Wireless LAN safety connecting-in control method
A wireless local area network and secure access technology, which is applied in the field of wireless local area network security, and can solve the problems of waste, roaming and other functions.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] The present invention will be further described below in conjunction with the embodiment shown in accompanying drawing:
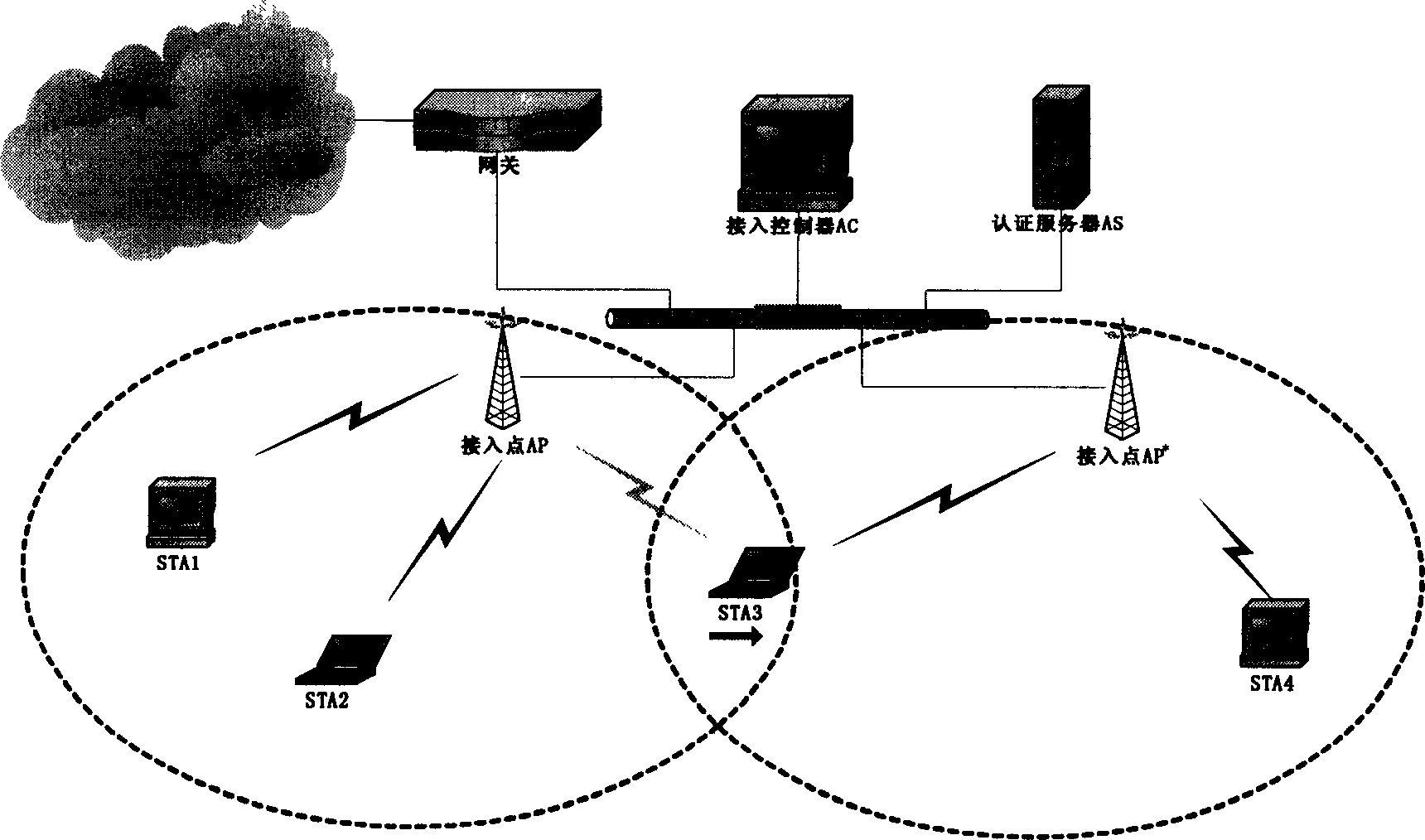
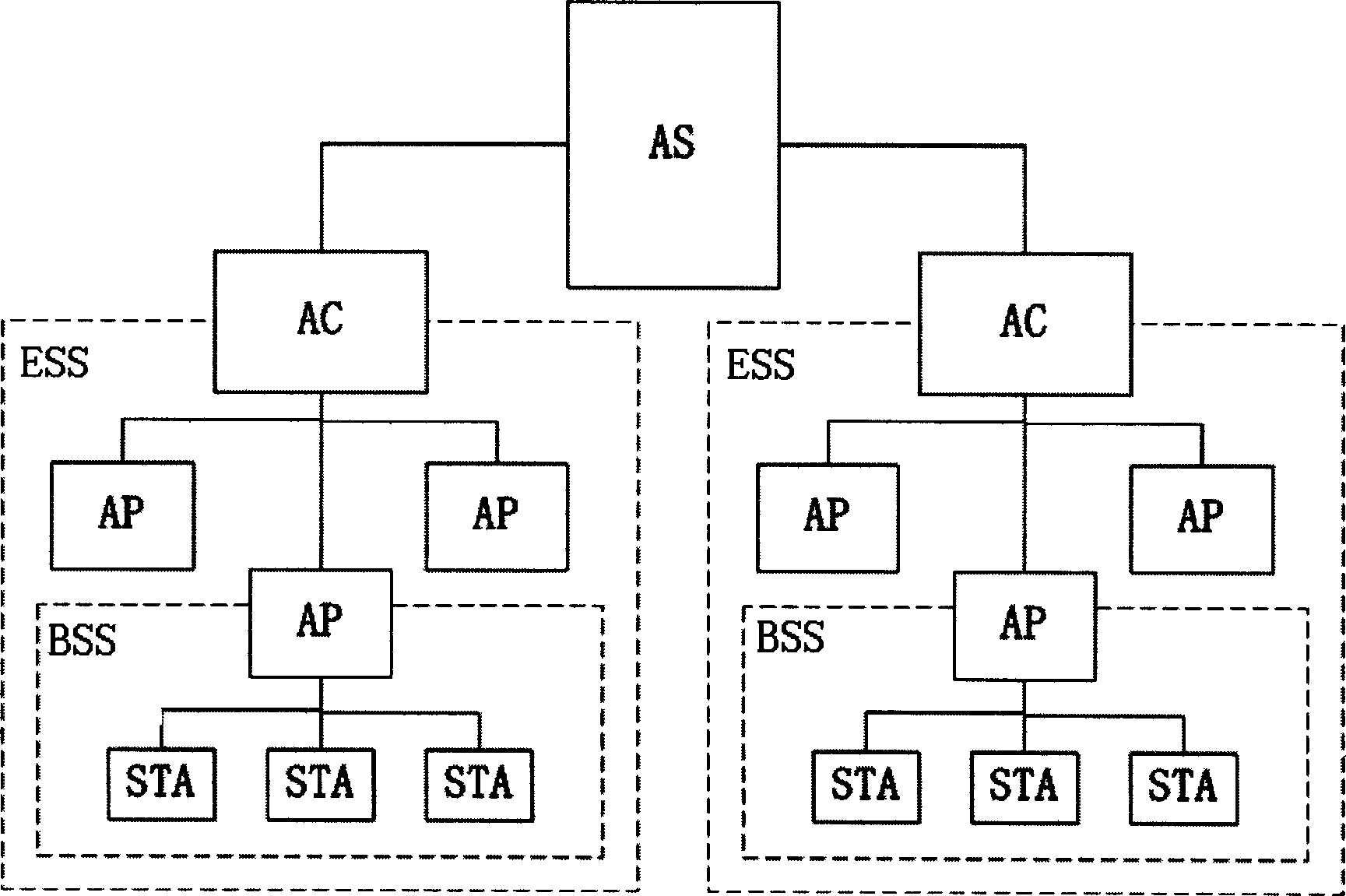
