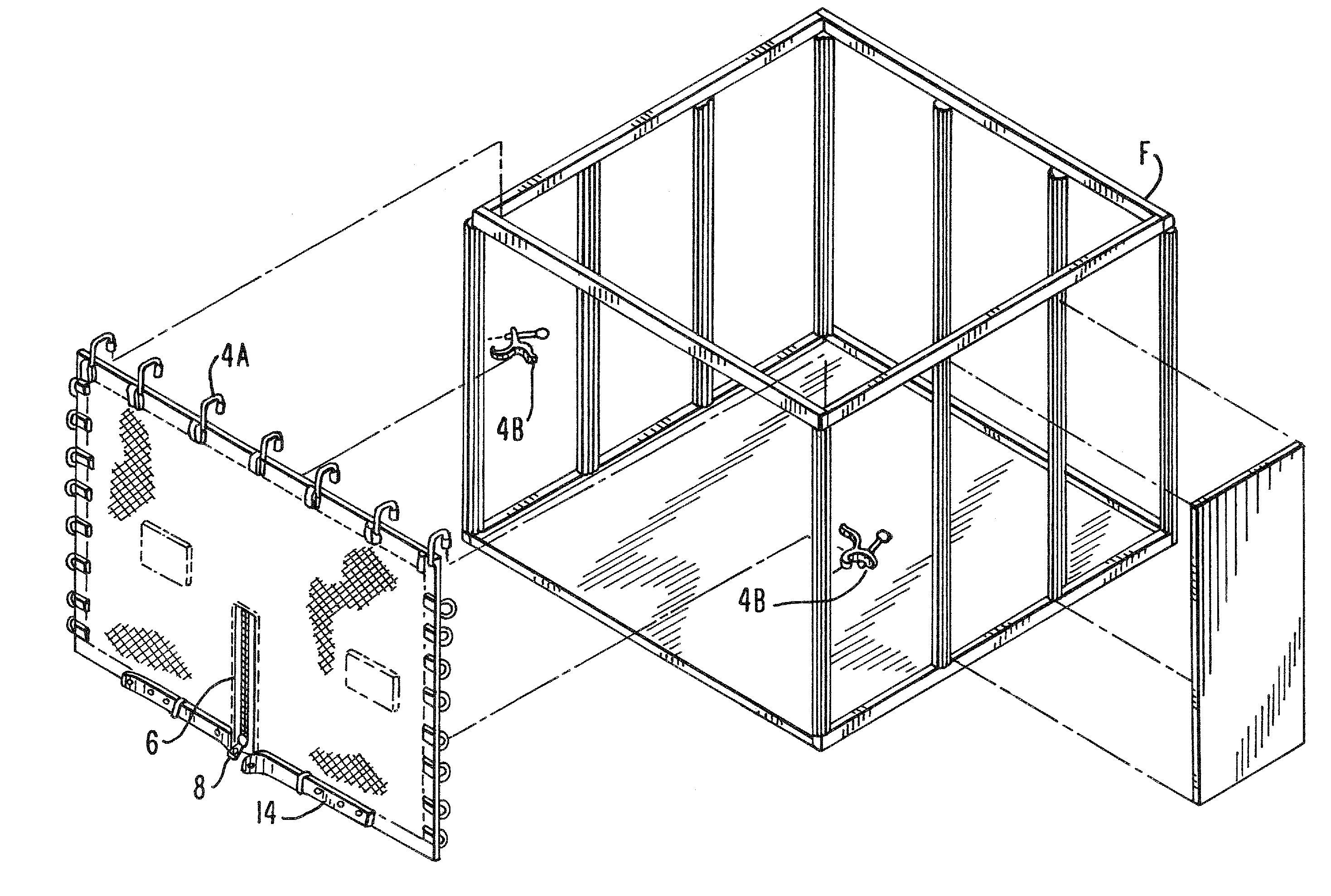
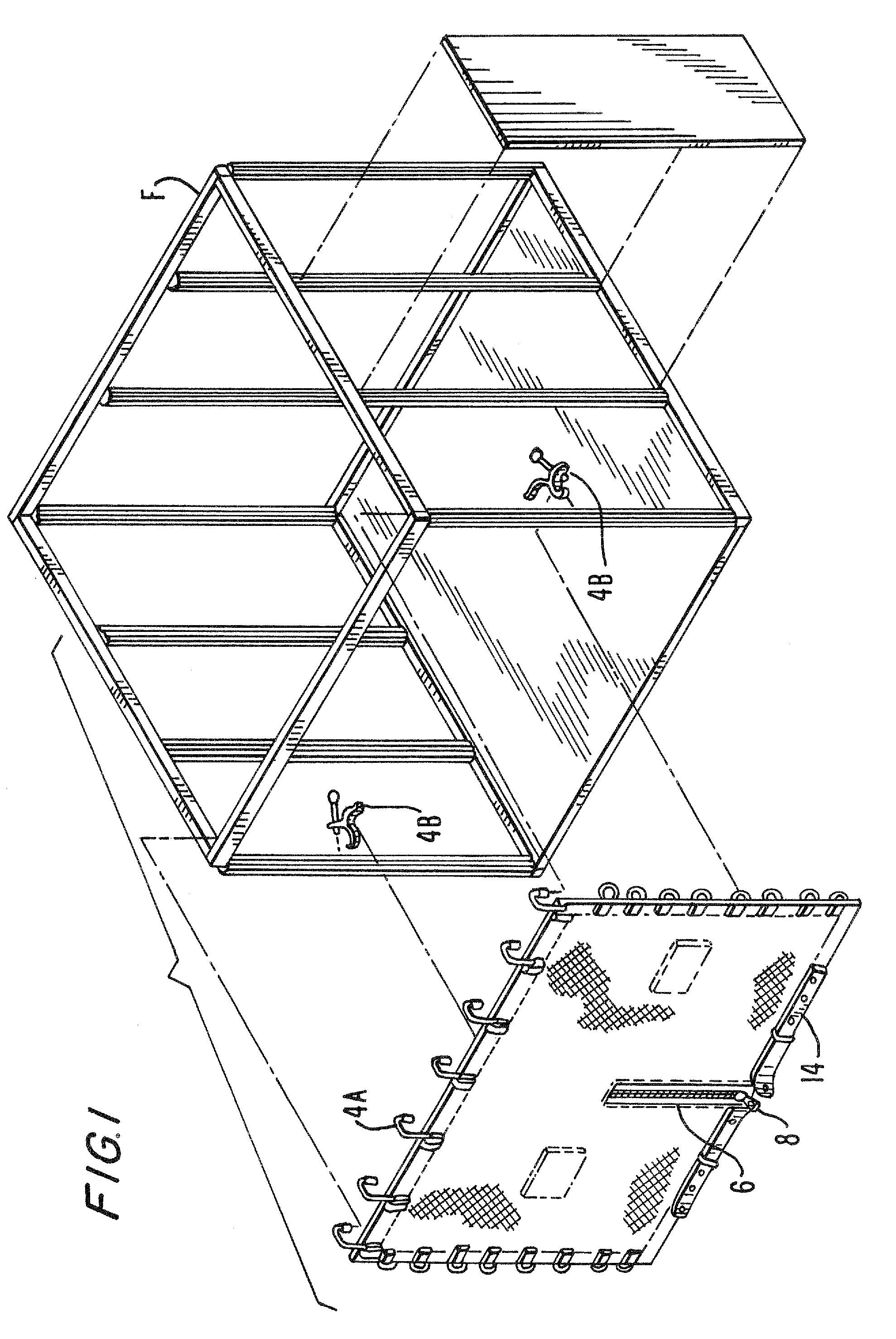
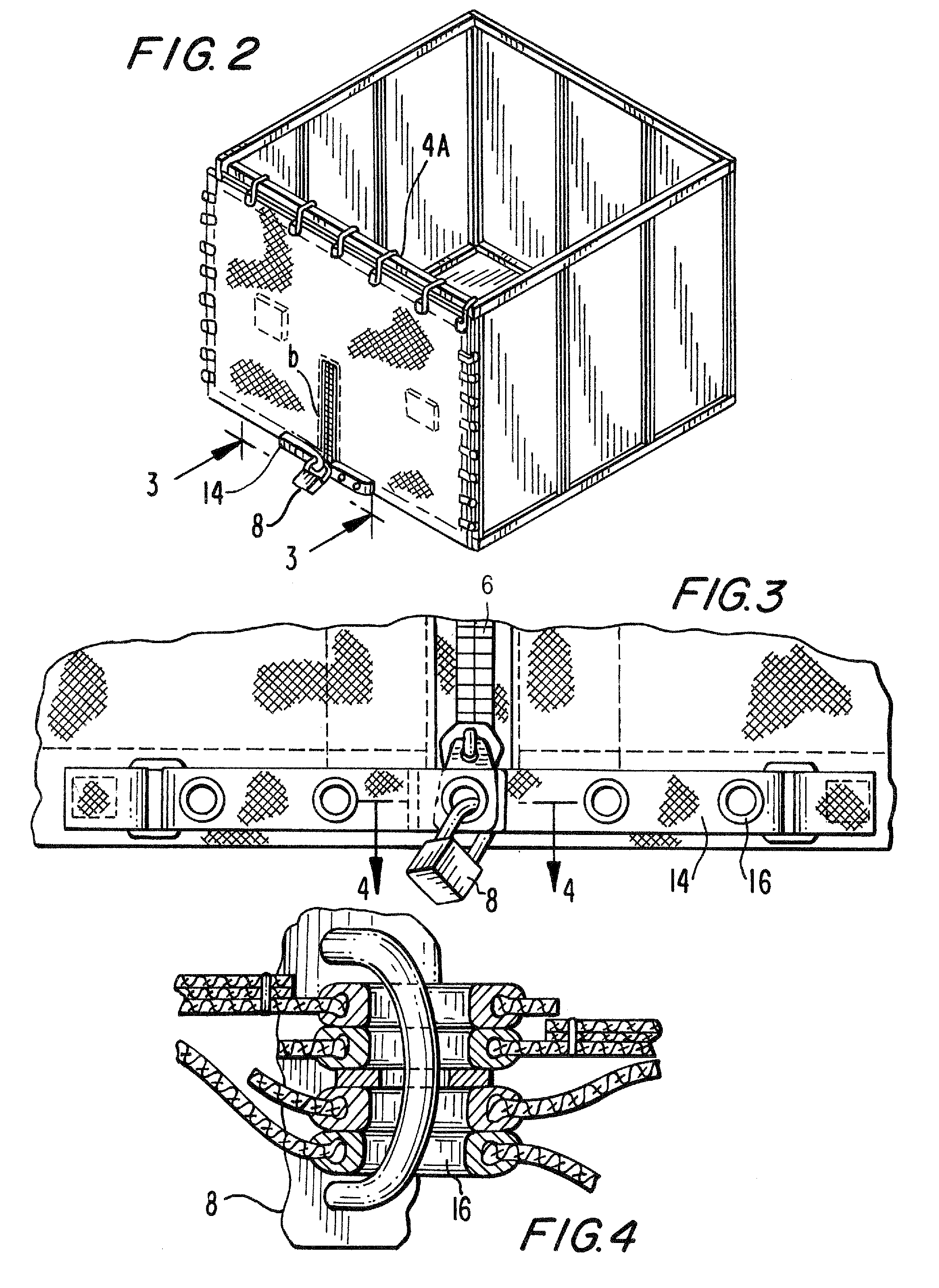
A securable cover apparatus for trade show booths comprising a flexible cover; a fastener mount attached to the flexible cover and a securable fastener having a rotating handle potion and a locking pin that is controlled by the handle portion. The fastener further includes a bracket wall with two guide members that are used to guide the fastener into a channel of the frame of the booth support structure. The securable cover apparatus is able to secure a trade show booth having a frame when the extending guide members of the securable fastener are slid between an opening in the frame and the locking pin is extended and rotated such that the frame of the tradeshow booth is positioned between flanges at the head of the locking pin and the bracket wall.
