Network asset risk assessment method, device and system
A network asset and risk assessment technology, applied in the Internet field, can solve the problems of unprofessional and inaccurate assessment, strong subjectivity, and unprofessional assessment.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
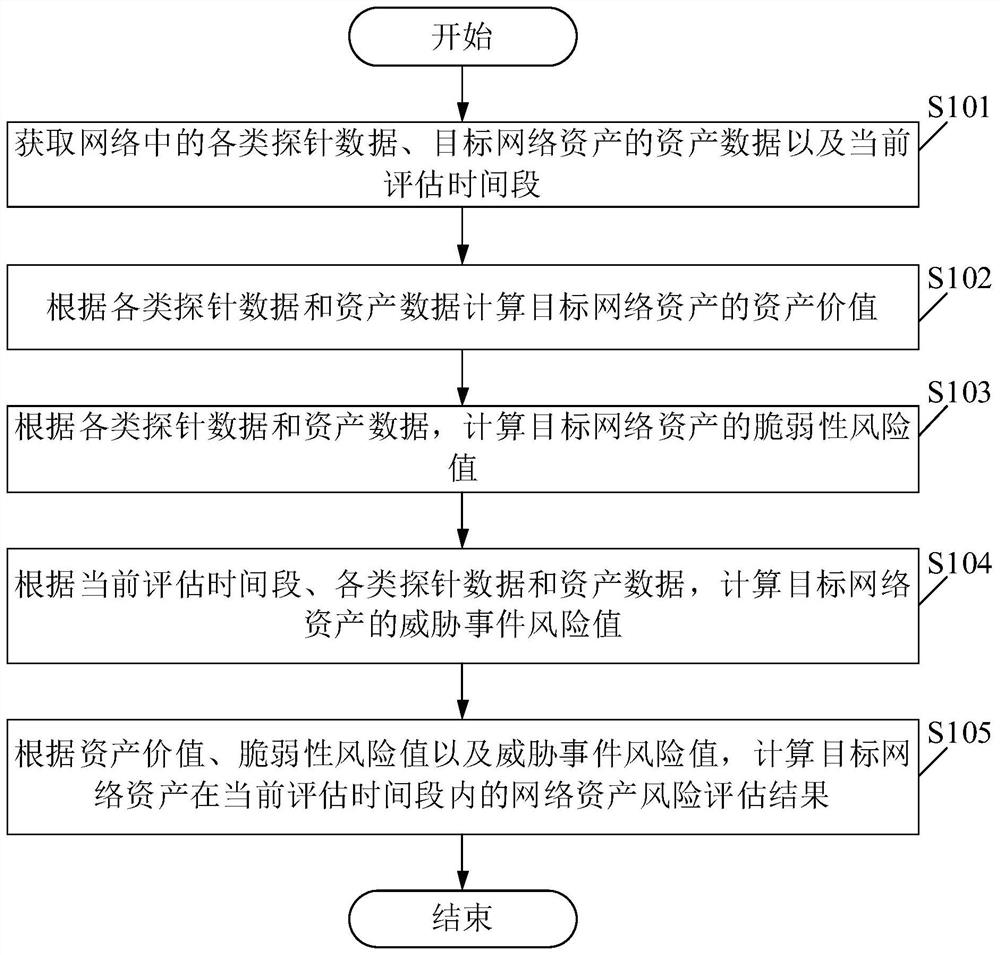
[0052] Please see figure 1 , figure 1 A schematic flowchart of a network asset risk assessment method is provided for this embodiment of the application. Among them, the network asset risk assessment method includes:
[0053] S101. Obtain various types of probe data in the network, asset data of target network assets, and a current assessment time period.
[0054] In the embodiment of the present application, the asset data specifically includes network asset data, etc., which is not limited in the embodiment of the present application. The network asset risk assessment method is specifically used for network asset risk assessment.
[0055] In the embodiment of the present application, various types of original probe data include traffic audit data, vulnerability data, security log data, etc., which is not limited in the embodiment of the present application.
[0056] In this embodiment of the application, the asset data of the target network asset includes asset name, IP ...
