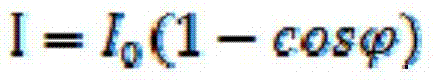Patents
Literature
54results about How to "Simple and flexible implementation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
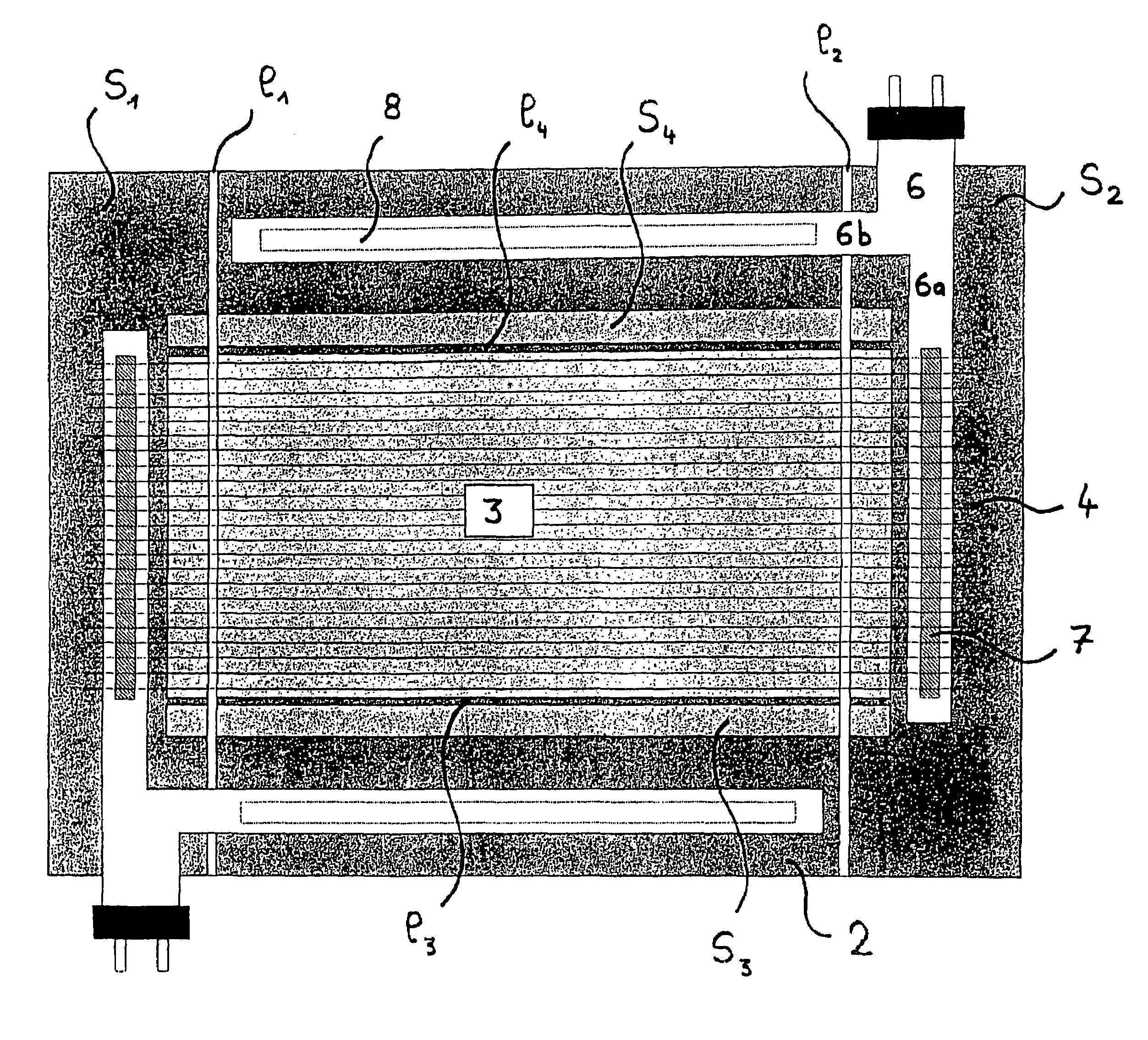
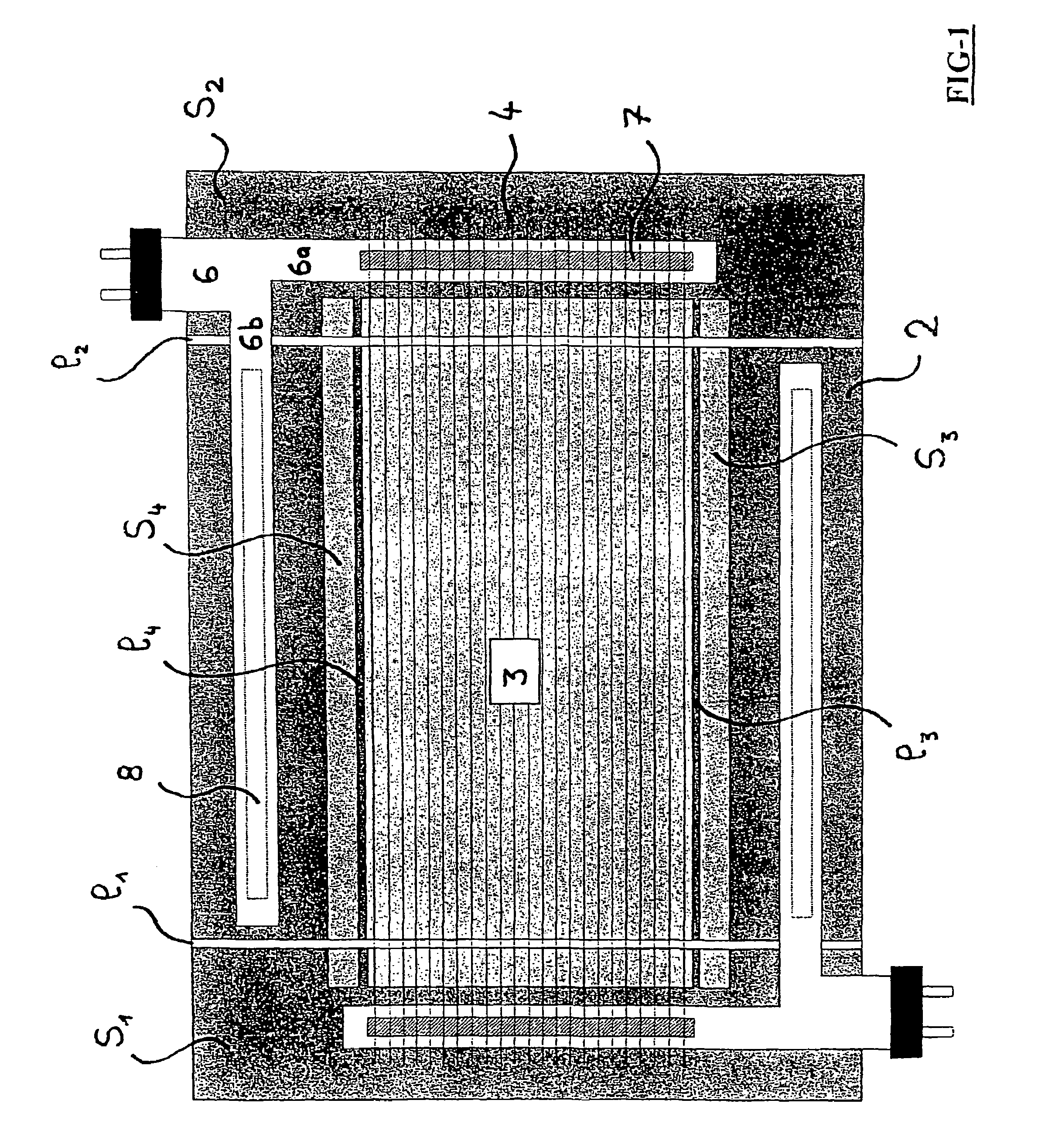
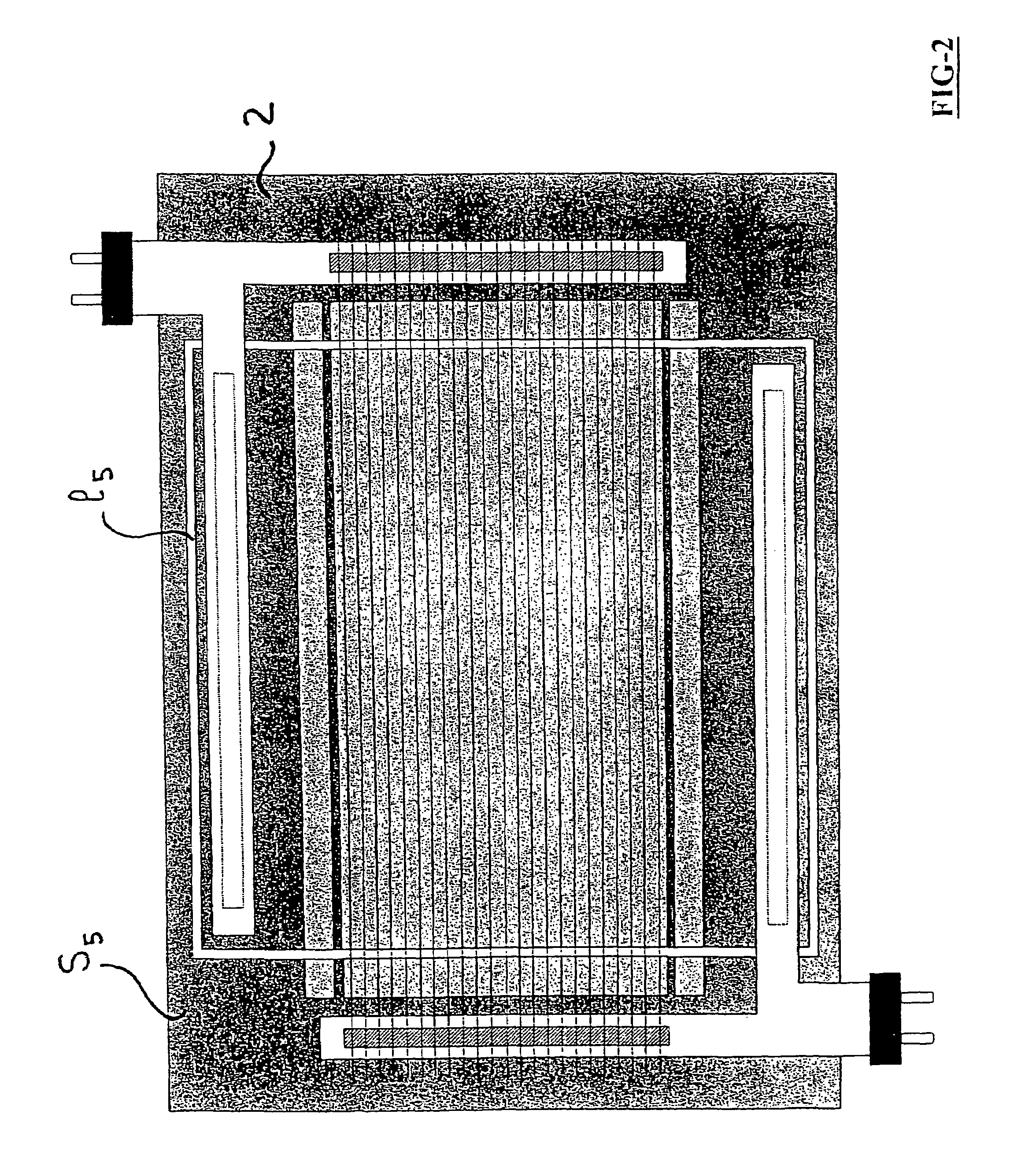
Electrochemical device such as electrochromic or photovoltaic device and electrical connection means thereof
InactiveUS7230748B2Smooth connectionSimple and flexible implementationElectrode carriers/collectorsSecondary cellsElectricityOptical property
An electrochemical device, especially an electrically controllable system with variable energy and / or optical properties or a photovoltaic device, including at least one substrate carrying an electroactive stack of layers arranged between a lower electrode and an upper electrode. Each electrode includes at least one electroconductive layer in electrical contact with at least one current lead. The current leads are arranged outside the region of the carrier substrate that is covered by the stack of electroactive layers.
Owner:SAINT-GOBAIN GLASS FRANCE
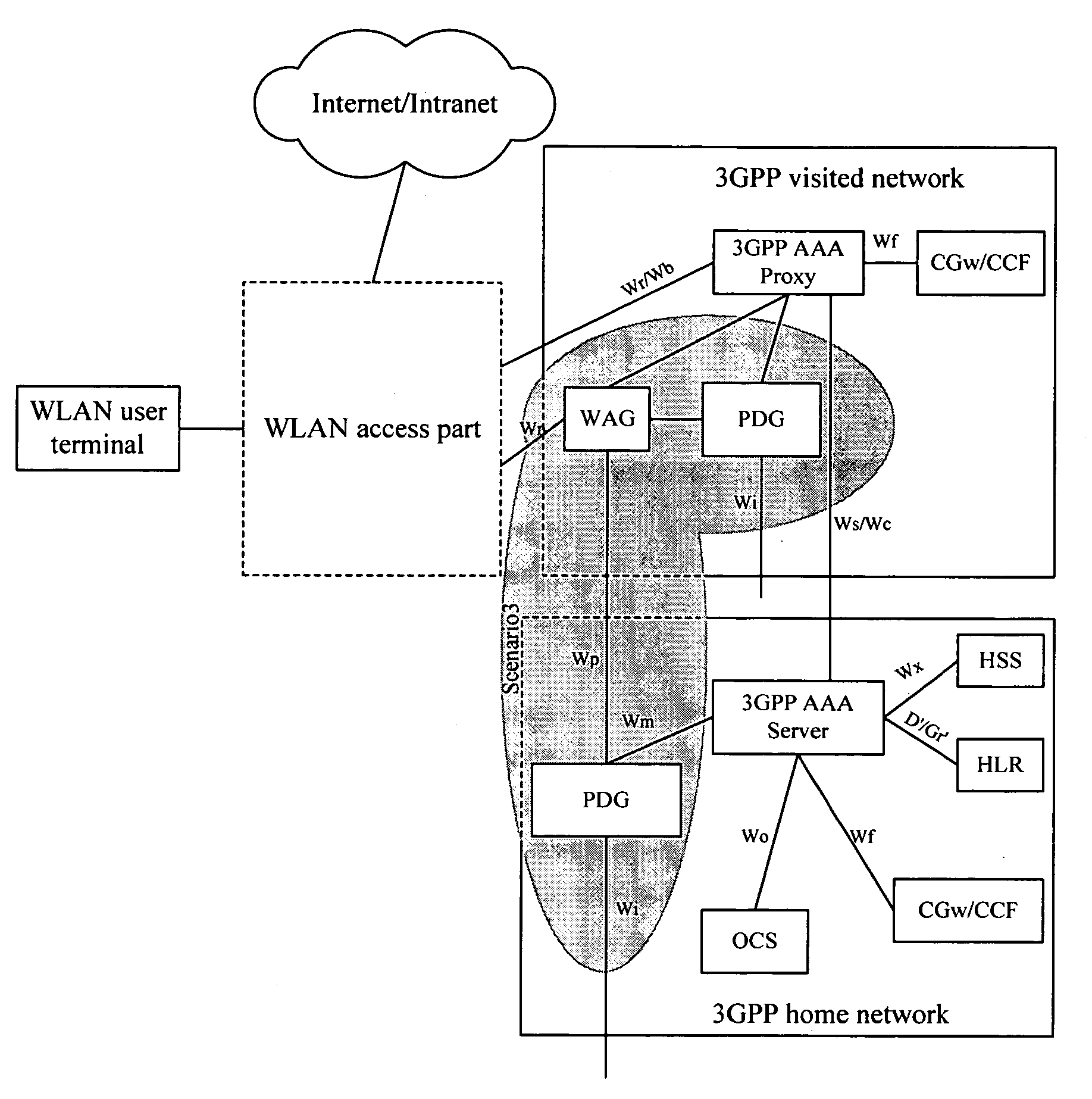
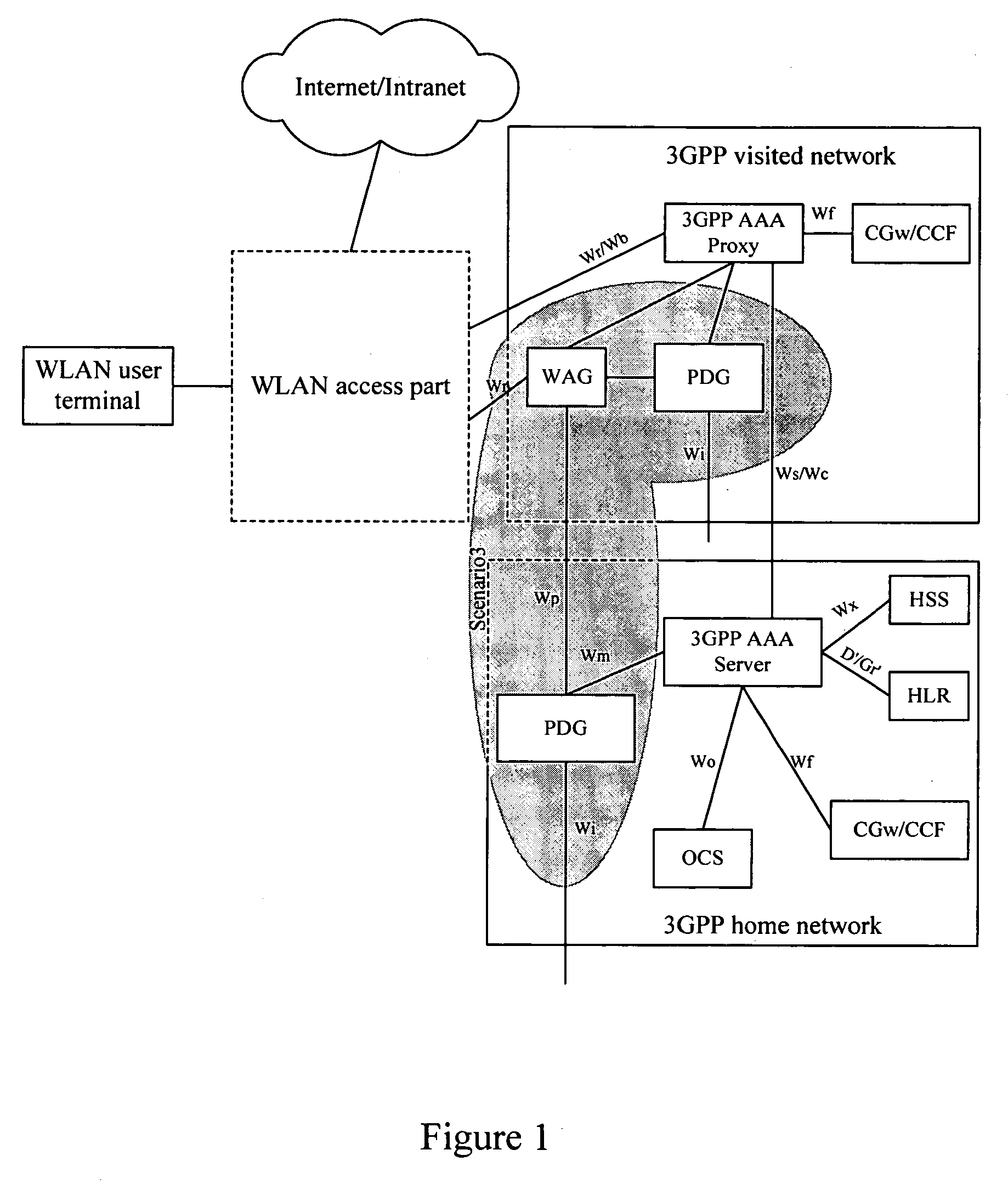
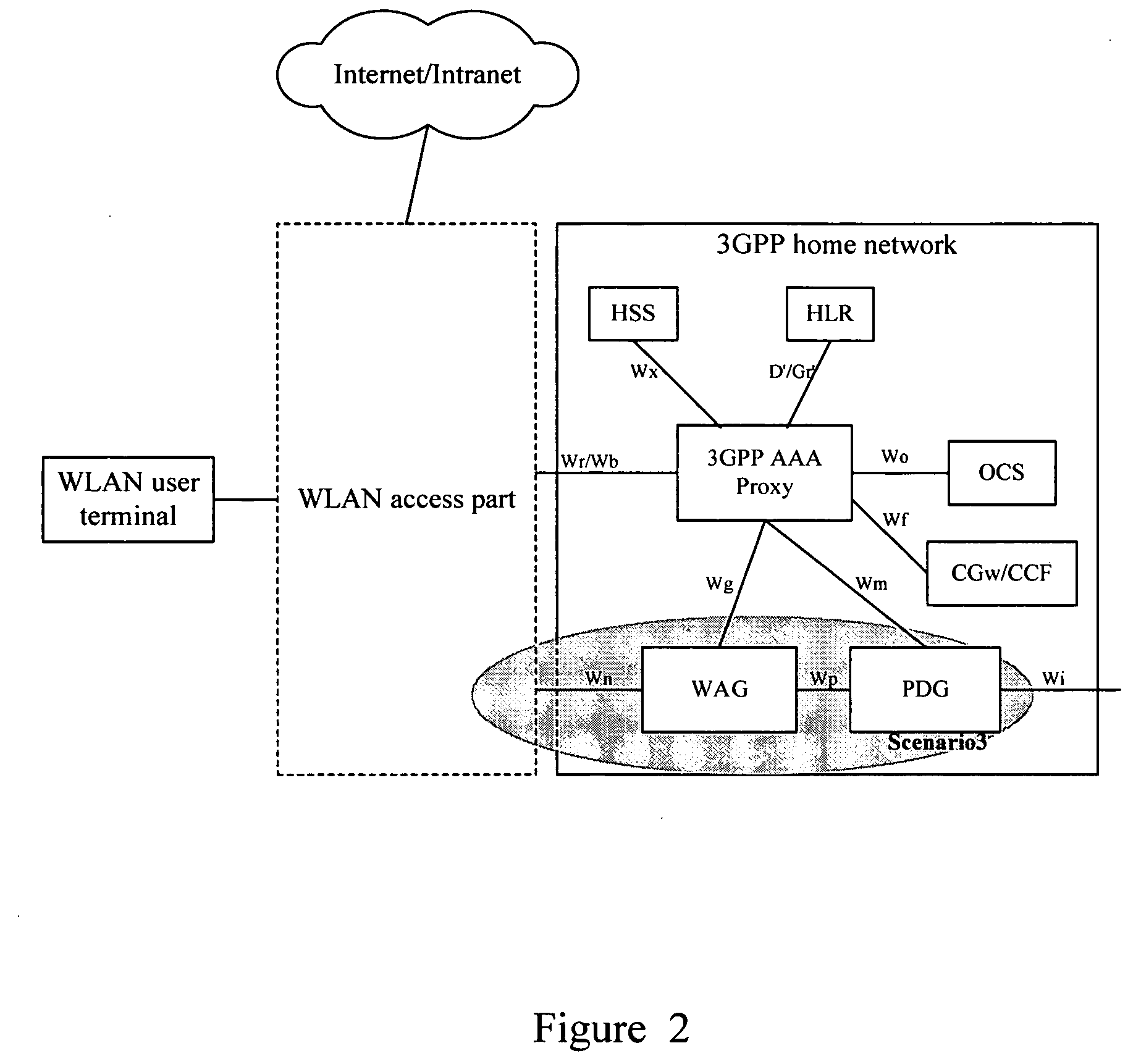
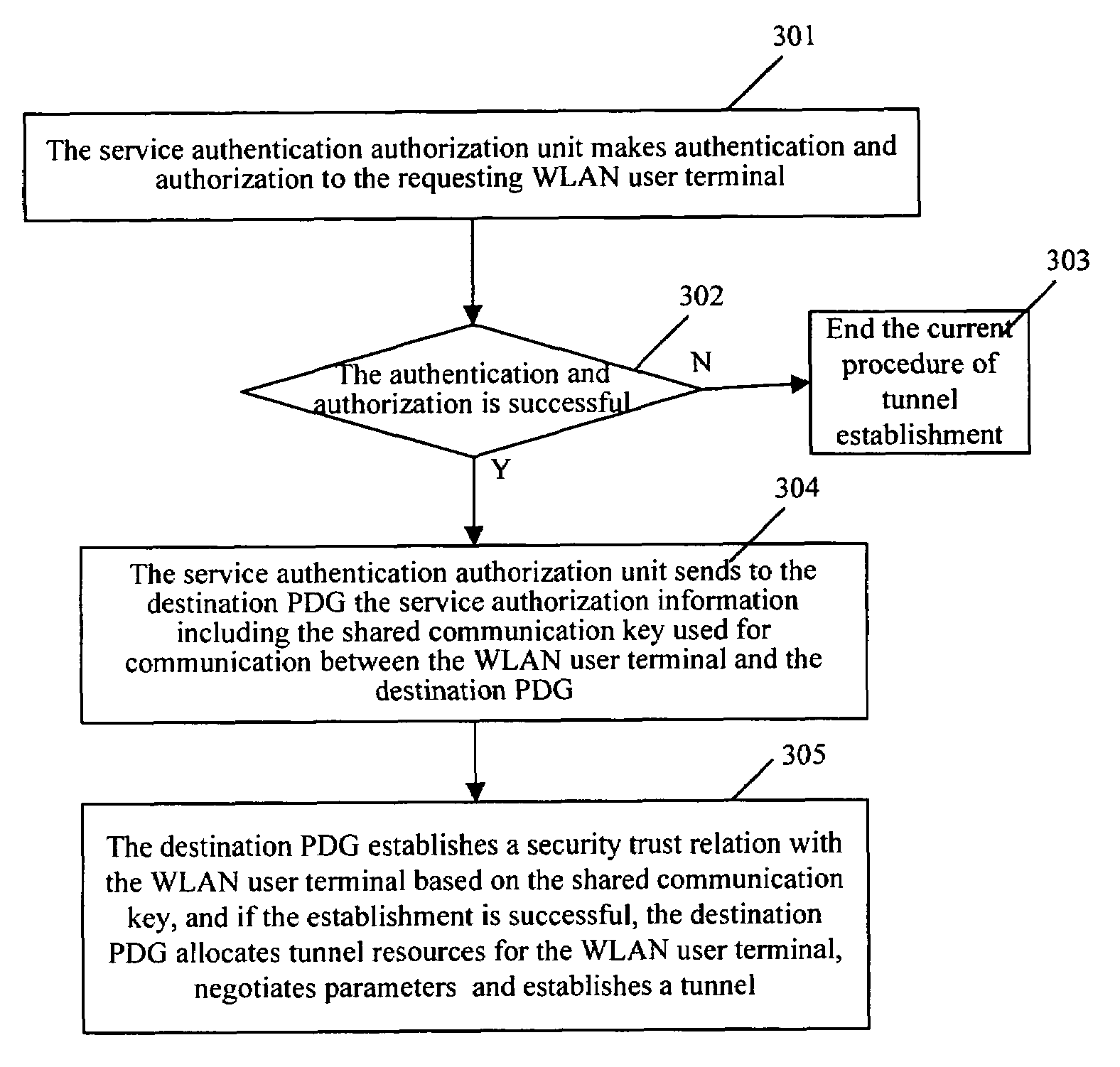
Method for establishment of a service tunnel in a WLAN
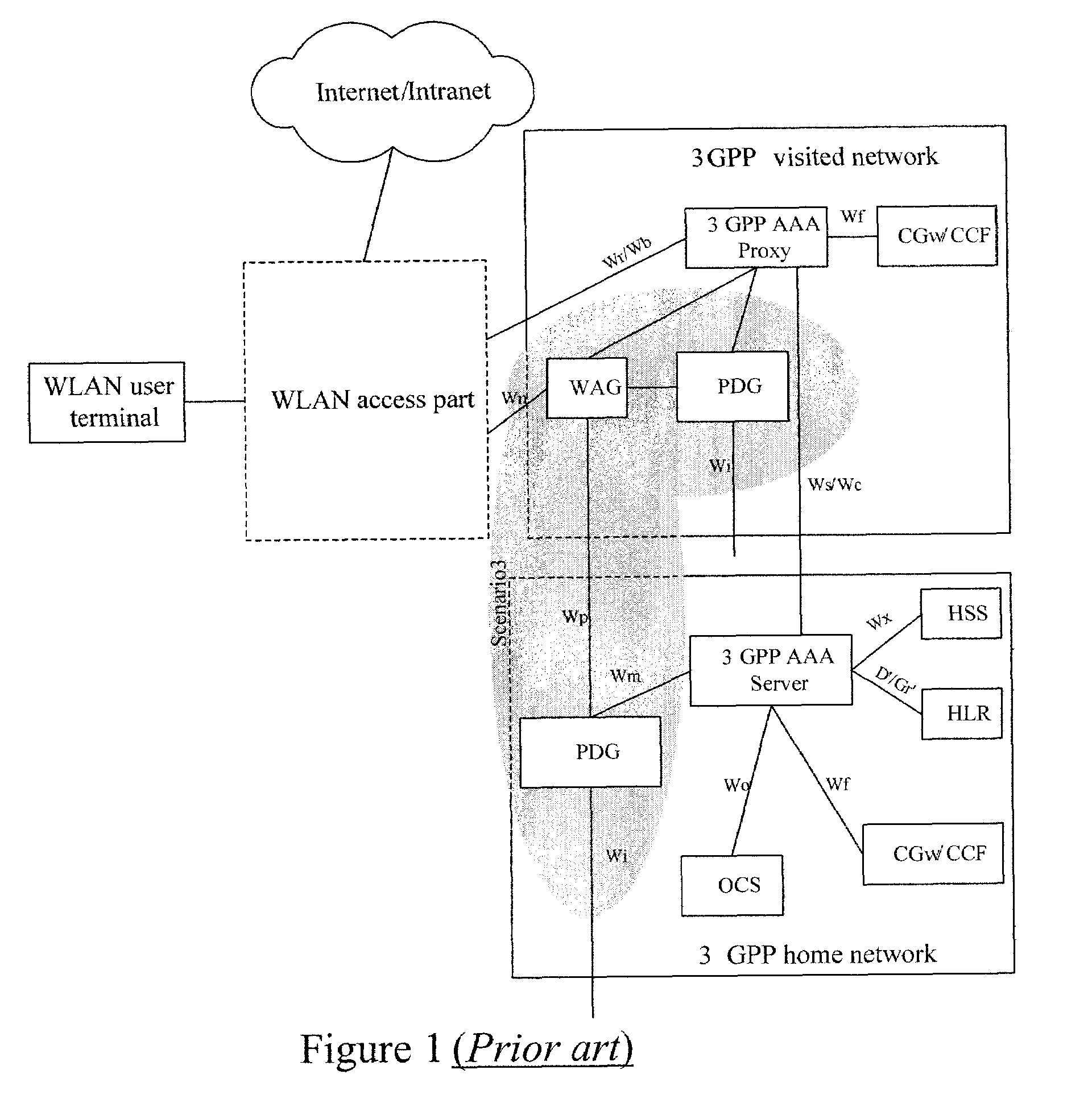
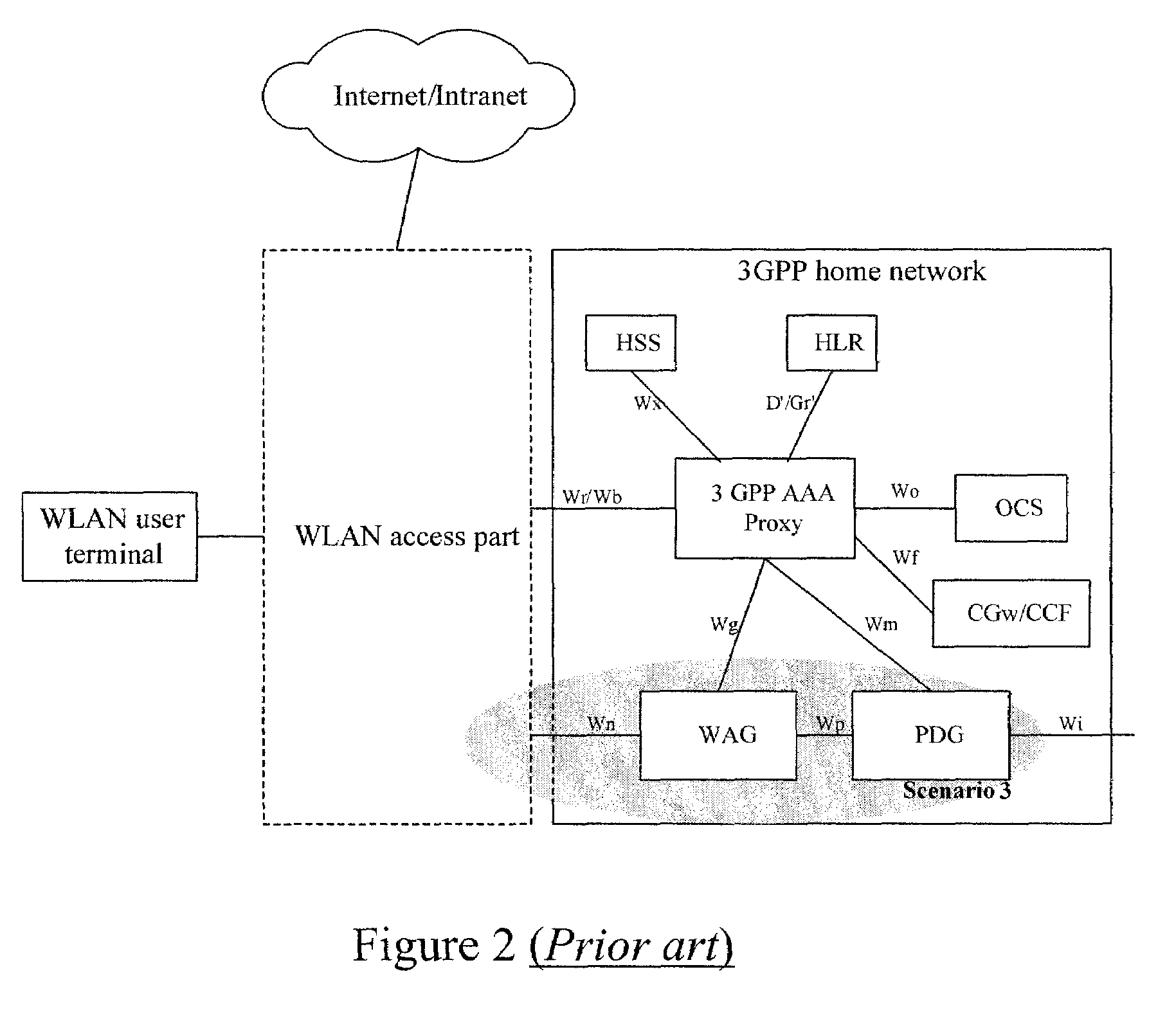
ActiveUS20060104234A1Simple and flexible implementationUser identity/authority verificationNetwork topologiesWireless lanPacket data gateway
Disclosed herein is a method for the establishment of a service tunnel in a wireless local area network (WLAN). The method includes a service authentication authorization unit making authentication and authorization to a WLAN user terminal currently requesting a service, and judging whether the authentication and authorization is successful. If successful, the method includes generating service authorization information that includes a shared communication key used for communication between the WLAN user terminal and a destination packet data gateway (PDG), and otherwise ending the procedure. The method further includes the service authentication authorization unit sending to the destination PDG the generated service authorization information including the shared communication key, and the destination PDG, according to the shared communication key, establishing a trust relation with the WLAN user terminal