Owner:BOOTHSEAL
Securable cover apparatus for trade show booths
InactiveUS20100107528A1Level of protectionEasy to installScreensBuilding roofsVertical edgeEngineering
Owner:BOOTHSEAL
Personal care products storage caddy and usage apparatus
InactiveUS20090008270A1Avoid formingLevel of protectionLarge containersOther accessoriesEngineeringPersonal Care Product
Owner:JONES MONICA ANNE
Securable cover apparatus for trade show booths
ActiveUS20130255895A1Level of protectionEasy to installScreensFurniture joining partsEngineeringFlange
A securable cover apparatus for trade show booths comprising a flexible cover; a fastener mount attached to the flexible cover and a securable fastener having a rotating handle potion and a locking pin that is controlled by the handle portion. The fastener further includes a bracket wall with two guide members that are used to guide the fastener into a channel of the frame of the booth support structure. The securable cover apparatus is able to secure a trade show booth having a frame when the extending guide members of the securable fastener are slid between an opening in the frame and the locking pin is extended and rotated such that the frame of the tradeshow booth is positioned between flanges at the head of the locking pin and the bracket wall.
Owner:BOOTHSEAL
Preserving privacy when statistically analyzing a large database
InactiveUS7653615B2Level of protectionComputer security arrangementsSpecial data processing applicationsStatistical analysisPrivacy protection
A database has a plurality of entries and a plurality of attributes common to each entry, where each entry corresponds to an individual. A query q is received from a querying entity query q and is passed to the database, and an answer a is received in response. An amount of noise e is generated and added to the answer a to result in an obscured answer o, and the obscured answer o is returned to the querying entity. Thus, a level of protection of privacy is provided to each individual represented within the database.
Owner:MICROSOFT TECH LICENSING LLC
Method for lifetime tracking of intellectual property
ActiveUS7900260B2Level of protectionIncrease flexibilityDigital data processing detailsAnalogue secracy/subscription systemsOperational systemIntellectual property
A method of storing and tracking digitally-encoded material includes associating a unique identifier with the digitally-encoded material, associating one or more built-in functions with the digitally-encoded material so that the unique identifier and the built-in functions are coupled to the digitally-encoded material. The built-in functions can govern transforms and rendering of the digitally-encoded material. The tracking is performed by associating a history of the digitally-encoded material with the digitally-encoded material. The history can be associated with the digitally-encoded material or kept in a database that communicates with the digitally-encoded material via the identifier. The built-in functions enable the digitally-encoded material to be stored in RAM in an encrypted form. A method for tracking can include encrypting a combination including the digitally-encoded material and the unique identifier and appending built-in function source code and the encrypted combination to form an executable entity executable independent of any particular operating system.
