Patents
Literature
268results about How to "Control process safety" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
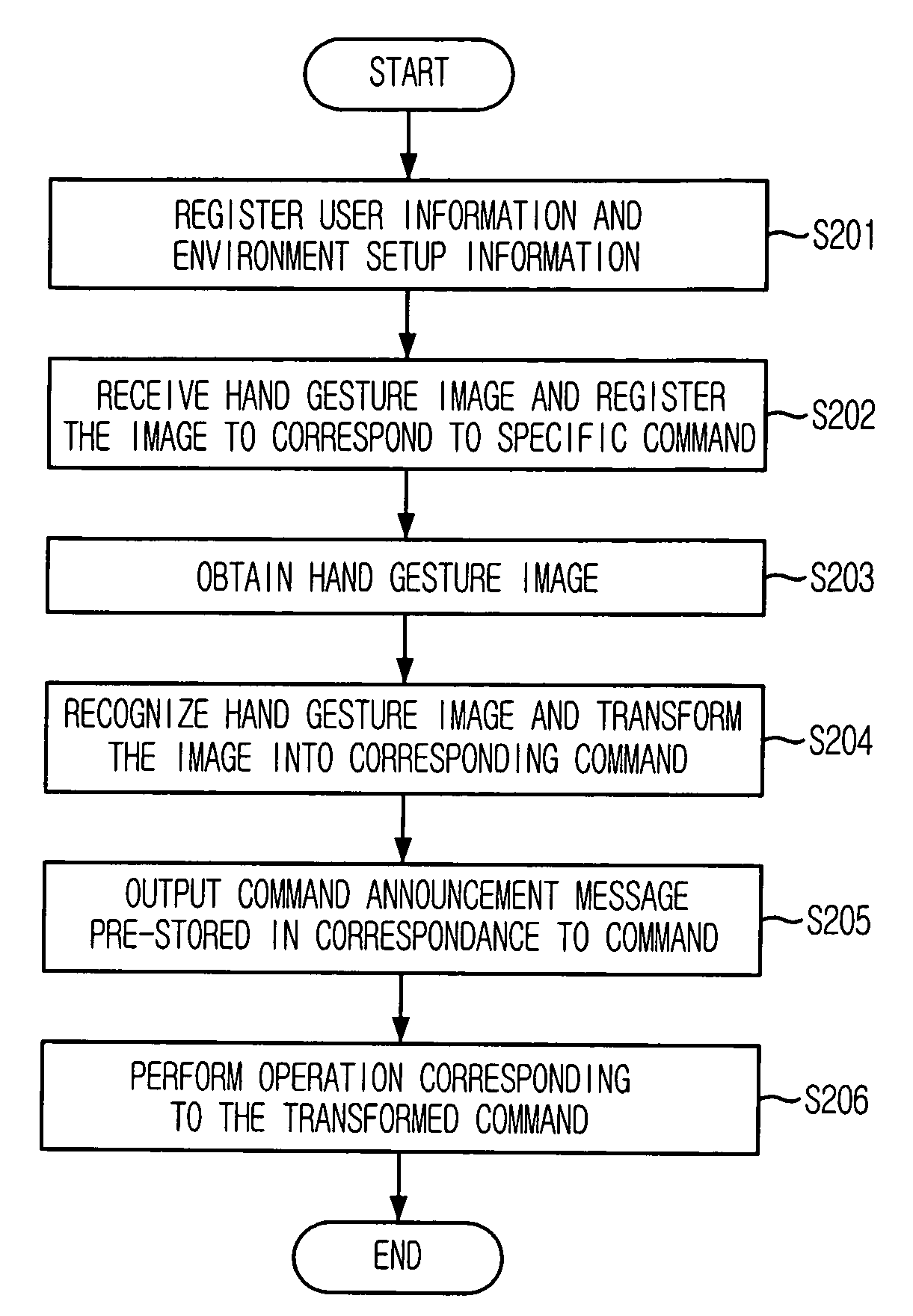
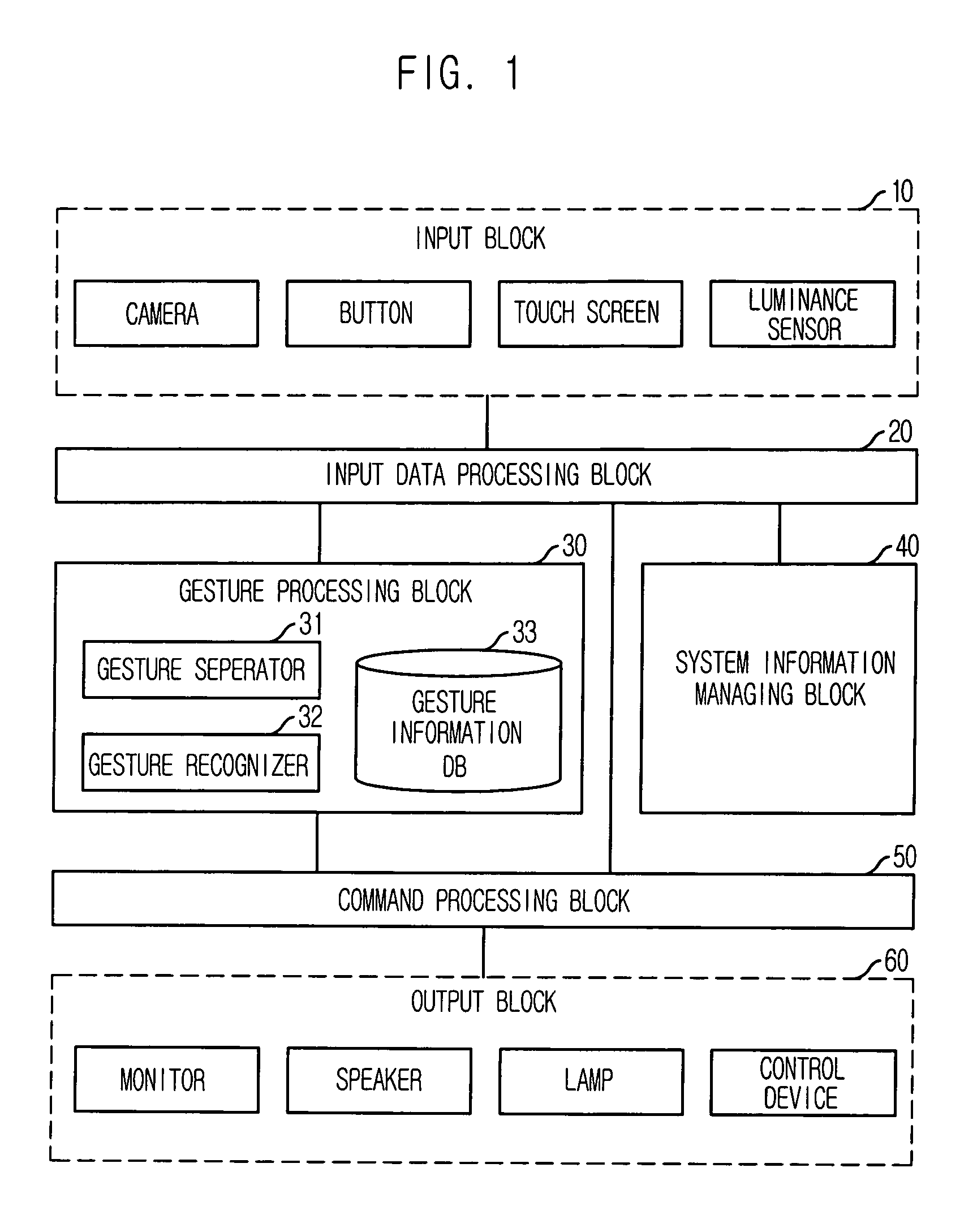
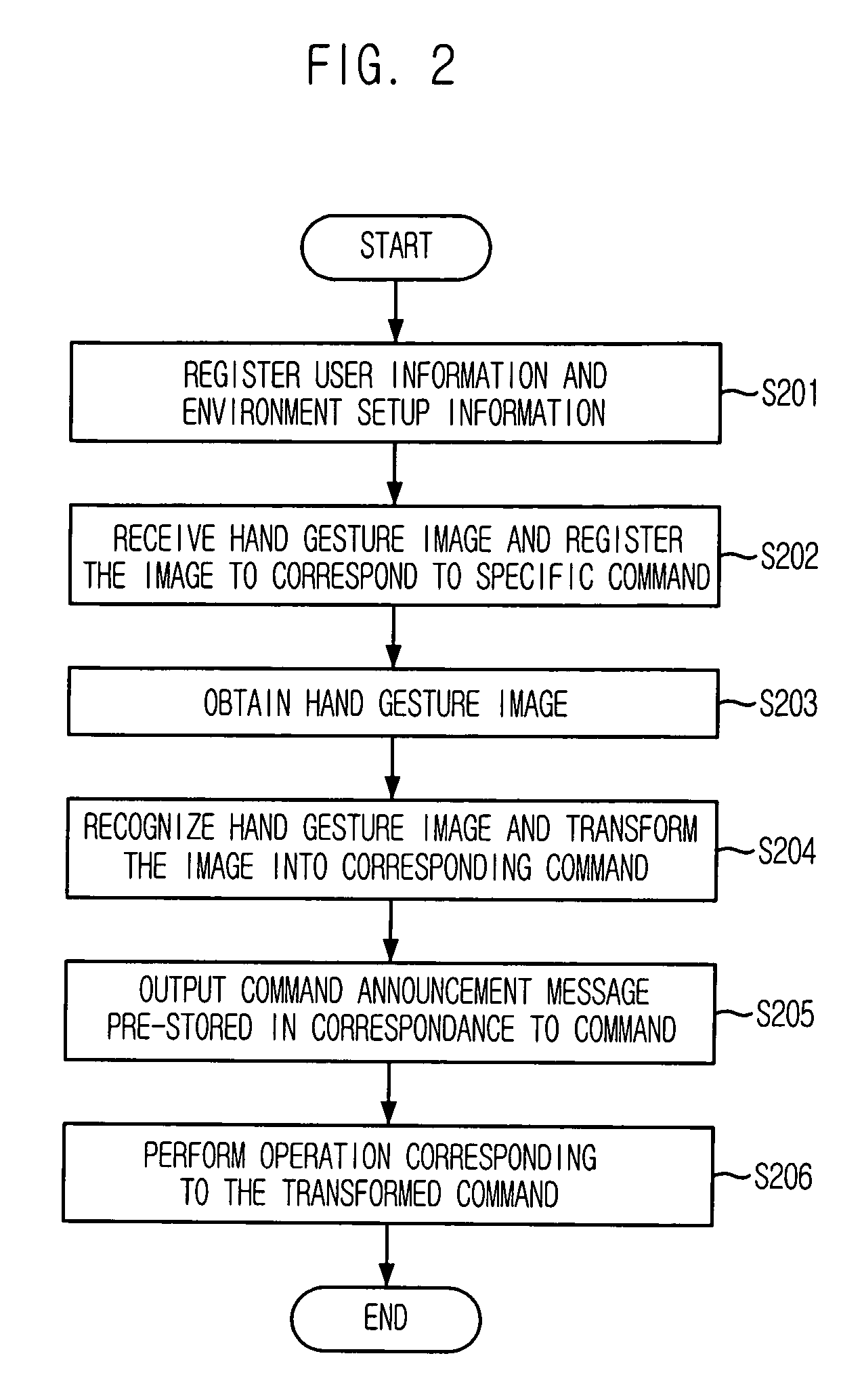
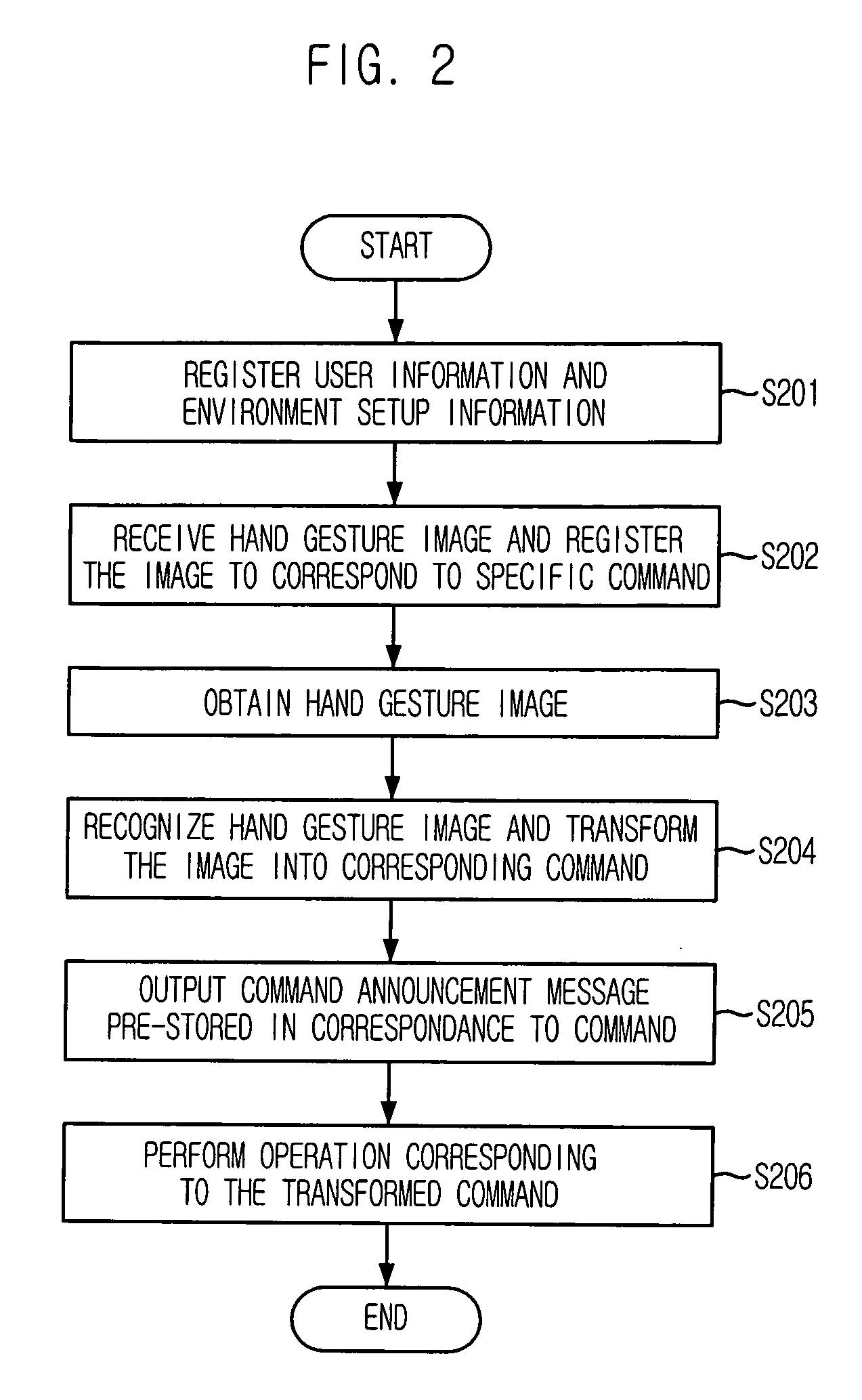
User interface apparatus using hand gesture recognition and method thereof
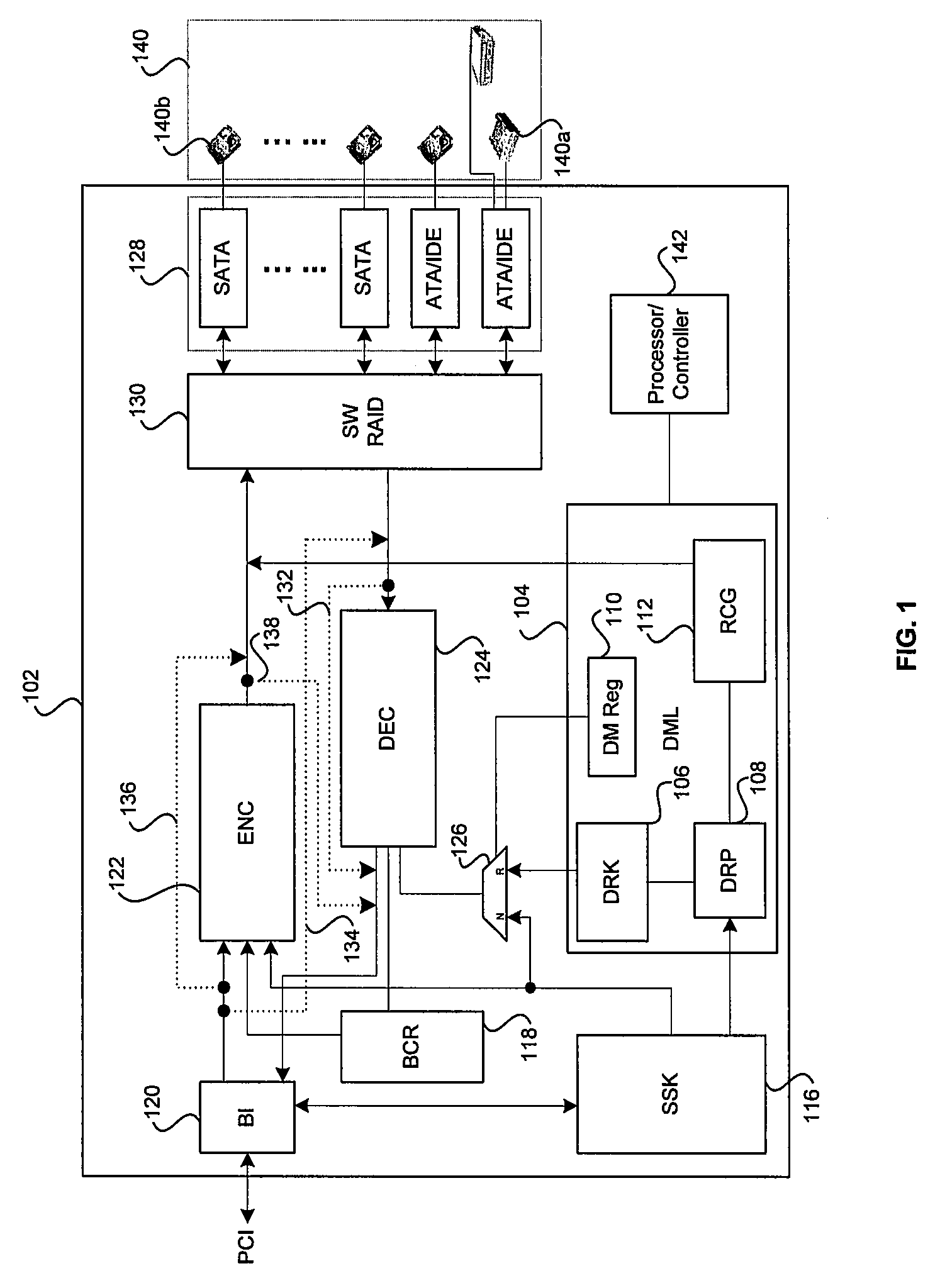
ActiveUS7702130B2Control process safetyEasily embodiedInput/output for user-computer interactionCharacter and pattern recognitionControl signalComputer terminal
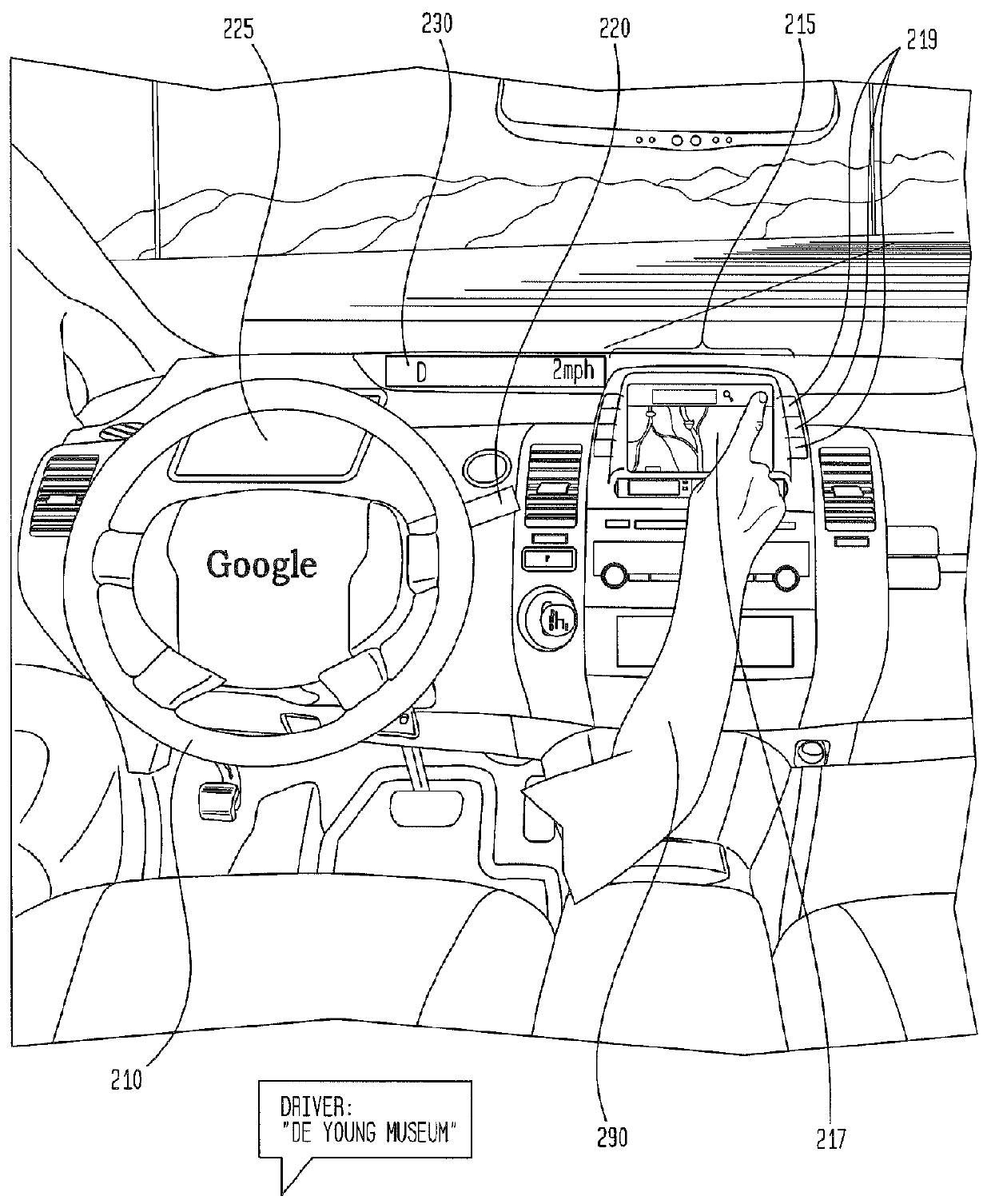
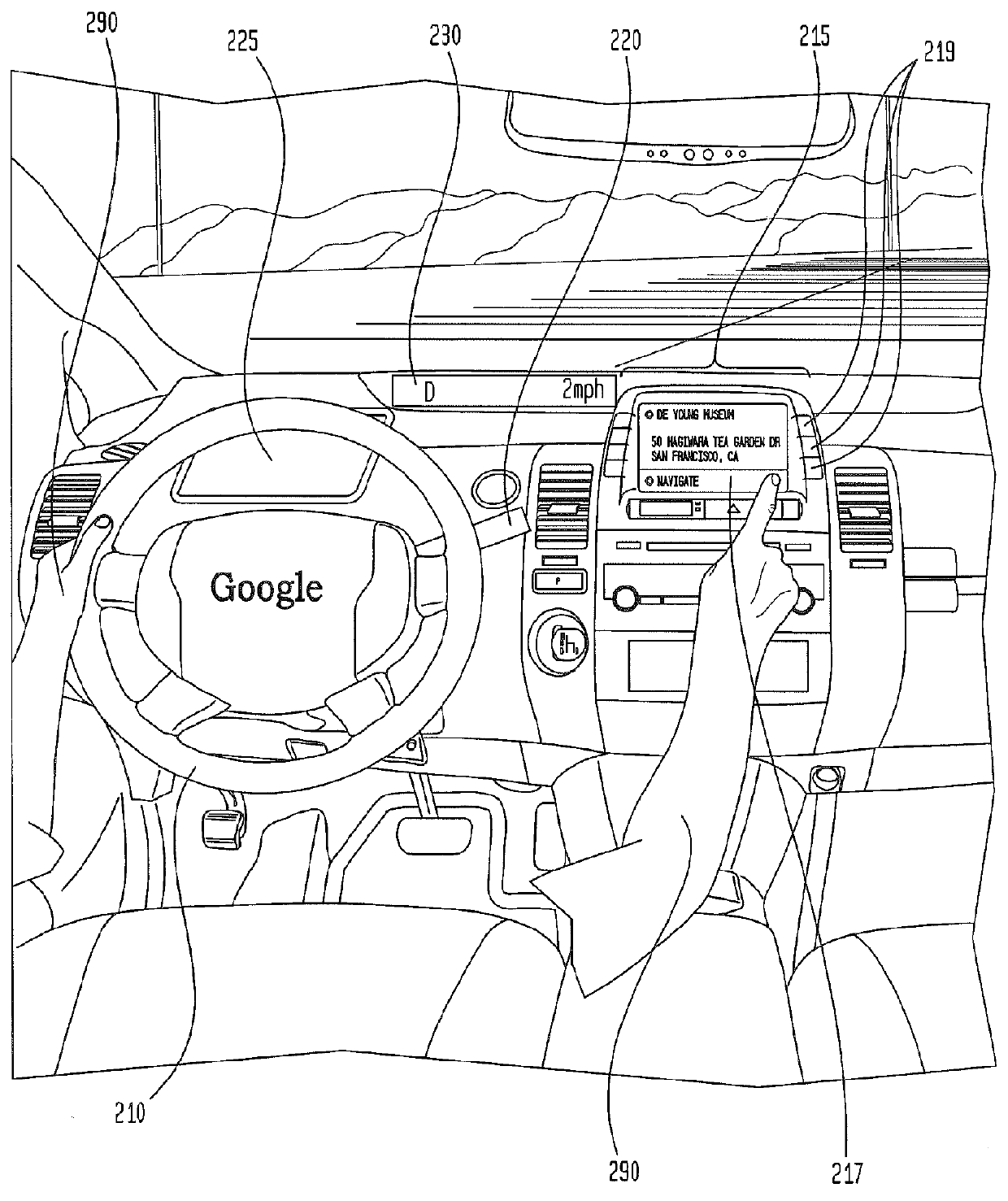
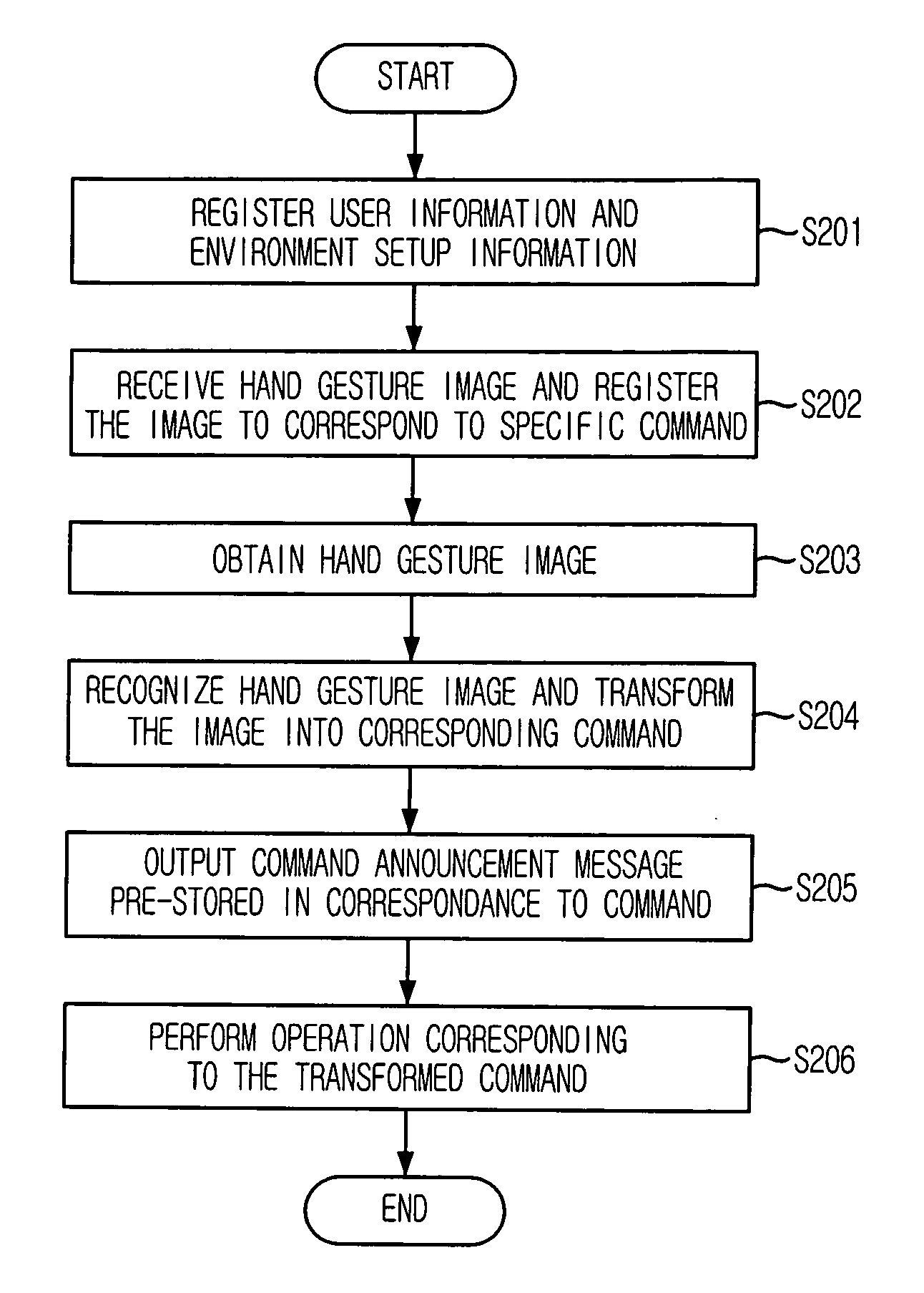
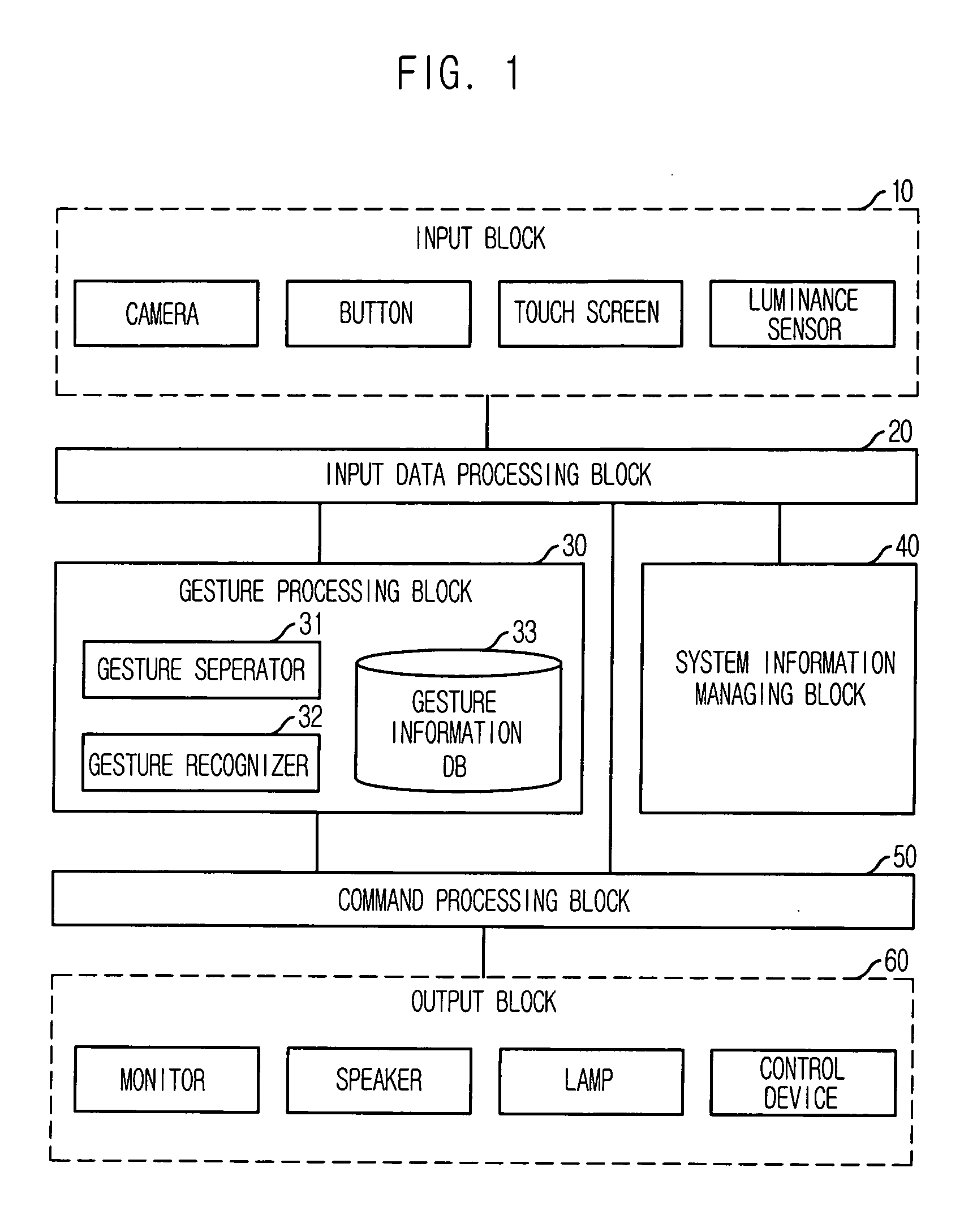
Provided is a user interface apparatus that can control a telematics terminal safely and comfortably while driving, by recognizing a hand gesture image received through a camera in the telematics terminal as a corresponding control signal, and a method thereof. The interface apparatus using a hand gesture recognition, includes: an input receiving block for receiving a command registration request signal and a command selection signal; a hand gesture recognizing block for storing the hand gesture image in connection with a specific command, and transforming the hand gesture image into the corresponding command by recognizing the hand gesture image from the image obtained in the image obtaining block; and a command performing block for performing an operation corresponding to a command transformed in the hand gesture recognizing block.