through negotiation with the WLAN user terminal. If the establishment of the trust relation is successful, the destination PDG allocates tunnel resources for the WLAN user terminal, negotiates parameters and then establishes a tunnel with the WLAN user terminal, and otherwise, ends the procedure. As a result, a secured service data tunnel may be established between the user terminal and the PDG.
Owner:HUAWEI TECH CO LTD
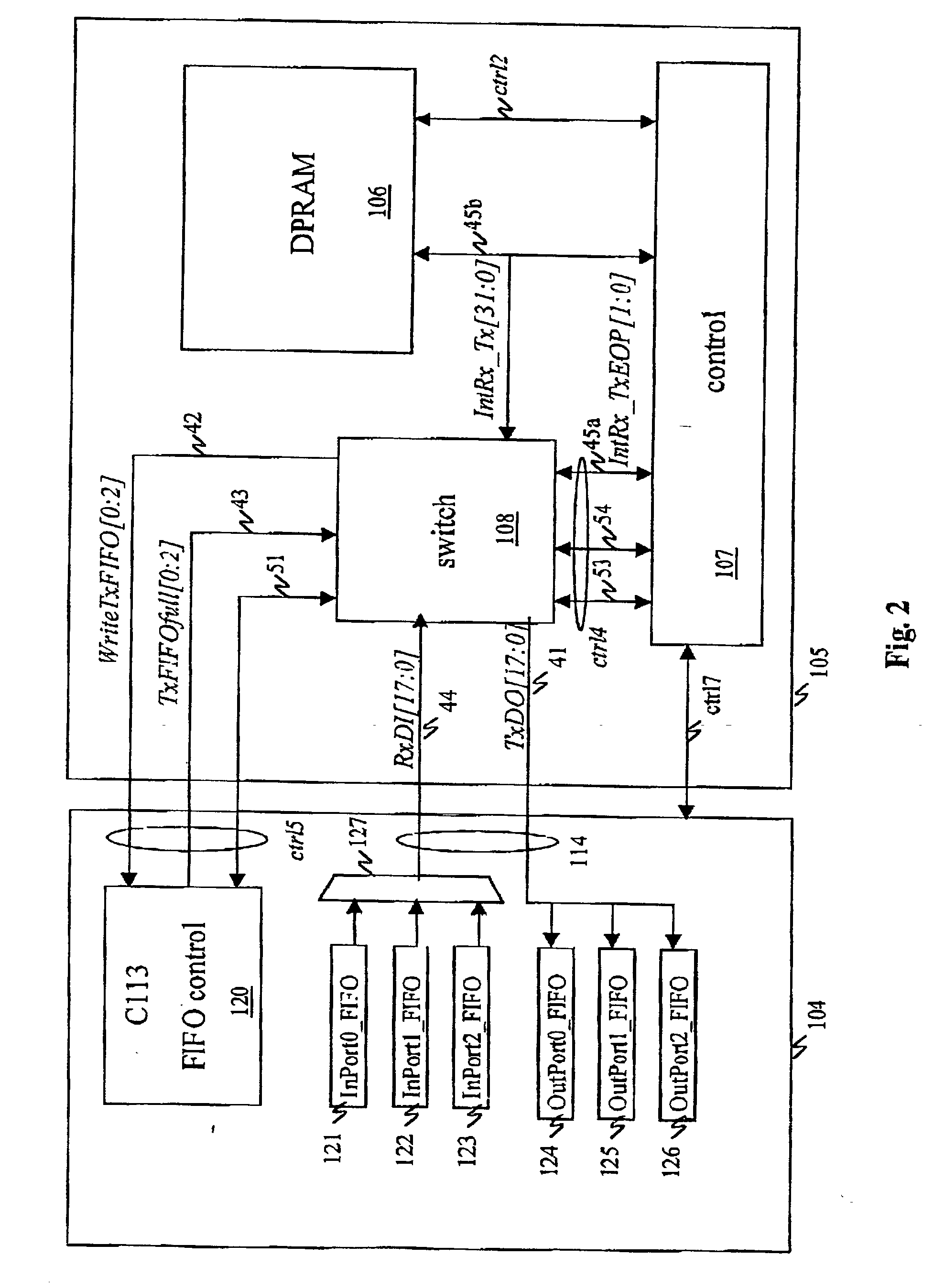
Device and method for transmission in a switch
InactiveUS20020126657A1Easy to implementLow costSpecial service provision for substationMultiplex system selection arrangementsInterconnectionEngineering
A protocol data unit switching implements switching means used for the selective interconnection of a transmitter port and at least one receiver port selected from among at least two receiver ports by means of at least one internal bus, each of the protocol data units being constituted by at least one piece of elementary data. The switching implements a synchronization mechanism defining time slots, known as connection cycles, on at least one of said internal buses; a mechanism for the allocation of at least one of said connection cycles to each of the selected receiver ports; and a mechanism for the writing of at least one piece of elementary data in the allocated connection cycle or cycles so as to enable the broadcasting of elementary data to said selected receiver ports.
Owner:CANON KK
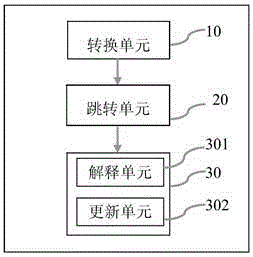
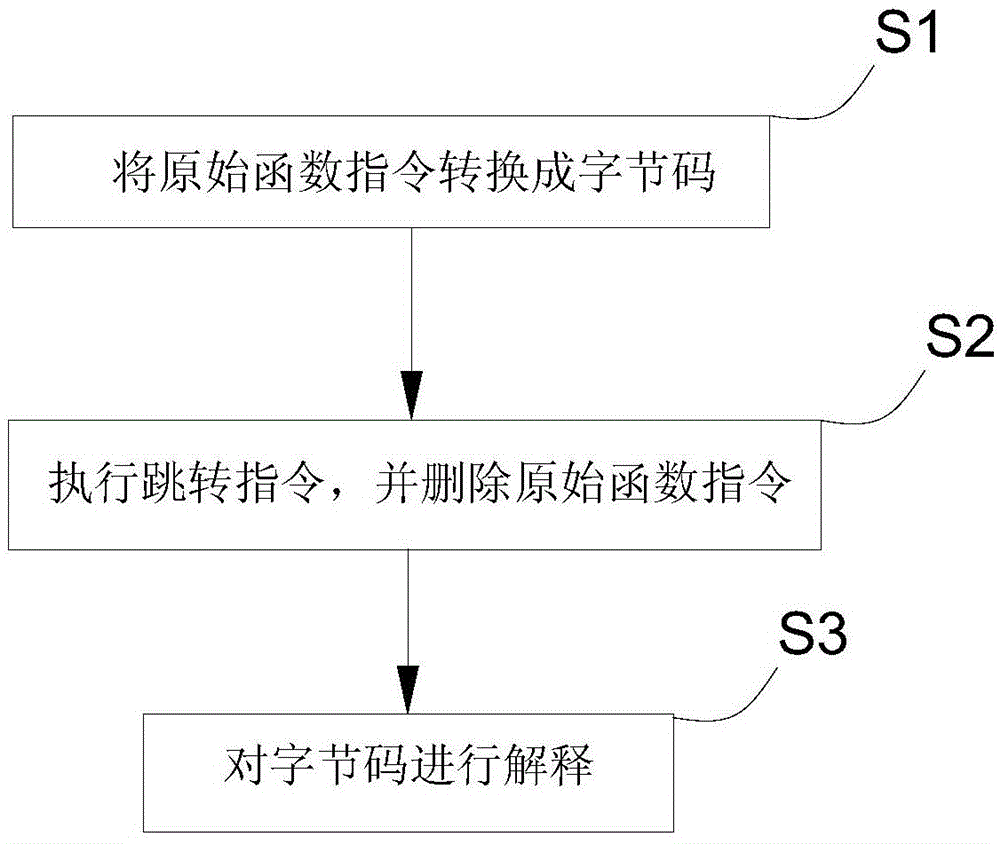
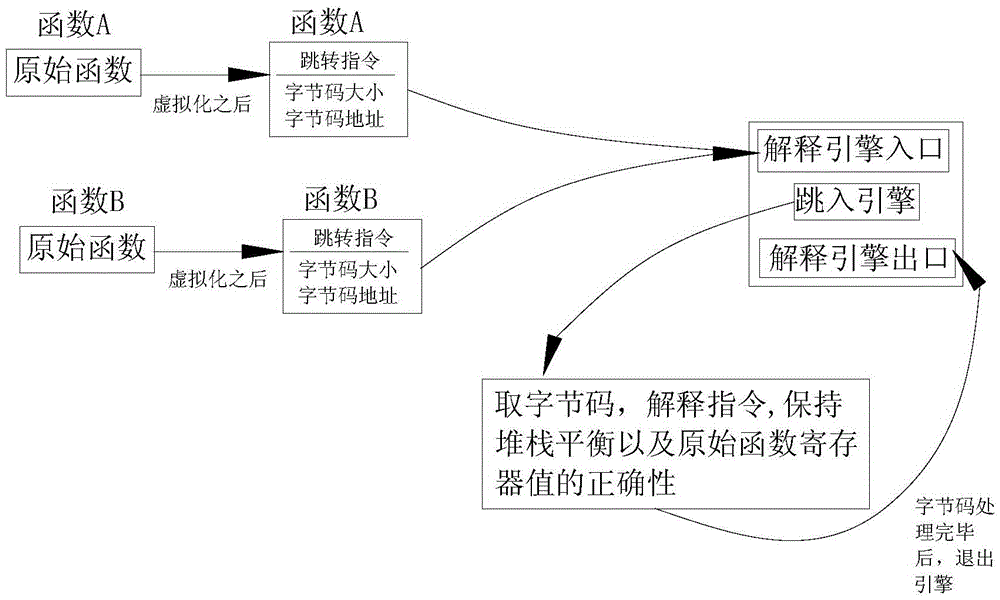
ELF file protection method and system based on ARM instruction virtualization
InactiveCN105608346AOrganizational forms are ever-changingSimple and flexible implementationProgram/content distribution protectionVirtualizationProcessor register
The invention discloses an ELF file protection method and system based on ARM instruction virtualization. The method includes the steps that an original function instruction is converted into bytecodes; a register and stack information of an original function are stored, a jump instruction is added, and other instructions are deleted; the jump instruction is executed, and the bytecodes are interpreted by jumping to an interpreting engine. In this way, the original function instruction is converted into the bytecodes in a virtualization mode, the difficulty of a cracker is increased, and the file protection strength is improved.