Owner:MICROSOFT TECH LICENSING LLC
Fluorescent substrates for detecting organophosphatase enzyme activity
InactiveUS20070042370A1High sensitivityStrong specificityEsterified saccharide compoundsSugar derivativesHydrogenFluorescence
Disclosed are compounds of the formula (I): wherein R3, R4, R5, R9, and R10 are selected from the group consisting of H and groups or atoms other than H, and R6 and R8 are halo or hydrogen; X1, X2, and X3 are independently O or S; provided that R9 and R10 are not simultaneously H, when all of X1, X2, and X3 are O; and of the formula (II) wherein R11-R14 are selected from the group consisting of H and groups or atoms other than H; X4-X9 are independently O or S; n and m are 0 or 1 but m and n cannot be 0 simultaneously; R15-R24 can be H or any substituent so long as the compound of formula II upon hydrolysis provides a fluorescent compound. These compounds are useful as substrates with high specificity for organophosphatase particularly human paraoxonase and bacterial organophosphorus hydrolase. Also disclosed is a method for detecting and / or measuring the paraoxonase activity in a fluid comprising contacting the fluid with a fluorescent substrate and measuring the fluorescence of the fluorescent product formed.
Owner:AMERICAN NAT RED CROSS
Methods and devices for enforcing network access control utilizing secure packet tagging
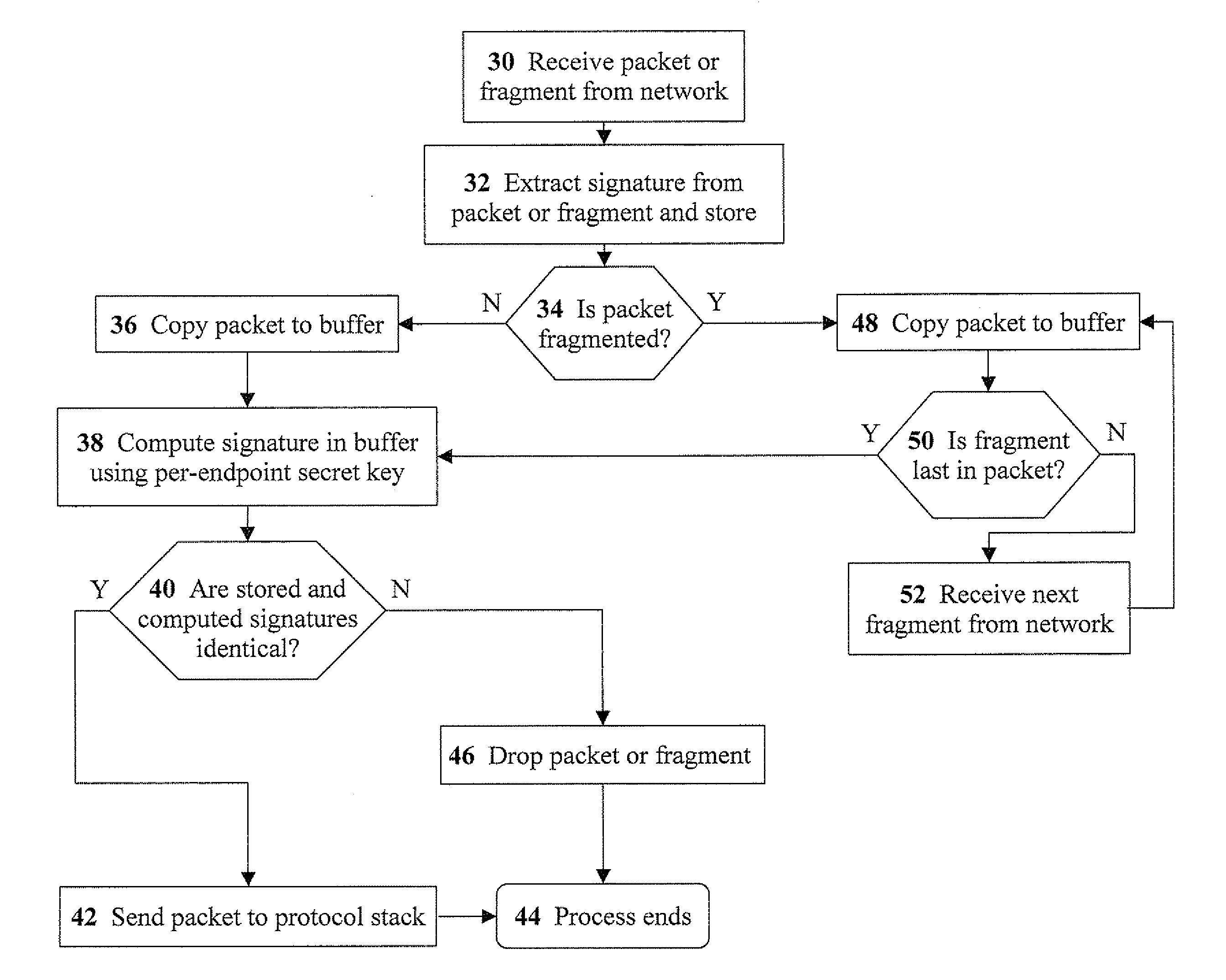
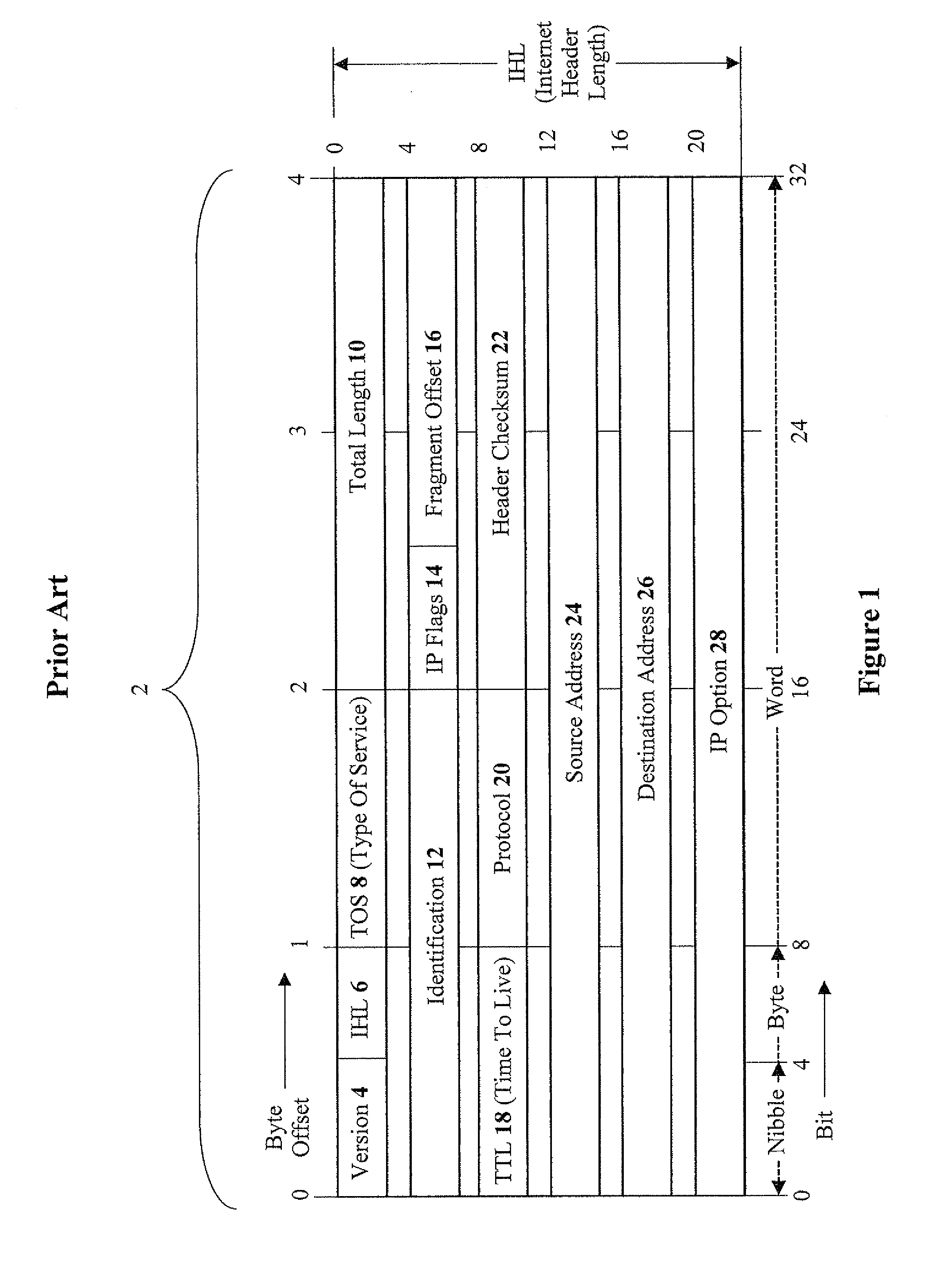
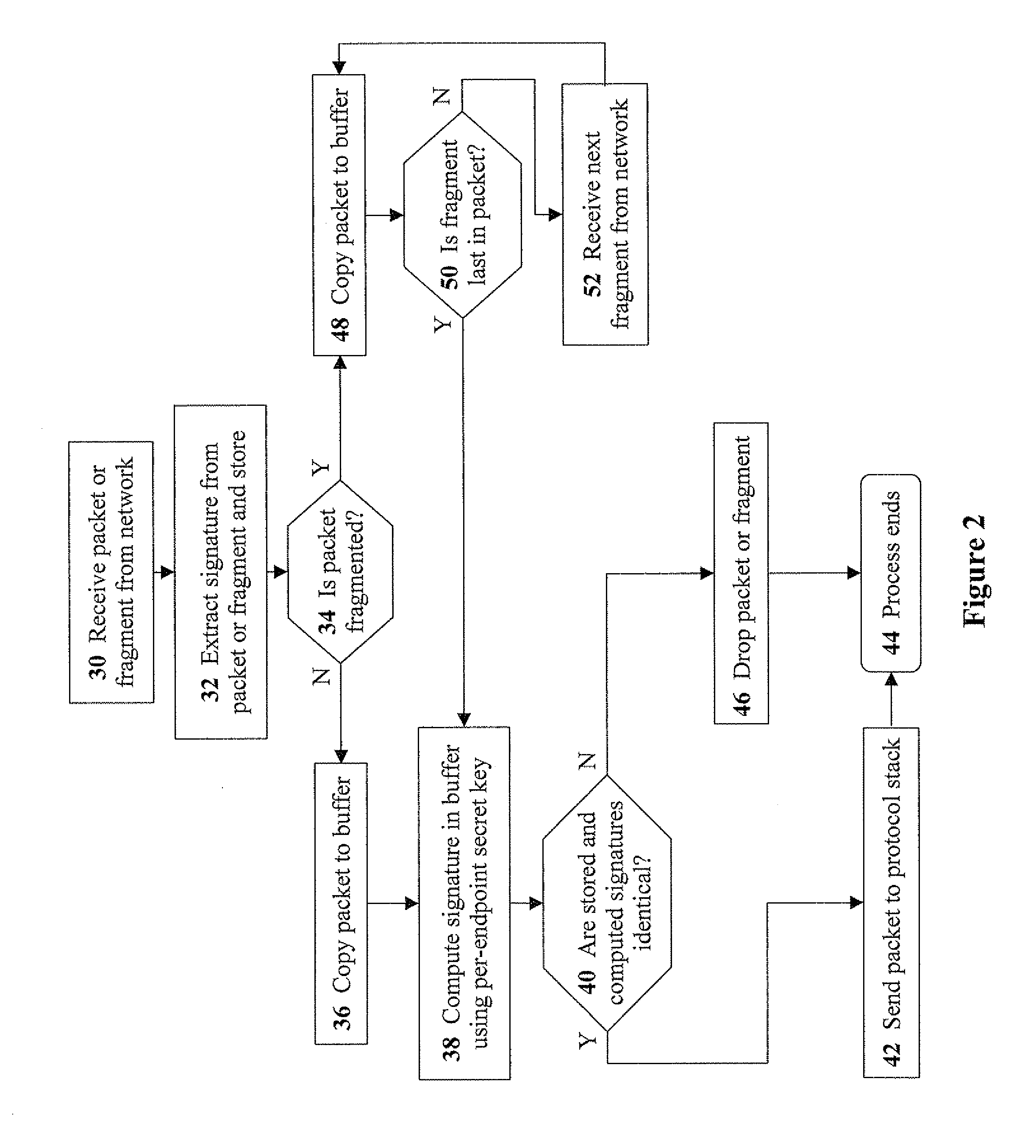
ActiveUS8713666B2Highly-secure packet-signingLevel of protectionMultiple digital computer combinationsProgram controlNetwork Access ControlProtocol stack
Disclosed are methods, devices, and media for enforcing network access control, the method including the steps of: extracting a packet signature from a packet (or packet fragment) received from a network; storing the packet signature and the packet in a buffer; computing a buffer signature using a per-endpoint secret key; determining whether the packet signature and the buffer signature are identical; and upon determining the packet signature and the buffer signature are identical, transmitting the packet to a protocol stack. Preferably, the step of extracting includes extracting the packet signature from a field (e.g. identification field) of a header of the packet. Preferably, the method further includes the step of: upon determining the packet signature and the buffer signature are not identical, discarding the packet. Methods for receiving a packet from a protocol stack, and transmitting the packet to a network are disclosed as well.
Owner:CHECK POINT SOFTWARE TECH LTD
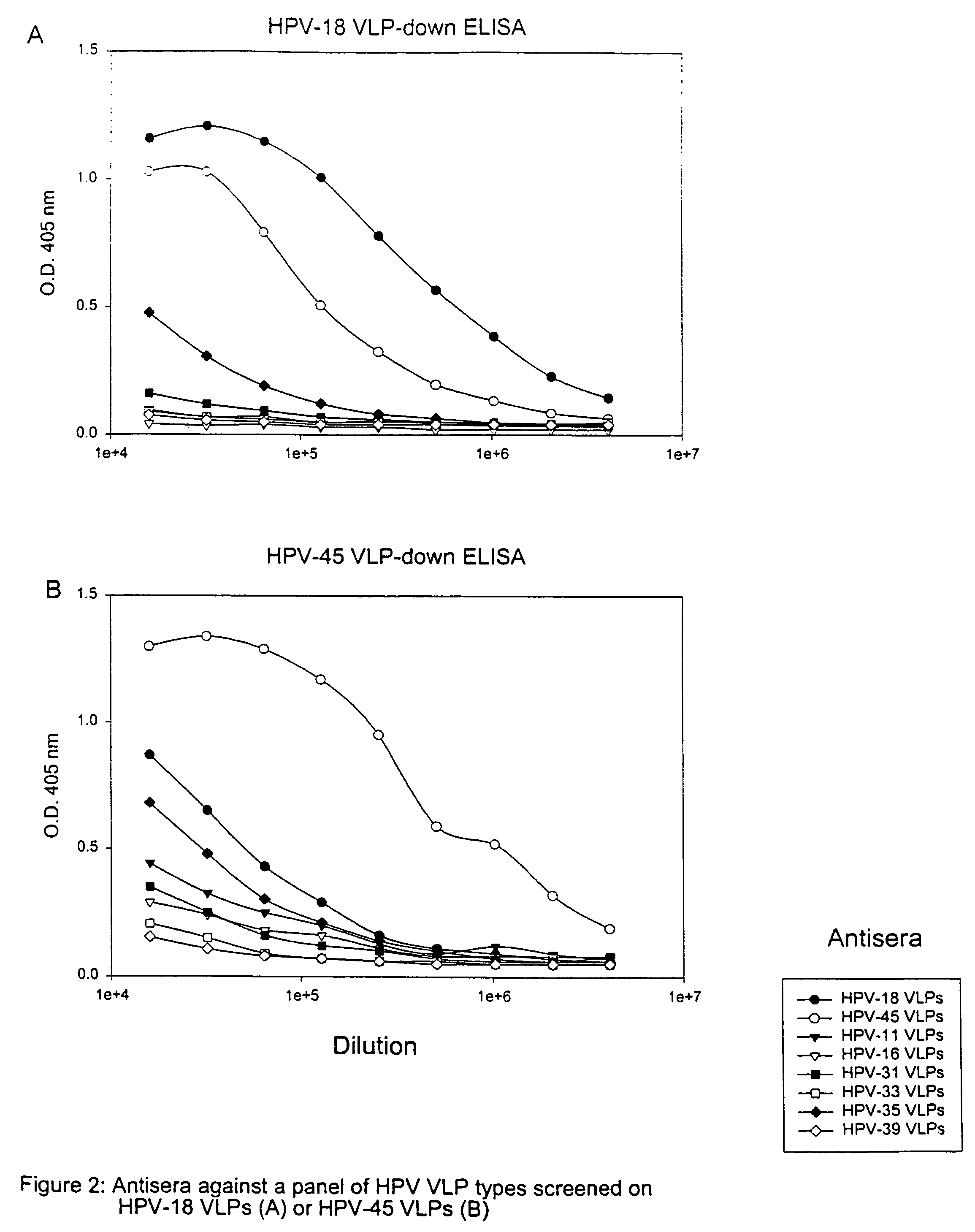
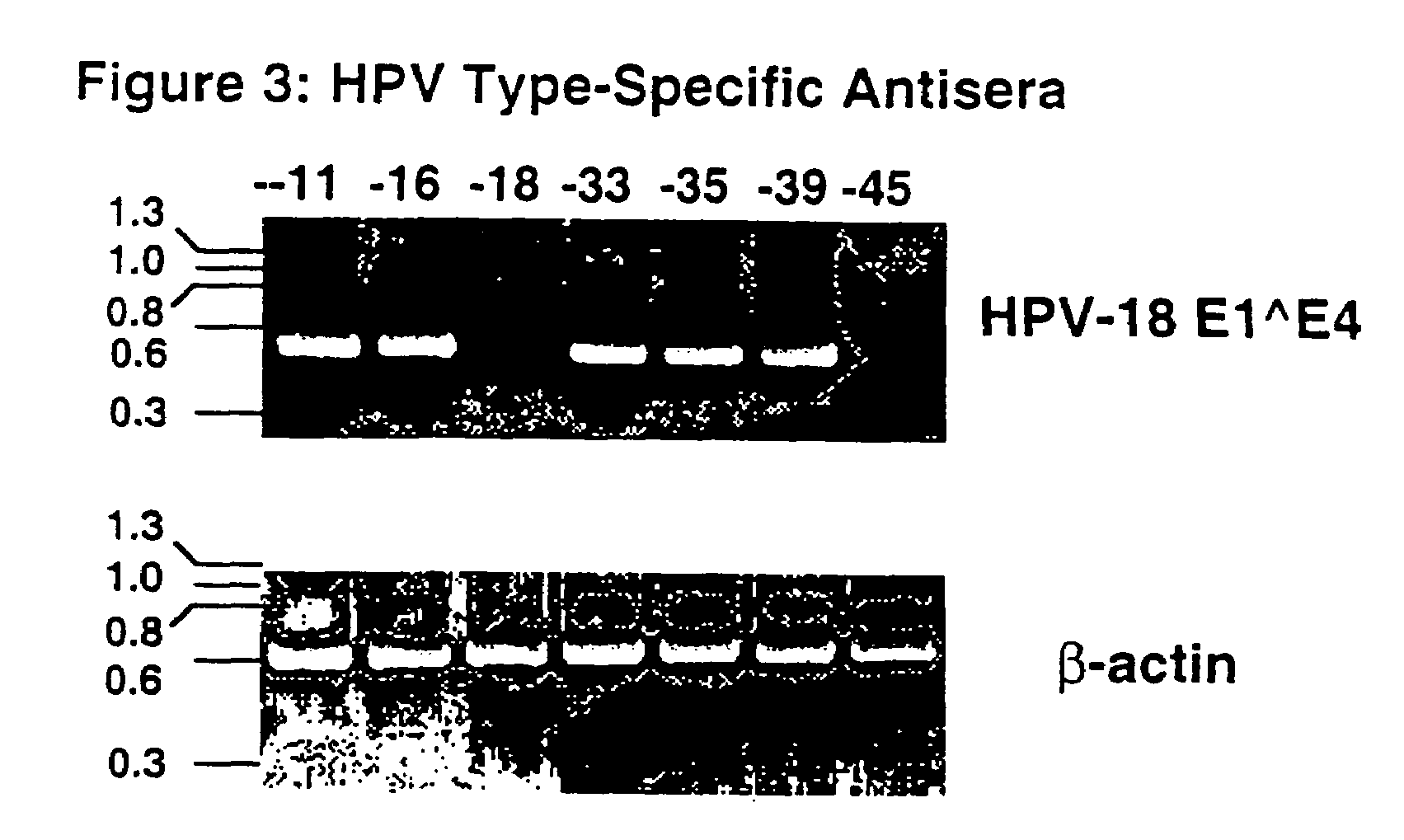
Chimeric human papillomavirus (HPV) L1 molecules and uses therefor
InactiveUS7390487B2Need can be quite largeLevel of protectionAntibody mimetics/scaffoldsMicrobiological testing/measurementHuman papillomavirusVirus-like particle
Disclosed are chimeric HPV L1 proteins and virus like particles comprising the same which are capable of generating high titer neutralizing antibody responses against at least two HPV types. The disclosed chimeric HPV L1 proteins and VLPs are useful as therapeutic and prophylactic reagents, as well as reagents for diagnosing papillomavirus infection.