Owner:INTELLECTUAL DISCOVERY CO LTD
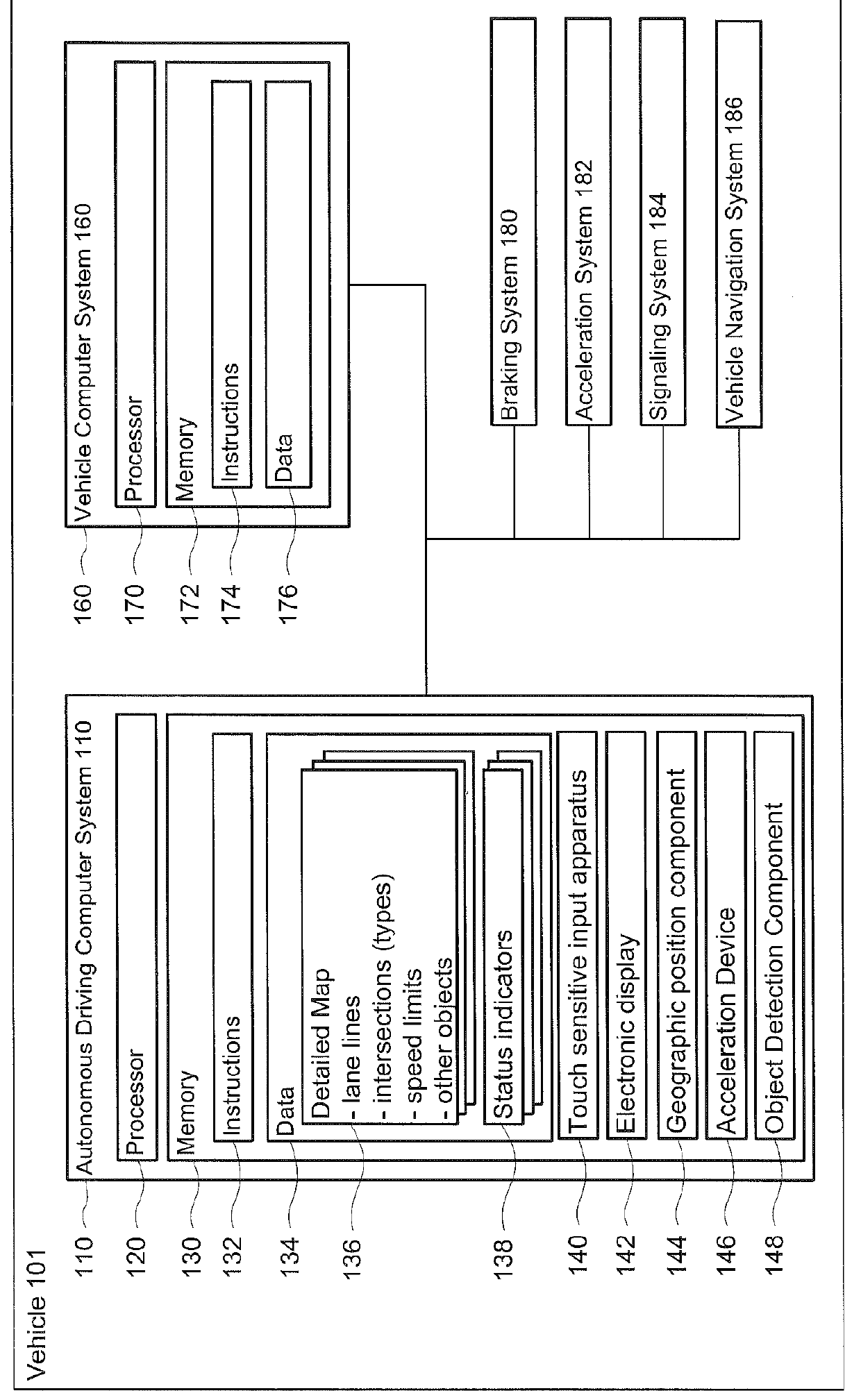
User interface for displaying internal state of autonomous driving system
ActiveUS8260482B1Control process safetyDigital data processing detailsNavigation instrumentsSteering wheelEmbedded system
A passenger in an automated vehicle may relinquish control of the vehicle to a control computer when the control computer has determined that it may maneuver the vehicle safely to a destination. The passenger may relinquish or regain control of the vehicle by applying different degrees of pressure, for example, on a steering wheel of the vehicle. The control computer may convey status information to a passenger in a variety of ways including by illuminating elements of the vehicle. The color and location of the illumination may indicate the status of the control computer, for example, whether the control computer has been armed, is ready to take control of the vehicle, or is currently controlling the vehicle.
Owner:WAYMO LLC
User interface apparatus using hand gesture recognition and method thereof
ActiveUS20060136846A1Control safely and comfortablyControl process safetyInput/output for user-computer interactionCharacter and pattern recognitionImage identificationUser interface
Provided is a user interface apparatus that can control a telematics terminal safely and comfortably while driving, by recognizing a hand gesture image received through a camera in the telematics terminal as a corresponding control signal, and a method thereof. The interface apparatus using a hand gesture recognition, includes: an input receiving block for receiving a command registration request signal and a command selection signal; a hand gesture recognizing block for storing the hand gesture image in connection with a specific command, and transforming the hand gesture image into the corresponding command by recognizing the hand gesture image from the image obtained in the image obtaining block; and a command performing block for performing an operation corresponding to a command transformed in the hand gesture recognizing block.
Owner:INTELLECTUAL DISCOVERY CO LTD
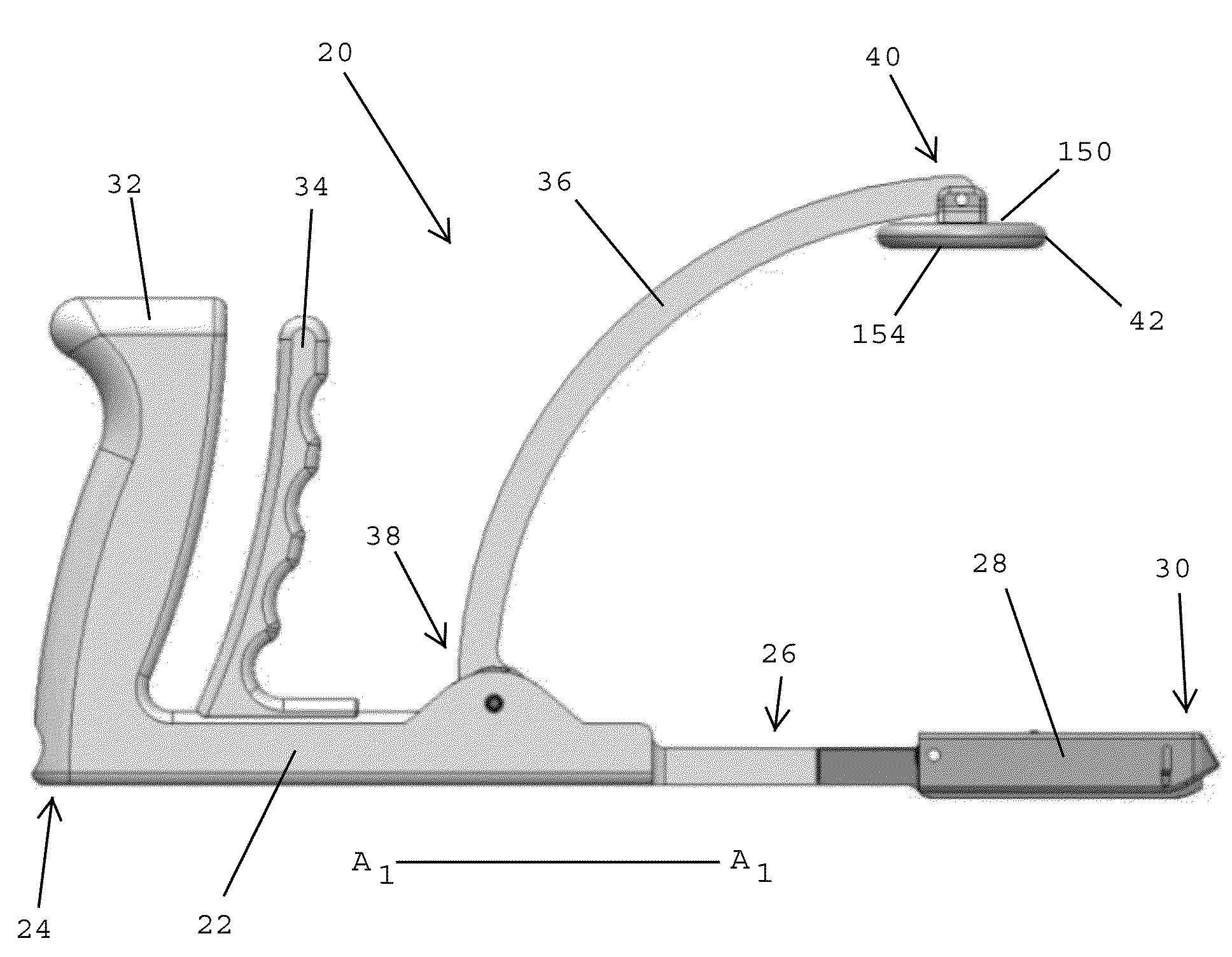
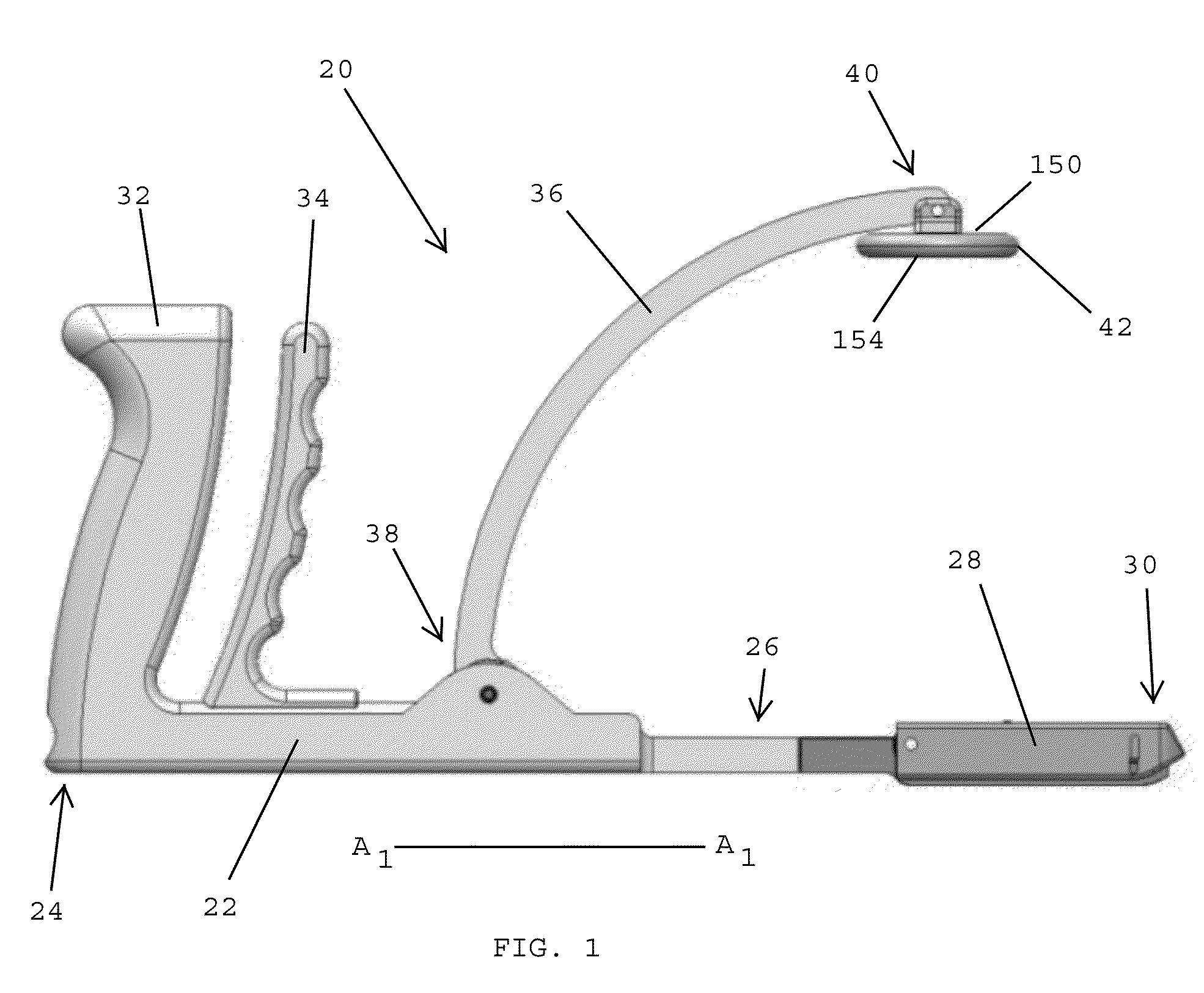
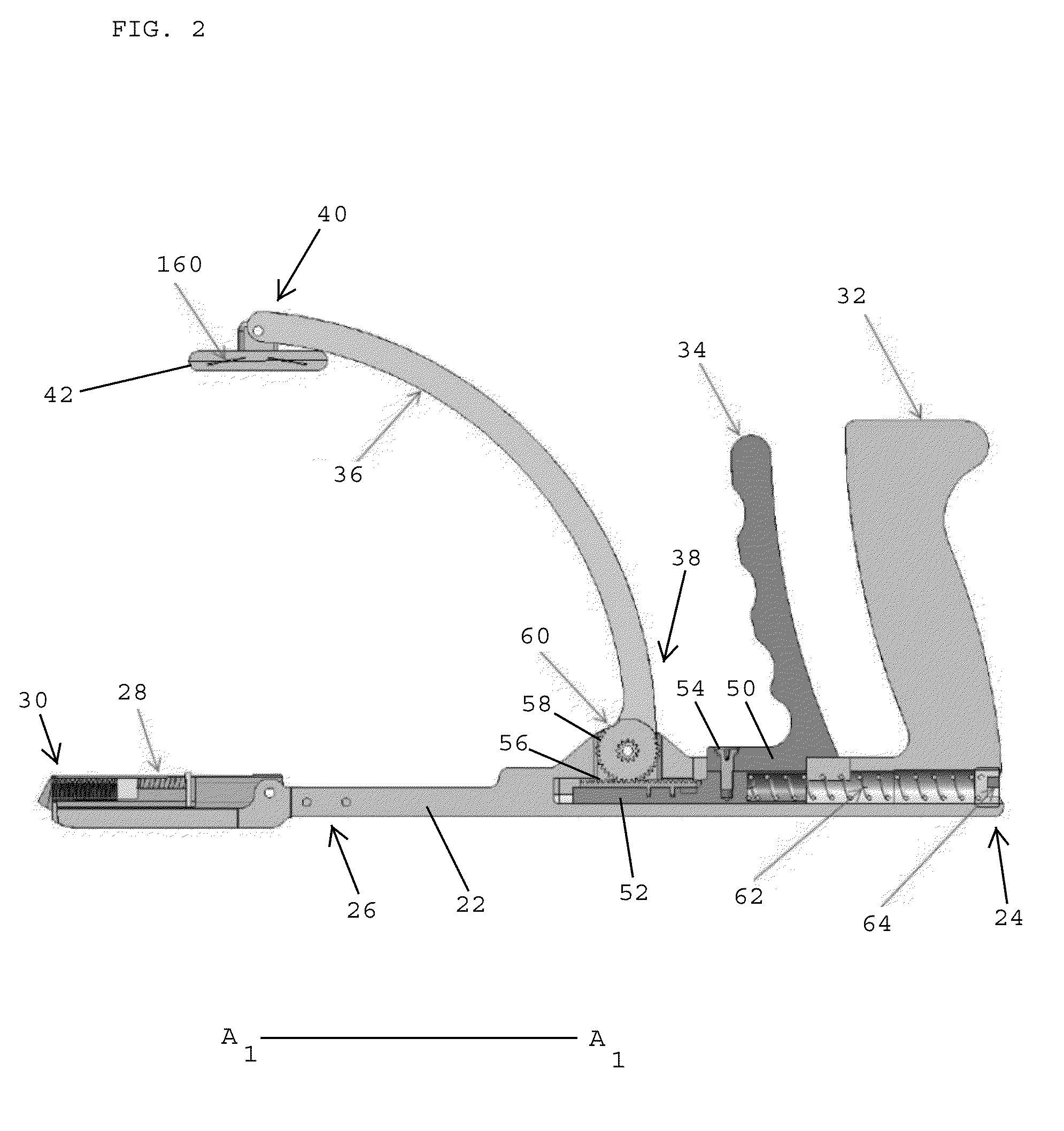
Clamping devices for dispensing surgical fasteners into soft media
ActiveUS9119617B2Preventing further travelUndue stressDiagnosticsStaplesActuatorBiomedical engineering
A clamping device for dispensing surgical fasteners includes a lower arm having a proximal end, a distal end, and a longitudinal axis extending between the proximal and distal ends, and an upper arm pivotally connected with the lower arm. An actuator is coupled with the upper and lower arms for moving the distal ends of the arms toward one another for closing the clamping device. A surgical fastener dispenser is secured to the distal end of the lower arm. The dispenser includes a cartridge body having a top surface with a surgical fastener dispenser opening. A pad is pivotally connected to the distal end of the upper arm. When the clamping device is closed, a bottom surface of the pad applies a clamping force upon the top surface of the cartridge body for dispensing one of the surgical fasteners at an angle that is perpendicular to the longitudinal axis.
