Wireless network authentication apparatus and methods
A technology of wireless services and user equipment, applied in the field of communication systems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] Referring now to the drawings, wherein like numerals refer to like parts throughout.
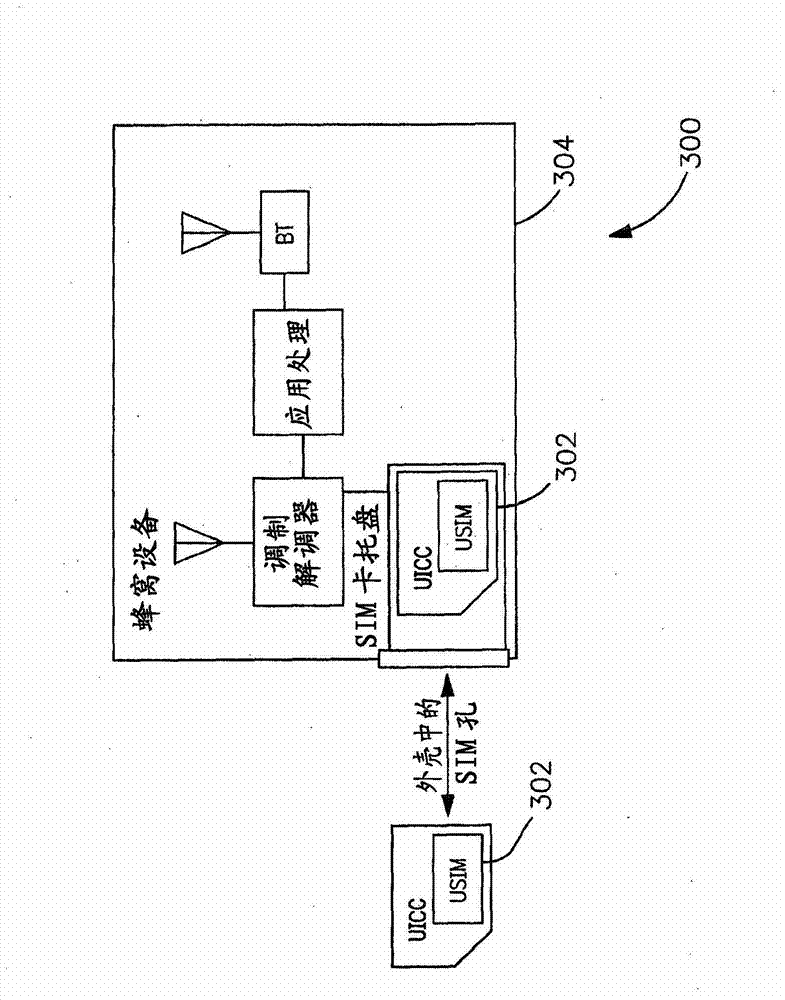
[0048] Those of ordinary skill in the relevant art will recognize that various embodiments of the present invention have different effects on prior art architectures (e.g., USIM data contained in a physical SIM card) and new architectures (e.g., USIM data stored in a secure element). data) are useful. In some variants, the present invention may further combine prior art card operations with secure element operations, enabling support for legacy SIM cards not stored in the secure element.
[0049] In an example embodiment of the invention, the SIM data includes high security content (eg keys and encryption algorithms, etc.) useful especially for authentication. For example, high security content may include authentication keys (Ki) and all encryption algorithms (eg, as published on December 31, 2009 and entitled "Specification of the MILENAGE Algorithm Set: An example algorithm set fo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com