Owner:MEDIMMUNE LLC
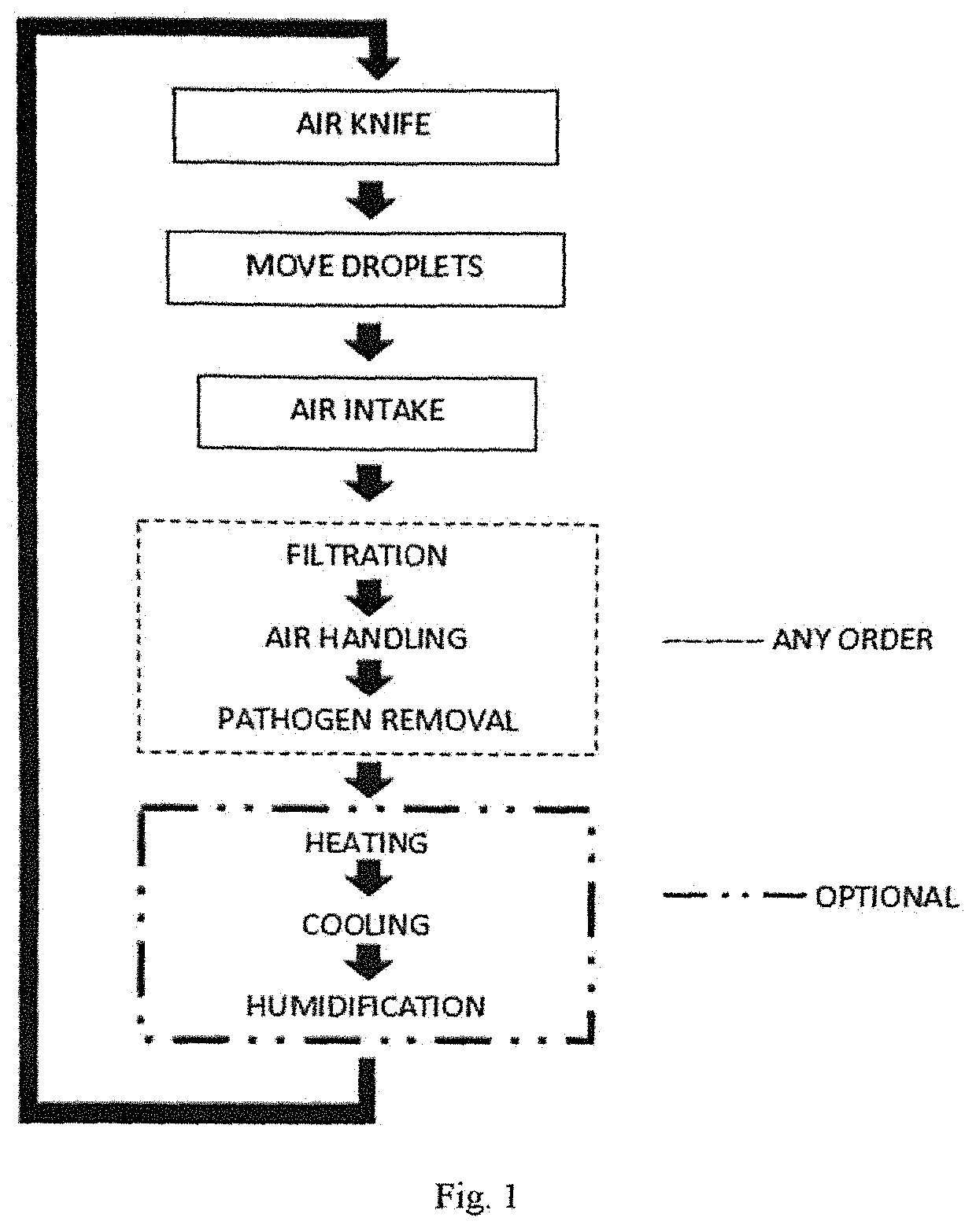
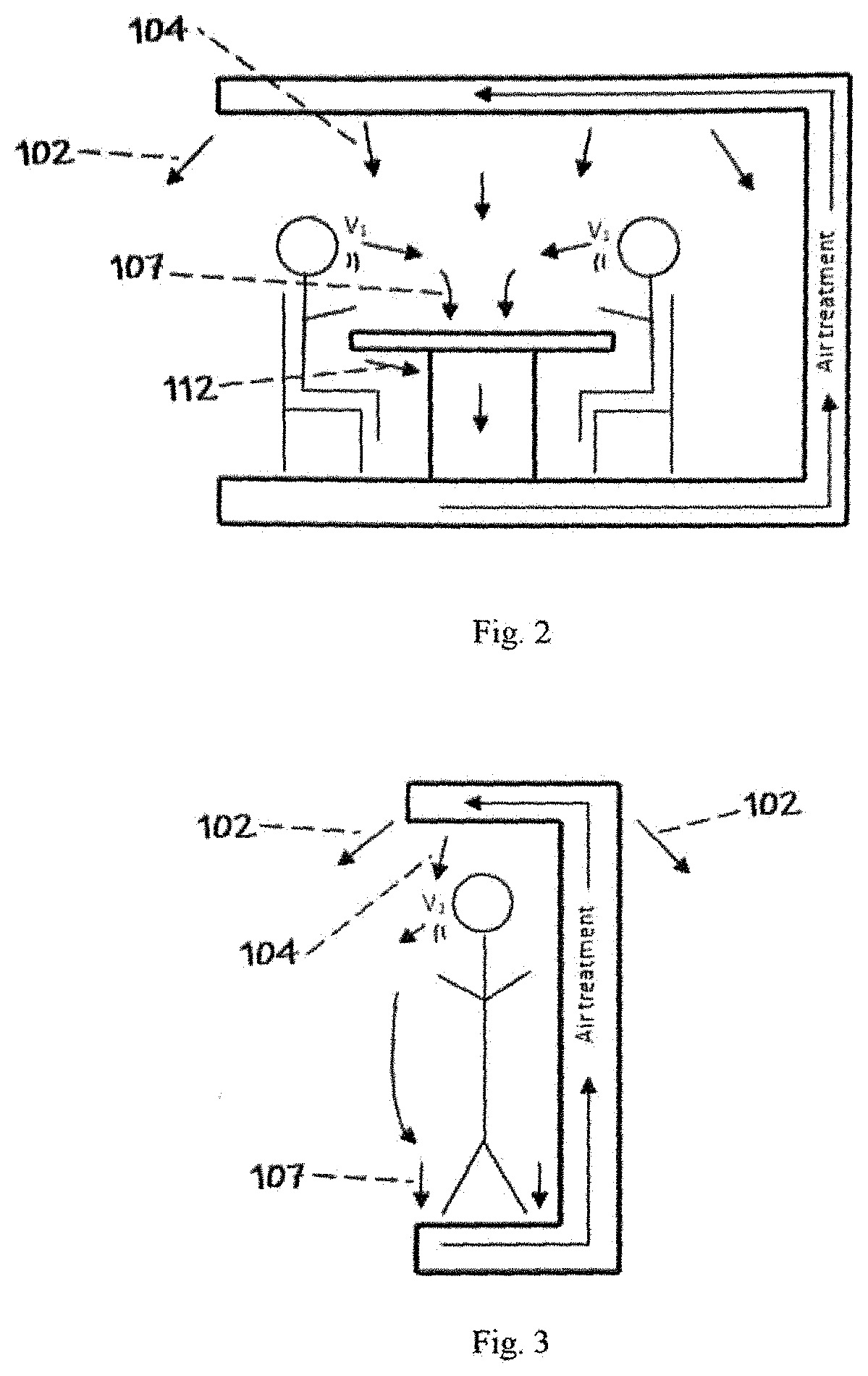
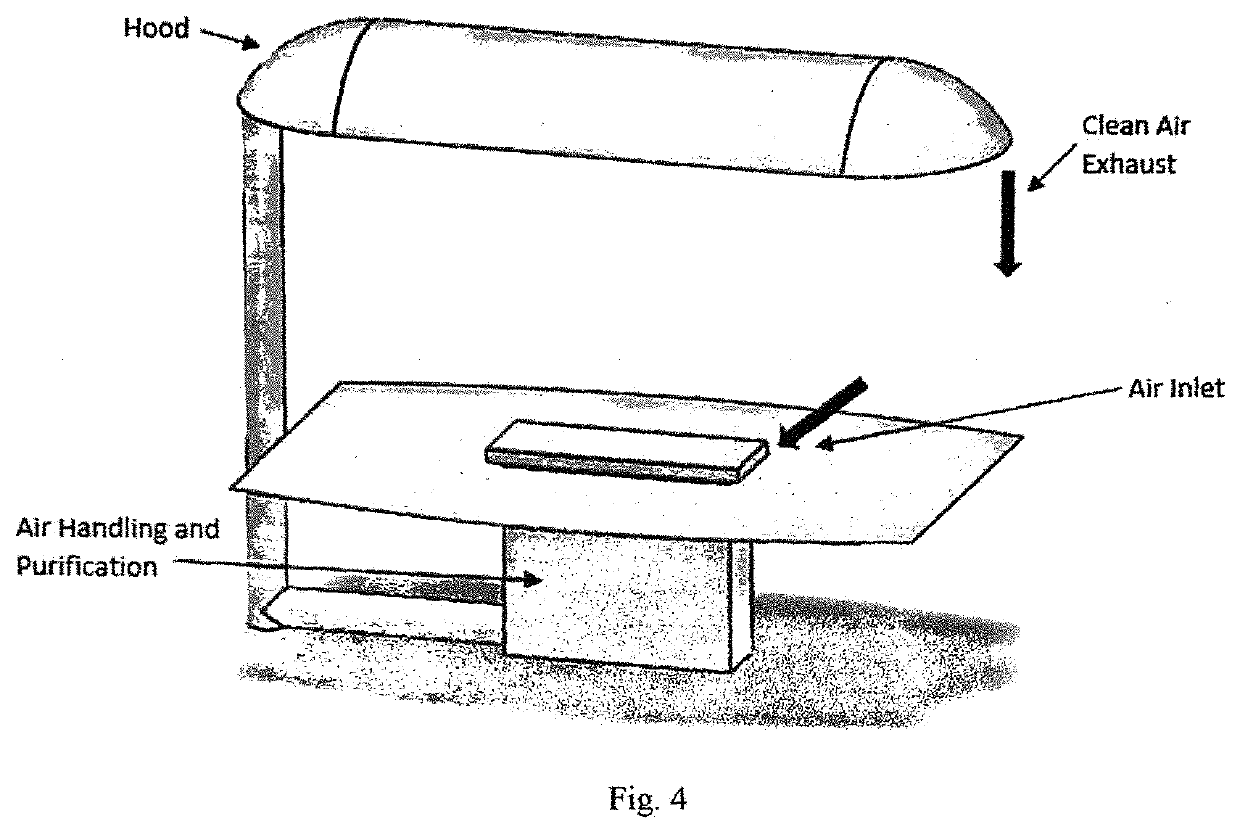
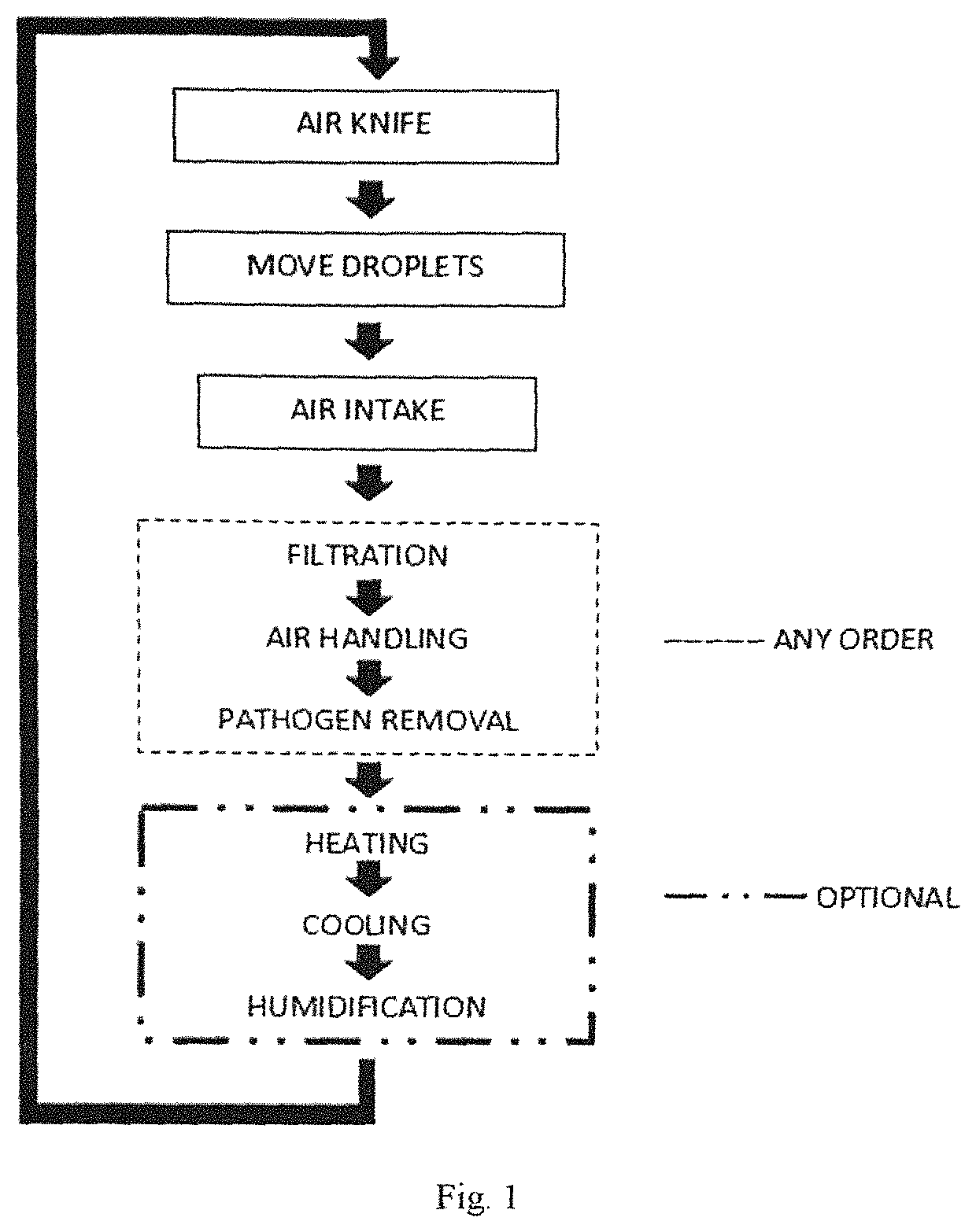