Owner:ETHICON INC
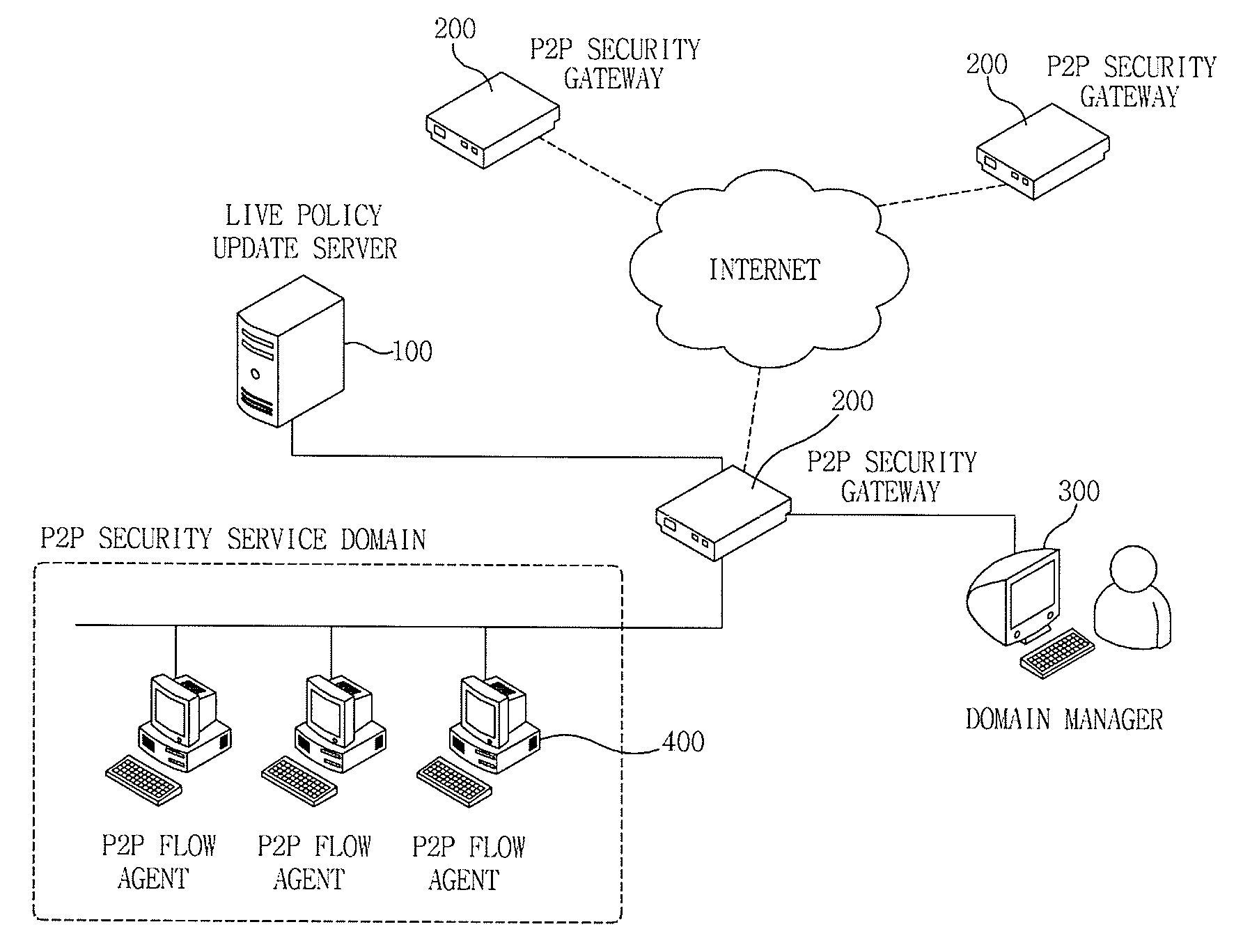
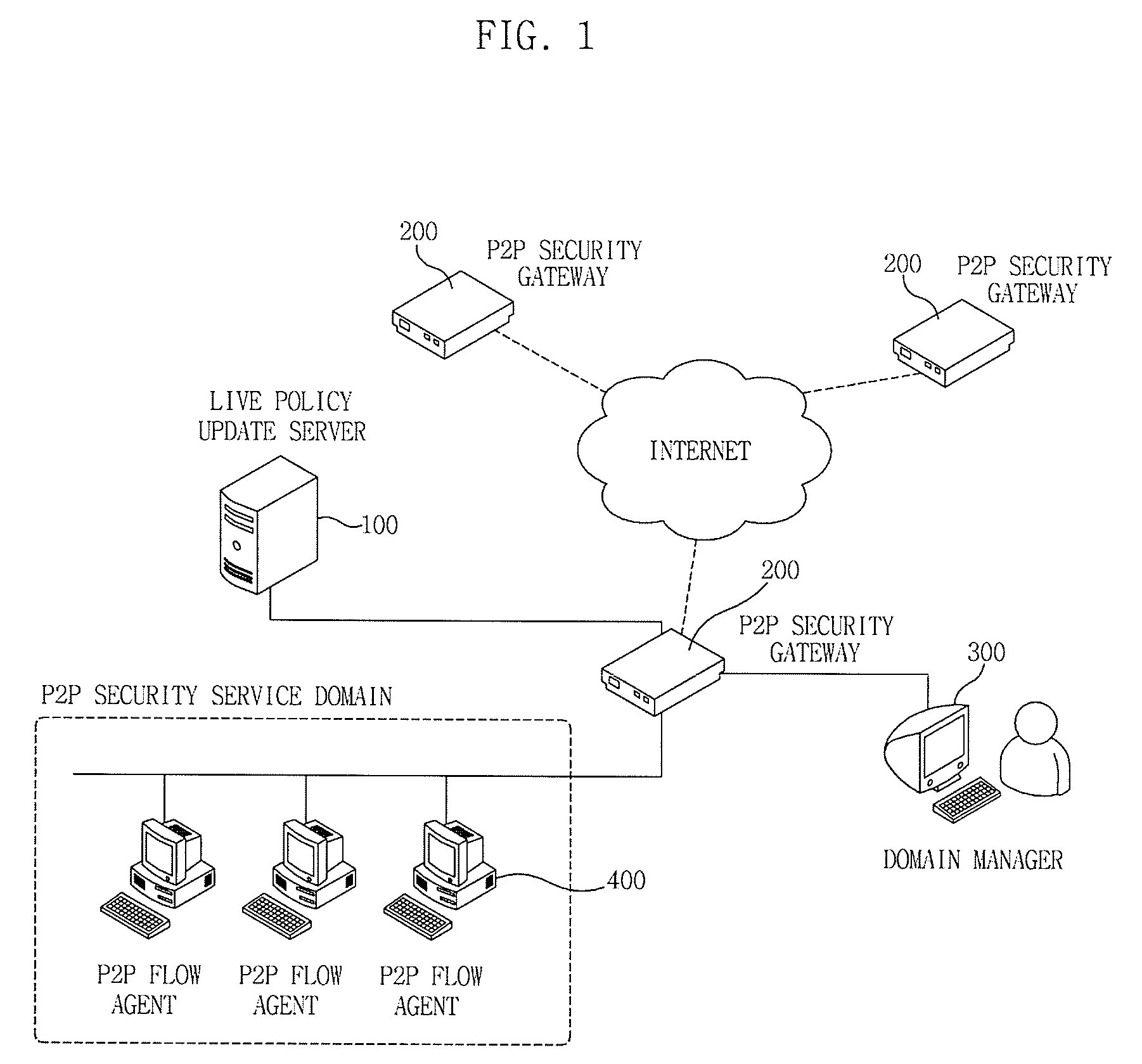
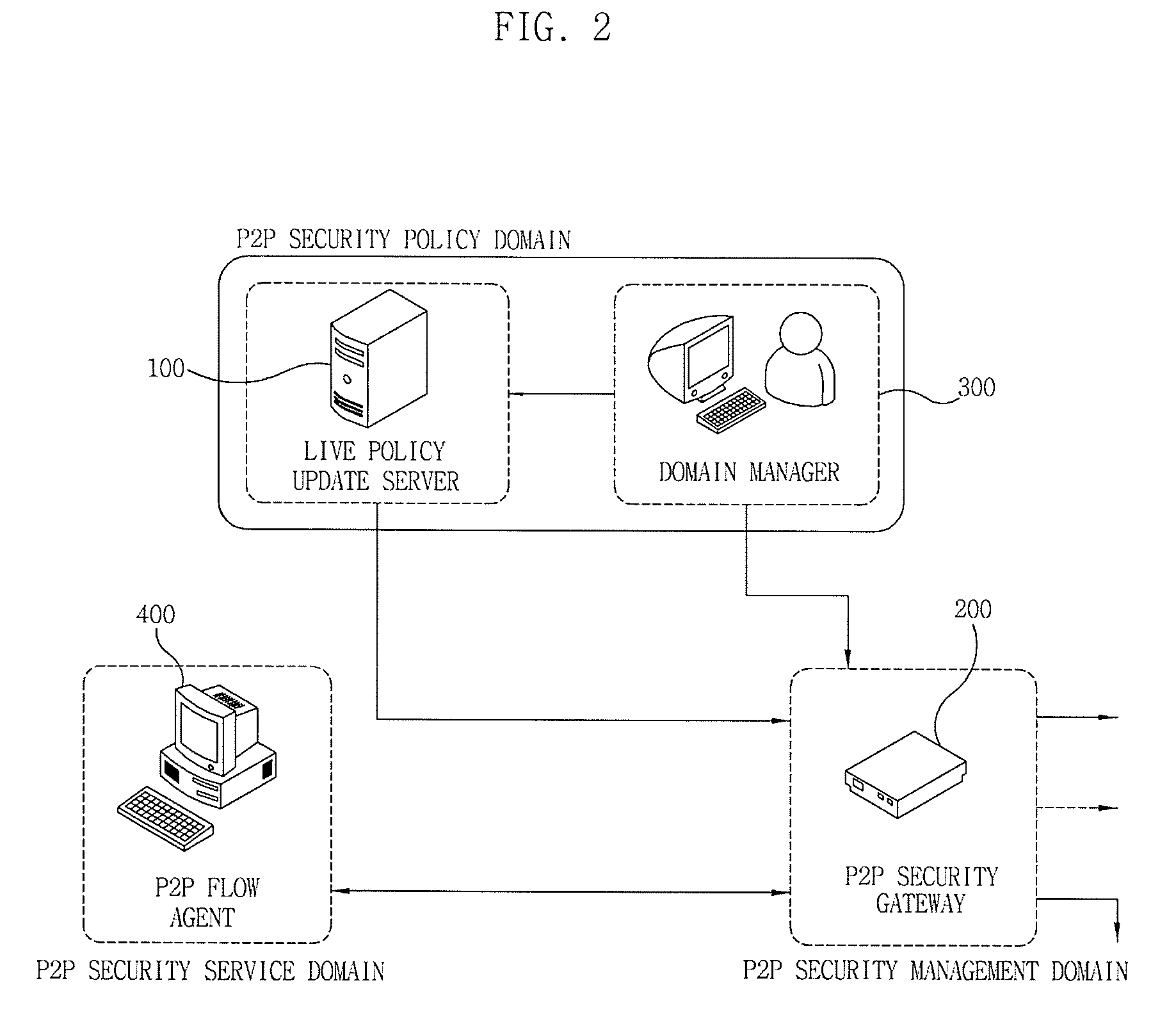
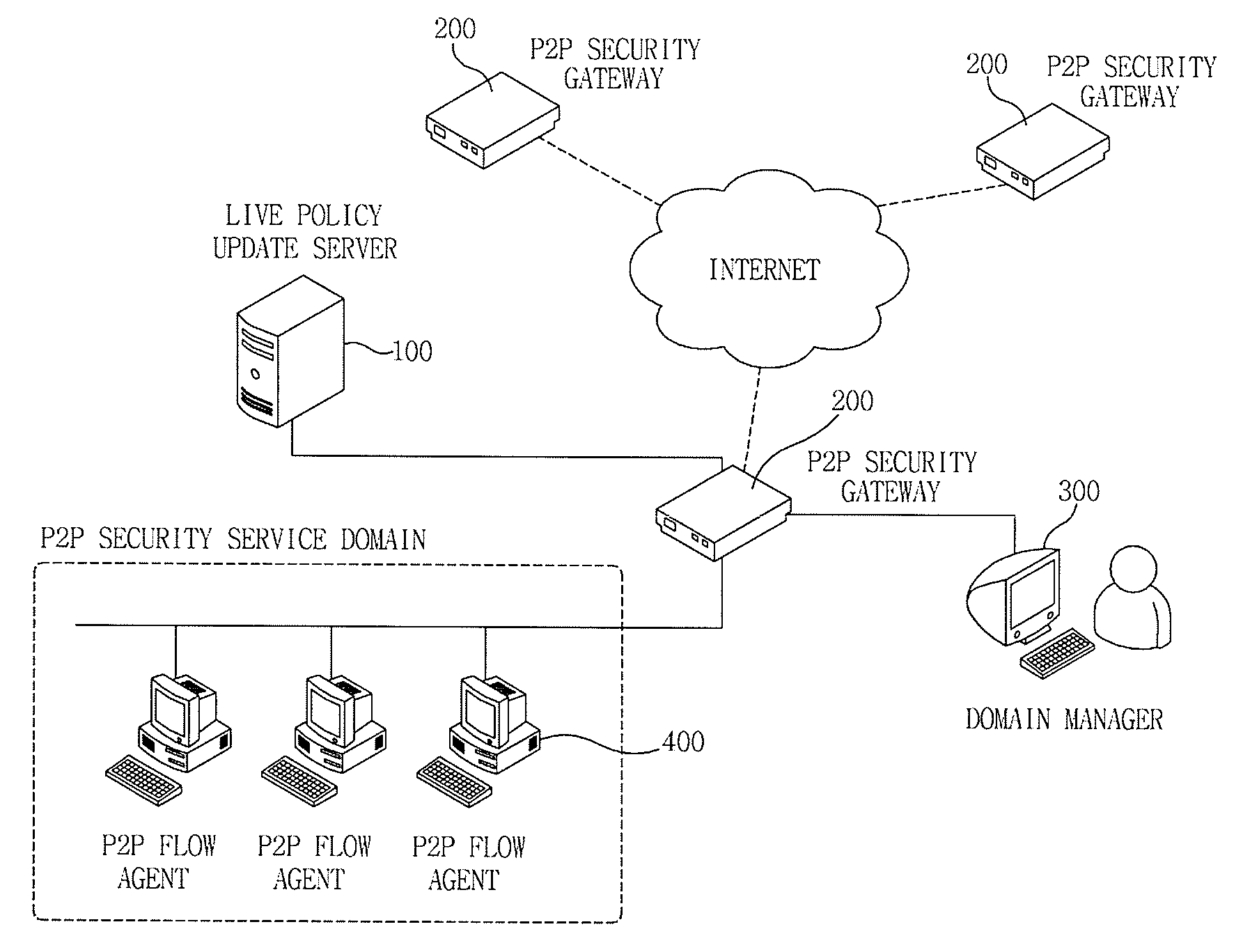
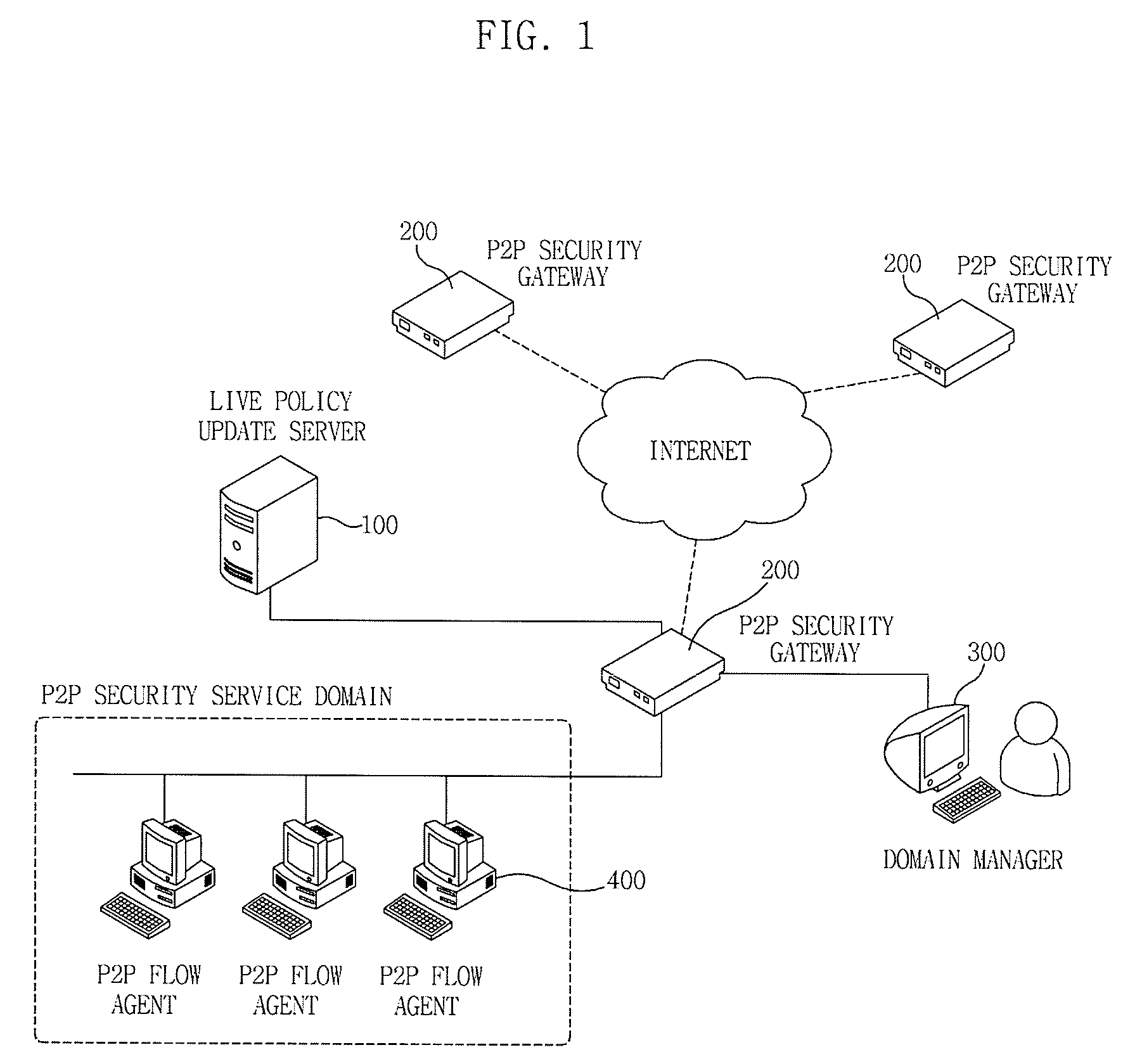
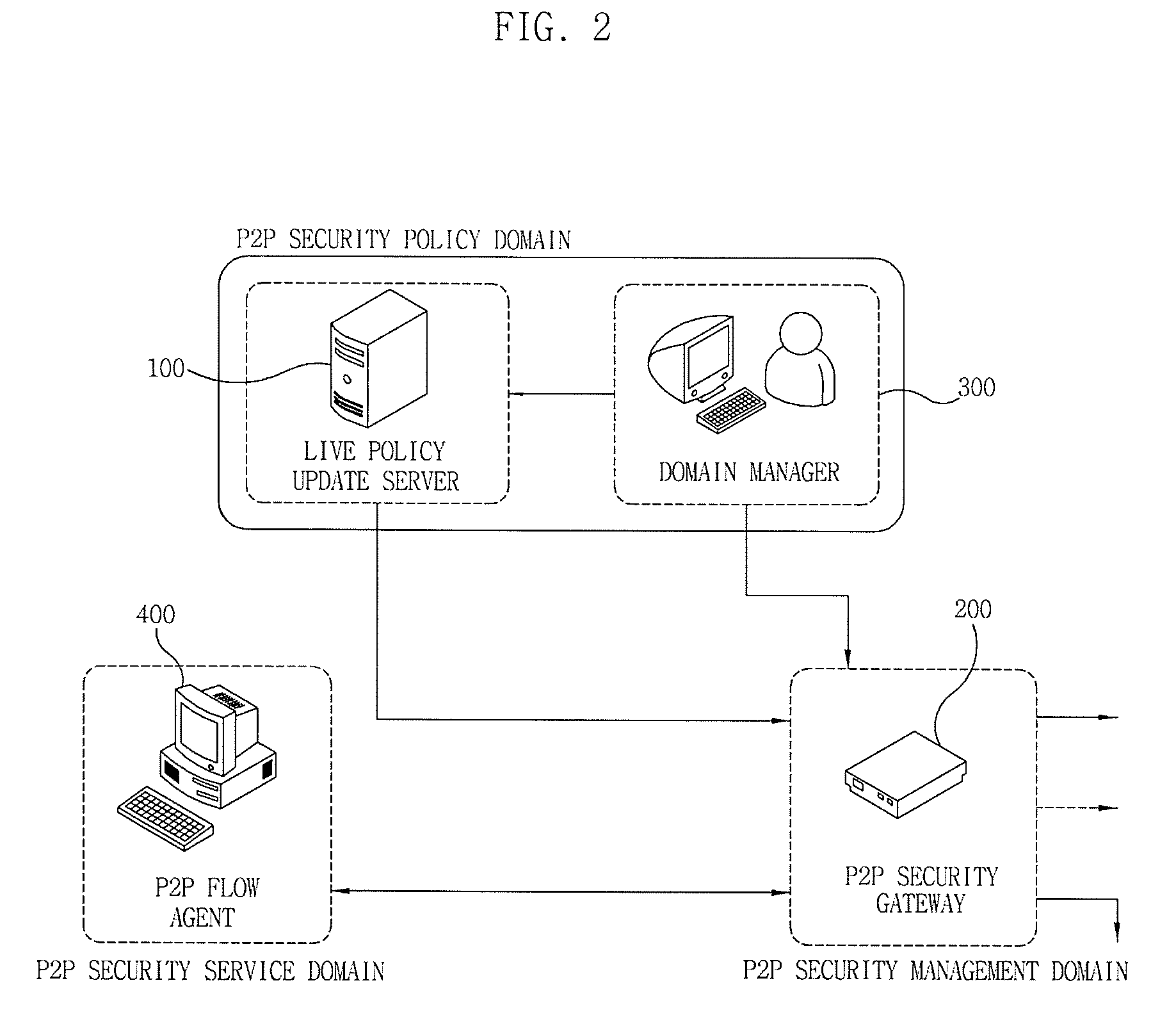
Apparatus and method for managing p2p traffic
ActiveUS20090150972A1Reduce overheadReduce time and costDigital data processing detailsUnauthorized memory use protectionTraffic volumeTraffic capacity
The invention relates to a P2P traffic management apparatus and method. A P2P flow agent monitors an executed application program to extract a P2P application program, adds application identifiers to packets generated by the application program according to a set policy, and transmits the packets. In this case, a P2P security gateway monitors the inflowing packets from the P2P flow agent to extract packets having the application identifiers, uses the extracted application identifiers to inquire and acquire a related policy, and controls the packets according to the acquired policy.
Owner:ELECTRONICS & TELECOMM RES INST
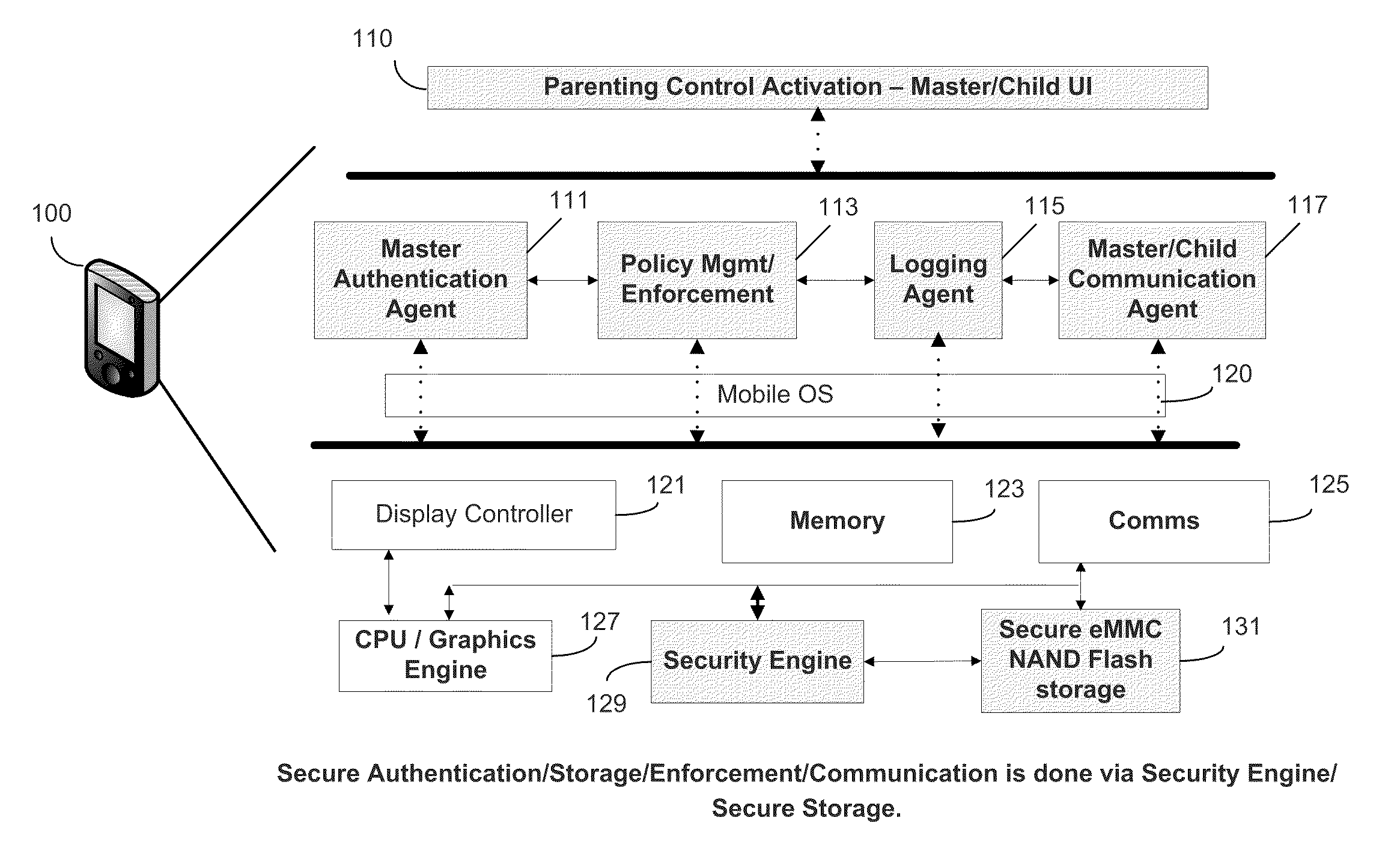
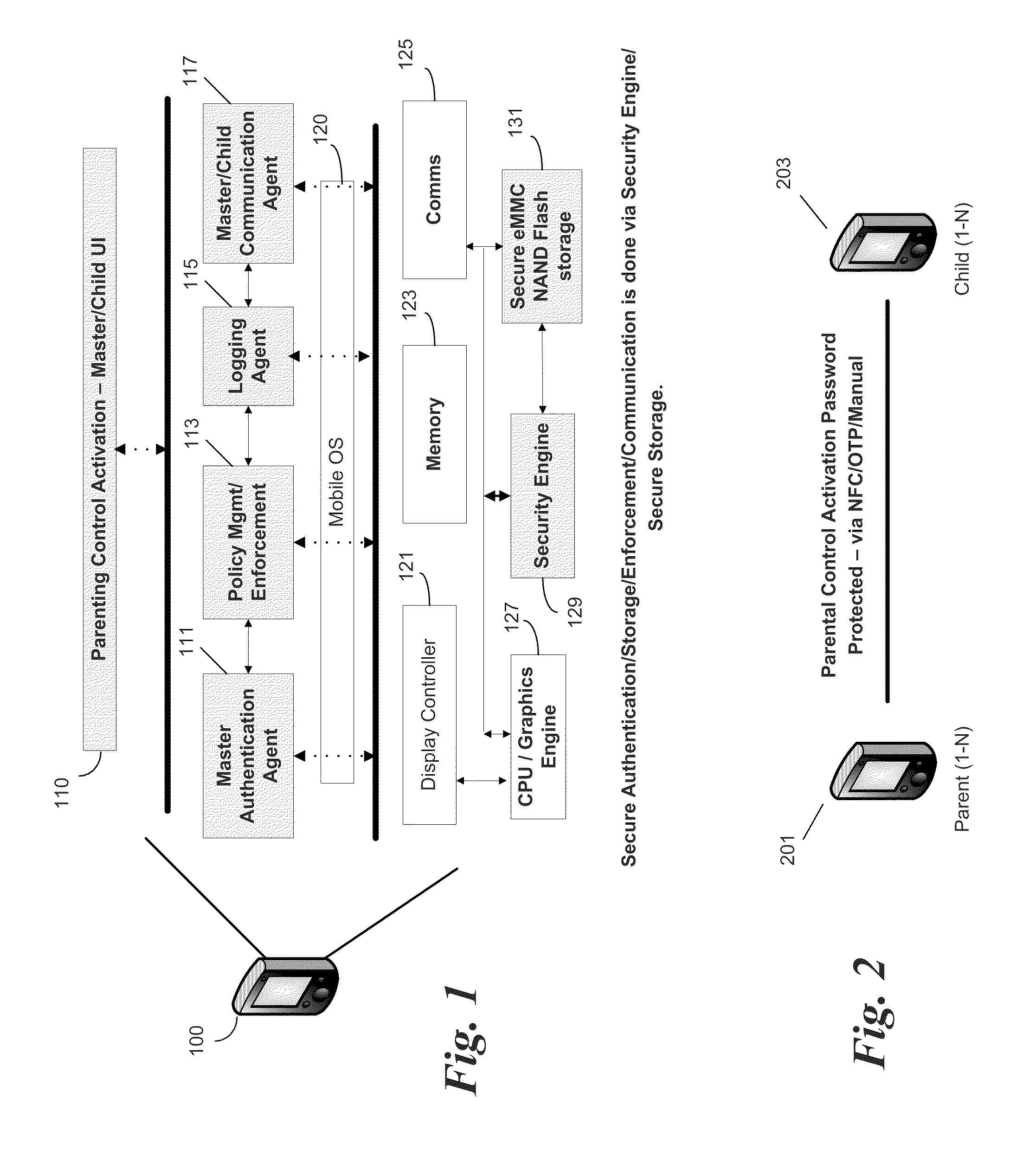
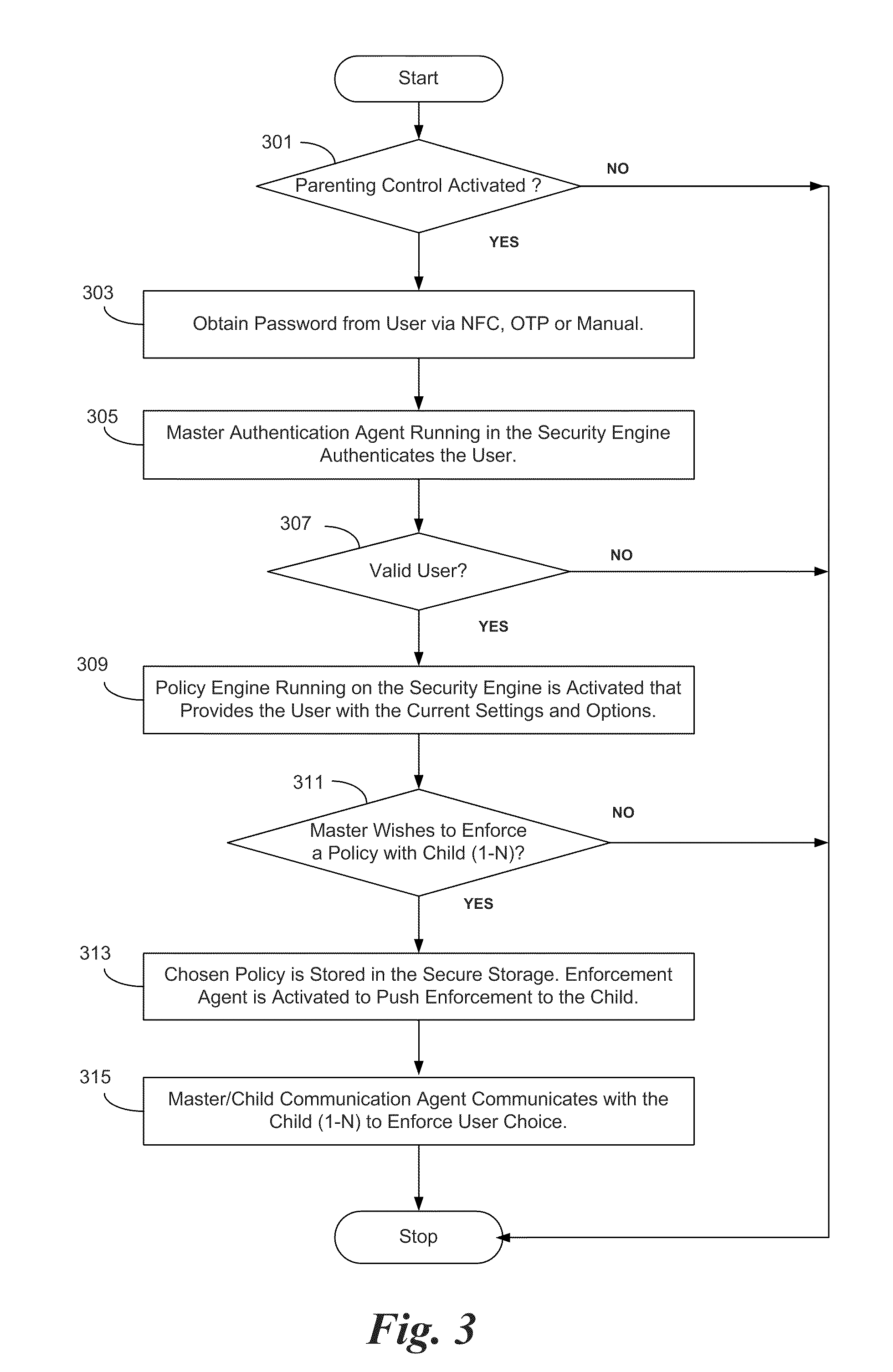
Method and apparatus for bearer and server independent parental control on smartphone, managed by the smartphone
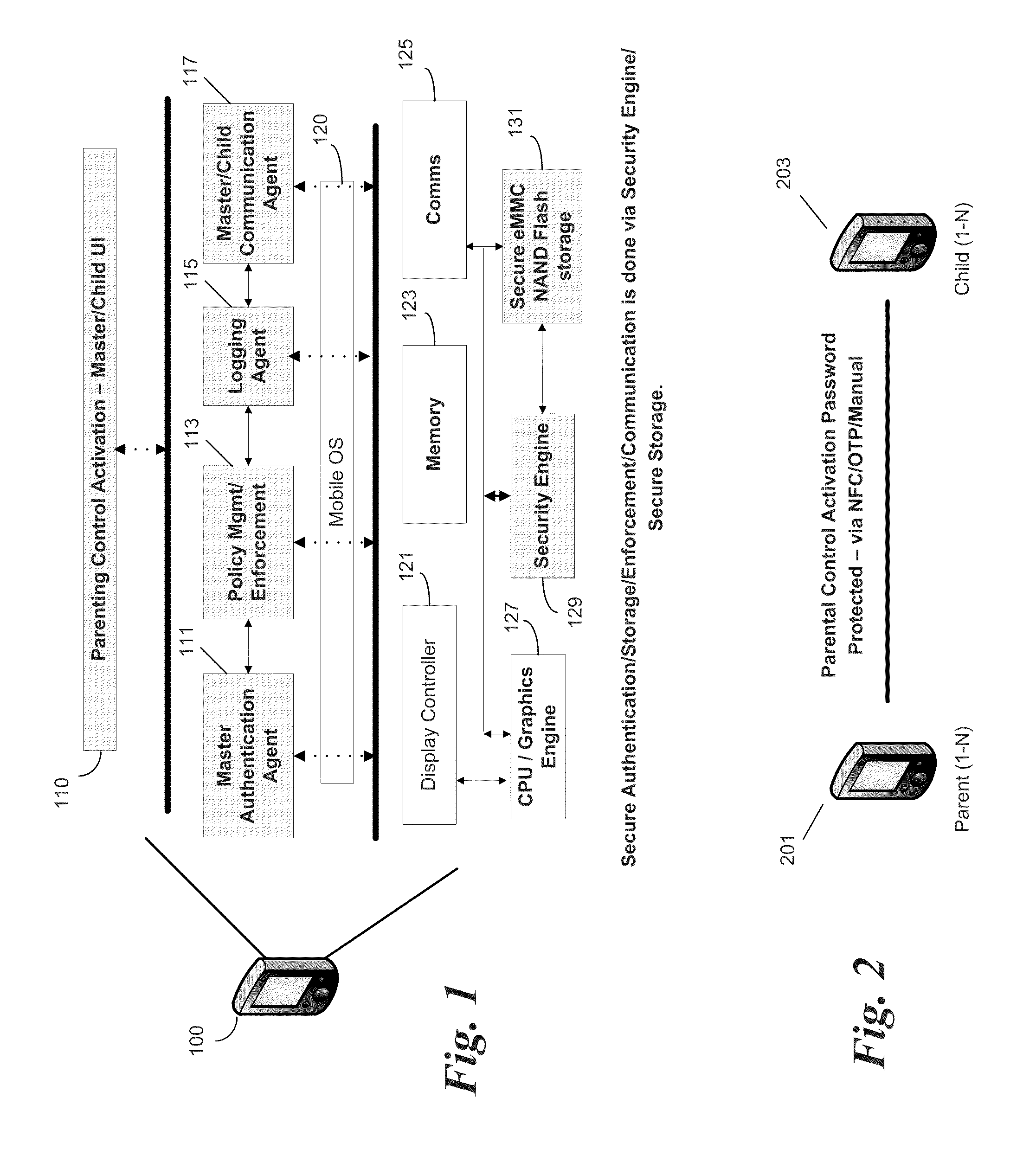
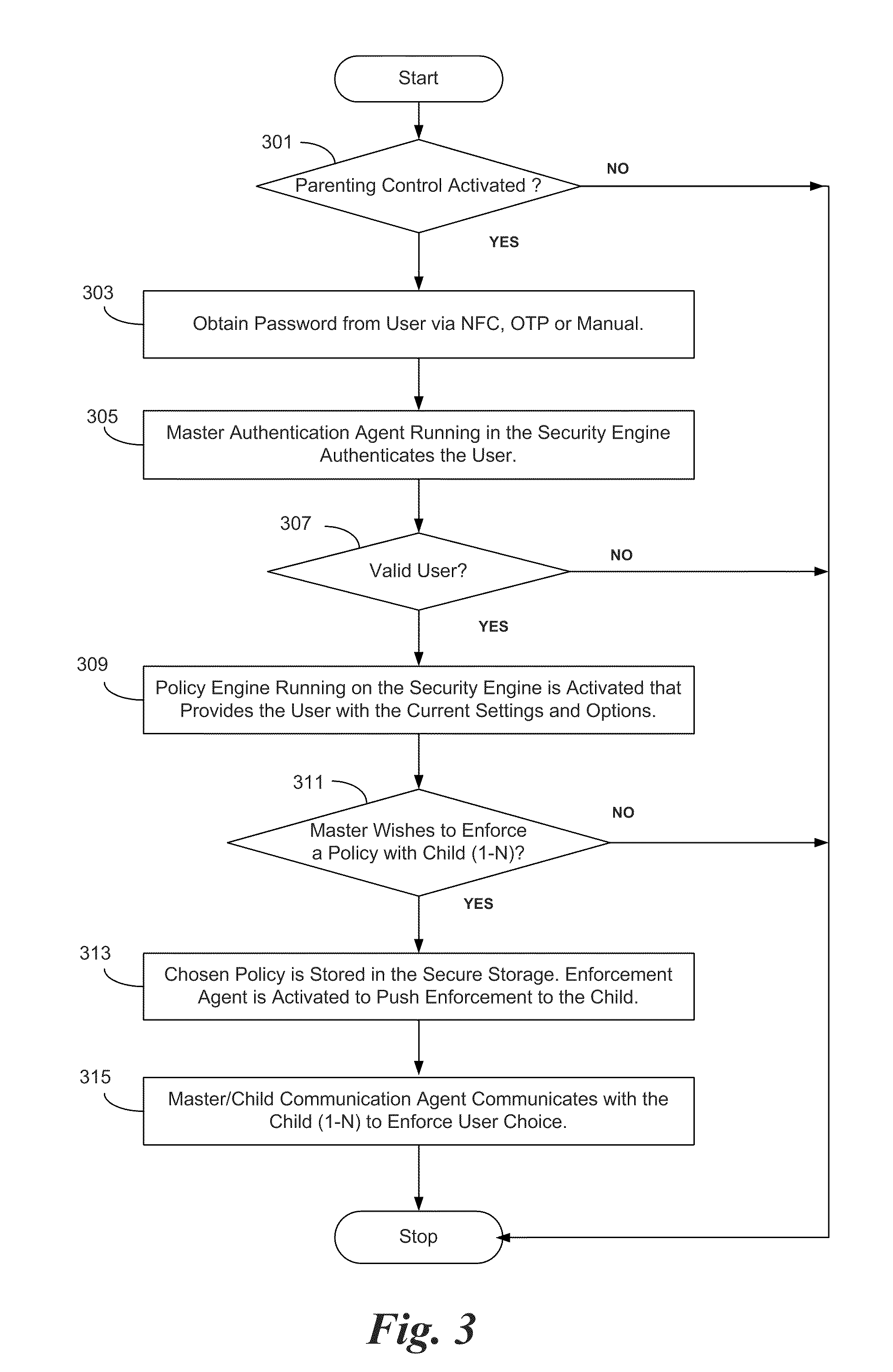
InactiveUS20110237221A1Control process safetyThorough understandingUnauthorised/fraudulent call preventionEavesdropping prevention circuitsCrypto phoneComputer hardware
In some embodiments, the invention involves parental or master control of a child or subordinate mobile phone without service provider intervention. An embodiment of the invention is a system and method relating to master control of the subordinate smart phone using features on the smart phones, and independent of features provided by the phone service providers. Communication between the master and subordinate phones may be initiated using SMS messaging, near field communication, Bluetooth, direct connect to a PC, or by other secure wireless or wired connections. Once initiated, desired communication events are captured by the parental control application to effect control policies on the subordinate phone. Communication between the phones may be encrypted to prevent malicious intervention of message traffic Other embodiments are described and claimed.
