Real-time identity authentication method based on mobile phone, bluetooth and two-dimensional barcode
A two-dimensional barcode, identity authentication technology, applied in the direction of user identity/authority verification, computer parts, character and pattern recognition, etc., can solve the problems of authentication information interception, easy imitation and stealing of authentication features, etc., to achieve high security , the effect of reducing the ambiguity of the connection object and reducing the possibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
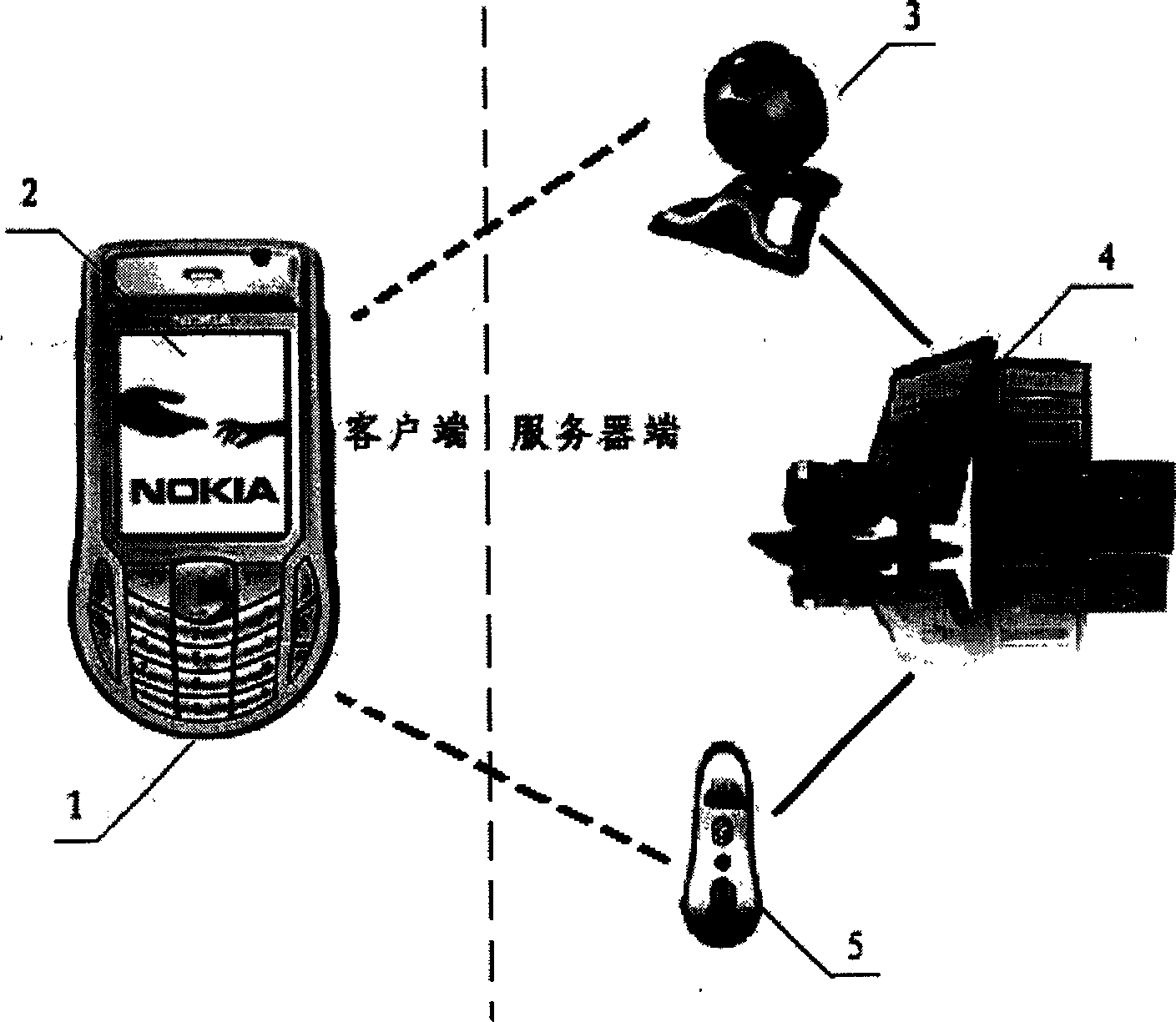
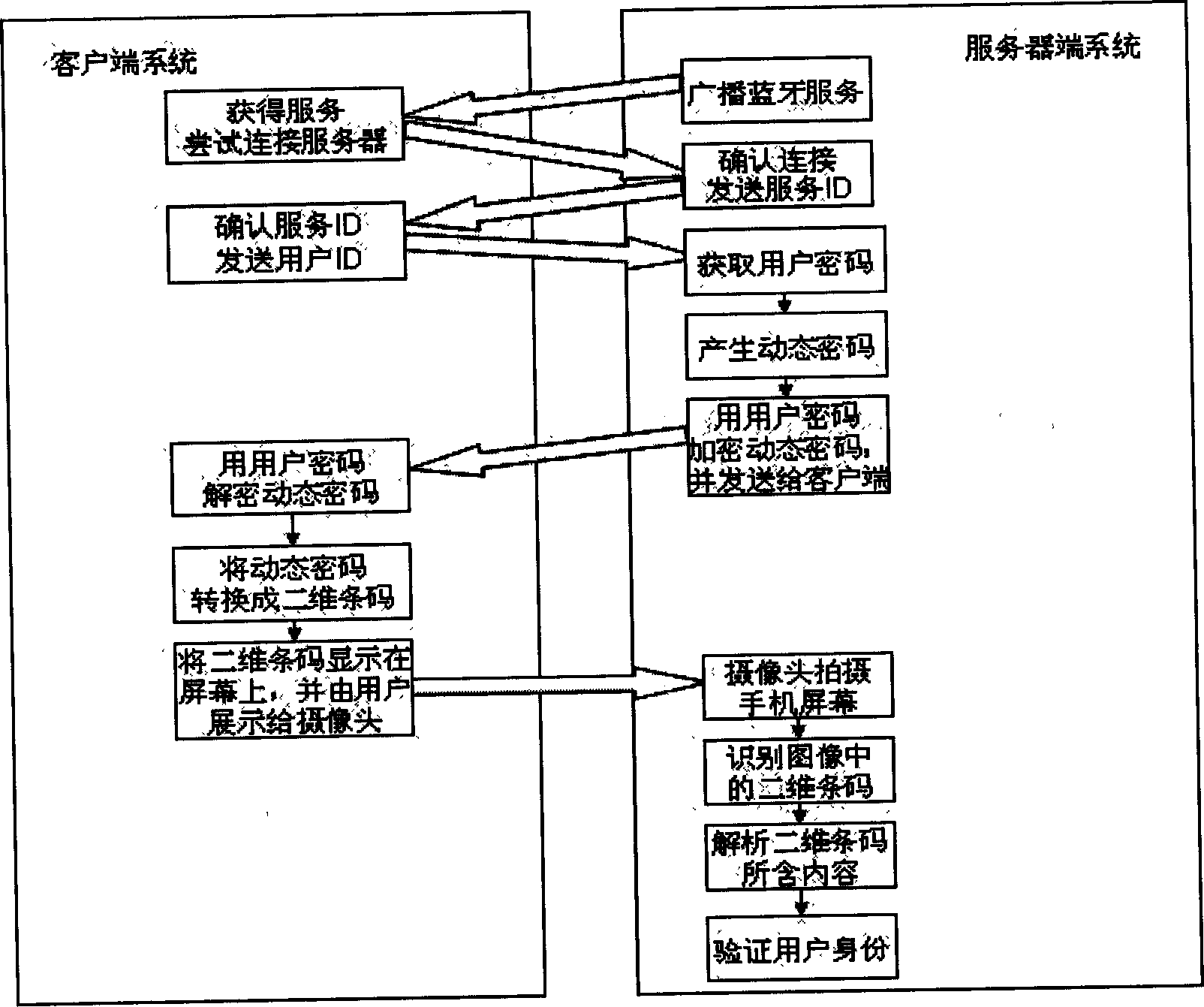
[0067] Such as Figure 11 , which provides an embodiment of the present invention used in the access control system.