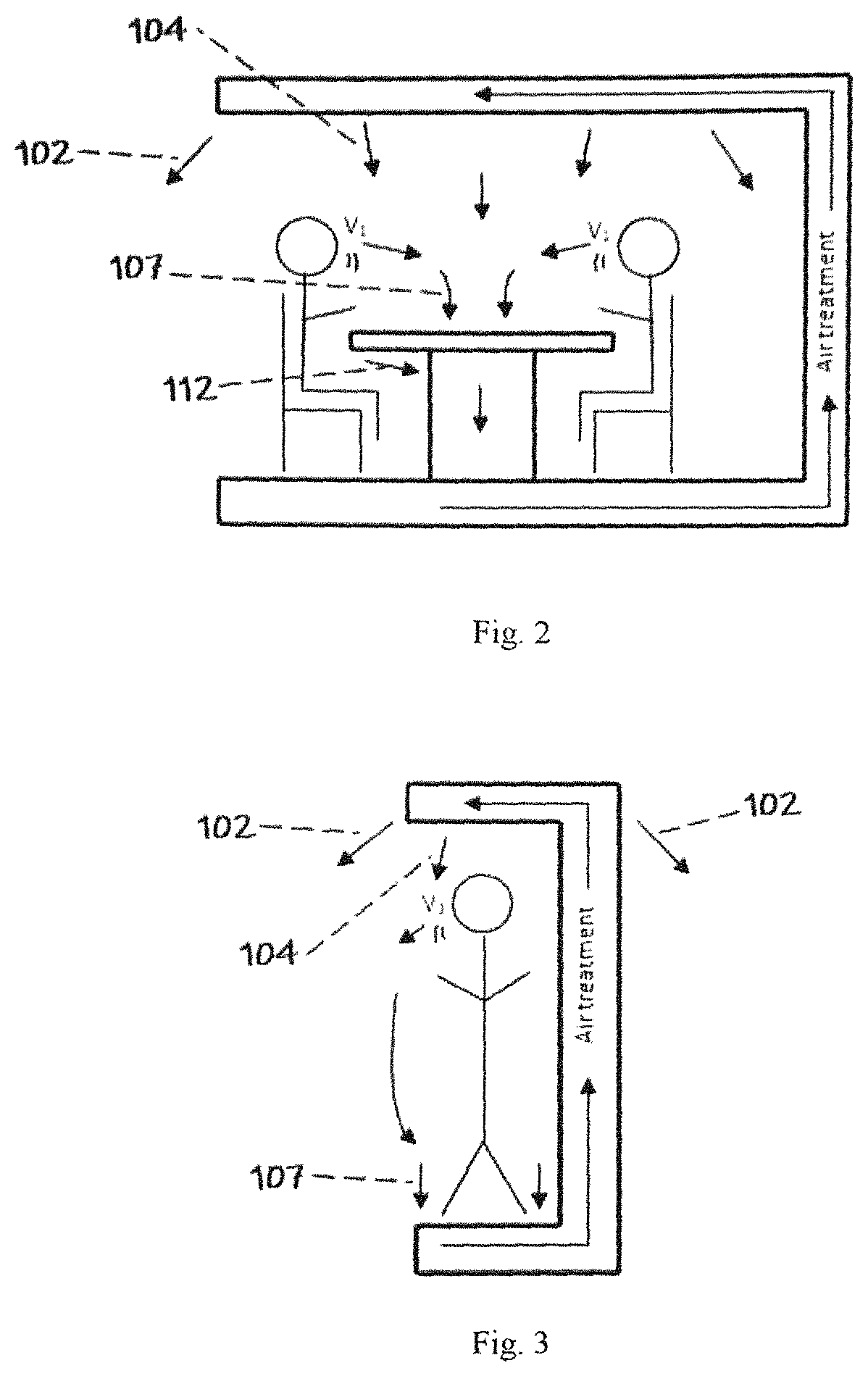
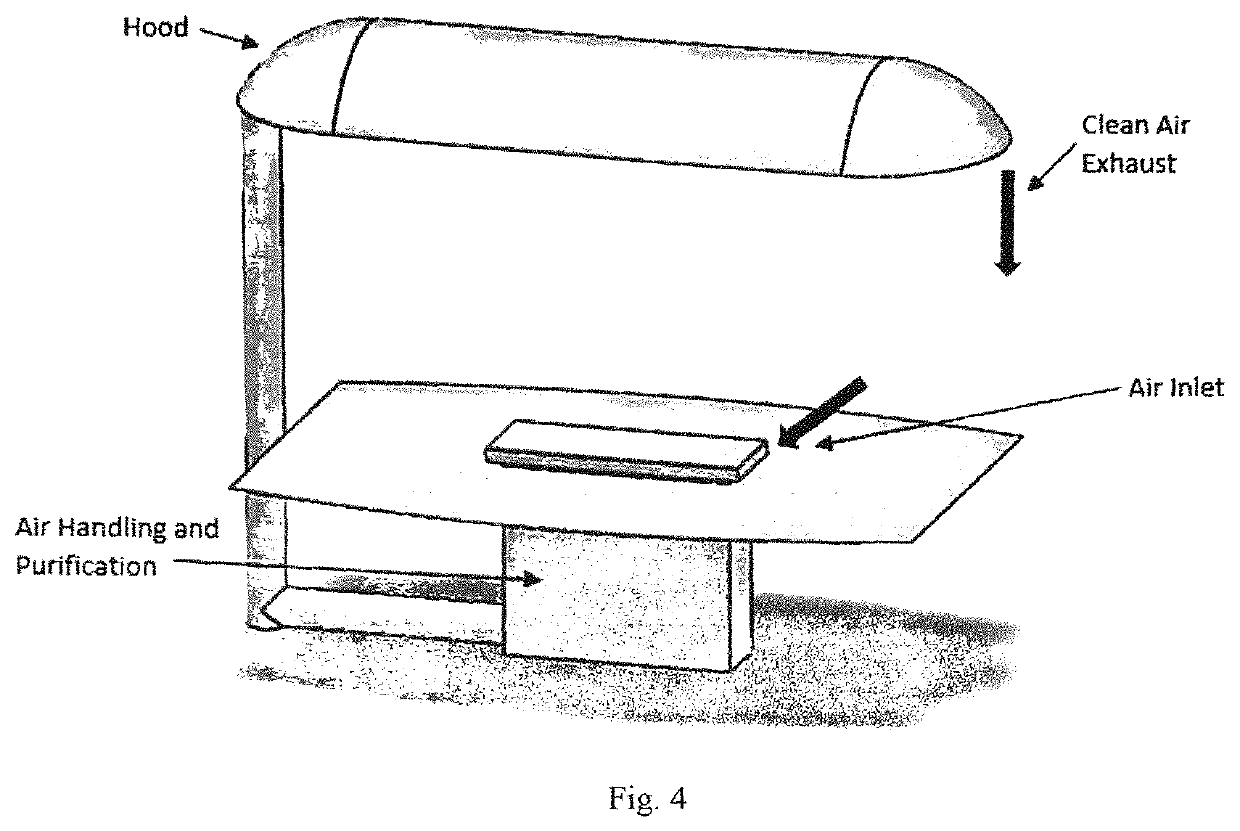
Modular recycling air curtain device to replace personal protection equipment (PPE) for reduction in the spread of viruses such as Covid-19.