Owner:BEIJING QIHOO TECH CO LTD +1
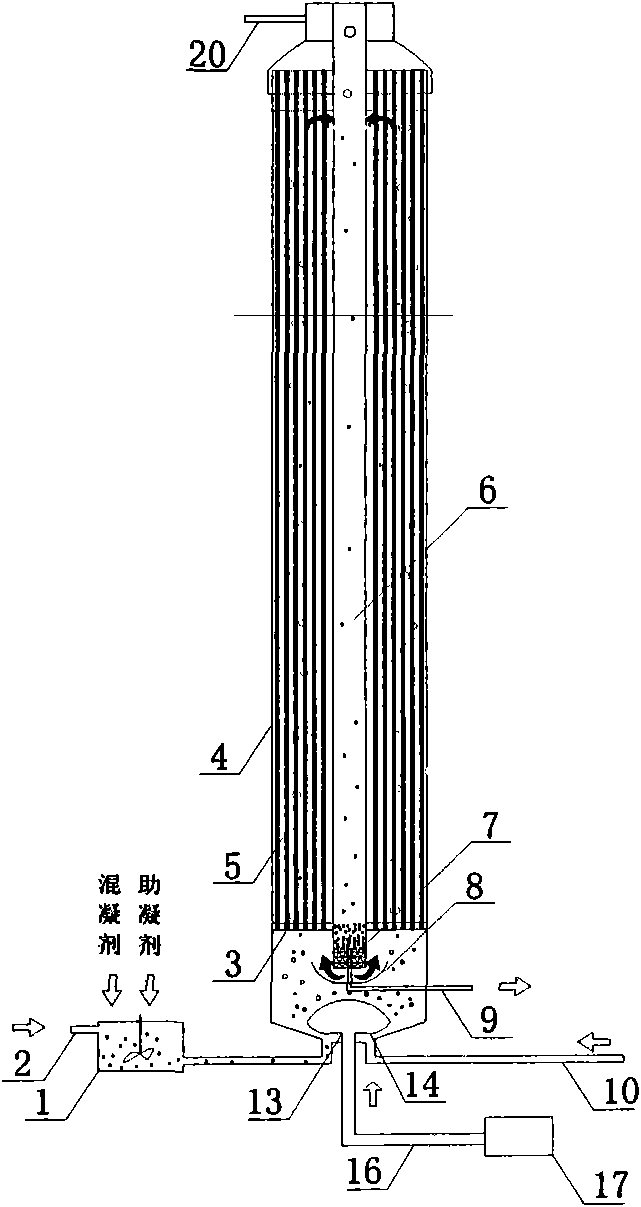
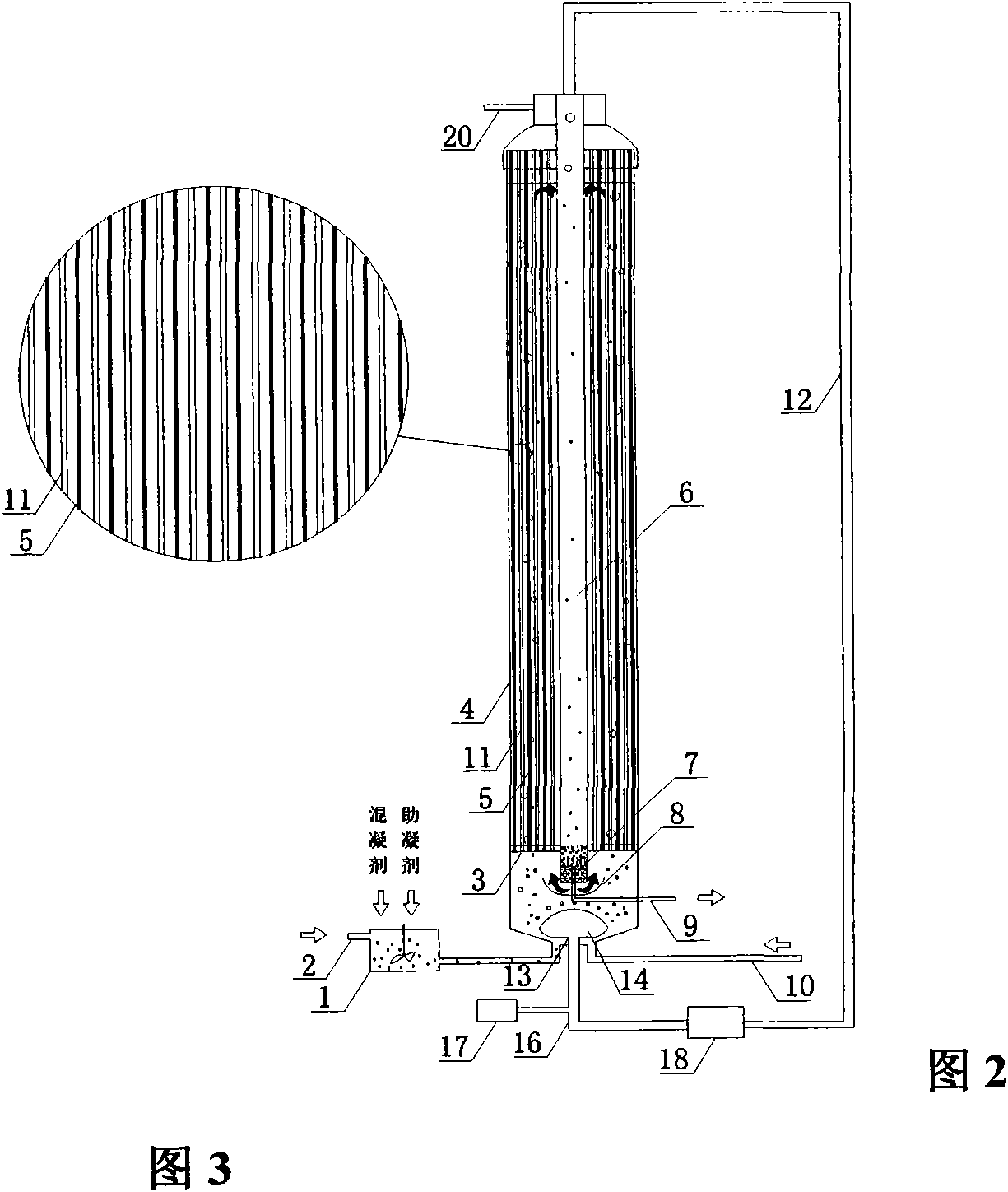
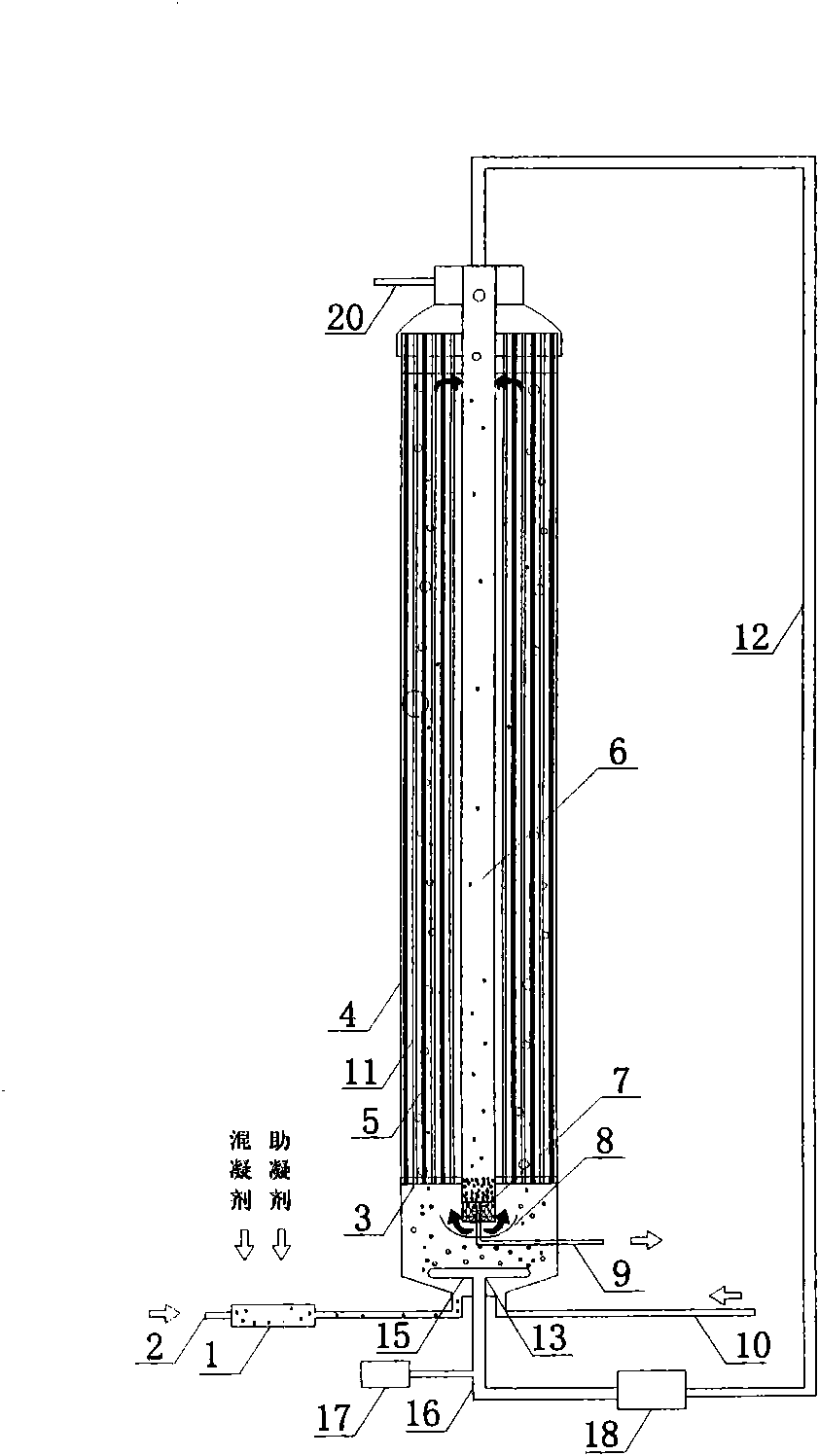
Enhanced coagulation-gas stripping-membrane integration method and device for lightening membrane pollution
InactiveCN101774731AReduce cloggingImprove processing efficiencyTreatment using aerobic processesWater/sewage treatment bu osmosis/dialysisFiltrationEngineering
The invention discloses an enhanced coagulation-gas stripping-membrane integration method for lightening membrane pollution. In the method, a coagulating agent and a coagulant aid are added into raw water and undergo enhanced coagulation reaction by applying hydraulic condition, and airflow circulation and lift treatment is performed while an external pressure hollow fiber membrane component is used for filtration. The invention also discloses an integration device designed according to the method. Through the technical measures of throwing the coagulating agent and the coagulant aid into the raw water, positioning gas stripping type aeration treatment under the filtering of the external pressure hollow fiber membrane component and the like, the method improves the pollutant removal rate and the water treatment effect, greatly lightens the membrane pollution, saves energy consumption of membrane component operation, prolongs the operating cycle of the membrane component, shortens the cleaning time, reduces the back washing cost, has small occupied area, low investment cost and simple and flexible implementation, is applicable to water treatment for large cities, and is also applicable to vast cities and towns and rural regions with imperfect water treatment process and small treatment scale.
Owner:SICHUAN UNIV
Method for establishment of a service tunnel in a WLAN
ActiveUS7450554B2Simple and flexible implementationUser identity/authority verificationNetwork topologiesPacket data gatewayAuthorization
Disclosed herein is a method for the establishment of a service tunnel in a wireless local area network (WLAN). The method includes a service authentication authorization unit making authentication and authorization to a WLAN user terminal currently requesting a service, and judging whether the authentication and authorization is successful. If successful, the method includes generating service authorization information that includes a shared communication key used for communication between the WLAN user terminal and a destination packet data gateway (PDG), and otherwise ending the procedure. The method further includes the service authentication authorization unit sending to the destination PDG the generated service authorization information including the shared communication key, and the destination PDG, according to the shared communication key, establishing a trust relation with the WLAN user terminal through negotiation with the WLAN user terminal. If the establishment of the trust relation is successful, the destination PDG allocates tunnel resources for the WLAN user terminal, negotiates parameters and then establishes a tunnel with the WLAN user terminal, and otherwise, ends the procedure. As a result, a secured service data tunnel may be established between the user terminal and the PDG.
Owner:HUAWEI TECH CO LTD
Method for grouting, filling and compacting goaf filling body from roof roadway