Owner:INTEL CORP
System and method for secure access
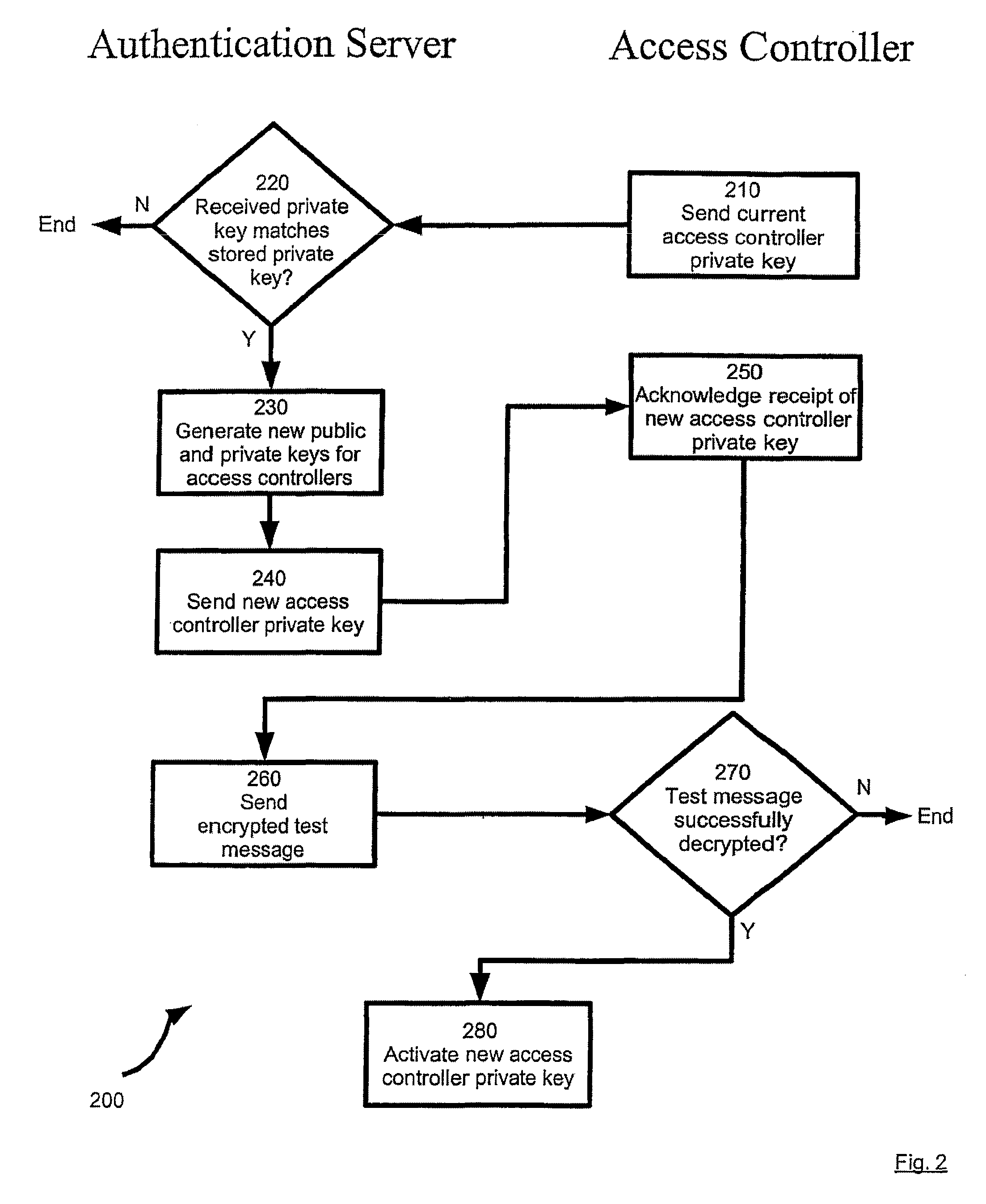
ActiveUS7930412B2Control process safetyReduce riskMultiple keys/algorithms usageError detection/correctionTelecommunications linkTransceiver
The present invention provides a method and system for secure access to computer equipment. An embodiment includes a secure access controller connected to a link between a transceiver (such as a modem) and the computer equipment. Public and private keys are used by the secure access controller and a remote user. The keys are provided to the secure access controller by an authentication server. Once the transceiver establishes a communication link with the user, the access controller uses these keys to authenticate packets issued by the user to the computer equipment. If the packet is authenticated, the access controller passes the packet to the computer equipment. Otherwise, the packet is discarded.
Owner:BCE
Airbag apparatus
InactiveUS20070145729A1Simple structureControl process safetyPedestrian/occupant safety arrangementEngineeringAirbag
The airbag apparatus includes an airbag having an exhaust hole for discharging part of inflation gas, an open / close controller for controlling opening and closing operations of the exhaust hole, and a flap element releasably joined to the open / close controller and being joined to a periphery of the exhaust hole in an outer side of the airbag which periphery is in a side facing away from the open / close controller, for opening and closing the exhaust hole. The apparatus further includes an open / close means arranged in the periphery of the exhaust hole. Upon airbag inflation, if the flap element is retained by the open / close controller, the open / close means is held down at its outer side by the flap element and keeps the exhaust hole closed. If the flap element is released from the open / close controller, the open / close means opens by the pressure of inflation gas to expand an opening area of the exhaust hole.
Owner:TOYODA GOSEI CO LTD
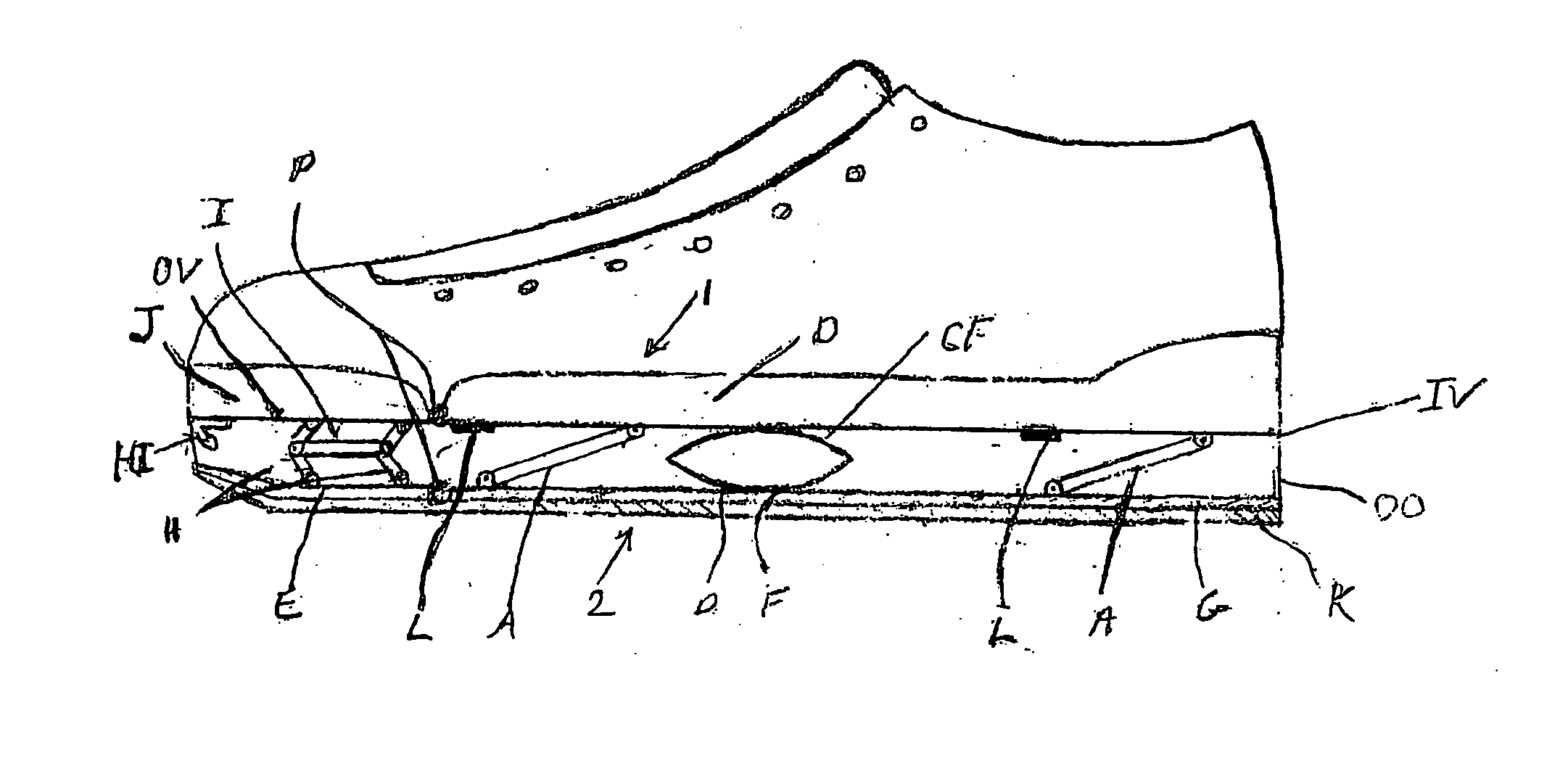
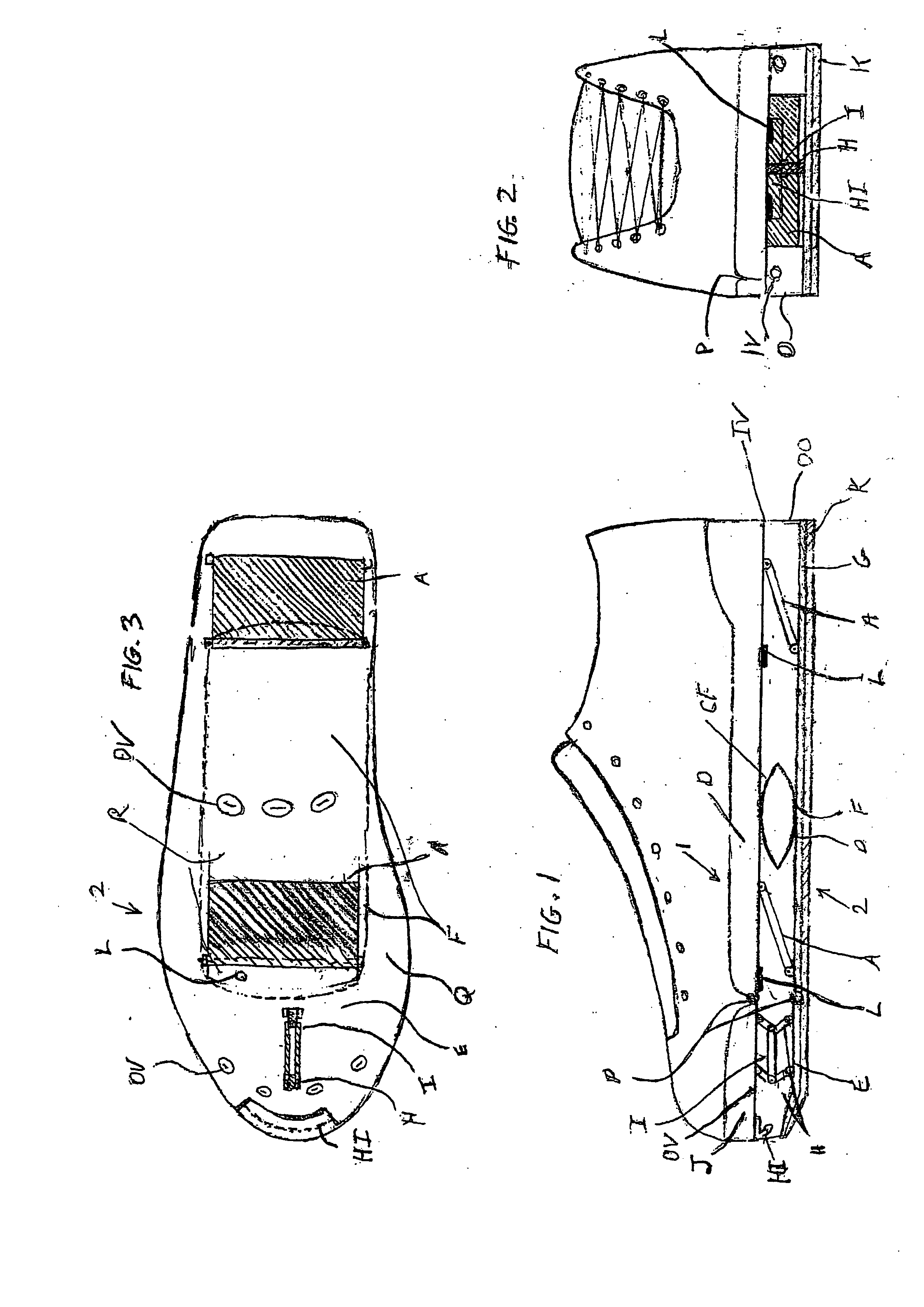
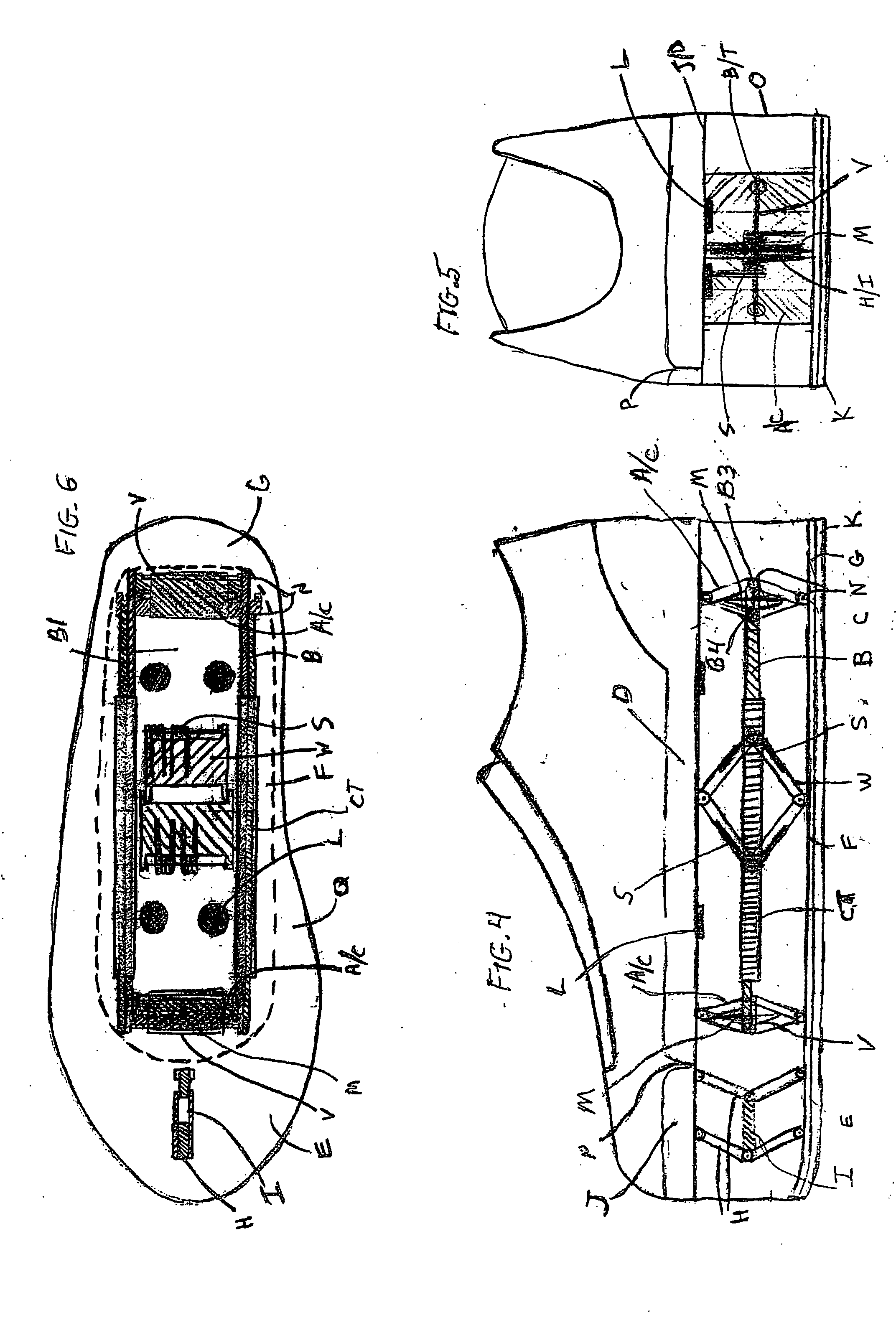
Shoe suspension system
A shoe suspension system for use with a shoe or boot having an upper and lower sole. The system includes a first tandem hinge pivotally engaged between the upper toe sole and the lower toe sole which opens and closes parallel to the longitudinal axis of the shoe a plurality of tandem hinges pivotally engaged between the upper mid heel sole and the lower sole which also open and close parallel to the longitudinal axis of the shoe and return springs engaged between the upper mid heel sole and the lower sole.
