Method and system for detecting scanning behaviors of ports
A technology for detecting ports and behaviors, applied in the field of port scanning behaviors and systems, it can solve the problems of high concealment, concealment, and difficulty in detection, and achieve the effect of avoiding false negatives and false positives.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] The technical solution of the present invention will be described in more detail below with reference to the drawings and embodiments.
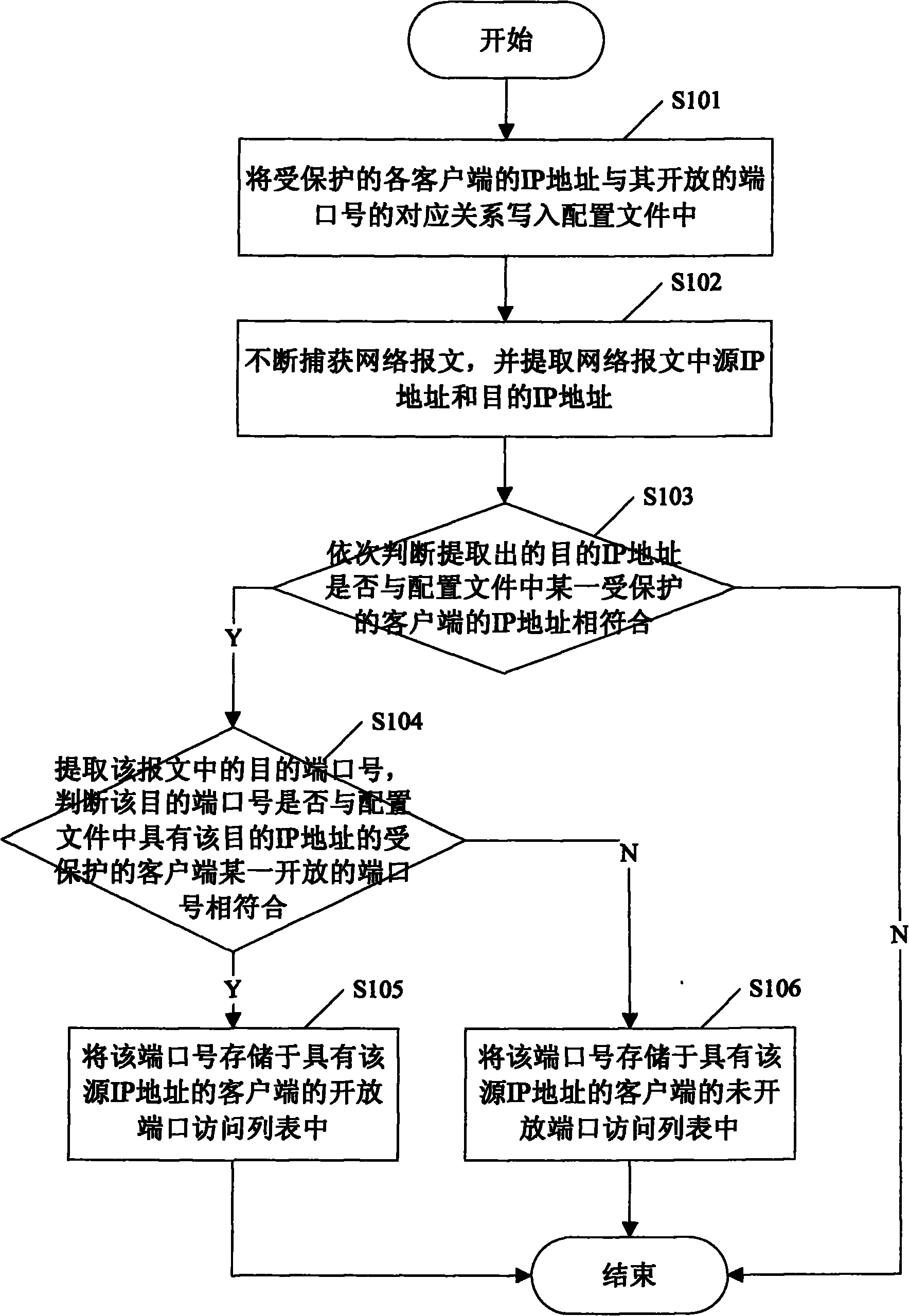
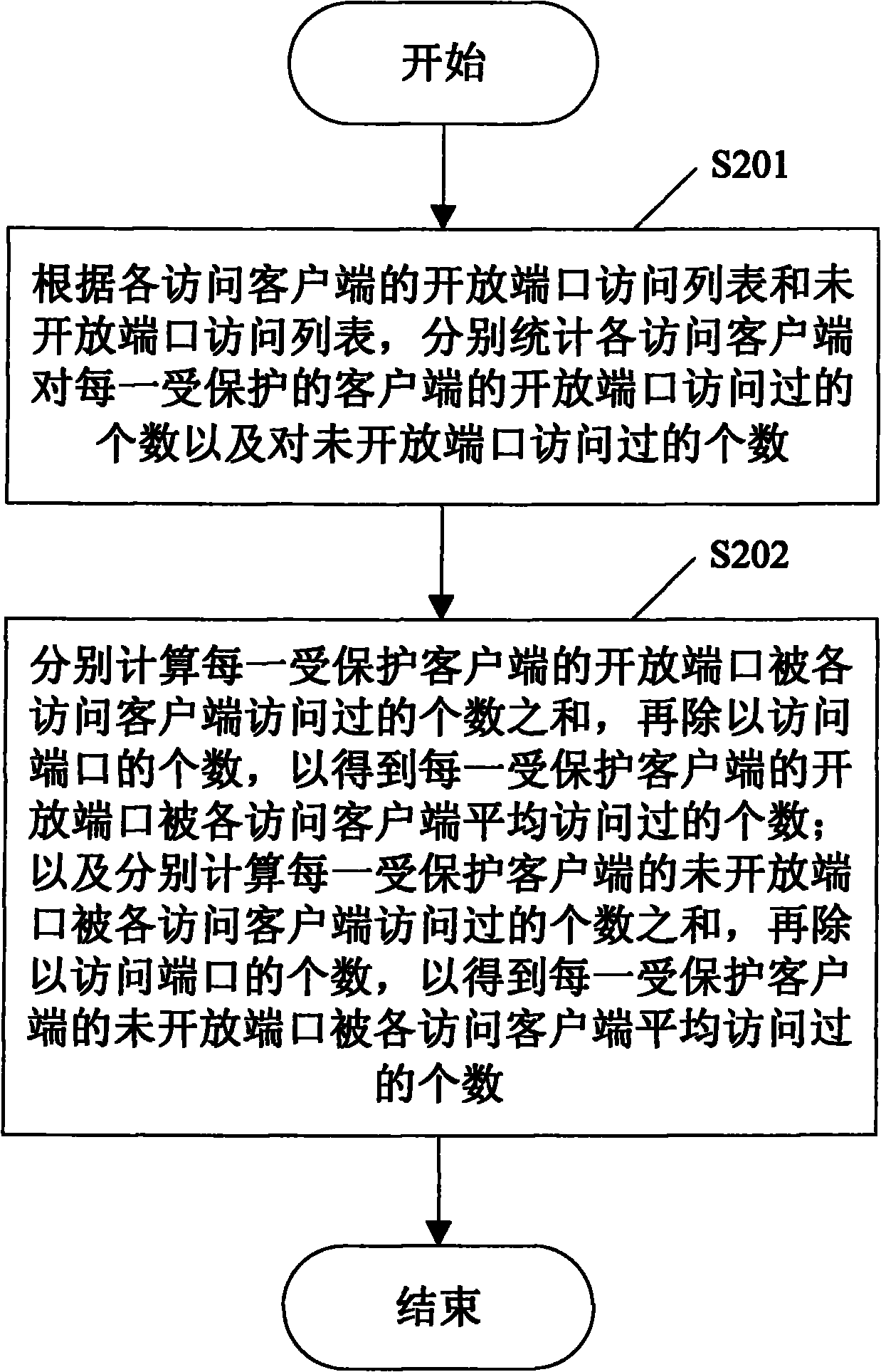
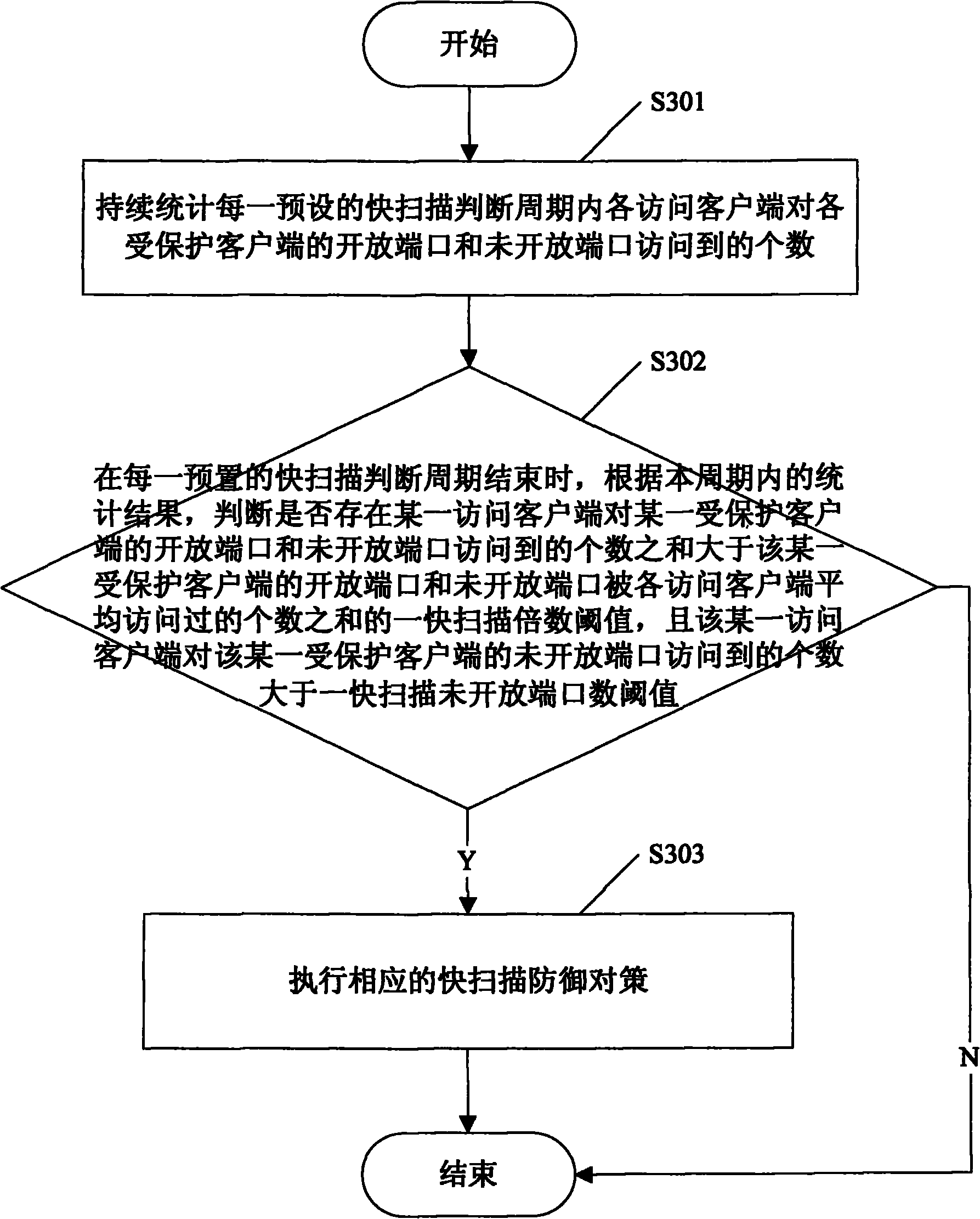
[0046] refer to figure 1 , which shows a method for collecting port scanning behavior data according to an embodiment of the present invention, including the following steps:
[0047] Step S101: write the corresponding relationship between the protected IP addresses of each client and its open port number in the configuration file;
[0048] Described port number is UDP / TCP port number;
[0049] The client is a host terminal or device;
[0050] Step S102: Continuously capturing network packets, and extracting the source IP address and destination IP address in the network packets;
[0051] Step S103: sequentially judge whether the extracted destination IP address matches the IP address of a certain protected client in the configuration file, if the judgment result is "yes", then enter step S104; if the judgment result is "no", then ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com