A method for grouting, filling and compacting a goaf filling body from a roof roadway is suitable for being used in a waste filling goaf mine. The method comprises the steps that every time a coal face is tunneled for L meters, a set of grouting drill holes (4) is formed in a goaf in the roof roadway (3) in the direction consistent with that of the coal face, the height of a diversion fissure zone hl is calculated according to the equivalent mining height hd of the filled goaf, and component drilled holes are filled. The method has the advantages of being easy and flexible to implement, small in interference on the prior art, low in cost and good in subsidence reduction effect, and meanwhile compared with ground grouting, the method has small influence on ground production activities, and is suitable for being implemented in the areas with dense buildings.
Owner:CHINA UNIV OF MINING & TECH
Method for processing ultra-pure ferrite stainless steel by using ladle refining furnace to control carbon and nitrogen content
The invention discloses a carbon and nitrogen content control method of processing super ferrite stainless steel with ladle refining furnace, comprising the procedures that, 1) during smelting ferrite stainless steel, arc furnace, induction furnace or converter are used for tapping, and argon oxygen decarburization furnace or vacuum oxygen decarburization furnace is used to reach the demand of steel liquid components of super ferrite stainless steel. 2) Ladle refinement: during power-on process, by blowing the mixture of coke oven gas and argon gas through the central hole of graphite electrodes, hydrogen containing plasma arc is formed at the lower end of graphite electrodes to achieve decarburization and denitrogen of liquid steel and guarantee the cleanness of liquid steel; among which the mixture proportion of coke oven gas and argon gas is between 95:5 and 5:95, with the pressure range between 0.02 and 10 MPa, the flow range of mixture gases between 0.01 and 50 Nm3 / h; 3) During power-off process: gases blowing to the central hole of graphite electrodes are suspended; ladles are hung away from ladle refining furnace after components and temperature of steel liquid meet the requirement, and sent to the next procedure for casting.
Owner:BAOSHAN IRON & STEEL CO LTD +1
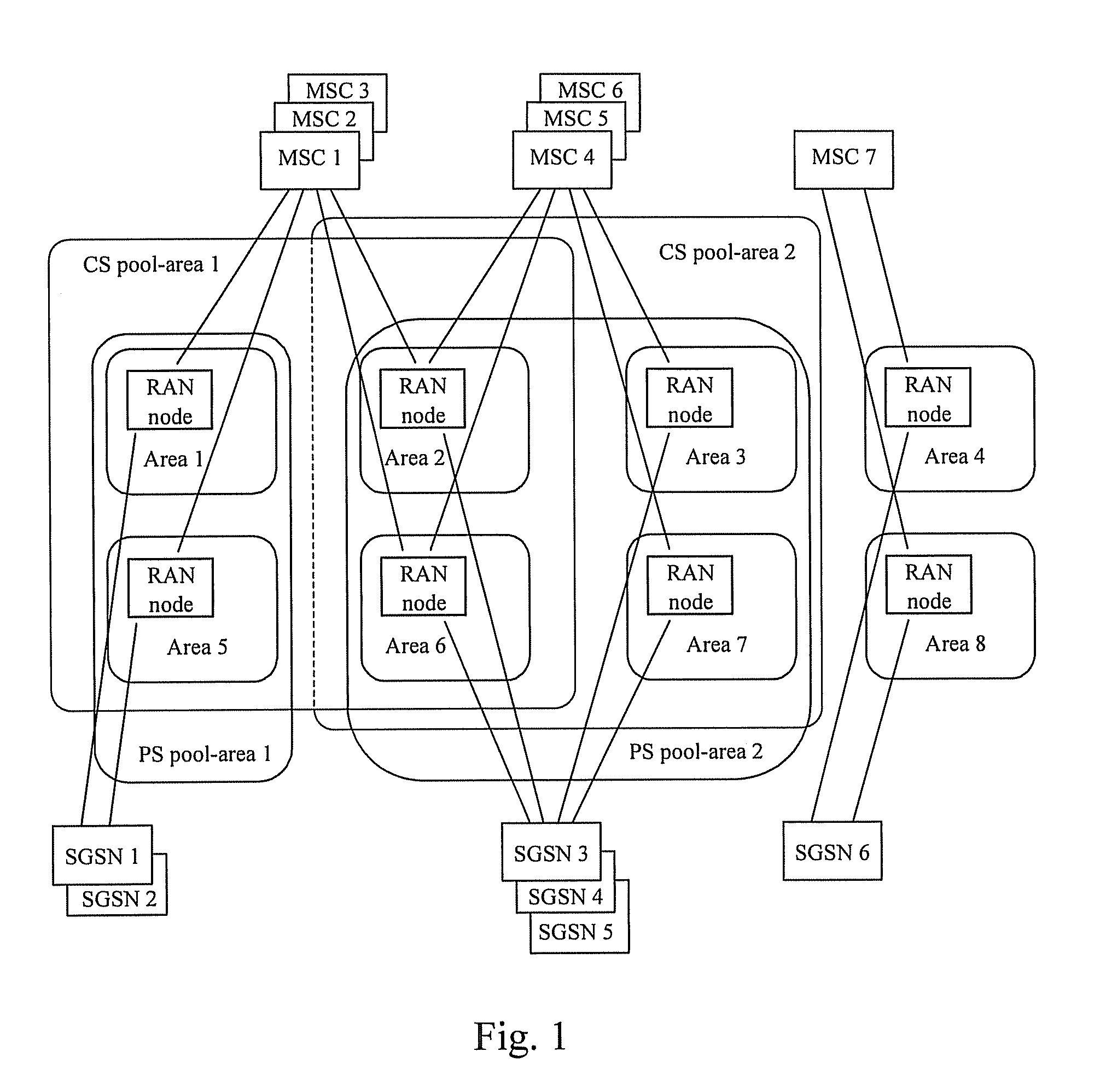
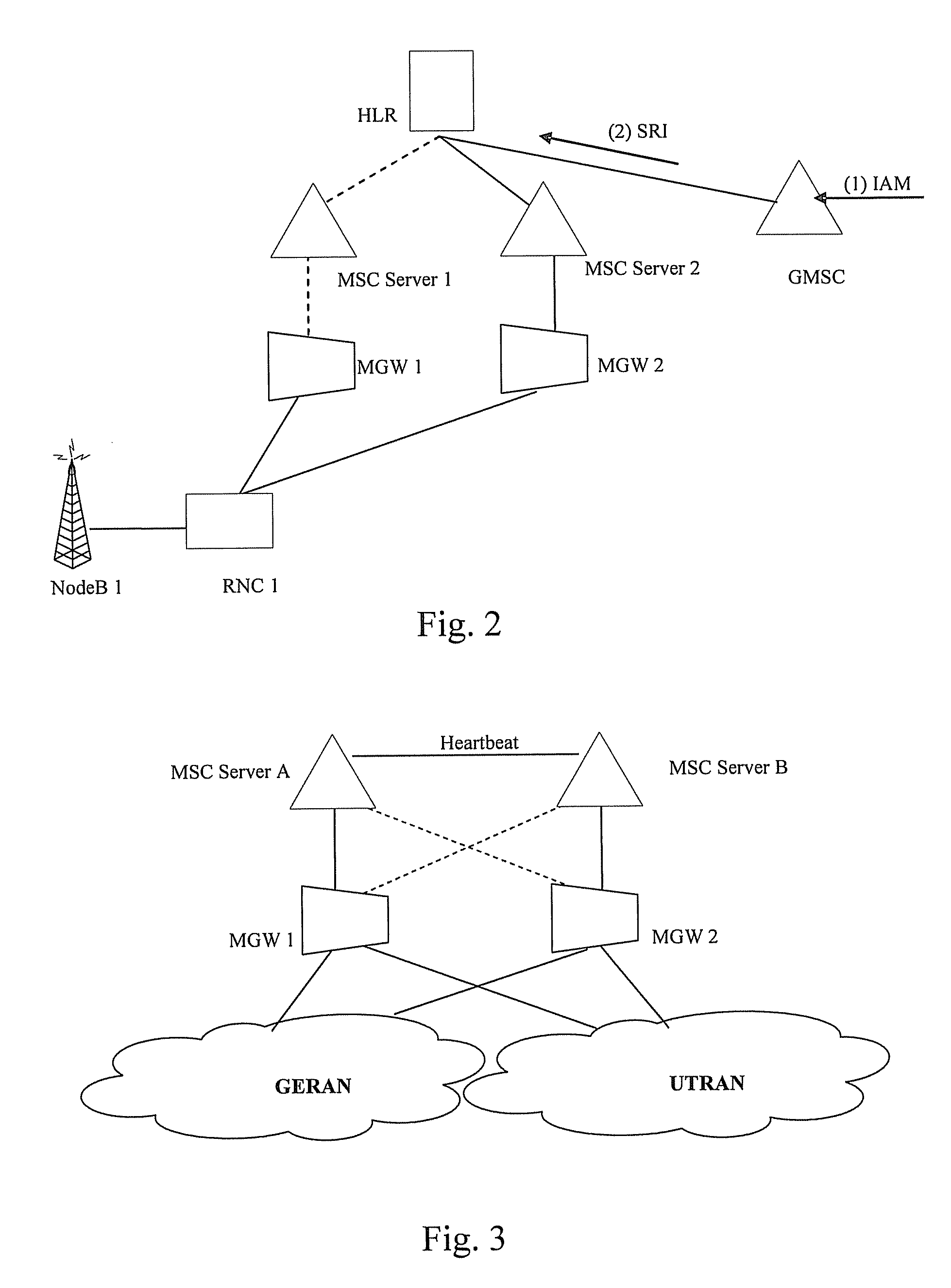
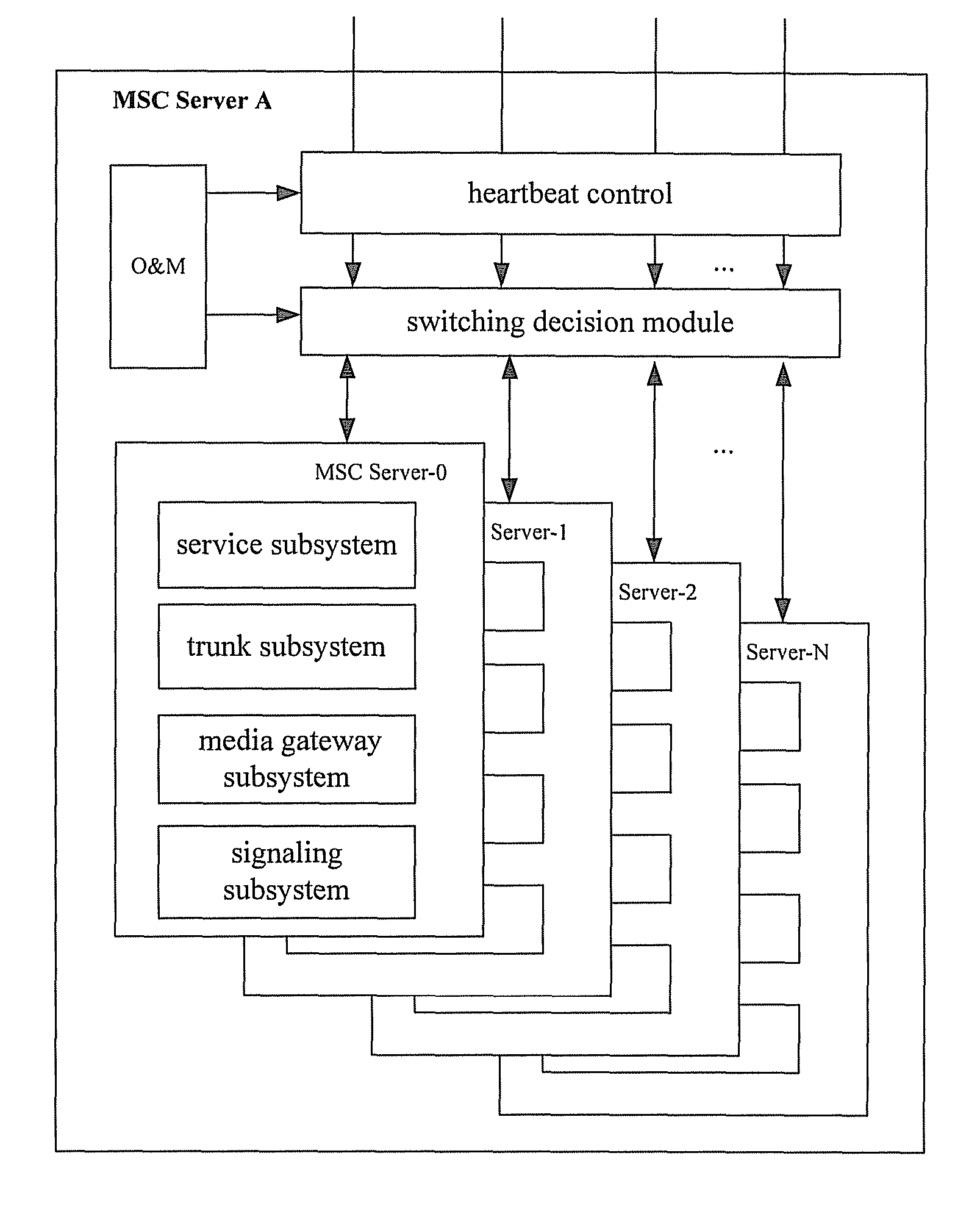
Method and system for implementing mobile switch center dual homing
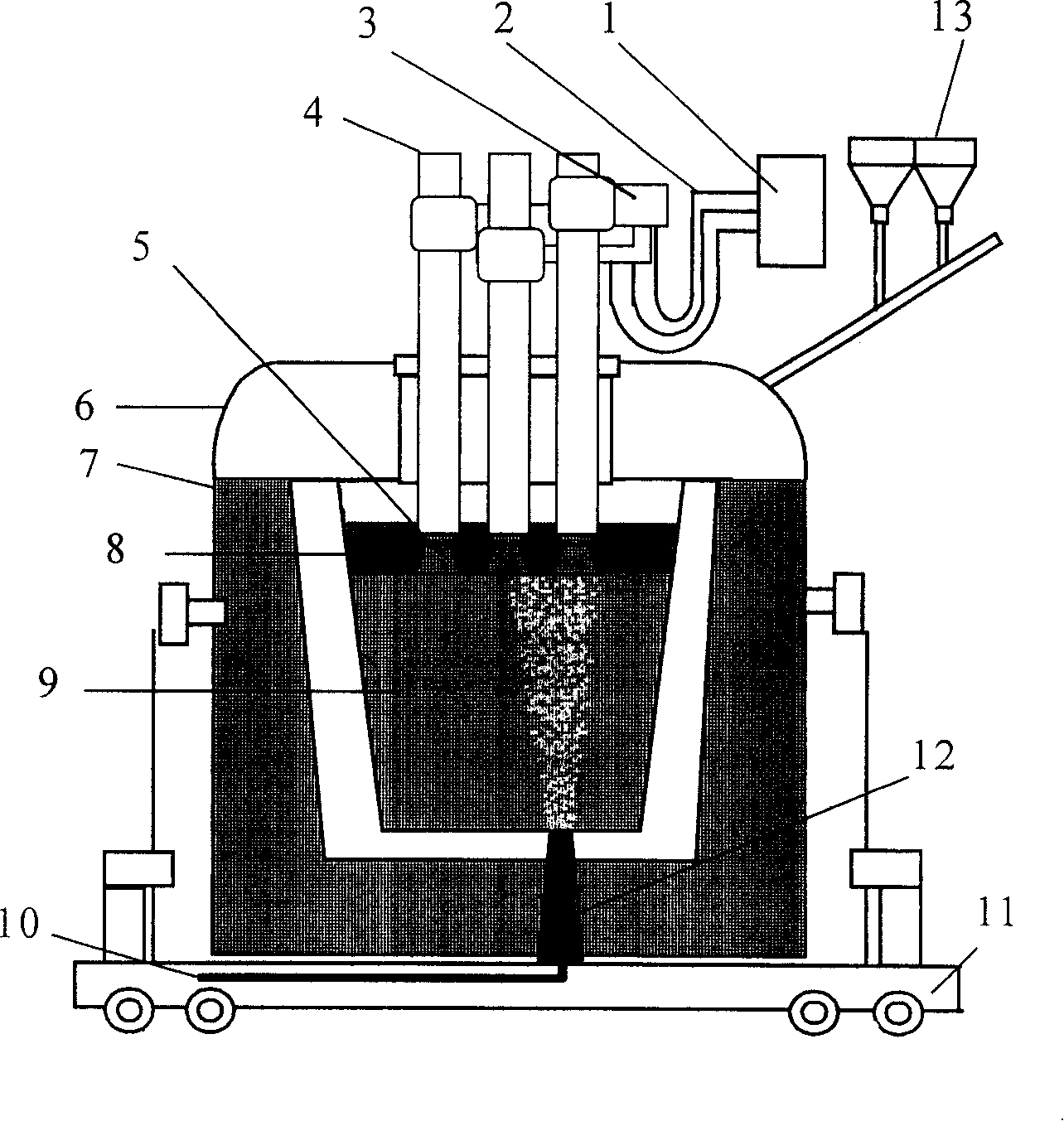
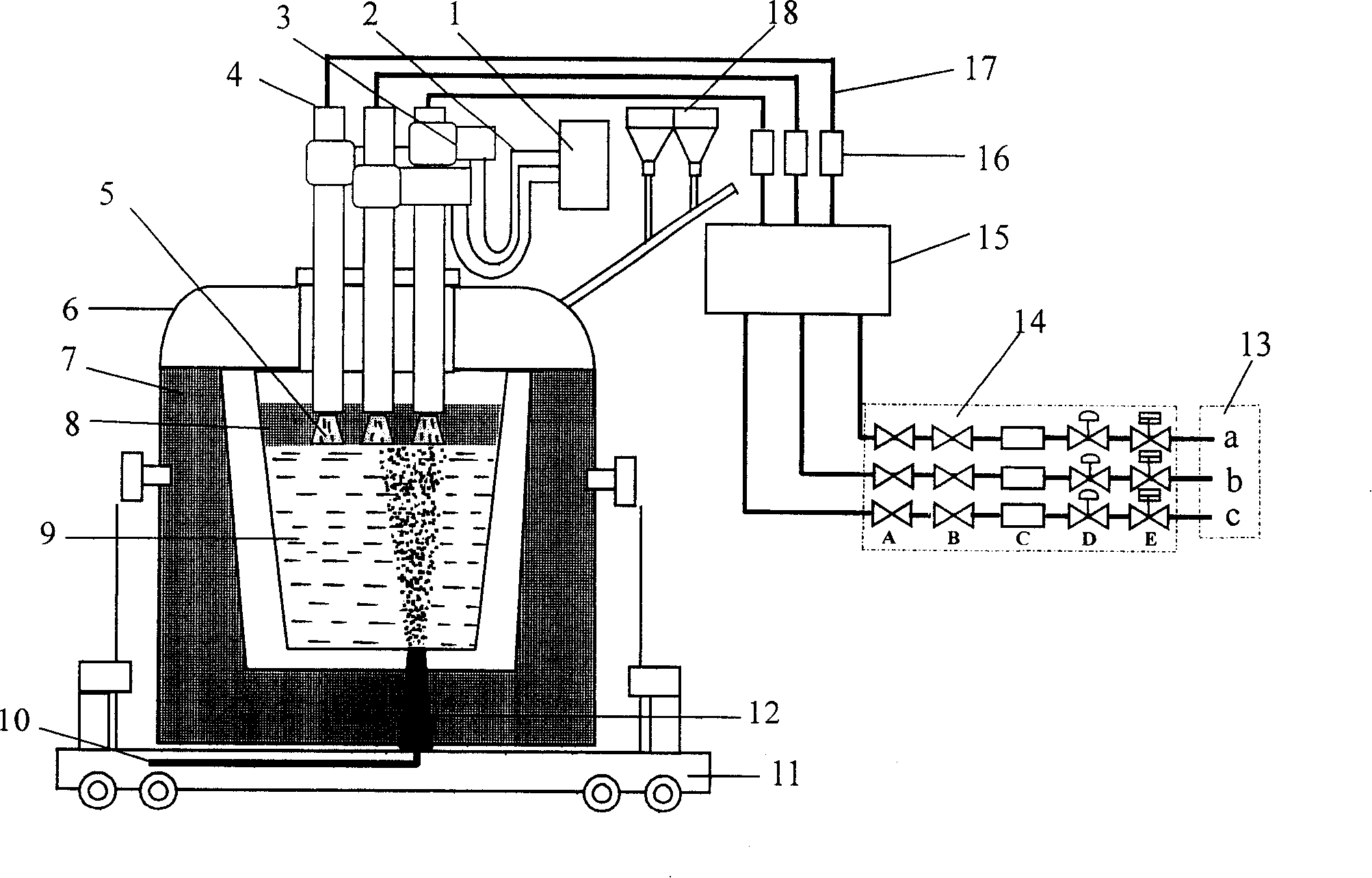
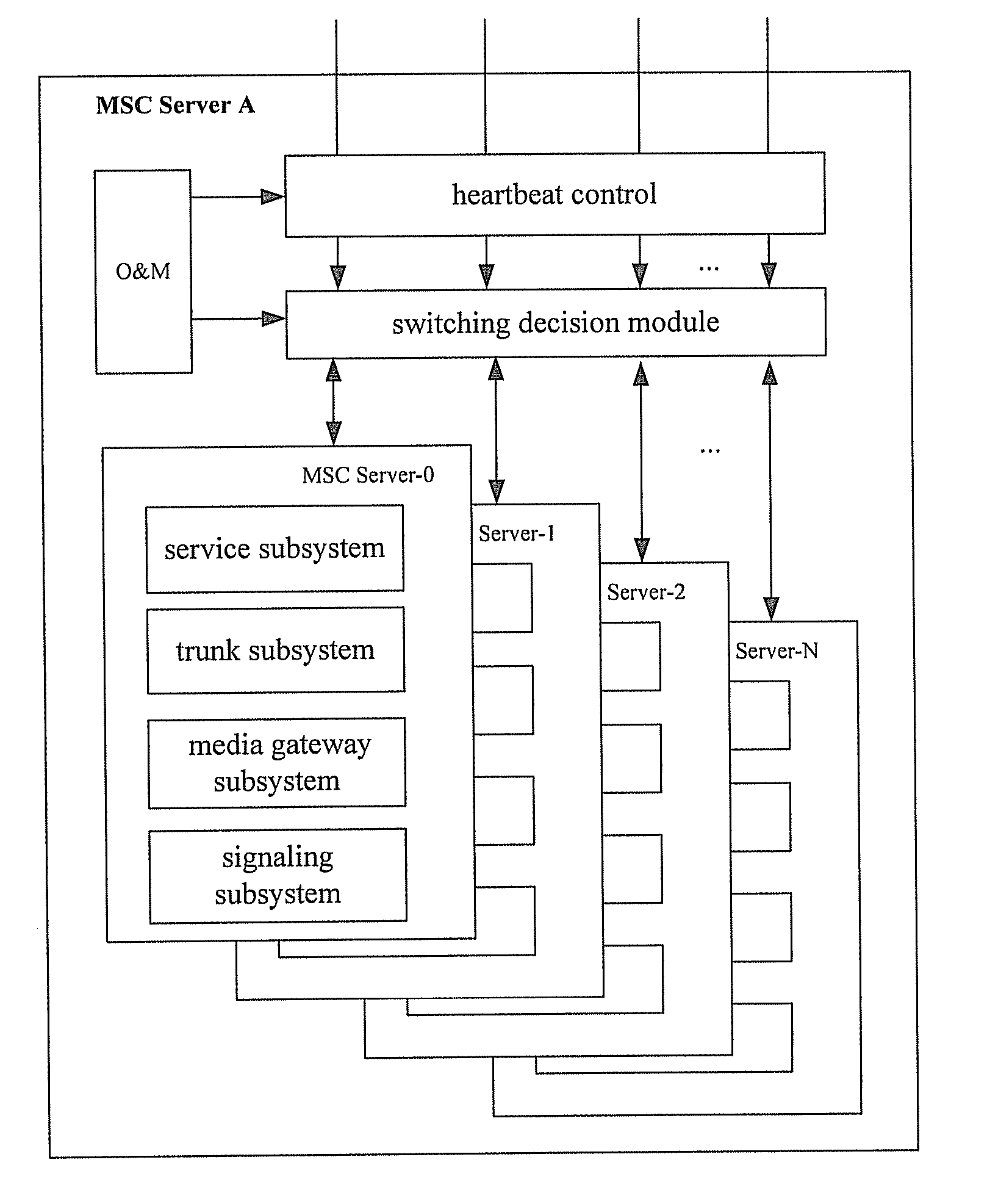
ActiveUS20080096547A1Improve reliabilityImplementation be simple and convenientRadio/inductive link selection arrangementsSubstation equipmentMobile communication networkComputer architecture
A method for implementing Mobile Switch Center (MSC) dual homing includes: dividing a first physical MSC Server into a plurality of virtual MSC Servers; establishing a dual homing relation between a first virtual MSC Server of the plurality of virtual MSC Servers and a second physical MSC Server; switching by the first virtual MSC Server from idle state to activate state if determining by the first virtual MSC Server that state switching is needed The scheme may implement the Mobile Switch Center (MSC) dual homing, and improve the reliability of mobile communication network; the implementation is simple and flexible.
Owner:HUAWEI TECH CO LTD
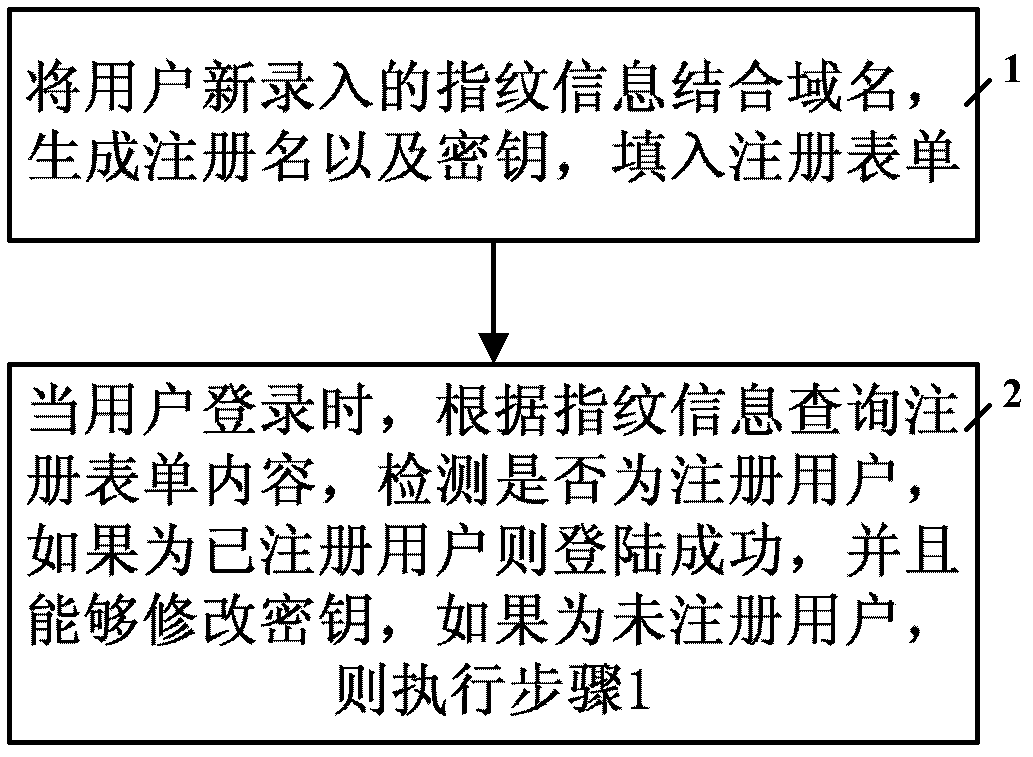
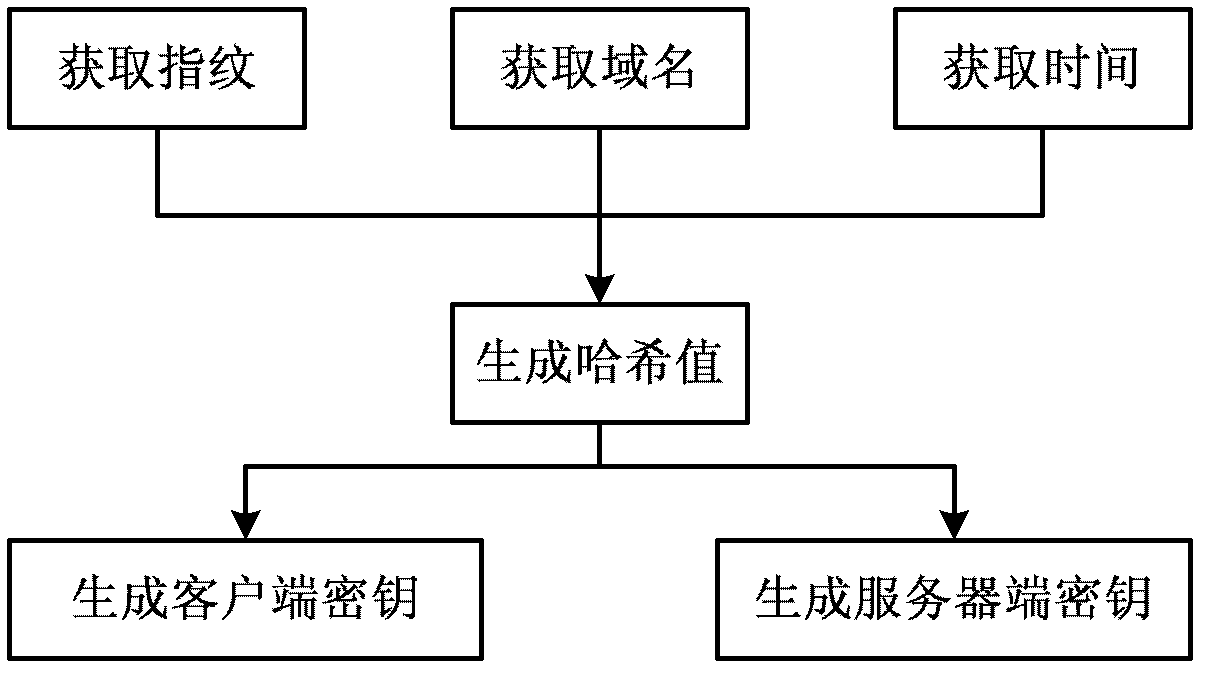
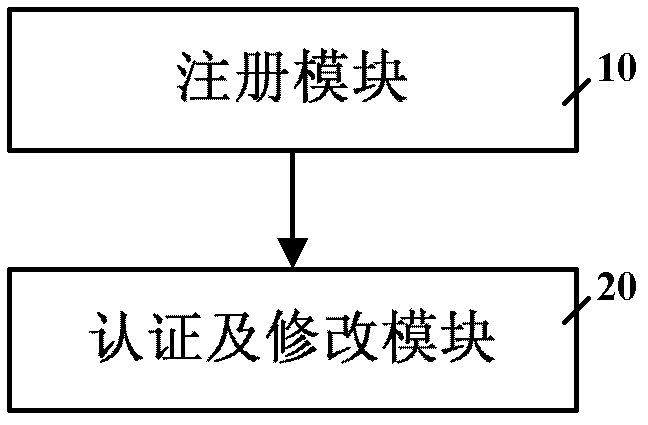