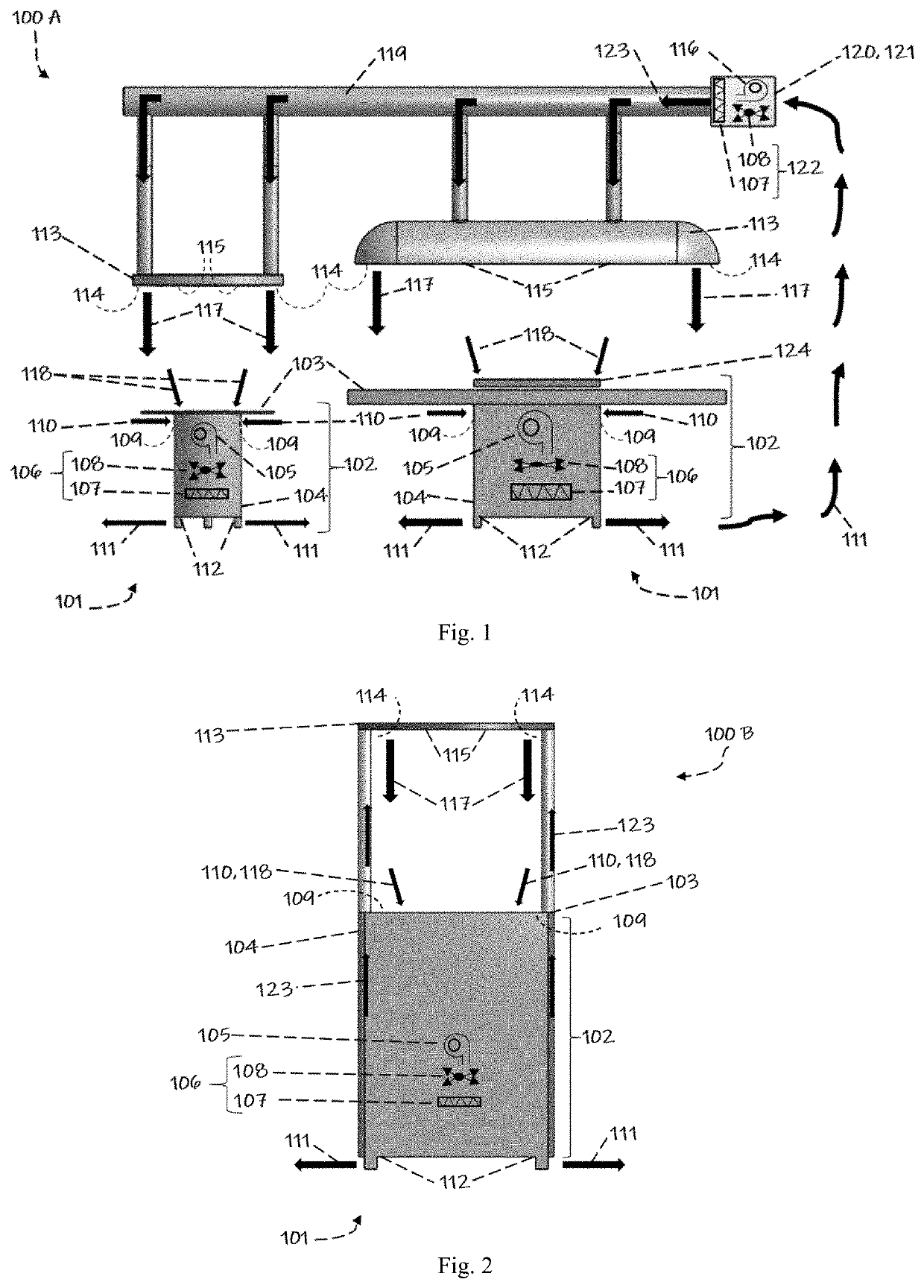
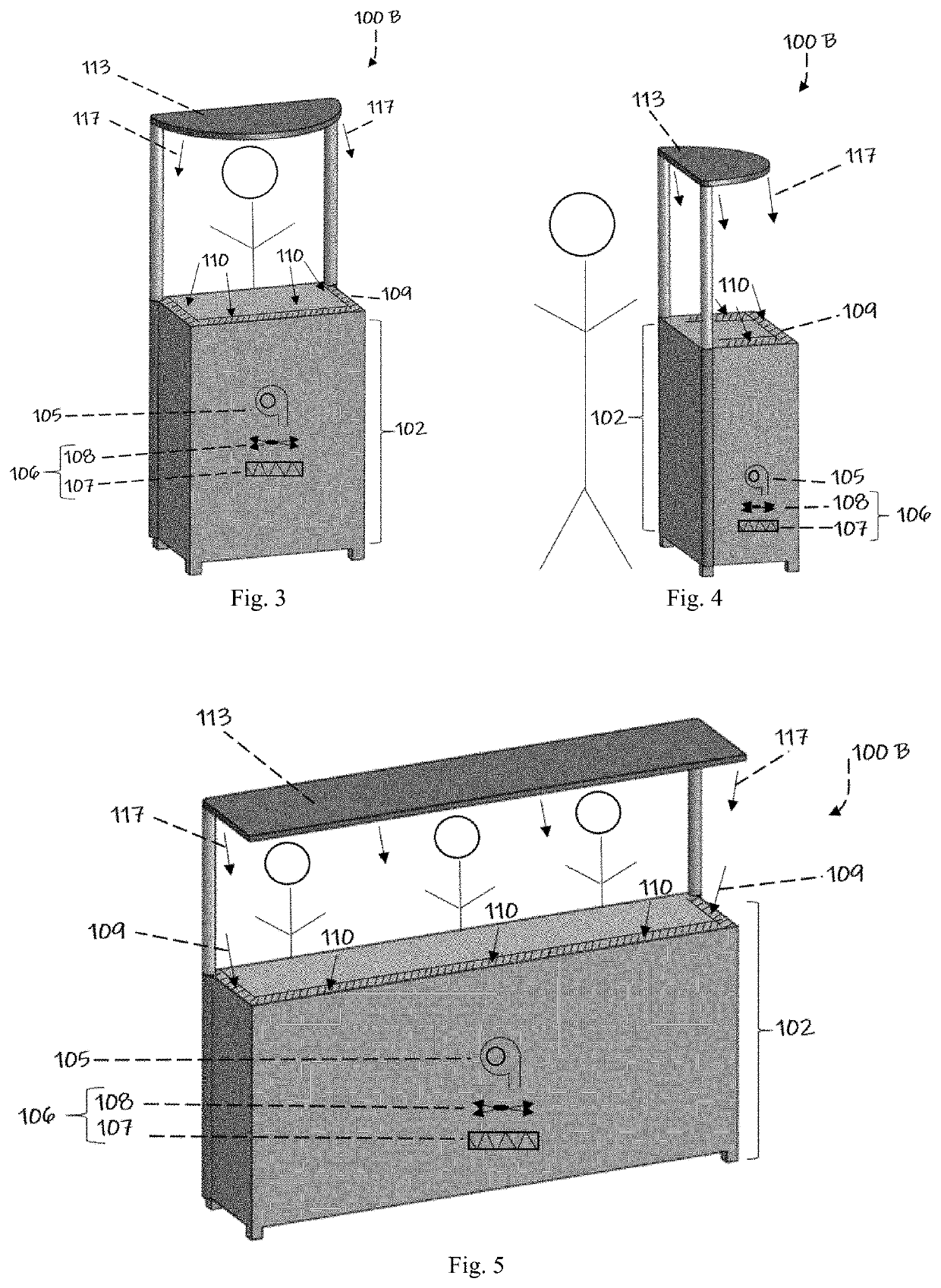
ActiveUS20220010988A1Easy to cleanEffectively conditionMechanical apparatusLighting and heating apparatusProcess engineeringMechanical engineering
A module air curtain and recirculation system that can be incorporated into various tables and workstations that provides 1) an effective air curtain between individuals, 2) a reduction of harmful viruses and 3) the ability for two or more people to be in close proximity without having to wear personal protective equipment such as face masks.
Owner:CASH JAMES T +1
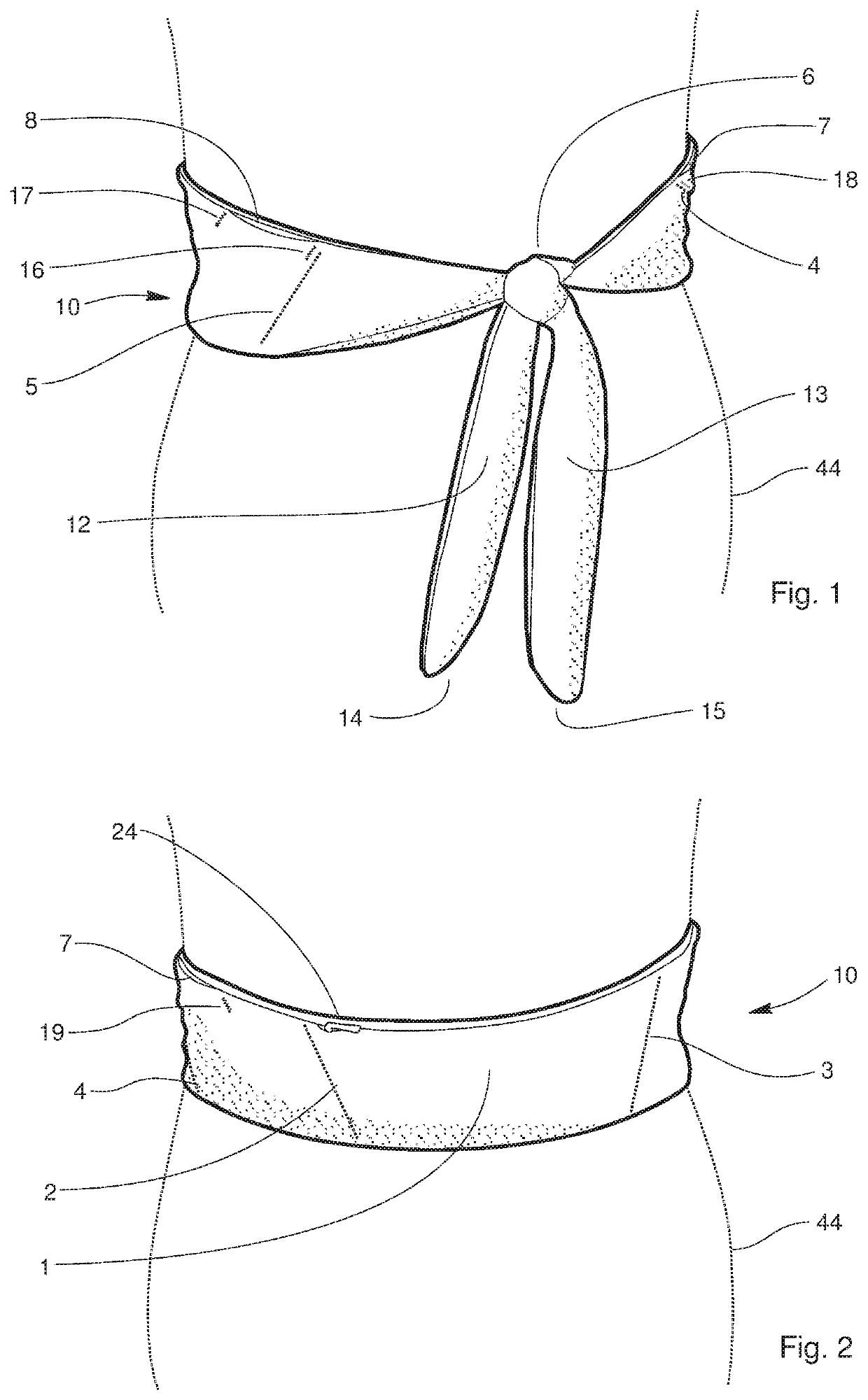
Stretch belt with pockets
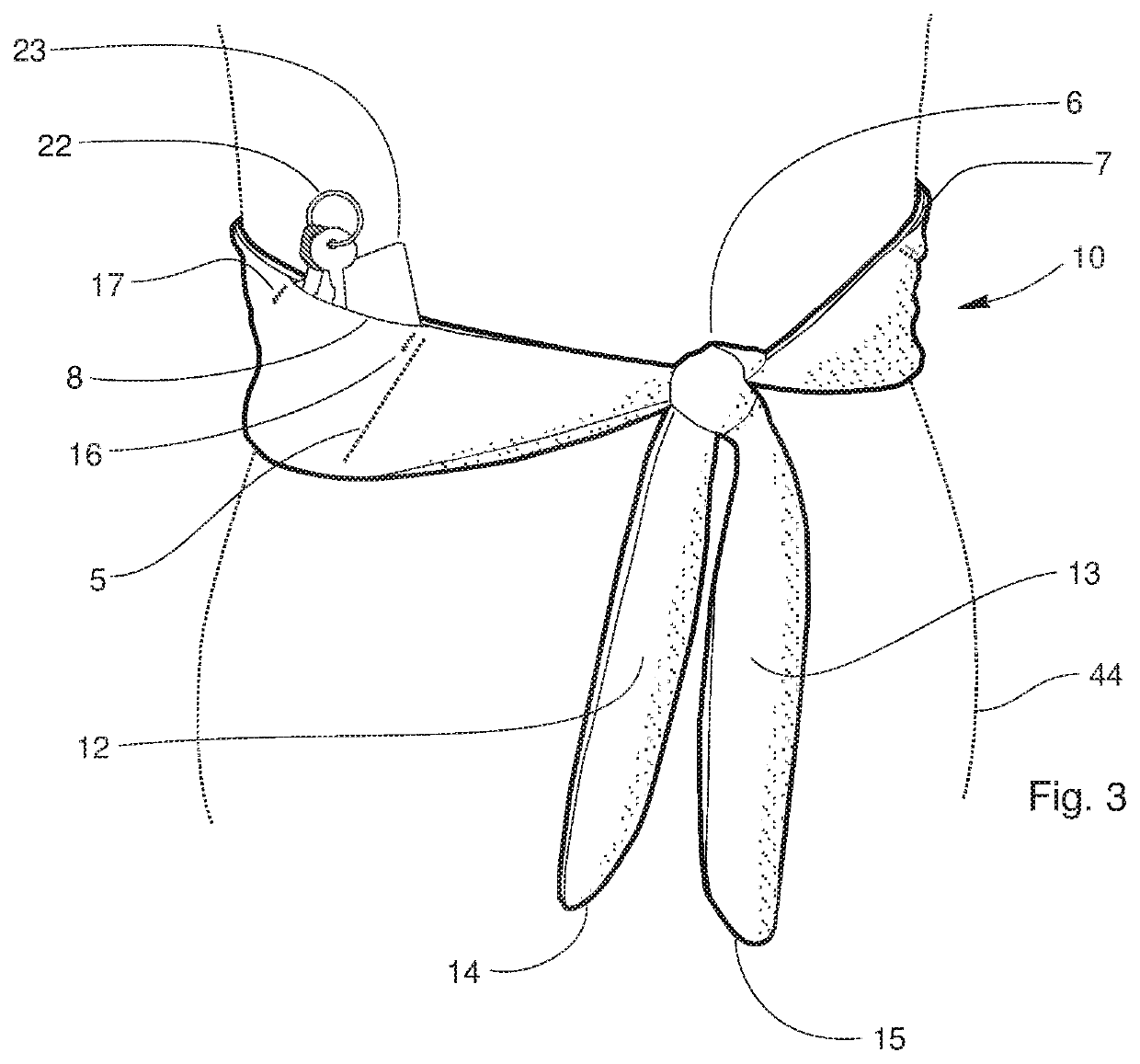
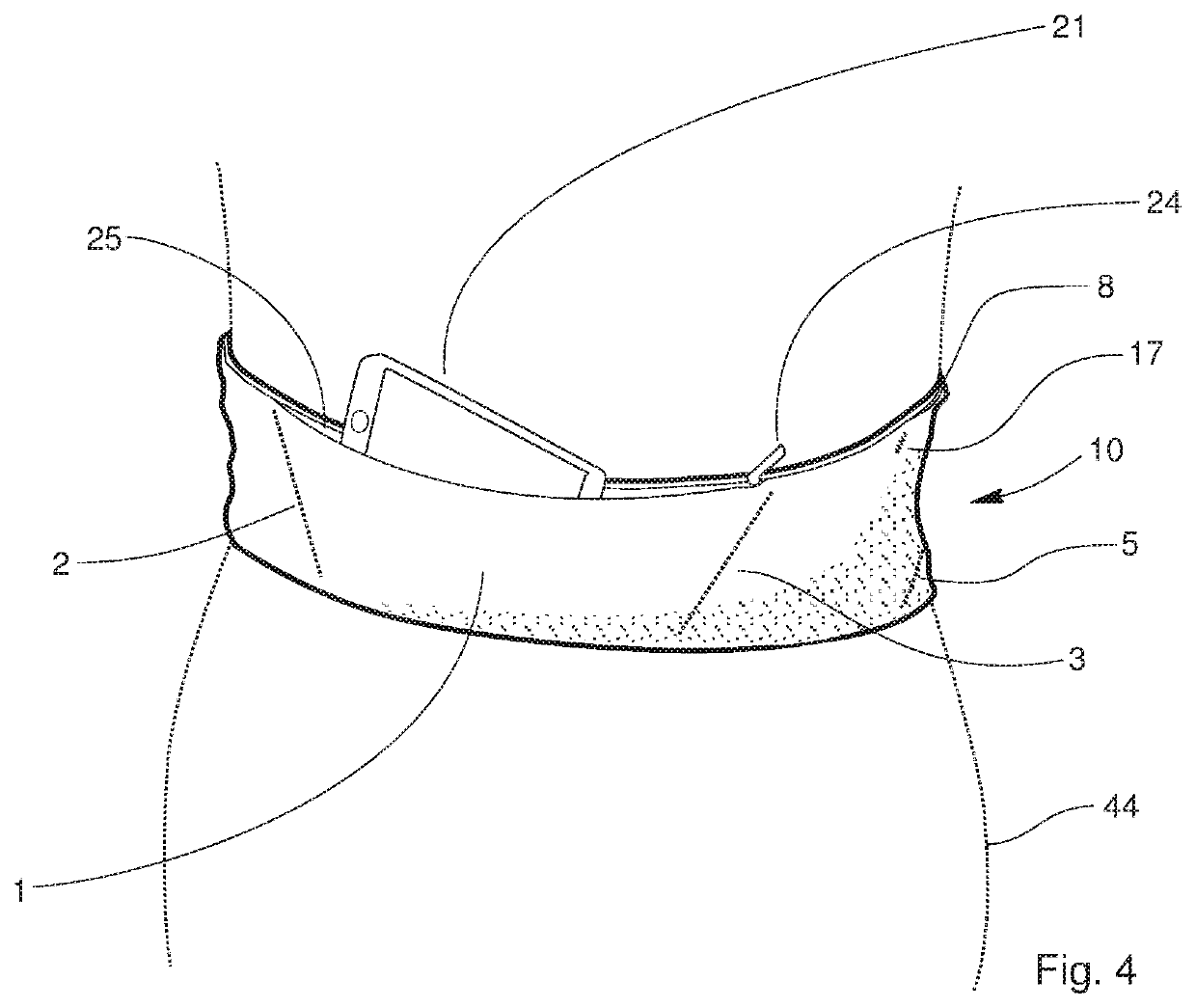
ActiveUS10986886B2Simple to wearSimple to useTravelling sacksOther accessoriesStructural engineeringMechanical engineering
A belt winch may be formed from stretchy fabric, includes a front panel joined to a rear panel. Flaps may be provided to form interior pockets, which are further formed by stitching or other joining techniques. Internal stiffening and resilient members may be incorporated between the panels at each end, aiding in the structure of the opposing ends of the belt which tie together.
Owner:AMPHIPOD
Method and device for authenticating a mobile device
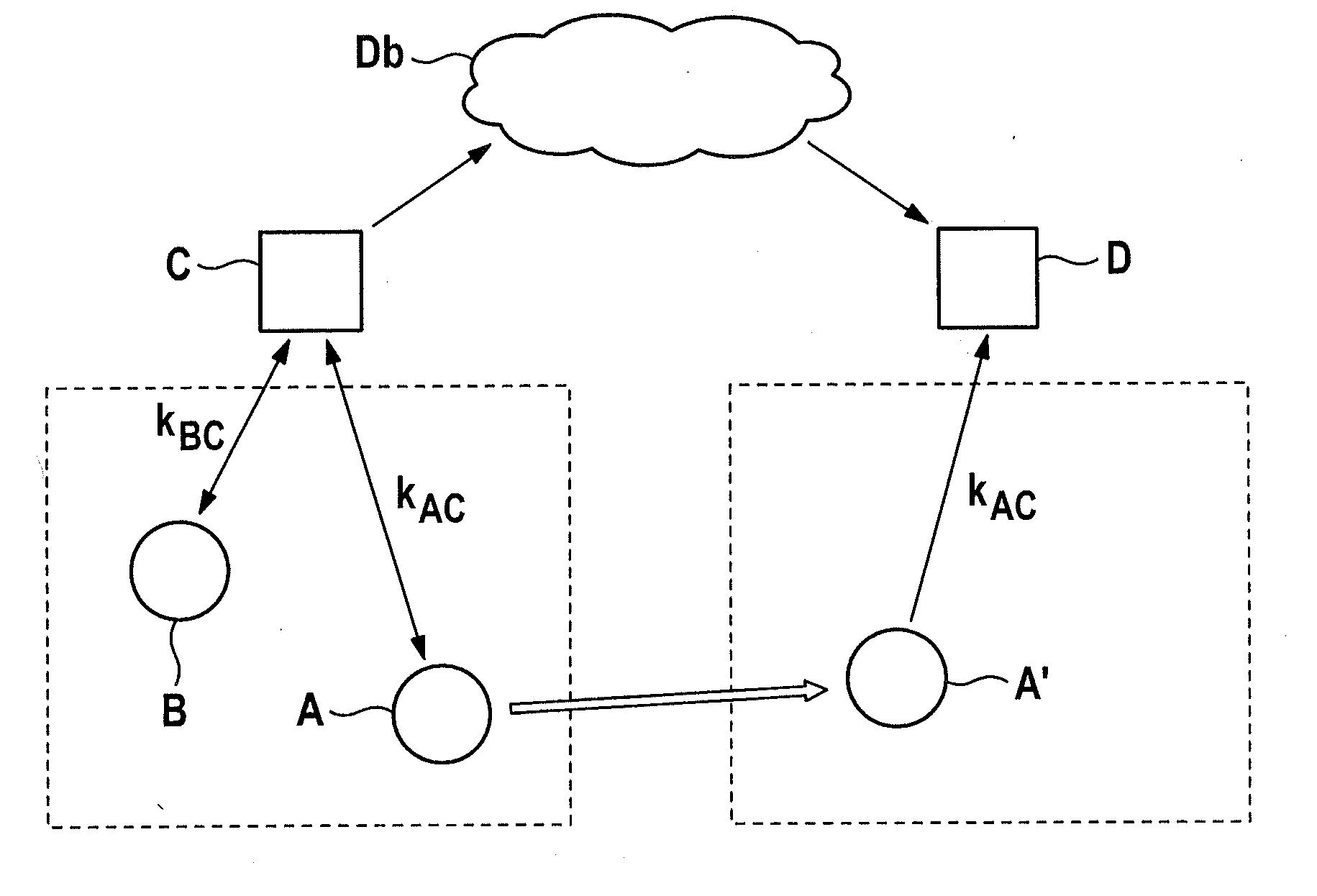
ActiveUS20150382192A1Level of protectionHigh protection levelUnauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile deviceRadio Base Station
A method for authenticating a mobile device includes: probing by the mobile device a fading channel which connects the mobile device to a first radio base station; determining a secret held in common with the first radio base station as a function of a physical property of the fading channel; storing the in-common secret; receiving a first request for the in-common secret from a second radio base station; and, in response to the first request, sending a proof of knowledge of the in-common secret to the second radio base station.
Owner:ROBERT BOSCH GMBH
Modular recycling air curtain device to replace personal protection equipment (PPE) for reduction in the spread of viruses such as Covid-19
ActiveUS11226122B1Easy to cleanEffectively conditionMechanical apparatusLighting and heating apparatusProcess engineeringMechanical engineering
A module air curtain and recirculation system that can be incorporated into various tables and workstations that provides 1) an effective air curtain between individuals, 2) a reduction of harmful viruses and 3) the ability for two or more people to be in close proximity without having to wear personal protective equipment such as face masks.
