Chaotic key-based data encryption transmission card
A data encryption and key technology, applied in the field of communication engineering, can solve problems such as insecurity, achieve the effect of solving complex computing problems, improving computing speed and deciphering difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
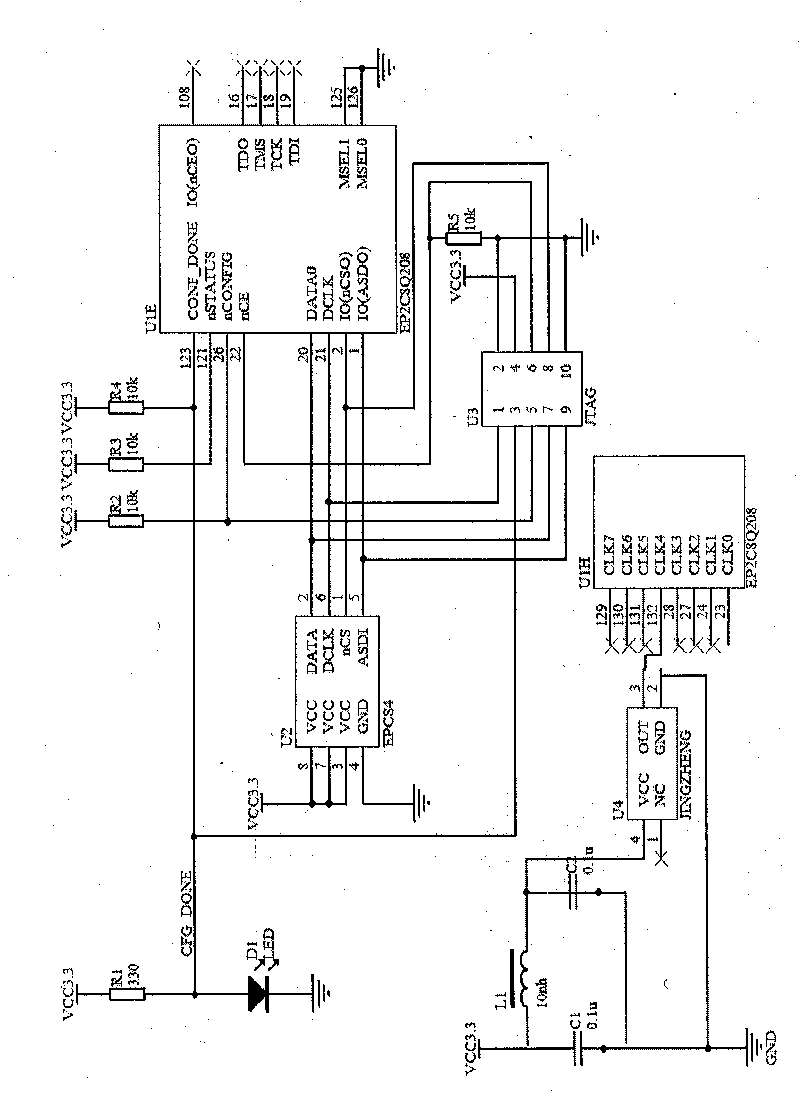
[0024] Example 1: Combining figure 1 , the present invention is a data encryption transmission card based on a chaotic key, which is composed of a standard RS-232 transceiver and an FPGA encryption chip, and the standard serial data sent by the serial port of the PC is demodulated by the standard RS-232 transceiver The standard TTL level is sent to the I / O port of the FPGA encryption chip. After being encrypted by the FPGA encryption chip, it is modulated by the RS-232 transceiver to a standard 232 level and sent to the communication channel.
[0025] The present invention also has the following technical characteristics:
[0026] Described FPGA encryption chip comprises chaotic key sequence module, control module, data encryption and decryption module and asynchronous serial sending and receiving module, under the control of control module, produces key sequence by chaotic key sequence module, provides data encryption The decryption module encrypts and decrypts, and the proc...
