Xen-based active defense method
An active defense, front-end driven technology, applied in the field of computer security, can solve problems such as impracticality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
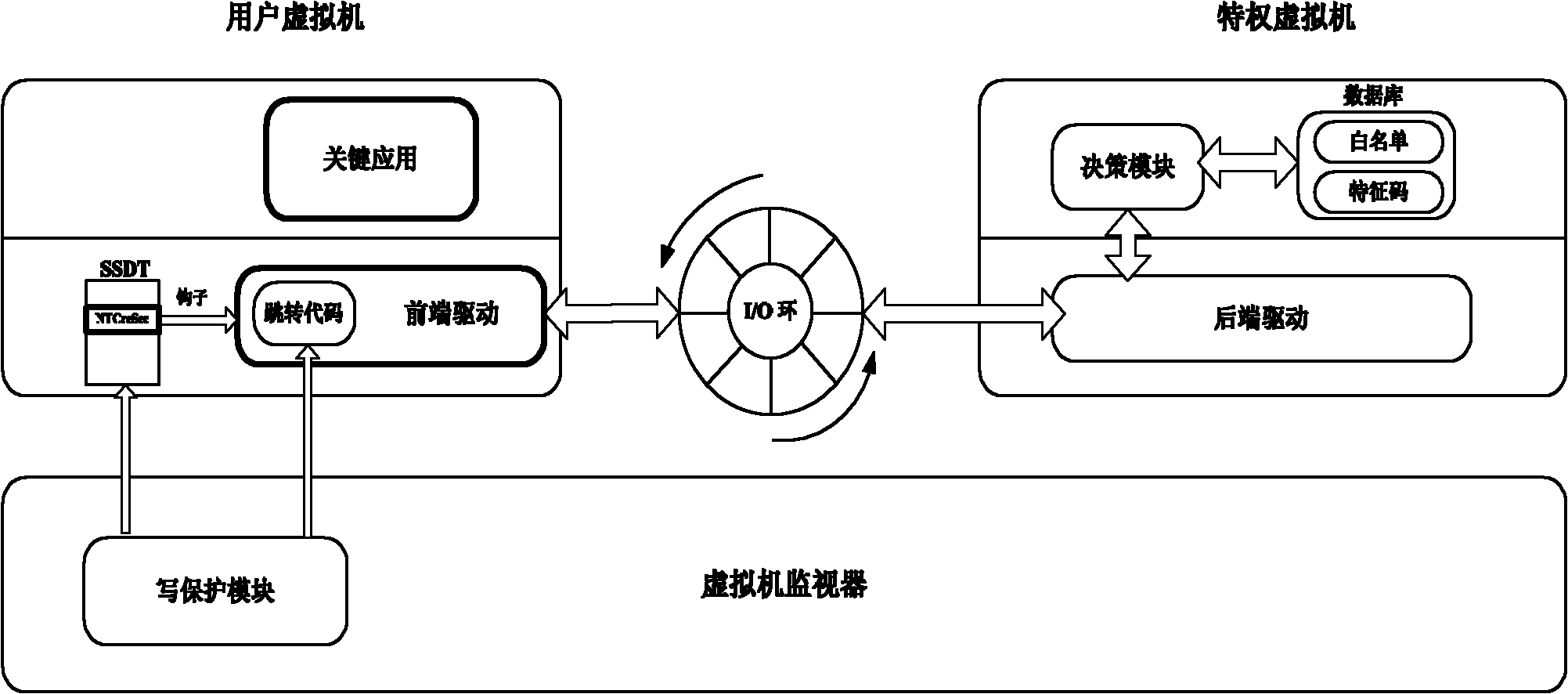
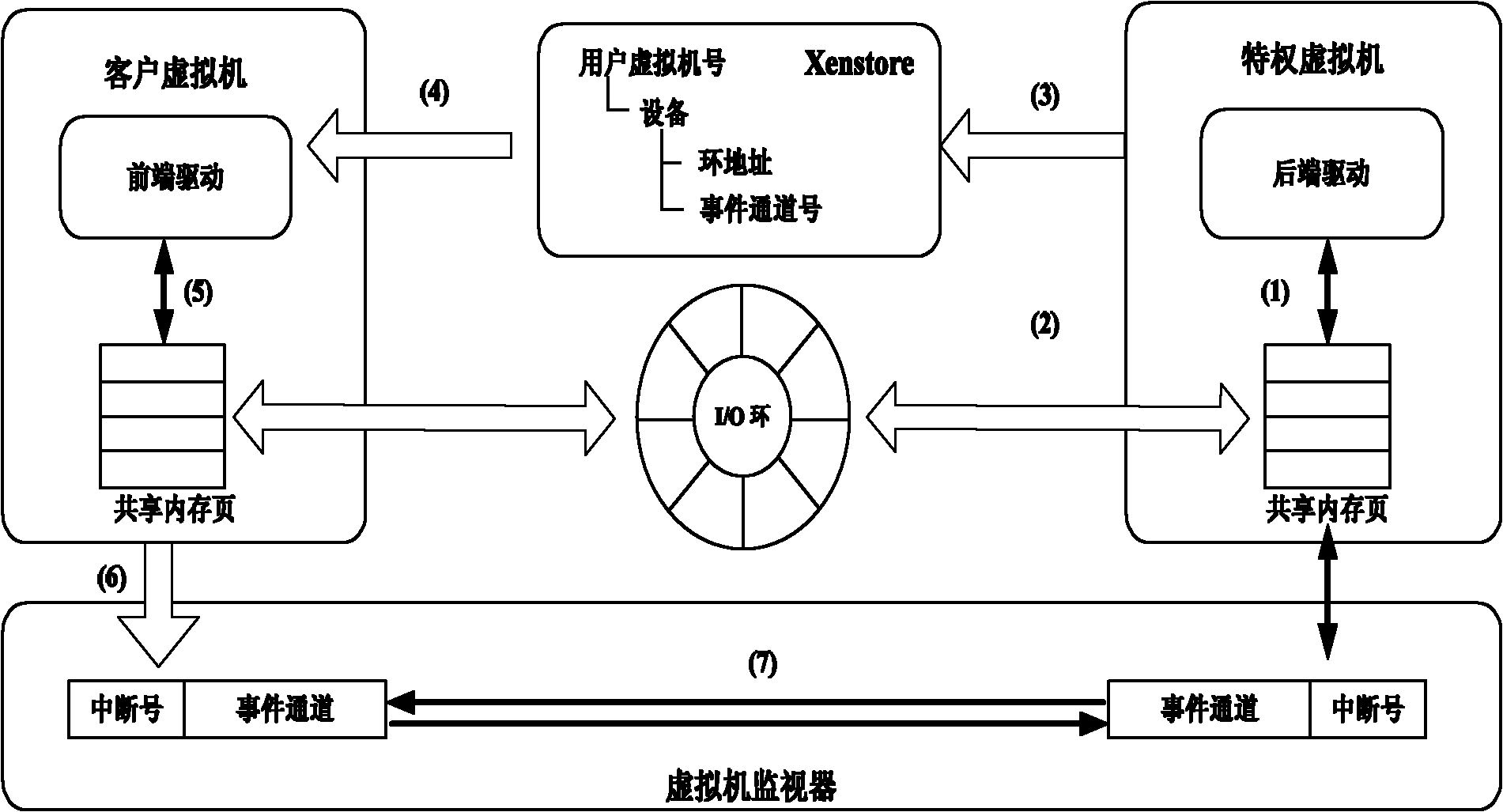
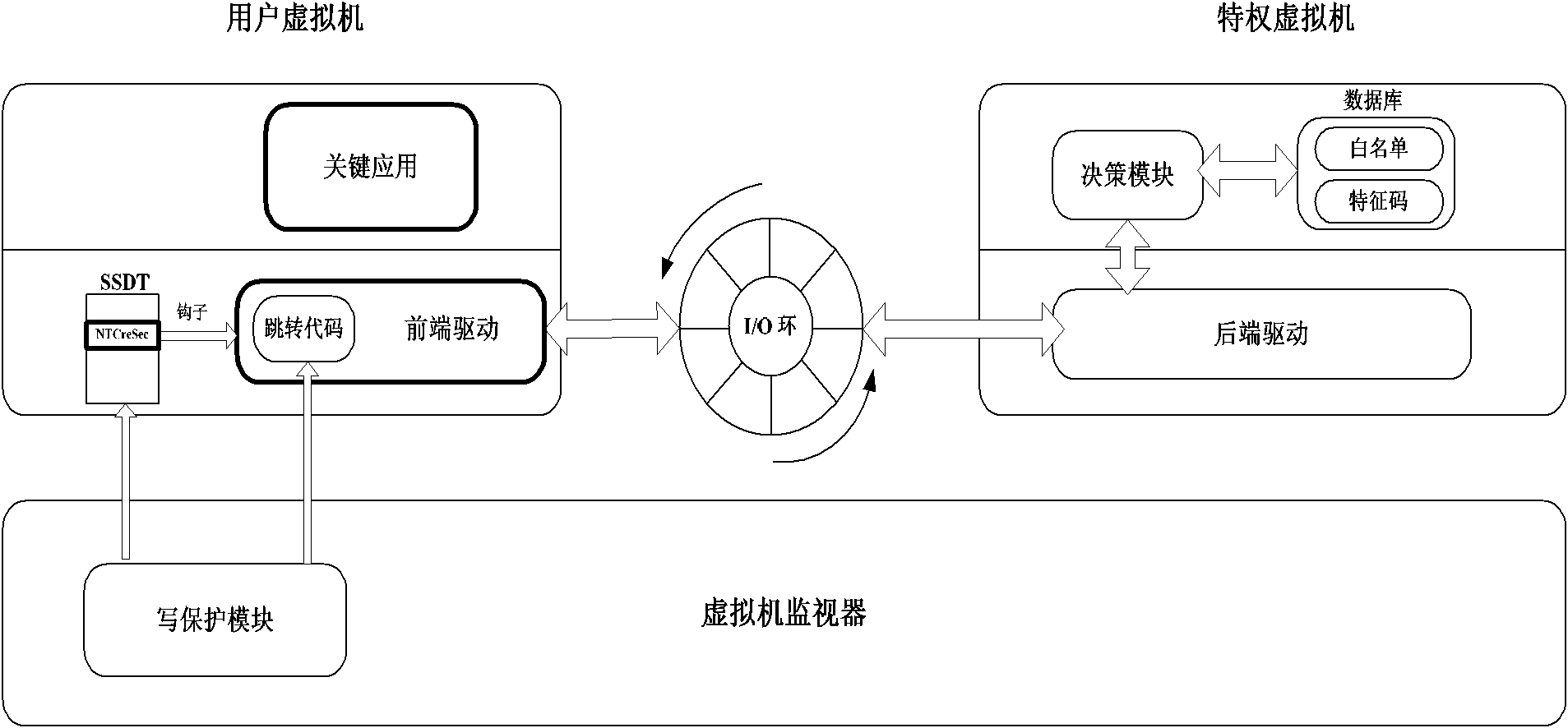
[0015] This method is implemented based on Xen, and the overall structure is a typical architecture of a type I virtual machine. In addition to Xen's own components, it contains four modules, such as figure 1 : First, the front-end driver in the protected virtual domain is implemented as a virtual PCI driver, which is responsible for intercepting system calls and communicating with the privileged virtual domain. The second component is the back-end driver in the privileged virtual domain, implemented as a kernel module, which communicates with the front-end driver, obtains system intercepted information, and passes it to the decision-making module in the user mode in the privileged virtual domain. The decision-making module is used for policy Formulation and decision-making, in our prototype system, it is a small database containing application blacklists and signatures. The fourth module is a memory protection module at the virtual machine monitor layer, which provides memory...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com