Owner:PERENICH STEPHEN
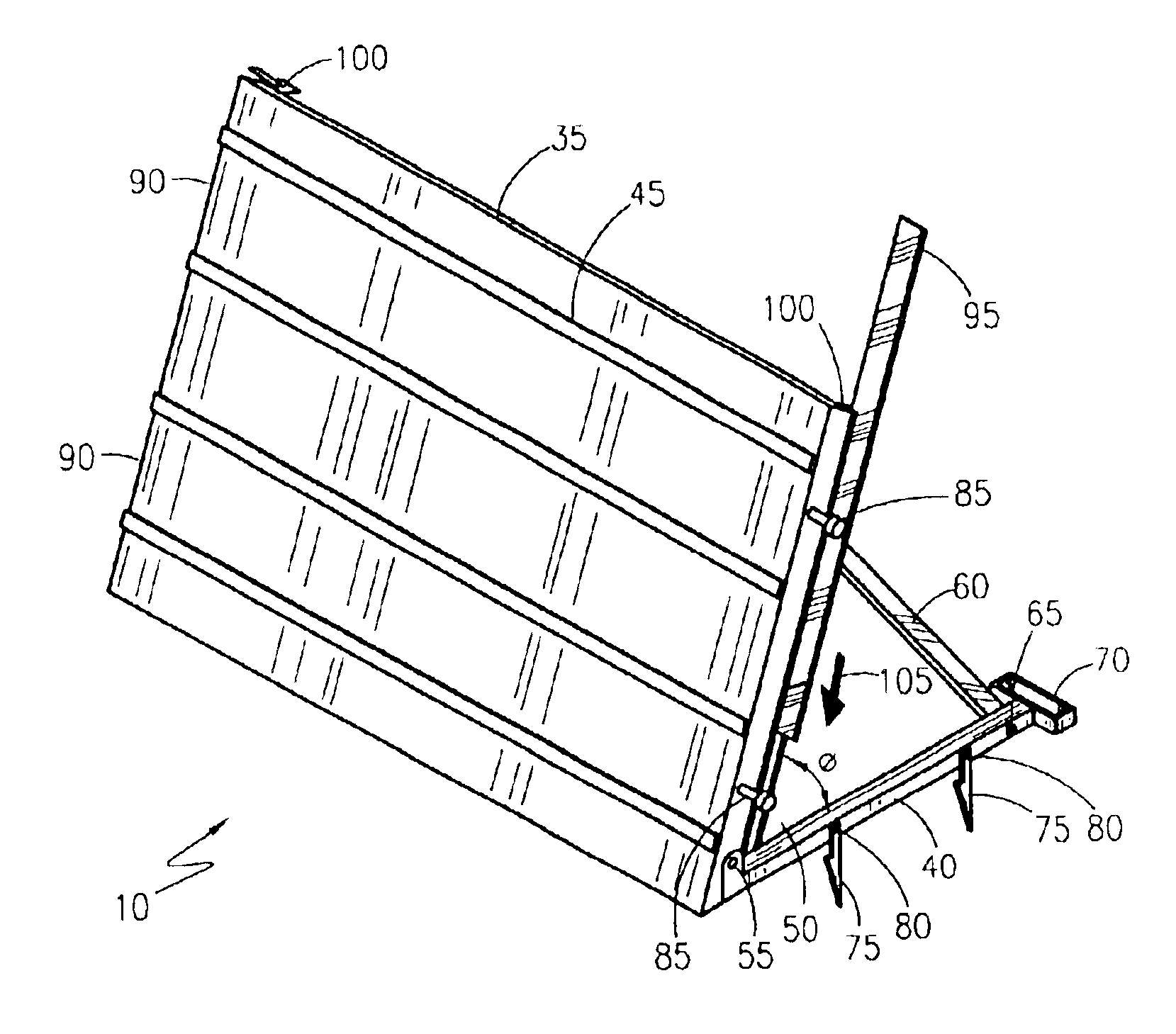
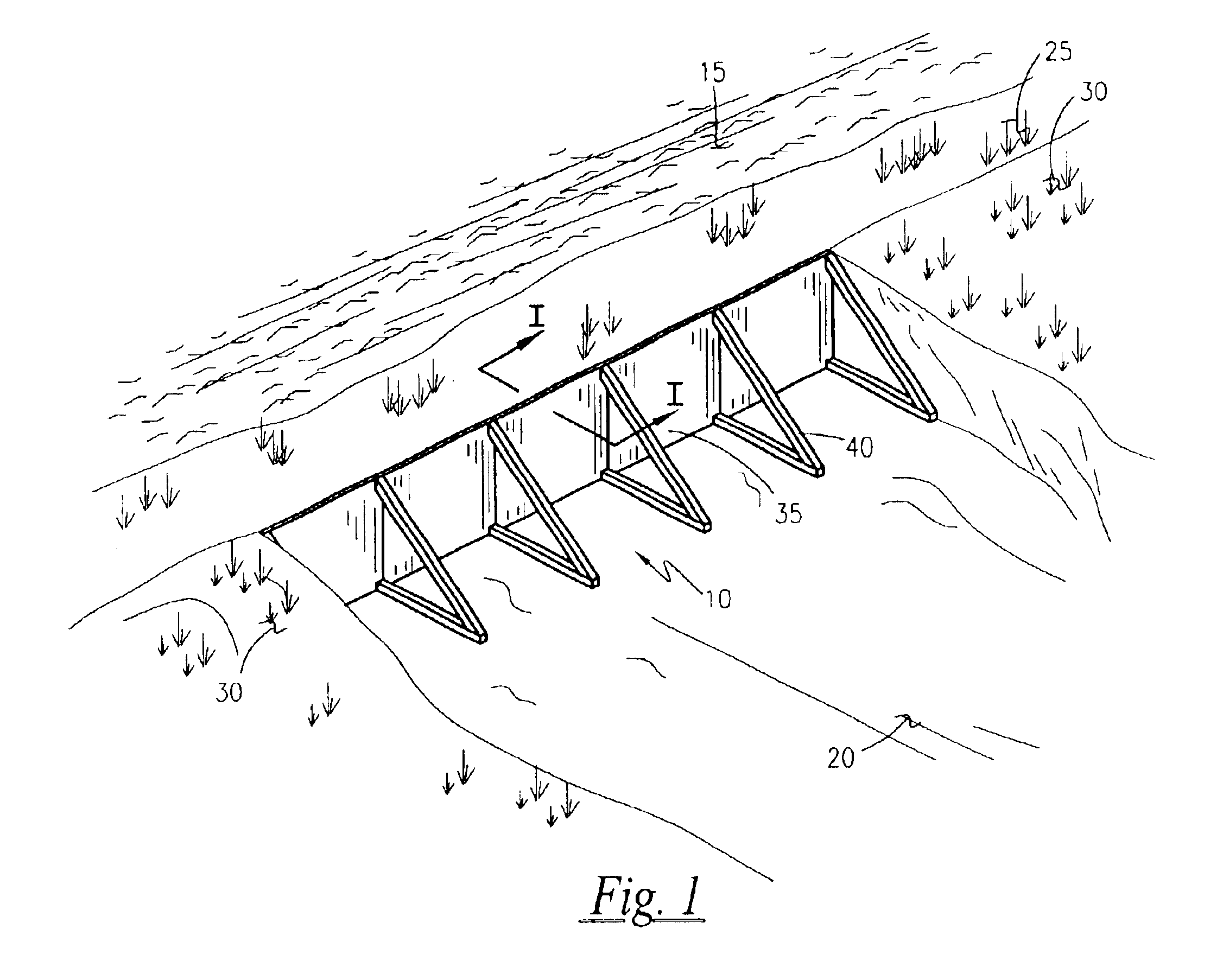
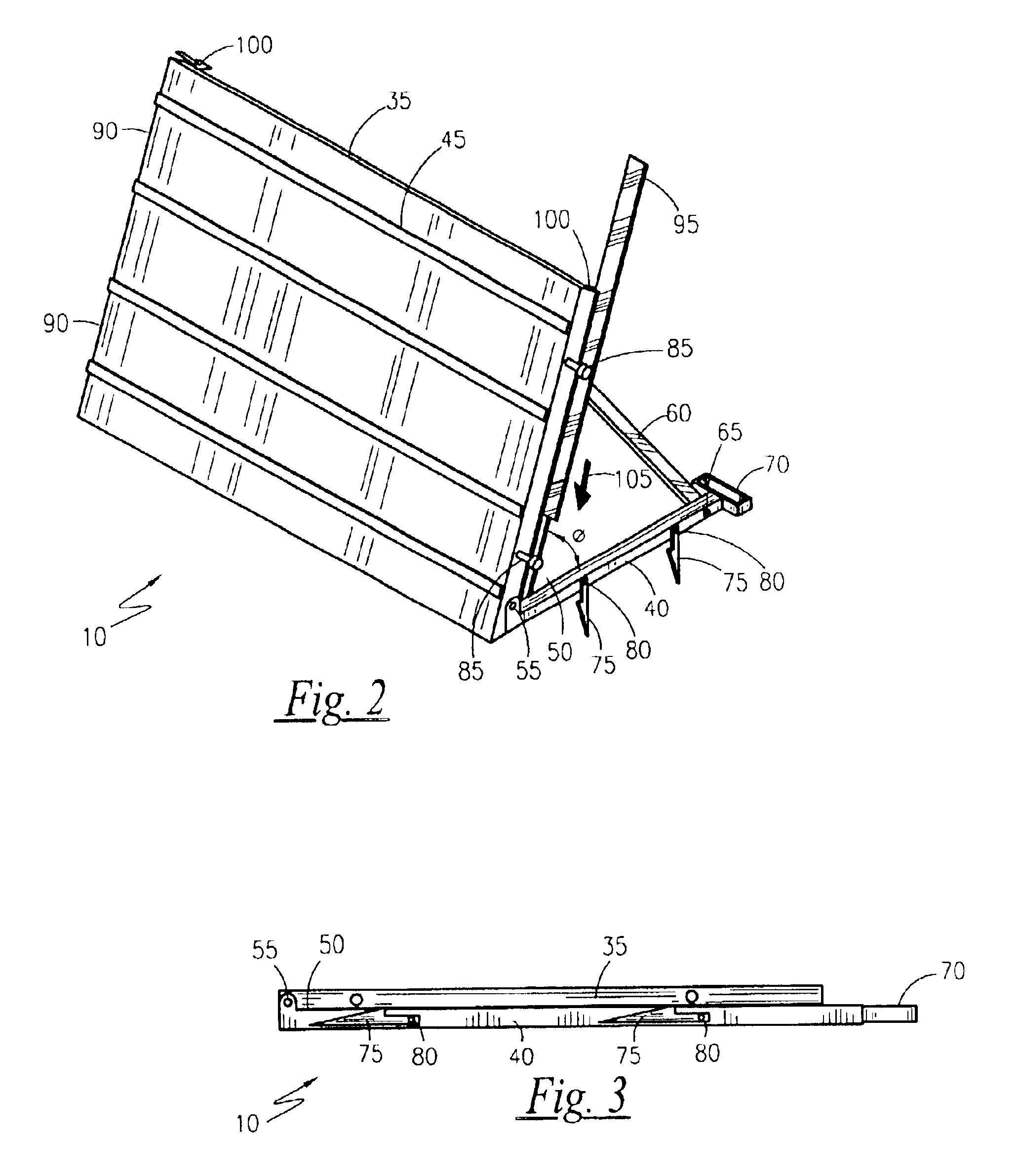
Flood control panel system
InactiveUS6840711B1Control process safetyQuick and easy and effectiveBarrages/weirsClimate change adaptationTruckFlood control
A modular flood control panel is provided having a base and supporting “A”-frame structure. The base locks into the ground, or supporting wall of sandbags, with a series of four adjustable angle stakes per each panel. The invention folds flat when not in use, for storage and for transportation on a truck to flood water areas. The panels are joined together with the use of a five inch wide joining slat that slides down into a channel on each side of each panel.
Owner:MARTINEZ ROSS R +1
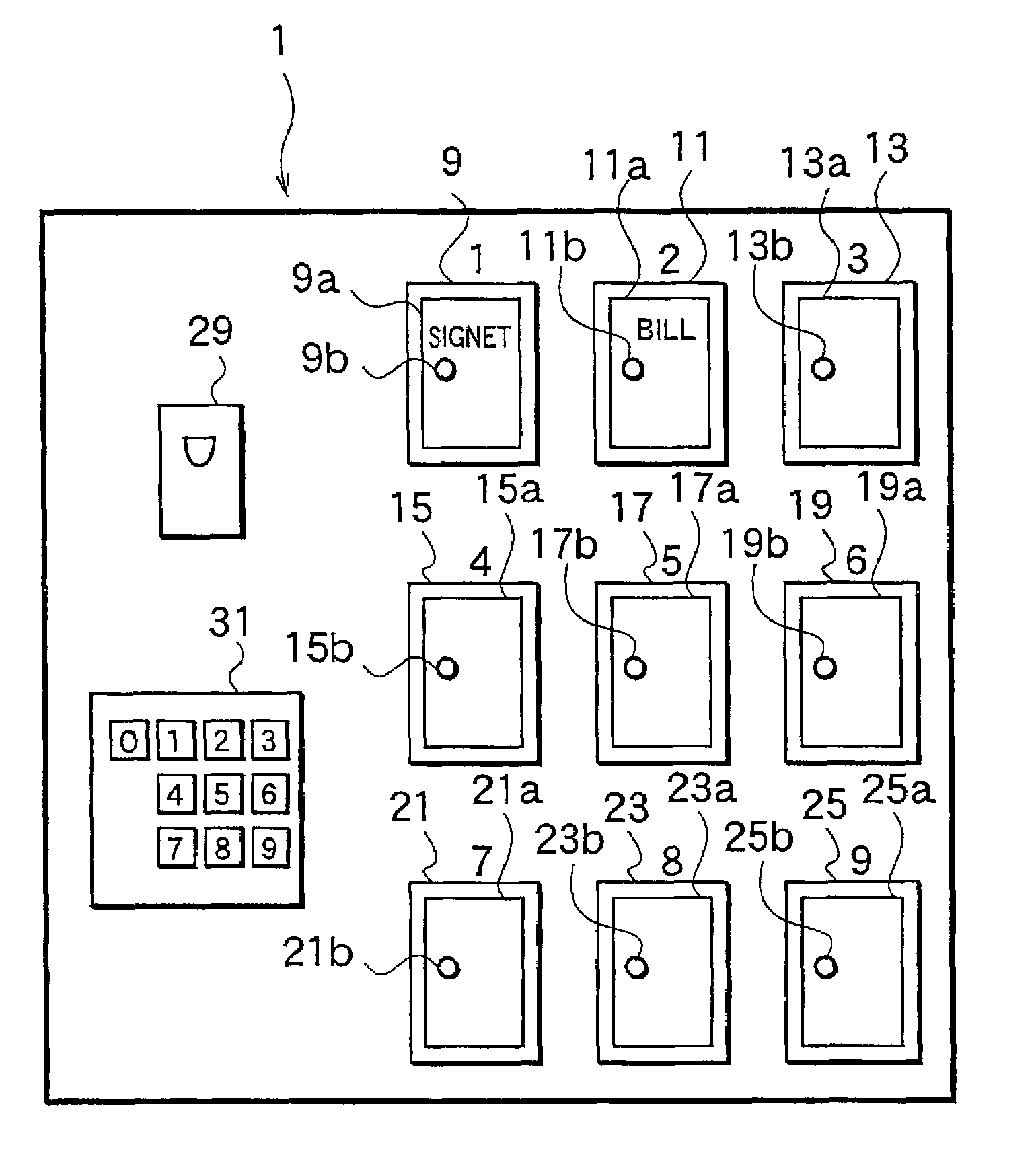
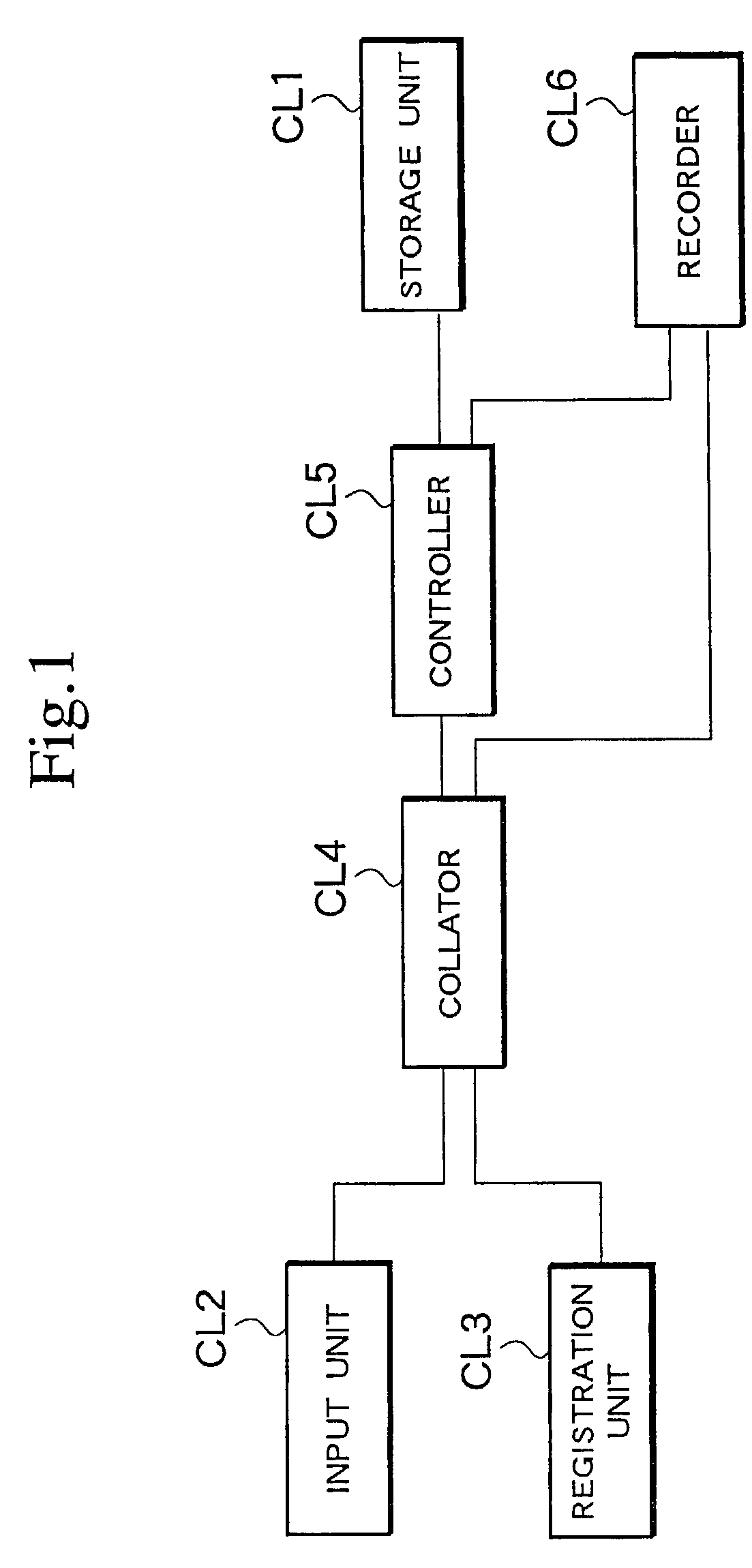
Apparatus for controlling articles in custody
InactiveUS7129817B2Control process safetyStrengthen security managementElectric signal transmission systemsImage analysisCollationComputer security
An apparatus for reliably and easily controlling articles in custody, for example articles in a safe, has a storage unit lockable to keep the articles therein and unlockable to allow the articles to be taken out therefrom, an input unit to input biometric information for unlocking the storage unit, a registration unit to register biometric information in advance, a collator to collate the input biometric information with the registered biometric information, a controller to unlock the storage unit if the collation by the collator authenticates the input biometric information, and a recorder to record at least a person related to the authenticated biometric information in response to the unlocking of the storage unit.
Owner:UNIREC +1
Robot and method of controlling safety thereof
InactiveUS20100057253A1Minimize damageSecures a user's safetyProgramme-controlled manipulatorSpecial data processing applicationsSafety controlControl theory
Disclosed are a robot, which performs biped walking similar to a human being, and a method of controlling safety of the robot. When the robot falls down, an air bag located in the falling direction is operated and the posture of the robot is changed into an attention posture. When the robot secondarily falls down after the falling of the robot, an air bag located in the secondary falling direction is operated to minimize damage to the elements of the robot due to the secondary falling of the robot.
Owner:SAMSUNG ELECTRONICS CO LTD
Apparatus and method for an electric power supply
ActiveUS20180043789A1Low costReduce spacingCharge equalisation circuitCircuit monitoring/indicationElectrical batteryElectric vehicle
A traction power source for electric vehicles in a single unit. Specifically, traction power source integrates several functions, such as the battery and inverter. In addition, further functionalities that are traditionally in separate units can be integrated into the system and efficiently performed by the same electronics, such as battery management and thermal management.
Owner:DR ING H C F PORSCHE AG
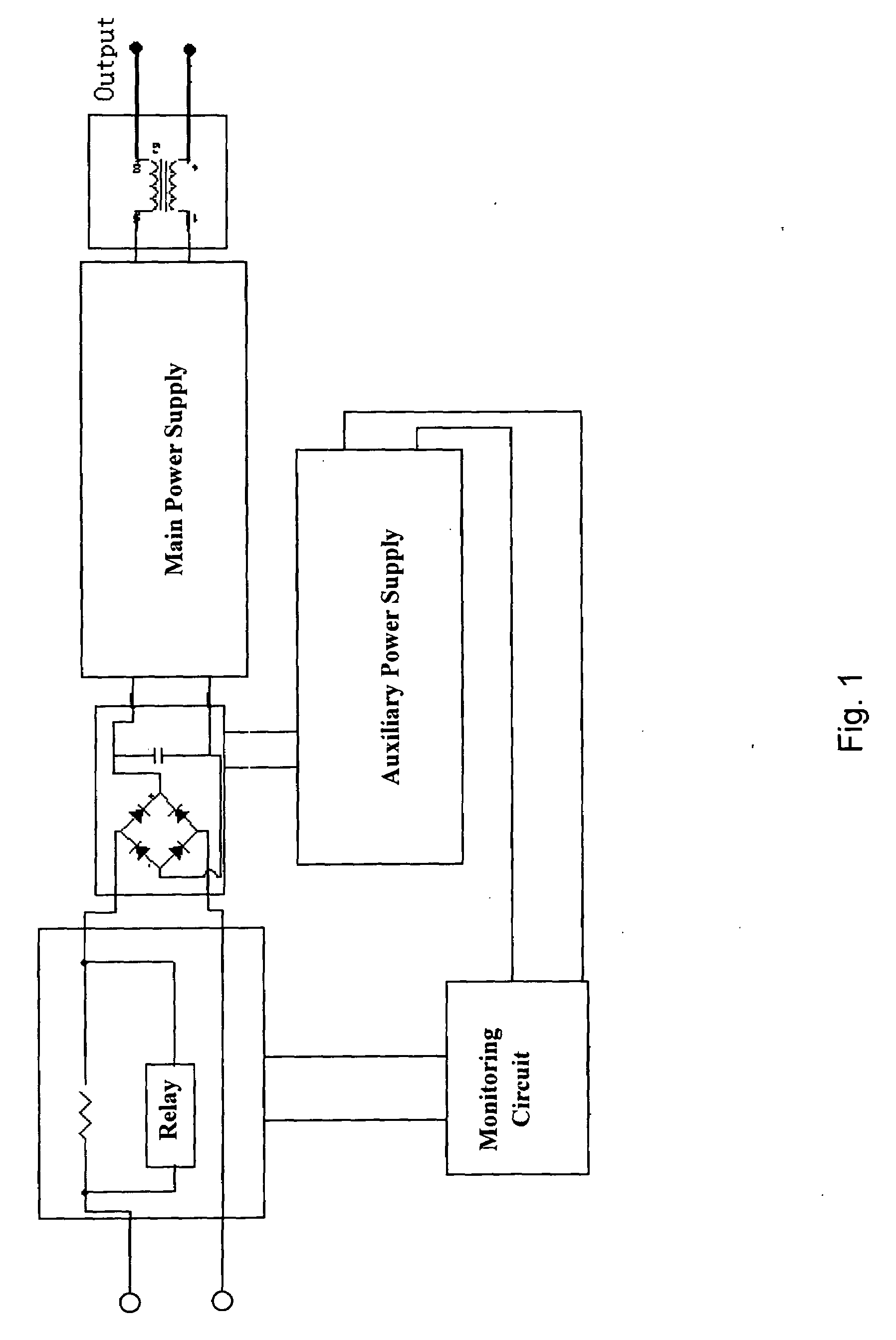
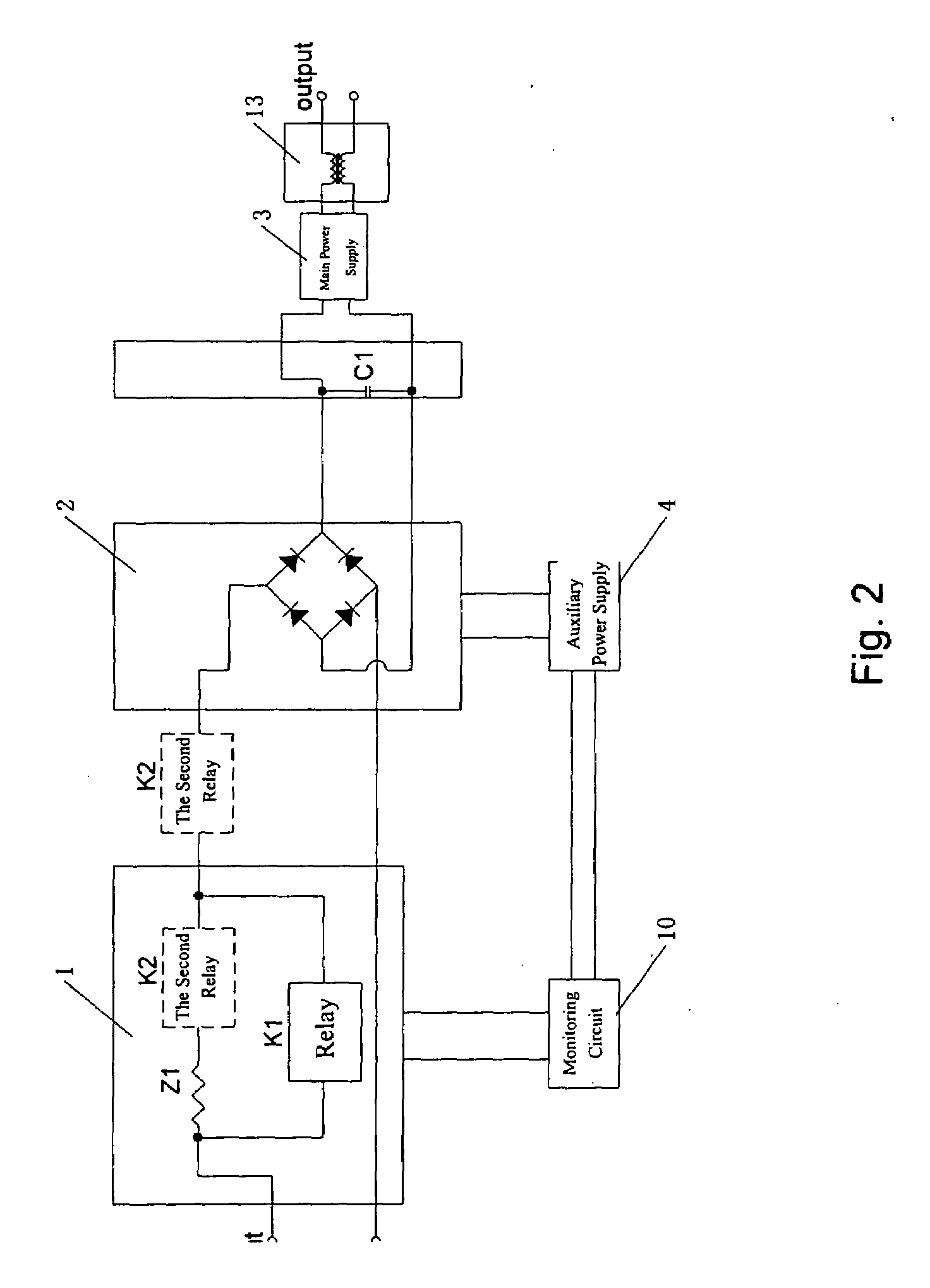
Switching Power Supply With Overvoltage Protection And Overvoltage Protection Method Thereof
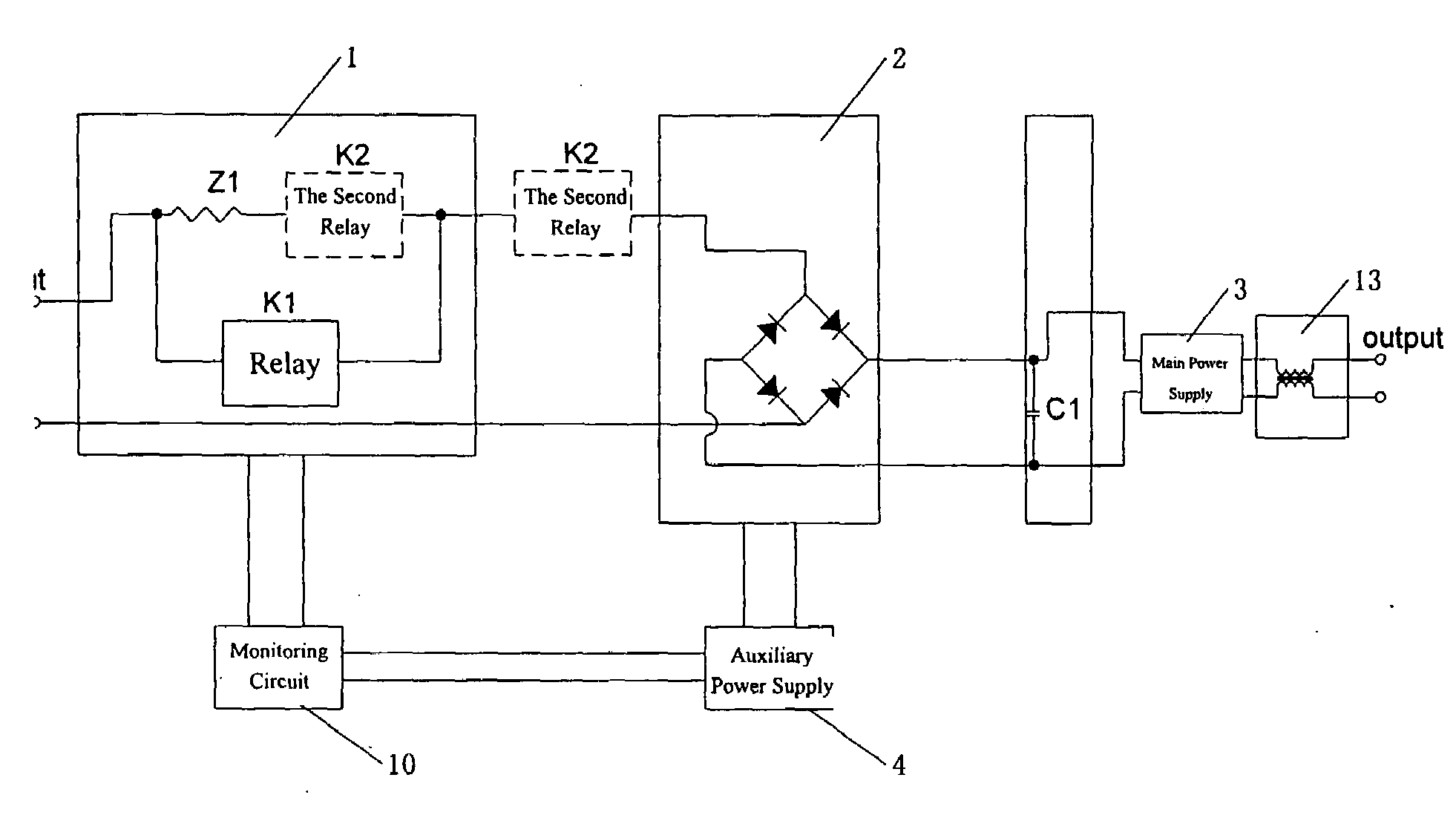
ActiveUS20090152950A1Control process safetyDc source parallel operationEmergency protective arrangements for limiting excess voltage/currentOvervoltageElectricity
A switching power supply with overvoltage protection includes a soft start circuit, a rectifying circuit, a filter capacitor, a main supply, an auxiliary supply and a monitoring circuit. When the input voltage is higher than the predetermined protection voltage, a first electric control switch is turned off, and the main power circuit of the switching power supply is shut off. At the moment, the actuation and release of the second electric control switch is controlled so as to control the input power supply to intermittently charge the power supply module such that the output voltage downstream of the rectifying circuit inside the power supply is controlled in a safe range. For instance, the second electric control is turned on when the output voltage is lower than a certain value, and is turned off when the output voltage is higher than a certain value. Thus, it is ensured that the bus line voltage inside the power supply is controlled within a safe range, to ensure the safety of the devices inside the power supply; and at the same time to ensure the safety of the inner devices of the switching power supply, such that the auxiliary power supply and the control circuit can work normally.
