Network safety protective method for preventing reject service attack event
A denial-of-service attack and network security protection technology, applied in the field of network security, can solve the problems of computing cookies cost, crash, large number of connections, etc., and achieve the effect of increasing processing performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
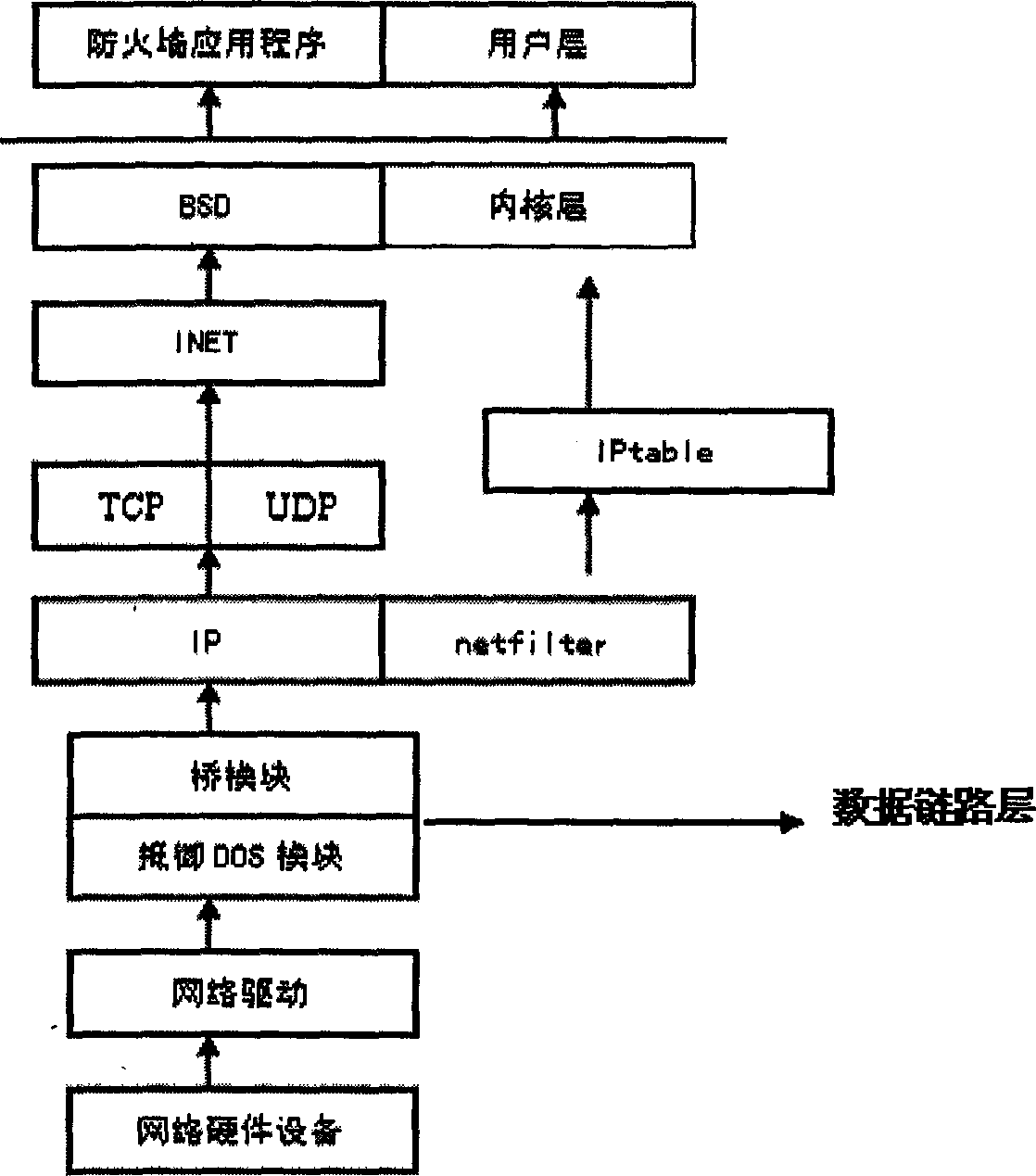
[0022] The protection module that the present invention proposes starts and carries out active protection when being attacked by denial of service, and its specific method is:
[0023] According to the characteristics of the denial of service attack, the quantity of the TCP request packet will become very large instantaneously when the attack occurs, so in the present invention, determine whether the network is under attack by adopting the method of counting the traffic of the TCP request packet. The system first judges what type of data packet it is according to the TCP header information, so as to count the number of TCP request packets arriving per second. Once the firewall detects that the TCP traffic exceeds the normal processing limit of the server, it starts the protection module to process the TCP request packet. And when the TCP flow returns to the normal state of the network, the firewall will no longer start the protection module, and still allow the client computer ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com