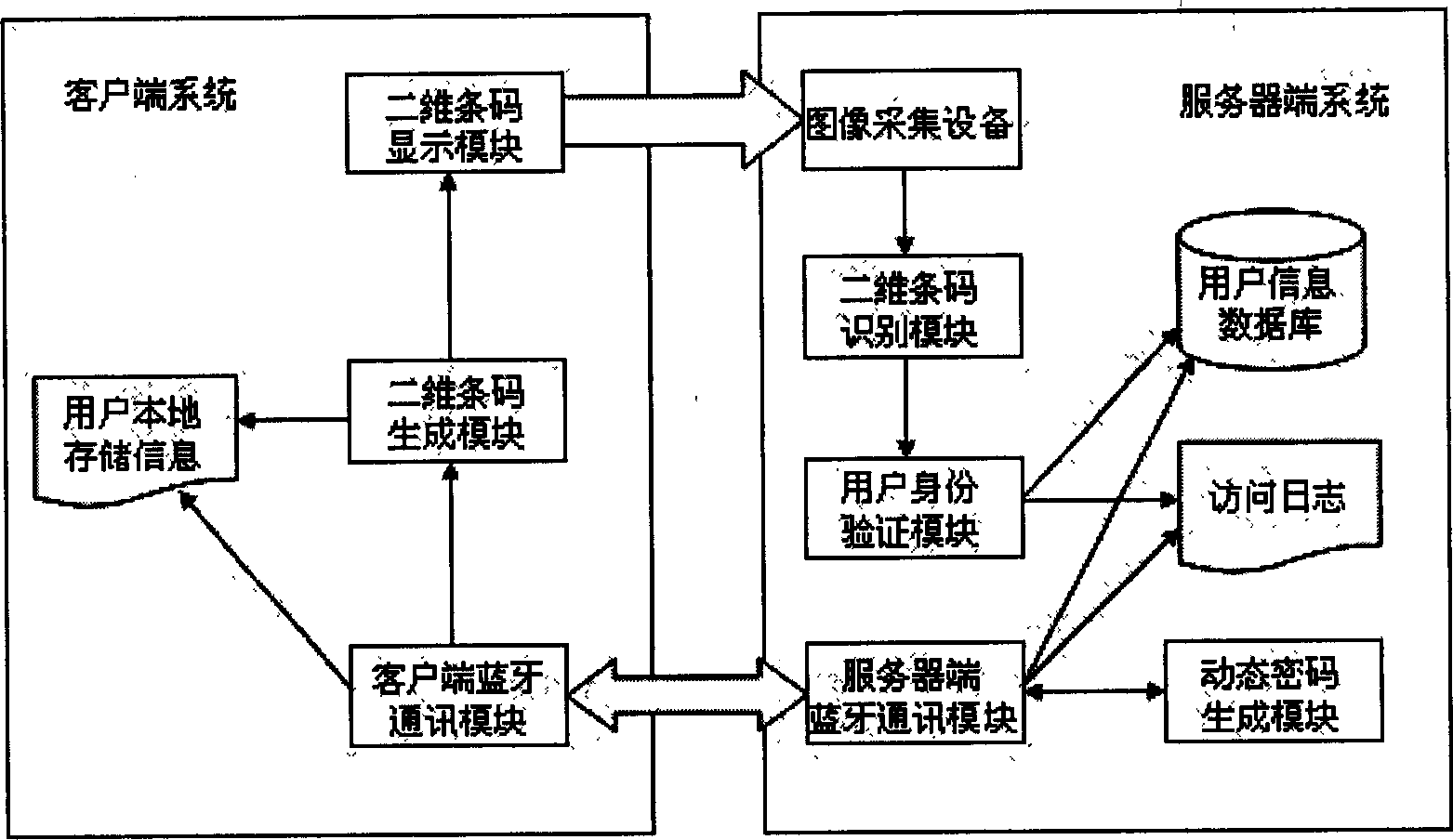
[0068] The hardware device on the server side of the access control system consists of a PC that can run WindowsXP SP2 or above, a Bluetooth communication module compatible with WindowsXP SP2 Bluetooth driver, and a camera. The server software of the identity authentication system is installed on the PC.
[0069] The client of this access control system is any mobile phone that supports Bluetooth and has a screen resolution greater than 50×50, including smart phones running Symbian, Windows, and Linux systems, CDMA mobile phones that support Brew platform, and other phones that support JSR82 API, that is, Java APIs A mobile phone for Bluetooth Wireless Technology (JABWT). The client program corresponding to the corresponding platform needs to be installed on the mobile phone. This example takes a mobile phone using the Symbian system as an example.
[0070...
Embodiment 2
[0077] Such as Figure 12 , provides an embodiment of the present invention using a shopping mall consumption system connected with a bank. Its process is similar to the above-mentioned embodiment 1, the difference is:
[0078] The user registers with the bank and obtains the service ID number from the bank. The service ID number of the consumer system is only used to distinguish different banks. The same bank has the same service ID number in the consumer systems of all shopping malls. Users can choose the bank service they want to use on the mobile phone.
[0079] When the mall verifies user information, it obtains the MD5-encrypted static key from the bank server through the bank network, that is, the above-mentioned string B. The mall does not keep relevant information about users. If the information verification is successful, the consumption activity is completed through the bank network.
[0080] Cancellation can be canceled through various methods such as online ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com