Owner:VERTIV CORP
Method of controlling movement of mobile robot
InactiveUS7818090B2Safe and appropriate accompanying behaviorAvoid collisionComputer controlSimulator controlEngineeringMobile robot
Owner:PANASONIC CORP
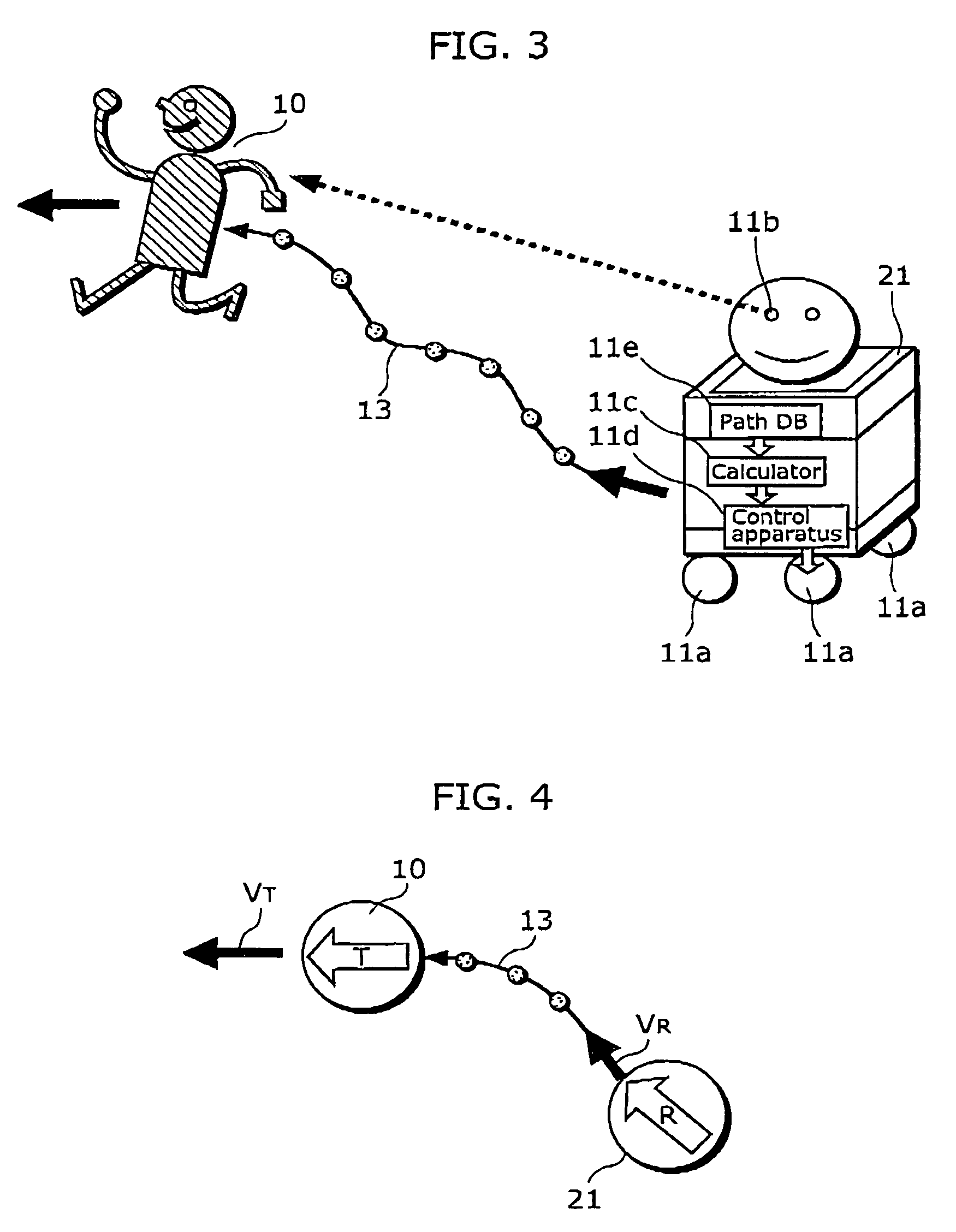
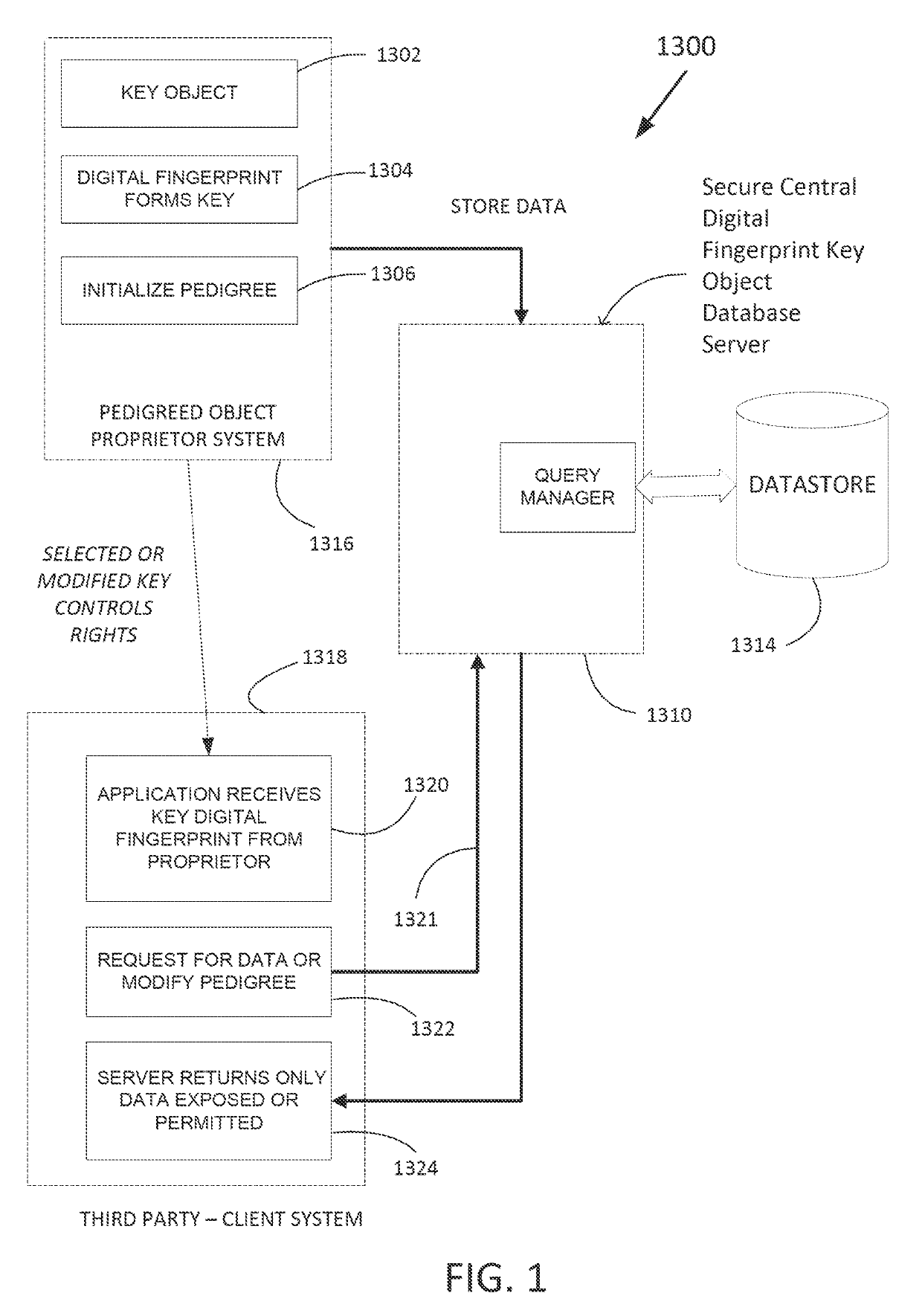
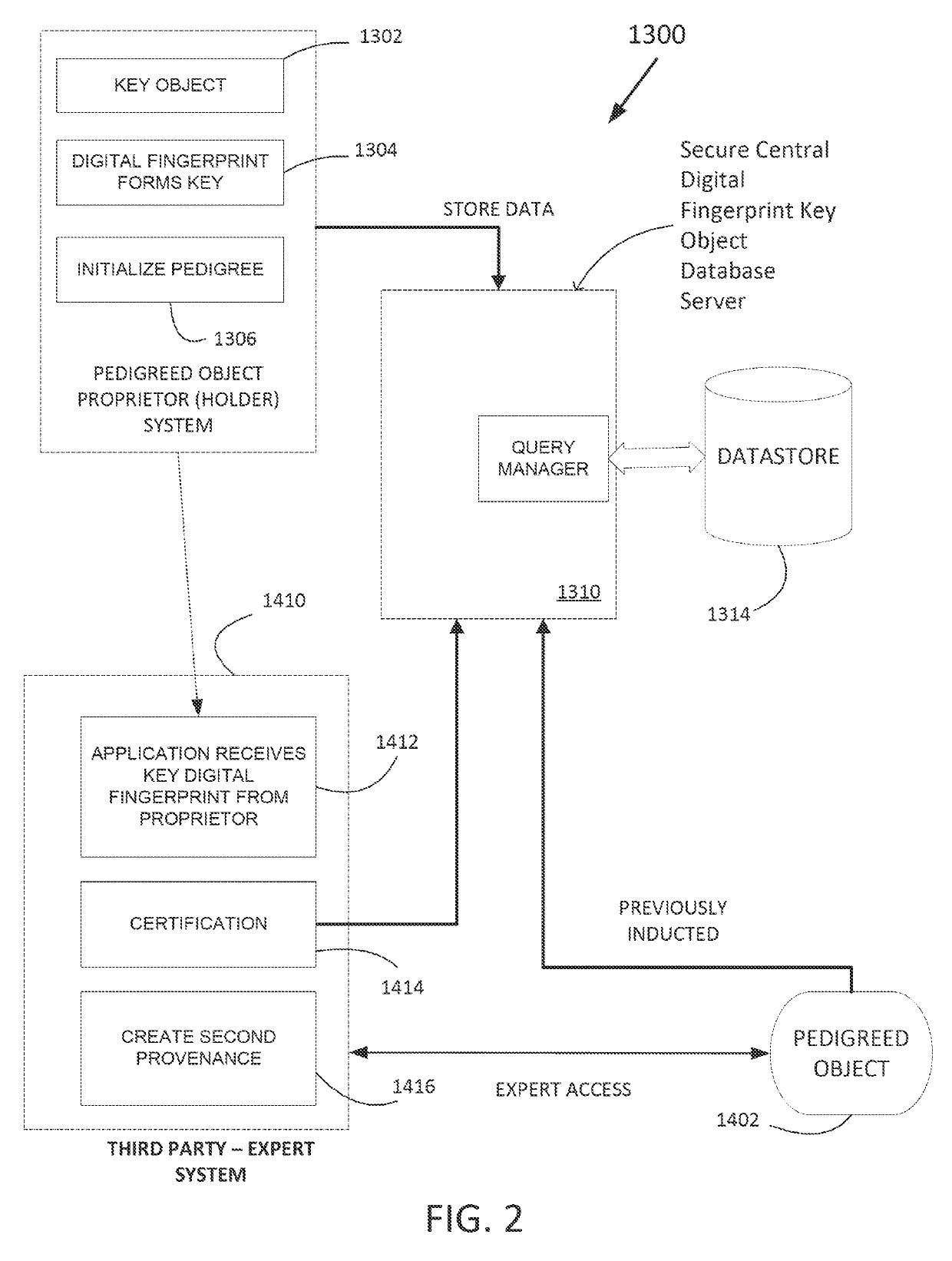
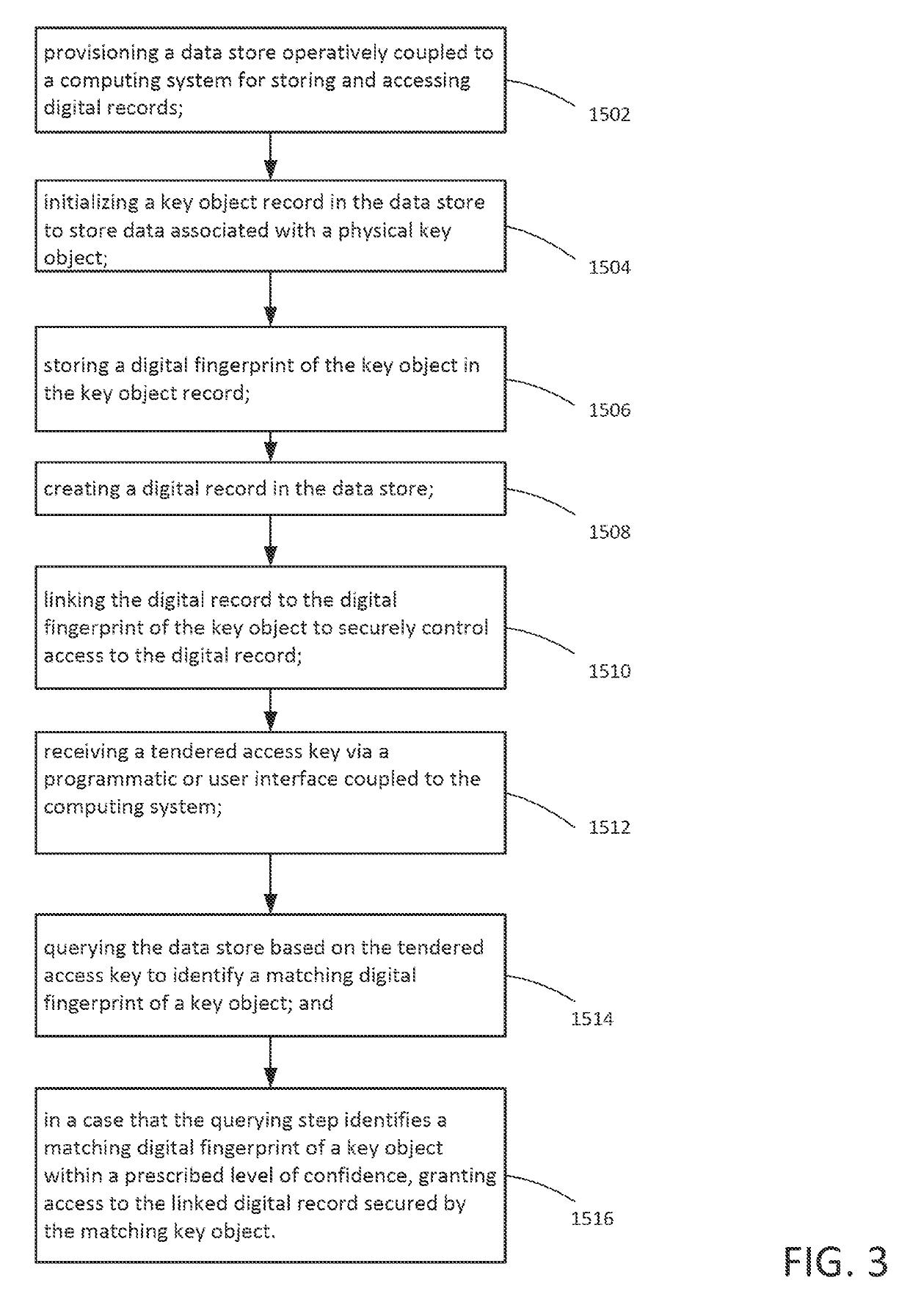
Secure digital fingerprint key object database
ActiveUS20190228174A1Control process safetyKey distribution for secure communicationUser identity/authority verificationDigital recordingData memory
A data store to store and access digital records is provided, and a key object record is initialized in the data store to store data associated with a physical key object. A digital fingerprint of the physical key object is stored in the key object record. Another digital record is created in the data store that is not the key object record. The digital record is linked to the digital fingerprint of the physical key object. The linking is arranged to provide secure control access to the linked digital record. A tendered access key is received via a programmatic interface or user interface, and the data store is queried based on the tendered access key to identify a matching digital fingerprint of a key object. In a case that the querying identifies the matching digital fingerprint of the key object within a prescribed level of confidence, access to the linked digital record secured by the key object is granted.
Owner:ALITHEON INC
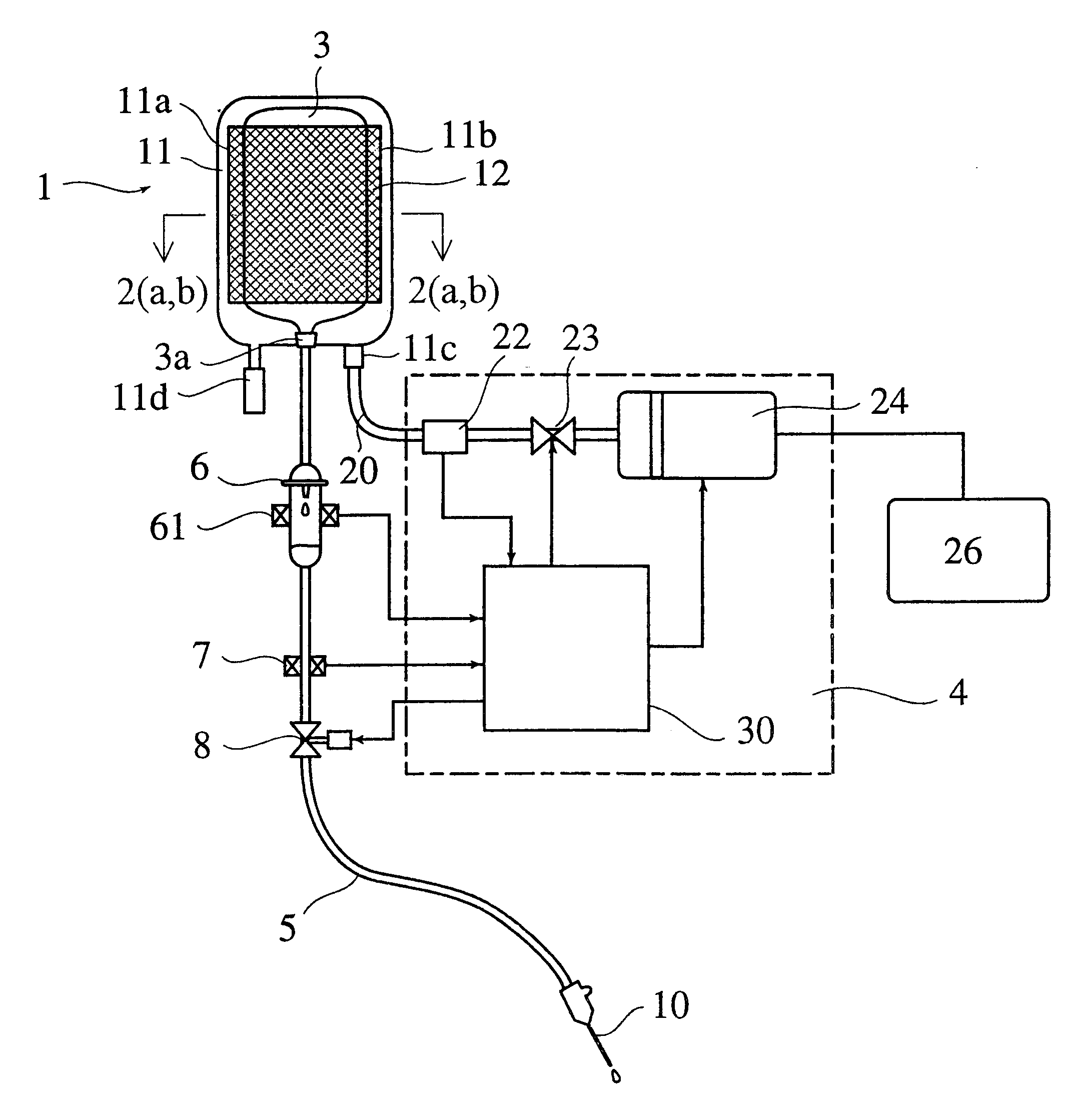
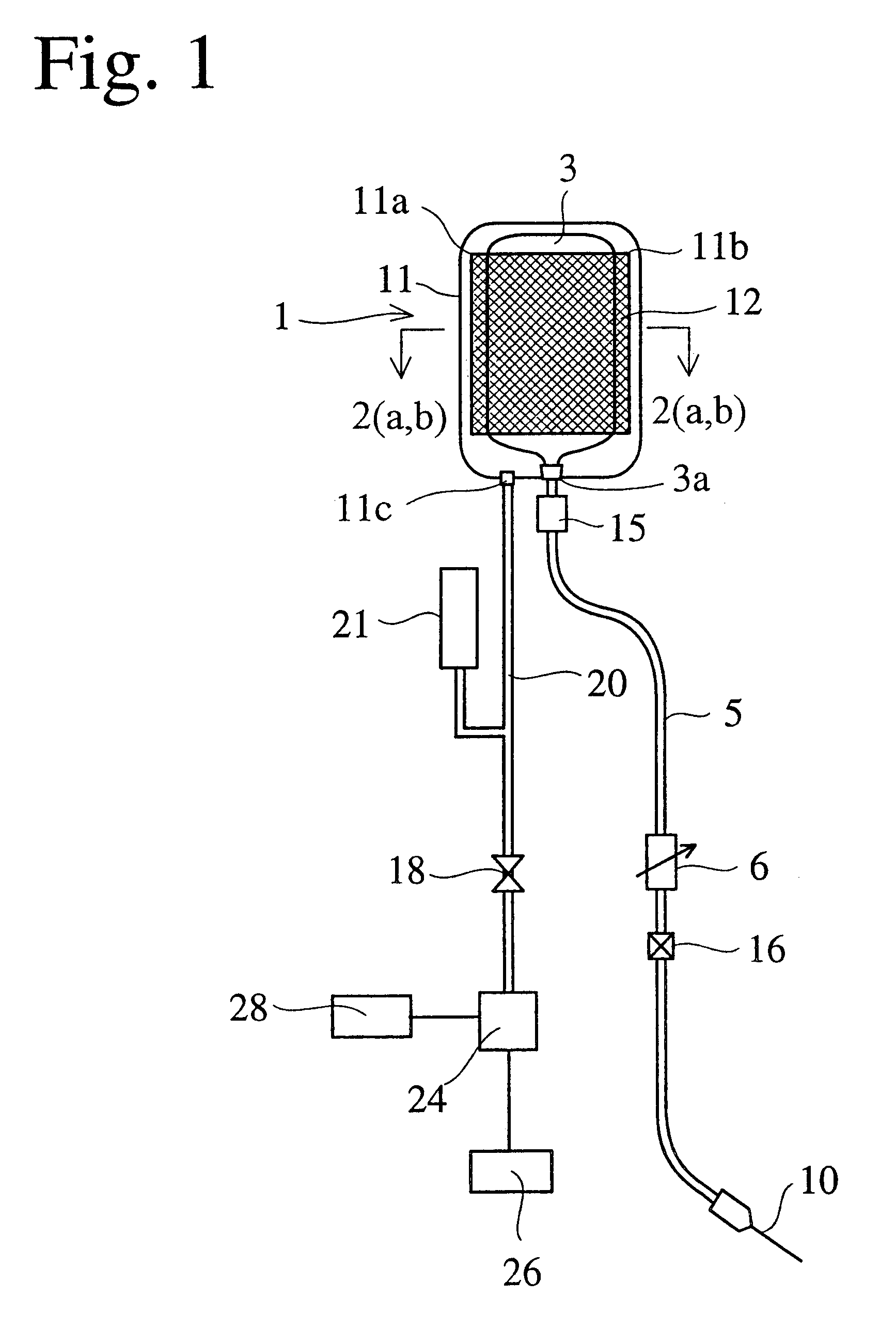
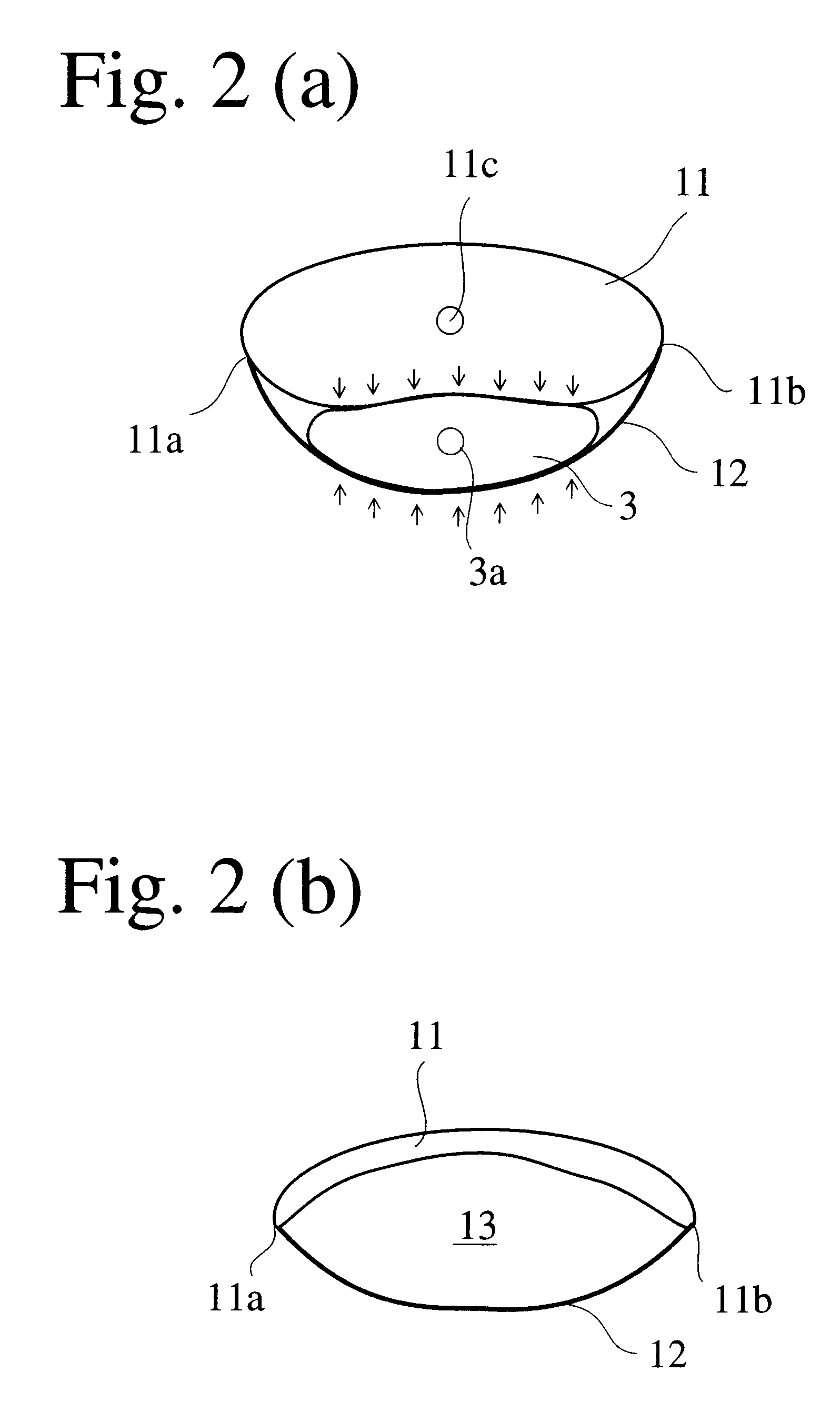
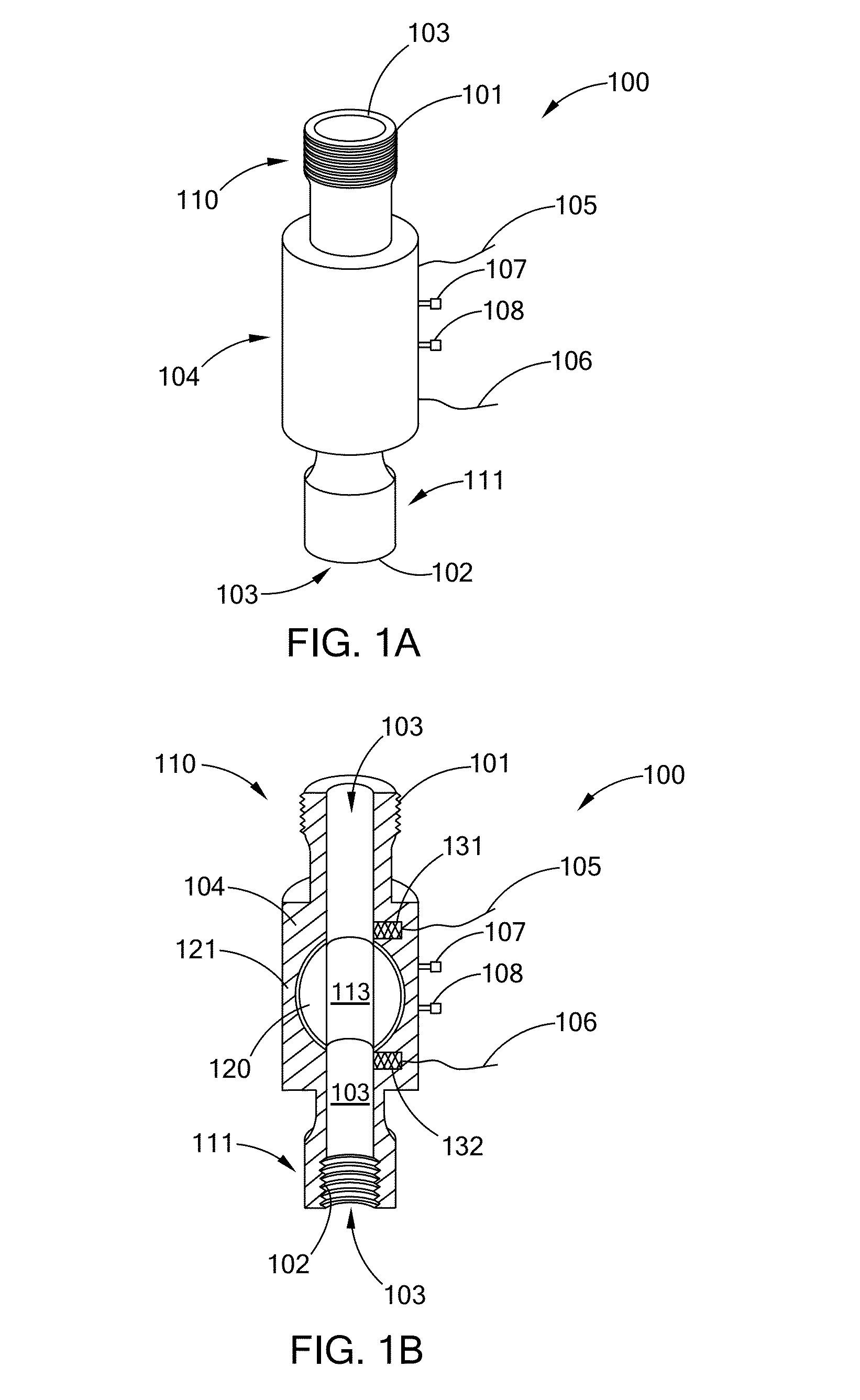
Automatic control-type, portable intravenous infusion apparatus and jacket therefor
InactiveUS6558346B1Constant dropping speed of an infusion liquid safely and surelyDrop in speedJet injection syringesMedical devicesAutomatic controlAir pump
Owner:MEDICOS HIRATA
Apparatus and method for managing P2P traffic
ActiveUS8146133B2Control process safetyReduce overheadDigital data processing detailsUnauthorized memory use protectionTraffic capacityApplication software
Owner:ELECTRONICS & TELECOMM RES INST
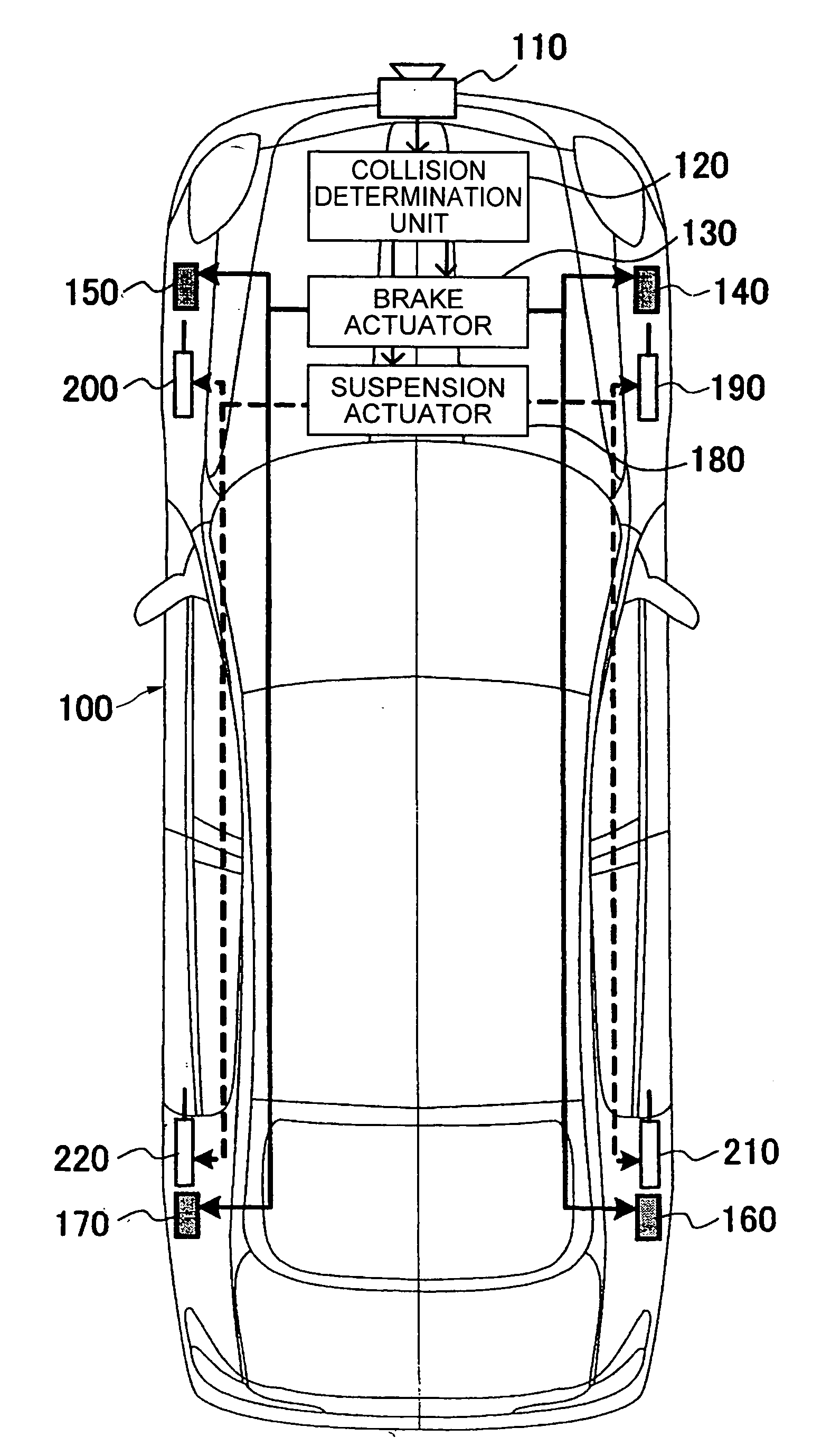
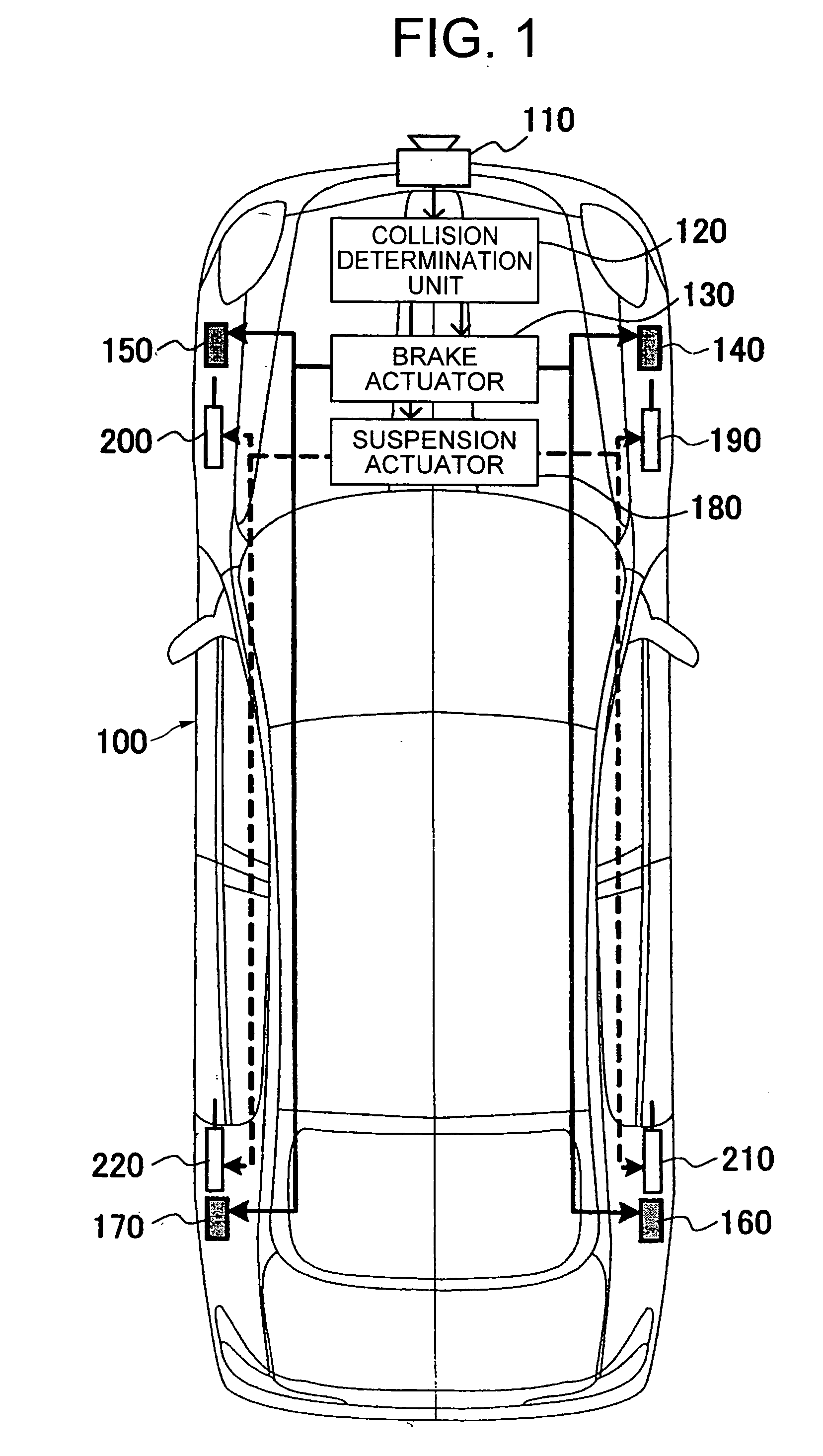
Vehicle safety control apparatus for avoiding collision
InactiveUS20070192030A1Improve friction forceShorten braking distanceDigital data processing detailsAnimal undercarriagesWheel loadEstimation result
A collision between a vehicle and an obstacle is estimated, and based on the estimation result, vehicle deceleration control is performed by a brake actuator to reduce the collision and vehicle wheel load is controlled by a suspension actuator.
Owner:HITACHI LTD
Hideaway Christmas Lights Party Lights Tuck Lights Train lights
InactiveUS20100110668A1Control process safetyEliminate needLighting support devicesElectric circuit arrangementsLight equipmentRemote control