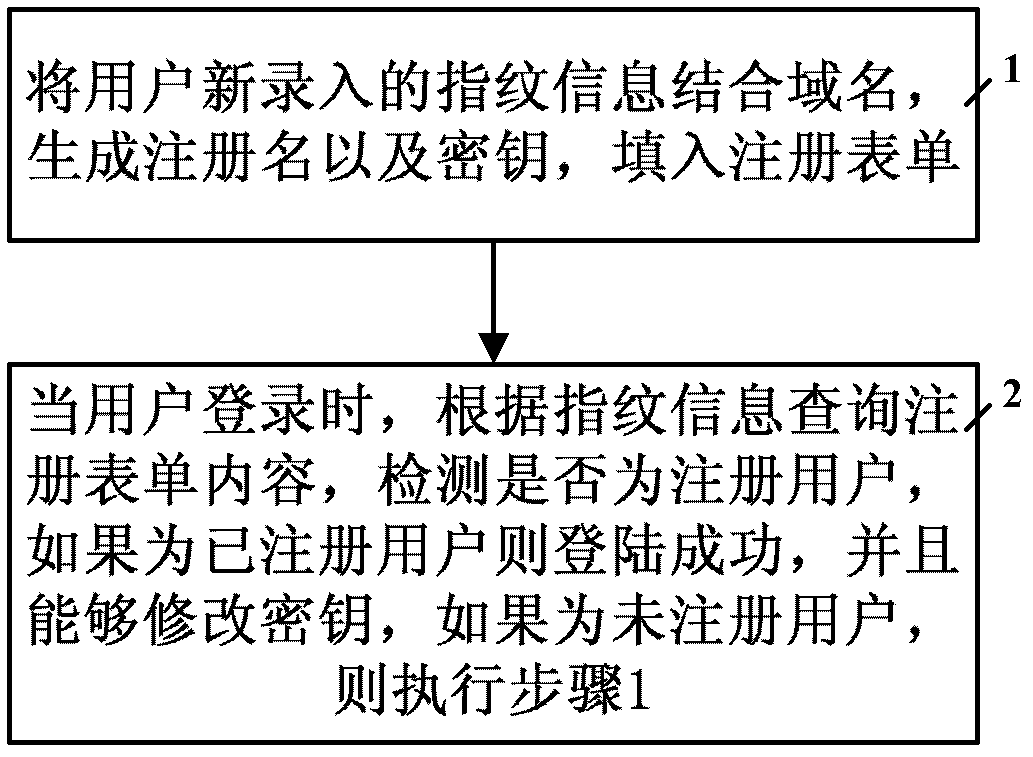
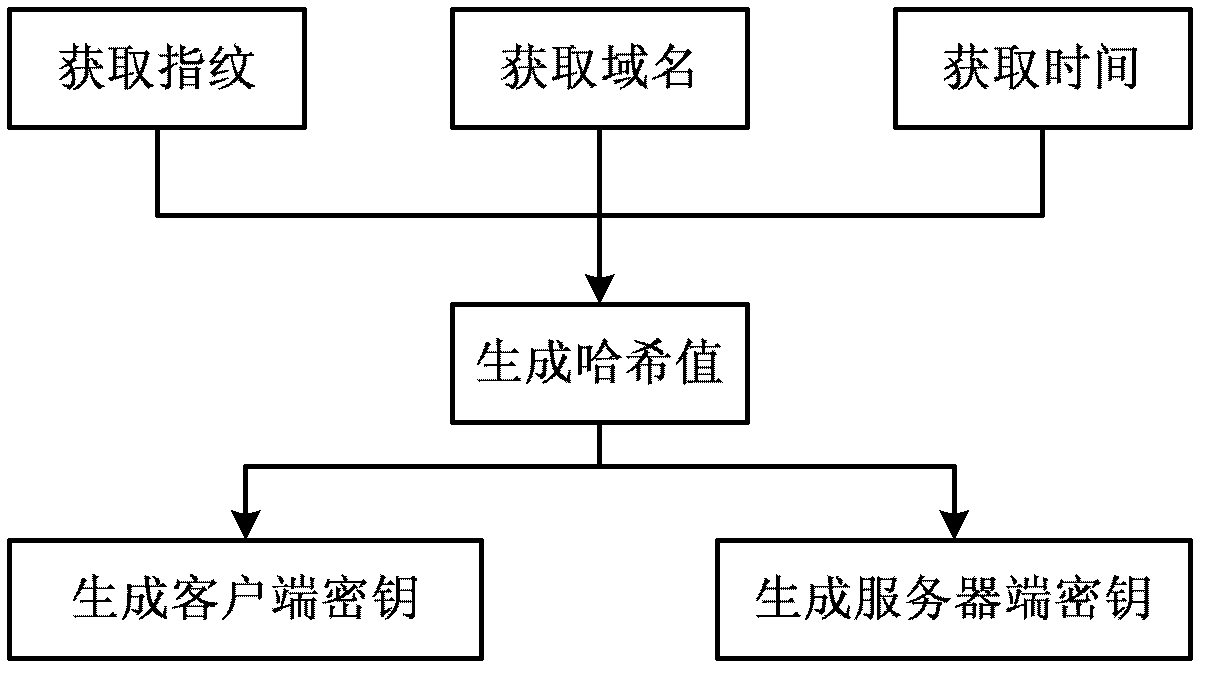
Universal method and system for user registration authentication based on fingerprint characteristics
The invention relates to a universal method and a universal system for user registration authentication based on fingerprint characteristics. The universal method is characterized by including steps of: 1 generating a registration name and a secret key by combining newly type-in fingerprint information with a realm name, and filling the registration name and the secret key into a registration form; and 2 searching for the content of the registration form according to the fingerprint information when a user logs in, detecting whether the user is registered, enabling the user to log in successfully when the user is registered and to be capable of correcting the secret key and performing step 1 if the user is not registered.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
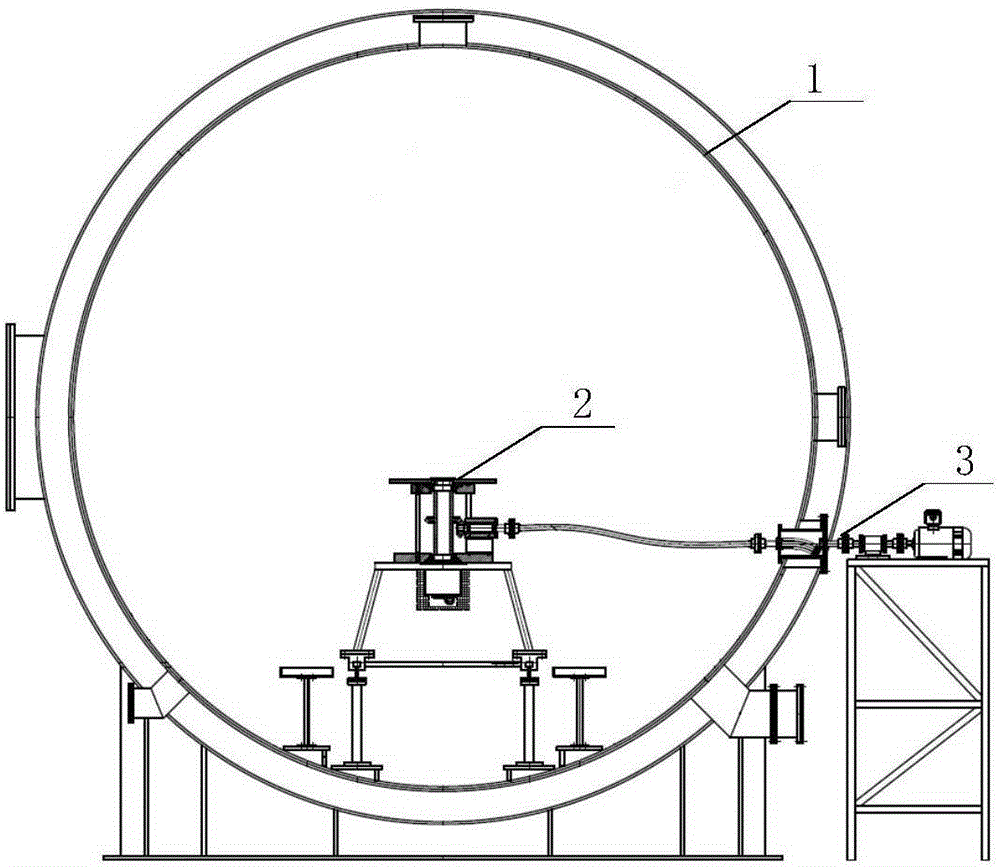
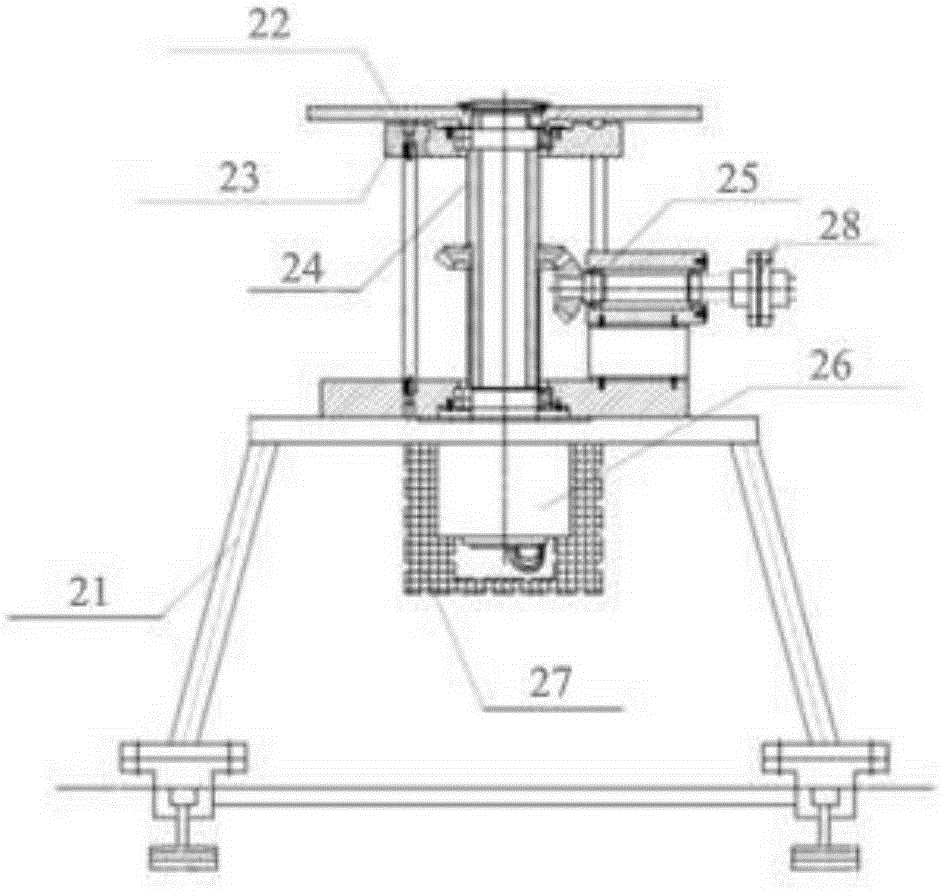
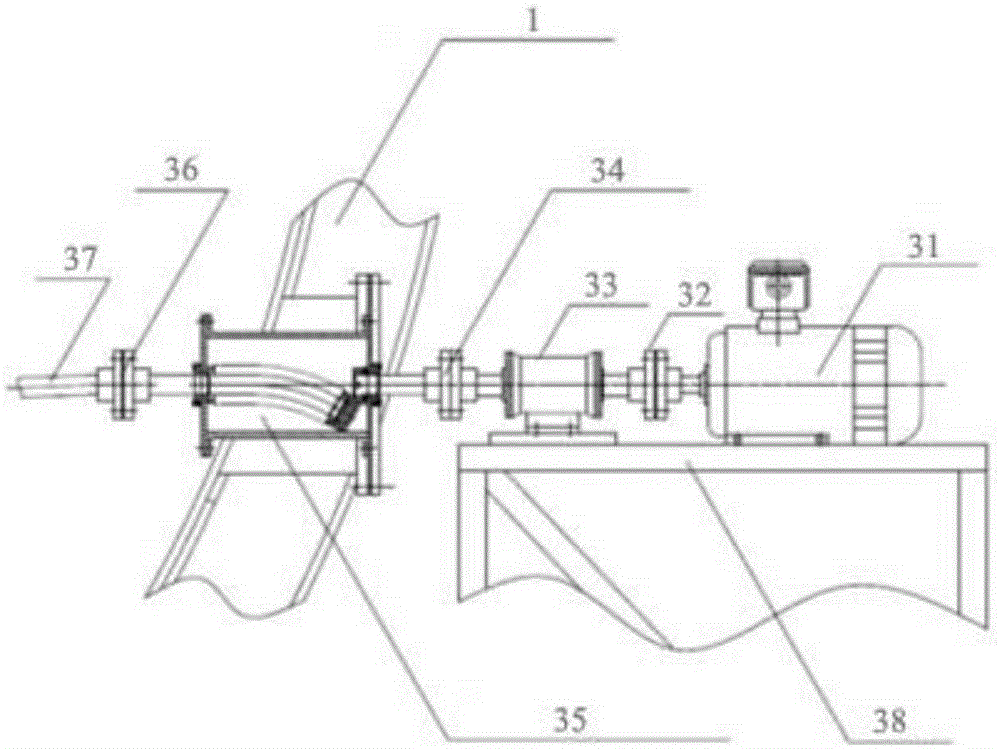
Electric rotating table under vacuum low-temperature environment
InactiveCN106516179ASolve key technical difficultiesSimple and flexible implementationCosmonautic condition simulationsMaterial thermal analysisElectricitySpace environment
The invention discloses an electric rotating table under vacuum low-temperature environment. The electric rotating table mainly comprises a rotating table bracket, a rotating table moving disk, a rotating table fixed disk, a main shaft, a motor, a flexible shaft, a bevel gear transmission mechanism, a conducting ring, a thermal protection device, a wall penetrating sealing unit and a control system. According to the electric rotating table disclosed by the invention, a driving motor is placed outside a space environment simulation chamber, the power is transmitted into the simulation chamber by a metal bellows in the wall penetrating sealing unit, and the flexible shaft is used for being coupled with the main shaft of the rotating table in the simulation chamber, so that the continuous rotation of the rotating table is realized, and an electricity supply channel and a testing signal transmission channel are provided for a tested product placed on the rotating table through the conducting ring; and the control system is connected with the conducting ring through a wall penetrating connector, and is used for supplying electricity to the product and acquiring a testing signal and a signal of a rotating table sensor, and adjusting the output power of the motor to control the rotating speed and the positioning angle of the rotating table.
Owner:BEIJING INST OF SPACECRAFT ENVIRONMENT ENG
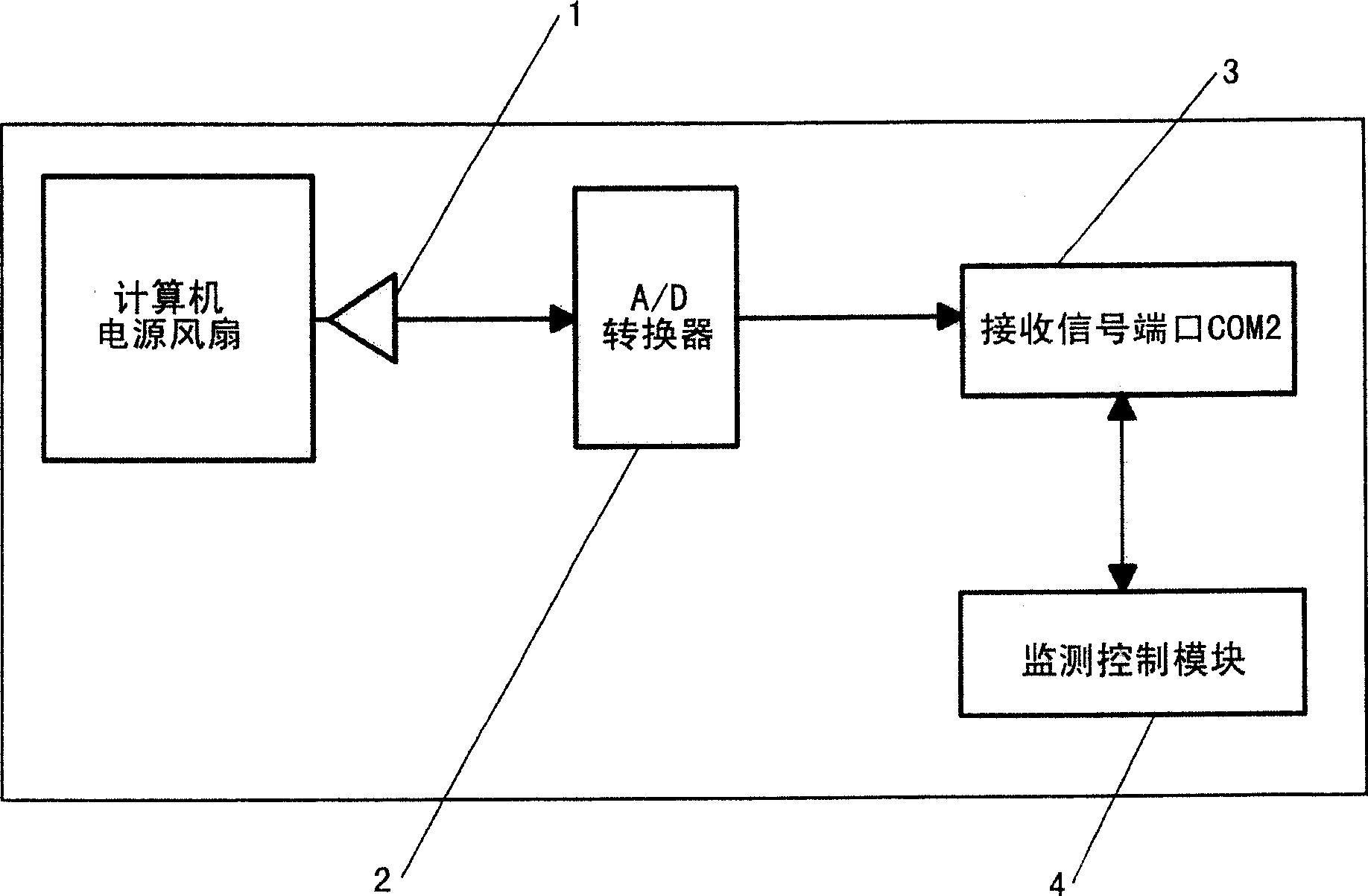
Method and device for monitoring status of computer power supply fan
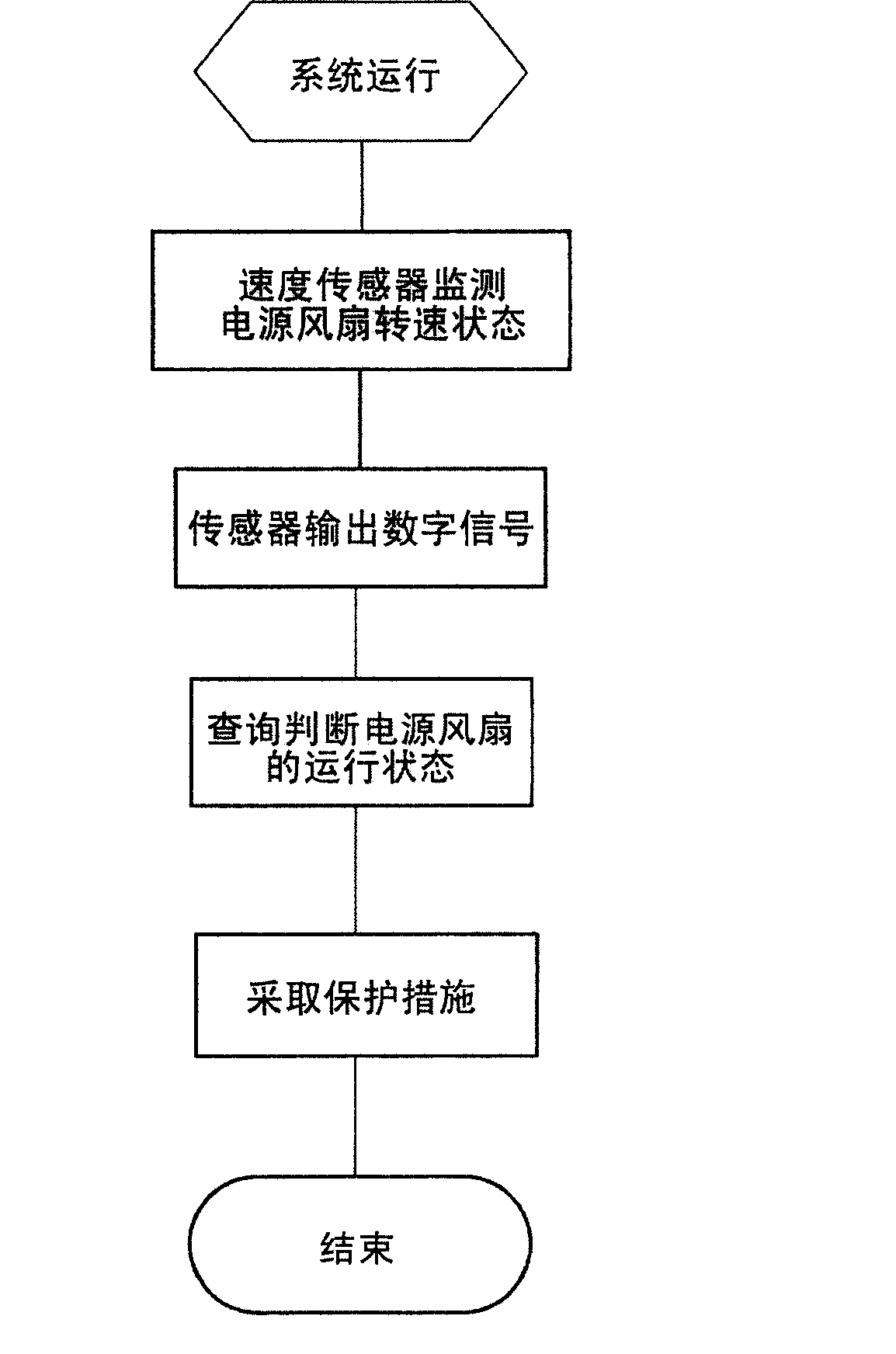
InactiveCN101008912AEasy to handlePerfectly compatibleHardware monitoringMonitoring statusControl system
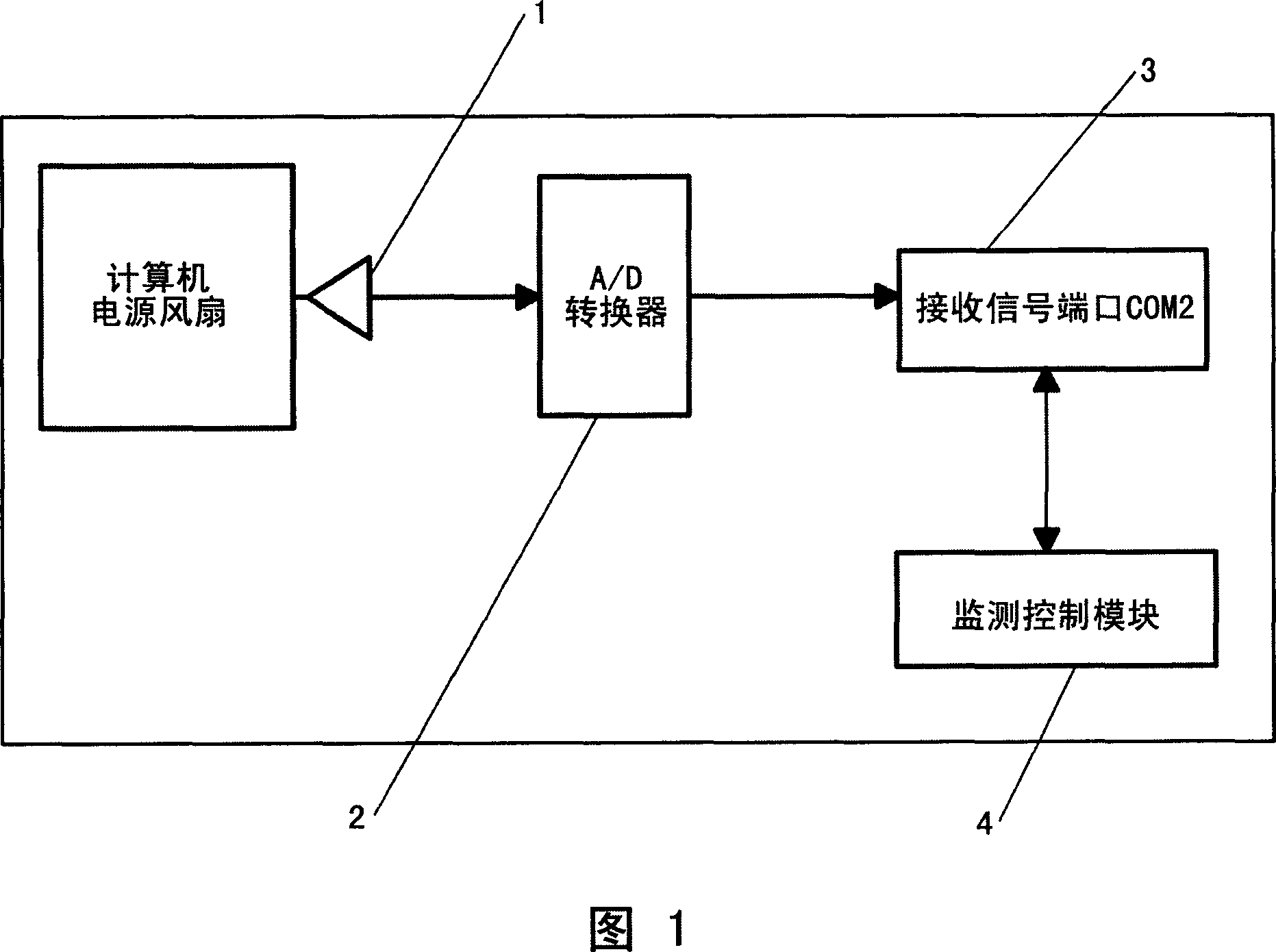
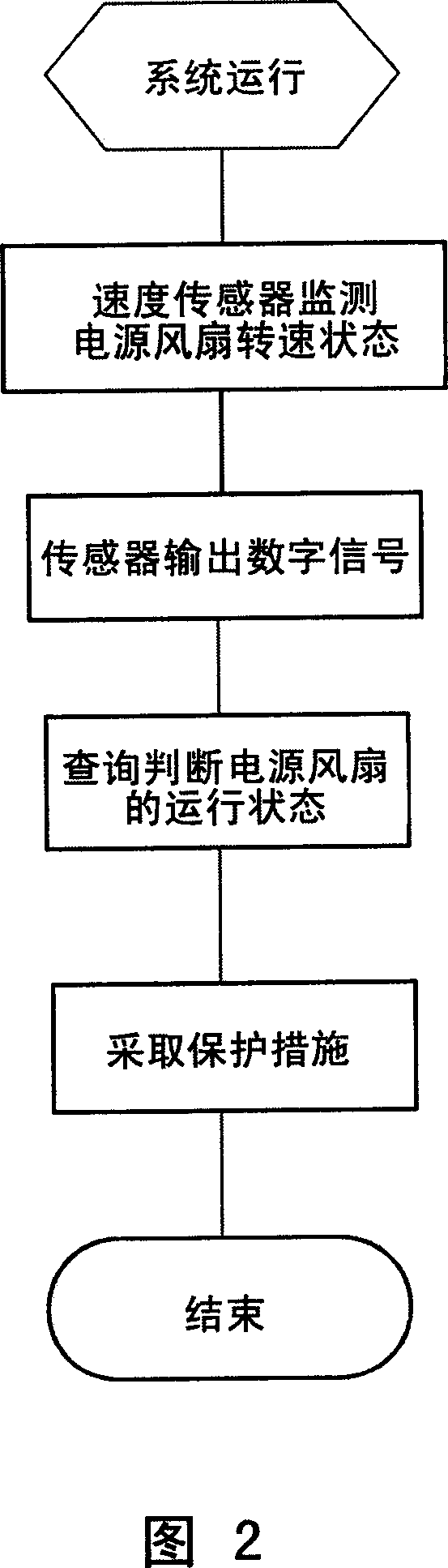
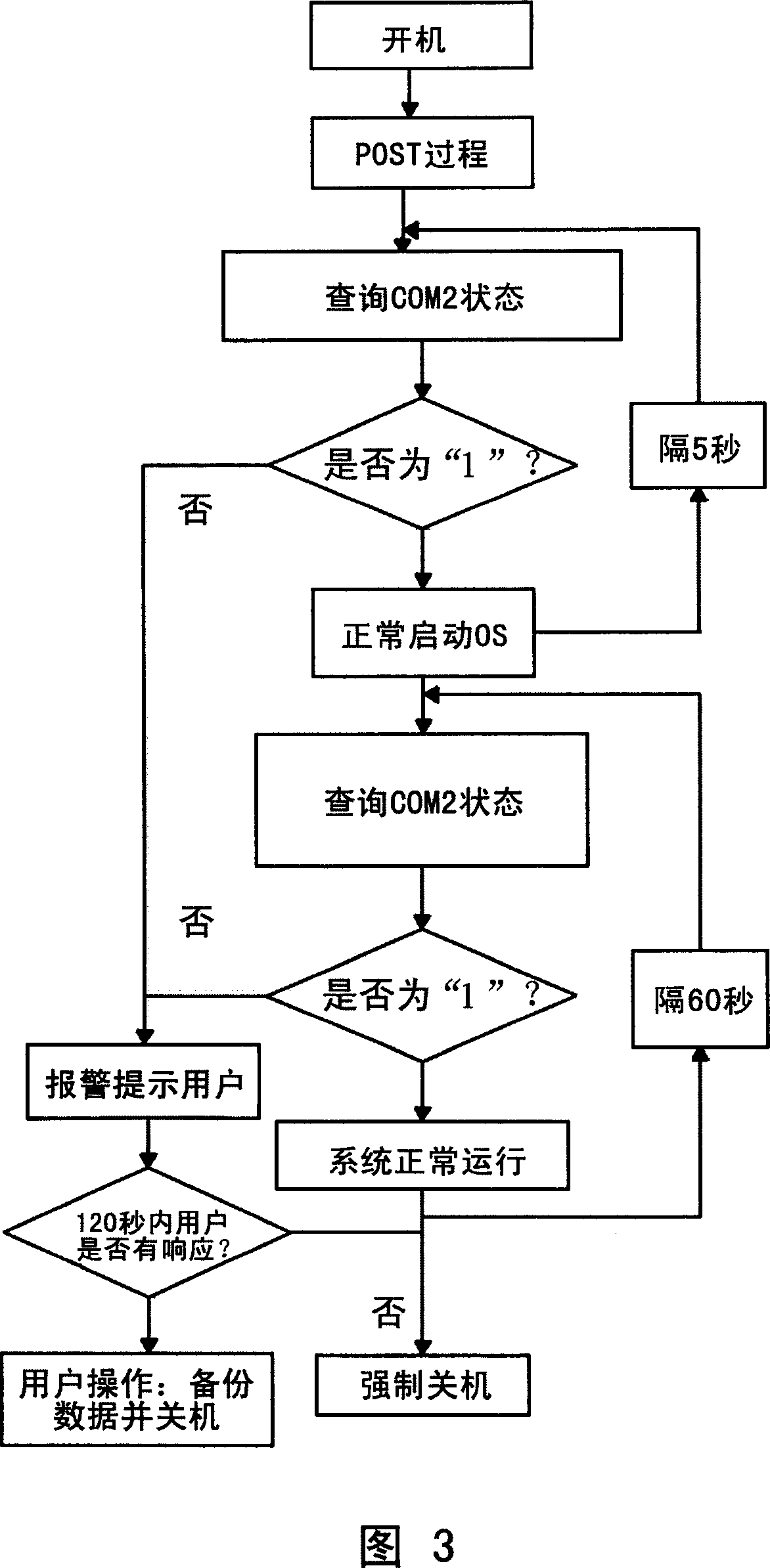
This invention relates to one device and method to monitor computer power fan status, which comprises the following parts: speed sensor connected to computer power exit; A / D converter; receive signal end on computer host board and monitor control module, monitor control module to read fan rotation signal from signal end to judge whether the fan is normal by protection actions of control system.
