Electronic contract security system and method based on biological information identification
An electronic contract and electronic security technology, which is applied in the field of electronic information authentication and security, can solve the problems of waste of resources, contract tampering, and impossibility of completely consistent keys, etc., and achieve the effect of high security and convenient authentication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
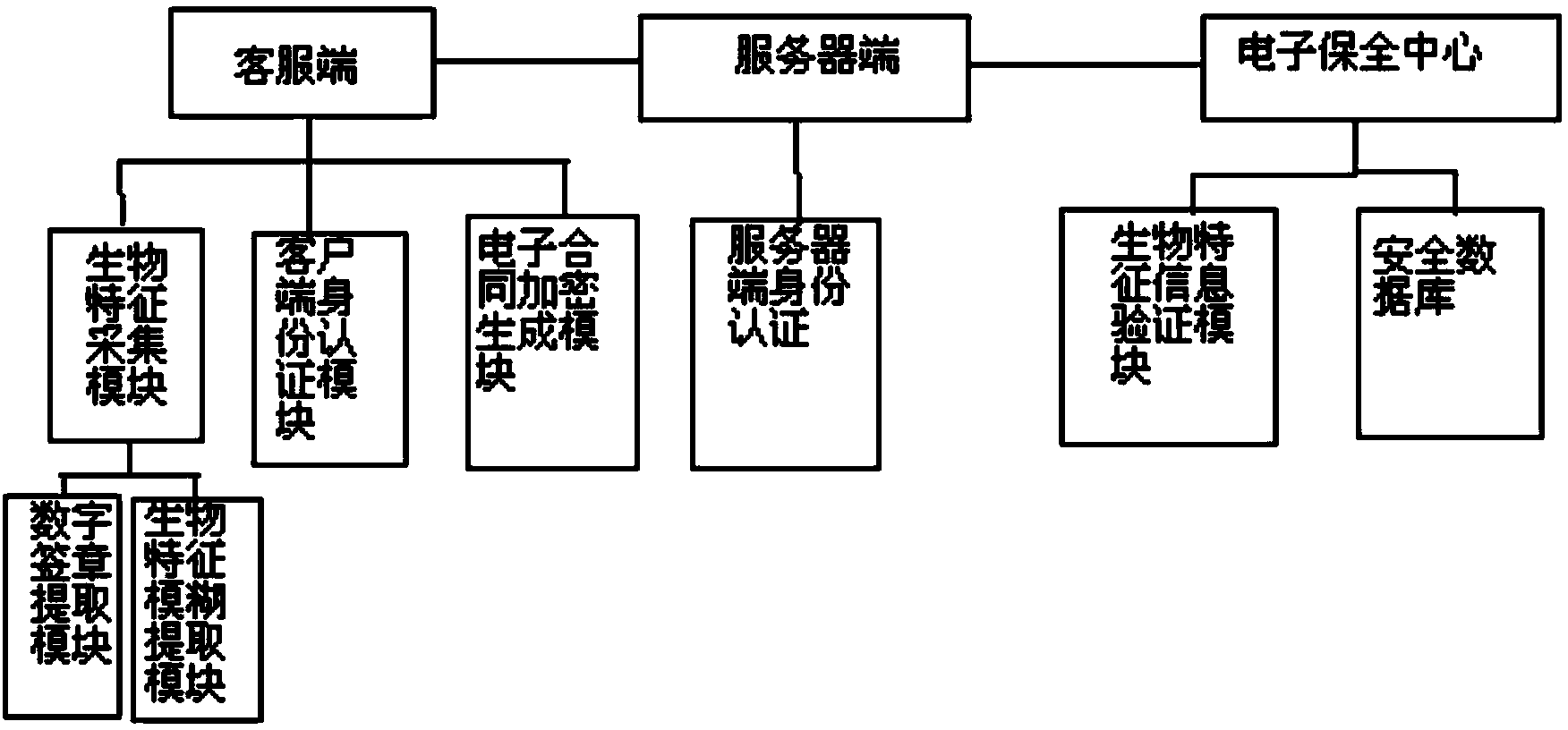
[0026] like figure 1 Shown is the functional block diagram of the electronic contract security system of the present invention, including: client U, server S, electronic security center T, the client includes: biological feature collection module, electronic contract encryption generation module, client identity authentication module; Including: server-side identity authentication module; electronic security center includes: safety database, biometric information verification module.