Improvements in remote control hideaway holiday / party lights / messages lights with a casing that is permanently fixed to a home or business is disclosed. The lights are on a string and roll up or down below over eve, fascia or rain gutters. After the holiday or event simply pressing a remote control will retract the lighting into a concealed enclosure till the next party or holiday season comes around. The remote has a distinctive key code, which makes the lights operate for each owner. The concealed enclosure consist of door(s), depends on the number of lighting styles, power supply, drive motor, a string light(s) on a spool inside and controls. The lights come in many colors and types and may include shapes. Each enclosure can be self-contained with a solar charger, light sensor, or timer, and a battery that allows each unit to operate autonomously.
Owner:MARLONIA IVY ANTRINETTE
Robot deployed weapon system and safing method
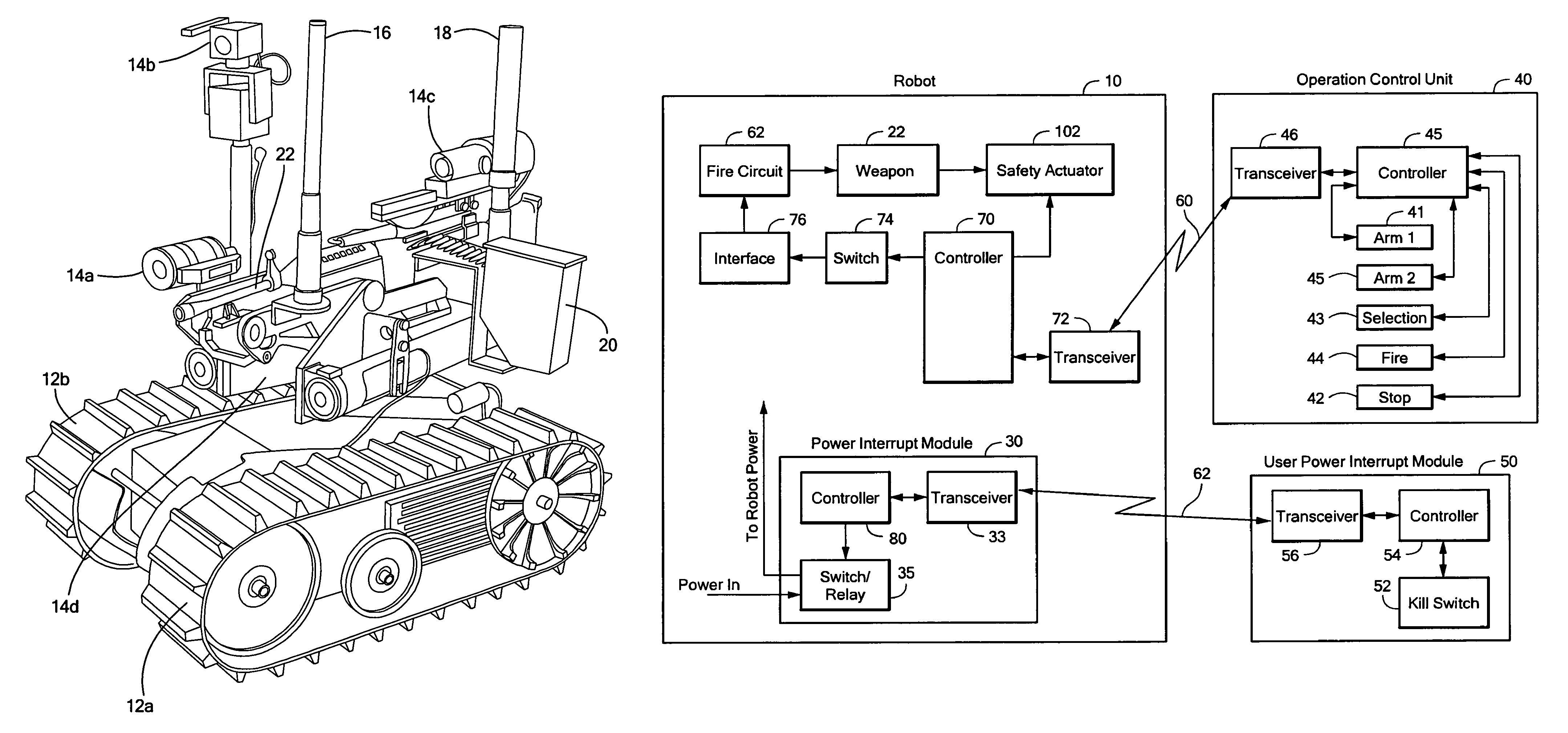
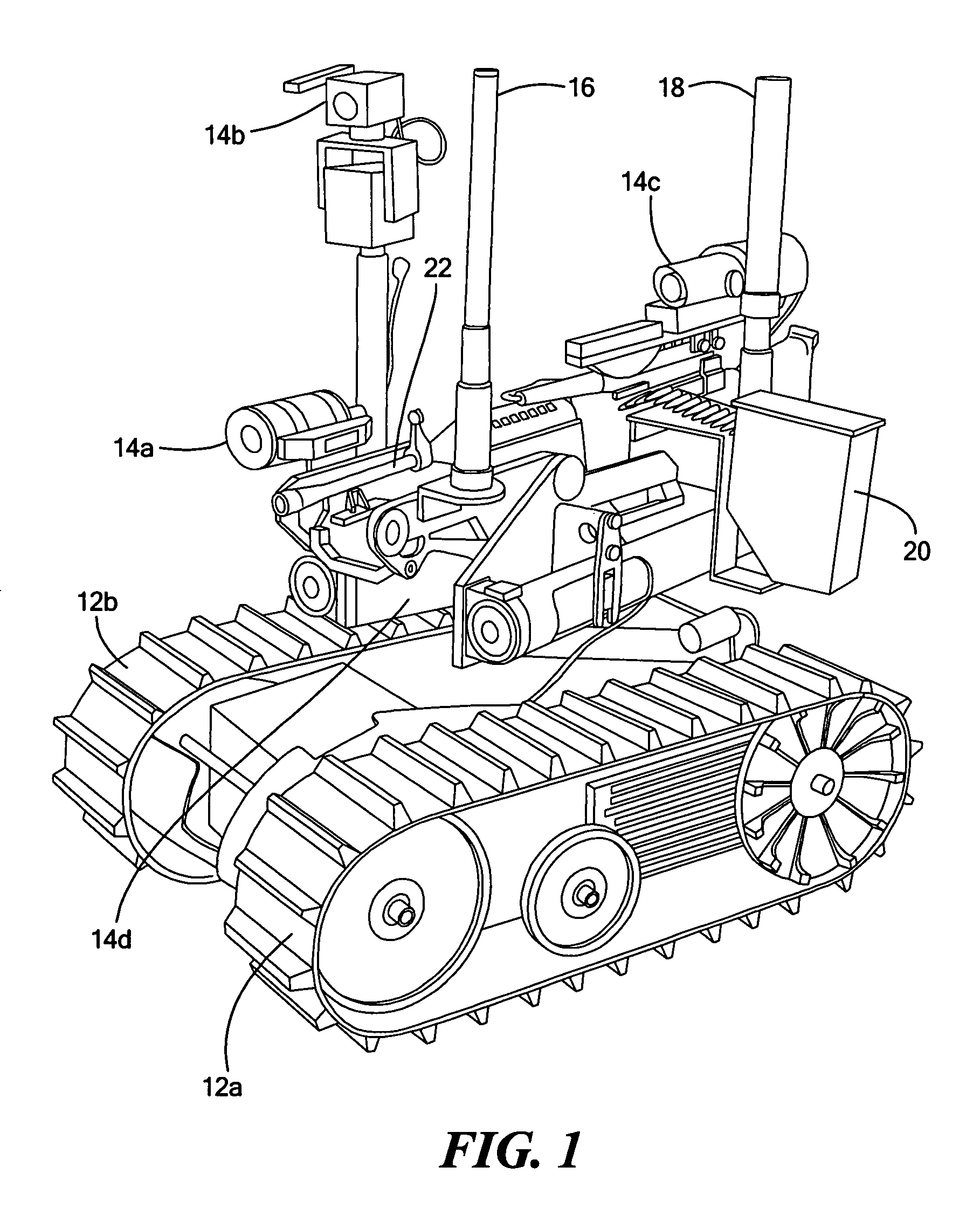
ActiveUS7974736B2Control process safetyProgramme-controlled manipulatorArmoured vehiclesTelecommunications linkOn board
Owner:FOSTER-MILLER
Method and system for disaster recovery of data from a storage device
InactiveUS20090052669A1Promote generationEnhanced couplingKey distribution for secure communicationEncryption apparatus with shift registers/memoriesPasswordRemovable media
Aspects of the invention provide a method and system for securely managing the storage and retrieval of data. Securely managing the storage and retrieval of data may include receiving a first disaster recovery code and acquiring a first password corresponding to the first disaster recovery code. A first disaster recovery key may be generated based on the first disaster recovery code and the first password. Another aspect of the invention may also include generating the received first disaster recovery code based on said first password and the first disaster recovery key. The generated disaster recovery code may be securely stored on at least a portion of a storage device or a removable media. Data stored on the storage device may be encrypted using the first generated disaster recovery key. Additionally, data read from the storage device may be decrypted using the generated first disaster recovery key.
Owner:AVAGO TECH INT SALES PTE LTD
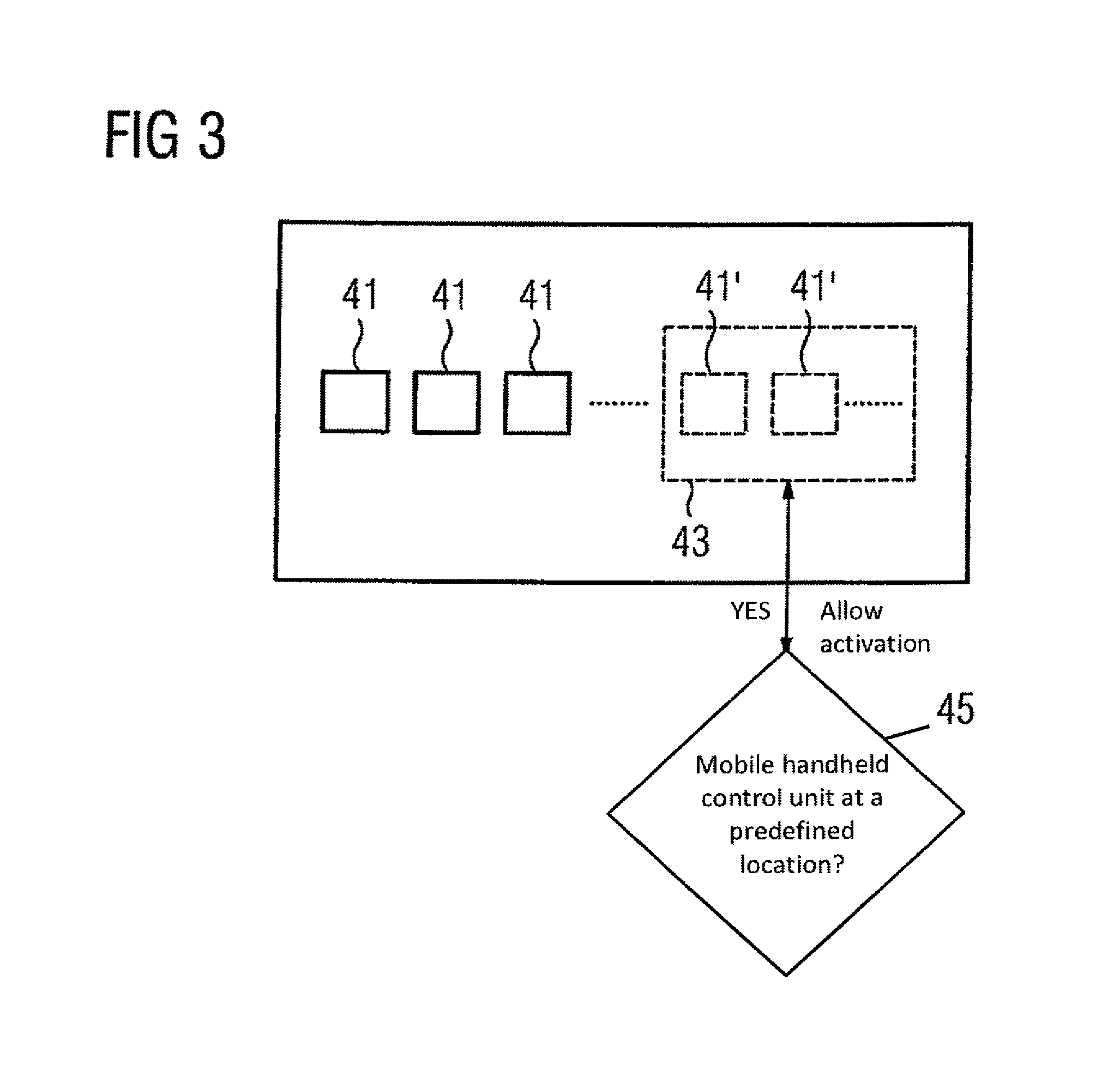
Methods and systems for position-enabled control of a medical system
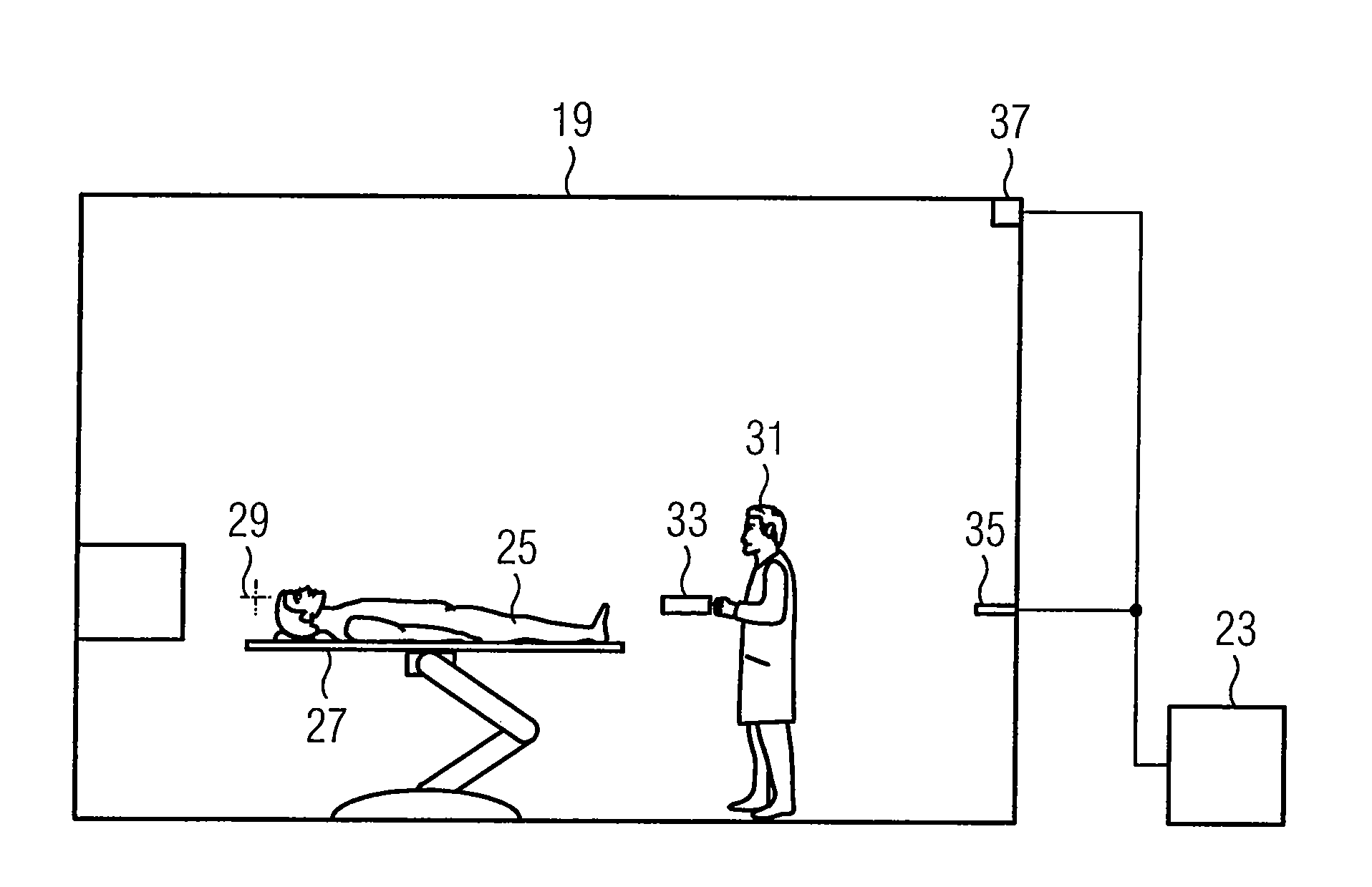
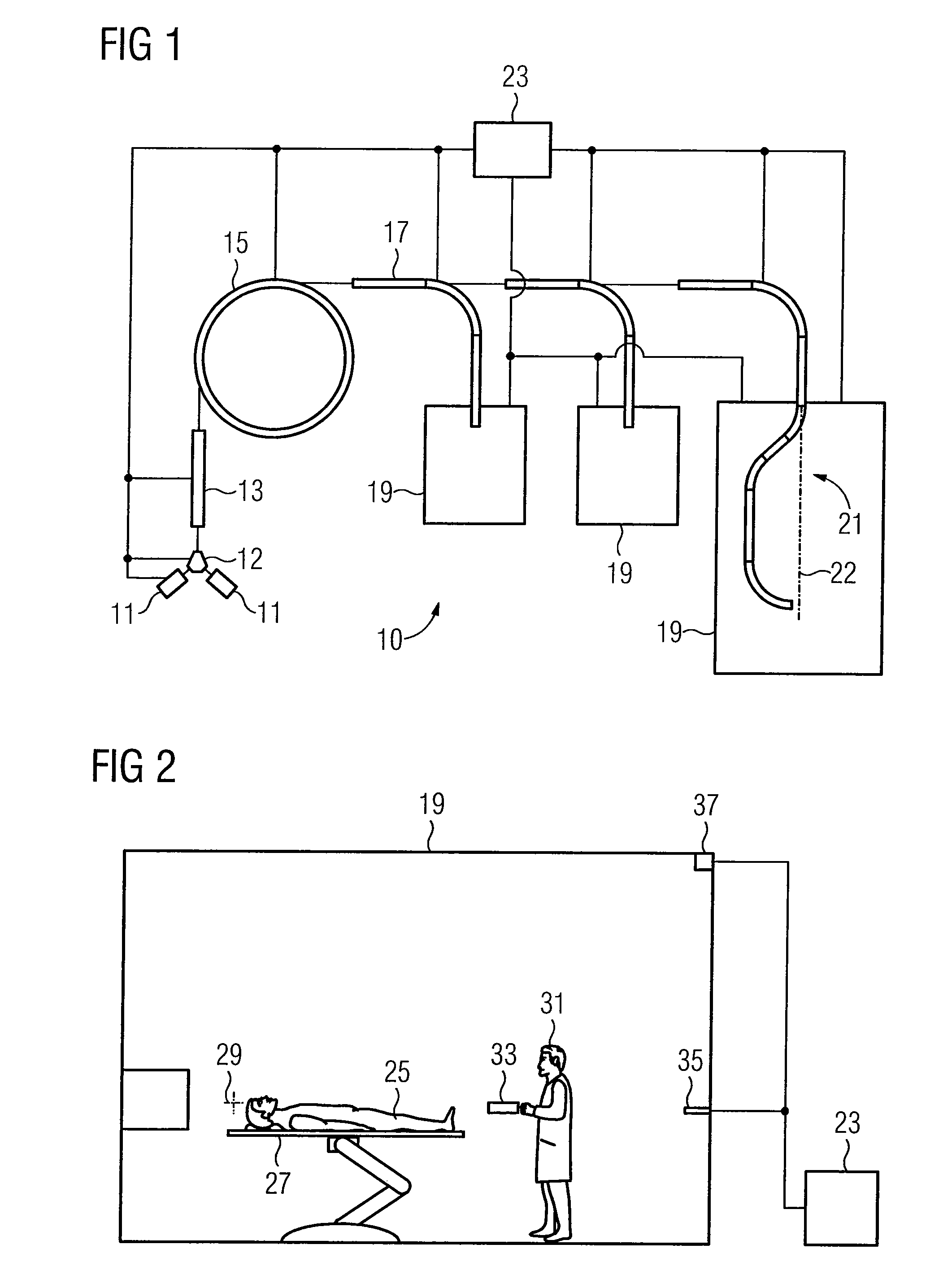
ActiveUS8657743B2Operational securityControl process safetyMechanical/radiation/invasive therapiesDigital data processing detailsMedical diagnosisExecution control
A control device for a medical system is provided. The medical system may be a medical diagnosis and / or medical therapy system. The medical system may include a control unit operable to be used to carry out control processes that control the medical system, and a mobile handheld control unit operable to control at least one controllable element of the medical system by a user. The control device may be configured so that one or more control processes may only be carried out by the control unit when the mobile handheld control unit is located at a predefined location.