Owner:LENOVO (BEIJING) CO LTD
Er-doped optical fiber source and near-Gaussian spectrum output generating method thereof
InactiveCN104184038ASimple and flexible implementationSimple designActive medium shape and constructionLength waveWave band
The invention discloses an er-doped optical fiber source and a near-Gaussian spectrum output generating method thereof. The method is specifically as follows: an er-doped optical fiber is divided into a plurality of sections and filters are connected between the sections of er-doped optical fibers; a pumping laser source, the wavelength of which is 980nm, is used to pump all the er-doped optical fibers; the filters filter 1530nm-waveband seed light generated by the sections of optical fibers and the 1530nm-waveband seed light is restricted from entering a next section of er-doped optical fiber for stimulated radiation amplification; and at last, near-Gaussian spectra, the average wavelength of which is 1550 wavebands, are output. Based on a gain modulation technology of cascade filtering, the er-doped optical fiber source obtains near-Gaussian spectrum output, and can also have higher output power and larger spectrum width at the same time.
Owner:ZHEJIANG UNIV
High-adaptability composite material pipe joint
InactiveCN102506249AVersatileImprove economyJoints with sealing surfacesNon-disconnectible pipe-jointsStress conditionsScrew thread
The invention relates to a high-adaptability composite material pipe joint. At least one end of a composite material pipe is a conical connecting section and is of the shape of an outer cone or an inner cone. A plurality of slits are circumferentially and evenly arranged. At the same time, a metallic taper pipe and a metallic tightening taper sleeve are arranged. The three sections of the metallic taper pipe are respectively a taper part, a male thread part and a connecting section part. The bottom diameter of a male thread is slightly larger than the outer diameter of the composite material pipe; the diameter of the small end of the taper part is equal to the inner diameter of the composite material pipe; the length of the taper part is equal to the depth of the slits of the composite material pipe; the small end of the metallic tightening taper sleeve is provided with inner taper, which is consistent with the total taper of the metallic taper pipe and the composite material pipe; the diameter of the small end of the metallic tightening taper sleeve is equal to the outer diameter of the composite material pipe; and the large end of the metallic tightening taper sleeve is provided with a female thread, which is matched with the male thread of the metallic taper pipe. The high-adaptability composite material pipe joint has good universality, economy and adaptability, the process is simple and reliable, the implementation is simple and flexible, joint schemes can be designed aiming at composite material pipes which are made of different materials, have different wall thicknesses and are used under different stress conditions, and the practicability and the applicability are high.
Owner:NANJING INST OF ASTRONOMICAL OPTICS & TECH NAT ASTRONOMICAL OBSE
Remotely operated target-processing system
ActiveUS20150247704A1Simple and flexible implementationLower acquisition costsArmoured vehiclesFiring/trigger mechanismsControl signalCentral unit
A remotely operated target-processing system includes a shooting robot having a stand supporting a firing part having an optoelectronic aiming device providing an image of the target, sensors detecting the relative position of the firing part, and actuators positioning the firing-part. A central unit receives the instructions and the signals from the sensors and generates control signals for the actuators and the firing-part. A control screen displays the image and embeds aiming data, and a control member directs the trajectory line.
Owner:LEVILLY PHILIPPE
Creation of remarkable regions in a digital image
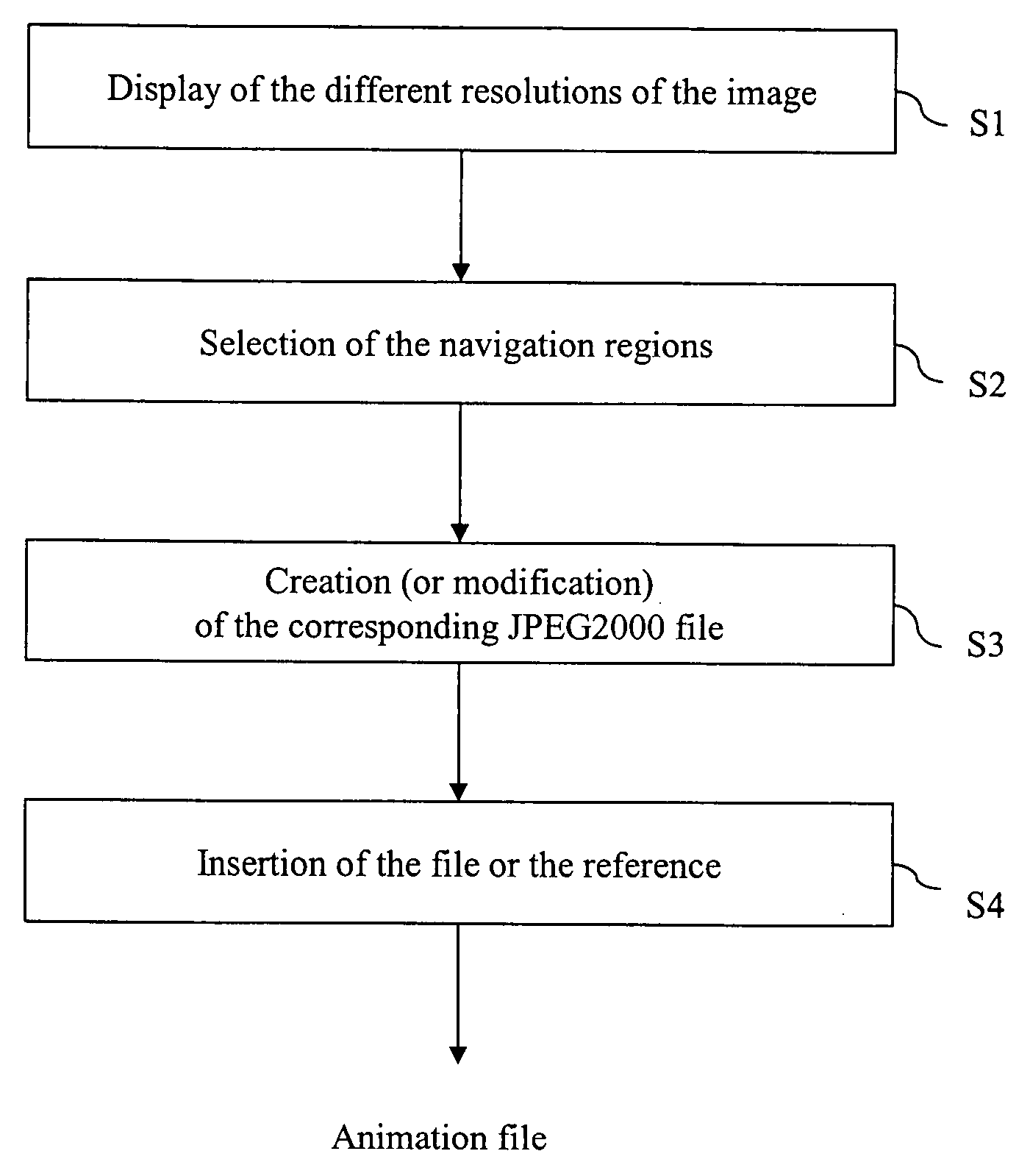
ActiveUS20050013493A1Simple and flexible implementationPulse modulation television signal transmissionCharacter and pattern recognitionImage resolutionData field
A method of creating a remarkable region in a digital image encoded at a plurality of resolution levels, the encoding data being organized in packets, each packet comprising a field of encoded data, comprises the steps of: selecting (S2) at least one remarkable region in at least one resolution level of the image, selecting (S3) data packets corresponding to the selected region, constructing (S3) an encoded form comprising the selected packets and modified packets, the modified packets corresponding respectively to the packets not selected and comprising an empty data field defining an inaccessible region.
Owner:CANON KK
Composite-material plate joint
InactiveCN104832507AApplicable connectionVersatileSheet joiningUltimate tensile strengthStructural safety
