Identity verifying method, device and system
An identity verification method and a verification code technology are applied in the fields of devices and systems, and identity verification methods to achieve the effect of simple verification process and high difficulty in deciphering
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
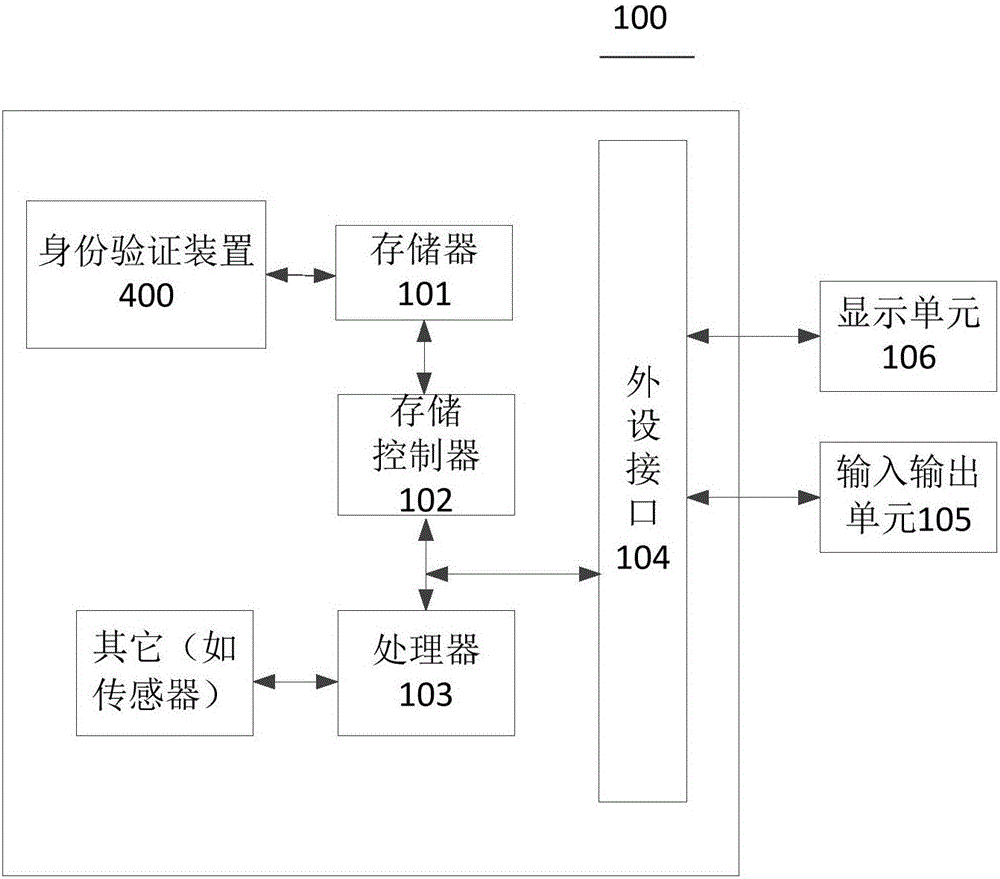
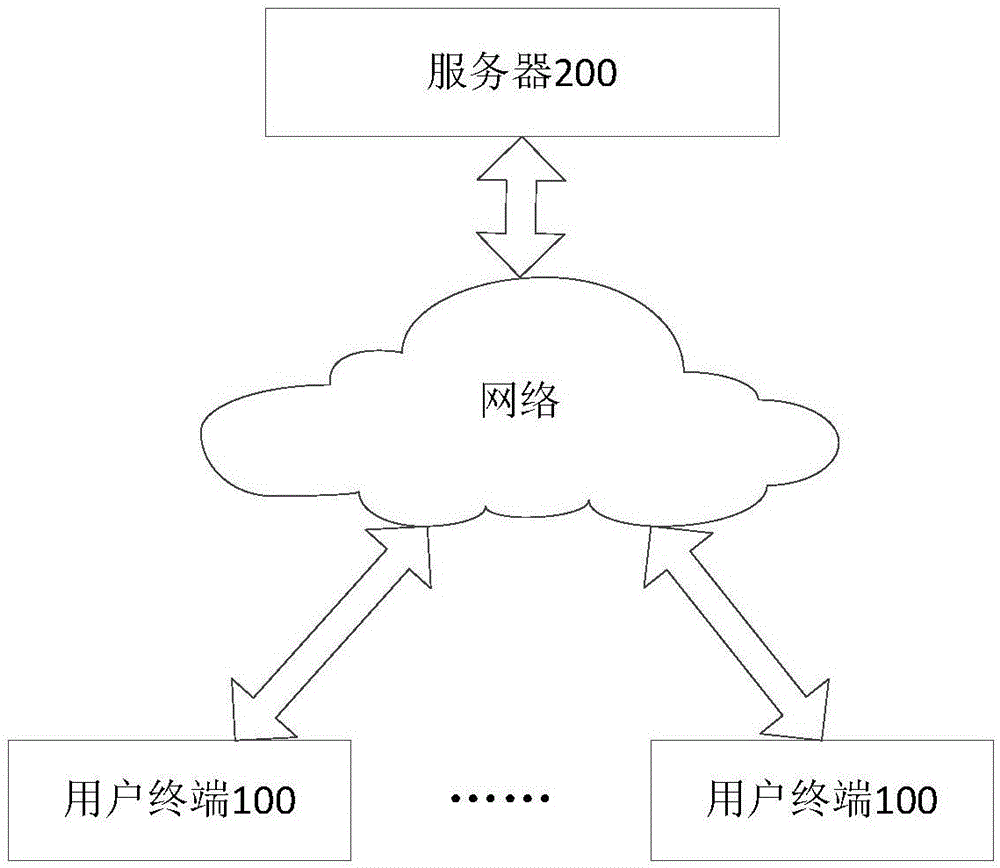
[0041] This embodiment provides an authentication method for such as figure 2 The authentication system shown. See image 3 , the method includes:
[0042] Step S110: the server 200 sends multiple sub-images to the user terminal 100 as a verification code, and the multiple sub-images are obtained by cutting an original image.