Embodiment 2
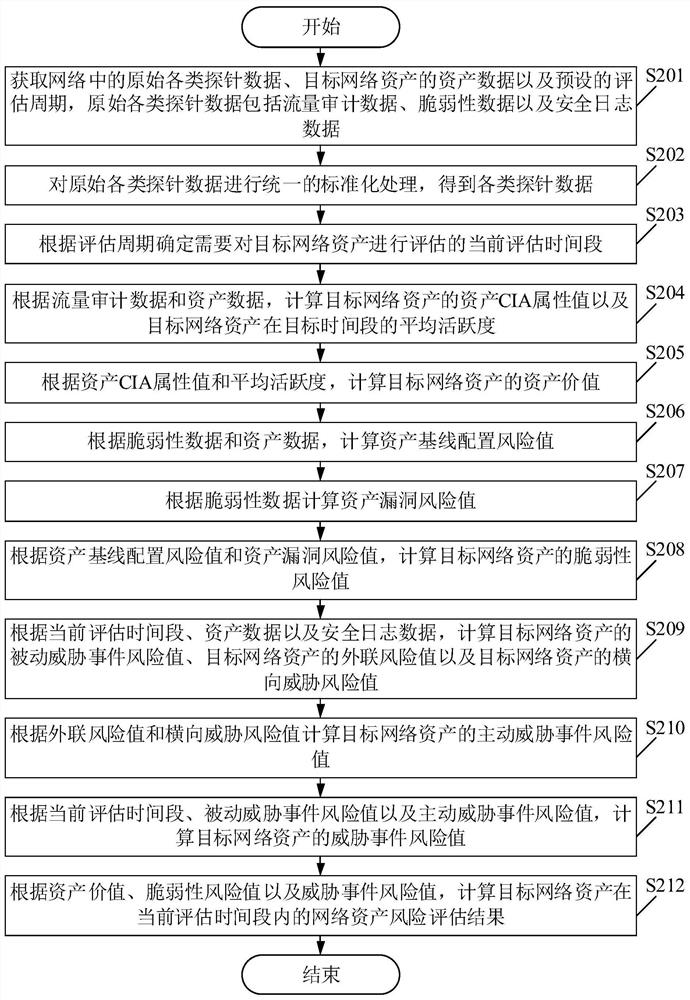
[0069] Please see figure 2 , figure 2 It is a schematic flowchart of another network asset risk assessment method provided in the embodiment of this application. Such as figure 2 As shown, among them, the network asset risk assessment method includes:
[0070] S201. Acquire various original probe data in the network, asset data of target network assets, and a preset evaluation period, where the original various probe data includes traffic audit data, vulnerability data, and security log data.
[0071] In the embodiment of the present application, the evaluation cycle may specifically be evaluated every 2 minutes, every 5 minutes, every 60 minutes, etc., which are preset, and are not limited in this embodiment.
[0072] S202. Perform unified standardized processing on the original data of various types of probes to obtain data of various types of probes.
[0073] S203. Determine the current assessment time period in which the target network asset needs to be assessed acc...
Embodiment 3
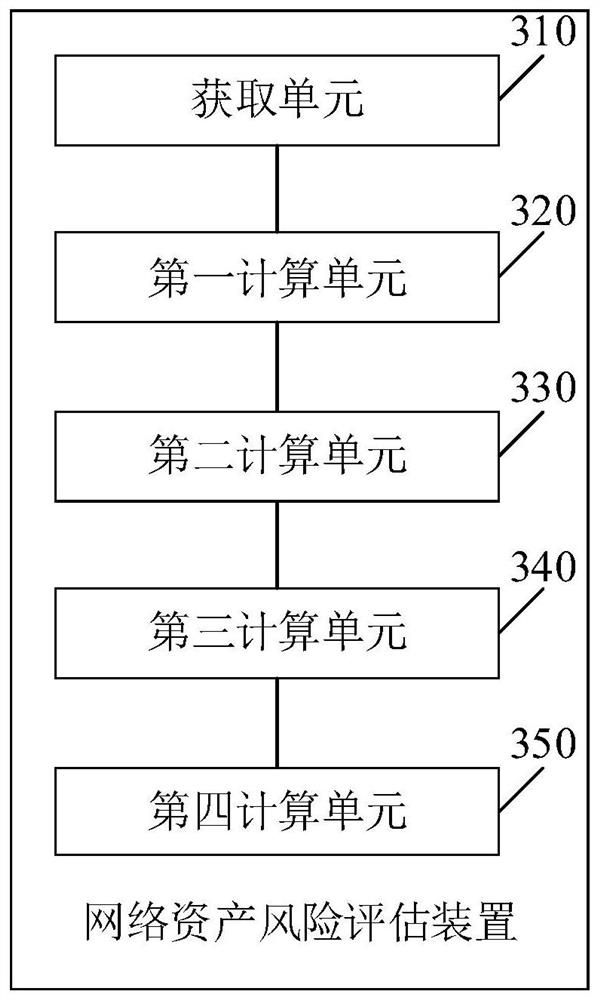
[0147] Please see image 3 , image 3 It is a schematic structural diagram of a network asset risk assessment device provided in the embodiment of this application. Such as image 3 As shown, the network asset risk assessment device includes:
[0148] An acquisition unit 310, configured to acquire various types of probe data in the network, asset data of target network assets, and a current assessment time period;
[0149] The first calculation unit 320 is configured to calculate the asset value of the target network asset according to various types of probe data and asset data;
[0150] The second calculation unit 330 is configured to calculate the vulnerability risk value of the target network asset according to various probe data and asset data;
[0151]The third calculation unit 340 is configured to calculate the threat event risk value of the target network asset according to the current evaluation time period, various probe data and asset data;
[0152] The fourth c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com