Data encryption method
A data encryption and data technology, applied in encryption devices with shift registers/memory, digital transmission systems, usage of multiple keys/algorithms, etc., can solve problems such as single algorithm, easy to be cracked, etc., to enhance security , the effect of ensuring safety and increasing safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
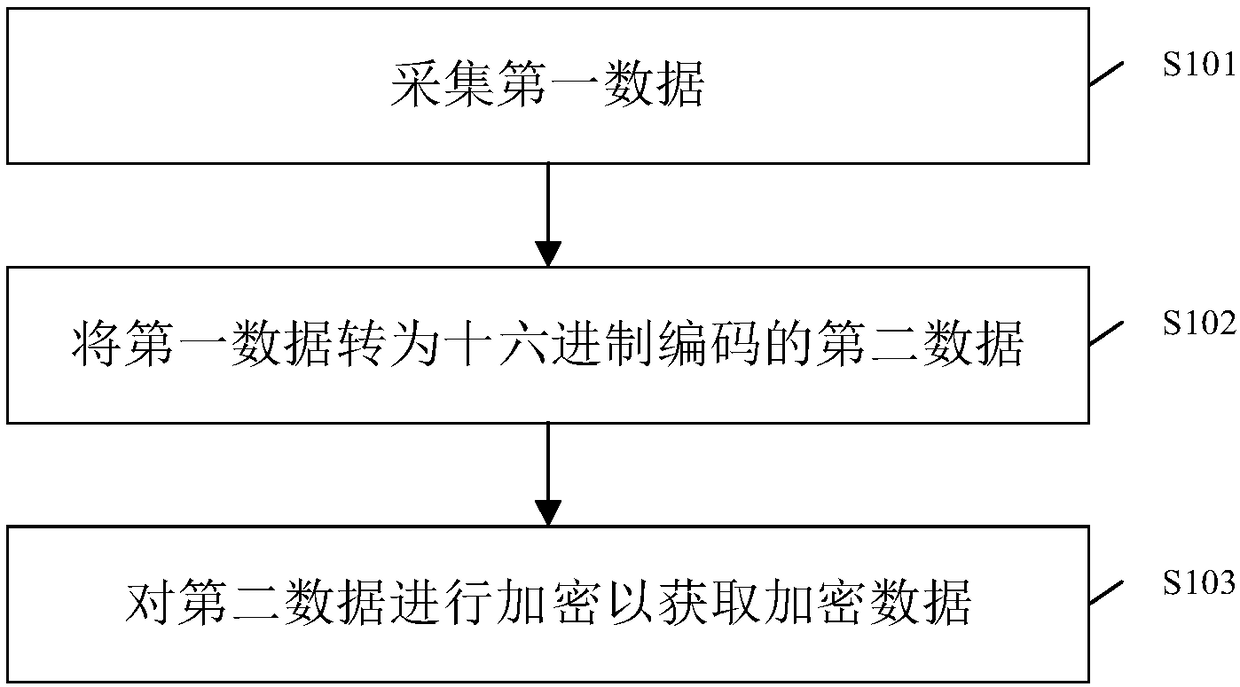
[0044] Such as figure 1 As shown, a data encryption method according to an embodiment of the present invention is provided, which includes the following steps:
[0045] S101 collects first data, where the first data is fingerprint data, ID card data, digital password and / or MF card data.
[0046] S102: Convert the first data into hexadecimal coded second data;
[0047] Further, converting the first data into hexadecimal-encoded second data means: when the first data is fingerprint data, the 498-bit hexadecimal encoding rule is adopted to convert the fingerprint data into hexadecimal. Encoded second data, each fingerprint data in the second data corresponds to two 249-bit hexadecimal coded data packets in the second data, and the two data packets have different numbers.
[0048] Further, converting the first data into hexadecimal-encoded second data refers to: when the first data is data other than fingerprint data, the 12-digit hexadecimal encoding rule is used to separate the fingerp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com