Embodiment 2
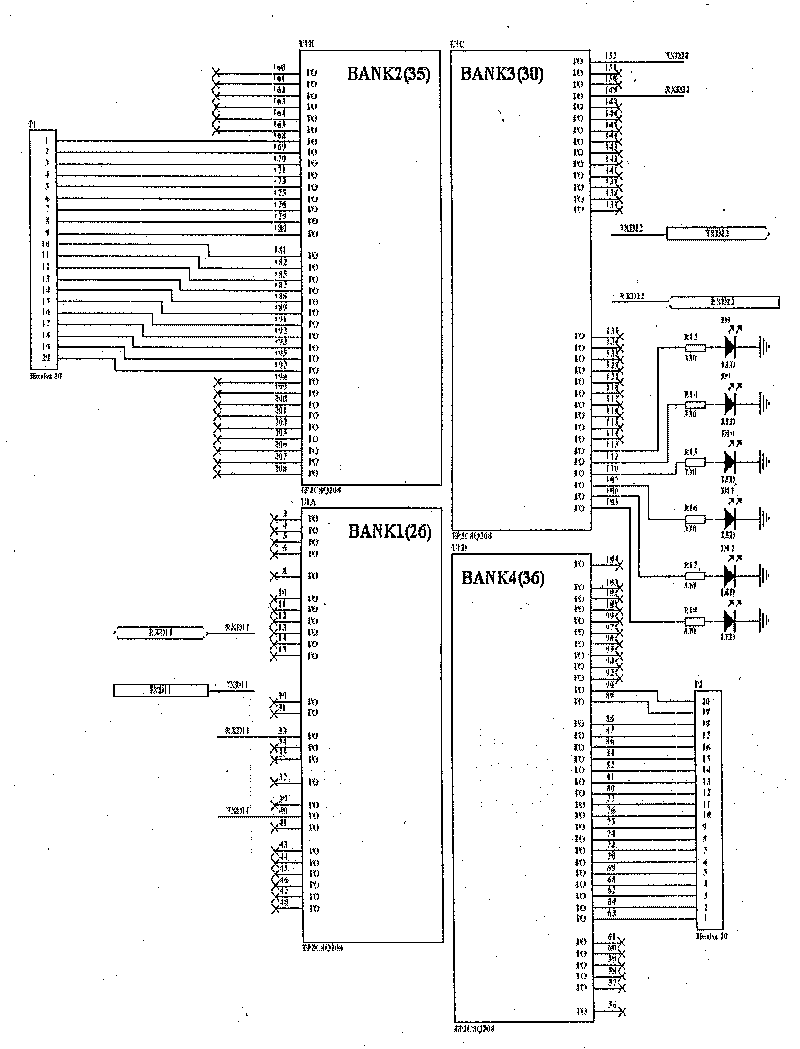
[0029] Example 2: Combining figure 1 , figure 2 , image 3 , the present invention is a data encryption transmission card based on a chaotic key, which is composed of an encryption chip and a peripheral circuit of the data encryption transmission card, and the encryption chip based on a chaotic key is housed on the described data encryption transmission card; the encryption The chip is composed of a chaotic key sequence module, a control module, a data encryption and decryption module, and an asynchronous serial sending and receiving module; the encryption chip based on the chaotic key performs data exchange through the RS232 interface, so that ordinary data can be encrypted and safely transmitted.
[0030] Data sending process: The packaged data sent by the test software is sent to the modem chip through the serial port of the PC for logic level conversion, and it sends the converted data to the asynchronous serial receiver of the data encryption channel At this time, the ...