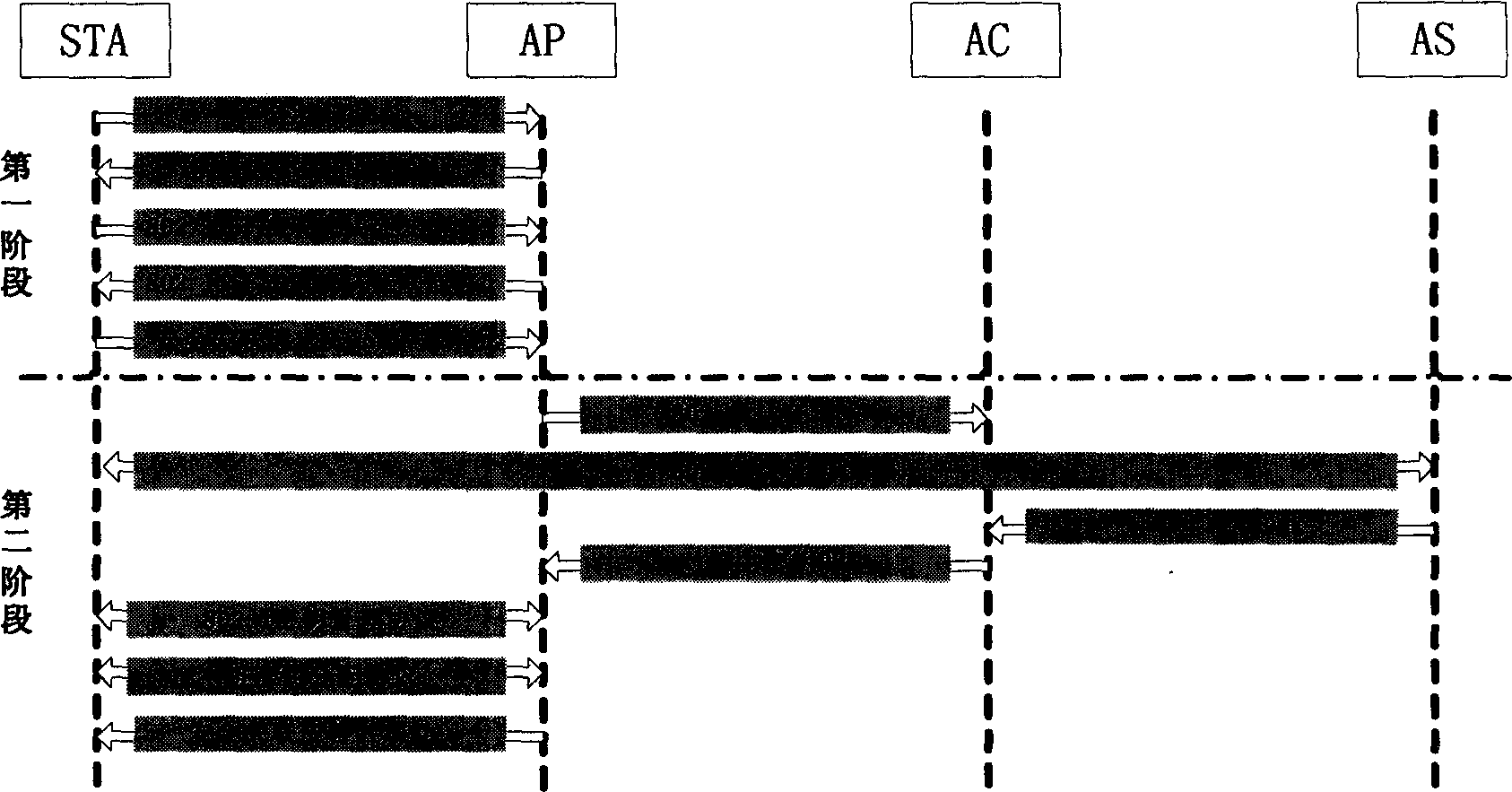
[0046] The wireless local area network security access control method of the present invention is characterized in that: when a STA that has not established a security association with any AP enters the service range of a certain AP, the STA establishes a connection with the AP and negotiates security performance, and then the STA sends a security association establishment link to the AP. The authentication server AS uses the IEEE 802.1x authentication protocol to authenticate the STA. If the authentication fails, the AS notifies the AP to reject the STA’s request to establish a security association. If the authentication succeeds, the peer-to-peer master secret is negotiated between the STA and the AS. PMK, the AS sends the PMK to the access controller AC to register the associated information and PMK information of the corresponding STA; the AC then...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com