Owner:VARIAN MEDICAL SYST PARTICLE THERAPY GMBH & CO KG
Method and apparatus for bearer and server independent parental control on smartphone, managed by the smartphone
InactiveUS8798610B2Control process safetyThorough understandingUnauthorised/fraudulent call preventionEavesdropping prevention circuitsCrypto phoneComputer hardware
In some embodiments, the invention involves parental or master control of a child or subordinate mobile phone without service provider intervention. An embodiment of the invention is a system and method relating to master control of the subordinate smart phone using features on the smart phones, and independent of features provided by the phone service providers. Communication between the master and subordinate phones may be initiated using SMS messaging, near field communication, Bluetooth, direct connect to a PC, or by other secure wireless or wired connections. Once initiated, desired communication events are captured by the parental control application to effect control policies on the subordinate phone. Communication between the phones may be encrypted to prevent malicious intervention of message traffic Other embodiments are described and claimed.
Owner:INTEL CORP
Robot deployed weapon system and safing method
ActiveUS20100263524A1Control process safetySafety arrangementArmoured vehiclesTelecommunications linkOn board
This subject invention features a robot deployed weapon system. A remotely controlled mobile robot has a weapon mounted to the robot. There is a firing circuit for the weapon and a weapon interrupt module on board the robot. An operator control unit is for remotely operating the robot and the weapon. The operating control unit preferably includes a stop switch. Also, a separate operator module is in communication with the weapon interrupt module. Preferably, the operator module includes a kill switch. There are two communication links. The first communication link is between the operator control unit and the robot. This communication link is configured to safe the weapon if the stop switch is activated and / or the first communication link degrades. The second communication link is between the operator module and the weapon interrupt module. The communication link is configured to safe the weapon if the kill switch is activated and / or the second communication link degrades.
Owner:FOSTER-MILLER
Airbag apparatus
InactiveUS7600782B2Simple structureControl process safetyPedestrian/occupant safety arrangementEngineeringAirbag
The airbag apparatus includes an airbag having an exhaust hole for discharging part of inflation gas, an open / close controller for controlling opening and closing operations of the exhaust hole, and a flap element releasably joined to the open / close controller and being joined to a periphery of the exhaust hole in an outer side of the airbag which periphery is in a side facing away from the open / close controller, for opening and closing the exhaust hole. The apparatus further includes an open / close means arranged in the periphery of the exhaust hole. Upon airbag inflation, if the flap element is retained by the open / close controller, the open / close means is held down at its outer side by the flap element and keeps the exhaust hole closed. If the flap element is released from the open / close controller, the open / close means opens by the pressure of inflation gas to expand an opening area of the exhaust hole.
Owner:TOYODA GOSEI CO LTD
Methods and devices for trusted protocols for a non-secured, distributed environment with applications to virtualization and cloud-computing security and management
ActiveUS20130247230A1Without impairing functionalityControl process safetyDigital data processing detailsAnalogue secracy/subscription systemsVirtualizationTrusted Computing
The present invention discloses methods for trusted protocols for a non-secure computing-environment. Methods include the steps of: upon request for determining that an untrusted computing resource is trustworthy, vouching for the untrusted resource as trustworthy by a trusted computing resource upon satisfying at least one criterion of: the trusted resource was directly involved in setting up and / or activating the untrusted resource; and / or has access to a database of identifying credentials and / or information which allow the trusted resource to verify that the untrusted resource is trustworthy; and concealing at least one secret that needs to be present on any computing resource, wherein at least one secret is concealed differently on each computing resource; and transmitting at least one secret from any computing resource to any other computing resource in a way that changes the step of concealing at least one secret without any computing resource knowing at least one secret.
Owner:PORTICOR
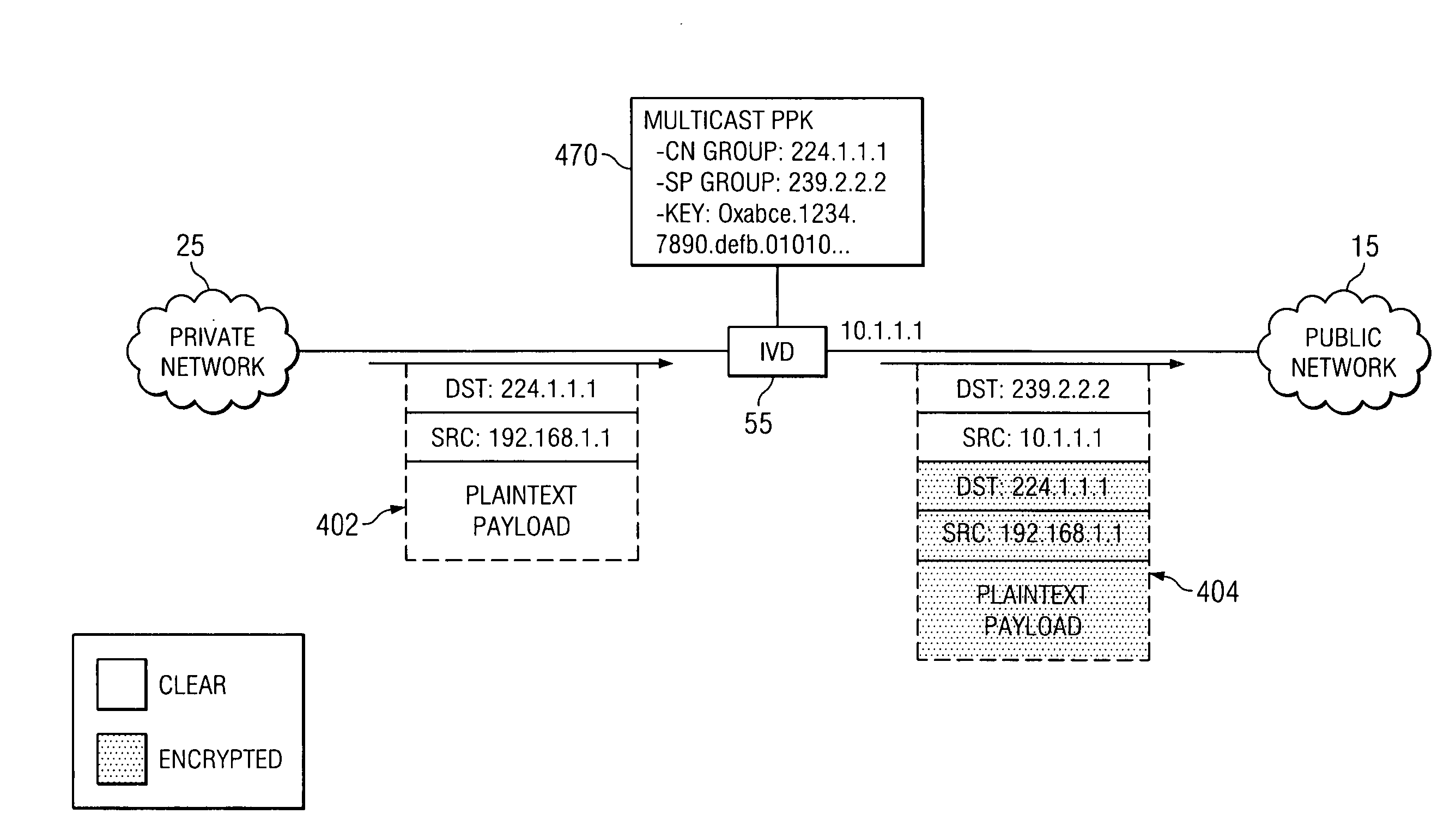
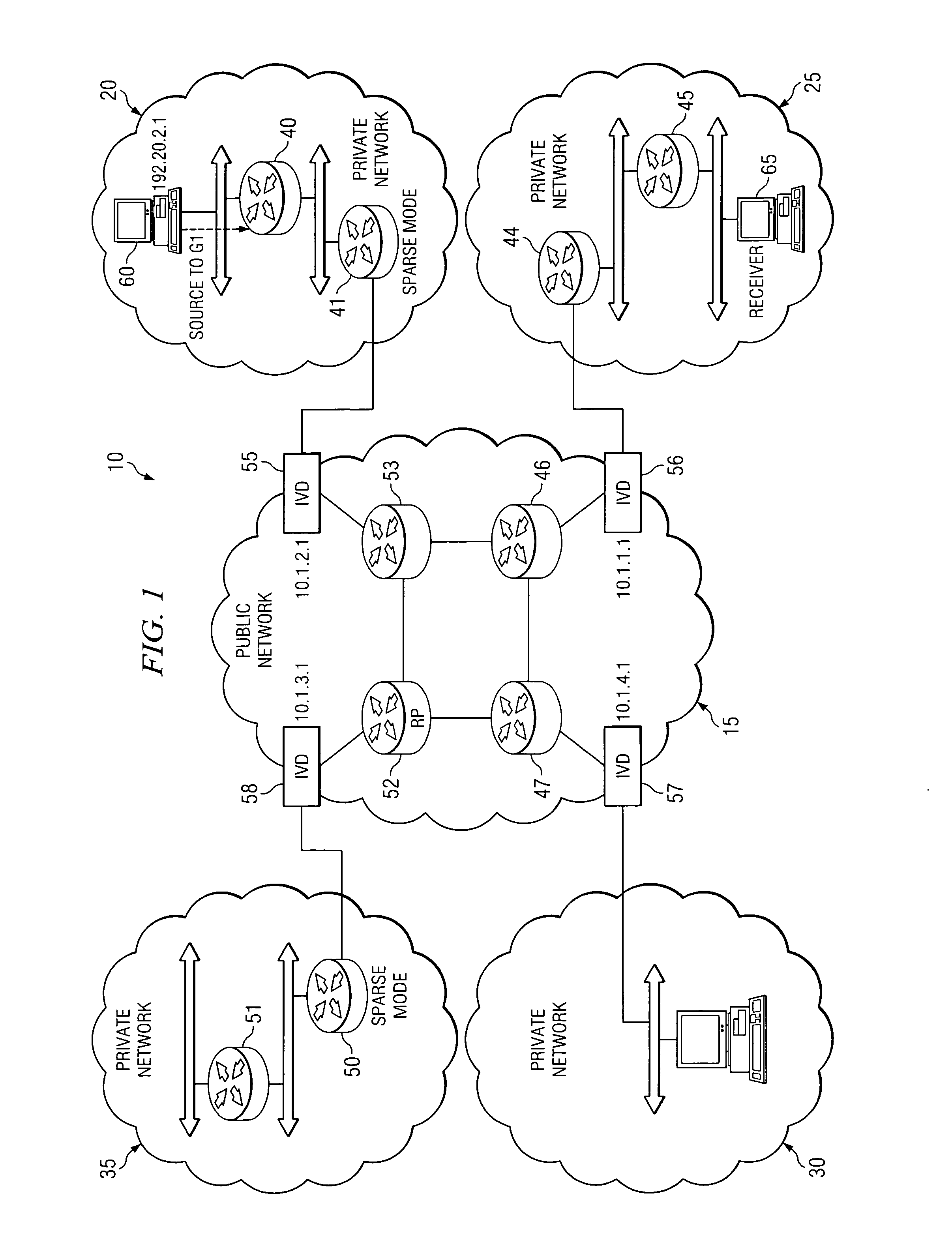
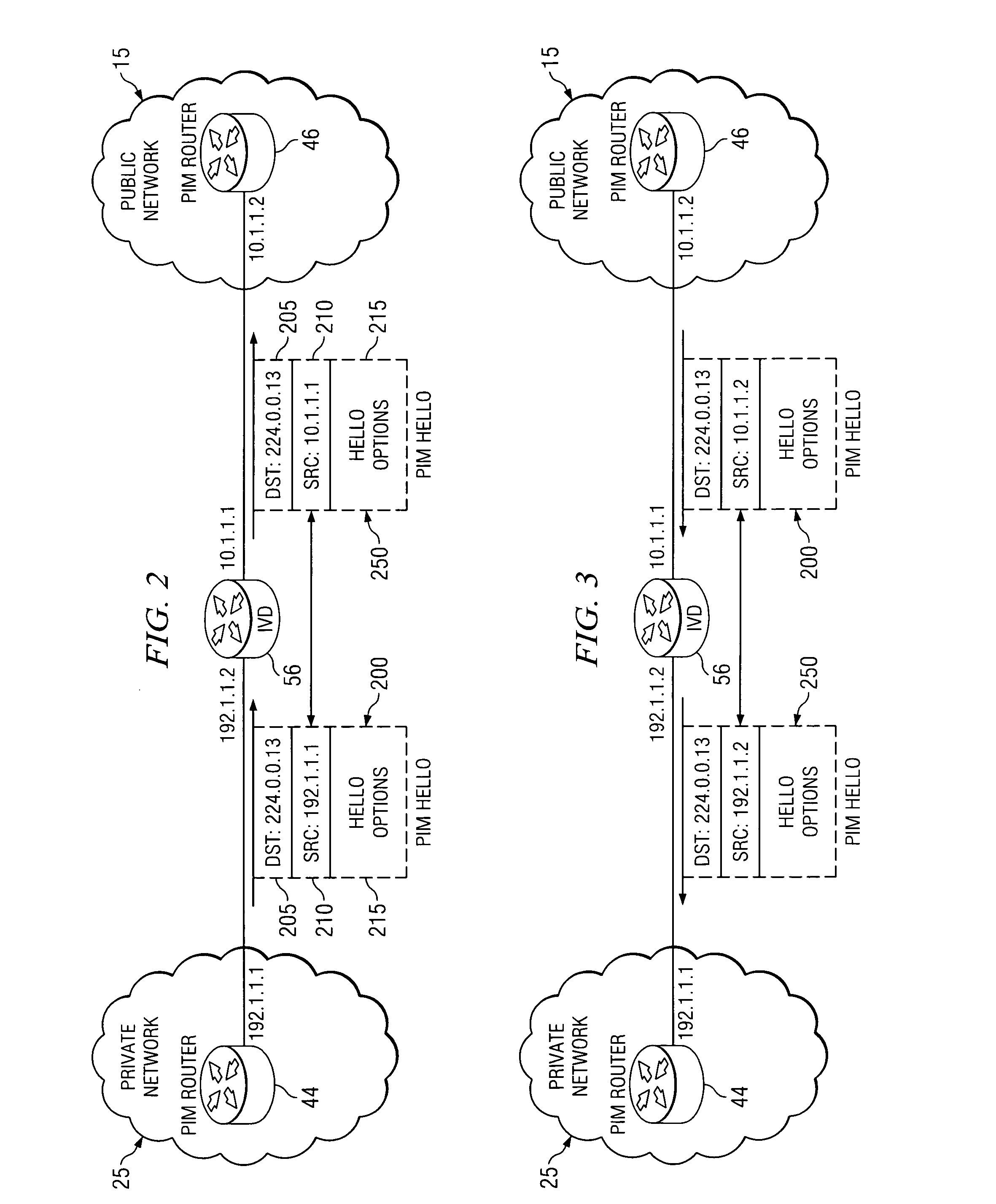
System and method for providing secure multicasting across virtual private networks
ActiveUS20070214359A1Prevent visibilityPreventing unauthorized analysisUser identity/authority verificationTime-division multiplexPrivate networkPublic network
A method is provided for securely transmitting multicast data across an unsecured public network. Such a method includes receiving a join message identifying at least one private multicast group; mapping the private multicast group to a public multicast group; generating a membership report specifying the public multicast group; and sending the membership report to the unsecured network. Additionally, the method may further comprise creating a secure tunnel through the unsecured network to a network element coupled; generating an encrypted control message specifying the private multicast group; and sending the encrypted control message through the secure tunnel to the network element.
Owner:CISCO TECH INC
Light weight high power laser presure control systems and methods of use
InactiveUS20140069896A1Control process safetyWell/borehole valve arrangementsSealing/packingHigh power lasersControl system
There is provided pressure control systems, methods and apparatus for the use of high power laser energy to server structures, such as rods, tubes, wireline, slickline and braided line in well and pipeline pressure control situations.
Owner:FORO ENERGY
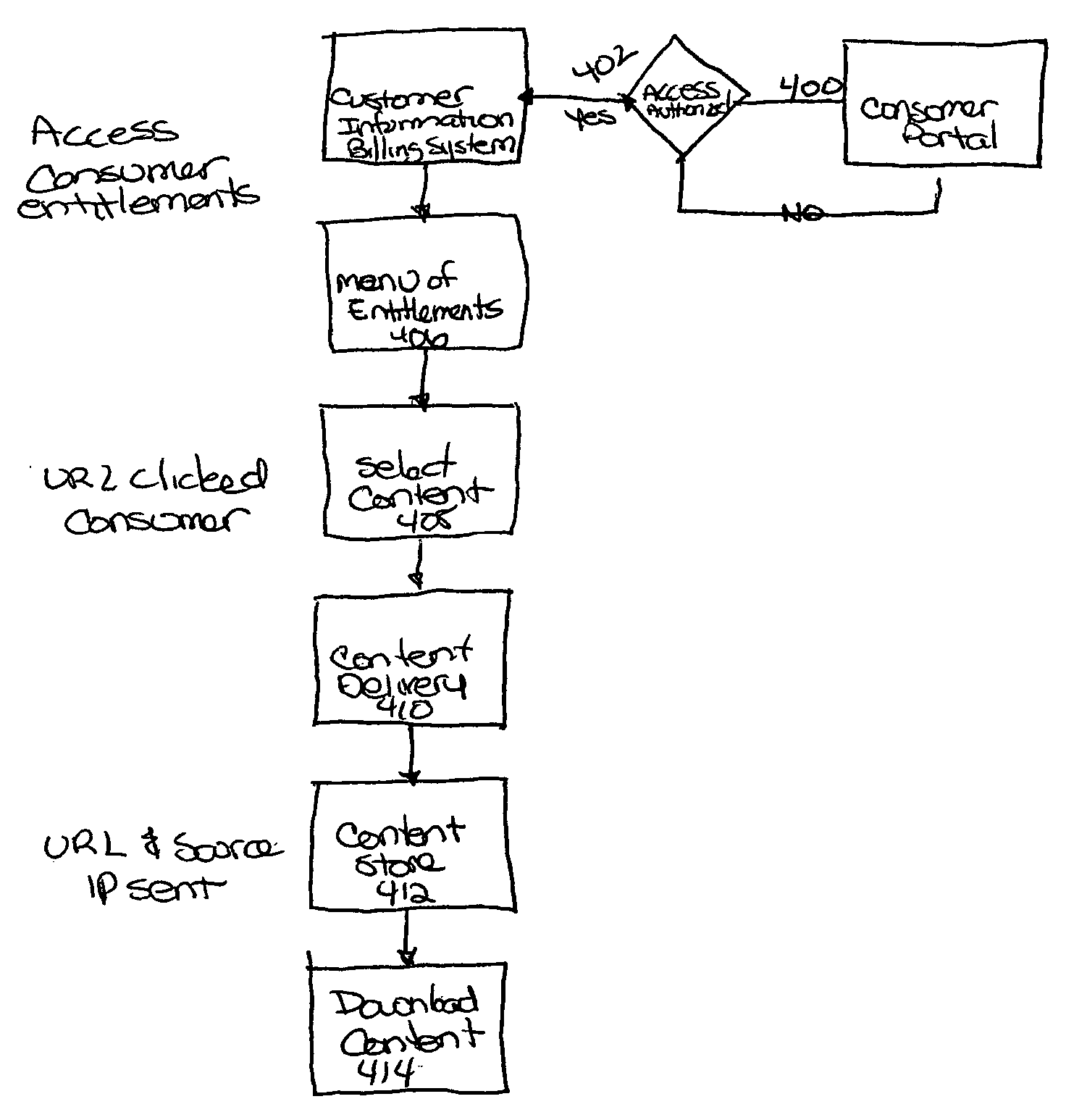
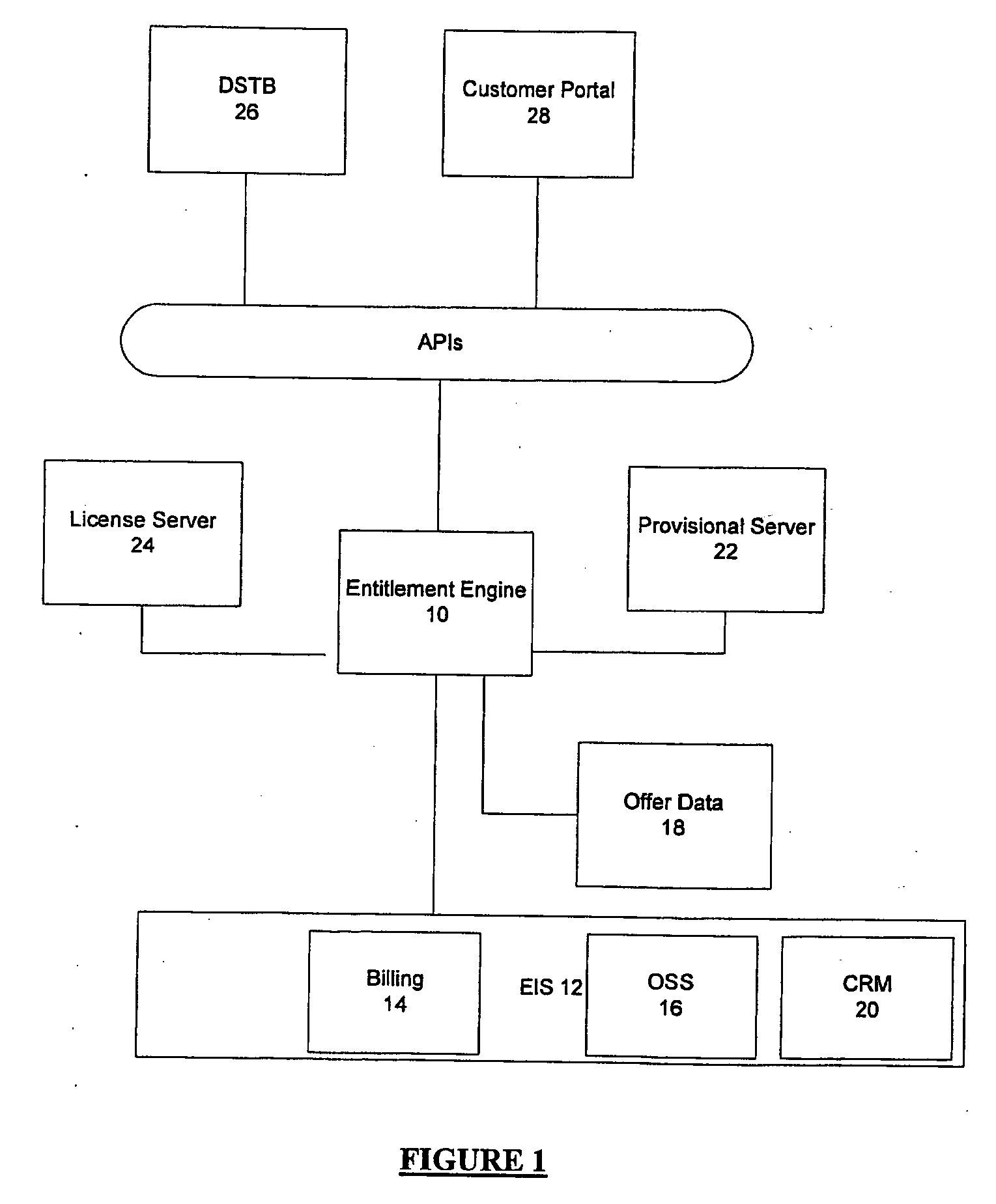
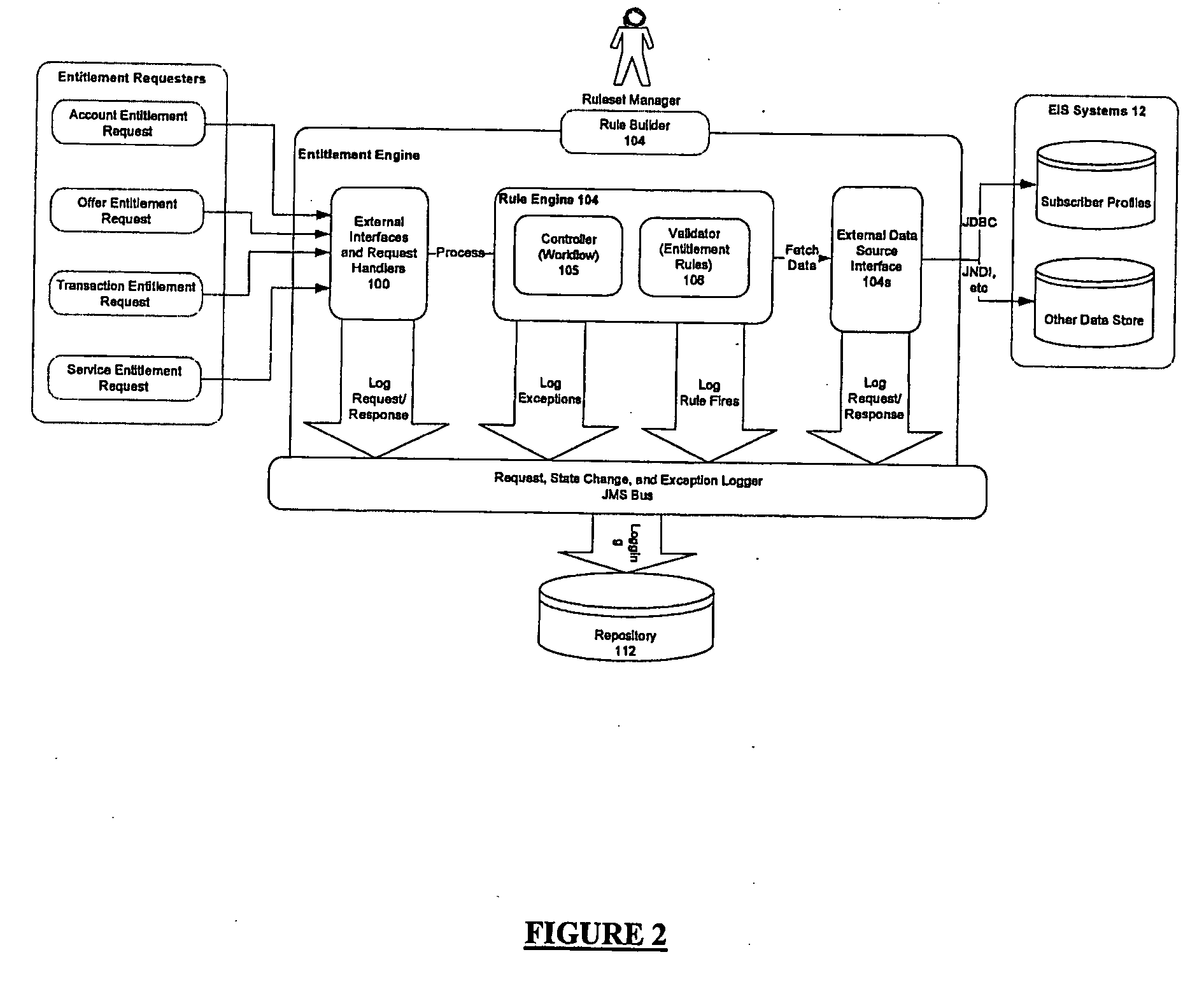
End-to-end digital media entitlement system
InactiveUS20060225138A1Efficient managementProtected contentDigital data processing detailsUser identity/authority verificationData needsSystem interface
A system for creating and processing customer entitlement rules employs a first interface for creating customer entitlement rules and a second interface for communicating with a portal for consuming digital content entitled to. An entitlement engine processes the entitlements, and the system interfaces with a plurality of modules in order to obtain data needed to make entitlement decisions. The entitlement engine allows digital content providers to track, secure and manage entitlements for the digital content.
Owner:COMPASS HORIZON FUNDING COMPANY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com