Embodiment 3
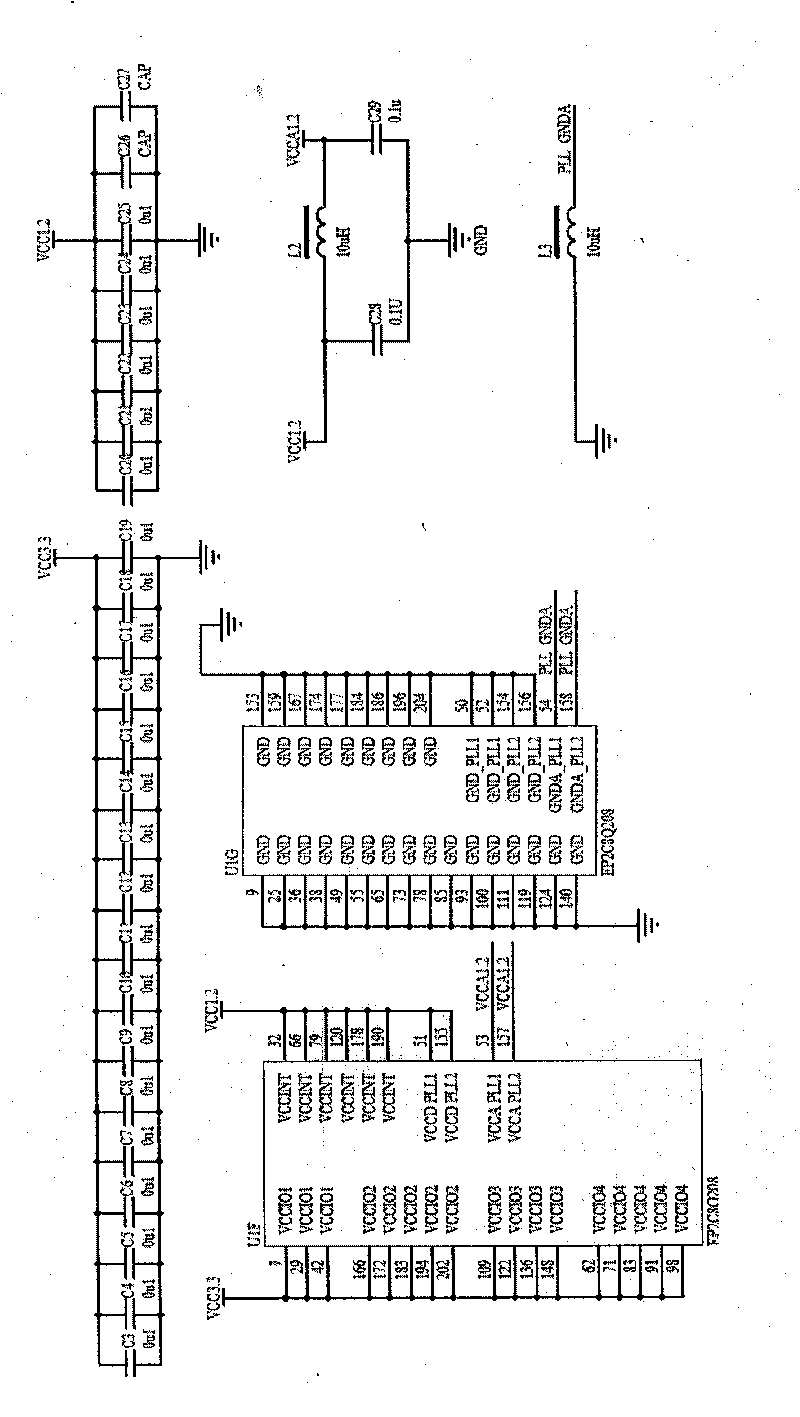
[0032] Example 3: Binding image 3 , Figure 4 , Figure 6 , the present invention is a kind of data encryption transmission card based on chaotic key, and its composition comprises data encryption transmission card, and the encryption chip based on chaotic key sequence is housed on the data encryption transmission card, and the encryption chip is composed of chaotic key sequence module, main control module , Data encryption and decryption module and asynchronous serial sending and receiving module.
[0033] The data encryption and decryption module is an improved A5 sequence cipher. On the basis of the original A5 sequence cipher, the chaos module is introduced as the initial data input and participates in the A5 cipher operation, which enhances the difficulty of password deciphering. More importantly, it uses VHDL programming to realize High-speed hardware encrypted transmission. In the circuit implementation, the bit signal of the extracted LFSR (LFSR, Linear Feedback Sh...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com