System and method for automatically initiating and dynamically establishing secure internet connections between a fire-walled server and a fire-walled client
a technology of automatic initiation and dynamic establishment, applied in the field of computer networking and network security, can solve the problems of ipv4 not providing sufficient unique addresses for the current expansion of the internet, the practical limit is much lower, and the number of scalability problems of the internet network, so as to avoid performance and security problems and achieve unprecedented ease of use.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
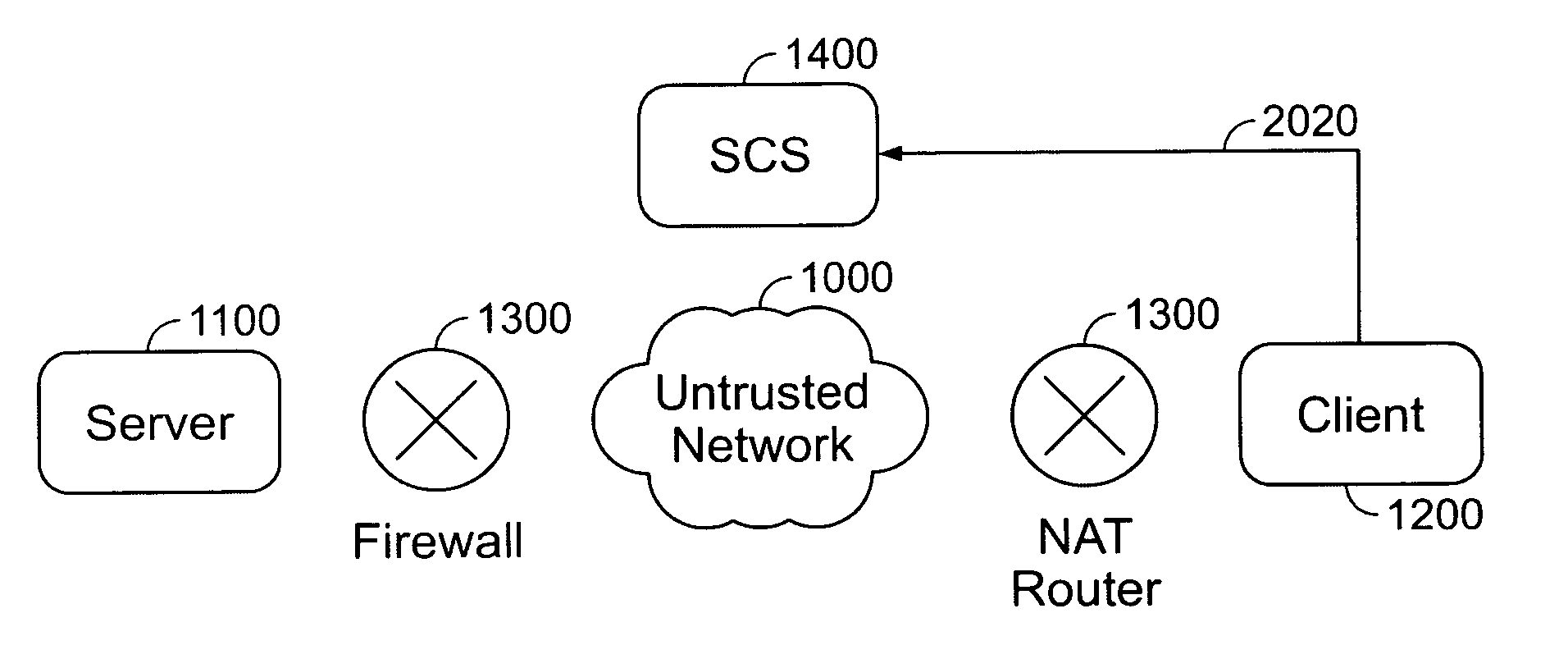
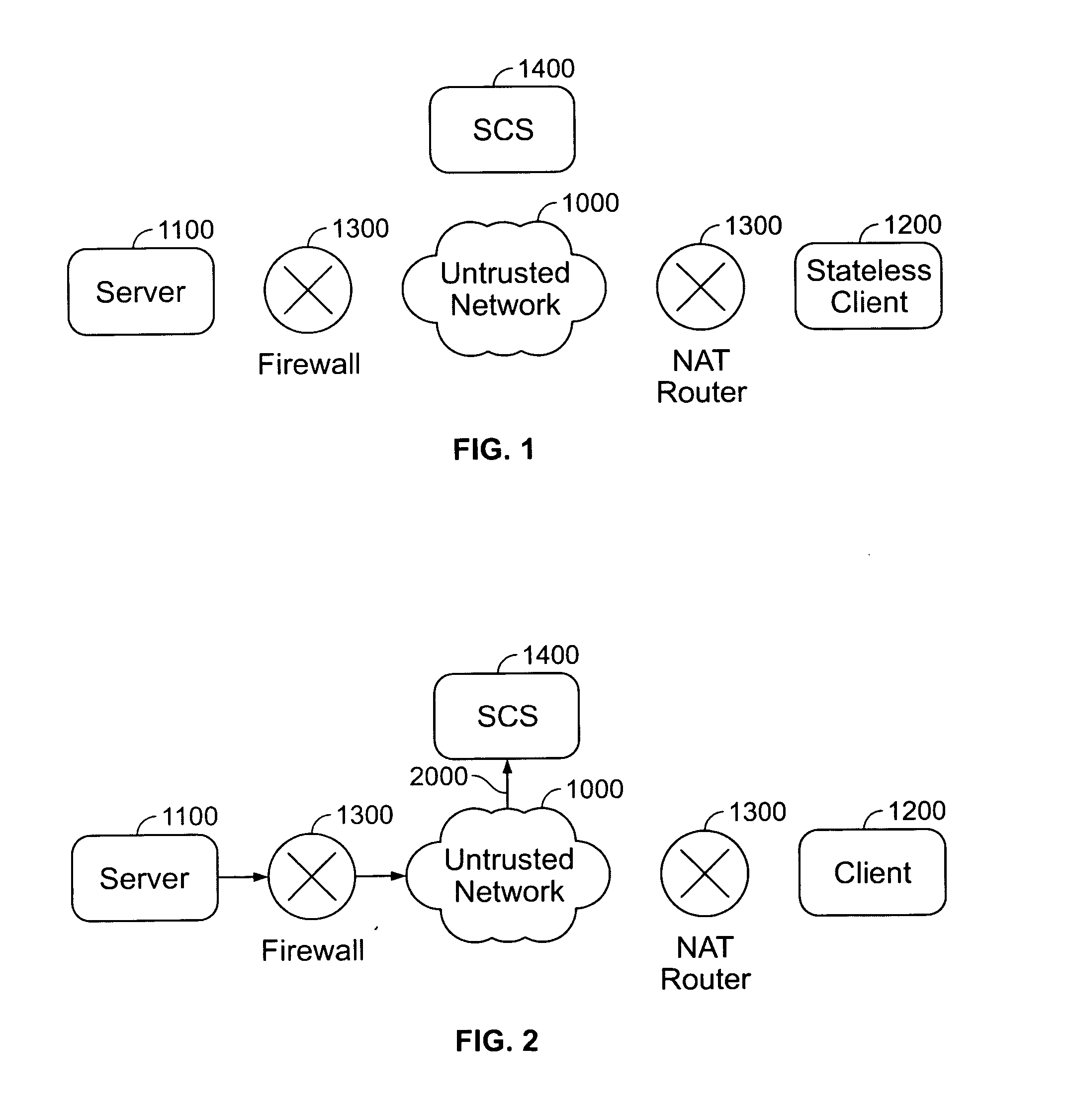
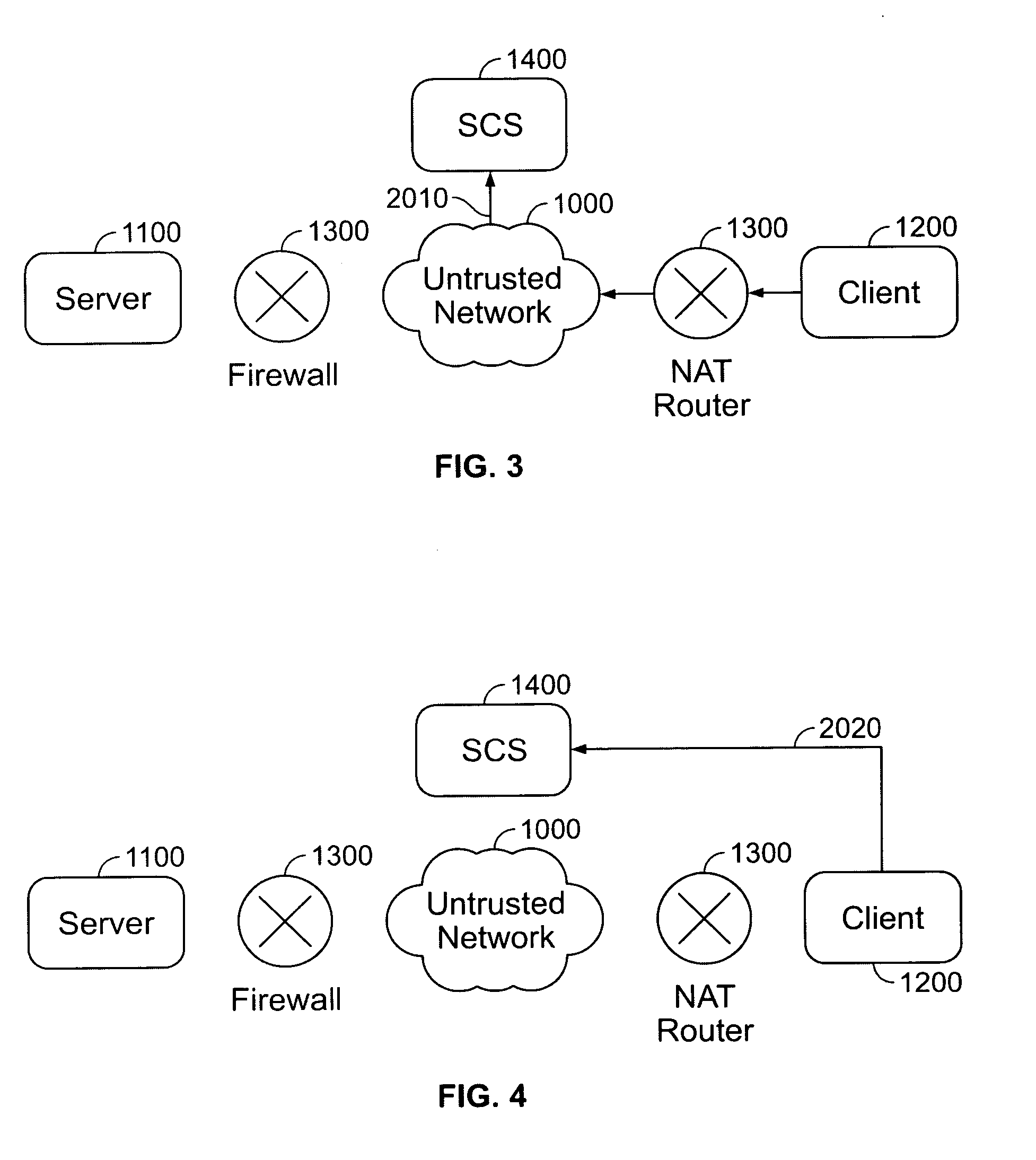
[0021] In accordance with an embodiment of the present invention, the system and method automatically and dynamically initiates and establishes connections, preferably secure connections, between a server and a fire-walled client device. Turning now to FIG. 1, there is illustrated a Server 1100 and a client device (Client 1200), both connected to an untrusted network 1000 (such as the Internet) through a Network Address Translator or Translation (NAT) router or a firewall 1300. The connections between the Server and the Client are initiated and established without requiring any user configuration on the Client 1200 and without accepting any explicit connection request and / or packets from the Client 1200 by the Server 1100, thereby allowing the Server firewall 1300 to always remain closed to all inbound traffic.
[0022] In accordance with an embodiment, the present invention utilizes a third computer 1400, e.g., a trusted party such as a session control server (“SCS”), with a public I...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com