Mobile phone and Bluetooth key signature verification ciphertext communication method
A technology of signature verification and communication method, applied in the service field, can solve the problems of inconvenience or loss of mobile phone users, high cost of sd card digital authentication, leakage and other problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
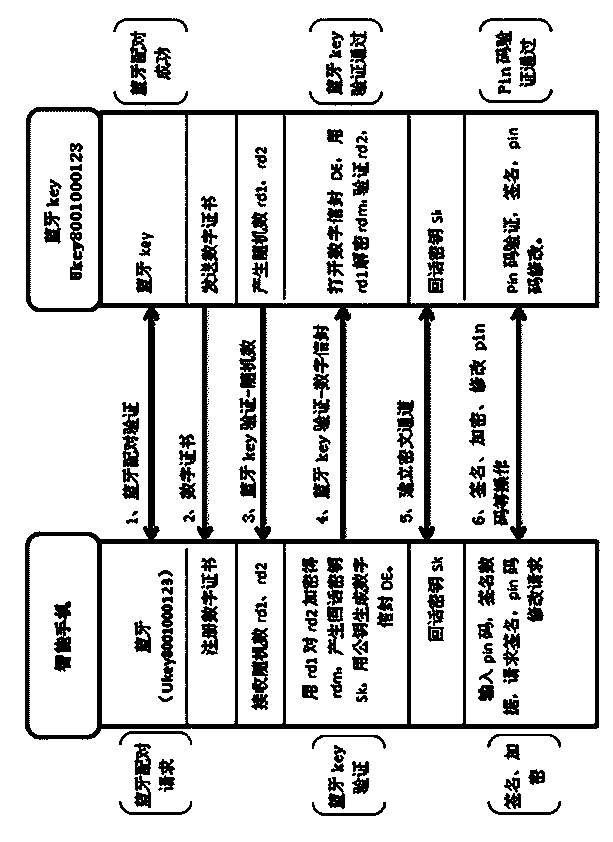
[0022] The following describes the content of the present invention through a simple mobile phone and Bluetooth key authentication process, but it does not constitute a limitation to the present invention.
[0023] according to figure 1 The authentication establishment process between the mobile phone and the Bluetooth key shown:
[0024] Step 1. The mobile phone user opens the Bluetooth settings, searches for the Bluetooth device, and finds the Bluetooth ukey device name (such as Ukey8001000123). If the Bluetooth device is not paired, please pair it. If it is already paired, the Bluetooth channel of the phone and the Bluetooth key has been connected.
[0025] Step 2: The mobile phone user obtains the Bluetooth key user certificate and registers it in the mobile browser.
[0026] Step 3: The mobile phone user automatically obtains the random numbers rd1 and rd2 of the Bluetooth key, and then encrypts rd2 with rd1 to obtain rdm.
[0027] Step 4, the mobile phone automatically generates ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com