Program processing method and program processing system
A program processing and program technology, applied in the field of program processing methods and systems, can solve problems such as failure to successfully intercept malicious programs, non-checking of dynamic link libraries, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
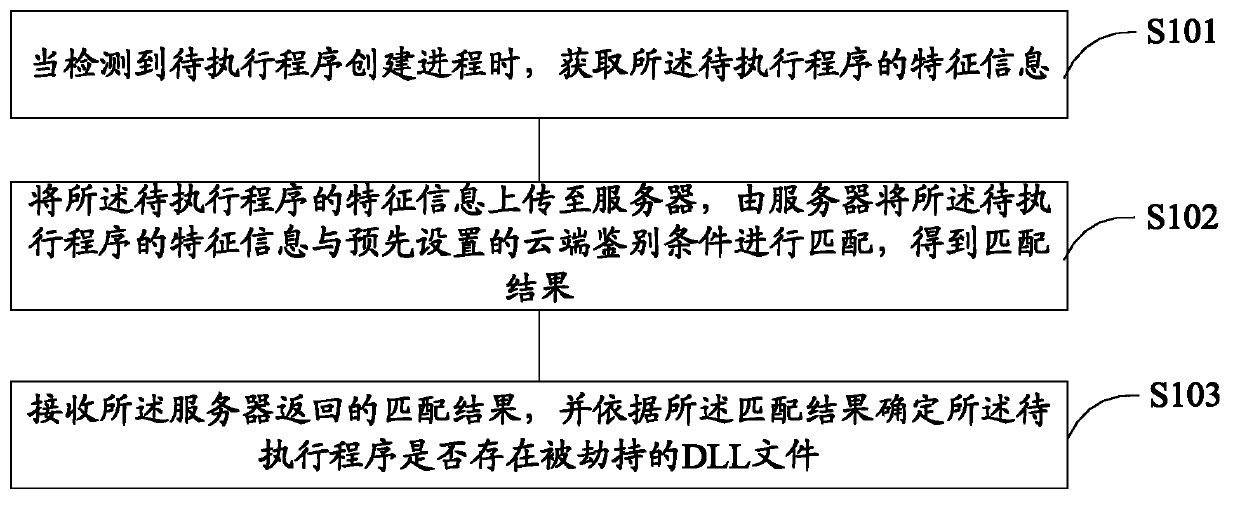
[0099] refer to figure 1 , which shows a flowchart of a program processing method according to an embodiment of the present invention, and the method may specifically include:
[0100] Step S101, when a creation process of a program to be executed is detected, feature information of the program to be executed is acquired.
[0101] Step S102, uploading the feature information of the program to be executed to the server, and the server matches the feature information of the program to be executed with the pre-set cloud identification conditions to obtain a matching result.
[0102] Step S103, receiving the matching result returned by the server, and determining whether there is a hijacked DLL file in the program to be executed according to the matching result.
[0103] The specific process of the program processing method proposed in this embodiment will be described in detail in the following embodiments.
[0104] Through the above steps S101-S103, it is possible to use the c...
Embodiment 2
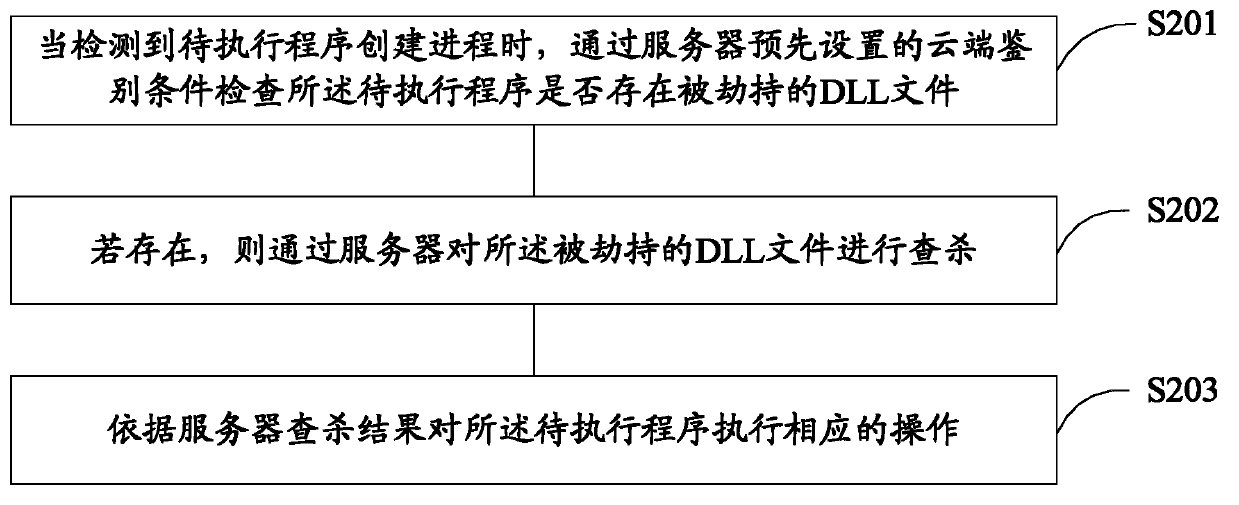
[0106] refer to figure 2 , shows a flowchart of a program processing method according to an embodiment of the present invention.