Owner:CASH JAMES T +1
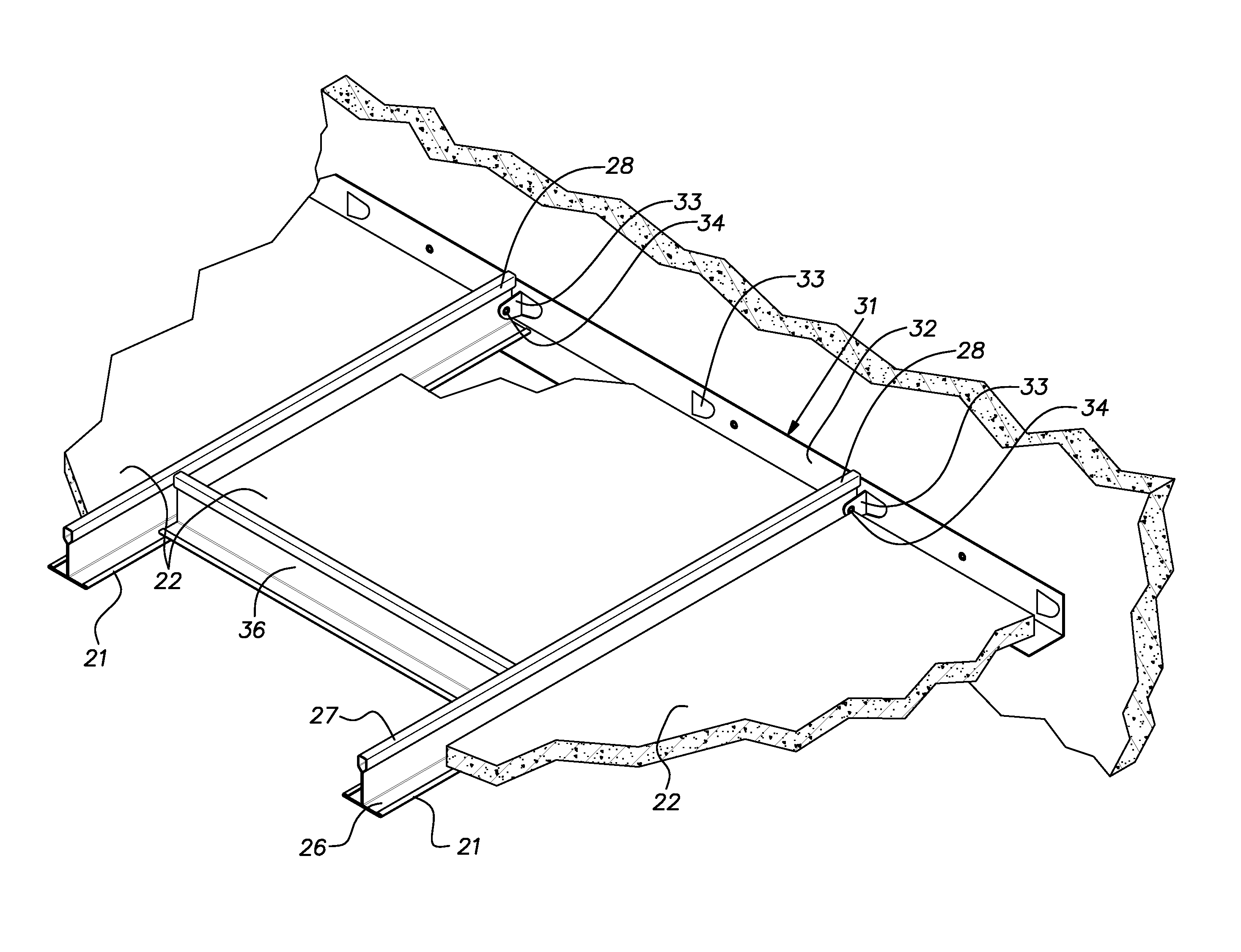
30-minute residential fire protection of floors
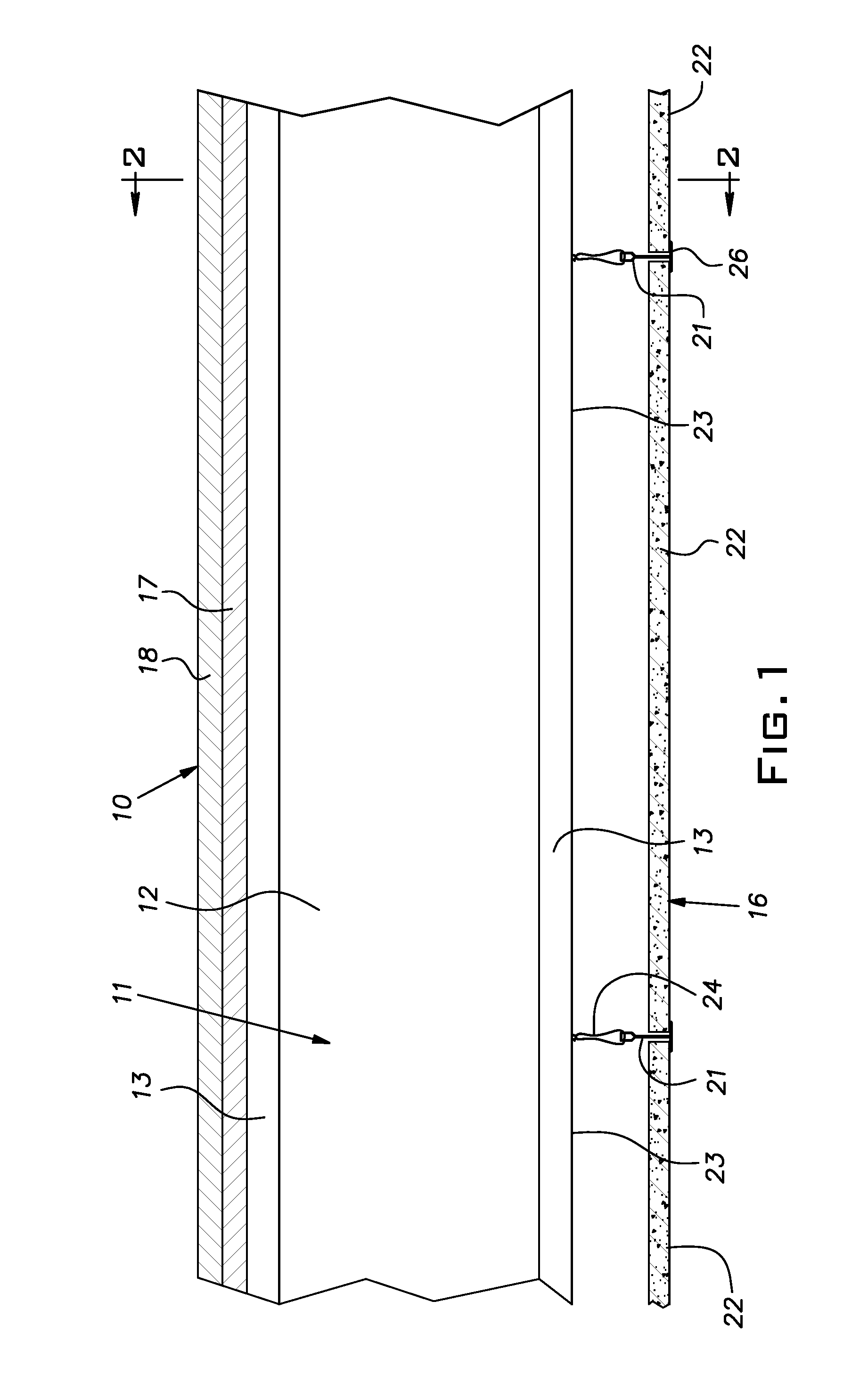
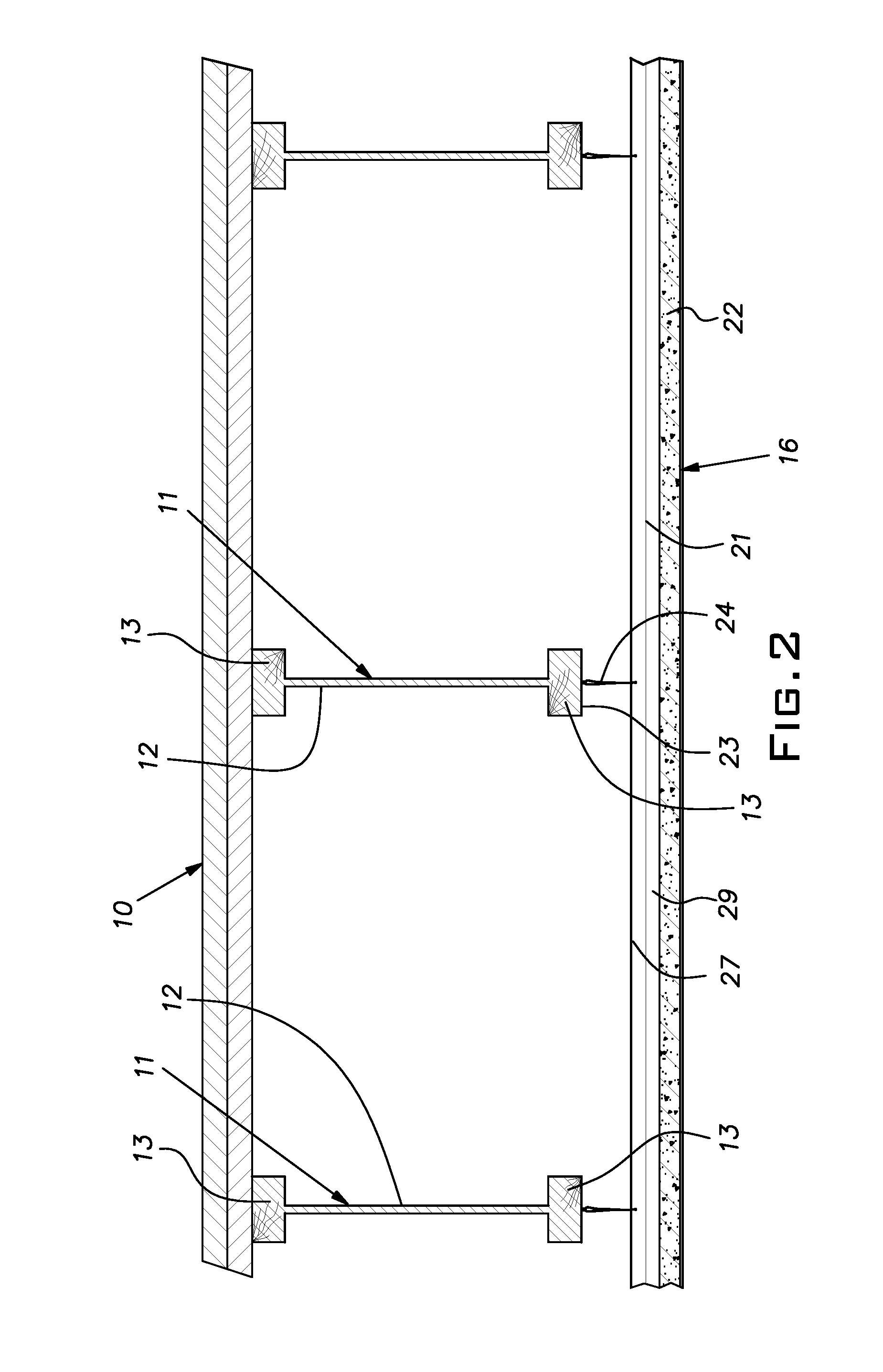
A fire protective barrier for a residential floor and a method of its construction, the construction involving a floor supported on lightweight joists of a type susceptible to early failure once exposed to a fire existing in the space below the floor, an array of elongated steel main tees suspended below the joists, the tees being parallel and spaced apart by a nominal distance of 2′, the tees having an upper hollow reinforcing bulb, a central vertical web extending downwardly from the bulb and a horizontal flange extending laterally from both sides of the web, drywall panels carried on upper faces of the flanges of adjacent pairs of tees, the drywall panels having a width of slightly less than the center-to-center distance of the tees, a majority of the panels having lengths of 8′ or more.
Owner:UNITED STATES GYPSUM CO
Modular Recycling Air Curtain Device
PendingUS20220010995A1Easy to cleanEffectively conditionMechanical apparatusLighting and heating apparatusAir purifiersAerosolize
A module air curtain and recirculation system that can be incorporated into various tables and workstations that provides 1) an effective air curtain between individuals, 2) a reduction of harmful viruses and 3) the ability for two or more people to be in close proximity without having to wear personal protective equipment such as face masks. The apparatus for indoor air filtration and conditioning creates an air curtain between and around people. The device captures aerosolized droplets expelled from occupants and recirculates cleaned air to operate the air curtain while greatly increasing effective air changes per hour in spaces it is employed. While portable room air purifiers are used to improve the air quality of indoor spaces and reduce particles, allergens, and viruses, they do little to stop the person-to-person transmission of viruses. This device solves these deficiencies. Through applied effort, ingenuity, innovation and testing these issues have been solved by the embodiment of the presently disclosed modular system. Employment of this system can allow businesses, schools and restaurants to resume more normal activity.
Owner:CASH JAMES T +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com