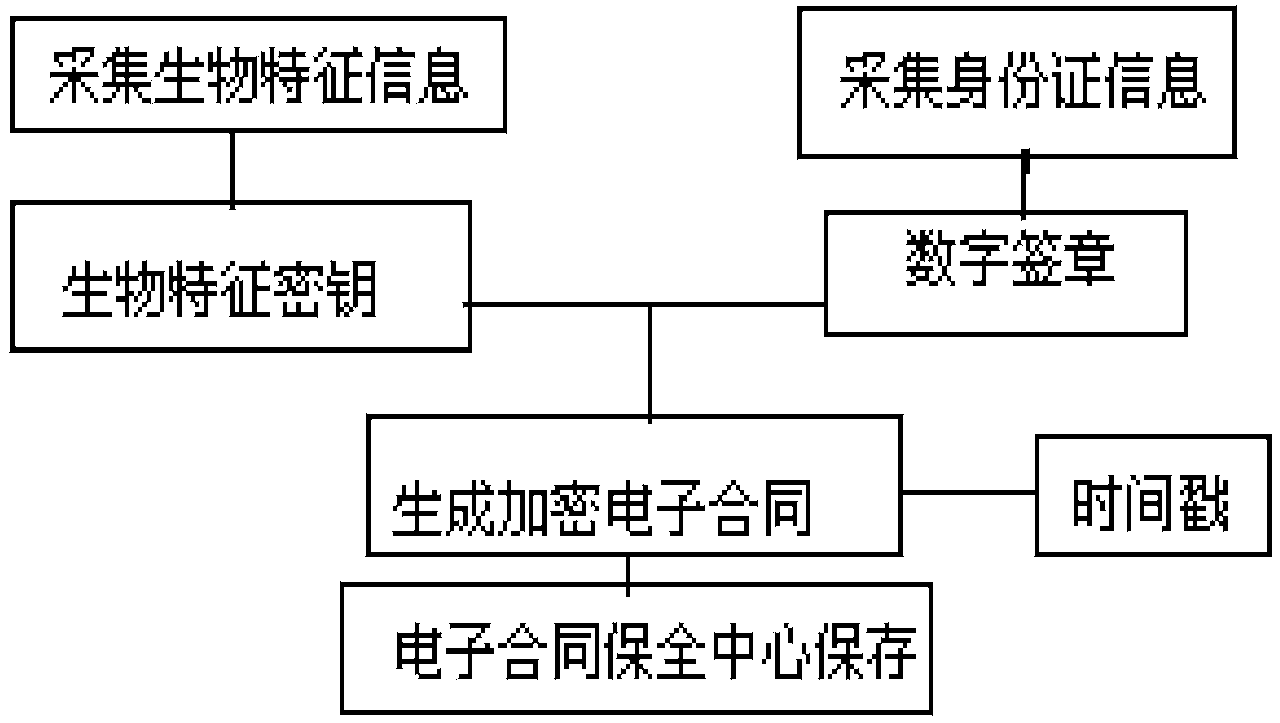
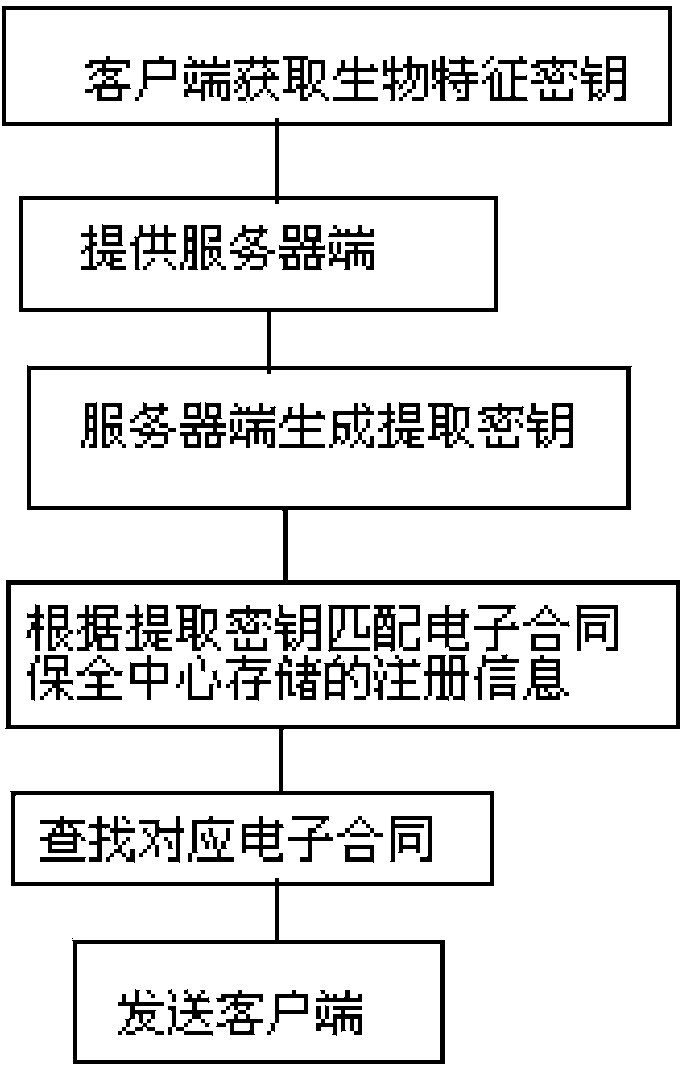
[0027] Biometric feature collection module: used to collect the user’s biometric features and extract biometric feature information, collect customer ID card scanning information, and obtain the ID card number as a digital signature. The biometric feature collection module converts the collected biometric feature images into biometric data , use the fuzzy extractor to fuzzy extract the biometric feature to obtain the user biometric key R. The biometric feature collection module can collect biom...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com