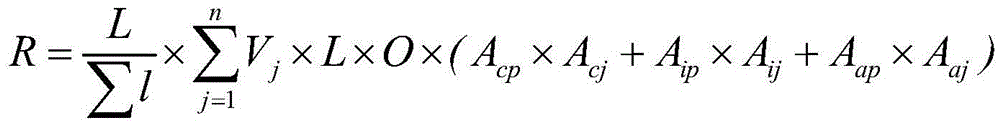Information system security performance assessment method
An information system and safety performance technology, applied in transmission systems, digital transmission systems, electrical components, etc., can solve problems such as inability to assess risks, inability to intuitively respond to risks, and inability to grasp the information risks of information systems in real time, and achieve evaluation results Intuitive and reliable, simple and scientific calculation method
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] Such as figure 1 As shown, it is a flow chart of the method of the present invention: the method for evaluating the security performance of the information system provided by the present invention includes the following steps:
[0040] S1. Grade and score the security level, operation and maintenance level, confidentiality, integrity and availability of the information system according to the importance of the information system;
[0041] The information system and the grading score of the information system are shown in Table 1:
[0042] Table 1 Information system classification table
[0043]
[0044]
[0045] S2. Classify the importance of the assets under the information system, and grade and score the confidentiality, integrity and availability of the assets;
[0046] Table 2 Classification and Confidentiality, Integrity and Availability Scoring Table of Assets Subordinate to Information System
[0047]
[0048]
[0049] S3. Carry out information se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com