Disclosed in the invention is a composite-material plate joint comprising a composite-material plate, a metal wedge block, and connecting plates. Connecting holes are formed in corresponding parts of the end portion of the composite-material plate, the metal wedge block, and the connecting plate. A gap is processed in the edge of the composite-material plate; and the metal wedge block is wedged into the gap. One side, has the same gradient as the metal wedge block, of each connecting plate is buckled at each of the two sides of the composite-material plate; and the connecting plates and the composite-material plate wedged into the metal wedge block are fixedly connected by bolts and nuts. The composite-material plate joint has the following advantages: the joint can be applied to connection between the composite-material plates with different materials and different heights and between the composite-material plate and other metal components and has high universality, economy, and adaptability. Moreover, the process is simple; the implementation is flexible; the mounting and dismounting become convenient; and the tensile strength is high and the structure is safe and reliable.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Method for implementing continuous carrier frequency configuration for CDMA (Code Division Multiple Address) digital optical fiber repeater
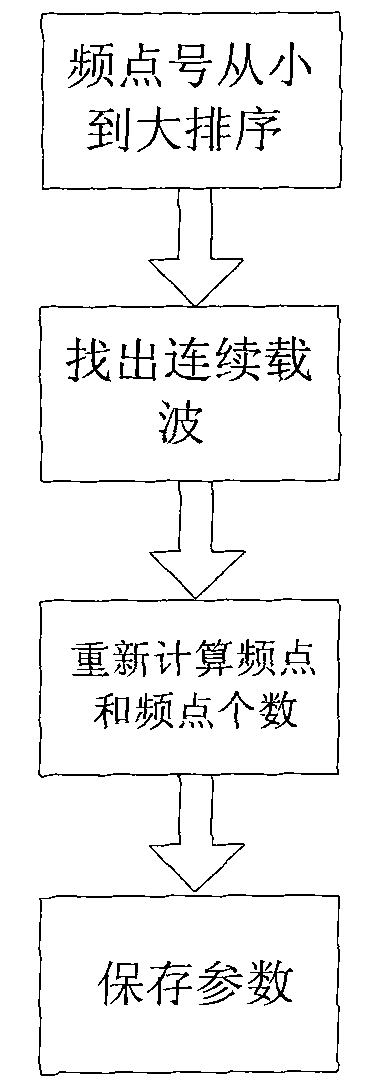
ActiveCN101841372ASimple and flexible implementationCarrier frequency processing capability can be changed in real timeElectromagnetic repeatersFrequency mixerDigital filter
The invention relates to a method for implementing continuous carrier frequency configuration for a CDMA digital optical fiber repeater, which comprises the following steps of: judging the currently used frequency point number, the number S of frequency points and n continuous carrier frequency manners according to the carrier frequency configuration of the superior network management by the CDMAdigital optical fiber repeater, wherein n is a natural number arranging from 1 to 7, judging and recording the number of the carrier frequencies used and the distribution of the continuous carrier frequencies by sequencing the frequency number and detecting the difference, calculating the configuration parameters of a digital mixer and the configuration bandwidth of a digital filter, treating thecontinuous carrier frequencies as one carrier frequency, using one mixing configuration parameter; reconstructing the used digital filter according to the configuration parameters of the digital mixer and the configuration bandwidth of the used digital filter to implement variable signal processing bandwidth and process different carrier frequency configuration manners; and accumulating data for different signal bandwidth processing channels to process a signal carrier frequency and various different continuous carrier frequencies. The invention is flexible and simple and has strong adaptability.
Owner:WUHAN HONGXIN TELECOMM TECH CO LTD
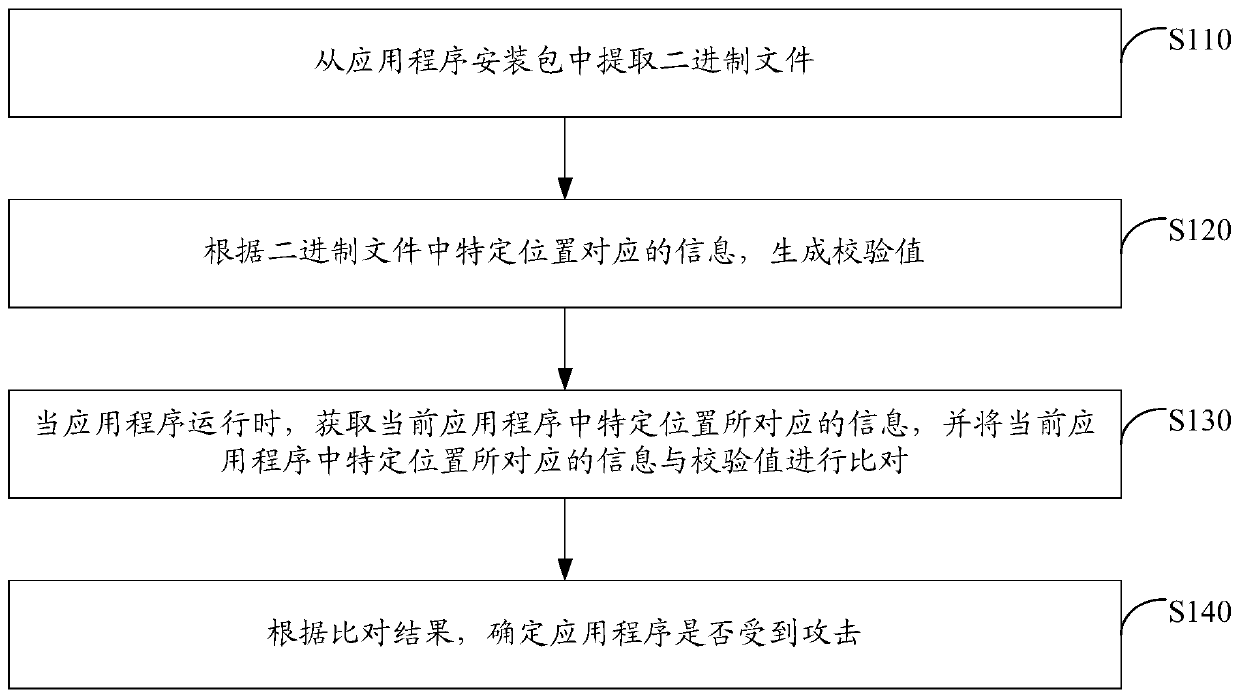
Application program security reinforcing method and device
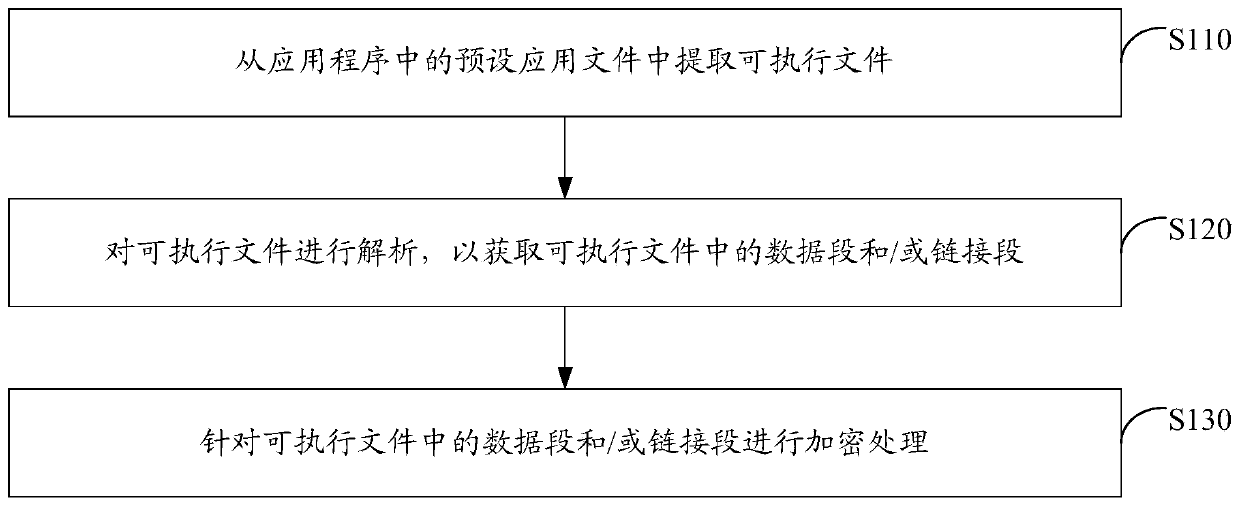
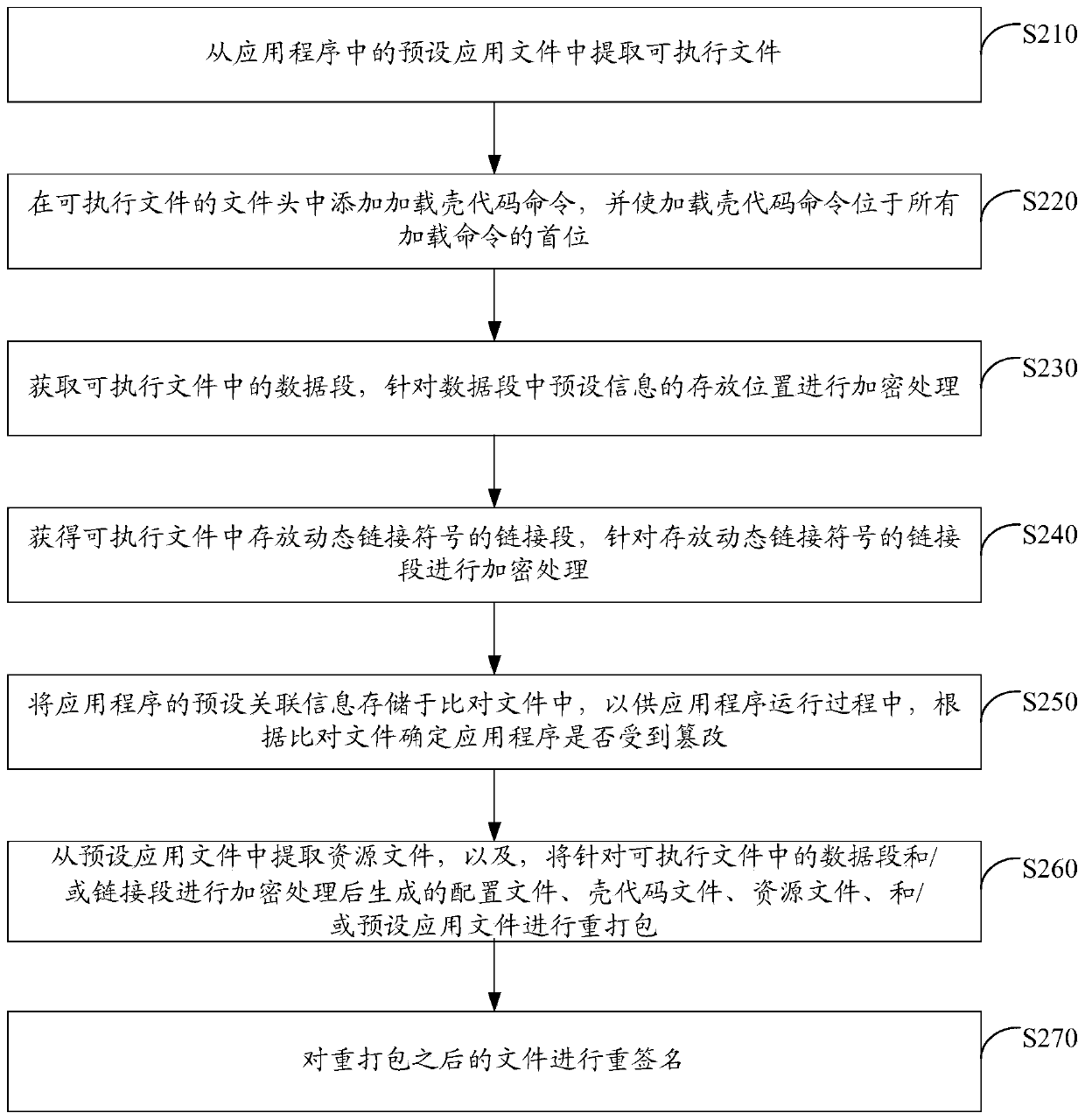
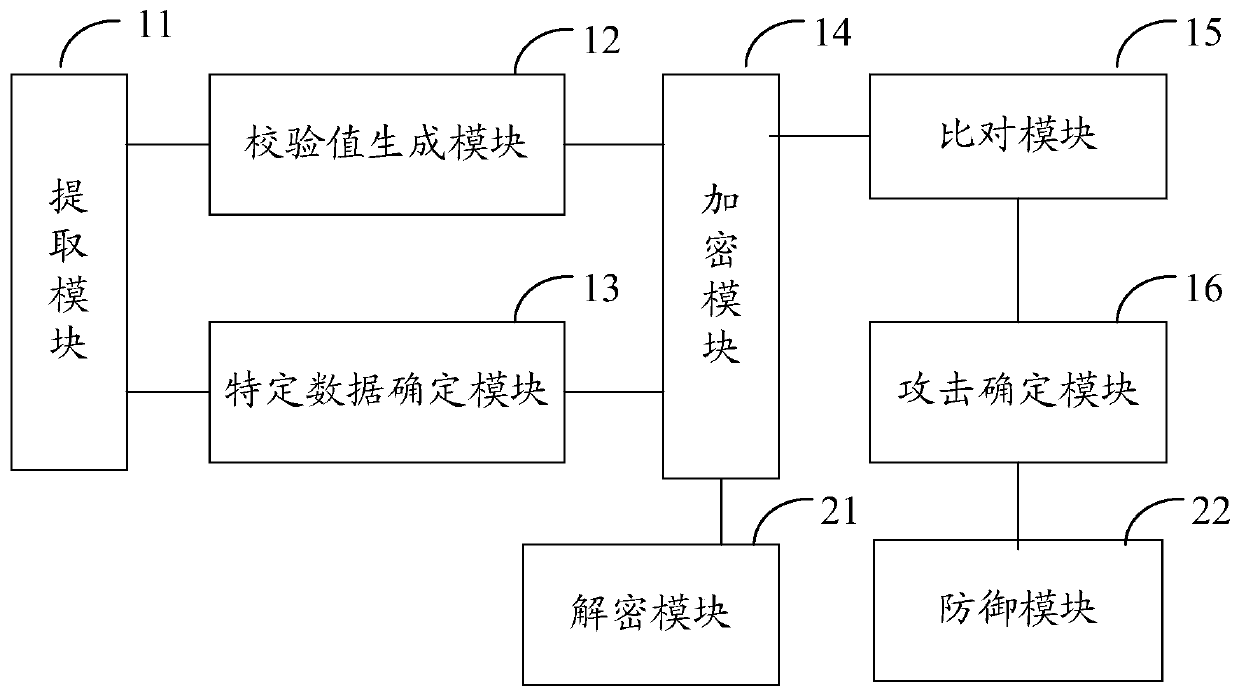
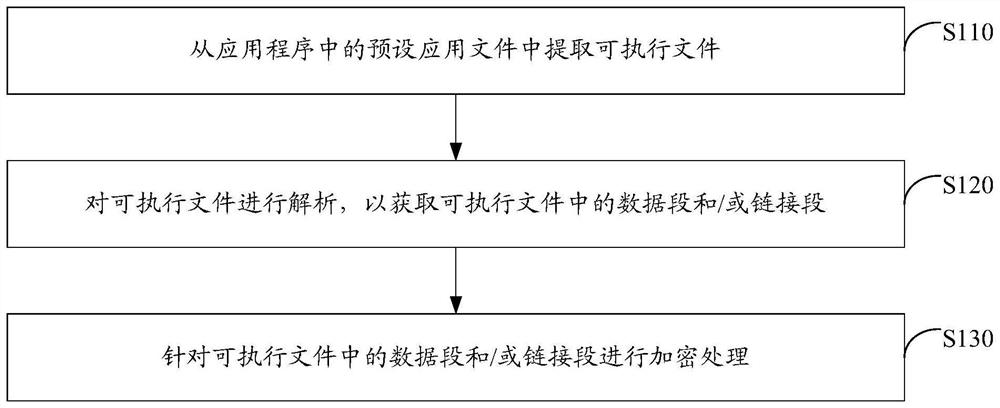
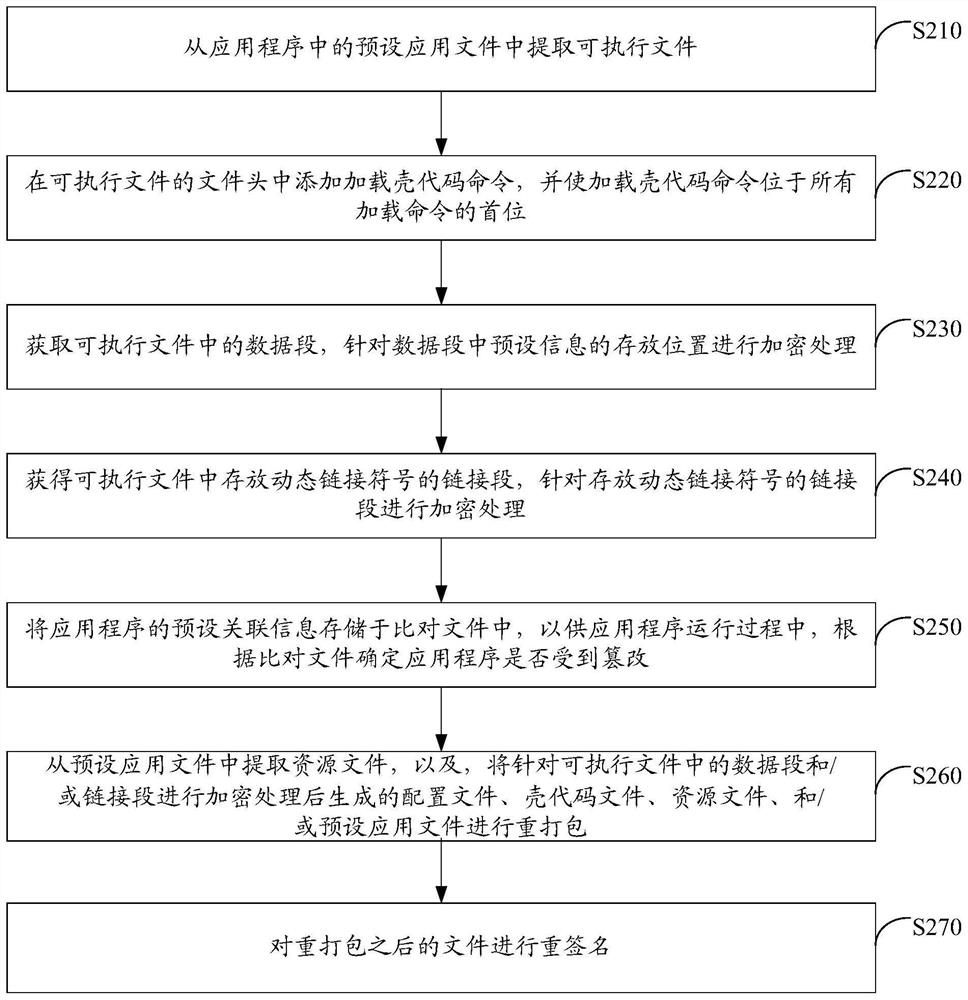
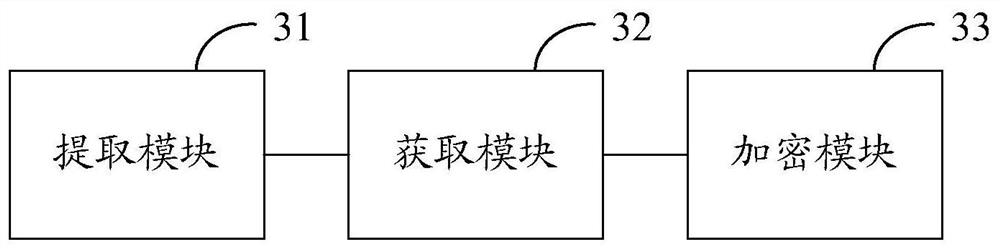
ActiveCN110147653ATo achieve reinforcementIncrease the reverse difficultyProgram/content distribution protectionReverse analysisData segment
The invention discloses an application program security reinforcing method and device. The application program security reinforcing method comprises the following steps: extracting an executable filefrom a preset application file in an application program; analyzing the executable file to obtain a data segment and / or a link segment in the executable file; and performing encryption processing on the data segment and / or the link segment in the executable file. According to the scheme, the data segment and / or the link segment of the binary file are / is encrypted to reinforce the application program, so that the reverse difficulty of the application program is greatly improved, and reverse analysis of the application program is effectively prevented, and code expansion of the application program is not easily caused; and the implementation process is simple and flexible, and batch maintenance is easy, and the maintenance cost is low.
Owner:JIANGSU PAYEGIS INFORMATION SECURITY TECH CO LTD +1
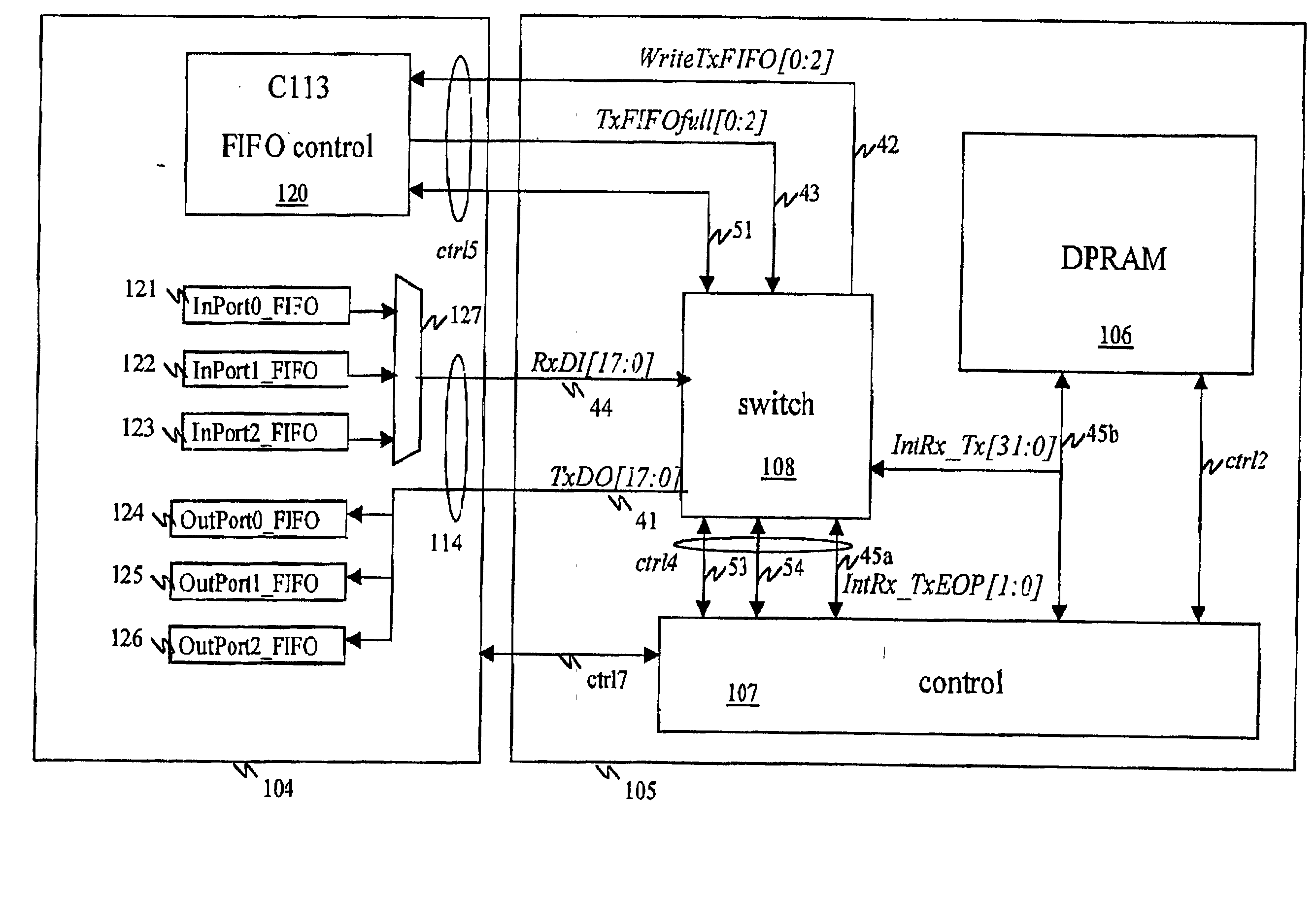
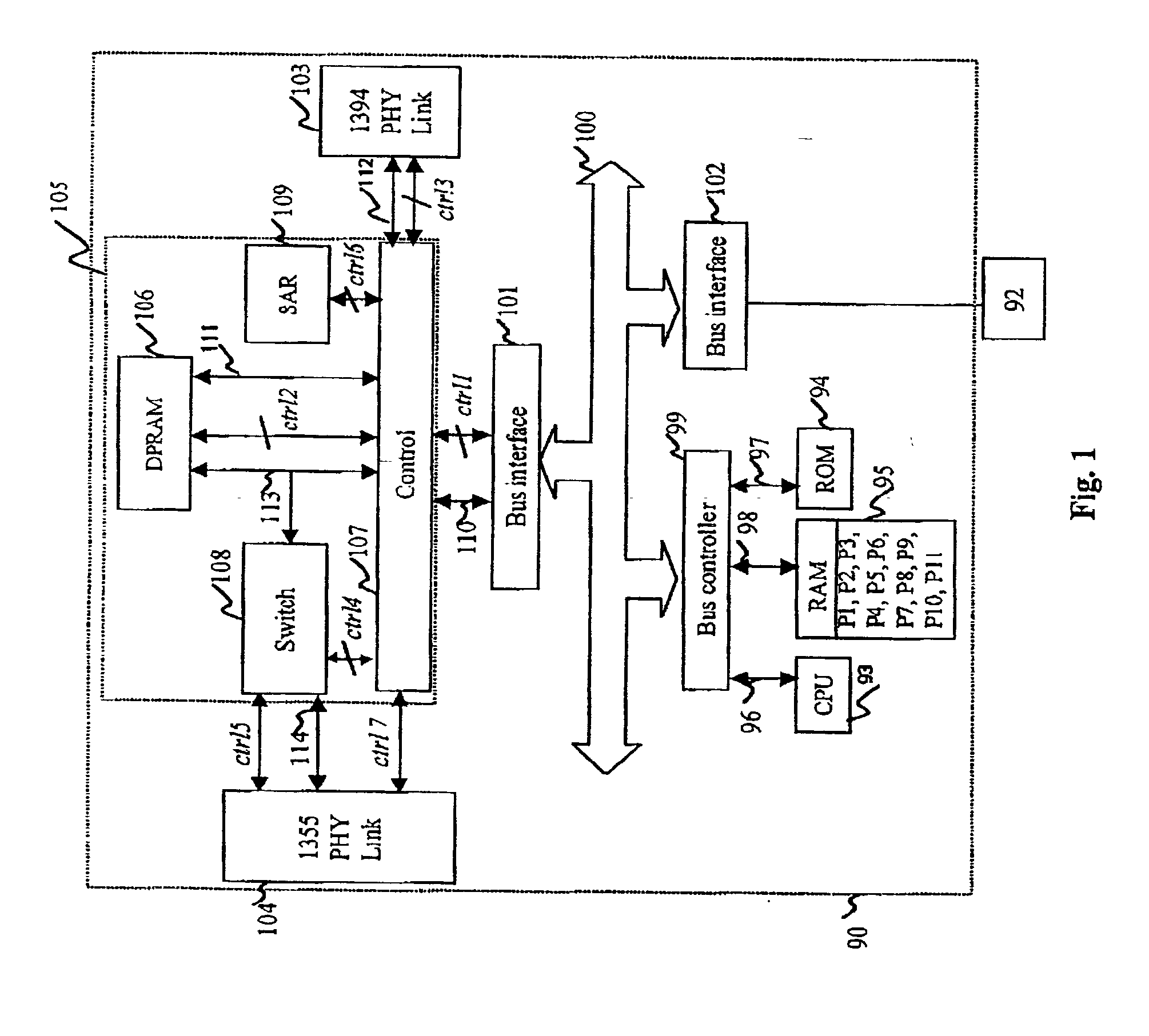
Rate adaption within a TDM switch using bit stuffing
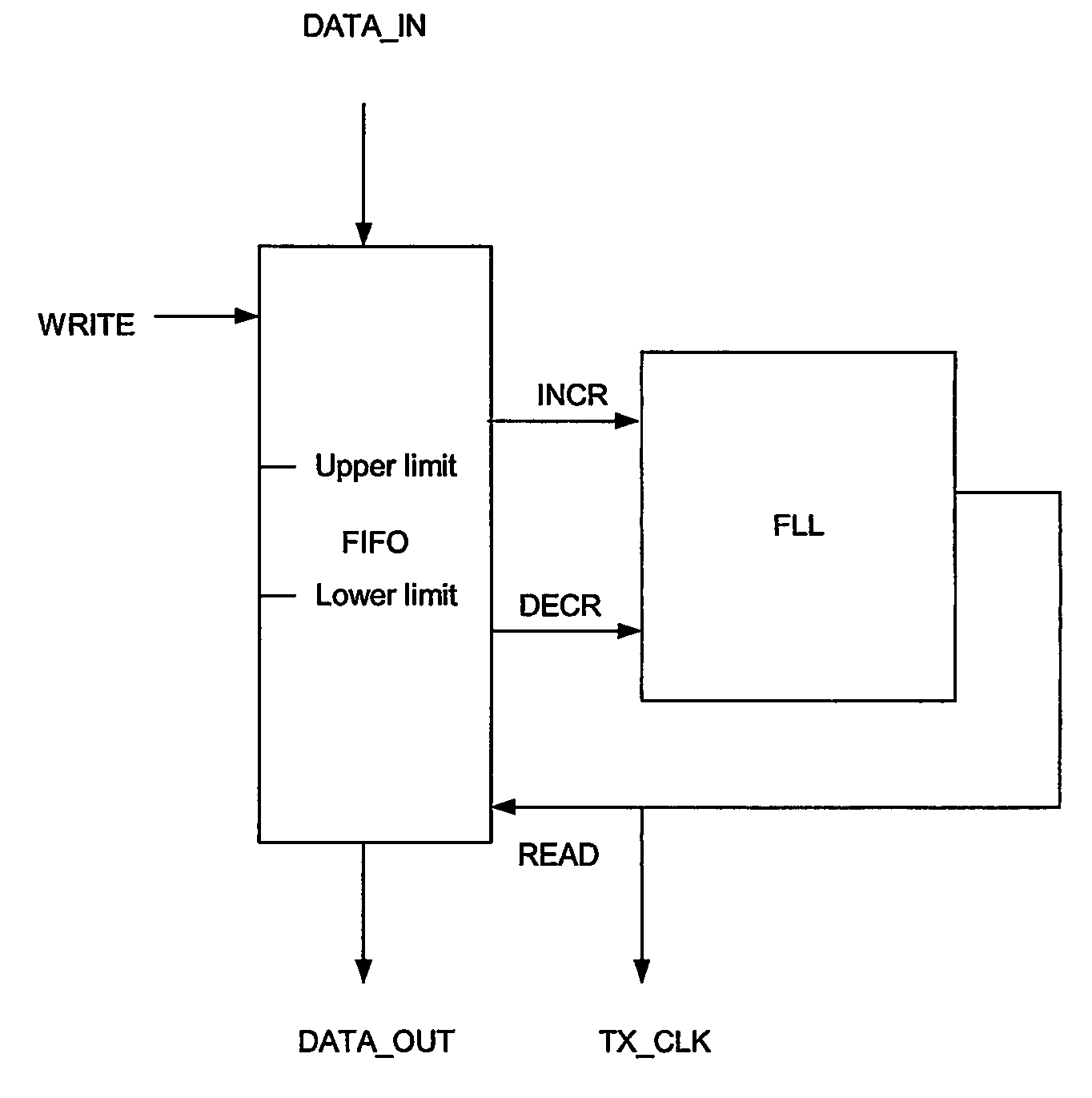
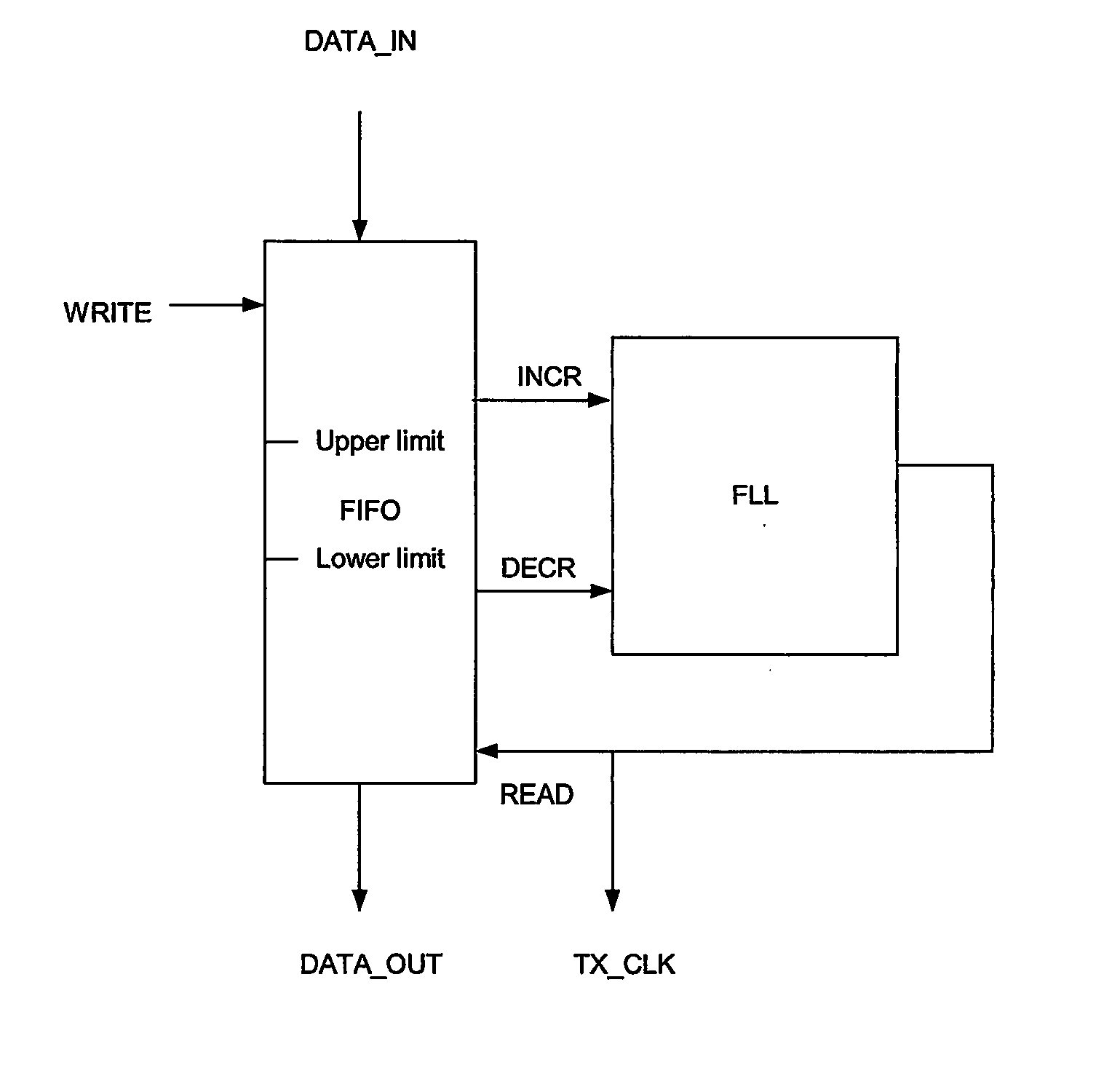
InactiveUS7372862B2Avoid introducingExcellent jitter and frequency stabilityError preventionFrequency-division multiplex detailsComputer hardwareRate adaptation
The present invention discloses a method and an arrangement providing transmission of data through a node, e.g. a switch, having different input and output line interfaces in a wide range of data speed, without introducing any loss of bits, but still maintaining the nominal bit rate. This is achieved by means of a very simple and flexible implementation. At the receiving side of the switch, one extra bit per frame is transferred over the time slot bus of the switch if the number of bits in the corresponding FIFO of the input line exceeds a predefined upper limit. In contrast, one bit less per frame is transferred if the number of bits in the corresponding FIFO of the input line goes below a predefined lower limit. At the transmitting side of the switch, a FLL circuit regulates the data rate out of the FIFOs. The FLL circuit is implemented as a P-regulator having i.a. the fill degree of the FIFO as a direct input. Consequently, excellent jitter and frequency stability are achieved, and because of not using an I-component, the FLL circuit becomes stable.