[0043] When the user terminal 100 conducts a visit that requires verification, the server 200 sends multiple sub-images obtained by cutting an original image to the user terminal 100 for verification. Preferably, in this embodiment, the original image may include a graphic that is natural and reasonable for users to recognize, such as a car, a mobile phone, a fruit, one or more vegetables, etc., such as Figure 4 , so that the user can easily distinguish the positional relationship between the sub-images when stitching multiple sub-images obtained by cutting the original image.
[0044] The multiple sub-images may be obtained by cutting the origina...
no. 2 example
[0077] This embodiment provides an identity verification method, which is applied to the user terminal 100, please refer to Figure 15 , the method includes:
[0078] Step S210: Receive the multi-block sub-images used as the verification code sent by the server 200, the multi-block sub-images are obtained by cutting an original image.
[0079] Step S220: Displaying the multiple sub-images in random order and simultaneously displaying a mosaic frame for placing the mosaic image, so that the user can mosaic the multiple sub-images into a mosaic image within the mosaic frame.
[0080] Step S230: According to the operation acting on the display interface, the multiple sub-images are spliced within the puzzle frame.
[0081] Step S240: When it is detected that the size of the current mosaic image in the mosaic frame reaches a predetermined size, send the mosaic image in the current mosaic frame to the server 200 so that the server 200 can verify the mosaic image.
[0082] For t...
no. 3 example
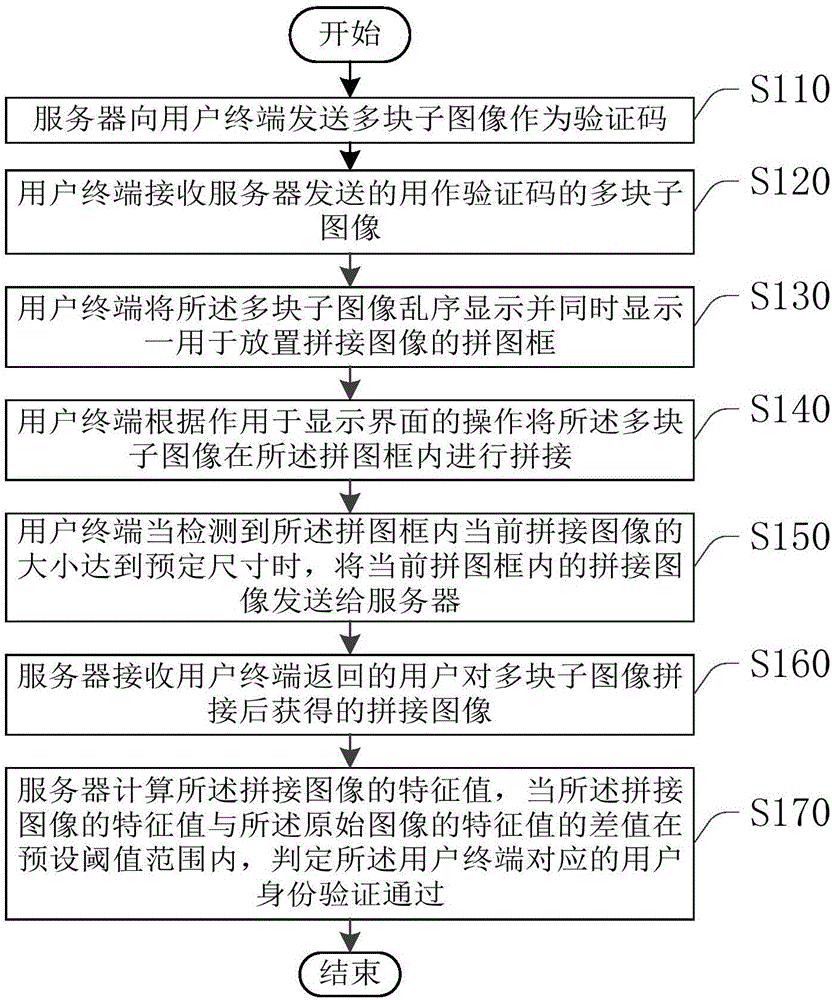
[0084] This embodiment provides an authentication method, which is applied to the server 200, please refer to Figure 16 , the method includes:
[0085] Step S310: Send multiple sub-images to the user terminal 100 as a verification code, so that the user can splicing the multiple sub-images through the user terminal 100 for identity verification, and the multiple sub-images are obtained by cutting an original image;
[0086] Step S320: Receive the spliced image returned by the user terminal 100 and obtained by the user after splicing multiple sub-images.
[0087] Step S330: Calculate the feature value of the stitched image, and when the difference between the feature value of the stitched image and the feature value of the original image is within a preset threshold range, it is determined that the user identity verification corresponding to the user terminal 100 is passed .
[0088] For the specific implementation manner of each step in this embodiment, reference may be m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com