[0107] In order to adapt to the update speed of malicious programs and quickly identify and kill malicious programs, active defense technologies are generally used to detect and kill malicious programs. Active defense technology is a real-time protection technology that conducts independent analysis and judgment based on the behavior of the program, and protects the key positions of the system by setting interception points at key positions of the system. When a program performs behaviors that modify these key locations (such as writing to the registry, creating scheduled tasks, modifying the browser homepage, modifying the default browser, and registering browser plug-ins, etc.), the program will be intercepted. It is necessary to judge whether the modification behavior is malicious. Usually, the judgment of the behavior is realized by judging w...
Embodiment 3
[0117] Next, a specific program processing method will be described in detail.
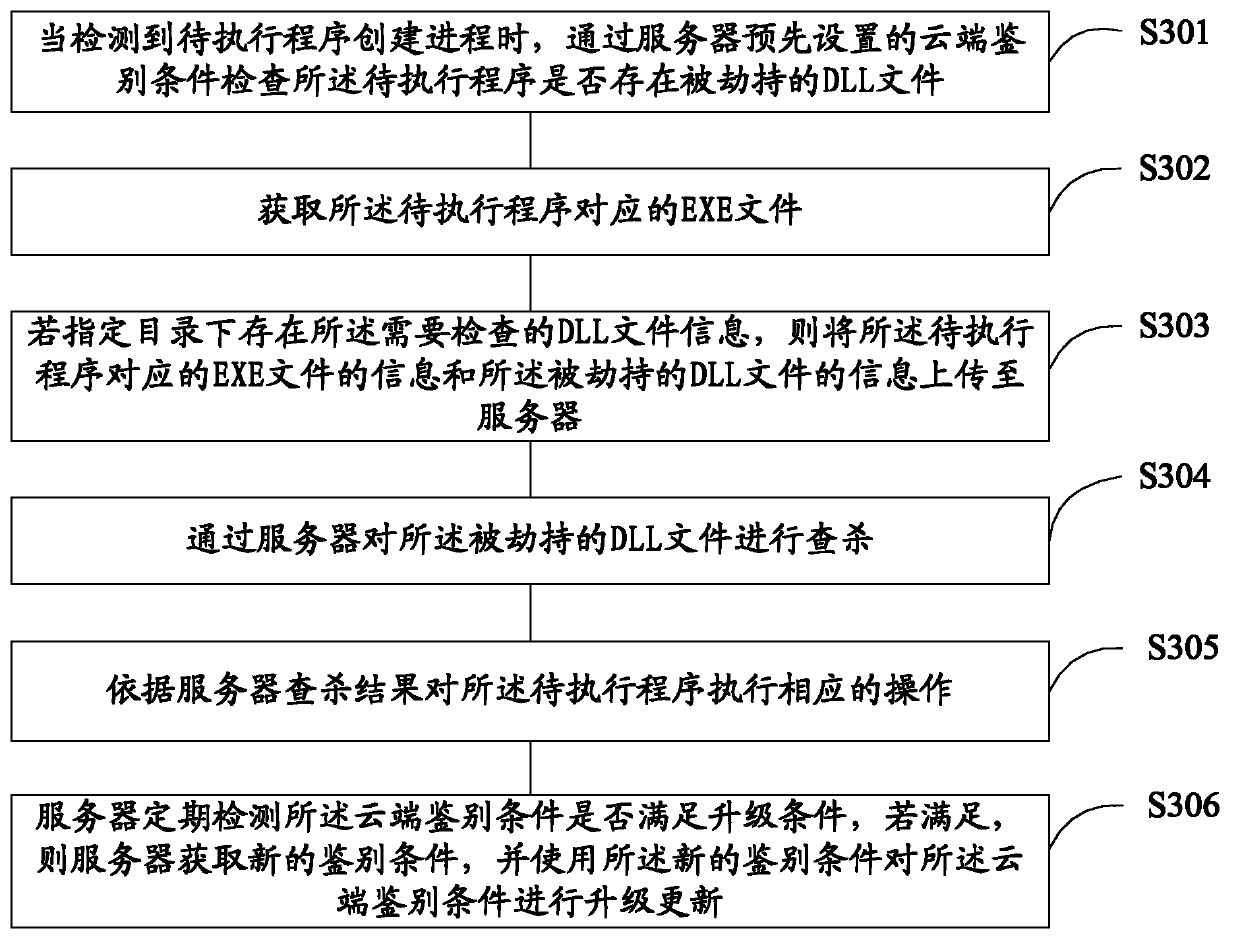
[0118] refer to image 3 , shows a flowchart of a program processing method according to an embodiment of the present invention, the method includes:
[0119] Step S301 , when the creation process of the program to be executed is detected, check whether there is a hijacked DLL file in the program to be executed through the cloud identification condition preset by the server.
[0120] The embodiment of the present invention is mainly to increase the query process of the DLL file when the program to be executed is created. It is necessary to check whether the program to be executed has a hijacked DLL file. If it exists, it means that the program to be executed may be used by a malicious program. , so it is necessary to further check whether these hijacked DLL files are safe.
[0121] In this embodiment, it is checked whether there is a hijacked DLL file in the program to be executed through the cl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com