Owner:TELEFON AB LM ERICSSON (PUBL)
Method and device for controlling a technical system by means of control models
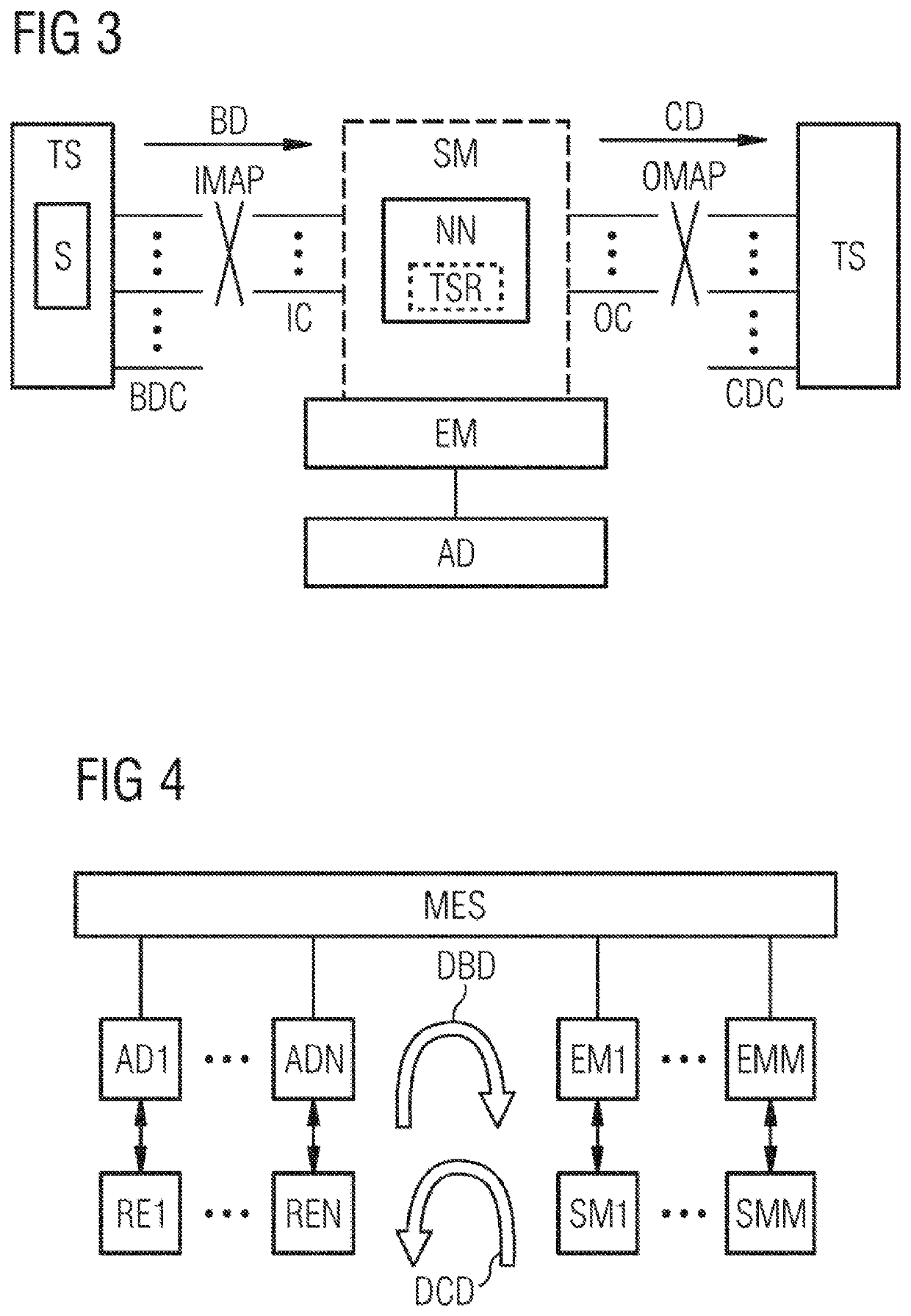
ActiveUS20200301375A1Simple and flexible implementationAppropriately drivenProgramme controlSimulator controlControl engineeringControl data
In order to control a technical system by means of control model a data container is received, in which data container a control model having a training structure and model type information are encoded over all the model types. One of multiple model-typespecific execution modules is selected for the technical system as a function of the model type information. Furthermore, operating data channels of the technical system are assigned input channels of the control model as a function of the model type information. Operating data of the technical system are acquired via a respective operating data channel and are transferred to the control model via an input channel assigned to this operating data channel. The control model is executed by means of the selected execution module, wherein control data are derived from the transferred operating data according to the training structure and are output to control the technical system.
Owner:SIEMENS AG
Rate adaption within a tdm switch using bit stuffing
InactiveUS20050002336A1Avoid introducingExcellent jitter and frequency stabilityError preventionTransmission systemsLower limitData rate
The present invention discloses a method and an arrangement providing transmission of data through a node, e.g. a switch, having different input and output line interfaces in a wide range of data speed, without introducing any loss of bits, but still maintaining the nominal bit rate. This is achieved by means of a very simple and flexible implementation. At the receiving side of the switch, one extra bit per frame is transferred over the time slot bus of the switch if the number of bits in the corresponding FIFO of the input line exceeds a predefined upper limit. In contrast, one bit less per frame is transferred if the number of bits in the corresponding FIFO of the input line goes below a predefined lower limit. At the transmitting side of the switch, a FLL circuit regulates the data rate out of the FIFOs. The FLL circuit is implemented as a P-regulator having i.a. the fill degree of the FIFO as a direct input. Consequently, excellent jitter and frequency stability are achieved, and because of not using an I-component, the FLL circuit becomes stable.
Owner:TELEFON AB LM ERICSSON (PUBL)
Universal method and system for user registration authentication based on fingerprint characteristics
The invention relates to a universal method and a universal system for user registration authentication based on fingerprint characteristics. The universal method is characterized by including steps of: 1 generating a registration name and a secret key by combining newly type-in fingerprint information with a realm name, and filling the registration name and the secret key into a registration form; and 2 searching for the content of the registration form according to the fingerprint information when a user logs in, detecting whether the user is registered, enabling the user to log in successfully when the user is registered and to be capable of correcting the secret key and performing step 1 if the user is not registered.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Method and device for monitoring status of computer power supply fan
InactiveCN100472467CEasy to handlePerfectly compatibleHardware monitoringMonitoring statusControl system
This invention relates to one device and method to monitor computer power fan status, which comprises the following parts: speed sensor connected to computer power exit; A / D converter; receive signal end on computer host board and monitor control module, monitor control module to read fan rotation signal from signal end to judge whether the fan is normal by protection actions of control system.
Owner:LENOVO (BEIJING) LTD
Security protection system and method for application program
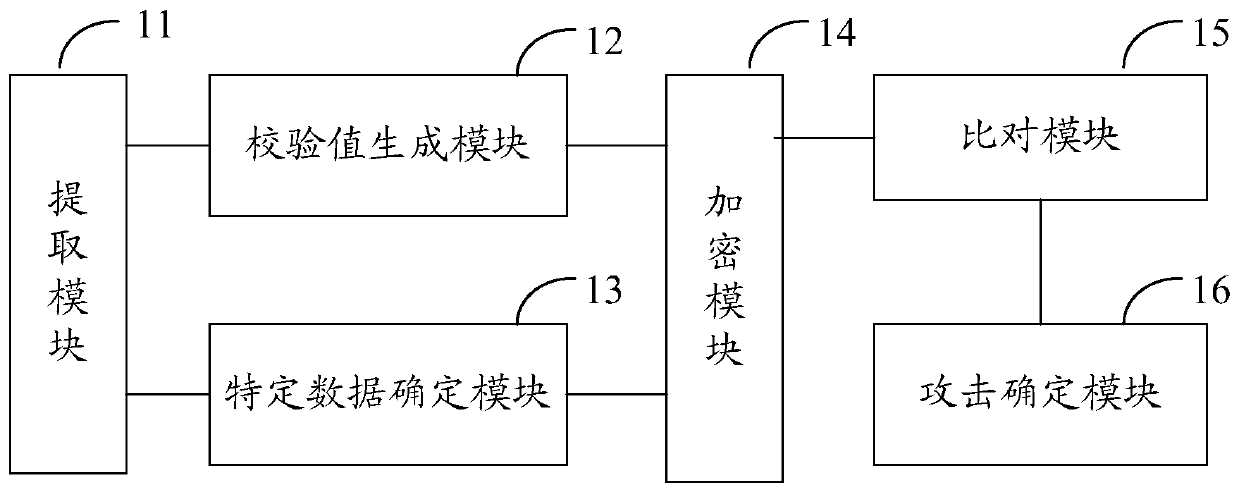
InactiveCN110147655ARealize security protectionSimple and flexible implementationDigital data protectionProgram/content distribution protectionApplication softwareProtection system
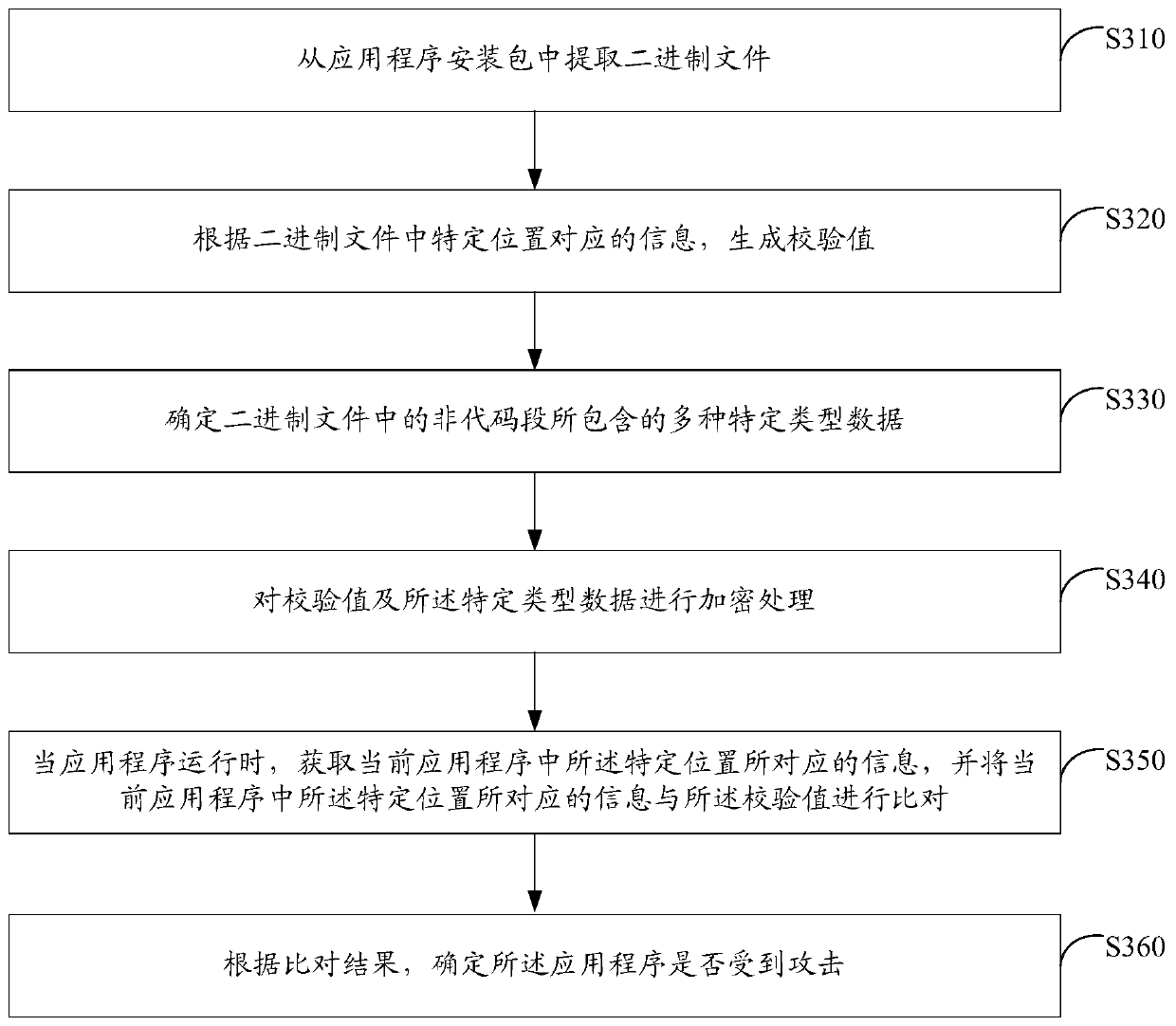
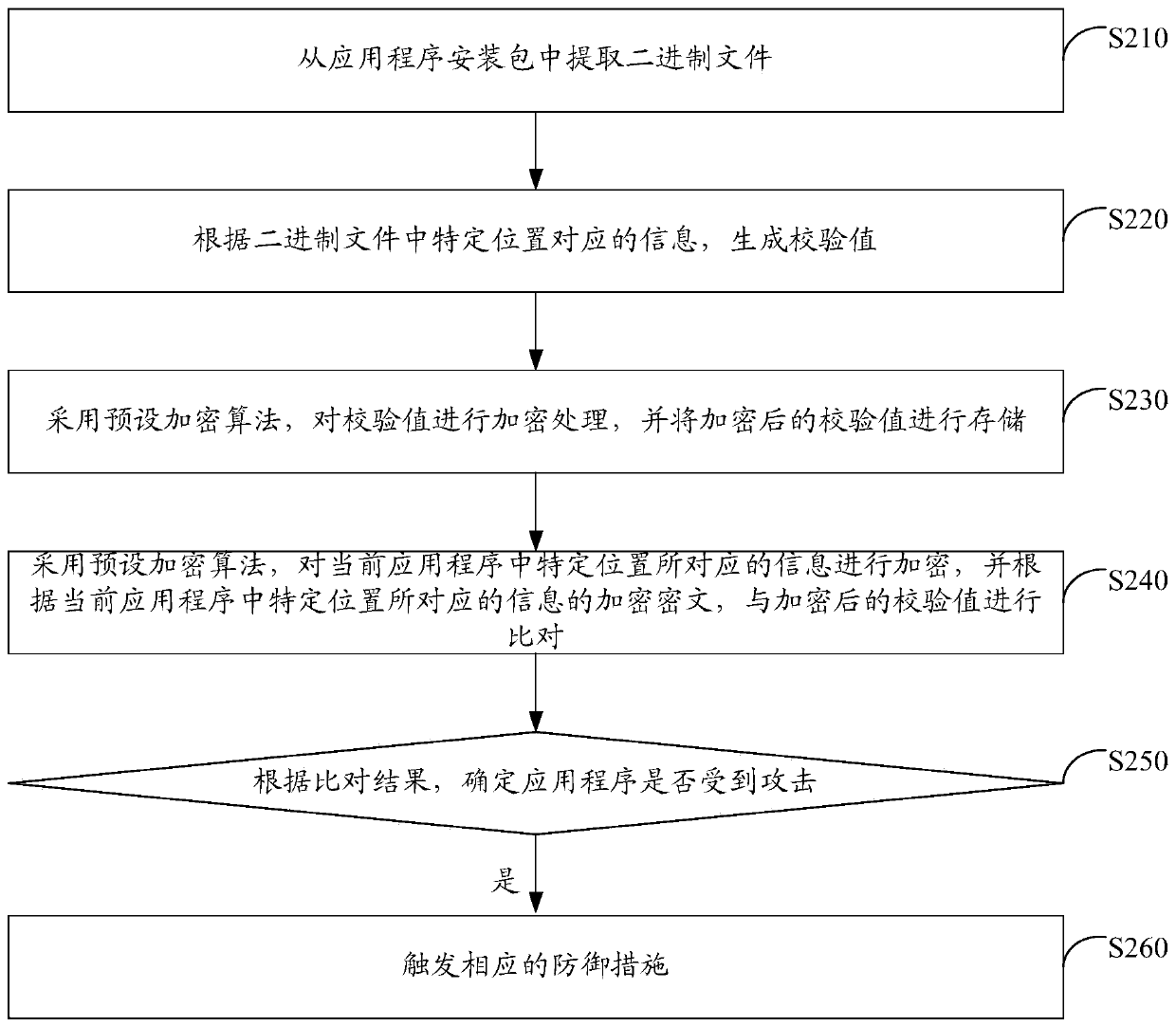
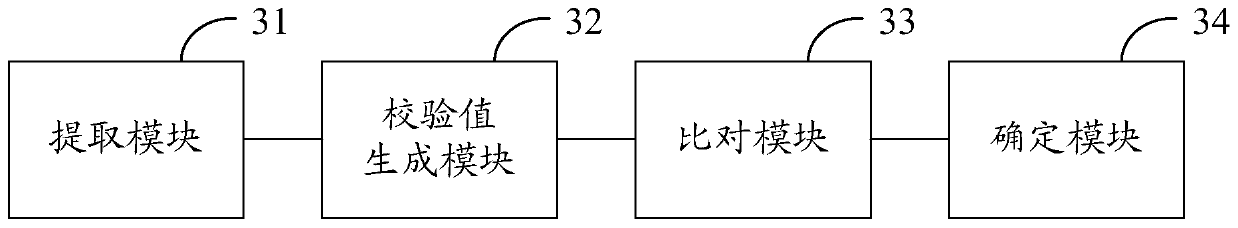
The invention discloses a security protection system and method for an application program. The security protection system comprises: an extraction module which is suitable for extracting a binary file from an application installation package, a check value generation module which is suitable for generating a check value according to the information corresponding to the specific position in the binary file, a specific data determining module which is suitable for determining various specific types of data contained in the non-code segment, an encryption module which is suitable for performingencryption processing on the check value and the specific type of data, a comparison module which is suitable for obtaining information corresponding to a specific position in the current applicationprogram when the application program runs and comparing the information corresponding to the specific position in the current application program with the verification value, and an attack determination module which is suitable for determining whether the application program is attacked or not according to the comparison result. According to the scheme, static analysis and dynamic analysis of theapplication program can be prevented, so that security protection of the application program is realized; and the implementation process is simple and flexible, and batch maintenance is easy, and themaintenance cost is low.
Owner:JIANGSU PAYEGIS INFORMATION SECURITY TECH CO LTD
Remotely operated target-processing system
ActiveUS9671197B2Simple and flexible implementationReduce in quantityArmoured vehiclesWeapon control systemsControl signalCentral unit
A remotely operated target-processing system includes a shooting robot having a stand supporting a firing part having an optoelectronic aiming device providing an image of the target, sensors detecting the relative position of the firing part, and actuators positioning the firing-pt. A central unit receives the instructions and the signals from the sensors and generates control signals for the actuators and the firing-pert. A control screen displays the image and embeds aiming data, and a control member directs the trajectory line.
Owner:LEVILLY PHILIPPE
Method and system for implementing mobile switch center dual homing
ActiveUS8452331B2Improve safety and reliability performanceSimple and flexible implementationSubstation equipmentTransmissionComputer architectureState switching
A method for implementing Mobile Switch Center (MSC) dual homing includes: dividing a first physical MSC Server into a plurality of virtual MSC Servers; establishing a dual homing relation between a first virtual MSC Server of the plurality of virtual MSC Servers and a second physical MSC Server; switching by the first virtual MSC Server from idle state to activate state if determining by the first virtual MSC Server that state switching is needed The scheme may implement the Mobile Switch Center (MSC) dual homing, and improve the reliability of mobile communication network; the implementation is simple and flexible.
Owner:HUAWEI TECH CO LTD
Application attack detection method and device
ActiveCN110135152APrevent dynamic attacksIncrease the reverse difficultyPlatform integrity maintainanceProgram/content distribution protectionComputer engineering
The invention discloses an application attack detection method and device, and is characterized in that the method comprises the steps: extracting a binary file from an application installation package; generating a check value according to the information corresponding to the specific position in the binary file; when the application program runs, obtaining information corresponding to a specificposition in the current application program, and comparing the information corresponding to the specific position in the current application program with the check value; and determining whether theapplication program is attacked or not according to a comparison result. According to the scheme, the information corresponding to the specific position in the binary file is used as the check value;the application program attack is monitored according to the check value, so that whether the application program is attacked or not can be quickly and accurately determined, the application program is prevented from being dynamically attacked, the reverse difficulty of the application program is greatly improved, the security of the application program is ensured, and code expansion of the application program is not easily caused; moreover, the implementation process is simple and flexible, batch maintenance is easy, and the maintenance cost is low.
Owner:JIANGSU PAYEGIS INFORMATION SECURITY TECH CO LTD +1
A closed-loop signal acquisition method in an optical interferometric gravimeter
ActiveCN105911605BHigh sensitivityHigh measurement accuracyGravitational wave measurementBeam splitterPhase difference
Owner:ZHEJIANG UNIV
Application security hardening method and device
ActiveCN110147653BTo achieve reinforcementIncrease the reverse difficultyProgram/content distribution protectionReverse analysisData segment
The invention discloses an application program security reinforcement method and device. Wherein, the method includes: extracting the executable file from the preset application file in the application program; parsing the executable file to obtain the data segment and / or link segment in the executable file; aiming at the data segment in the executable file and / or link segments for encryption. By encrypting the data segment and / or link segment of the binary file, this solution can realize the reinforcement of the application program, thereby greatly increasing the reverse difficulty of the application program, effectively preventing the reverse analysis of the application program, and is not easy to cause the code of the application program to Expansion; moreover, the implementation process of this solution is simple and flexible, easy to maintain in batches, and the maintenance cost is low.
Owner:JIANGSU PAYEGIS INFORMATION SECURITY TECH CO LTD +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com